Comprehensive Report on Security Issues in Wireless Networks
VerifiedAdded on 2023/06/04
|12
|2771
|266
Report
AI Summary
This report provides a comprehensive overview of security issues in wireless networks, focusing on challenges and prevention methods. It begins with an introduction to wireless network security, highlighting the flexibility and long-distance communication capabilities of wireless technologies such as WLAN and Ad-Hoc networks. The report identifies key security threats, including parking lot attacks, shared key authentication flaws, denial-of-service (DOS) attacks, and configuration conflicts. It explores technologies like Service Set Identifiers (SSID), open system authentication, and access points used to enhance wireless security. The literature review identifies gaps in addressing data breaches and cyber-attacks, proposing the adoption of robust security policies and biometric technologies. The report concludes by emphasizing the importance of security programs, cryptography, and reliable equipment to protect wireless networks from unauthorized access and data breaches, suggesting future improvements in speed, performance, and encryption for more secure communication systems. Desklib provides access to this and other solved assignments for students.

Security of Wireless networks
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORK SECURITY
1
Abstract
A wireless network is a part of a communication system which is used by many
organizations because it is more flexible as compared to other computer networks. This
latest technology covers a large range of capabilities oriented programmes and with the
help of wireless system users can move their computer device from one place to
another. WLAN is one of the best types of a wireless network because it provides a
platform to share information over long distance and it is more reliable communication
systems. AD-HOC network is used to interconnect two or more digital devices and it
does not require any connecting cables because it uses wireless transmitters and
receivers. The main purpose of this report is to understand security issues faced in
wireless networks and their prevention methods. For security, users can adopt
advanced networks and systems like encryption, cryptography, and IOT.
Keywords: WLAN, Ad-Hoc network, transmitter and receiver, IOT, and flexibility.
1
Abstract
A wireless network is a part of a communication system which is used by many
organizations because it is more flexible as compared to other computer networks. This
latest technology covers a large range of capabilities oriented programmes and with the
help of wireless system users can move their computer device from one place to
another. WLAN is one of the best types of a wireless network because it provides a
platform to share information over long distance and it is more reliable communication
systems. AD-HOC network is used to interconnect two or more digital devices and it
does not require any connecting cables because it uses wireless transmitters and
receivers. The main purpose of this report is to understand security issues faced in
wireless networks and their prevention methods. For security, users can adopt
advanced networks and systems like encryption, cryptography, and IOT.
Keywords: WLAN, Ad-Hoc network, transmitter and receiver, IOT, and flexibility.

WIRELESS NETWORK SECURITY
2
Table of Contents
Abstract.................................................................................................................................................1
Introduction...........................................................................................................................................3
Overview of wireless networks security................................................................................................3
Technologies used in Wireless network security...................................................................................4
Service Set Identifier..........................................................................................................................5
Open system authentication.............................................................................................................5
Access point.......................................................................................................................................5
Ad Hoc networks...............................................................................................................................5
Challenges/issues faced in wireless networks.......................................................................................6
Parking Lot Attack..............................................................................................................................6
Shared key authentication flaw.........................................................................................................6
DOS attack.........................................................................................................................................7
Configuration conflict........................................................................................................................7
(Literature Review) Gaps in the literature.............................................................................................8
Proposed Design....................................................................................................................................8
Future scope..........................................................................................................................................8
Conclusion.............................................................................................................................................9
References...........................................................................................................................................10
2
Table of Contents
Abstract.................................................................................................................................................1
Introduction...........................................................................................................................................3
Overview of wireless networks security................................................................................................3
Technologies used in Wireless network security...................................................................................4
Service Set Identifier..........................................................................................................................5
Open system authentication.............................................................................................................5
Access point.......................................................................................................................................5
Ad Hoc networks...............................................................................................................................5
Challenges/issues faced in wireless networks.......................................................................................6
Parking Lot Attack..............................................................................................................................6
Shared key authentication flaw.........................................................................................................6
DOS attack.........................................................................................................................................7
Configuration conflict........................................................................................................................7
(Literature Review) Gaps in the literature.............................................................................................8
Proposed Design....................................................................................................................................8
Future scope..........................................................................................................................................8
Conclusion.............................................................................................................................................9
References...........................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS NETWORK SECURITY
3
Introduction
Wireless technologies are very popular in terms of communication and
flexibility. The main benefit of this computer system is that it can be used for long
distance communication that means consumers can share their private data from one
location to another. The main objective of this paper is to describe different kinds of
security challenges and threats faced in wireless networks and how users can reduce
this type of issues. Wireless security is a platform where users can avoid unauthorized
servers and damage to computer systems. This report is categorized into three parts, for
example, an overview of wireless network security, challenges and issues, and the gap
in the literature.
