A Comprehensive Review of Wireless Network Security Protocols
VerifiedAdded on 2023/06/13
|19
|4360
|328
Report
AI Summary
This report provides a comprehensive review of wireless network security, focusing on current security protocols, potential threats, and future security measures. It begins with a literature search, refining search queries to identify relevant research papers. The project proposal outlines the research purpose, background context, and methodology, including primary and secondary data collection methods. The literature review covers security in WMAN (802.16) and WLAN (802.11), including protocols like WEP and EAPOL. The report also addresses professional and ethical issues, concluding with findings on aspects of wireless security and a discussion of future directions. Desklib offers this assignment and many other resources to aid students in their studies.

Running head: WIRELESS NETWORK SECURITY
Wireless Network Security
Name of Student
Name of the University
Author Note
Wireless Network Security
Name of Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
WIRELESS NETWORK SECURITY
Table of Contents
Part1: Literature Search / Review....................................................................................................5
Introduction..................................................................................................................................5
Search Question...........................................................................................................................5
Search..........................................................................................................................................5
Assess results...............................................................................................................................6
Refine question............................................................................................................................6
Refine search...............................................................................................................................6
Assess Results..............................................................................................................................6
Refine Question...........................................................................................................................6
Refine search...............................................................................................................................6
Assess results...............................................................................................................................6
Criteria for Deciding the Relevance............................................................................................6
Conclusion...................................................................................................................................7
Part 2: Project Proposal...................................................................................................................7
Research Purpose.........................................................................................................................7
Background Context....................................................................................................................8
Security and Wireless Overview.............................................................................................8
Research Methodology................................................................................................................8
Evaluation Methodology.............................................................................................................8
Literature Review........................................................................................................................8
Introduction to Security...........................................................................................................8
Introduction to the Wireless World.......................................................................................13
WMAN (Wireless MAN)......................................................................................................13
WLAN (Wireless LAN)........................................................................................................14
Security Breaches..................................................................................................................14
Security in WMAN (802.16).....................................................................................................15
Protocol Layers......................................................................................................................15
Security Concerns..................................................................................................................16
Security in WLAN (802.11)......................................................................................................17
802.11 standard......................................................................................................................17
(Wired Equivalent Privacy) WEP..........................................................................................18
WEP Weaknesses..................................................................................................................18
802.1x: EAP Over LAN (EAPOL)........................................................................................18
WIRELESS NETWORK SECURITY
Table of Contents
Part1: Literature Search / Review....................................................................................................5
Introduction..................................................................................................................................5
Search Question...........................................................................................................................5
Search..........................................................................................................................................5
Assess results...............................................................................................................................6
Refine question............................................................................................................................6
Refine search...............................................................................................................................6
Assess Results..............................................................................................................................6
Refine Question...........................................................................................................................6
Refine search...............................................................................................................................6
Assess results...............................................................................................................................6
Criteria for Deciding the Relevance............................................................................................6
Conclusion...................................................................................................................................7
Part 2: Project Proposal...................................................................................................................7
Research Purpose.........................................................................................................................7
Background Context....................................................................................................................8
Security and Wireless Overview.............................................................................................8
Research Methodology................................................................................................................8
