MN603 Wireless Networks and Security: Evaluation of LTE/LTE-A Security
VerifiedAdded on 2023/06/07
|8
|1935
|62
Report
AI Summary
This report provides a detailed evaluation of LTE/LTE-A network security, beginning with a comparison of various cellular networks like GSM, EV-Do, EDGE, UMTS, DECT, and iDEN, focusing on their communication spectrum, modulation techniques, network speed, and bandwidth utilization. It then delves into the architecture of LTE/LTE-A, outlining the user equipment (UE), evolved UMTS Terrestrial Radio Access Network (E-UTRAN), and evolved packet core (EPC). The report identifies and analyzes potential attacks on LTE/LTE-A networks, differentiating between access network and core network attacks, such as IMSI disclosure, sniffing, spoofing, and DoS/DDoS attacks. Countermeasures to mitigate these risks, including IMSI confidentiality, secure location tracking, and filtering techniques, are discussed. The conclusion highlights LTE's superior speed and bandwidth, emphasizing the importance of robust security measures to protect against identified vulnerabilities. This report will be published on Desklib, a platform offering a wide array of study tools and solved assignments for students.

Running head: WIREESS NETWORK AND SECURITY
Wireless Network and Security
Name of the Student
Name of the University
Author Note
Wireless Network and Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIREESS NETWORK AND SECURITY
Introduction:
The main aim of the report is to discuss and compare the wireless networking. The network
security based on LTE/LTE-A will also be discussed in this report. LTE stands for long-term evolution. This is
based on UMTS/HSPA and GSM/EDGE. This network provides high speed and better capacity then other
networks as this uses different interfaces with different wavelength of radio. This helps in improving the
speed, in addition to this they uses core network for improving the speed. The discussion will include
performance of all the existing cellular networks in the market. Further, the paper will focus on the
architecture of LTE/LTE-A. The possible attacks for this network will be discussed further in the report.
Comparison between Existing Cellular Networks:
Communication Spectrum:
In the current communication technology, there are varieties of cellular networks. The various
cellular technologies consists of GSM, GPRS , EV-Do , EDGE ,UMTS, DECT, iDEN [1].
GSM: Global system for Mobiles (GSM) is a standard developed by European Telecommunication Standards
Institute. This describes the protocols that are needed to be followed by the users of mobiles or networks
while using 2nd Generation digital cellular networks.
EV-Do: The telecommunication that takes place with wireless data communication takes place, through
the means of radio waves. This is the advanced and developed version of CDMA2000 standard [4]. This is
also used with wireless carrier’s voice service.
EDGE: EDGE was first deployed in the year 2003 with association of Cingular in the United States. This is
basically a mobile technology that provides better and improve rate of transmitting data.
UMTS: UMTS was developed by 3rd Generation Partnership Project. Based on the GSM standard, this is the
third generation network for 3G mobiles.
DECT: DECT was basically originated in Europe with a standard created for wireless telephone system. Later
on by the people of Europe this was considered as the universal standard and replaced all other existing
telephone standards [5].
iDEN: The technology that is connected , so that they can provide users with benefit for using cellular
telephone and trunked radio. iDEN uses TDMA and speech density , so that they can place users in a given
spectral space.
Introduction:
The main aim of the report is to discuss and compare the wireless networking. The network
security based on LTE/LTE-A will also be discussed in this report. LTE stands for long-term evolution. This is
based on UMTS/HSPA and GSM/EDGE. This network provides high speed and better capacity then other
networks as this uses different interfaces with different wavelength of radio. This helps in improving the
speed, in addition to this they uses core network for improving the speed. The discussion will include
performance of all the existing cellular networks in the market. Further, the paper will focus on the
architecture of LTE/LTE-A. The possible attacks for this network will be discussed further in the report.
Comparison between Existing Cellular Networks:
Communication Spectrum:
In the current communication technology, there are varieties of cellular networks. The various
cellular technologies consists of GSM, GPRS , EV-Do , EDGE ,UMTS, DECT, iDEN [1].
GSM: Global system for Mobiles (GSM) is a standard developed by European Telecommunication Standards
Institute. This describes the protocols that are needed to be followed by the users of mobiles or networks
while using 2nd Generation digital cellular networks.
EV-Do: The telecommunication that takes place with wireless data communication takes place, through
the means of radio waves. This is the advanced and developed version of CDMA2000 standard [4]. This is
also used with wireless carrier’s voice service.
