University Wireless Network Assignment: Security and Network Analysis
VerifiedAdded on 2023/06/04
|6
|1010
|240
Report
AI Summary
This report provides an analysis of wireless networks, focusing on Near Field Communication (NFC) and Radio-Frequency Identification (RFID) technologies. It explains the operational mechanisms of NFC, its advantages, such as peer-to-peer mode, and its applications, including its use as a smart card. The report also addresses security considerations and challenges associated with NFC, such as snooping and intervention attacks, and emphasizes the need for secure communication channels. Furthermore, the report includes a practical component involving the simulation of a wireless network using Packet Tracer. The simulation covers network configuration, ping tests, and the implementation of WPA2-PSK security with AES encryption. The report details the connection process and the impact of security settings on network communication, as well as the effects of channel changes and passphrase mismatches. The report concludes with a bibliography of relevant sources.

Running head: WIRELESS NETWORK
Wireless Network
Name of the Student:
Name of the University:
Author Note
Wireless Network
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORK
Part A
Answer to question number 1
For any kind of short distanced between two different devices the “Near Field
communication” or NFC is entrenched along with the NFC sensors. In order to transfer data
from any device regardless of power sources a tag is used. At the same time the information
transmission will not be completed successfully without the application of the small
transmitter. The mechanism of NFC works in a similar pattern for all other wireless signals,
Bluetooth and Wi Fi connections. For the transition of any information between the devices
radio wave is used as an intermediary. Though in order to successfully communicate with the
rest of the devices some additional requirements are to be incorporated to the system. In order
to transfer information from one device to another with the NFC operation the RFID
technology is utilized because it uses electromagnetic induction for data communication. The
most significant advantage associated to this technology is that it does not require external
power sources rather the in order to turn on the operation the electromagnetic field is helpful.
In order to transmit data the radio frequency required by the NFC is 1356 MHz and a speed
of 424 Kb/second (or 106212). This speed is enough for successful transmission of pictures,
music and other details of contracts. Three different operational approaches are available for
the Near Field Communication (NFC) technology and among three of these the most
appropriate and suitable one is peer to peer mode. For successful exchange of confidential
information this specific peer to peer mode is used. Whenever the device receives data from
the sender side is referred to as the passive data and vise versa. Apart from this it is also
determined that, in case of car emulation mode the NFC device can also be utilized as a smart
card. These kinds of smart cards are also used to tap into various systems and to make
payments also thus it can be also defined as a contactless credit card. While tags on the
WIRELESS NETWORK
Part A
Answer to question number 1
For any kind of short distanced between two different devices the “Near Field
communication” or NFC is entrenched along with the NFC sensors. In order to transfer data
from any device regardless of power sources a tag is used. At the same time the information
transmission will not be completed successfully without the application of the small
transmitter. The mechanism of NFC works in a similar pattern for all other wireless signals,
Bluetooth and Wi Fi connections. For the transition of any information between the devices
radio wave is used as an intermediary. Though in order to successfully communicate with the
rest of the devices some additional requirements are to be incorporated to the system. In order
to transfer information from one device to another with the NFC operation the RFID
technology is utilized because it uses electromagnetic induction for data communication. The
most significant advantage associated to this technology is that it does not require external
power sources rather the in order to turn on the operation the electromagnetic field is helpful.
In order to transmit data the radio frequency required by the NFC is 1356 MHz and a speed
of 424 Kb/second (or 106212). This speed is enough for successful transmission of pictures,
music and other details of contracts. Three different operational approaches are available for
the Near Field Communication (NFC) technology and among three of these the most
appropriate and suitable one is peer to peer mode. For successful exchange of confidential
information this specific peer to peer mode is used. Whenever the device receives data from
the sender side is referred to as the passive data and vise versa. Apart from this it is also
determined that, in case of car emulation mode the NFC device can also be utilized as a smart
card. These kinds of smart cards are also used to tap into various systems and to make
payments also thus it can be also defined as a contactless credit card. While tags on the
2
WIRELESS NETWORK
receiver devices are utilized to link up with the receiver devices for the successful
transmission of information the NFC devices are used. This is implies as another major
application of the NFC devices. Whenever this specific technology and application is utilized
in this specific mode that time it is referred to as a read write mode. However, various
security level challenges are also associated to this technology among them snooping is the
most affecting risks. The third party needs not to access any information for collecting
information. Though, in order to accomplish a secured communication the transmission
channel is required to be well encrypted. While transmitting information from the sender side
to the receiver side security challenges may occur. The confidentiality of data can be
compromised due to unethical activities and third party interference. The NFC technology
will be referred to as a vulnerable one if any intermediary gets opportunities to access the
information without authentication. Only secured link of communication and active
communication can reduce the security challenges while transmitting datagram or
information packets. The other risks those have been identified for this technology are
intervention attack and this is required to be mitigated for establishing a secured
communication among the sender and the receiver.
