Detailed Network Design and Implementation for A4A Organization
VerifiedAdded on 2020/03/16
|26
|3940
|111
Report
AI Summary
This report details a comprehensive network design for the Academics for Academics (A4A) organization, which has offices in Sydney and Singapore. The project aims to create a secure wireless network to facilitate online registration for universities and colleges, and to enable volunteer recruitment. The report includes an executive summary, project goals, and scope, along with design requirements that encompass business and technical goals, user communities, and assumptions. It presents both logical and physical network designs, detailing IP addressing, network devices, and justifications for the design choices. The report also covers routing and switching protocols (BGP, RIP, EIGRP), security mechanisms (including firewalls), and a total cost estimation. A test plan and reflection section analyze user, business, and security requirements, compare alternative designs, and discuss the top-down network design methodology. Finally, it concludes with final documentation, designed network requirements, suggestions, and references, providing a complete overview of the proposed network solution.

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
The A4A organization interest to design a comprehensive network to provide the
wireless connection for an organization. It has the two branches such as head office and
branch offices. The head office is located at Sydney and branch office is located at Singapore.
The A4A organization funds all of its activities and projects from the public donations. It has
10 employees. The six members are located in Sydney office and four members are located in
Singapore office. It was stablished to help small private and public colleges and universities
in southeast Asia and Australia. It creates the proposed network to universities and colleges
are register the online by using wireless connection. The proposed wireless connection easily
communicates the two offices. It provides the secure wireless connection between the head
office and branch office. It meets the various requirements like security, user and business
requirements. It delivers the secure network services for an organization. It easily enable the
student to apply for recruitment to be volunteers in institutions.
1
The A4A organization interest to design a comprehensive network to provide the
wireless connection for an organization. It has the two branches such as head office and
branch offices. The head office is located at Sydney and branch office is located at Singapore.
The A4A organization funds all of its activities and projects from the public donations. It has
10 employees. The six members are located in Sydney office and four members are located in
Singapore office. It was stablished to help small private and public colleges and universities
in southeast Asia and Australia. It creates the proposed network to universities and colleges
are register the online by using wireless connection. The proposed wireless connection easily
communicates the two offices. It provides the secure wireless connection between the head
office and branch office. It meets the various requirements like security, user and business
requirements. It delivers the secure network services for an organization. It easily enable the
student to apply for recruitment to be volunteers in institutions.
1

Table of Contents
Executive Summary...............................................................................................................................1
Project Goal and Scope..........................................................................................................................2
Design Requirements.............................................................................................................................3
1. Business Goals and Constraints.................................................................................................3
2. Technical Goals and Trade-offs.................................................................................................4
3. User Communities and Network Applications...........................................................................4
4. Assumptions..............................................................................................................................4
Logical Design......................................................................................................................................4
5. Network Design.........................................................................................................................4
6. IP addressing and Naming.........................................................................................................5
7. Network Devices.....................................................................................................................11
8. Justification of Logical Design................................................................................................12
9. List of Routing and Switching Protocols.................................................................................12
10. Security Mechanisms...........................................................................................................13
Physical Network Design....................................................................................................................13
11. Network Diagram and Justification.....................................................................................13
12. IP addresses.........................................................................................................................14
13. Network components...........................................................................................................17
14. Total Cost Estimation..........................................................................................................19
15. Test plan and Test Script......................................................................................................19
Reflection............................................................................................................................................21
16. User, business and Security Requirements...........................................................................21
17. Analyse the user, business and security Requirements........................................................22
18. Compare and Contrast the possible alternative network design...........................................22
19. Top down network design methodology..............................................................................22
20. Final Documentation............................................................................................................22
21. Designed Network Requirement..........................................................................................23
22. Unit......................................................................................................................................23
23. Suggestion...........................................................................................................................23
References...........................................................................................................................................23
2
Executive Summary...............................................................................................................................1
Project Goal and Scope..........................................................................................................................2
Design Requirements.............................................................................................................................3
1. Business Goals and Constraints.................................................................................................3
