MITS5003 Wireless Networks and Communication Assignment
VerifiedAdded on 2022/12/18
|10
|1225
|57
Homework Assignment
AI Summary
This document presents a comprehensive solution to a Wireless Networks and Communication assignment, covering various aspects of the subject. It begins by addressing the role of IP in the TCP protocol and the functions of the network access layer. The solution then provides a three-level diagram illustrating communication between individuals using translators and a telephone network. Further, it delves into signal analysis, including calculations for amplitude, frequency, time period, and phase for different waveforms. The assignment also explores isotropic free space loss, the analysis of signals with multiple frequencies, and the application of the Nyquist theorem. Additionally, the document compares and contrasts packet switching and circuit switching and concludes with a calculation of tower heights based on given parameters. This resource is designed to aid students in understanding and solving complex problems related to wireless networks and communication.

Running head: WIRELESS NETWORKS AND COMMUNICATION
WIRELESS NETWORKS AND COMMUNICATION
Name of the Student
Name of the University
Author Note
WIRELESS NETWORKS AND COMMUNICATION
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRELESS NETWORKS AND COMMUNICATION
French prime
minister
Translator
Telephone
Chinese PM
Translator
Telephone
Telephone Network
Question 1:
IP in TCP protocol is considered for assigning address to the data packets so that the data
packets are sent to the required host of the network.
Network access layer is responsible for ensuring that data is sent to the exact address as
defined by the IP address of the data packets that is already described in this context.
Therefore, it is important to identify that IP layer is responsible for logical addressing while
network access layer is responsible for sending data packets according to the address
assigned to the data packets by the IP layer of TCP/IP protocol and this means that both of
these layers integrate different control information required for ensuring that the
communication through the network is effective and efficient as well.
Question 2:
The description of the three level diagram according to the requirement is provided in this
context:
WIRELESS NETWORKS AND COMMUNICATION
French prime
minister
Translator
Telephone
Chinese PM
Translator
Telephone
Telephone Network
Question 1:
IP in TCP protocol is considered for assigning address to the data packets so that the data
packets are sent to the required host of the network.
Network access layer is responsible for ensuring that data is sent to the exact address as
defined by the IP address of the data packets that is already described in this context.
Therefore, it is important to identify that IP layer is responsible for logical addressing while
network access layer is responsible for sending data packets according to the address
assigned to the data packets by the IP layer of TCP/IP protocol and this means that both of
these layers integrate different control information required for ensuring that the
communication through the network is effective and efficient as well.
Question 2:
The description of the three level diagram according to the requirement is provided in this
context:
2
WIRELESS NETWORKS AND COMMUNICATION
In order to ensure that both the prime minister communicate with each other, the translator in
each side converts the message in French or Chinese into English when respective prime
minister need to talk something to each other. For example, when the French prime minister
talks something in French, it is first converted into English by the translator of the French
prime minister and then that message is communicated through the telephone network. After
the message is revived by the Chinese communicator, it is then converted into Chinese
language so that it is interpreted by the Chinese prime minister. The same process is followed
when the Chinese prime minister needs to communicate something to the French prime
minister.
