Wireless Network and Communication
VerifiedAdded on 2023/04/04
|14
|1646
|156
AI Summary
This document discusses various topics related to wireless network and communication, including modulation techniques, frequency assignments, analog and frequency modulation waveforms, error detection process, frame check sequence computation, direct sequence spread spectrum, infrastructure and ad hoc modes in WLAN, and a comparison of TCP and OSI protocols for wired and wireless LANs. It also explains why hexagonal shape cells are more appropriate for cellular communications compared to square and circle shapes.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: - WIRELESS NETWORK AND COMMUNICATION
WIRELESS NETWORK AND COMMUNICATION
Name of the Student
Name of the University
Author Note
WIRELESS NETWORK AND COMMUNICATION
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
1WIRELESS NETWORK AND COMMUNICATION
Assignment No-2
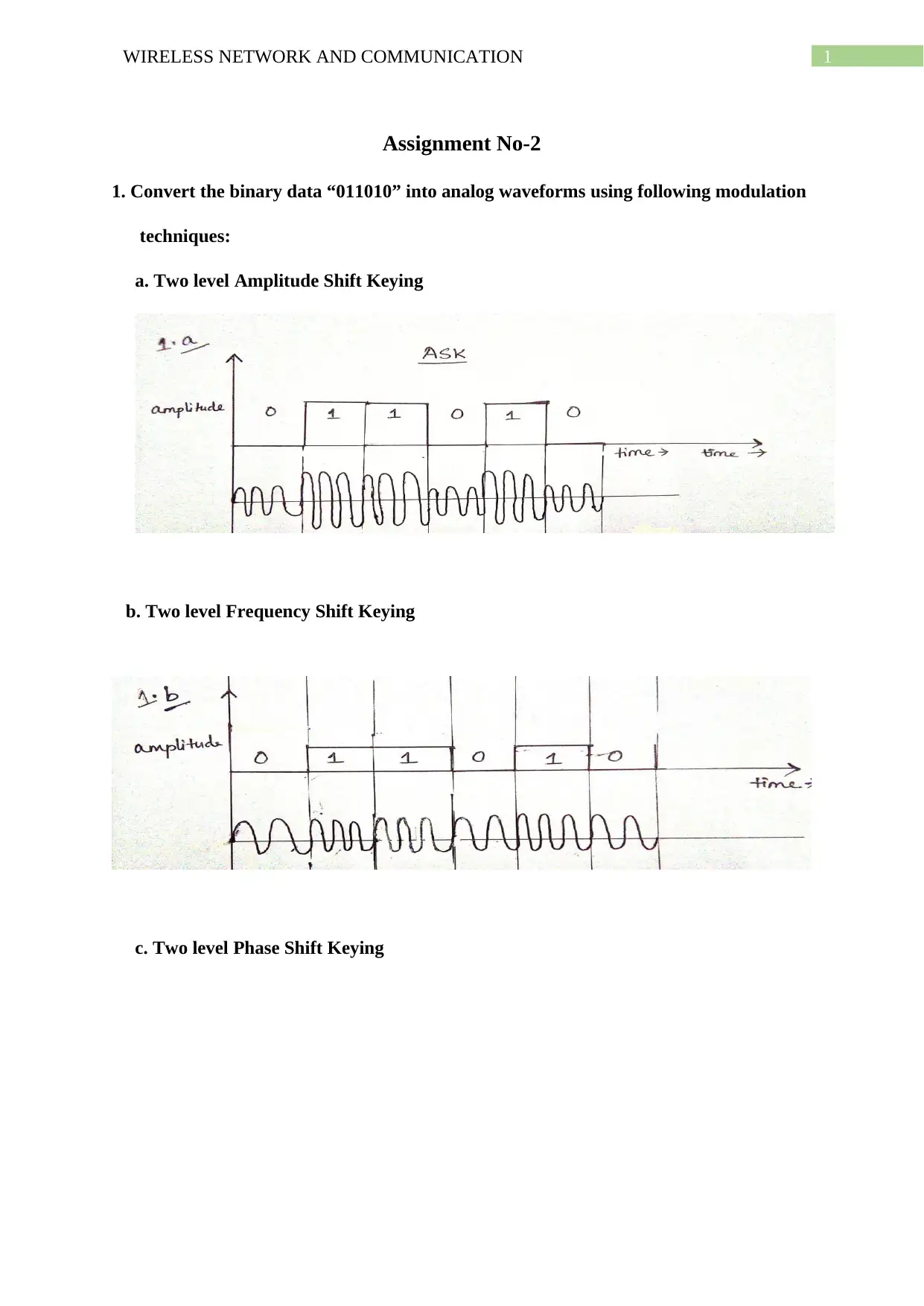
1. Convert the binary data “011010” into analog waveforms using following modulation
techniques:
a. Two level Amplitude Shift Keying
b. Two level Frequency Shift Keying
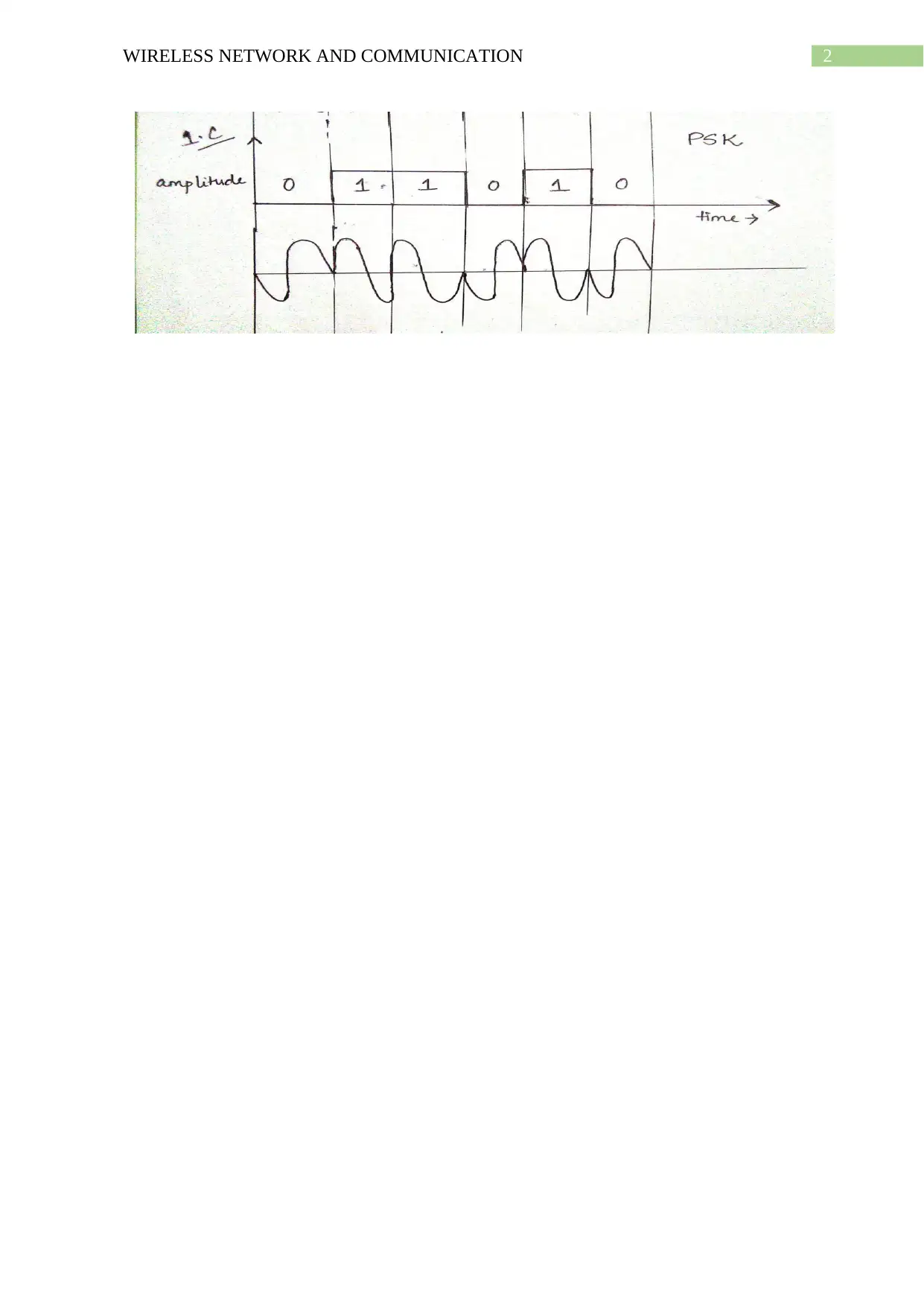
c. Two level Phase Shift Keying
Assignment No-2
1. Convert the binary data “011010” into analog waveforms using following modulation
techniques:
a. Two level Amplitude Shift Keying
b. Two level Frequency Shift Keying
c. Two level Phase Shift Keying
2WIRELESS NETWORK AND COMMUNICATION
3WIRELESS NETWORK AND COMMUNICATION
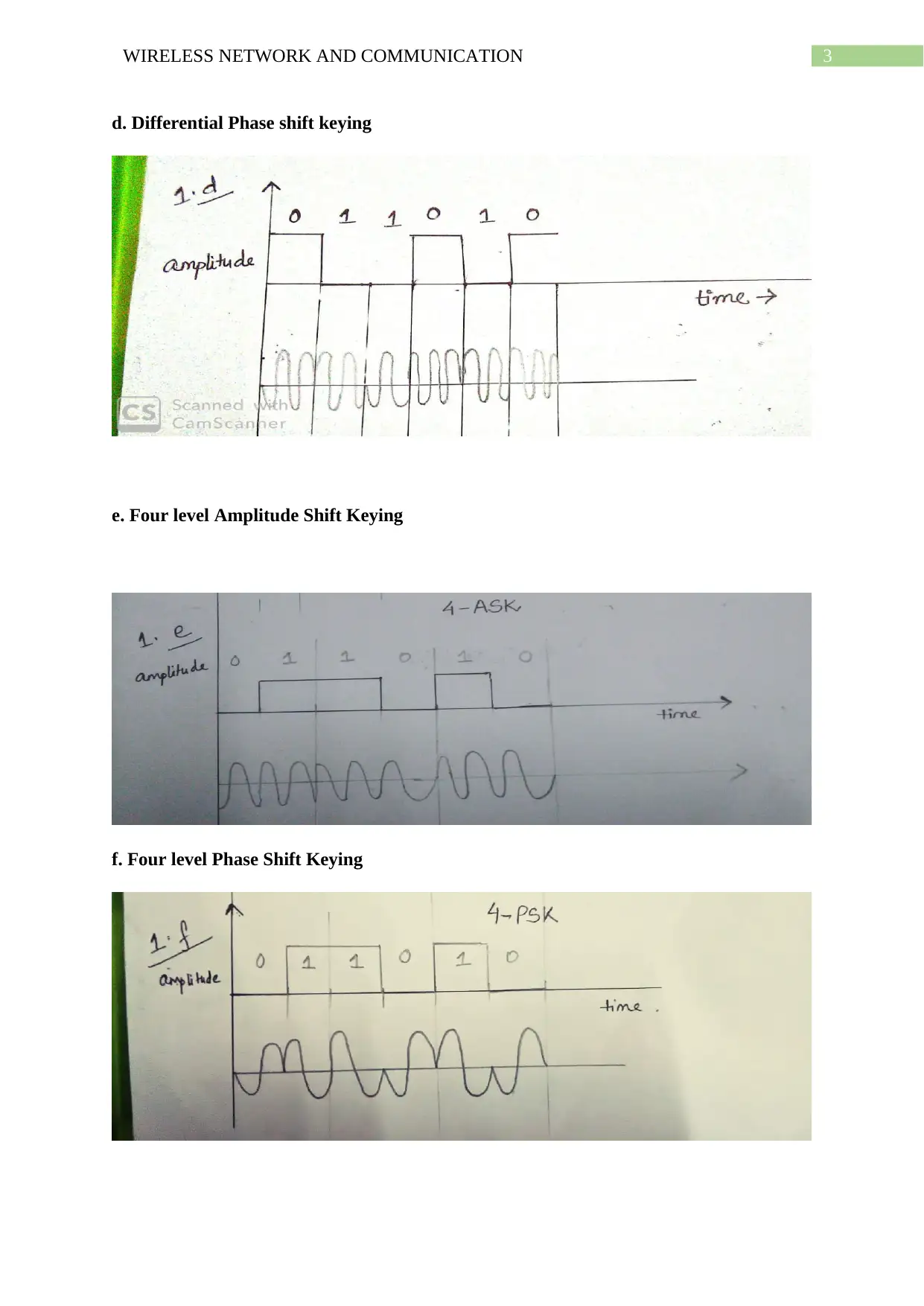
d. Differential Phase shift keying
e. Four level Amplitude Shift Keying
f. Four level Phase Shift Keying
d. Differential Phase shift keying
e. Four level Amplitude Shift Keying
f. Four level Phase Shift Keying
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4WIRELESS NETWORK AND COMMUNICATION
g. Eight level Amplitude Shift Keying
2. With fc = 500 kHz, fd = 25 kHz, and M = 16 (L = 4 bits), compute the frequency
assignments for each of the sixteen possible 4-bit data combinations.
Given: -
fc = 500 kHz, fd = 25 kHz, and M = 16, L = 4 bits
fi=fc + (2i – 1 – M) *fd
M=2^L =2^4 = 16, M=16
0000 where i=1, f1= 125KHz
0001 where i=2, f2= 175KHZ
0010 where i=3, f3= 225KHZ
0011 where i=4, f4= 275KHz
0100 where i=5, f5= 325KHz
0101 where i=6, f6= 375KHz
0110 where i=7, f7= 425KHz
0111 where i=8, f8=475KHz
1000 where i=9, f9=525KHz
1001 where i=10, f10= 575KHz
1010 where i=11, f11= 625KHz
g. Eight level Amplitude Shift Keying
2. With fc = 500 kHz, fd = 25 kHz, and M = 16 (L = 4 bits), compute the frequency
assignments for each of the sixteen possible 4-bit data combinations.