2. Technical Goals and Trade-offs.................................................................................................4
3. User Communities and Network Applications...........................................................................4
4. Assumptions..............................................................................................................................4
Logical Design......................................................................................................................................4
5. Network Design.........................................................................................................................4
6. IP addressing and Naming.........................................................................................................5
7. Network Devices.....................................................................................................................11
8. Justification of Logical Design................................................................................................12
9. List of Routing and Switching Protocols.................................................................................12
10. Security Mechanisms...........................................................................................................13
Physical Network Design....................................................................................................................13
11. Network Diagram and Justification.....................................................................................13
12. IP addresses.........................................................................................................................14
13. Network components...........................................................................................................17
14. Total Cost Estimation..........................................................................................................19
15. Test plan and Test Script......................................................................................................19
Reflection............................................................................................................................................21
16. User, business and Security Requirements...........................................................................21
17. Analyse the user, business and security Requirements........................................................22
18. Compare and Contrast the possible alternative network design...........................................22
19. Top down network design methodology..............................................................................22
20. Final Documentation............................................................................................................22
21. Designed Network Requirement..........................................................................................23
22. Unit......................................................................................................................................23
23. Suggestion...........................................................................................................................23
References...........................................................................................................................................23
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Goal and Scope
Main Goal of the project is to design a comprehensive network for Academics for
academics (A4A) organization. The A4A organization has two offices like head office and
branch office. The A4A head office is located at Sydney and branch office is Singapore. The
A4A funds the overall of project and activities for public donations. The A4A organization
has the one team to provide the funds for public donations. It has a team of 10 members. The
six members are located in Sydney office and four members are located in Singapore office.
The A4A organization was helps to small private and small colleges and universities in
southeast Asia and Australia. The A4A head office and branch office are have the local
network. The A4A organization needs to creates the wireless connection by design the new
network design. The current A4A network does not allow the institutions such as universities
and colleges registrations. So, the proposed network meets the various requirements after
analysis of the A4A current network. It allows the online registration by using the wireless
connections. It easily enables the student to apply the recruitment to be volunteers in the
institutions. The proposed network provides the security and productivity and it keeps the
member information securely. The Proposed network design will be identified the design
requirements. It identified the technical goal and trade-offs for A4A organization. The logical
and physical network design will be created. The network component and IP addressing will
be identified.
Design Requirements
1. Business Goals and Constraints
The A4A organization analyse the business goals and constraints by using the top down
methodology network design. The Business constraints and goals are used to gathering the
below information for an organization. They are,
It provides the high security
It improves the communications between the client and server.
It increases the revenue.
It offers the better customer support and services.
It reduces the operational and maintenance costs.
3
Main Goal of the project is to design a comprehensive network for Academics for
academics (A4A) organization. The A4A organization has two offices like head office and
branch office. The A4A head office is located at Sydney and branch office is Singapore. The
A4A funds the overall of project and activities for public donations. The A4A organization
has the one team to provide the funds for public donations. It has a team of 10 members. The
six members are located in Sydney office and four members are located in Singapore office.
The A4A organization was helps to small private and small colleges and universities in
southeast Asia and Australia. The A4A head office and branch office are have the local
network. The A4A organization needs to creates the wireless connection by design the new
network design. The current A4A network does not allow the institutions such as universities
and colleges registrations. So, the proposed network meets the various requirements after
analysis of the A4A current network. It allows the online registration by using the wireless
connections. It easily enables the student to apply the recruitment to be volunteers in the
institutions. The proposed network provides the security and productivity and it keeps the
member information securely. The Proposed network design will be identified the design
requirements. It identified the technical goal and trade-offs for A4A organization. The logical
and physical network design will be created. The network component and IP addressing will
be identified.
Design Requirements
1. Business Goals and Constraints
The A4A organization analyse the business goals and constraints by using the top down
methodology network design. The Business constraints and goals are used to gathering the
below information for an organization. They are,
It provides the high security
It improves the communications between the client and server.
It increases the revenue.
It offers the better customer support and services.
It reduces the operational and maintenance costs.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2. Technical Goals and Trade-offs
The A4A organization technical goals and trade-offs are analysed by using the top down
network design. The Technical trade-offs provides the following information like response
and delay time requirement, jitter requirements, packet loss requirement and bandwidth
requirement. The identification of technical goals is including the network adaptability,
availability, performance, affordability, scalability, usability and manageability.