Question 3:
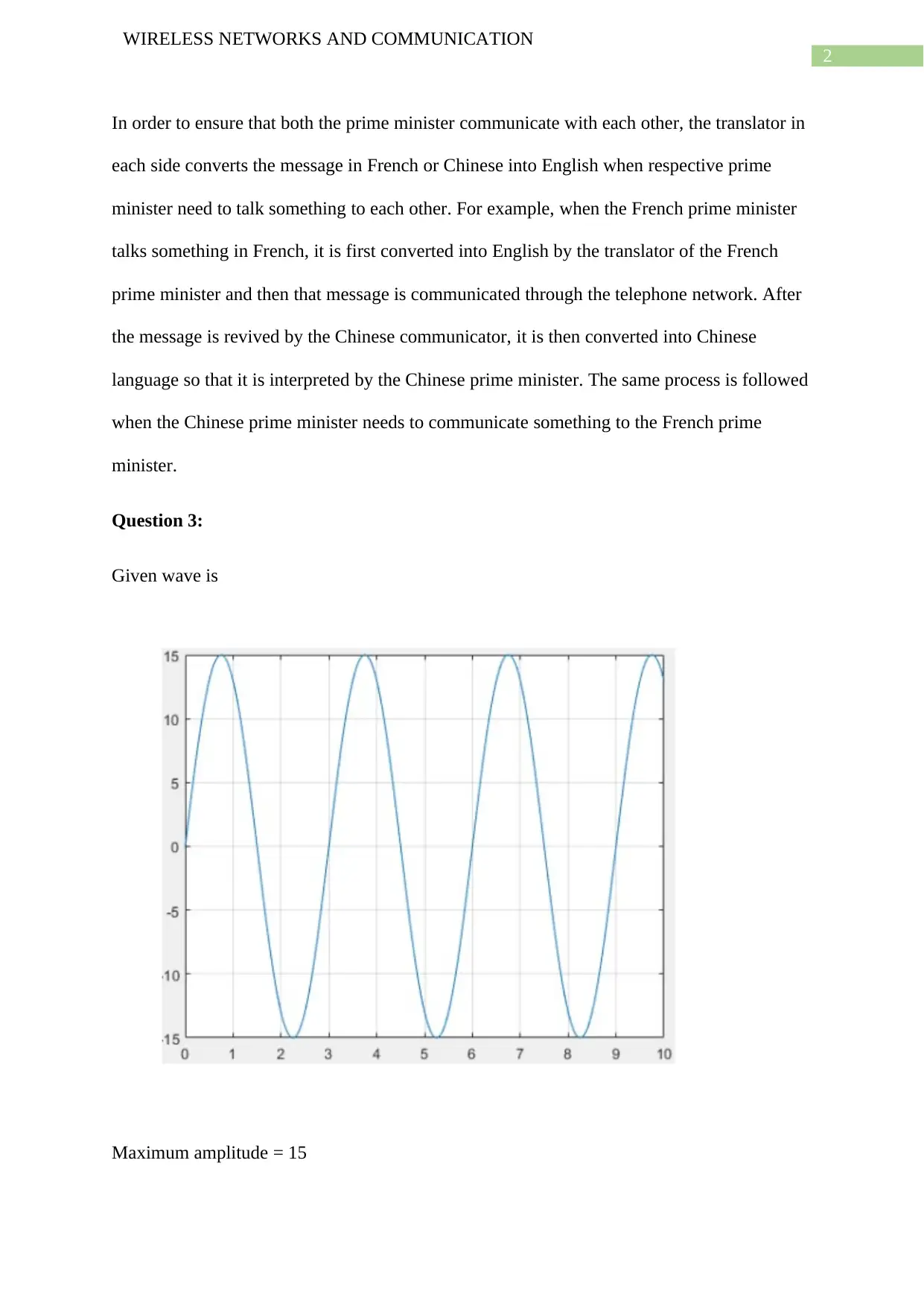
Given wave is
Maximum amplitude = 15
WIRELESS NETWORKS AND COMMUNICATION
In order to ensure that both the prime minister communicate with each other, the translator in
each side converts the message in French or Chinese into English when respective prime
minister need to talk something to each other. For example, when the French prime minister
talks something in French, it is first converted into English by the translator of the French
prime minister and then that message is communicated through the telephone network. After
the message is revived by the Chinese communicator, it is then converted into Chinese
language so that it is interpreted by the Chinese prime minister. The same process is followed
when the Chinese prime minister needs to communicate something to the French prime
minister.