Given: -
fc = 500 kHz, fd = 25 kHz, and M = 16, L = 4 bits
fi=fc + (2i – 1 – M) *fd
M=2^L =2^4 = 16, M=16
0000 where i=1, f1= 125KHz
0001 where i=2, f2= 175KHZ
0010 where i=3, f3= 225KHZ
0011 where i=4, f4= 275KHz
0100 where i=5, f5= 325KHz
0101 where i=6, f6= 375KHz
0110 where i=7, f7= 425KHz
0111 where i=8, f8=475KHz
1000 where i=9, f9=525KHz
1001 where i=10, f10= 575KHz
1010 where i=11, f11= 625KHz
5WIRELESS NETWORK AND COMMUNICATION
1011 where i=12, f12=675KHz
1100 where i=13, f13= 725KHz
1101 where i=14, f14=775KHz
1110 where i=15, f15=825KHz
1111 where i=16, f16=875KHz
This scheme can support data rate of
1/Tb = 2Lfd = 2*4*25 = 200Kbps
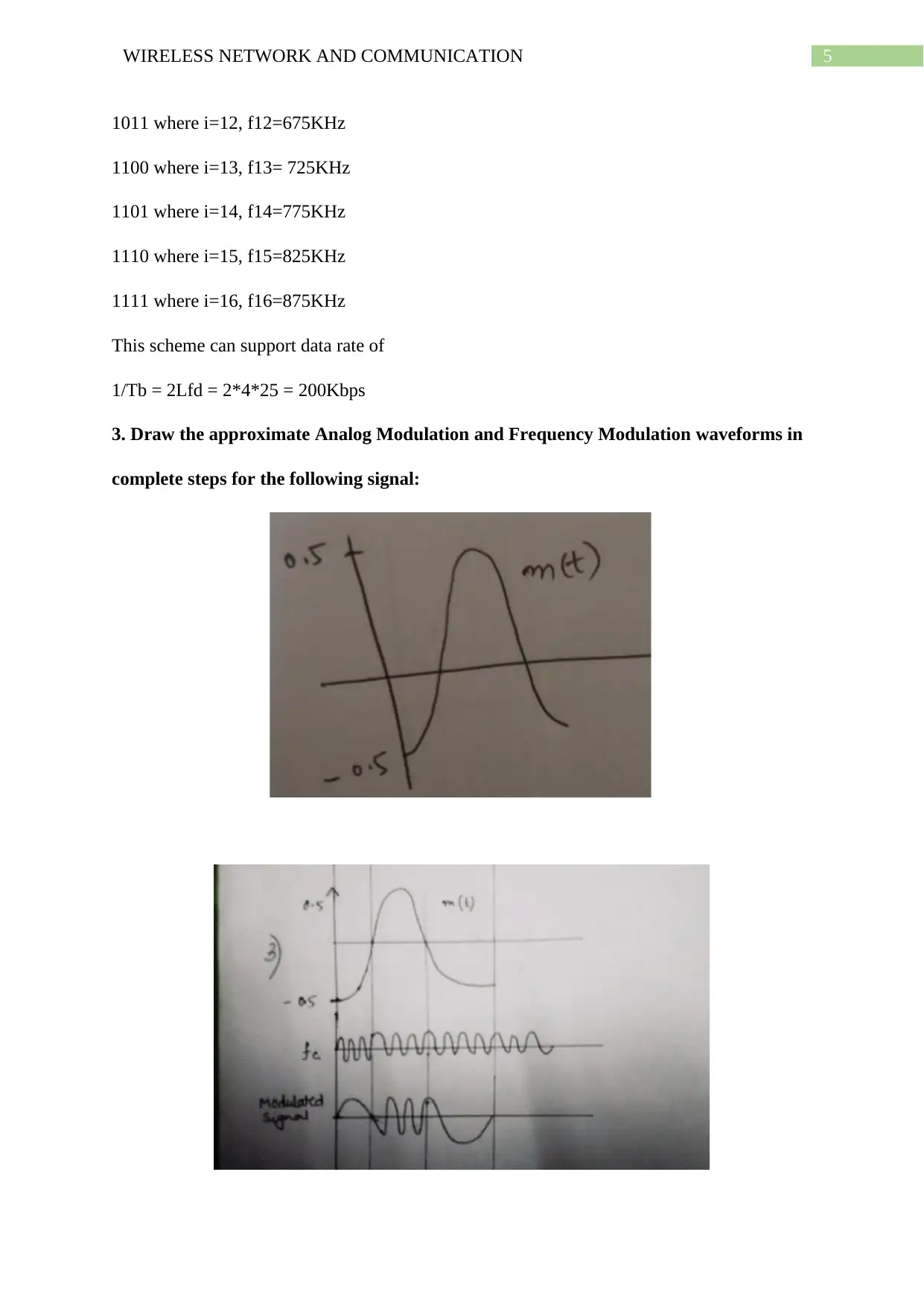
3. Draw the approximate Analog Modulation and Frequency Modulation waveforms in
complete steps for the following signal:
1011 where i=12, f12=675KHz
1100 where i=13, f13= 725KHz
1101 where i=14, f14=775KHz
1110 where i=15, f15=825KHz
1111 where i=16, f16=875KHz
This scheme can support data rate of
1/Tb = 2Lfd = 2*4*25 = 200Kbps
3. Draw the approximate Analog Modulation and Frequency Modulation waveforms in
complete steps for the following signal:
6WIRELESS NETWORK AND COMMUNICATION
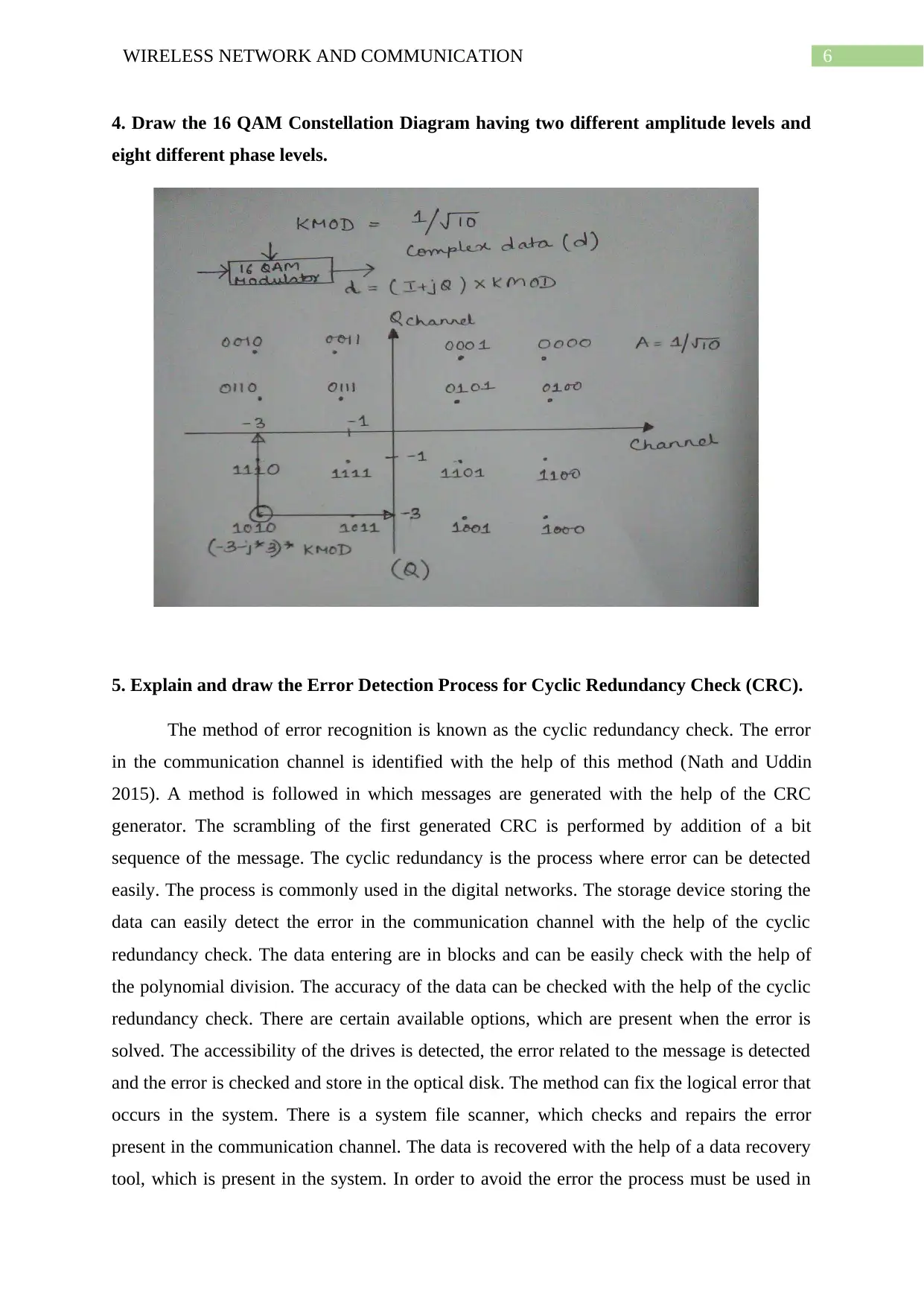
4. Draw the 16 QAM Constellation Diagram having two different amplitude levels and
eight different phase levels.
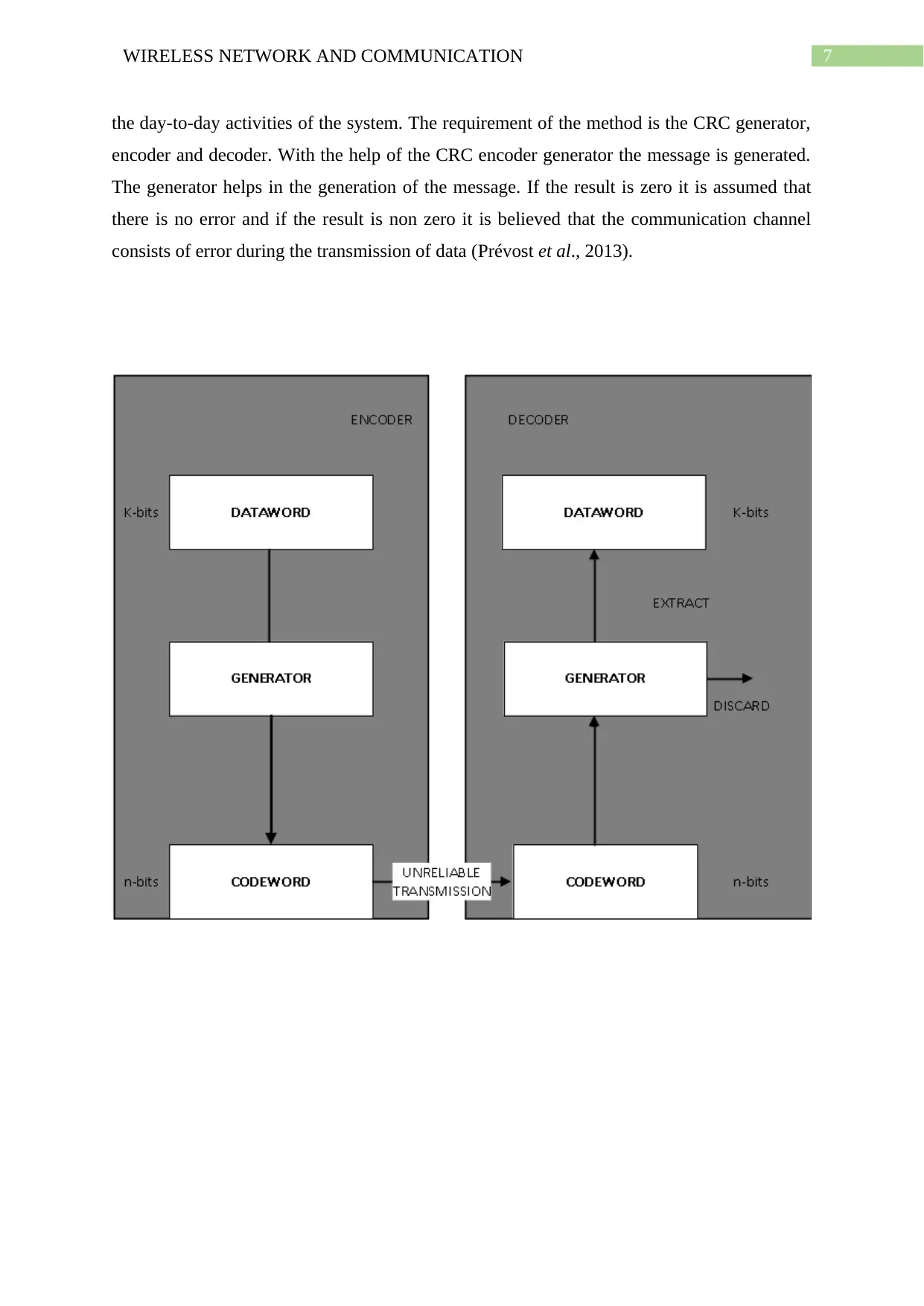
5. Explain and draw the Error Detection Process for Cyclic Redundancy Check (CRC).
The method of error recognition is known as the cyclic redundancy check. The error
in the communication channel is identified with the help of this method (Nath and Uddin
2015). A method is followed in which messages are generated with the help of the CRC
generator. The scrambling of the first generated CRC is performed by addition of a bit
sequence of the message. The cyclic redundancy is the process where error can be detected
easily. The process is commonly used in the digital networks. The storage device storing the
data can easily detect the error in the communication channel with the help of the cyclic