3. User Communities and Network Applications
The A4A organization user communities are support the proposed network design. It
provides the end to end network solution and high network performance. The user
communities are including the group of users to sharing the best network practices on high
performance networking to raise the end to end network performance. The user communities
are identifying the set of users and their network performance by requiring the network
applications and resources (Jisc, 2017). The network applications are used to find the network
requirement to design a proposed network.
4. Assumptions
Various assumptions are applied during the network design to increase the network
design performance. They are listed below.
Compatibility
Reliability
Availability
Stability
Scalability
Integrity
Logical Design
5. Network Design
Logical network design for Singapore branch office is shown in below.
4
The A4A organization technical goals and trade-offs are analysed by using the top down
network design. The Technical trade-offs provides the following information like response
and delay time requirement, jitter requirements, packet loss requirement and bandwidth
requirement. The identification of technical goals is including the network adaptability,
availability, performance, affordability, scalability, usability and manageability.
3. User Communities and Network Applications
The A4A organization user communities are support the proposed network design. It
provides the end to end network solution and high network performance. The user
communities are including the group of users to sharing the best network practices on high
performance networking to raise the end to end network performance. The user communities
are identifying the set of users and their network performance by requiring the network
applications and resources (Jisc, 2017). The network applications are used to find the network
requirement to design a proposed network.
4. Assumptions
Various assumptions are applied during the network design to increase the network
design performance. They are listed below.
Compatibility
Reliability
Availability
Stability
Scalability
Integrity
Logical Design
5. Network Design
Logical network design for Singapore branch office is shown in below.
4
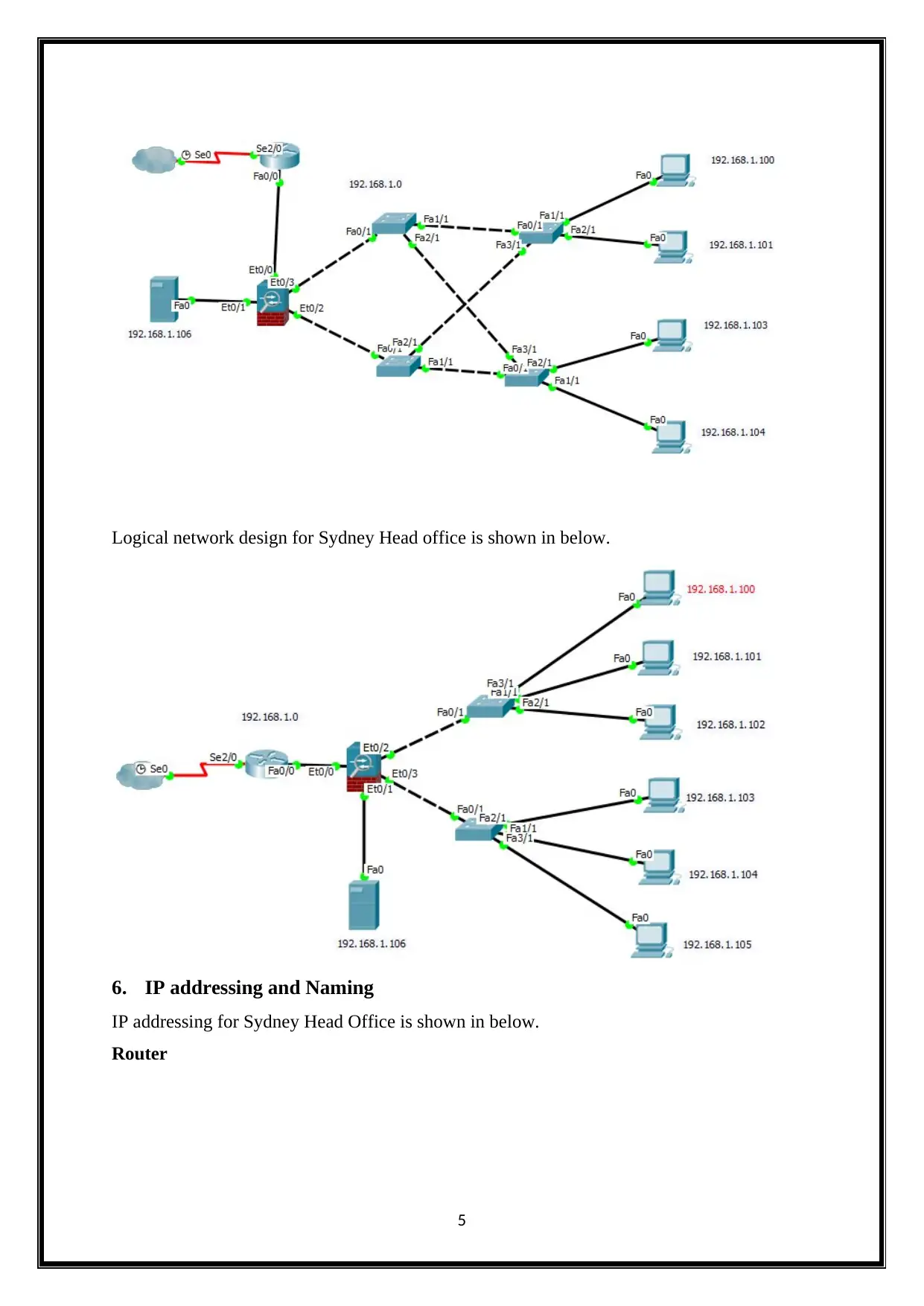
Logical network design for Sydney Head office is shown in below.
6. IP addressing and Naming
IP addressing for Sydney Head Office is shown in below.
Router
5
6. IP addressing and Naming