Question 3:
Given wave is
Maximum amplitude = 15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
WIRELESS NETWORKS AND COMMUNICATION
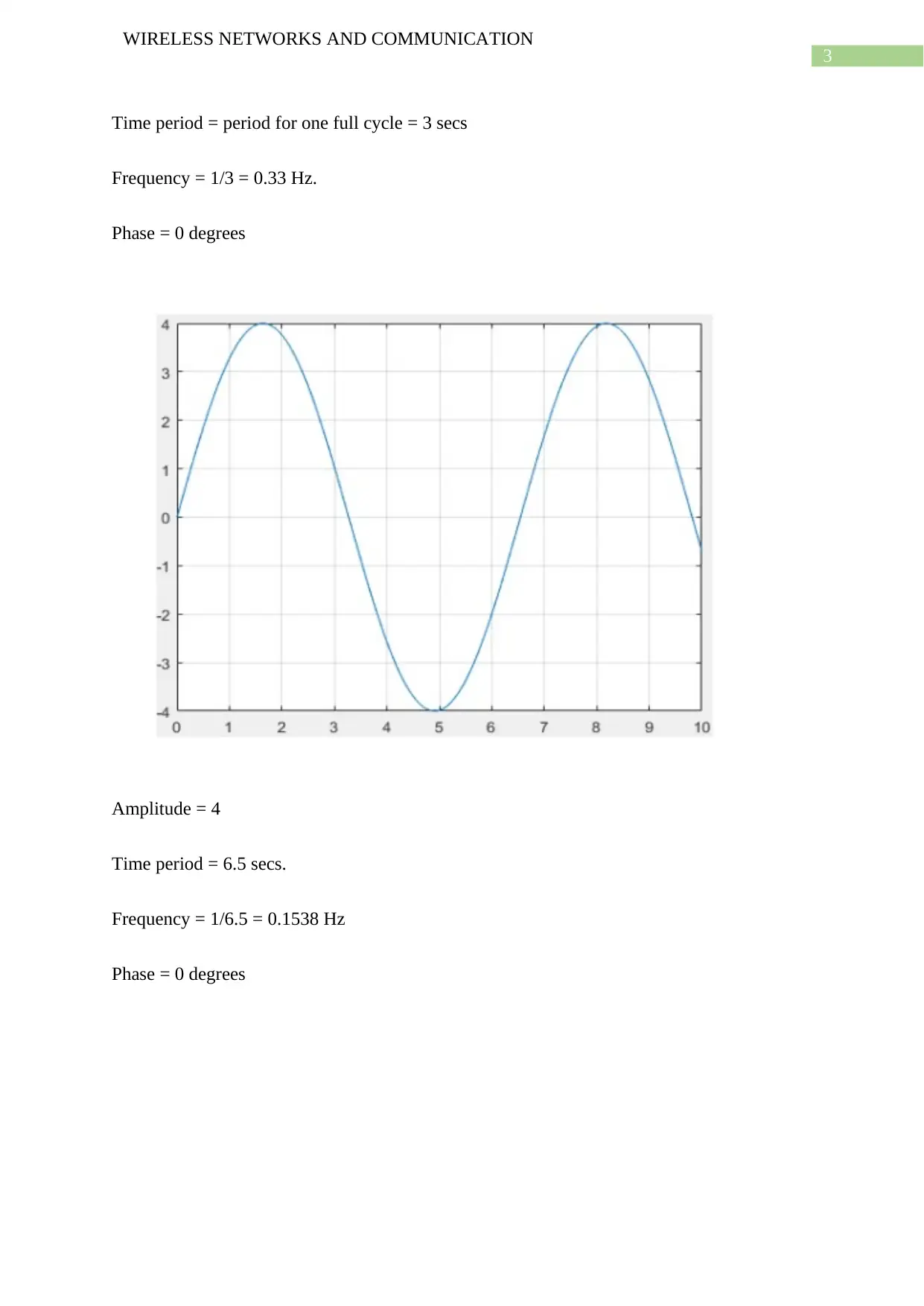
Time period = period for one full cycle = 3 secs
Frequency = 1/3 = 0.33 Hz.
Phase = 0 degrees
Amplitude = 4
Time period = 6.5 secs.
Frequency = 1/6.5 = 0.1538 Hz
Phase = 0 degrees
WIRELESS NETWORKS AND COMMUNICATION
Time period = period for one full cycle = 3 secs
Frequency = 1/3 = 0.33 Hz.
Phase = 0 degrees
Amplitude = 4
Time period = 6.5 secs.