redundancy check. The data entering are in blocks and can be easily check with the help of
the polynomial division. The accuracy of the data can be checked with the help of the cyclic
redundancy check. There are certain available options, which are present when the error is
solved. The accessibility of the drives is detected, the error related to the message is detected
and the error is checked and store in the optical disk. The method can fix the logical error that
occurs in the system. There is a system file scanner, which checks and repairs the error
present in the communication channel. The data is recovered with the help of a data recovery
tool, which is present in the system. In order to avoid the error the process must be used in
4. Draw the 16 QAM Constellation Diagram having two different amplitude levels and
eight different phase levels.
5. Explain and draw the Error Detection Process for Cyclic Redundancy Check (CRC).
The method of error recognition is known as the cyclic redundancy check. The error
in the communication channel is identified with the help of this method (Nath and Uddin
2015). A method is followed in which messages are generated with the help of the CRC
generator. The scrambling of the first generated CRC is performed by addition of a bit
sequence of the message. The cyclic redundancy is the process where error can be detected
easily. The process is commonly used in the digital networks. The storage device storing the
data can easily detect the error in the communication channel with the help of the cyclic
redundancy check. The data entering are in blocks and can be easily check with the help of
the polynomial division. The accuracy of the data can be checked with the help of the cyclic
redundancy check. There are certain available options, which are present when the error is
solved. The accessibility of the drives is detected, the error related to the message is detected
and the error is checked and store in the optical disk. The method can fix the logical error that
