A Comprehensive Report on Wireless Network Routing and Security
VerifiedAdded on 2020/04/29
|9
|1050
|121
Report
AI Summary
This report provides a comprehensive overview of wireless network security, addressing the increasing deployment of wireless networks and the associated security risks. It delves into the causes of security issues, highlighting the weaknesses of network protocols and inherent characteristics of wireless networks. The report then explores various security measures, including cryptography and authentication, and discusses different security levels such as confidential, restricted, and unclassified access. Furthermore, it examines several security schemes developed for wireless sensor networks, detailing their features and the attacks they are designed to deter, such as wormhole attacks, Sybil attacks, and jamming. The conclusion emphasizes the importance of stronger protocols and schemes to mitigate and prevent security threats in widely used wireless networks, supported by references to relevant research and government publications.

WIRELESS NETWORK
ROUTING AND SWITCHING
ROUTING AND SWITCHING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORK
Contents
ROUTING AND SWITCHING..........................................................................................4
INTRODUCTION...............................................................................................................4
WIRELESS NETWORK SECURITY................................................................................4
Causes..........................................................................................................................................5
Security Measures........................................................................................................................5
Security Levels............................................................................................................................5
Security Schemes.........................................................................................................................6
CONCLUSION....................................................................................................................9
REFERENCES....................................................................................................................9
Contents
ROUTING AND SWITCHING..........................................................................................4
INTRODUCTION...............................................................................................................4
WIRELESS NETWORK SECURITY................................................................................4
Causes..........................................................................................................................................5
Security Measures........................................................................................................................5
Security Levels............................................................................................................................5
Security Schemes.........................................................................................................................6
CONCLUSION....................................................................................................................9
REFERENCES....................................................................................................................9

WIRELESS NETWORK
ROUTING AND SWITCHING
INTRODUCTION
The advancement of technology, consistently, with increasing performance
and decreased prices, accessibility of the internet through wireless is increasingly
deployed in public as well as the office environments. When there are numerous
stakeholders are involved, connecting digitally, it is quite possible to experience
security risks and threats, in the network (EFTA, 2014). Best and secured practices
have become mandatory to deploy in the network, along with the privileges.
WIRELESS NETWORK SECURITY
Wireless network is established through wireless local area network and
wireless communication is established through the Access Point hardware, like
mobile computers, PDAs, etc. connecting the network with no wire. Most of the
networks provide access to the network through open system authentication, with
the 802.11 standard through, a default protocol.
ROUTING AND SWITCHING
INTRODUCTION
The advancement of technology, consistently, with increasing performance
and decreased prices, accessibility of the internet through wireless is increasingly
deployed in public as well as the office environments. When there are numerous
stakeholders are involved, connecting digitally, it is quite possible to experience
security risks and threats, in the network (EFTA, 2014). Best and secured practices
have become mandatory to deploy in the network, along with the privileges.