EDGE: EDGE was first deployed in the year 2003 with association of Cingular in the United States. This is
basically a mobile technology that provides better and improve rate of transmitting data.
UMTS: UMTS was developed by 3rd Generation Partnership Project. Based on the GSM standard, this is the
third generation network for 3G mobiles.
DECT: DECT was basically originated in Europe with a standard created for wireless telephone system. Later
on by the people of Europe this was considered as the universal standard and replaced all other existing
telephone standards [5].
iDEN: The technology that is connected , so that they can provide users with benefit for using cellular
telephone and trunked radio. iDEN uses TDMA and speech density , so that they can place users in a given
spectral space.
2WIREESS NETWORK AND SECURITY
Modulation Technique:
Different networks use different modulation techniques. Starting with 1st generation network in the
cellular networks, after this the 2nd generation digital network came in the market of networking and kept
on expanding the features.
Network Speed and Bandwidth Utilization:
With the evolution of technology, the digital network became better in respect of time speed and
the bandwidth provided by these networks. The frequency used by 1g follows analogue communication
system [2]. All the networks after 1g use digital communication mechanism that is the 2g, 3g and the 4g.
With the development in the technology of the cellular network the speed, bandwidth and frequency of all
the networks increases. The speed of different networks varies widely from 1g to 4g. 1g gives speed of 2.4