Evaluation Methodology.............................................................................................................8
Literature Review........................................................................................................................8
Introduction to Security...........................................................................................................8
Introduction to the Wireless World.......................................................................................13
WMAN (Wireless MAN)......................................................................................................13
WLAN (Wireless LAN)........................................................................................................14
Security Breaches..................................................................................................................14
Security in WMAN (802.16).....................................................................................................15
Protocol Layers......................................................................................................................15
Security Concerns..................................................................................................................16
Security in WLAN (802.11)......................................................................................................17
802.11 standard......................................................................................................................17
(Wired Equivalent Privacy) WEP..........................................................................................18
WEP Weaknesses..................................................................................................................18
802.1x: EAP Over LAN (EAPOL)........................................................................................18

3
WIRELESS NETWORK SECURITY
Schedule and Publishing............................................................................................................19
Gantt chart.............................................................................................................................20
Professional and Ethical Issues..................................................................................................20
Findings.....................................................................................................................................21
Aspects of Wireless Security.................................................................................................21
Conclusion.................................................................................................................................22
References......................................................................................................................................23
WIRELESS NETWORK SECURITY
Schedule and Publishing............................................................................................................19
Gantt chart.............................................................................................................................20
Professional and Ethical Issues..................................................................................................20
Findings.....................................................................................................................................21
Aspects of Wireless Security.................................................................................................21
Conclusion.................................................................................................................................22
References......................................................................................................................................23
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
WIRELESS NETWORK SECURITY
Part1: Literature Search / Review
Introduction
Wireless network has become the integral part of the life as; technology advancement has
been changing the face of the world continuously. Technologies such as Internet of Things, WI -
FI, Bluetooth, Internet, WLAN, WMAN, and many more have become very popular and are
being applicable in every sector of the world in the present time. The wireless network came in
practice after 2000 when the prices for the wireless network went down, as previously, the
military were the biggest client of the networks. Wireless security can be defined as the
capability of the system to maintain and manage the protection for the network and allow safer
exchange of data and information.
Search Question
The research question emphasizes on the identification of the security standards available
in the present world and analyzes their effectiveness within the existing network. Following are
the questions for which, the literature review will be made:
What are the standard security protocols of wireless technology?
Available security protocols are capable of eliminating all the possible threats or not?
What are the aspects for the security of the wireless technology in future?
Search
First attempt was driven through searching the Teesside University library’s online
databases with the search code “Wireless Network.”
WIRELESS NETWORK SECURITY
Part1: Literature Search / Review
Introduction
Wireless network has become the integral part of the life as; technology advancement has
been changing the face of the world continuously. Technologies such as Internet of Things, WI -
FI, Bluetooth, Internet, WLAN, WMAN, and many more have become very popular and are
being applicable in every sector of the world in the present time. The wireless network came in
practice after 2000 when the prices for the wireless network went down, as previously, the
military were the biggest client of the networks. Wireless security can be defined as the
capability of the system to maintain and manage the protection for the network and allow safer
exchange of data and information.
Search Question
The research question emphasizes on the identification of the security standards available
in the present world and analyzes their effectiveness within the existing network. Following are
the questions for which, the literature review will be made:
What are the standard security protocols of wireless technology?
Available security protocols are capable of eliminating all the possible threats or not?
What are the aspects for the security of the wireless technology in future?
Search
First attempt was driven through searching the Teesside University library’s online
databases with the search code “Wireless Network.”
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
WIRELESS NETWORK SECURITY
Assess results
Many articles link appeared and they had many information related to the wireless
network however, security was missing in most of the papers.
Refine question
Thereafter, search attempts were made for the wireless network and security
Refine search
Search was modified from wireless network to wireless network and security
Assess Results
Most of the articles were relevant to the topic and they had many information related to
the wireless network and security including old and new ones
Refine Question
Present wireless network security protocols needed to be identified
Refine search
Wireless and network security protocols was searched in the database
Assess results
Identified many papers relevant to the topic
Criteria for Deciding the Relevance
A primary criterion was the date of the paper uploaded in the database that was filtered
from 2014 to 2017 to identify the articles with latest information on the topics. Thereafter,
articles chosen from the first search assesses were sorted out as per the information and primary
researches made on the same topic. The articles were sorted out considering the type of research
WIRELESS NETWORK SECURITY
Assess results
Many articles link appeared and they had many information related to the wireless
network however, security was missing in most of the papers.