Research problem
The main problem occurs with wireless networks is data breach and denial of
services attack. This report finds various kinds of problem and issues of wireless
network security.
Research Justification
There are many wireless networks developed in the last few years by which
users can improve the performance of their systems like WLAN, and IoT (Chen, Qian,
Mao, Tang, & Yang, 2016). The problem of security can be reduced by encryption and
firewall software and consumers can use the robust process to block unwanted traffic
signals.
Overview of wireless networks security
For any computer network security is a very important key factor and from last
few year security issues in a wireless system is increasing very fast (Al, Al, Shojafar, &
Shamshirband, 2017). It is defined as a step to improve the security of user private
information and it is also called a subset of computer security that provides protection
methods for wireless communication. Generally, security of the wireless network is
produced with the help of various computer and digital devices like routers, switched
and hubs (Díaz, Martín, & Rubio, 2016). It is estimated that if any user adopts security
plans for their networks then the hacker is not able to enter into personal servers.
3
Introduction
Wireless technologies are very popular in terms of communication and
flexibility. The main benefit of this computer system is that it can be used for long
distance communication that means consumers can share their private data from one
location to another. The main objective of this paper is to describe different kinds of
security challenges and threats faced in wireless networks and how users can reduce
this type of issues. Wireless security is a platform where users can avoid unauthorized
servers and damage to computer systems. This report is categorized into three parts, for
example, an overview of wireless network security, challenges and issues, and the gap
in the literature.
Research problem
The main problem occurs with wireless networks is data breach and denial of
services attack. This report finds various kinds of problem and issues of wireless
network security.
Research Justification
There are many wireless networks developed in the last few years by which
users can improve the performance of their systems like WLAN, and IoT (Chen, Qian,
Mao, Tang, & Yang, 2016). The problem of security can be reduced by encryption and
firewall software and consumers can use the robust process to block unwanted traffic
signals.
Overview of wireless networks security
For any computer network security is a very important key factor and from last
few year security issues in a wireless system is increasing very fast (Al, Al, Shojafar, &
Shamshirband, 2017). It is defined as a step to improve the security of user private
information and it is also called a subset of computer security that provides protection
methods for wireless communication. Generally, security of the wireless network is
produced with the help of various computer and digital devices like routers, switched
and hubs (Díaz, Martín, & Rubio, 2016). It is estimated that if any user adopts security
plans for their networks then the hacker is not able to enter into personal servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORK SECURITY
4
Wireless intrusion prevention method and detection process also deliver protection of
networks with the help of altering the computer devices administrator in case of the
data breach.
Figure: Wireless network architecture
(Source: Díaz, Martín, & Rubio, 2016)
There are main two algorithms are used to ensure the security of wireless
systems, for example, WPA and WEP. Many attackers use complex flooding process by
which they design unauthentic servers and block computer systems of an organization
for which WIPS and WIDS are developed to enforce policies of wireless security
(Farooq, Waseem, Khairi, & Mazhar, 2015). Moreover, there are numbers of security
risks and threats associated with this technology due to which many users lost their
private account details. Hacking is also very easier and more accessible and anyone can
learn from the internet by which privacy of peripheral device is also reduced.
Technologies used in Wireless network security
There are numbers of technologies and processes are used in the field of wireless
networks which are described below:
Service Set Identifier
Access point
Wireless LANs
Ad Hoc networks
4
Wireless intrusion prevention method and detection process also deliver protection of
networks with the help of altering the computer devices administrator in case of the
data breach.