Frequency = 1/6.5 = 0.1538 Hz
Phase = 0 degrees
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
WIRELESS NETWORKS AND COMMUNICATION
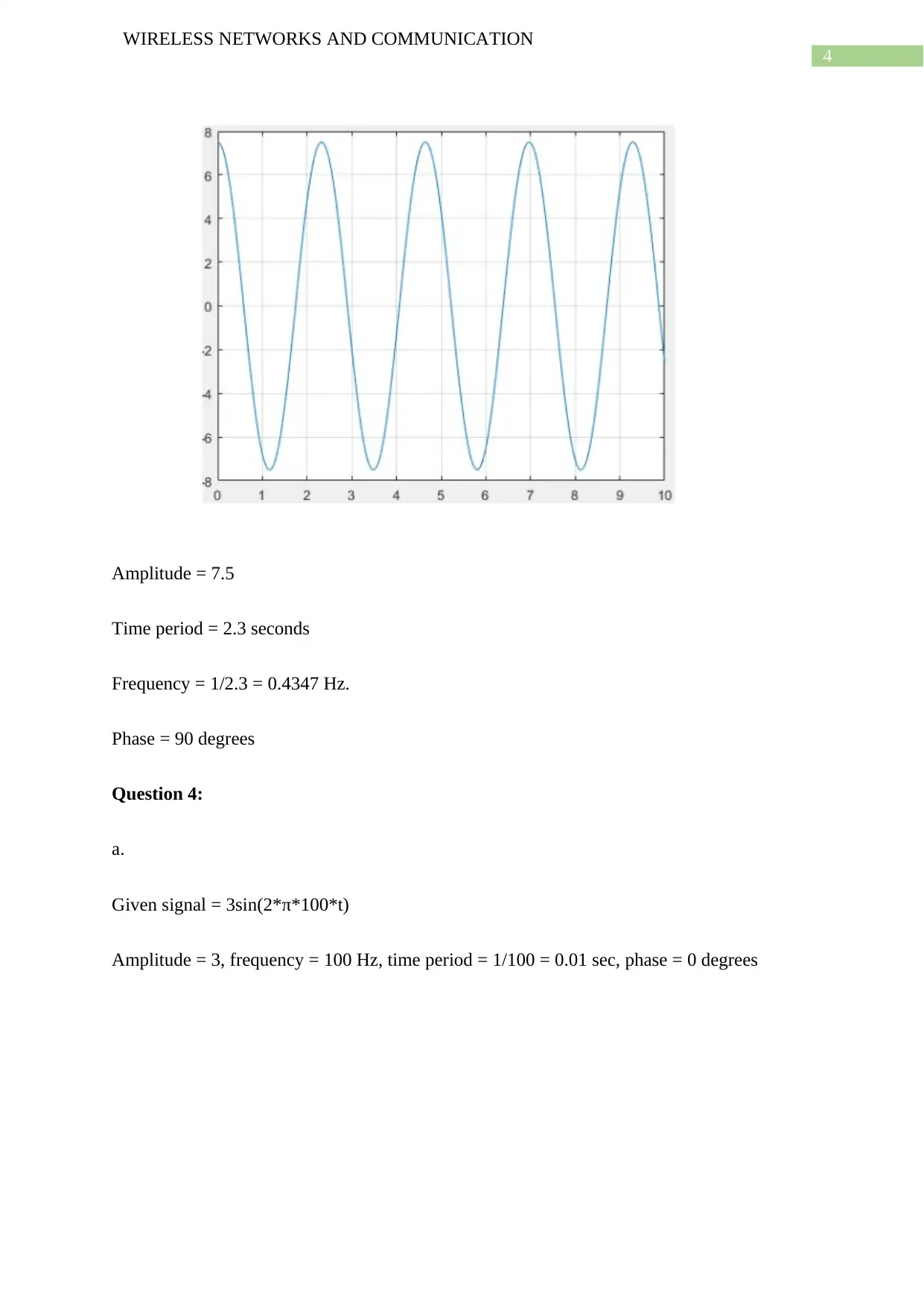
Amplitude = 7.5
Time period = 2.3 seconds
Frequency = 1/2.3 = 0.4347 Hz.
Phase = 90 degrees
Question 4:
a.
Given signal = 3sin(2*π*100*t)
Amplitude = 3, frequency = 100 Hz, time period = 1/100 = 0.01 sec, phase = 0 degrees
WIRELESS NETWORKS AND COMMUNICATION
Amplitude = 7.5
Time period = 2.3 seconds
Frequency = 1/2.3 = 0.4347 Hz.
Phase = 90 degrees
Question 4:
a.