WIRELESS NETWORK SECURITY
Wireless network is established through wireless local area network and
wireless communication is established through the Access Point hardware, like
mobile computers, PDAs, etc. connecting the network with no wire. Most of the
networks provide access to the network through open system authentication, with
the 802.11 standard through, a default protocol.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
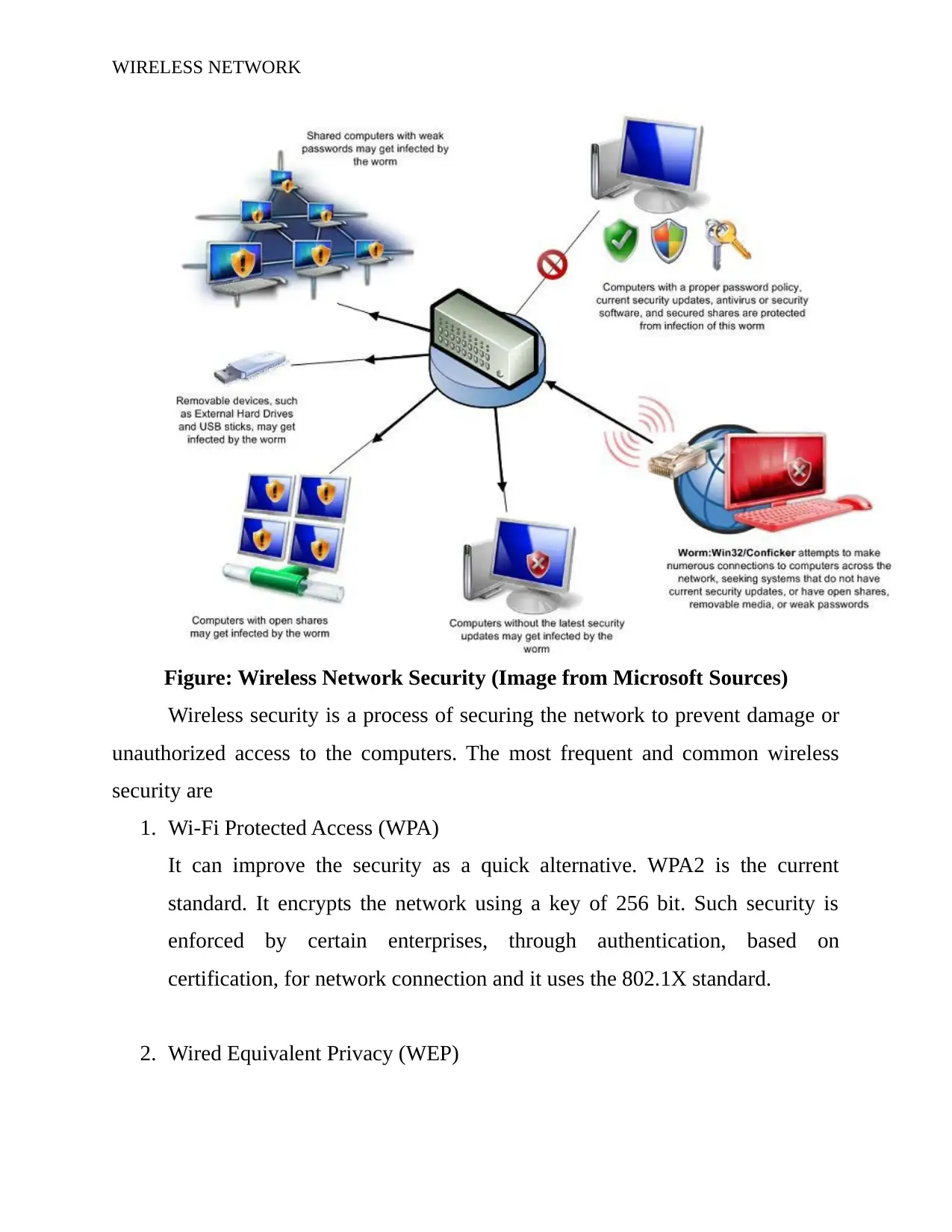
WIRELESS NETWORK
Figure: Wireless Network Security (Image from Microsoft Sources)
Wireless security is a process of securing the network to prevent damage or
unauthorized access to the computers. The most frequent and common wireless
security are
1. Wi-Fi Protected Access (WPA)
It can improve the security as a quick alternative. WPA2 is the current
standard. It encrypts the network using a key of 256 bit. Such security is
enforced by certain enterprises, through authentication, based on
certification, for network connection and it uses the 802.1X standard.
2. Wired Equivalent Privacy (WEP)
Figure: Wireless Network Security (Image from Microsoft Sources)
Wireless security is a process of securing the network to prevent damage or
unauthorized access to the computers. The most frequent and common wireless
security are
1. Wi-Fi Protected Access (WPA)
It can improve the security as a quick alternative. WPA2 is the current
standard. It encrypts the network using a key of 256 bit. Such security is
enforced by certain enterprises, through authentication, based on
certification, for network connection and it uses the 802.1X standard.
2. Wired Equivalent Privacy (WEP)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORK
It is a weak standard of security as its password can be easily discovered
with certain software tools. It is outdated.