Refine question
Thereafter, search attempts were made for the wireless network and security
Refine search
Search was modified from wireless network to wireless network and security
Assess Results
Most of the articles were relevant to the topic and they had many information related to
the wireless network and security including old and new ones
Refine Question
Present wireless network security protocols needed to be identified
Refine search
Wireless and network security protocols was searched in the database
Assess results
Identified many papers relevant to the topic
Criteria for Deciding the Relevance
A primary criterion was the date of the paper uploaded in the database that was filtered
from 2014 to 2017 to identify the articles with latest information on the topics. Thereafter,
articles chosen from the first search assesses were sorted out as per the information and primary
researches made on the same topic. The articles were sorted out considering the type of research

6
WIRELESS NETWORK SECURITY
methodology used for the findings and results in the research paper. The articles those have the
primary research analysis driven were selected for the review. Some of the articles were out of
the box because of the old data availability and not introducing the new protocols and
approaches driven for the project. Finally, the articles and research papers following these
criteria are selected as the chosen papers for the literature review.
Conclusion
The above criteria helped in identifying the relevant papers on the related topics. Total
nineteen research papers were selected for the literature review as mentioned in the reference
section of this paper. These papers had all the relevant data and information those needed to be
evaluated for identifying the answers of the research questions and assuring the efficiency of the
findings and results for this paper.
Part 2: Project Proposal
1. Research purpose
Wireless networks are a revolutionary progression in the world of technology that would
be under constant upgrading. This latest implementation in the networking era would be able to
reduce costs at a huge level since the technology has eradicated the use of cables, enabling
mobility and agility in networking. However, since the inception of this revolution in the world
of wireless networking, there would be immense usability of the services offered.
The most common and popular is the mobility factor that wireless networking offers.
Since, this network also enables the virtualization of networks and the sharing of infrastructure,
there might be a possibility about the security feature that the technology has to offer. There can
be a possibility that due to a shared facility available in the networking system, security takes a
WIRELESS NETWORK SECURITY
methodology used for the findings and results in the research paper. The articles those have the
primary research analysis driven were selected for the review. Some of the articles were out of
the box because of the old data availability and not introducing the new protocols and
approaches driven for the project. Finally, the articles and research papers following these
criteria are selected as the chosen papers for the literature review.
Conclusion
The above criteria helped in identifying the relevant papers on the related topics. Total
nineteen research papers were selected for the literature review as mentioned in the reference
section of this paper. These papers had all the relevant data and information those needed to be
evaluated for identifying the answers of the research questions and assuring the efficiency of the
findings and results for this paper.
Part 2: Project Proposal
1. Research purpose
Wireless networks are a revolutionary progression in the world of technology that would
be under constant upgrading. This latest implementation in the networking era would be able to
reduce costs at a huge level since the technology has eradicated the use of cables, enabling
mobility and agility in networking. However, since the inception of this revolution in the world
of wireless networking, there would be immense usability of the services offered.
The most common and popular is the mobility factor that wireless networking offers.
Since, this network also enables the virtualization of networks and the sharing of infrastructure,
there might be a possibility about the security feature that the technology has to offer. There can
be a possibility that due to a shared facility available in the networking system, security takes a
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
WIRELESS NETWORK SECURITY
backseat in the structure. Wireless features are not found to be inherently secured. The nodes that
are deployed near the communication channels in the wireless networks can possess malicious
adversaries. Besides this, if any malicious attacker gets the access to one of the nodes that induce
the interconnection; it can bring about hacking possibilities as well.
The wireless network also expands the technology to the advanced usage of sensory
networks and the sharing of infrastructures over radio spectrum resources. Although it reduces
the expenses of network deploying, the network system does not possess complete permeability
to the malicious hackers and even the malware attacks.
Therefore, it needs to be researched upon about the malevolent security issues that the
wireless network possesses despite having the potential vision about the virtualization of
network. The security challenges that wireless network has can be addressed over the widespread
deployment of the technology that happens to include the likes of isolation, allocation, resource
discovery, control signaling, mobility management, and operation security of the network
management. The research purpose analyzes the situation over these factors to identify the
several important issues in these networking structures with the help of primary and secondary
data collection method about the security issues.