Figure: Wireless network architecture
(Source: Díaz, Martín, & Rubio, 2016)
There are main two algorithms are used to ensure the security of wireless
systems, for example, WPA and WEP. Many attackers use complex flooding process by
which they design unauthentic servers and block computer systems of an organization
for which WIPS and WIDS are developed to enforce policies of wireless security
(Farooq, Waseem, Khairi, & Mazhar, 2015). Moreover, there are numbers of security
risks and threats associated with this technology due to which many users lost their
private account details. Hacking is also very easier and more accessible and anyone can
learn from the internet by which privacy of peripheral device is also reduced.
Technologies used in Wireless network security
There are numbers of technologies and processes are used in the field of wireless
networks which are described below:
Service Set Identifier
Access point
Wireless LANs
Ad Hoc networks

WIRELESS NETWORK SECURITY
5
PDA (Personal digital assistants)
Open System Authentication
Wired Equivalent Privacy Protocol
Service Set Identifier
An SSID is defined as a configuration process which is used to reduce the
problem of conflict in wireless networks. The main benefit of this technology is that it
allows wireless users to communicate with access points of networks. If any consumer
does not use the appropriate configuration process then he is not able to communicate
with their access points. However, this process can be used as a single shared password
system between consumers and network.
Open system authentication
It is the default authorized network protocols for 802.11 standards. It uses
simple authentication process which contains identity and response of failure data.
When any network is designed than client use authentication step by which they can
improve the performance of their computer devices and networks. This type of step can
be used with wired equivalent privacy because it has the capability to improve the
security of the communication system (Hasrouny, Samhat, Bassil, & Laouiti, 2017).
Access point
Access point refers to a hardware system which provides a platform where users
can communicate with peripheral devices. Generally, it interconnects two or more
computing devices with the help of wired networks and generates a bridge for
communication between wired and wireless network.
Ad Hoc networks
The main objective of this system is to connect various remote devices, for
example, mobile phones, computer system, and other PDAs. This network shift topology
of wireless networks and it can maintain the process of configuration (Hu, & Qian,
2014). Master-slave system is used to make a communication medium between clients
and computer devices. The main advantage of this technology is that it has the
capability to support direct links between peripheral devices.
5
PDA (Personal digital assistants)
Open System Authentication
Wired Equivalent Privacy Protocol
Service Set Identifier
An SSID is defined as a configuration process which is used to reduce the
problem of conflict in wireless networks. The main benefit of this technology is that it