Causes
The causes of more security issues and threats in the wireless networks are
because of the are the weakness of the protocols of the wireless network and
inherent characteristics of the network (Ramin et al, 2014). Eventually, these issues
are to be explored and discovered to counteract, before applying the wireless
network in specific environment, either in office or public spaces.
Security Measures
The primary security measures in wireless network are established by
cryptography, a standard secrecy method, towards protection of the information to
be transmitted, from unauthorized access, by unauthorized users. Various users of
the wireless network need and authenticated for various levels of data and
information. Other measure is an establishment of covert communication, where
the communication existence is concealed, against any possible threats or
adversaries (Boyle et al, 2015).
Security Levels
Security of network can be preserved by providing limited levels of
privileges for access of the data, as the following.
1. Confidential – Sufficient transmission encryption security and authentication
controls attain the encryption needed to provide access to the information
that is confidential. Strong encryption and authentication tunnel can be
provided by using VPN, over the connection of WLAN (Wireless Local
Area Network). Configuration policies and proper key management can
make it more secured.
2. Restricted – it needs higher level of authentication, for more private data.
It is a weak standard of security as its password can be easily discovered
with certain software tools. It is outdated.
Causes
The causes of more security issues and threats in the wireless networks are
because of the are the weakness of the protocols of the wireless network and
inherent characteristics of the network (Ramin et al, 2014). Eventually, these issues
are to be explored and discovered to counteract, before applying the wireless
network in specific environment, either in office or public spaces.
Security Measures
The primary security measures in wireless network are established by
cryptography, a standard secrecy method, towards protection of the information to
be transmitted, from unauthorized access, by unauthorized users. Various users of
the wireless network need and authenticated for various levels of data and