2. Background context
During the times where networking could not introduce the factor of using wireless
technology, the cost for implementing the networking technology was high. The further
technological advancements also introduced costly frameworks till wireless services were
introduced. The introduction of the wireless networking structure had reduced the cost of
implementation of the networking even over a huge selection of area. The virtualization into
WIRELESS NETWORK SECURITY
backseat in the structure. Wireless features are not found to be inherently secured. The nodes that
are deployed near the communication channels in the wireless networks can possess malicious
adversaries. Besides this, if any malicious attacker gets the access to one of the nodes that induce
the interconnection; it can bring about hacking possibilities as well.
The wireless network also expands the technology to the advanced usage of sensory
networks and the sharing of infrastructures over radio spectrum resources. Although it reduces
the expenses of network deploying, the network system does not possess complete permeability
to the malicious hackers and even the malware attacks.
Therefore, it needs to be researched upon about the malevolent security issues that the
wireless network possesses despite having the potential vision about the virtualization of
network. The security challenges that wireless network has can be addressed over the widespread
deployment of the technology that happens to include the likes of isolation, allocation, resource
discovery, control signaling, mobility management, and operation security of the network
management. The research purpose analyzes the situation over these factors to identify the
several important issues in these networking structures with the help of primary and secondary
data collection method about the security issues.
2. Background context
During the times where networking could not introduce the factor of using wireless
technology, the cost for implementing the networking technology was high. The further
technological advancements also introduced costly frameworks till wireless services were
introduced. The introduction of the wireless networking structure had reduced the cost of
implementation of the networking even over a huge selection of area. The virtualization into
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
WIRELESS NETWORK SECURITY
cloud environment had even been implemented into the wired technology, but the wireless
structure had been detected to be attracting more network attacks than before.
Wireless networks are a revolutionary progression in the world of technology that would
be under constant upgrading. This latest implementation in the networking era would be able to
reduce costs at a huge level since the technology has eradicated the use of cables, enabling
mobility and agility in networking. However, since the inception of this revolution in the world
of wireless networking, there would be immense usability of the services offered. Particularly,
unlike wired networks, where bandwidth resource abstraction and isolation can be done on
hardware, the wireless networks do not have a straightforward isolation structure. Instead, due to
its inherent broadcasting nature, stochastic virtualization problems happen over the networking.
The most popular is the mobility factor that the wireless networking offers. Since, this
network also enables the virtualization of networks and the sharing of infrastructure, there might
be a possibility about the security feature that the technology has to offer. There can be a
possibility that due to a shared facility available in the networking system, security takes a
backseat in the structure. Wireless features are not found to be inherently secured. Despite the
potential vision that wireless structure has, the research needs to address the challenges that
remains regarding the widespread deployment of wireless services. The research thus is
conducted over a series of primary as well as secondary data that would be collected over a
dedicated time span, that decides how secure the wireless network services are. Since there have
been incidences that the wireless network structure would be breached upon by malicious users,
it needs to be identified whether the latest implementation in the technological world has any
added credibility over the security issues that the wired services have or the situation about
security is further worse.
WIRELESS NETWORK SECURITY
cloud environment had even been implemented into the wired technology, but the wireless
structure had been detected to be attracting more network attacks than before.
Wireless networks are a revolutionary progression in the world of technology that would
be under constant upgrading. This latest implementation in the networking era would be able to
reduce costs at a huge level since the technology has eradicated the use of cables, enabling
mobility and agility in networking. However, since the inception of this revolution in the world
of wireless networking, there would be immense usability of the services offered. Particularly,
unlike wired networks, where bandwidth resource abstraction and isolation can be done on
hardware, the wireless networks do not have a straightforward isolation structure. Instead, due to
its inherent broadcasting nature, stochastic virtualization problems happen over the networking.