allows wireless users to communicate with access points of networks. If any consumer
does not use the appropriate configuration process then he is not able to communicate
with their access points. However, this process can be used as a single shared password
system between consumers and network.
Open system authentication
It is the default authorized network protocols for 802.11 standards. It uses
simple authentication process which contains identity and response of failure data.
When any network is designed than client use authentication step by which they can
improve the performance of their computer devices and networks. This type of step can
be used with wired equivalent privacy because it has the capability to improve the
security of the communication system (Hasrouny, Samhat, Bassil, & Laouiti, 2017).
Access point
Access point refers to a hardware system which provides a platform where users
can communicate with peripheral devices. Generally, it interconnects two or more
computing devices with the help of wired networks and generates a bridge for
communication between wired and wireless network.
Ad Hoc networks
The main objective of this system is to connect various remote devices, for
example, mobile phones, computer system, and other PDAs. This network shift topology
of wireless networks and it can maintain the process of configuration (Hu, & Qian,
2014). Master-slave system is used to make a communication medium between clients
and computer devices. The main advantage of this technology is that it has the
capability to support direct links between peripheral devices.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
WIRELESS NETWORK SECURITY
6
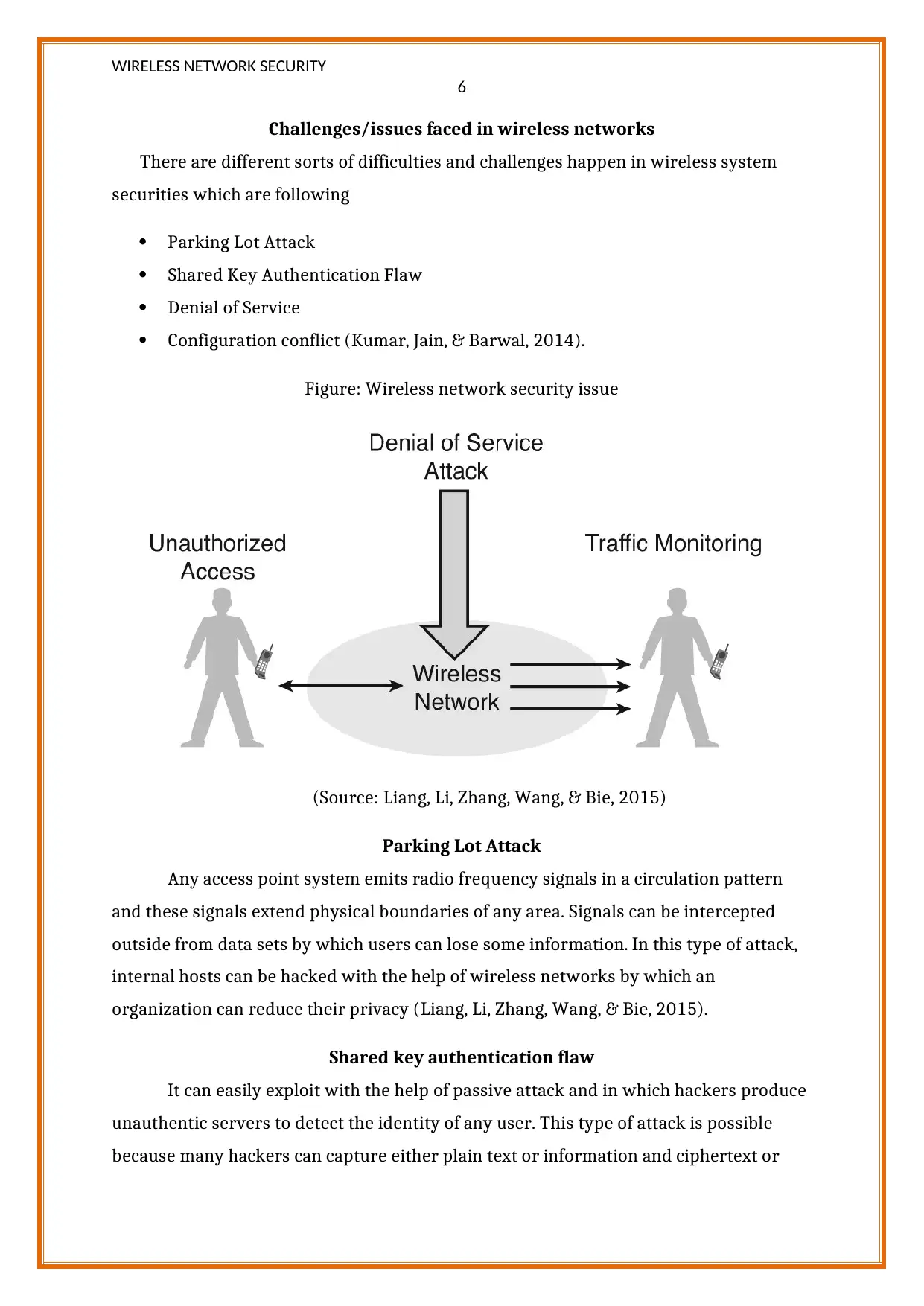
Challenges/issues faced in wireless networks
There are different sorts of difficulties and challenges happen in wireless system
securities which are following
Parking Lot Attack
Shared Key Authentication Flaw
Denial of Service
Configuration conflict (Kumar, Jain, & Barwal, 2014).
Figure: Wireless network security issue
(Source: Liang, Li, Zhang, Wang, & Bie, 2015)
Parking Lot Attack
Any access point system emits radio frequency signals in a circulation pattern
and these signals extend physical boundaries of any area. Signals can be intercepted
outside from data sets by which users can lose some information. In this type of attack,
internal hosts can be hacked with the help of wireless networks by which an
organization can reduce their privacy (Liang, Li, Zhang, Wang, & Bie, 2015).
Shared key authentication flaw
It can easily exploit with the help of passive attack and in which hackers produce
unauthentic servers to detect the identity of any user. This type of attack is possible
because many hackers can capture either plain text or information and ciphertext or
6
Challenges/issues faced in wireless networks
There are different sorts of difficulties and challenges happen in wireless system
securities which are following
Parking Lot Attack
Shared Key Authentication Flaw
Denial of Service
Configuration conflict (Kumar, Jain, & Barwal, 2014).