Kbps to 14.4 kbps, whereas speed given by 2g network is 14.4 Kbps. The 3g network provides a speed of 3.1
Mbps and 4g network provides speed of 100 Mbps. Among all the networks, 1g is the only one that gives
analog bandwidth. Both 1g and 2g network have same frequency [3]. With time, the bandwidth allocation
has also improved with enhancement in technologies for cellular networks.
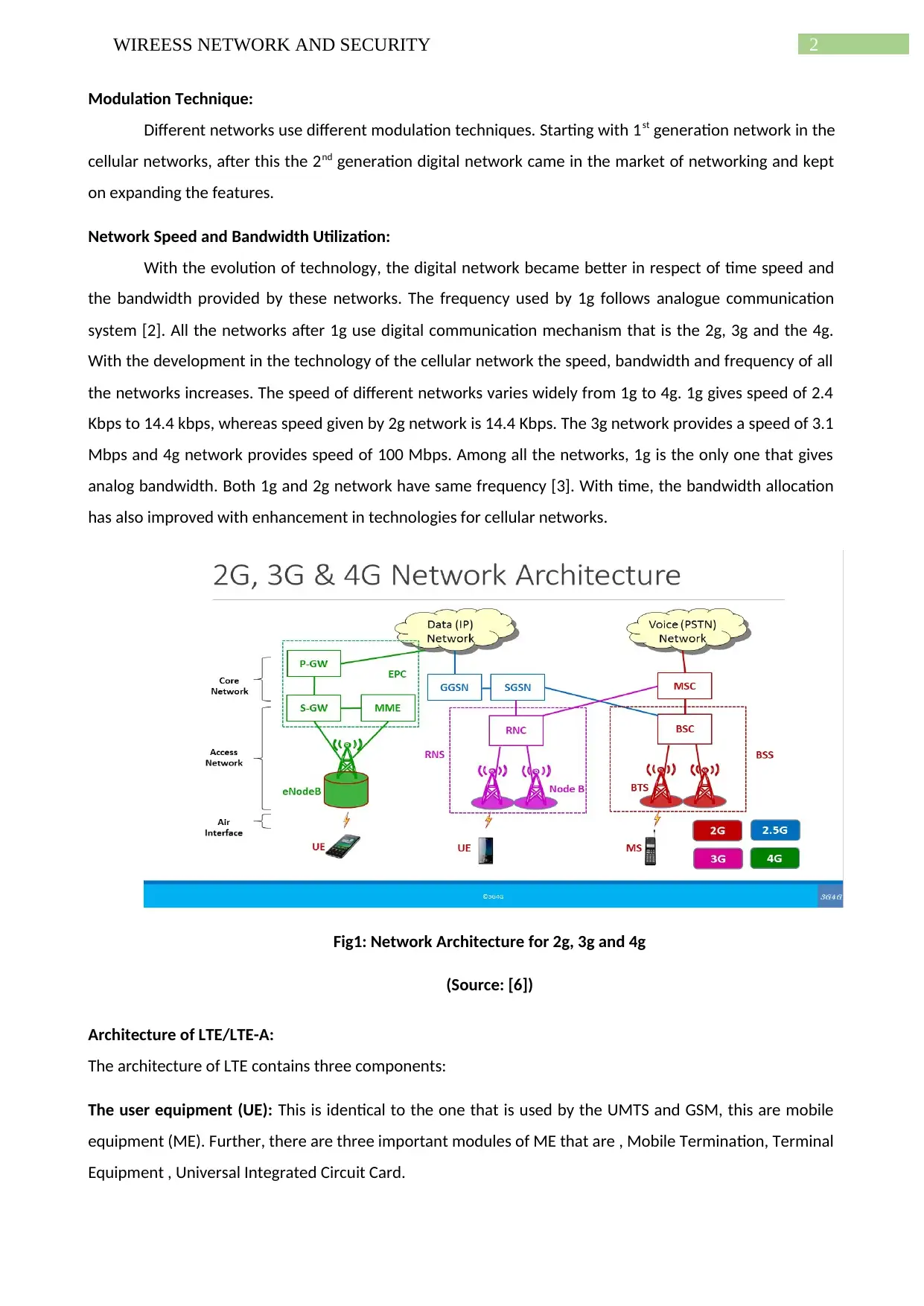
Fig1: Network Architecture for 2g, 3g and 4g
(Source: [6])
Architecture of LTE/LTE-A:
The architecture of LTE contains three components:
The user equipment (UE): This is identical to the one that is used by the UMTS and GSM, this are mobile
equipment (ME). Further, there are three important modules of ME that are , Mobile Termination, Terminal
Equipment , Universal Integrated Circuit Card.
Modulation Technique:
Different networks use different modulation techniques. Starting with 1st generation network in the
cellular networks, after this the 2nd generation digital network came in the market of networking and kept
on expanding the features.
Network Speed and Bandwidth Utilization:
With the evolution of technology, the digital network became better in respect of time speed and
the bandwidth provided by these networks. The frequency used by 1g follows analogue communication
system [2]. All the networks after 1g use digital communication mechanism that is the 2g, 3g and the 4g.
With the development in the technology of the cellular network the speed, bandwidth and frequency of all
the networks increases. The speed of different networks varies widely from 1g to 4g. 1g gives speed of 2.4
Kbps to 14.4 kbps, whereas speed given by 2g network is 14.4 Kbps. The 3g network provides a speed of 3.1