The most popular is the mobility factor that the wireless networking offers. Since, this
network also enables the virtualization of networks and the sharing of infrastructure, there might
be a possibility about the security feature that the technology has to offer. There can be a
possibility that due to a shared facility available in the networking system, security takes a
backseat in the structure. Wireless features are not found to be inherently secured. Despite the
potential vision that wireless structure has, the research needs to address the challenges that
remains regarding the widespread deployment of wireless services. The research thus is
conducted over a series of primary as well as secondary data that would be collected over a
dedicated time span, that decides how secure the wireless network services are. Since there have
been incidences that the wireless network structure would be breached upon by malicious users,
it needs to be identified whether the latest implementation in the technological world has any
added credibility over the security issues that the wired services have or the situation about
security is further worse.

9
WIRELESS NETWORK SECURITY
3. Research methodology
The research conducted for checking the security issues regarding the wireless
networking would be done by adopting two methodologies. Amongst them, one should be the
primary data collection and the other would be the secondary data collection. The detailed data
collection methods would be described as follows:
Primary Data Collection Method: As far as the primary data collection method is
concerned, the data collected in this method would be done by the means of qualitative and
quantitative methods and all the data are self collected. This is to ensure that the data that is
collected is absolutely raw and unique. Therefore, all the data that are collected belongs solely to
this research and does not belong to any other research or anybody else has access to it. There
are many methodologies that are adopted for conducting the primary data and these are done by
the following ways:
Conducting questionnaires
Conducting interviews
Conducting focus group interviews
Observation of research methodologies
Case study observations
Conducting scientific experiments
Secondary data collection method: Secondary data collection method is also a type of
collection of quantitative data that should be done in this research to collect data that has also
been collected by someone else for some different purpose other than this research topic. This
method would use the following data collecting methodologies:
WIRELESS NETWORK SECURITY
3. Research methodology
The research conducted for checking the security issues regarding the wireless
networking would be done by adopting two methodologies. Amongst them, one should be the
primary data collection and the other would be the secondary data collection. The detailed data
collection methods would be described as follows:
Primary Data Collection Method: As far as the primary data collection method is
concerned, the data collected in this method would be done by the means of qualitative and
quantitative methods and all the data are self collected. This is to ensure that the data that is
collected is absolutely raw and unique. Therefore, all the data that are collected belongs solely to
this research and does not belong to any other research or anybody else has access to it. There
are many methodologies that are adopted for conducting the primary data and these are done by
the following ways:
Conducting questionnaires
Conducting interviews
Conducting focus group interviews
Observation of research methodologies
Case study observations
Conducting scientific experiments
Secondary data collection method: Secondary data collection method is also a type of
collection of quantitative data that should be done in this research to collect data that has also
been collected by someone else for some different purpose other than this research topic. This
method would use the following data collecting methodologies:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
WIRELESS NETWORK SECURITY
Simple referencing of the original data, with evidence supported for the argument.
Some data can also be edited with basic questions being asked about the subject under
research, in this case, about the vulnerabilities that the wireless networking holds.
4. Evaluation methodology
The data analysis being driven will include evaluation of all the data collected during the
research and relative findings were linked at a single platform in manner to present a specific
result that is efficient and effective for the readers. The secondary data analysis will be delivered
for the development of a platform that will support the ongoing research and it will be also
helpful in developing the scope and objective for the sectors those have been untouched for now.
The secondary data analysis will result in the identification of the sectors those will contribute in
the further research and major focus will be made on those certain topics only. The scholar
articles in addition to the collected articles will be collected for further proceeding with the
research and thus, the knowledge contribution of different respectable writers will be embedded
within the new research for better clarification on the topic. The data collected by those writers
will contribute in better findings as most of the research gaps will be filled by further attempts of
the research. Thus, the secondary data analysis will assure that the research being driven will be
helpful in implementing the innovation within the research and reaching at a result that will be a
new section. In addition to the secondary data analysis, primary data analysis will be driven in
manner to be more specific and efficient towards the findings and assuring that the driven
direction of the research is on the correct path. The data collected through the interview and
questionnaire sessions will be collected and analyzed to reach at an exact and specific result.