Figure: Wireless network security issue
(Source: Liang, Li, Zhang, Wang, & Bie, 2015)
Parking Lot Attack
Any access point system emits radio frequency signals in a circulation pattern
and these signals extend physical boundaries of any area. Signals can be intercepted
outside from data sets by which users can lose some information. In this type of attack,
internal hosts can be hacked with the help of wireless networks by which an
organization can reduce their privacy (Liang, Li, Zhang, Wang, & Bie, 2015).
Shared key authentication flaw
It can easily exploit with the help of passive attack and in which hackers produce
unauthentic servers to detect the identity of any user. This type of attack is possible
because many hackers can capture either plain text or information and ciphertext or
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
WIRELESS NETWORK SECURITY
7
encrypt signals (Mahmood, Javaid, & Razzaq, 2015). WEP utilize the RC4 process to
encrypt any data file and if any user clicks on unwanted links then they can lose their
privacy.
DOS attack
It refers to the denial of service which is a very common security threat to the
wireless network. The rate of DOS is growing very fast and hackers target a large
number of networks by which they can control access prints of computer devices. In
this type of security risk, hackers generate a large amount of traffic and botnet and
transfer to organization websites due to which users can suffer from data breach
problem.
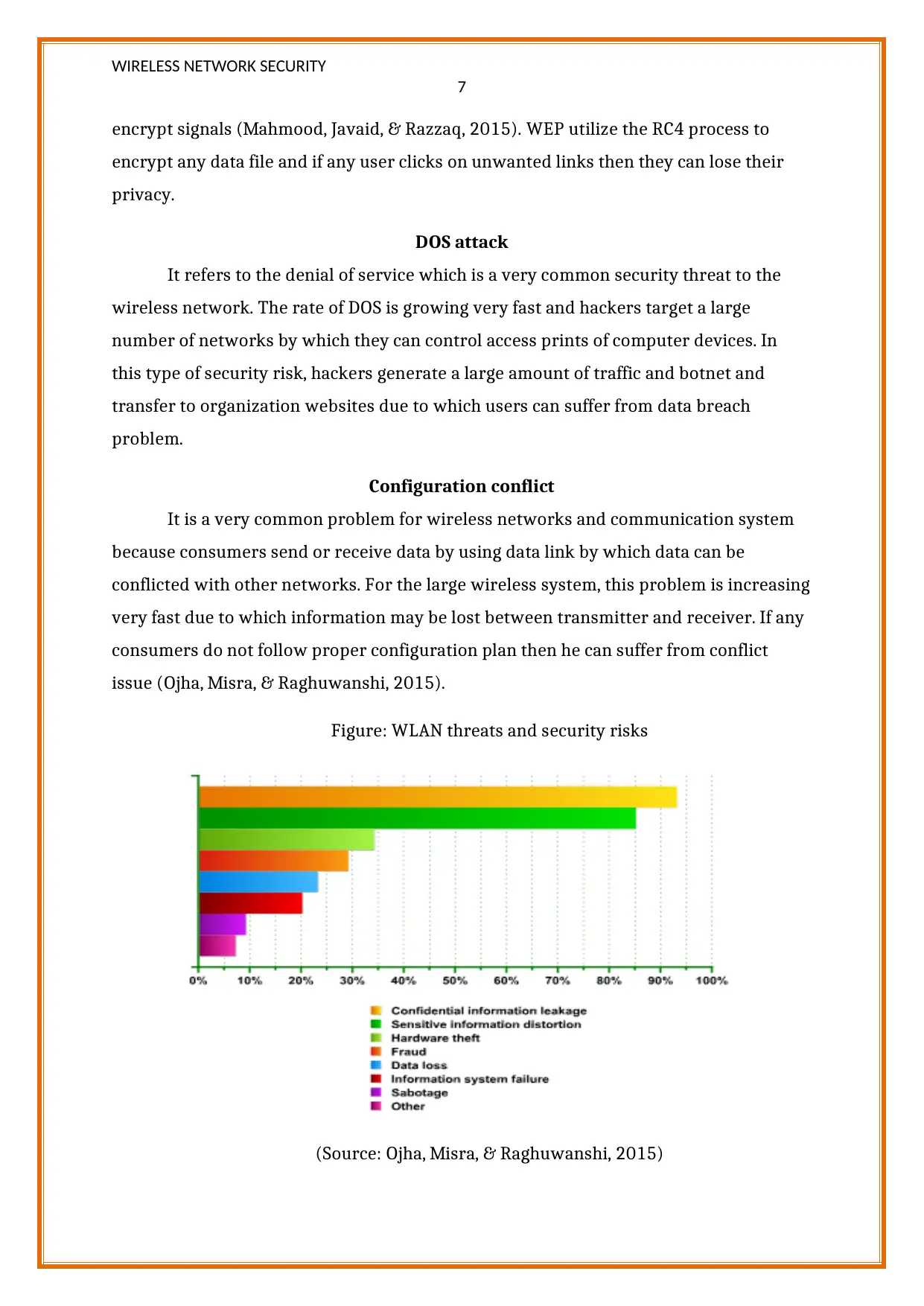
Configuration conflict
It is a very common problem for wireless networks and communication system
because consumers send or receive data by using data link by which data can be
conflicted with other networks. For the large wireless system, this problem is increasing
very fast due to which information may be lost between transmitter and receiver. If any
consumers do not follow proper configuration plan then he can suffer from conflict
issue (Ojha, Misra, & Raghuwanshi, 2015).