IP addressing for Sydney Head Office is shown in below.
Router
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The router has the IP address as 192.168.1.0,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Server
The Server has the IP address as 192.168.1.6,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Firewall
The firewall has the IP address as 192.168.1.7,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
6
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Server
The Server has the IP address as 192.168.1.6,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Firewall
The firewall has the IP address as 192.168.1.7,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
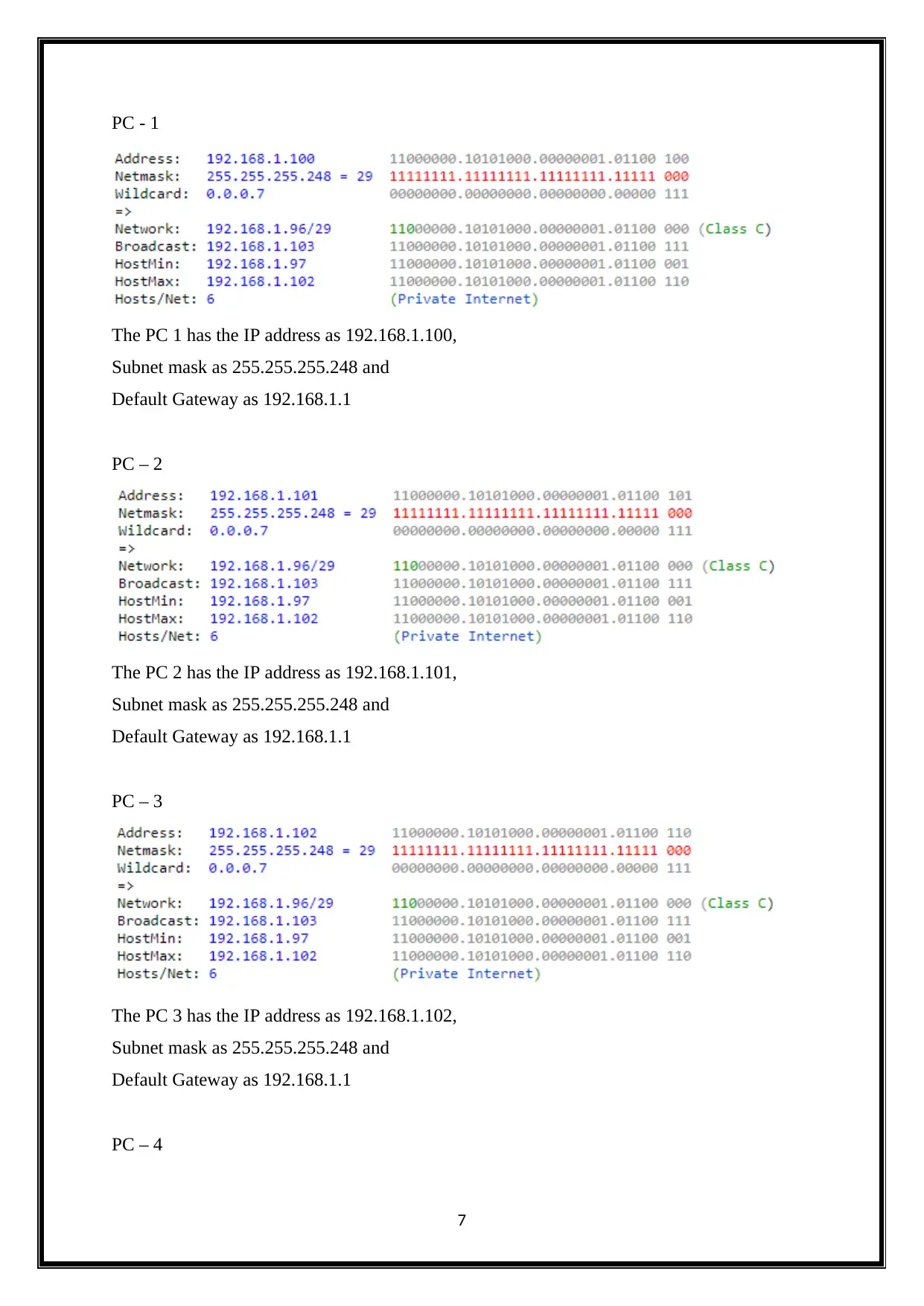
PC - 1
The PC 1 has the IP address as 192.168.1.100,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 2
The PC 2 has the IP address as 192.168.1.101,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 3
The PC 3 has the IP address as 192.168.1.102,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 4
7
The PC 1 has the IP address as 192.168.1.100,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 2
The PC 2 has the IP address as 192.168.1.101,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 3