The secondary data analysis ad primary data analysis will be used for the evaluation of
the findings through analyzing all the data and information collected through these methods.
WIRELESS NETWORK SECURITY
Simple referencing of the original data, with evidence supported for the argument.
Some data can also be edited with basic questions being asked about the subject under
research, in this case, about the vulnerabilities that the wireless networking holds.
4. Evaluation methodology
The data analysis being driven will include evaluation of all the data collected during the
research and relative findings were linked at a single platform in manner to present a specific
result that is efficient and effective for the readers. The secondary data analysis will be delivered
for the development of a platform that will support the ongoing research and it will be also
helpful in developing the scope and objective for the sectors those have been untouched for now.
The secondary data analysis will result in the identification of the sectors those will contribute in
the further research and major focus will be made on those certain topics only. The scholar
articles in addition to the collected articles will be collected for further proceeding with the
research and thus, the knowledge contribution of different respectable writers will be embedded
within the new research for better clarification on the topic. The data collected by those writers
will contribute in better findings as most of the research gaps will be filled by further attempts of
the research. Thus, the secondary data analysis will assure that the research being driven will be
helpful in implementing the innovation within the research and reaching at a result that will be a
new section. In addition to the secondary data analysis, primary data analysis will be driven in
manner to be more specific and efficient towards the findings and assuring that the driven
direction of the research is on the correct path. The data collected through the interview and
questionnaire sessions will be collected and analyzed to reach at an exact and specific result.
The secondary data analysis ad primary data analysis will be used for the evaluation of
the findings through analyzing all the data and information collected through these methods.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
WIRELESS NETWORK SECURITY
Thus, the collected data will provide the quantitative and qualitative result or findings in relation
to the respective topic. Identifying the quantitative value will be more specific than the
secondary data analysis and hence, it will be applied to the collected data and information and
thus, it will result in proposing a specific result related to the topics.