Figure: WLAN threats and security risks
(Source: Ojha, Misra, & Raghuwanshi, 2015)
7
encrypt signals (Mahmood, Javaid, & Razzaq, 2015). WEP utilize the RC4 process to
encrypt any data file and if any user clicks on unwanted links then they can lose their
privacy.
DOS attack
It refers to the denial of service which is a very common security threat to the
wireless network. The rate of DOS is growing very fast and hackers target a large
number of networks by which they can control access prints of computer devices. In
this type of security risk, hackers generate a large amount of traffic and botnet and
transfer to organization websites due to which users can suffer from data breach
problem.
Configuration conflict
It is a very common problem for wireless networks and communication system
because consumers send or receive data by using data link by which data can be
conflicted with other networks. For the large wireless system, this problem is increasing
very fast due to which information may be lost between transmitter and receiver. If any
consumers do not follow proper configuration plan then he can suffer from conflict
issue (Ojha, Misra, & Raghuwanshi, 2015).
Figure: WLAN threats and security risks
(Source: Ojha, Misra, & Raghuwanshi, 2015)

WIRELESS NETWORK SECURITY
8
(Literature Review) Gaps in the literature
Wireless technology is very modern innovation in the field of communication
because many users and organization use this system to interconnect two or more
digital devices (Qiu, Chen, Li, Qiao, & Fu, 2017). A number of writers identified security
risks and threats of wireless networks and they also addressed the issue of performance
and conflict. From last four years problem of data breach and denial of service, attack is
growing very fast because consumers use unauthorized websites and servers which are
developed by hackers (Sgora, Vergados, & Chatzimisios, 2016). There are two types of
process are used by attackers malware and botnet and they share fraud emails to the
organization by which they can control and monitor accounts of employees. Authors
have not addressed the issue of data breach and cyber-attacks due to that many
organizations are facing the problem of data leak (Yang, et al., 2015). According to my
opinion, we can adopt various security plans and policies for any corporation and
employees use their accounts into authentic servers by which we can secure our private
details. Users can adopt biometric technology because hackers can detect login ID and
password so we can use fingerprint and iris recognition system (Yang, et al., 2015).
Proposed Design
In this report, mixed research design will be used because it contains the
fundamental concept of both qualitative and quantitative research analysis. In this
research paper, qualitative research design can help to understand concept of wireless
networks in the field of security and quantitative data can help to gather the numeric or
statistical data about security of wireless networks.
Future scope
Information and technologies organization developed many wireless networks
which are very secure and more reliable for example, internet of thing, Zigbee, long-
term evaluation, and wireless local area networks. In future wireless technology will
improve overall speed and performance of their systems and they can use encryption
and cryptography and robust technology in their networks to improve the efficiency of
the communication system (Zeng, 2015). In the future, we will address the security
challenges faced by wireless networks and steps to improve the performance of the
communication system.