Mbps and 4g network provides speed of 100 Mbps. Among all the networks, 1g is the only one that gives
analog bandwidth. Both 1g and 2g network have same frequency [3]. With time, the bandwidth allocation
has also improved with enhancement in technologies for cellular networks.
Fig1: Network Architecture for 2g, 3g and 4g
(Source: [6])
Architecture of LTE/LTE-A:
The architecture of LTE contains three components:
The user equipment (UE): This is identical to the one that is used by the UMTS and GSM, this are mobile
equipment (ME). Further, there are three important modules of ME that are , Mobile Termination, Terminal
Equipment , Universal Integrated Circuit Card.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3WIREESS NETWORK AND SECURITY
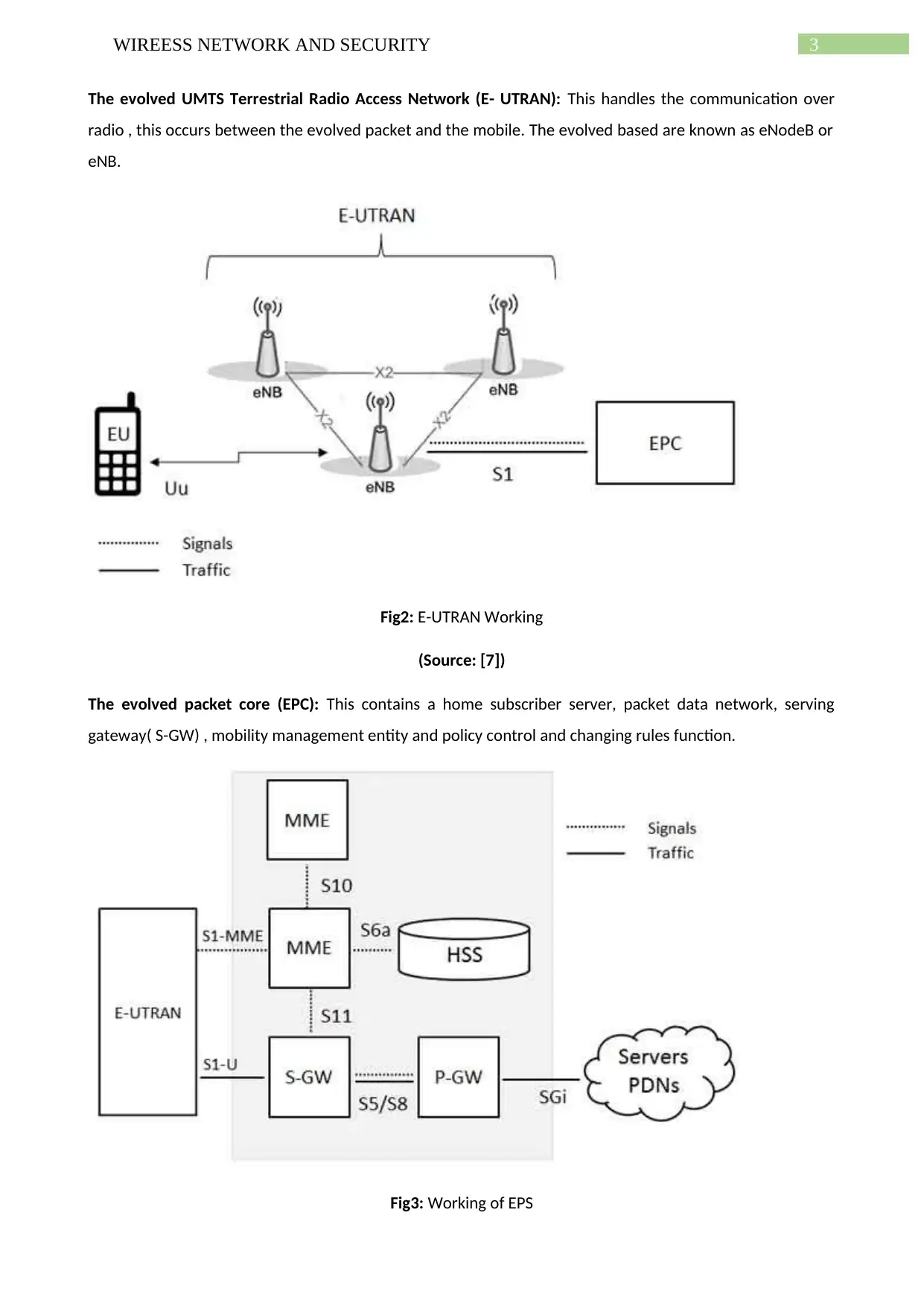
The evolved UMTS Terrestrial Radio Access Network (E- UTRAN): This handles the communication over
radio , this occurs between the evolved packet and the mobile. The evolved based are known as eNodeB or
eNB.
Fig2: E-UTRAN Working
(Source: [7])
The evolved packet core (EPC): This contains a home subscriber server, packet data network, serving
gateway( S-GW) , mobility management entity and policy control and changing rules function.
Fig3: Working of EPS
The evolved UMTS Terrestrial Radio Access Network (E- UTRAN): This handles the communication over
radio , this occurs between the evolved packet and the mobile. The evolved based are known as eNodeB or
eNB.
Fig2: E-UTRAN Working
(Source: [7])
The evolved packet core (EPC): This contains a home subscriber server, packet data network, serving
gateway( S-GW) , mobility management entity and policy control and changing rules function.