information. Other measure is an establishment of covert communication, where
the communication existence is concealed, against any possible threats or
adversaries (Boyle et al, 2015).
Security Levels
Security of network can be preserved by providing limited levels of
privileges for access of the data, as the following.
1. Confidential – Sufficient transmission encryption security and authentication
controls attain the encryption needed to provide access to the information
that is confidential. Strong encryption and authentication tunnel can be
provided by using VPN, over the connection of WLAN (Wireless Local
Area Network). Configuration policies and proper key management can
make it more secured.
2. Restricted – it needs higher level of authentication, for more private data.
WIRELESS NETWORK
3. Unclassified – This is high level of private data, which is accessed by higher
level of management and authentication. Usually, key business data or
deeper personal data is accessed with this highest authorization level.
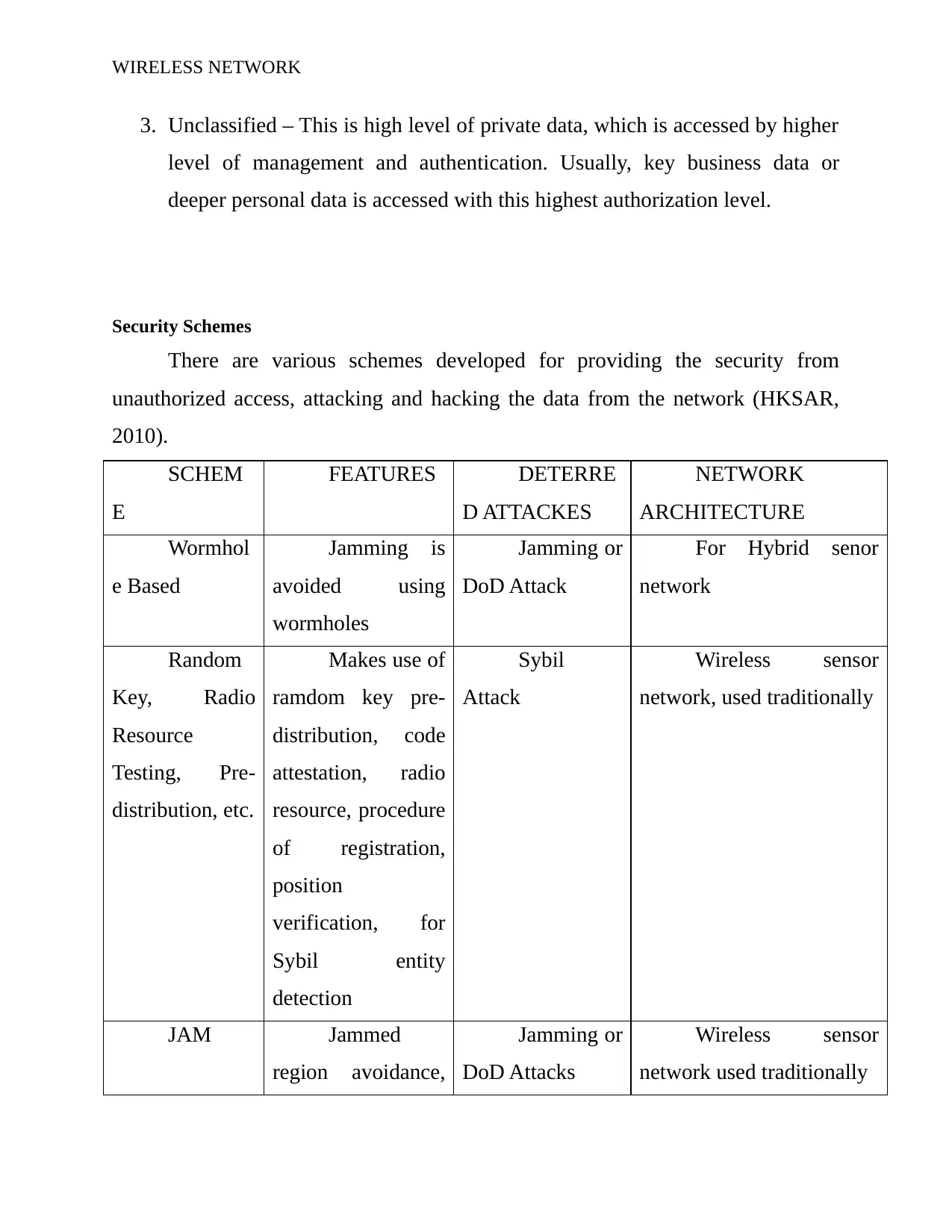
Security Schemes
There are various schemes developed for providing the security from
unauthorized access, attacking and hacking the data from the network (HKSAR,
2010).
SCHEM
E
FEATURES DETERRE
D ATTACKES
NETWORK
ARCHITECTURE
Wormhol
e Based
Jamming is
avoided using
wormholes
Jamming or
DoD Attack
For Hybrid senor
network
Random
Key, Radio
Resource
Testing, Pre-
distribution, etc.
Makes use of
ramdom key pre-
distribution, code
attestation, radio
resource, procedure
of registration,
position
verification, for
Sybil entity
detection
Sybil
Attack
Wireless sensor
network, used traditionally
JAM Jammed
region avoidance,
Jamming or
DoD Attacks
Wireless sensor
network used traditionally
3. Unclassified – This is high level of private data, which is accessed by higher
level of management and authentication. Usually, key business data or
deeper personal data is accessed with this highest authorization level.
Security Schemes
There are various schemes developed for providing the security from
unauthorized access, attacking and hacking the data from the network (HKSAR,
2010).
SCHEM
E
FEATURES DETERRE
D ATTACKES
NETWORK
ARCHITECTURE
Wormhol
e Based
Jamming is
avoided using
wormholes
Jamming or
DoD Attack
For Hybrid senor
network
Random
Key, Radio
Resource
Testing, Pre-
distribution, etc.