5. Schedule and publishing
The research will need proper planning and management in manner to assure that the
entire research has been accomplished in an efficient and effective manner. The proper planning
is always necessary for the successful accomplishment of the research and to follow a path that
can lead to certain specific and accurate findings. Following table describes the list of the
activities those need to be accomplished in a sequential manner in manner to allow the research
to be proceed in right path and deliver all the necessary activities those could lead the research
towards success. There are three major phases in this entire research that include planning,
execution, and closure in addition to various sub activities embedded within these activities.
These enlisted activities while planning to deliver the research will be helpful in assuring that the
research reaches to the final phase. The research will be closed after the submission of the
research. In manner to keep the realistic research, the listed activities will be accomplished as it
is and thus, the entire research will be effectively delivered to certain conclusion.
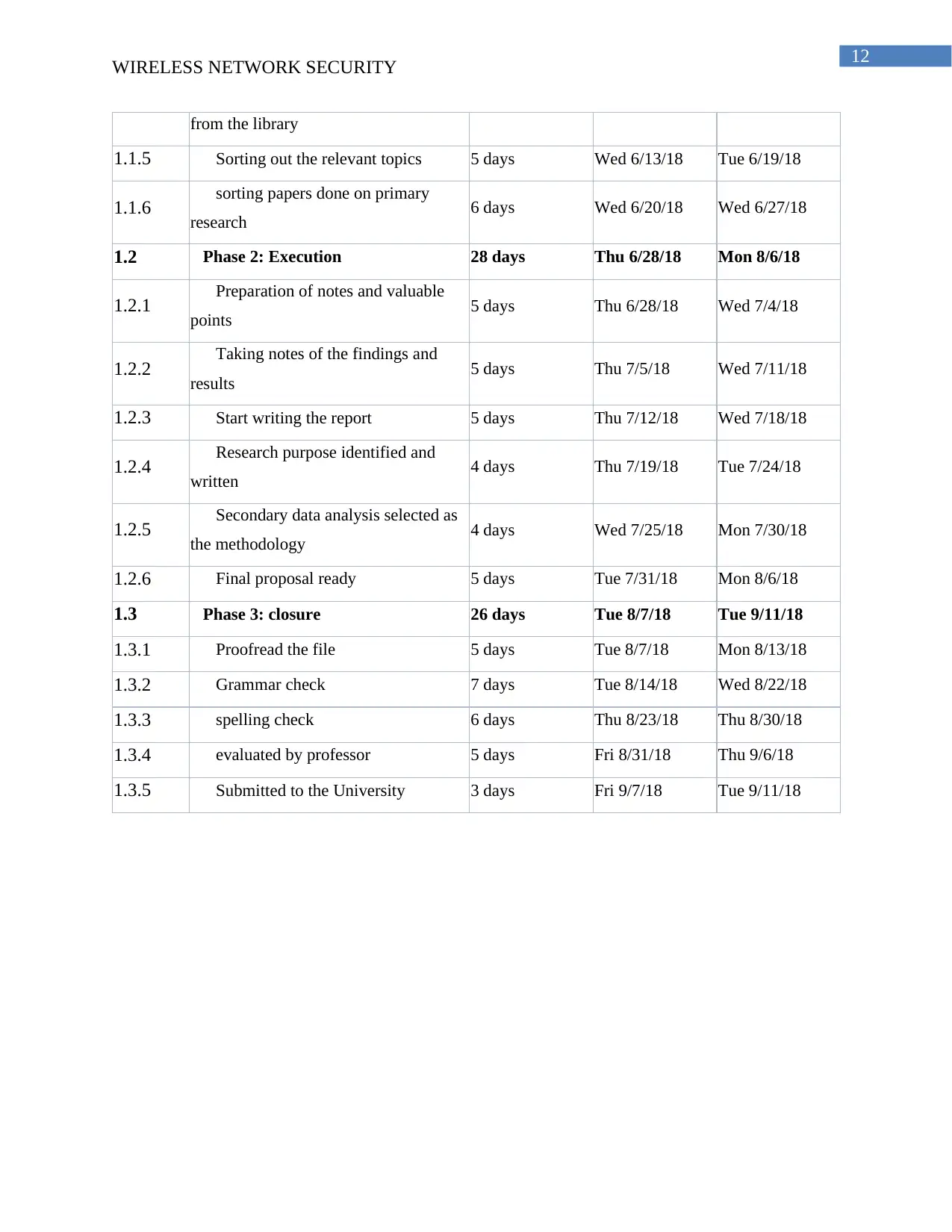
WBS Task Name Duration Start Finish
1 Schedule and Publishing 91 days Tue 5/8/18 Tue 9/11/18
1.1 Phase 1: Planning 37 days Tue 5/8/18 Wed 6/27/18
1.1.1 Identification of the Topics 7 days Tue 5/8/18 Wed 5/16/18
1.1.2 Selection of the Topic 5 days Thu 5/17/18 Wed 5/23/18
1.1.3 Approval for the Topic 8 days Thu 5/24/18 Mon 6/4/18
1.1.4 Collecting literatures and resources 6 days Tue 6/5/18 Tue 6/12/18
WIRELESS NETWORK SECURITY
Thus, the collected data will provide the quantitative and qualitative result or findings in relation
to the respective topic. Identifying the quantitative value will be more specific than the
secondary data analysis and hence, it will be applied to the collected data and information and
thus, it will result in proposing a specific result related to the topics.
5. Schedule and publishing
The research will need proper planning and management in manner to assure that the
entire research has been accomplished in an efficient and effective manner. The proper planning
is always necessary for the successful accomplishment of the research and to follow a path that
can lead to certain specific and accurate findings. Following table describes the list of the
activities those need to be accomplished in a sequential manner in manner to allow the research
to be proceed in right path and deliver all the necessary activities those could lead the research
towards success. There are three major phases in this entire research that include planning,
execution, and closure in addition to various sub activities embedded within these activities.