Fig3: Working of EPS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4WIREESS NETWORK AND SECURITY
(Source: [7])
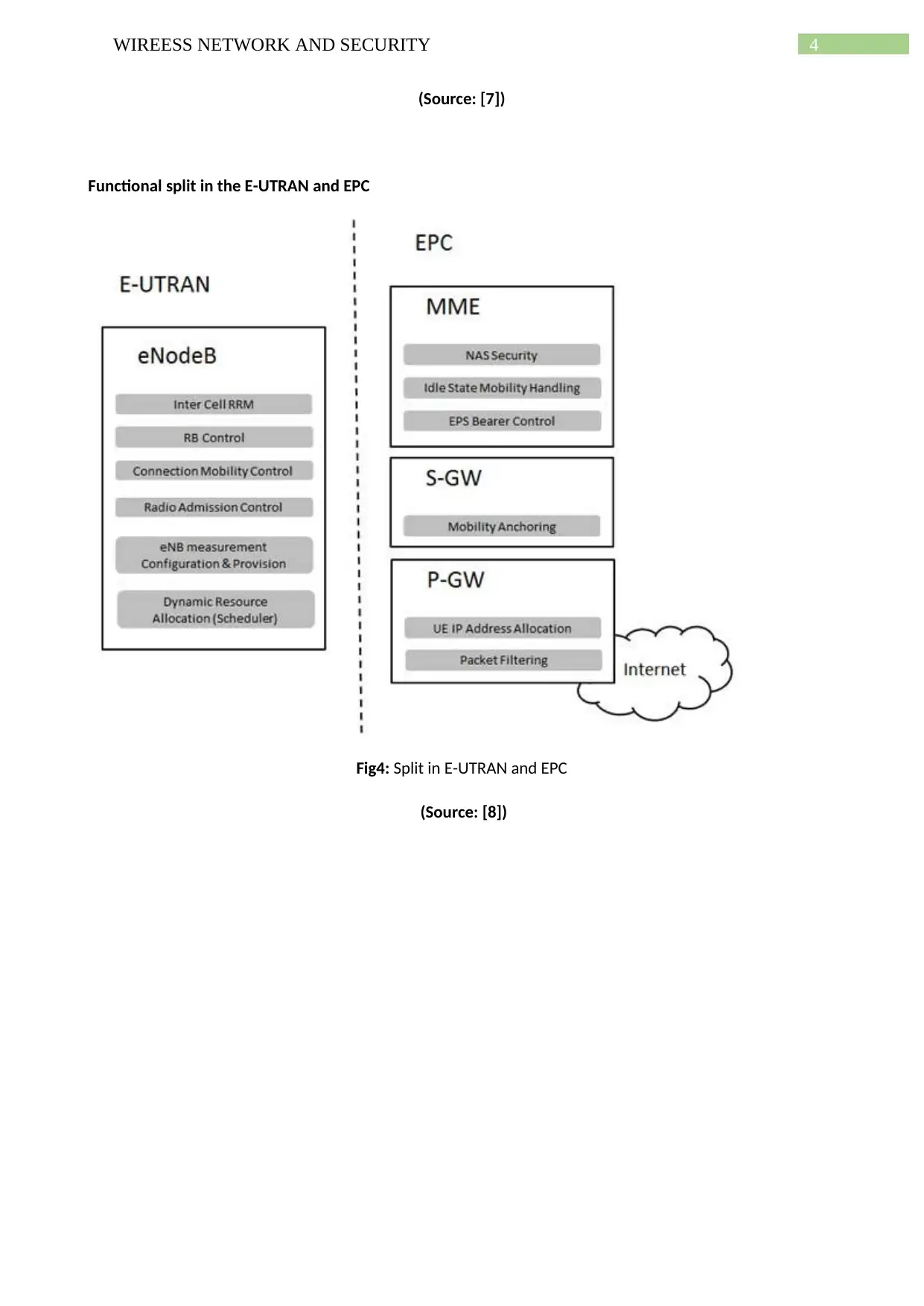
Functional split in the E-UTRAN and EPC
Fig4: Split in E-UTRAN and EPC
(Source: [8])
(Source: [7])
Functional split in the E-UTRAN and EPC
Fig4: Split in E-UTRAN and EPC
(Source: [8])
5WIREESS NETWORK AND SECURITY
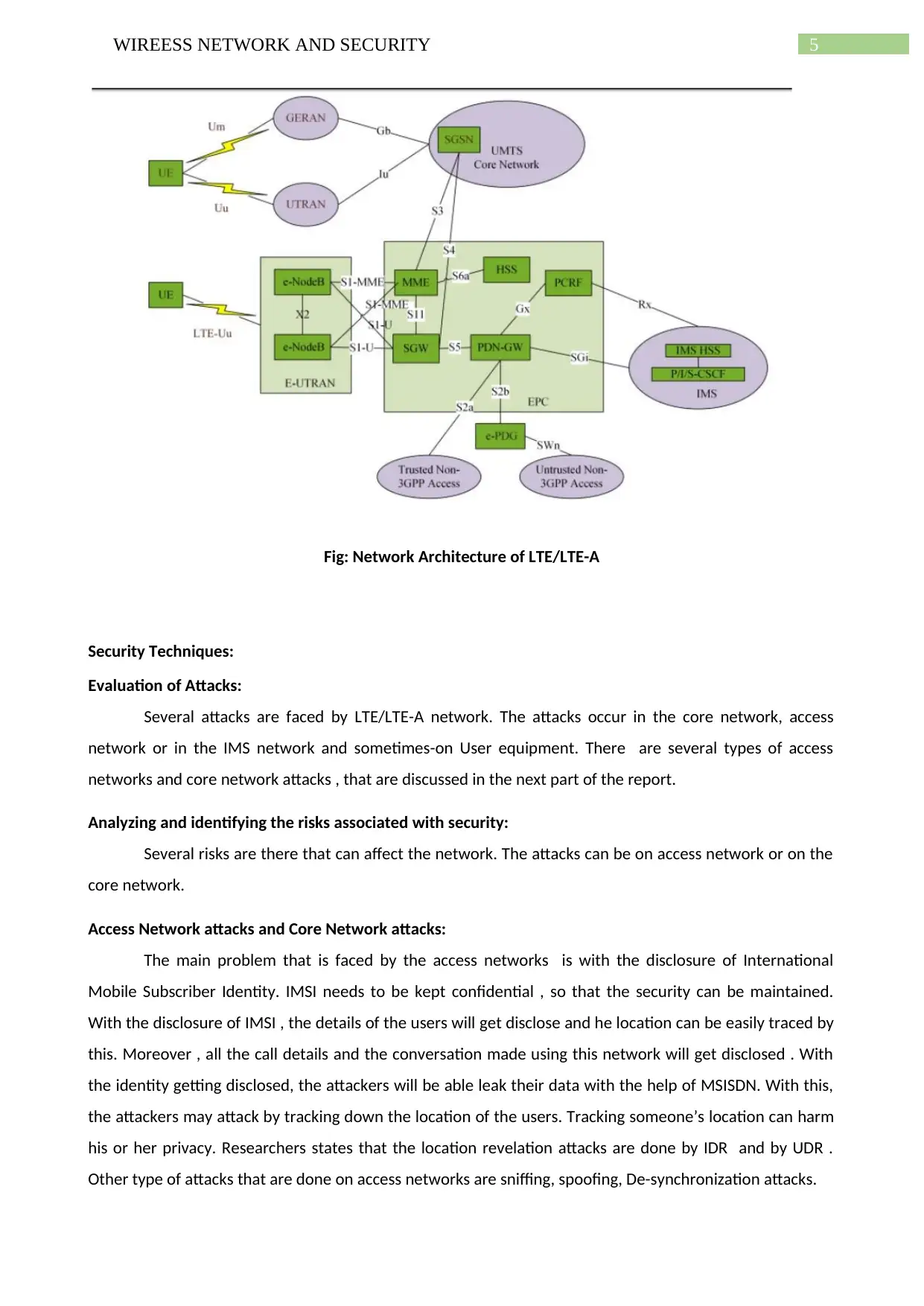
Fig: Network Architecture of LTE/LTE-A
Security Techniques:
Evaluation of Attacks:
Several attacks are faced by LTE/LTE-A network. The attacks occur in the core network, access
network or in the IMS network and sometimes-on User equipment. There are several types of access
networks and core network attacks , that are discussed in the next part of the report.
Analyzing and identifying the risks associated with security:
Several risks are there that can affect the network. The attacks can be on access network or on the
core network.
Access Network attacks and Core Network attacks:
The main problem that is faced by the access networks is with the disclosure of International
Mobile Subscriber Identity. IMSI needs to be kept confidential , so that the security can be maintained.
With the disclosure of IMSI , the details of the users will get disclose and he location can be easily traced by
this. Moreover , all the call details and the conversation made using this network will get disclosed . With
the identity getting disclosed, the attackers will be able leak their data with the help of MSISDN. With this,
the attackers may attack by tracking down the location of the users. Tracking someone’s location can harm
his or her privacy. Researchers states that the location revelation attacks are done by IDR and by UDR .
Other type of attacks that are done on access networks are sniffing, spoofing, De-synchronization attacks.
Fig: Network Architecture of LTE/LTE-A
Security Techniques:
Evaluation of Attacks:
Several attacks are faced by LTE/LTE-A network. The attacks occur in the core network, access
network or in the IMS network and sometimes-on User equipment. There are several types of access
networks and core network attacks , that are discussed in the next part of the report.