Makes use of
ramdom key pre-
distribution, code
attestation, radio
resource, procedure
of registration,
position
verification, for
Sybil entity
detection
Sybil
Attack
Wireless sensor
network, used traditionally
JAM Jammed
region avoidance,
Jamming or
DoD Attacks
Wireless sensor
network used traditionally
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
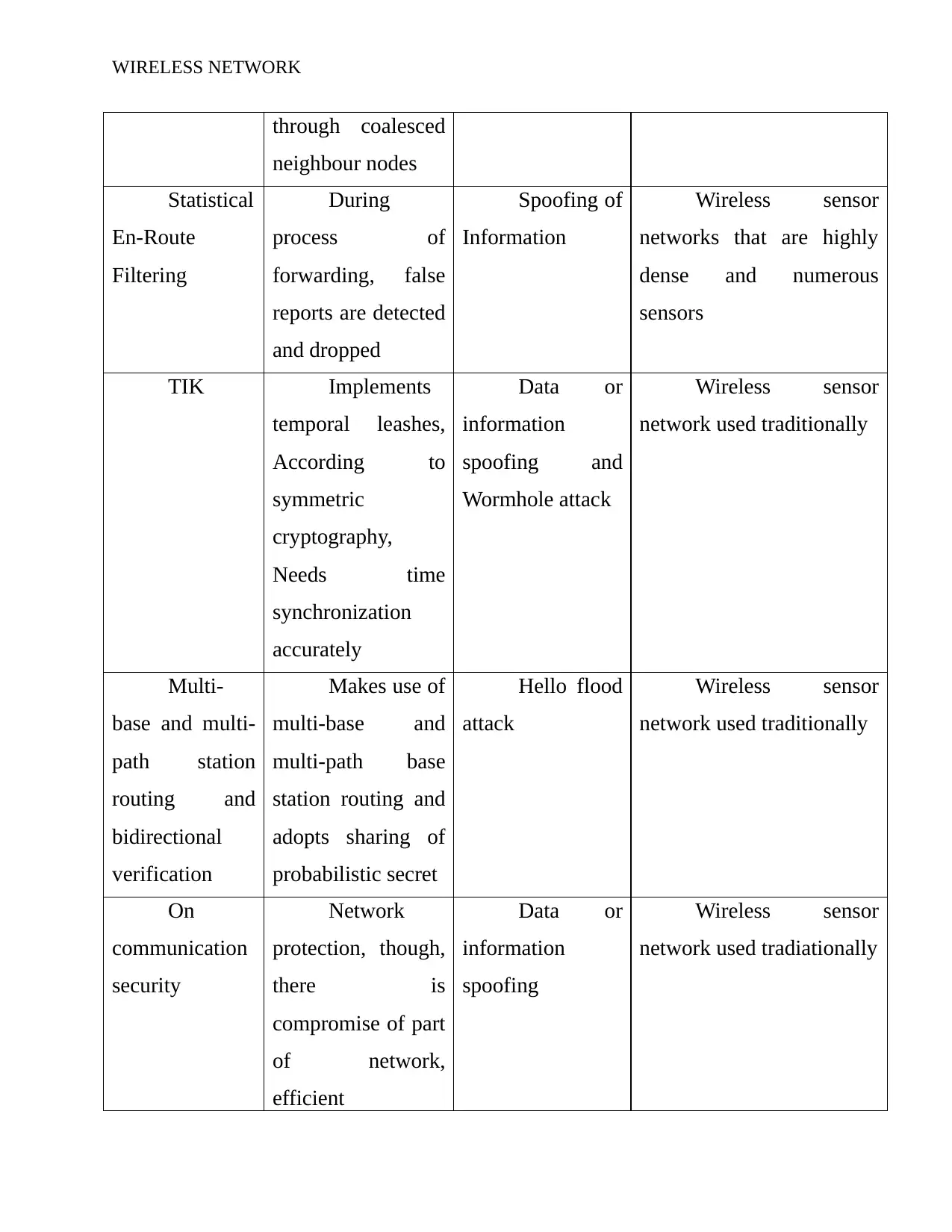
WIRELESS NETWORK
through coalesced
neighbour nodes
Statistical
En-Route
Filtering
During
process of
forwarding, false
reports are detected
and dropped
Spoofing of
Information
Wireless sensor
networks that are highly
dense and numerous
sensors
TIK Implements
temporal leashes,
According to
symmetric
cryptography,
Needs time
synchronization
accurately
Data or
information
spoofing and
Wormhole attack
Wireless sensor
network used traditionally
Multi-
base and multi-
path station
routing and
bidirectional
verification
Makes use of
multi-base and
multi-path base
station routing and
adopts sharing of
probabilistic secret
Hello flood
attack
Wireless sensor
network used traditionally
On
communication
security
Network
protection, though,
there is
compromise of part
of network,
efficient
Data or
information
spoofing
Wireless sensor
network used tradiationally
through coalesced
neighbour nodes
Statistical
En-Route
Filtering
During
process of
forwarding, false
reports are detected
and dropped
Spoofing of
Information
Wireless sensor
networks that are highly
dense and numerous
sensors
TIK Implements
temporal leashes,
According to
symmetric
cryptography,
Needs time
synchronization
accurately
Data or
information
spoofing and
Wormhole attack
Wireless sensor
network used traditionally