The PC 3 has the IP address as 192.168.1.102,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 4
7
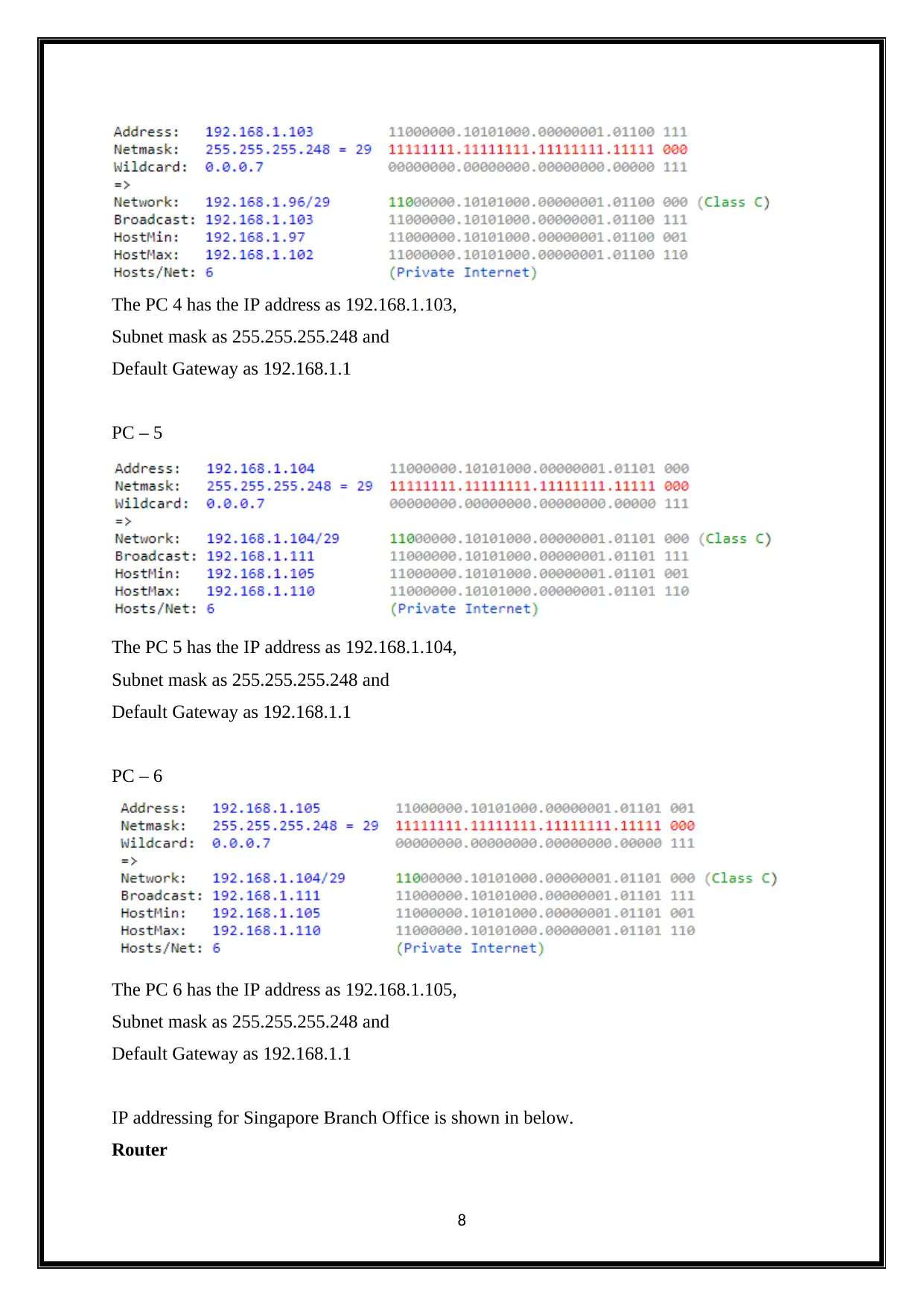
The PC 4 has the IP address as 192.168.1.103,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 5
The PC 5 has the IP address as 192.168.1.104,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 6
The PC 6 has the IP address as 192.168.1.105,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
IP addressing for Singapore Branch Office is shown in below.
Router
8
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 5
The PC 5 has the IP address as 192.168.1.104,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 6
The PC 6 has the IP address as 192.168.1.105,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
IP addressing for Singapore Branch Office is shown in below.
Router
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The router has the IP address as 192.168.1.0,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Server
The Server has the IP address as 192.168.1.104,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Firewall
The firewall has the IP address as 192.168.1.7,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
9
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Server