Analyzing and identifying the risks associated with security:
Several risks are there that can affect the network. The attacks can be on access network or on the
core network.
Access Network attacks and Core Network attacks:
The main problem that is faced by the access networks is with the disclosure of International
Mobile Subscriber Identity. IMSI needs to be kept confidential , so that the security can be maintained.
With the disclosure of IMSI , the details of the users will get disclose and he location can be easily traced by
this. Moreover , all the call details and the conversation made using this network will get disclosed . With
the identity getting disclosed, the attackers will be able leak their data with the help of MSISDN. With this,
the attackers may attack by tracking down the location of the users. Tracking someone’s location can harm
his or her privacy. Researchers states that the location revelation attacks are done by IDR and by UDR .
Other type of attacks that are done on access networks are sniffing, spoofing, De-synchronization attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIREESS NETWORK AND SECURITY
The first attack that is made in the core network is the attack related to the DOS/DDOS. There is a
huge threat for LTE/LTE- A with the attack on DOS/DDOS [8]. To attack the DDOS/DOS botnet is used. This is
used to generate attacks on the core network. Secondly, the core network is vulnerable to insider attacks.
In these cases, the attackers are the one who have the access to this core network. The insiders have the
power to completely stop the base station [9].
Countermeasure for avoid the risks:
To overcome the risks , the countermeasures are as follows:
The IMSI should be kept confidential; this will protect the network from attackers.
The system should ensure the security, by providing only the location details while tracking any
device, no other information should be shared.
The network should ensure that no sniffing or data breaching occurs within the networks. This will
help the network to maintain the confidentiality of the user’s information.
To protect the DoS/DDoS against attacks, there are two methods that are needed to be considered
are filtering and blackholing. These will help to avoid the attacks on the DoS/DDoS.
By limiting the authorization insider attack can be prevented within the network.
Conclusion:
The above report discusses about the LTE/LTE-A. The bandwidth and the speed provided by the LTE
network are higher than other networks. The above report discusses about the different types of cellular
networks and the bandwidth and speed provided by them . Further, the report describes the structure of
the LTE networks and the possible risks that are associated with the LTE networks. The impacts of this type
of attacks on the network are discussed in the later part of the report. From the above report, it can be
concluded that LTE provides a better form of wireless communication with better speed and bandwidth.
The first attack that is made in the core network is the attack related to the DOS/DDOS. There is a
huge threat for LTE/LTE- A with the attack on DOS/DDOS [8]. To attack the DDOS/DOS botnet is used. This is
used to generate attacks on the core network. Secondly, the core network is vulnerable to insider attacks.
In these cases, the attackers are the one who have the access to this core network. The insiders have the
power to completely stop the base station [9].
Countermeasure for avoid the risks:
To overcome the risks , the countermeasures are as follows:
The IMSI should be kept confidential; this will protect the network from attackers.
The system should ensure the security, by providing only the location details while tracking any
device, no other information should be shared.
The network should ensure that no sniffing or data breaching occurs within the networks. This will
help the network to maintain the confidentiality of the user’s information.
To protect the DoS/DDoS against attacks, there are two methods that are needed to be considered
are filtering and blackholing. These will help to avoid the attacks on the DoS/DDoS.
By limiting the authorization insider attack can be prevented within the network.
Conclusion:
The above report discusses about the LTE/LTE-A. The bandwidth and the speed provided by the LTE
network are higher than other networks. The above report discusses about the different types of cellular
networks and the bandwidth and speed provided by them . Further, the report describes the structure of
the LTE networks and the possible risks that are associated with the LTE networks. The impacts of this type
of attacks on the network are discussed in the later part of the report. From the above report, it can be
concluded that LTE provides a better form of wireless communication with better speed and bandwidth.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIREESS NETWORK AND SECURITY
References:
[1] J. Cao, M. Ma, H. Li, Y. Zhang and Z. Luo, A survey on security aspects for LTE and LTE-A
networks, IEEE Communications Surveys & Tutorials, 16(1), pp.283-302 ,(2014).
[2] F. Ghavimi and H.H. Chen, M2M communications in 3GPP LTE/LTE-A networks: Architectures,
service requirements, challenges, and applications, IEEE Communications Surveys & Tutorials, 17(2),
pp.525-549, (2015).