Multi-
base and multi-
path station
routing and
bidirectional
verification
Makes use of
multi-base and
multi-path base
station routing and
adopts sharing of
probabilistic secret
Hello flood
attack
Wireless sensor
network used traditionally
On
communication
security
Network
protection, though,
there is
compromise of part
of network,
efficient
Data or
information
spoofing
Wireless sensor
network used tradiationally
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
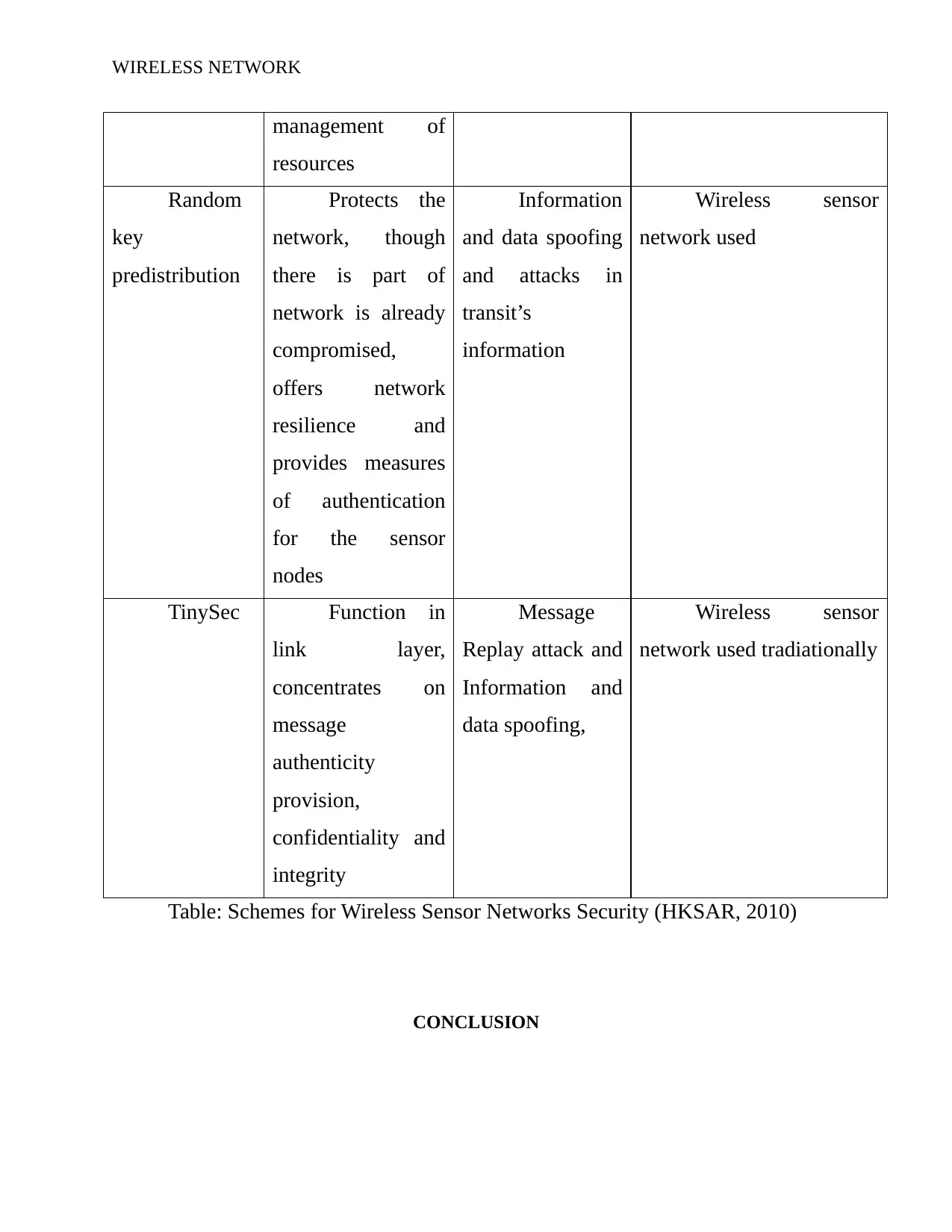
WIRELESS NETWORK
management of
resources
Random
key
predistribution
Protects the
network, though
there is part of
network is already
compromised,
offers network
resilience and
provides measures
of authentication
for the sensor
nodes
Information
and data spoofing
and attacks in
transit’s
information
Wireless sensor
network used
TinySec Function in
link layer,
concentrates on
message
authenticity
provision,
confidentiality and
integrity
Message
Replay attack and
Information and
data spoofing,
Wireless sensor
network used tradiationally
Table: Schemes for Wireless Sensor Networks Security (HKSAR, 2010)
CONCLUSION
management of
resources
Random
key
predistribution
Protects the
network, though
there is part of
network is already
compromised,
offers network
resilience and
provides measures
of authentication
for the sensor
nodes
Information
and data spoofing
and attacks in
transit’s
information
Wireless sensor
network used
TinySec Function in
link layer,
concentrates on
message
authenticity
provision,
confidentiality and
integrity
Message
Replay attack and
Information and
data spoofing,
Wireless sensor
network used tradiationally