Answer to question number 2
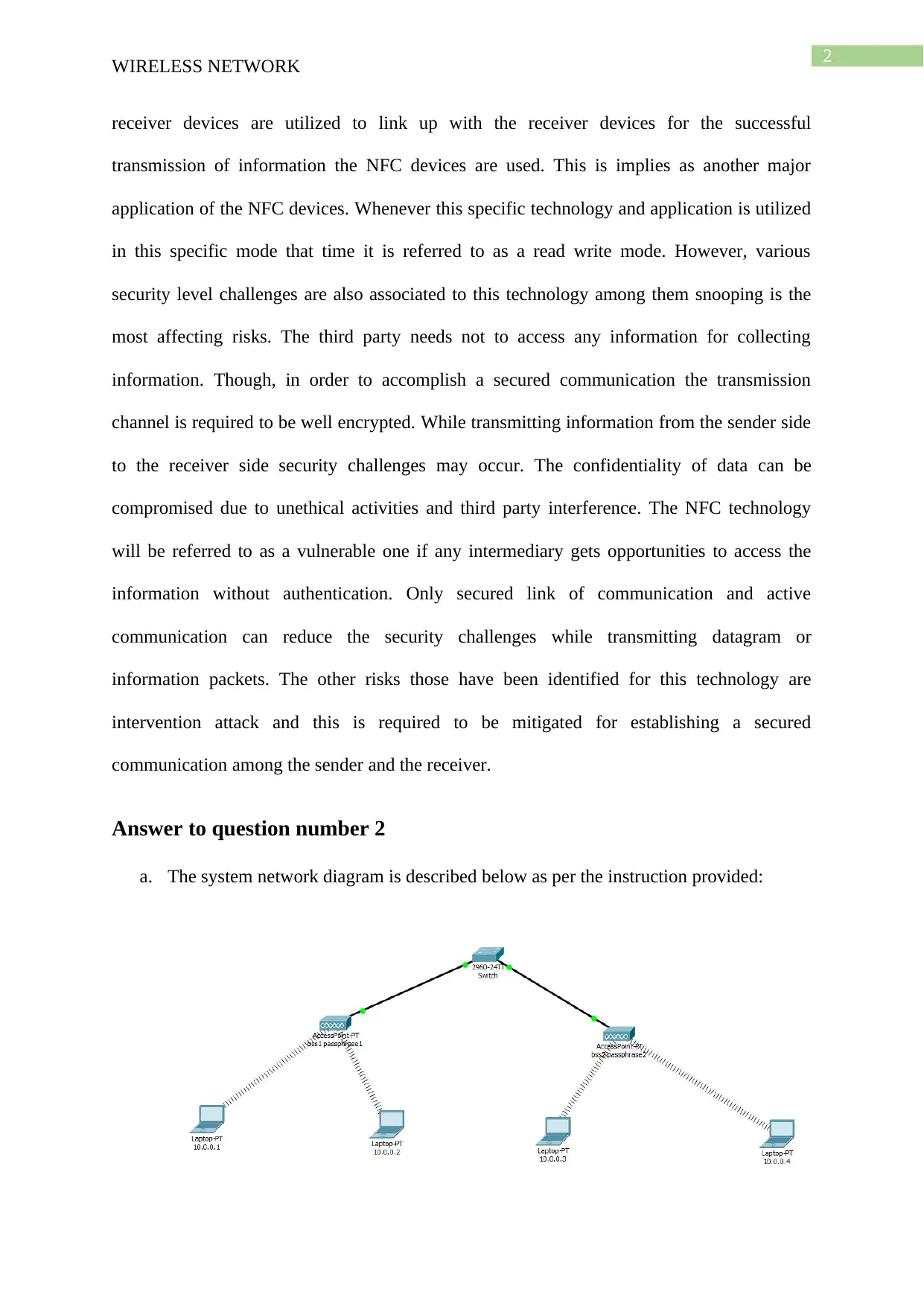
a. The system network diagram is described below as per the instruction provided:
WIRELESS NETWORK
receiver devices are utilized to link up with the receiver devices for the successful
transmission of information the NFC devices are used. This is implies as another major
application of the NFC devices. Whenever this specific technology and application is utilized
in this specific mode that time it is referred to as a read write mode. However, various
security level challenges are also associated to this technology among them snooping is the
most affecting risks. The third party needs not to access any information for collecting
information. Though, in order to accomplish a secured communication the transmission
channel is required to be well encrypted. While transmitting information from the sender side
to the receiver side security challenges may occur. The confidentiality of data can be
compromised due to unethical activities and third party interference. The NFC technology
will be referred to as a vulnerable one if any intermediary gets opportunities to access the
information without authentication. Only secured link of communication and active
communication can reduce the security challenges while transmitting datagram or
information packets. The other risks those have been identified for this technology are
intervention attack and this is required to be mitigated for establishing a secured
communication among the sender and the receiver.