occurs in the system. There is a system file scanner, which checks and repairs the error
present in the communication channel. The data is recovered with the help of a data recovery
tool, which is present in the system. In order to avoid the error the process must be used in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7WIRELESS NETWORK AND COMMUNICATION
the day-to-day activities of the system. The requirement of the method is the CRC generator,
encoder and decoder. With the help of the CRC encoder generator the message is generated.
The generator helps in the generation of the message. If the result is zero it is assumed that
there is no error and if the result is non zero it is believed that the communication channel
consists of error during the transmission of data (Prévost et al., 2013).
the day-to-day activities of the system. The requirement of the method is the CRC generator,
encoder and decoder. With the help of the CRC encoder generator the message is generated.
The generator helps in the generation of the message. If the result is zero it is assumed that
there is no error and if the result is non zero it is believed that the communication channel
consists of error during the transmission of data (Prévost et al., 2013).

8WIRELESS NETWORK AND COMMUNICATION
6. Compute the frame check sequence for the following information:
Message = 10111100, Pattern = 11011
7. Compute the transmitted signal using Direct Sequence Spread Spectrum for the
following information:
Input: 1011, Locally Generated PN bit stream: 101011011010, T = 3Tc
6. Compute the frame check sequence for the following information:
Message = 10111100, Pattern = 11011
7. Compute the transmitted signal using Direct Sequence Spread Spectrum for the
following information:
Input: 1011, Locally Generated PN bit stream: 101011011010, T = 3Tc

9WIRELESS NETWORK AND COMMUNICATION
8. What is the difference between Infrastructure and ad hoc modes in WLAN? Draw
their relative diagrams as well.