8
(Literature Review) Gaps in the literature
Wireless technology is very modern innovation in the field of communication
because many users and organization use this system to interconnect two or more
digital devices (Qiu, Chen, Li, Qiao, & Fu, 2017). A number of writers identified security
risks and threats of wireless networks and they also addressed the issue of performance
and conflict. From last four years problem of data breach and denial of service, attack is
growing very fast because consumers use unauthorized websites and servers which are
developed by hackers (Sgora, Vergados, & Chatzimisios, 2016). There are two types of
process are used by attackers malware and botnet and they share fraud emails to the
organization by which they can control and monitor accounts of employees. Authors
have not addressed the issue of data breach and cyber-attacks due to that many
organizations are facing the problem of data leak (Yang, et al., 2015). According to my
opinion, we can adopt various security plans and policies for any corporation and
employees use their accounts into authentic servers by which we can secure our private
details. Users can adopt biometric technology because hackers can detect login ID and
password so we can use fingerprint and iris recognition system (Yang, et al., 2015).
Proposed Design
In this report, mixed research design will be used because it contains the
fundamental concept of both qualitative and quantitative research analysis. In this
research paper, qualitative research design can help to understand concept of wireless
networks in the field of security and quantitative data can help to gather the numeric or
statistical data about security of wireless networks.
Future scope
Information and technologies organization developed many wireless networks
which are very secure and more reliable for example, internet of thing, Zigbee, long-
term evaluation, and wireless local area networks. In future wireless technology will
improve overall speed and performance of their systems and they can use encryption
and cryptography and robust technology in their networks to improve the efficiency of
the communication system (Zeng, 2015). In the future, we will address the security
challenges faced by wireless networks and steps to improve the performance of the
communication system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WIRELESS NETWORK SECURITY
9
Conclusion
Any remote system utilizes Ad Hoc and WLAN networks by which users can
share or receive data from one place to another. There are many advantages of wireless
networks for example, flexible, reliable, more efficient, and can be used for long-
distance communication. This report described various security issues of wireless
networks and overview of security of wireless technologies. There are many third party
sellers which provide low-quality equipment’s by which user can face data breach and
conflict issues. For which consumers can adopt efficient routers and host networks
because routers have the ability to maintain the overall performance of communication
systems. People should focus on security programmes and they can use robust and
cryptography technologies to block unwanted traffic signals and unauthentic servers.
9
Conclusion
Any remote system utilizes Ad Hoc and WLAN networks by which users can
share or receive data from one place to another. There are many advantages of wireless
networks for example, flexible, reliable, more efficient, and can be used for long-
distance communication. This report described various security issues of wireless
networks and overview of security of wireless technologies. There are many third party
sellers which provide low-quality equipment’s by which user can face data breach and
conflict issues. For which consumers can adopt efficient routers and host networks
because routers have the ability to maintain the overall performance of communication
systems. People should focus on security programmes and they can use robust and
cryptography technologies to block unwanted traffic signals and unauthentic servers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

WIRELESS NETWORK SECURITY
10
References
Al-Janabi, S., Al-Shourbaji, I., Shojafar, M., & Shamshirband, S. (2017). Survey of main
challenges (security and privacy) in wireless body area networks for healthcare
applications. Egyptian Informatics Journal, 18(2), 113-122.
Chen, M., Qian, Y., Mao, S., Tang, W., & Yang, X. (2016). Software-defined mobile
networks security. Mobile Networks and Applications, 21(5), 729-743.
Díaz, M., Martín, C., & Rubio, B. (2016). State-of-the-art, challenges, and open issues in
the integration of the Internet of things and cloud computing. Journal of Network
and Computer Applications, 67, 99-117.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis of the
security concerns of the internet of things (IoT). International Journal of
Computer Applications, 111(7), 14-20.
Hasrouny, H., Samhat, A. E., Bassil, C., & Laouiti, A. (2017). VANet security challenges
and solutions: A survey. Vehicular Communications, 7(2), 7-20.
Hu, R. Q., & Qian, Y. (2014). An energy efficient and spectrum efficient wireless
heterogeneous network framework for 5G systems. IEEE Communications
Magazine, 52(5), 94-101.
Kumar, V., Jain, A., & Barwal, P. N. (2014). Wireless sensor networks: security issues,
challenges, and solutions. International Journal of Information and Computation
Technology (IJICT), 4(8), 859-868.