These enlisted activities while planning to deliver the research will be helpful in assuring that the
research reaches to the final phase. The research will be closed after the submission of the
research. In manner to keep the realistic research, the listed activities will be accomplished as it
is and thus, the entire research will be effectively delivered to certain conclusion.
WBS Task Name Duration Start Finish
1 Schedule and Publishing 91 days Tue 5/8/18 Tue 9/11/18
1.1 Phase 1: Planning 37 days Tue 5/8/18 Wed 6/27/18
1.1.1 Identification of the Topics 7 days Tue 5/8/18 Wed 5/16/18
1.1.2 Selection of the Topic 5 days Thu 5/17/18 Wed 5/23/18
1.1.3 Approval for the Topic 8 days Thu 5/24/18 Mon 6/4/18
1.1.4 Collecting literatures and resources 6 days Tue 6/5/18 Tue 6/12/18
12
WIRELESS NETWORK SECURITY
from the library
1.1.5 Sorting out the relevant topics 5 days Wed 6/13/18 Tue 6/19/18
1.1.6 sorting papers done on primary
research 6 days Wed 6/20/18 Wed 6/27/18
1.2 Phase 2: Execution 28 days Thu 6/28/18 Mon 8/6/18
1.2.1 Preparation of notes and valuable
points 5 days Thu 6/28/18 Wed 7/4/18
1.2.2 Taking notes of the findings and
results 5 days Thu 7/5/18 Wed 7/11/18
1.2.3 Start writing the report 5 days Thu 7/12/18 Wed 7/18/18
1.2.4 Research purpose identified and
written 4 days Thu 7/19/18 Tue 7/24/18
1.2.5 Secondary data analysis selected as
the methodology 4 days Wed 7/25/18 Mon 7/30/18
1.2.6 Final proposal ready 5 days Tue 7/31/18 Mon 8/6/18
1.3 Phase 3: closure 26 days Tue 8/7/18 Tue 9/11/18
1.3.1 Proofread the file 5 days Tue 8/7/18 Mon 8/13/18
1.3.2 Grammar check 7 days Tue 8/14/18 Wed 8/22/18
1.3.3 spelling check 6 days Thu 8/23/18 Thu 8/30/18
1.3.4 evaluated by professor 5 days Fri 8/31/18 Thu 9/6/18
1.3.5 Submitted to the University 3 days Fri 9/7/18 Tue 9/11/18
WIRELESS NETWORK SECURITY
from the library
1.1.5 Sorting out the relevant topics 5 days Wed 6/13/18 Tue 6/19/18
1.1.6 sorting papers done on primary
research 6 days Wed 6/20/18 Wed 6/27/18
1.2 Phase 2: Execution 28 days Thu 6/28/18 Mon 8/6/18
1.2.1 Preparation of notes and valuable
points 5 days Thu 6/28/18 Wed 7/4/18
1.2.2 Taking notes of the findings and
results 5 days Thu 7/5/18 Wed 7/11/18
1.2.3 Start writing the report 5 days Thu 7/12/18 Wed 7/18/18
1.2.4 Research purpose identified and
written 4 days Thu 7/19/18 Tue 7/24/18
1.2.5 Secondary data analysis selected as
the methodology 4 days Wed 7/25/18 Mon 7/30/18
1.2.6 Final proposal ready 5 days Tue 7/31/18 Mon 8/6/18
1.3 Phase 3: closure 26 days Tue 8/7/18 Tue 9/11/18
1.3.1 Proofread the file 5 days Tue 8/7/18 Mon 8/13/18
1.3.2 Grammar check 7 days Tue 8/14/18 Wed 8/22/18
1.3.3 spelling check 6 days Thu 8/23/18 Thu 8/30/18
1.3.4 evaluated by professor 5 days Fri 8/31/18 Thu 9/6/18
1.3.5 Submitted to the University 3 days Fri 9/7/18 Tue 9/11/18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