WLAN infrastructure mode
WLAN ad-hoc mode
It can be stated that all the networks, which are constructed, are different. There are
two different modes the ad-hoc and the infrastructure mood. The Wi-Fi linked device can
only be connected with the infrastructure mode. The Wi-Fi device cannot be connected with
the infrastructure mode. All the devices, which are available in the infrastructure mode, is
communicated with the help of a single access point. In case of the ad-hoc network all the
device, communicate directly with each other. The ad-hoc is also a type of local area
network. The data can be send directly with the help of the ad-hoc network. The network
does not require any centralized point of access. Each of the node which is wireless can
communicate between themselves directly with the ad-hoc mode. The ad-hoc mode offers
peer-to-peer communication. The topology is mesh network topology in the ad-hoc mode. In
the ad-hoc mode group of nodes communicating are independent (Sarkar, Basavaraju and
Puttamadappa 2016). In the infrastructure mode, the topology is the star network topology.
All the nodes communicate via a wireless access point. In the infrastructure, the group of
nodes communicating comprises of a wireless access point (Liang and Yu 2014).
8. What is the difference between Infrastructure and ad hoc modes in WLAN? Draw
their relative diagrams as well.
WLAN infrastructure mode
WLAN ad-hoc mode
It can be stated that all the networks, which are constructed, are different. There are
two different modes the ad-hoc and the infrastructure mood. The Wi-Fi linked device can
only be connected with the infrastructure mode. The Wi-Fi device cannot be connected with
the infrastructure mode. All the devices, which are available in the infrastructure mode, is
communicated with the help of a single access point. In case of the ad-hoc network all the
device, communicate directly with each other. The ad-hoc is also a type of local area
network. The data can be send directly with the help of the ad-hoc network. The network
does not require any centralized point of access. Each of the node which is wireless can
communicate between themselves directly with the ad-hoc mode. The ad-hoc mode offers
peer-to-peer communication. The topology is mesh network topology in the ad-hoc mode. In
the ad-hoc mode group of nodes communicating are independent (Sarkar, Basavaraju and
Puttamadappa 2016). In the infrastructure mode, the topology is the star network topology.
All the nodes communicate via a wireless access point. In the infrastructure, the group of
nodes communicating comprises of a wireless access point (Liang and Yu 2014).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10WIRELESS NETWORK AND COMMUNICATION
9. Compare the differences of TCP and OSI protocols for wired and wireless LANs
using diagrams.
The TCP protocols are the standard one, which helps in the development of the
internet. The TCP model is much simple has it contains few level. The OSI model is referred
to as the reference tool and comparatively the TCP is more reliable (Ravali 2013). One of the
model is protocol independent which is the OSI model. On the other hand, the TCP model is
the protocol dependent model. The TCP protocol is much easy. It is based on the internet
model. The OSI model contains seven layers. The model helps in understanding the ways in
which the application can communicate in the network. However, the TCP protocol is used to
study the interconnected network and the function of the networking system. The OSI model
ensures that the packets are delivered properly. The model contains separate session layer.
The service provided by the OSI protocol is both connection less and connection related.
However, the TCP protocol offers only connection less service. The model helps in creating
clear distinction between the different layers. The support provided by the TCP is
connectionless and the support provided by the OSI model is based on the connection. The
two model have complete different approach. The model having horizontal approach is TCP.
The model having the vertical approach is OSI (Nath and Uddin 2015).
9. Compare the differences of TCP and OSI protocols for wired and wireless LANs
using diagrams.
The TCP protocols are the standard one, which helps in the development of the
internet. The TCP model is much simple has it contains few level. The OSI model is referred
to as the reference tool and comparatively the TCP is more reliable (Ravali 2013). One of the
model is protocol independent which is the OSI model. On the other hand, the TCP model is
the protocol dependent model. The TCP protocol is much easy. It is based on the internet
model. The OSI model contains seven layers. The model helps in understanding the ways in
which the application can communicate in the network. However, the TCP protocol is used to
study the interconnected network and the function of the networking system. The OSI model
ensures that the packets are delivered properly. The model contains separate session layer.
The service provided by the OSI protocol is both connection less and connection related.
However, the TCP protocol offers only connection less service. The model helps in creating
clear distinction between the different layers. The support provided by the TCP is
connectionless and the support provided by the OSI model is based on the connection. The
two model have complete different approach. The model having horizontal approach is TCP.
The model having the vertical approach is OSI (Nath and Uddin 2015).

11WIRELESS NETWORK AND COMMUNICATION
10. Explain why the square and circle shapes cells for cellular communications are not
appropriate as compared to hexagonal shape cells.
Blackspots are the region which receive no signal inside the cell. It is one of the
drawbacks related to the cellular communication. All the cells and the regions must have
equal distribution of the signals. When the cell shape is square the drawback faced is related
to the even distribution of the signal (Ahmadi et al., 2015). The reason is that the distance of
the side from the centre is greater. This is the disadvantage that is faced when the cell shape
is square. When the cell shape of the cell is circle all the point in the circle receive equal
signal but when number of cells are join together, the blackspot region is created. The
hexagon shape for the cellular communication is one of the most efficient shape. With the
help of the wireless communication network, the problem related to the spectral congestion is
overcome. The entire cellular network is divided into different parts and all the cells contain
its own antenna that is used for the transmission of the signals. The antennas and the signal
provided must be equally distributed. The concept of frequency reuse is also in the cellular
communication process. The antenna and the propagation of wave plays an important role in
10. Explain why the square and circle shapes cells for cellular communications are not
appropriate as compared to hexagonal shape cells.