Answer to question number 2
a. The system network diagram is described below as per the instruction provided:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
WIRELESS NETWORK
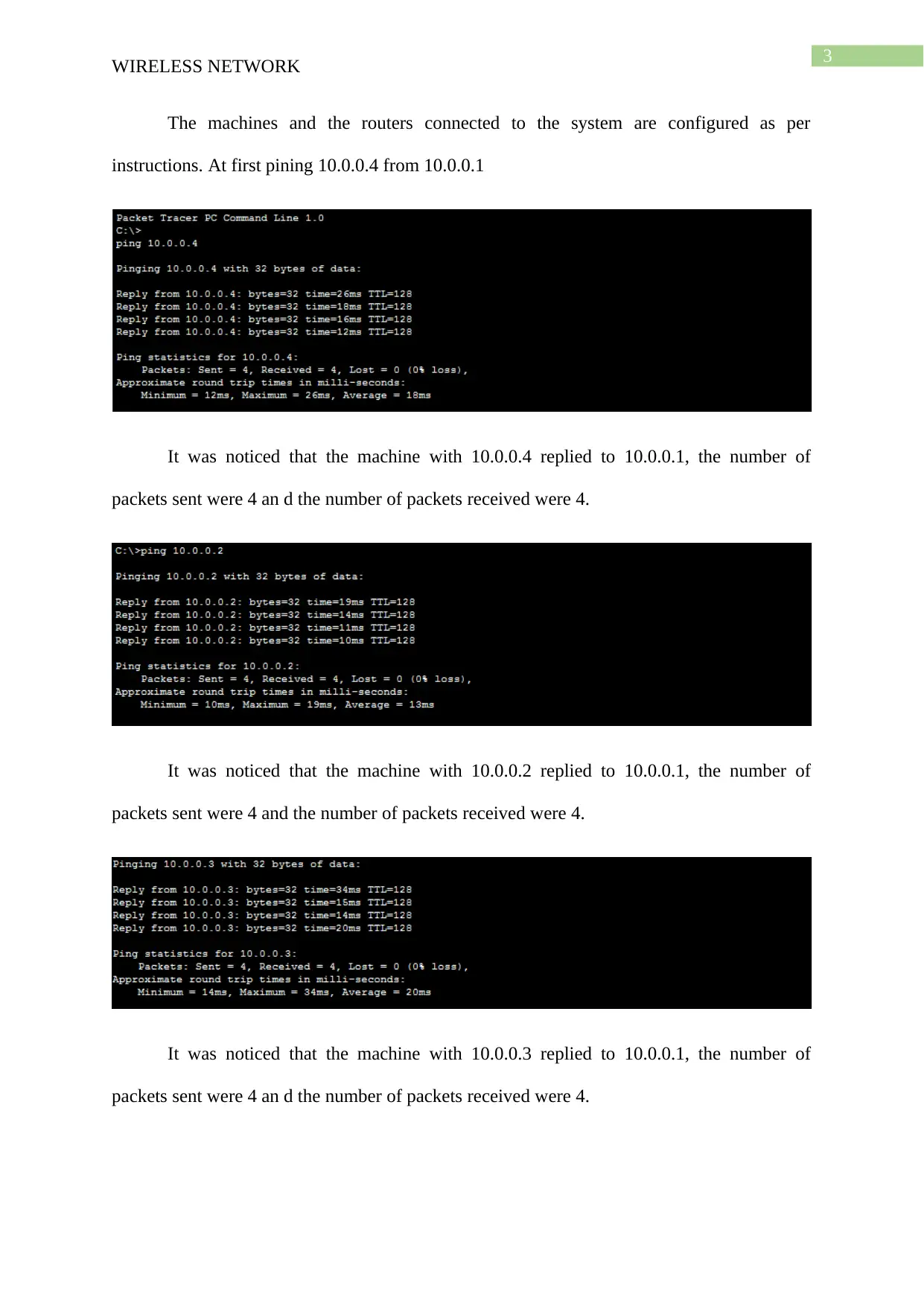
The machines and the routers connected to the system are configured as per
instructions. At first pining 10.0.0.4 from 10.0.0.1
It was noticed that the machine with 10.0.0.4 replied to 10.0.0.1, the number of
packets sent were 4 an d the number of packets received were 4.