The Server has the IP address as 192.168.1.104,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
Firewall
The firewall has the IP address as 192.168.1.7,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
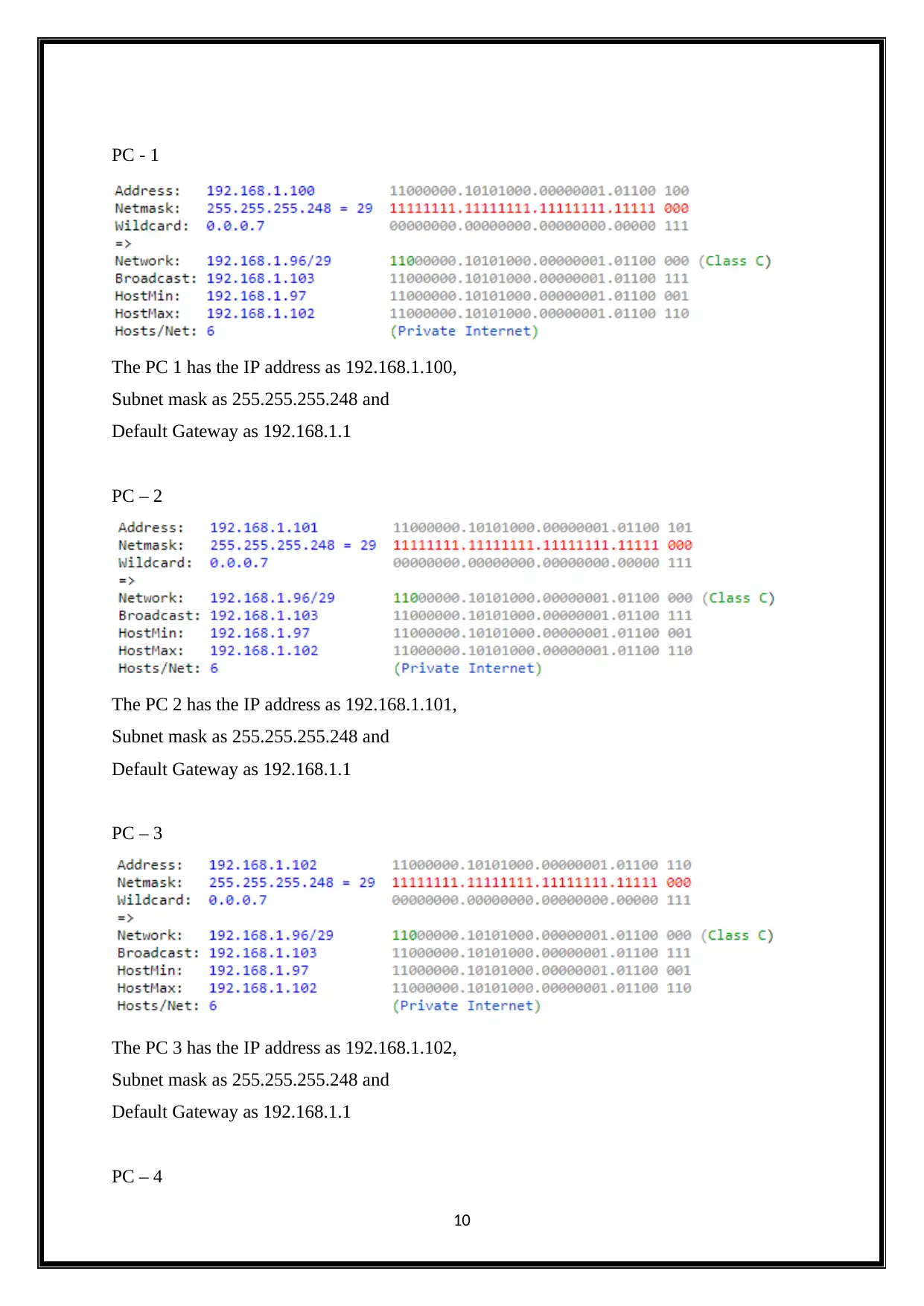
PC - 1
The PC 1 has the IP address as 192.168.1.100,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 2
The PC 2 has the IP address as 192.168.1.101,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 3
The PC 3 has the IP address as 192.168.1.102,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 4
10
The PC 1 has the IP address as 192.168.1.100,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 2
The PC 2 has the IP address as 192.168.1.101,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 3
The PC 3 has the IP address as 192.168.1.102,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1
PC – 4
10
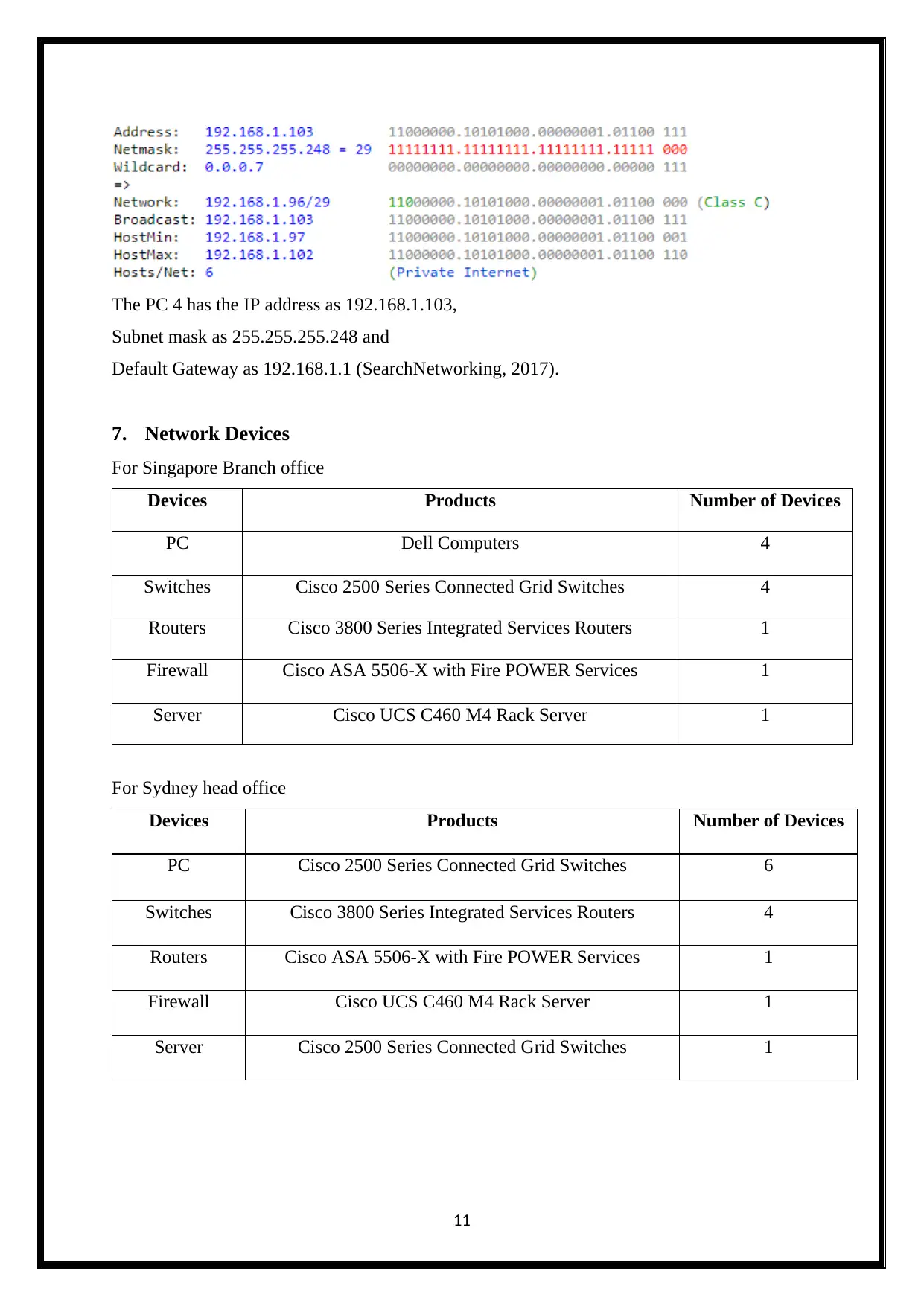
The PC 4 has the IP address as 192.168.1.103,
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1 (SearchNetworking, 2017).
7. Network Devices
For Singapore Branch office
Devices Products Number of Devices
PC Dell Computers 4
Switches Cisco 2500 Series Connected Grid Switches 4
Routers Cisco 3800 Series Integrated Services Routers 1
Firewall Cisco ASA 5506-X with Fire POWER Services 1