[3] B. Guo, W. Cao, A. Tao and D. Samardzija, LTE/LTE-A signal compression on the CPRI interface, Bell
Labs Technical Journal, 18(2), pp.117-133 ,(2013).
[4] M.K. Hasan, A.F. Ismail, A.H. Abdalla, K. Abdullah, H. Ramli, S. Islam, and R.A. Saeed , August. Inter-
cell interference coordination in LTE-A HetNets: A survey on self organizing approaches, In Computing,
Electrical and Electronics Engineering (ICCEEE), 2013 International Conference on (pp. 196-201), IEEE,
(2013).
[5] M. Labib, V. Marojevic and J.H. Reed, October. Analyzing and enhancing the resilience of LTE/LTE-A
systems to RF spoofing. In Standards for Communications and Networking (CSCN), 2015 IEEE
Conference on (pp. 315-320), IEEE, (2015).
[6] Y.L. Lee, T.C. Chuah, J. Loo and A. Vinel, Recent advances in radio resource management for
heterogeneous LTE/LTE-A networks, IEEE Communications Surveys & Tutorials, 16(4), pp.2142-2180 ,
(2014).
[7] M. Lichtman, R.P. Jover, M. Labib, R. Rao, V. Marojevic and J.H. Reed, LTE/LTE-A jamming, spoofing,
and sniffing: threat assessment and mitigation, IEEE Communications Magazine, 54(4), pp.54-61 ,
(2016).
[8] S. Mishra and N. Mathur, Load Balancing Optimization in LTE/LTE-A Cellular Networks: A
Review, arXiv preprint arXiv:1412.7273,(2014).
[9] A. Virdis, G. Stea and G. Nardini, G., 2014, August. SimuLTE-A modular system-level simulator for
LTE/LTE-A networks based on OMNeT++. In Simulation and Modeling Methodologies, Technologies and
Applications (SIMULTECH), International Conference on (pp. 59-70),IEEE, (2014).
References:
[1] J. Cao, M. Ma, H. Li, Y. Zhang and Z. Luo, A survey on security aspects for LTE and LTE-A
networks, IEEE Communications Surveys & Tutorials, 16(1), pp.283-302 ,(2014).
[2] F. Ghavimi and H.H. Chen, M2M communications in 3GPP LTE/LTE-A networks: Architectures,
service requirements, challenges, and applications, IEEE Communications Surveys & Tutorials, 17(2),
pp.525-549, (2015).
[3] B. Guo, W. Cao, A. Tao and D. Samardzija, LTE/LTE-A signal compression on the CPRI interface, Bell
Labs Technical Journal, 18(2), pp.117-133 ,(2013).
[4] M.K. Hasan, A.F. Ismail, A.H. Abdalla, K. Abdullah, H. Ramli, S. Islam, and R.A. Saeed , August. Inter-
cell interference coordination in LTE-A HetNets: A survey on self organizing approaches, In Computing,
Electrical and Electronics Engineering (ICCEEE), 2013 International Conference on (pp. 196-201), IEEE,
(2013).
[5] M. Labib, V. Marojevic and J.H. Reed, October. Analyzing and enhancing the resilience of LTE/LTE-A
systems to RF spoofing. In Standards for Communications and Networking (CSCN), 2015 IEEE
Conference on (pp. 315-320), IEEE, (2015).
[6] Y.L. Lee, T.C. Chuah, J. Loo and A. Vinel, Recent advances in radio resource management for
heterogeneous LTE/LTE-A networks, IEEE Communications Surveys & Tutorials, 16(4), pp.2142-2180 ,
(2014).
[7] M. Lichtman, R.P. Jover, M. Labib, R. Rao, V. Marojevic and J.H. Reed, LTE/LTE-A jamming, spoofing,
and sniffing: threat assessment and mitigation, IEEE Communications Magazine, 54(4), pp.54-61 ,
(2016).
[8] S. Mishra and N. Mathur, Load Balancing Optimization in LTE/LTE-A Cellular Networks: A
Review, arXiv preprint arXiv:1412.7273,(2014).
[9] A. Virdis, G. Stea and G. Nardini, G., 2014, August. SimuLTE-A modular system-level simulator for
LTE/LTE-A networks based on OMNeT++. In Simulation and Modeling Methodologies, Technologies and
Applications (SIMULTECH), International Conference on (pp. 59-70),IEEE, (2014).
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