It was noticed that the machine with 10.0.0.2 replied to 10.0.0.1, the number of
packets sent were 4 and the number of packets received were 4.
It was noticed that the machine with 10.0.0.3 replied to 10.0.0.1, the number of
packets sent were 4 an d the number of packets received were 4.
WIRELESS NETWORK
The machines and the routers connected to the system are configured as per
instructions. At first pining 10.0.0.4 from 10.0.0.1
It was noticed that the machine with 10.0.0.4 replied to 10.0.0.1, the number of
packets sent were 4 an d the number of packets received were 4.
It was noticed that the machine with 10.0.0.2 replied to 10.0.0.1, the number of
packets sent were 4 and the number of packets received were 4.
It was noticed that the machine with 10.0.0.3 replied to 10.0.0.1, the number of
packets sent were 4 an d the number of packets received were 4.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
WIRELESS NETWORK
The discussion is evident enough for anyone to conclude that there is a steady
connection in between the machines which has been installed in the system.
b. The network never gets affected if any of the access point of the channel is changed.
However, if the nearby routers utilize similar channels then only interference may occur and
it also makes the neighbour router weak in nature.
c. If in between the access points any mismatch of passphrase occurs then the access point
will not allow the devices to keep connected along with the access points while sending and
receiving information packets.
WIRELESS NETWORK
The discussion is evident enough for anyone to conclude that there is a steady
connection in between the machines which has been installed in the system.
b. The network never gets affected if any of the access point of the channel is changed.
However, if the nearby routers utilize similar channels then only interference may occur and
it also makes the neighbour router weak in nature.
c. If in between the access points any mismatch of passphrase occurs then the access point
will not allow the devices to keep connected along with the access points while sending and
receiving information packets.

5
WIRELESS NETWORK
Bibliography
Bernardos, C. J., De La Oliva, A., Serrano, P., Banchs, A., Contreras, L. M., Jin, H., &
Zúñiga, J. C. (2014). An architecture for software defined wireless networking. IEEE
wireless communications, 21(3), 52-61.
Ransing, R. S., & Rajput, M. (2015, January). Smart home for elderly care, based on wireless
sensor network. In Nascent Technologies in the Engineering Field (ICNTE), 2015
International Conference on (pp. 1-5). IEEE.
Torfs, G., Li, H., Agneessens, S., Bauwelinck, J., Breyne, L., Caytan, O., ... & Ginste, D. V.
(2018). ATTO: Wireless networking at fiber speed. Journal of Lightwave Technology,
36(8), 1468-1477.
WIRELESS NETWORK
Bibliography
Bernardos, C. J., De La Oliva, A., Serrano, P., Banchs, A., Contreras, L. M., Jin, H., &
Zúñiga, J. C. (2014). An architecture for software defined wireless networking. IEEE
wireless communications, 21(3), 52-61.
Ransing, R. S., & Rajput, M. (2015, January). Smart home for elderly care, based on wireless
sensor network. In Nascent Technologies in the Engineering Field (ICNTE), 2015
International Conference on (pp. 1-5). IEEE.
Torfs, G., Li, H., Agneessens, S., Bauwelinck, J., Breyne, L., Caytan, O., ... & Ginste, D. V.
(2018). ATTO: Wireless networking at fiber speed. Journal of Lightwave Technology,
36(8), 1468-1477.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