Server Cisco UCS C460 M4 Rack Server 1
For Sydney head office
Devices Products Number of Devices
PC Cisco 2500 Series Connected Grid Switches 6
Switches Cisco 3800 Series Integrated Services Routers 4
Routers Cisco ASA 5506-X with Fire POWER Services 1
Firewall Cisco UCS C460 M4 Rack Server 1
Server Cisco 2500 Series Connected Grid Switches 1
11
Subnet mask as 255.255.255.248 and
Default Gateway as 192.168.1.1 (SearchNetworking, 2017).
7. Network Devices
For Singapore Branch office
Devices Products Number of Devices
PC Dell Computers 4
Switches Cisco 2500 Series Connected Grid Switches 4
Routers Cisco 3800 Series Integrated Services Routers 1
Firewall Cisco ASA 5506-X with Fire POWER Services 1
Server Cisco UCS C460 M4 Rack Server 1
For Sydney head office
Devices Products Number of Devices
PC Cisco 2500 Series Connected Grid Switches 6
Switches Cisco 3800 Series Integrated Services Routers 4
Routers Cisco ASA 5506-X with Fire POWER Services 1
Firewall Cisco UCS C460 M4 Rack Server 1
Server Cisco 2500 Series Connected Grid Switches 1
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

![Designing A4A's Logical and Physical Network - [Course Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fsr%2F670b95c66d3b44ffa9310d4645c6b62e.jpg&w=256&q=75)