Blackspots are the region which receive no signal inside the cell. It is one of the
drawbacks related to the cellular communication. All the cells and the regions must have
equal distribution of the signals. When the cell shape is square the drawback faced is related
to the even distribution of the signal (Ahmadi et al., 2015). The reason is that the distance of
the side from the centre is greater. This is the disadvantage that is faced when the cell shape
is square. When the cell shape of the cell is circle all the point in the circle receive equal
signal but when number of cells are join together, the blackspot region is created. The
hexagon shape for the cellular communication is one of the most efficient shape. With the
help of the wireless communication network, the problem related to the spectral congestion is
overcome. The entire cellular network is divided into different parts and all the cells contain
its own antenna that is used for the transmission of the signals. The antennas and the signal
provided must be equally distributed. The concept of frequency reuse is also in the cellular
communication process. The antenna and the propagation of wave plays an important role in
12WIRELESS NETWORK AND COMMUNICATION
the process of wireless communication. The cell need to be designed in a way that all the
problems related to noise, fading, propagation could be easily solved. Both the disadvantages
are prevented when the shape of the cell is hexagon because of its structure that helps in the
even distribution of the signal and prevent the creation of the blackspots (Guo et al., 2013).
the process of wireless communication. The cell need to be designed in a way that all the
problems related to noise, fading, propagation could be easily solved. Both the disadvantages
are prevented when the shape of the cell is hexagon because of its structure that helps in the
even distribution of the signal and prevent the creation of the blackspots (Guo et al., 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13WIRELESS NETWORK AND COMMUNICATION
References
Guo, F., French, J.B., Li, P., Zhao, H., Chan, C.Y., Fick, J.R., Benkovic, S.J. and Huang, T.J.,
2013. Probing cell–cell communication with microfluidic devices. Lab on a Chip, 13(16),
pp.3152-3162.
Ravali, P., 2013. A comparative evaluation of OSI and TCP/IP models. International Journal
of Science and Research, 4(7), pp.514-521.
Nath, P.B. and Uddin, M.M., 2015. TCP-IP Model in Data Communication and
Networking. American Journal of Engineering Research, 4(10), pp.102-107.
Pi, Z., Samsung Electronics Co Ltd, 2014. Techniques for cyclic redundancy check encoding
in communication system. U.S. Patent 8,627,171.
Prévost, R., Coulon, M., Bonacci, D., LeMaitre, J., Millerioux, J.P. and Tourneret, J.Y., 2013.
Cyclic redundancy check‐based detection algorithms for automatic identification system
signals received by satellite. International Journal of Satellite Communications and
Networking, 31(4), pp.157-176.
Sarkar, S.K., Basavaraju, T.G. and Puttamadappa, C., 2016. Ad hoc mobile wireless
networks: principles, protocols, and applications. CRC Press.
Liang, C. and Yu, F.R., 2014. Wireless network virtualization: A survey, some research
issues and challenges. IEEE Communications Surveys & Tutorials, 17(1), pp.358-380.
Ahmadi, M., Tong, F., Zheng, L. and Pan, J., 2015, April. Performance analysis for two-tier
cellular systems based on probabilistic distance models. In 2015 IEEE Conference on
Computer Communications (INFOCOM) (pp. 352-360). IEEE.
References
Guo, F., French, J.B., Li, P., Zhao, H., Chan, C.Y., Fick, J.R., Benkovic, S.J. and Huang, T.J.,
2013. Probing cell–cell communication with microfluidic devices. Lab on a Chip, 13(16),
pp.3152-3162.
Ravali, P., 2013. A comparative evaluation of OSI and TCP/IP models. International Journal
of Science and Research, 4(7), pp.514-521.
Nath, P.B. and Uddin, M.M., 2015. TCP-IP Model in Data Communication and
Networking. American Journal of Engineering Research, 4(10), pp.102-107.
Pi, Z., Samsung Electronics Co Ltd, 2014. Techniques for cyclic redundancy check encoding
in communication system. U.S. Patent 8,627,171.
Prévost, R., Coulon, M., Bonacci, D., LeMaitre, J., Millerioux, J.P. and Tourneret, J.Y., 2013.
Cyclic redundancy check‐based detection algorithms for automatic identification system
signals received by satellite. International Journal of Satellite Communications and
Networking, 31(4), pp.157-176.
Sarkar, S.K., Basavaraju, T.G. and Puttamadappa, C., 2016. Ad hoc mobile wireless
networks: principles, protocols, and applications. CRC Press.
Liang, C. and Yu, F.R., 2014. Wireless network virtualization: A survey, some research
issues and challenges. IEEE Communications Surveys & Tutorials, 17(1), pp.358-380.
Ahmadi, M., Tong, F., Zheng, L. and Pan, J., 2015, April. Performance analysis for two-tier
cellular systems based on probabilistic distance models. In 2015 IEEE Conference on
Computer Communications (INFOCOM) (pp. 352-360). IEEE.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