Table: Schemes for Wireless Sensor Networks Security (HKSAR, 2010)
CONCLUSION

WIRELESS NETWORK
Wireless network is widely spread and so widely prone to security threats.
The threats can be mitigated and prevented only through stronger protocols and
schemes.
REFERENCES
1. HKSAR, Wireless Networking Security, (2010), The Government of the
Hong Kong Special Administrative Region, Hong Kong.
2. EFTA, (2014). "SECURITY VULNERABILITIES AND RISKS IN
INDUSTRIAL USAGE OF WIRELESS COMMUNICATION". IEEE ETFA
2014 - 19th IEEE International Conference on Emerging Technology and
Factory Automation
3. Ramin, S., Boulat, B., Dennis, G., Saikat, G., Don, T. (2014). "Covert
Single-hop Communication in a Wireless Network with Distributed
Artificial Noise Generation". arXiv:
4. Boyle, Randall, Panko, Raymond. (2015). Corporate Computer Security.
Upper Saddle River, New Jersey
Wireless network is widely spread and so widely prone to security threats.
The threats can be mitigated and prevented only through stronger protocols and
schemes.
REFERENCES
1. HKSAR, Wireless Networking Security, (2010), The Government of the
Hong Kong Special Administrative Region, Hong Kong.
2. EFTA, (2014). "SECURITY VULNERABILITIES AND RISKS IN
INDUSTRIAL USAGE OF WIRELESS COMMUNICATION". IEEE ETFA
2014 - 19th IEEE International Conference on Emerging Technology and
Factory Automation
3. Ramin, S., Boulat, B., Dennis, G., Saikat, G., Don, T. (2014). "Covert
Single-hop Communication in a Wireless Network with Distributed
Artificial Noise Generation". arXiv:
4. Boyle, Randall, Panko, Raymond. (2015). Corporate Computer Security.
Upper Saddle River, New Jersey
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