Liang, W., Li, Z., Zhang, H., Wang, S., & Bie, R. (2015). Vehicular ad hoc networks:
architectures, research issues, methodologies, challenges, and
trends. International Journal of Distributed Sensor Networks, 11(8), 745303.
Mahmood, A., Javaid, N., & Razzaq, S. (2015). A review of wireless communications for
the smart grid. Renewable and sustainable energy reviews, 41, 248-260.
10
References
Al-Janabi, S., Al-Shourbaji, I., Shojafar, M., & Shamshirband, S. (2017). Survey of main
challenges (security and privacy) in wireless body area networks for healthcare
applications. Egyptian Informatics Journal, 18(2), 113-122.
Chen, M., Qian, Y., Mao, S., Tang, W., & Yang, X. (2016). Software-defined mobile
networks security. Mobile Networks and Applications, 21(5), 729-743.
Díaz, M., Martín, C., & Rubio, B. (2016). State-of-the-art, challenges, and open issues in
the integration of the Internet of things and cloud computing. Journal of Network
and Computer Applications, 67, 99-117.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis of the
security concerns of the internet of things (IoT). International Journal of
Computer Applications, 111(7), 14-20.
Hasrouny, H., Samhat, A. E., Bassil, C., & Laouiti, A. (2017). VANet security challenges
and solutions: A survey. Vehicular Communications, 7(2), 7-20.
Hu, R. Q., & Qian, Y. (2014). An energy efficient and spectrum efficient wireless
heterogeneous network framework for 5G systems. IEEE Communications
Magazine, 52(5), 94-101.
Kumar, V., Jain, A., & Barwal, P. N. (2014). Wireless sensor networks: security issues,
challenges, and solutions. International Journal of Information and Computation
Technology (IJICT), 4(8), 859-868.
Liang, W., Li, Z., Zhang, H., Wang, S., & Bie, R. (2015). Vehicular ad hoc networks:
architectures, research issues, methodologies, challenges, and
trends. International Journal of Distributed Sensor Networks, 11(8), 745303.
Mahmood, A., Javaid, N., & Razzaq, S. (2015). A review of wireless communications for
the smart grid. Renewable and sustainable energy reviews, 41, 248-260.

WIRELESS NETWORK SECURITY
11
Ojha, T., Misra, S., & Raghuwanshi, N. S. (2015). Wireless sensor networks for
agriculture: The state-of-the-art in practice and future challenges. Computers and
Electronics in Agriculture, 118, 66-84.
Qiu, T., Chen, N., Li, K., Qiao, D., & Fu, Z. (2017). Heterogeneous ad hoc networks:
Architectures, advances, and challenges. Ad Hoc Networks, 55, 143-152.
Sgora, A., Vergados, D. D., & Chatzimisios, P. (2016). A survey on security and privacy
issues in wireless mesh networks. Security and Communication Networks, 9(13),
1877-1889.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J., & Di Renzo, M. (2015). Safeguarding
5G wireless communication networks using physical layer security. IEEE
Communications Magazine, 53(4), 20-27.
Zeng, K. (2015). Physical layer key generation in wireless networks: challenges and
opportunities. IEEE Communications Magazine, 53(6), 33-39.
11
Ojha, T., Misra, S., & Raghuwanshi, N. S. (2015). Wireless sensor networks for
agriculture: The state-of-the-art in practice and future challenges. Computers and
Electronics in Agriculture, 118, 66-84.
Qiu, T., Chen, N., Li, K., Qiao, D., & Fu, Z. (2017). Heterogeneous ad hoc networks:
Architectures, advances, and challenges. Ad Hoc Networks, 55, 143-152.
Sgora, A., Vergados, D. D., & Chatzimisios, P. (2016). A survey on security and privacy
issues in wireless mesh networks. Security and Communication Networks, 9(13),
1877-1889.
Yang, N., Wang, L., Geraci, G., Elkashlan, M., Yuan, J., & Di Renzo, M. (2015). Safeguarding
5G wireless communication networks using physical layer security. IEEE
Communications Magazine, 53(4), 20-27.
Zeng, K. (2015). Physical layer key generation in wireless networks: challenges and
opportunities. IEEE Communications Magazine, 53(6), 33-39.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