Given signal = 3sin(2*π*100*t)
Amplitude = 3, frequency = 100 Hz, time period = 1/100 = 0.01 sec, phase = 0 degrees
5
WIRELESS NETWORKS AND COMMUNICATION
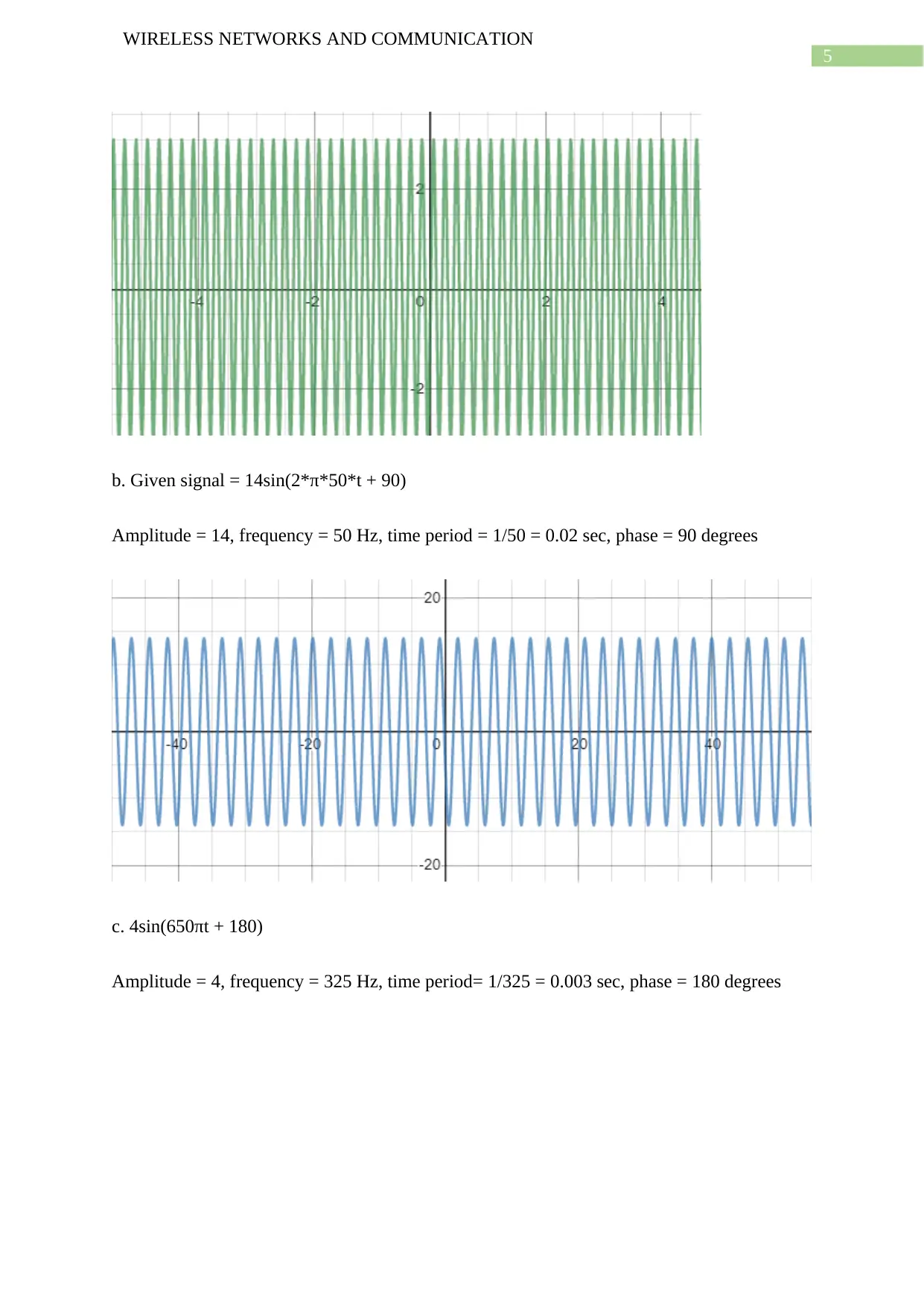
b. Given signal = 14sin(2*π*50*t + 90)
Amplitude = 14, frequency = 50 Hz, time period = 1/50 = 0.02 sec, phase = 90 degrees
c. 4sin(650πt + 180)
Amplitude = 4, frequency = 325 Hz, time period= 1/325 = 0.003 sec, phase = 180 degrees
WIRELESS NETWORKS AND COMMUNICATION
b. Given signal = 14sin(2*π*50*t + 90)
Amplitude = 14, frequency = 50 Hz, time period = 1/50 = 0.02 sec, phase = 90 degrees
c. 4sin(650πt + 180)
Amplitude = 4, frequency = 325 Hz, time period= 1/325 = 0.003 sec, phase = 180 degrees
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
WIRELESS NETWORKS AND COMMUNICATION
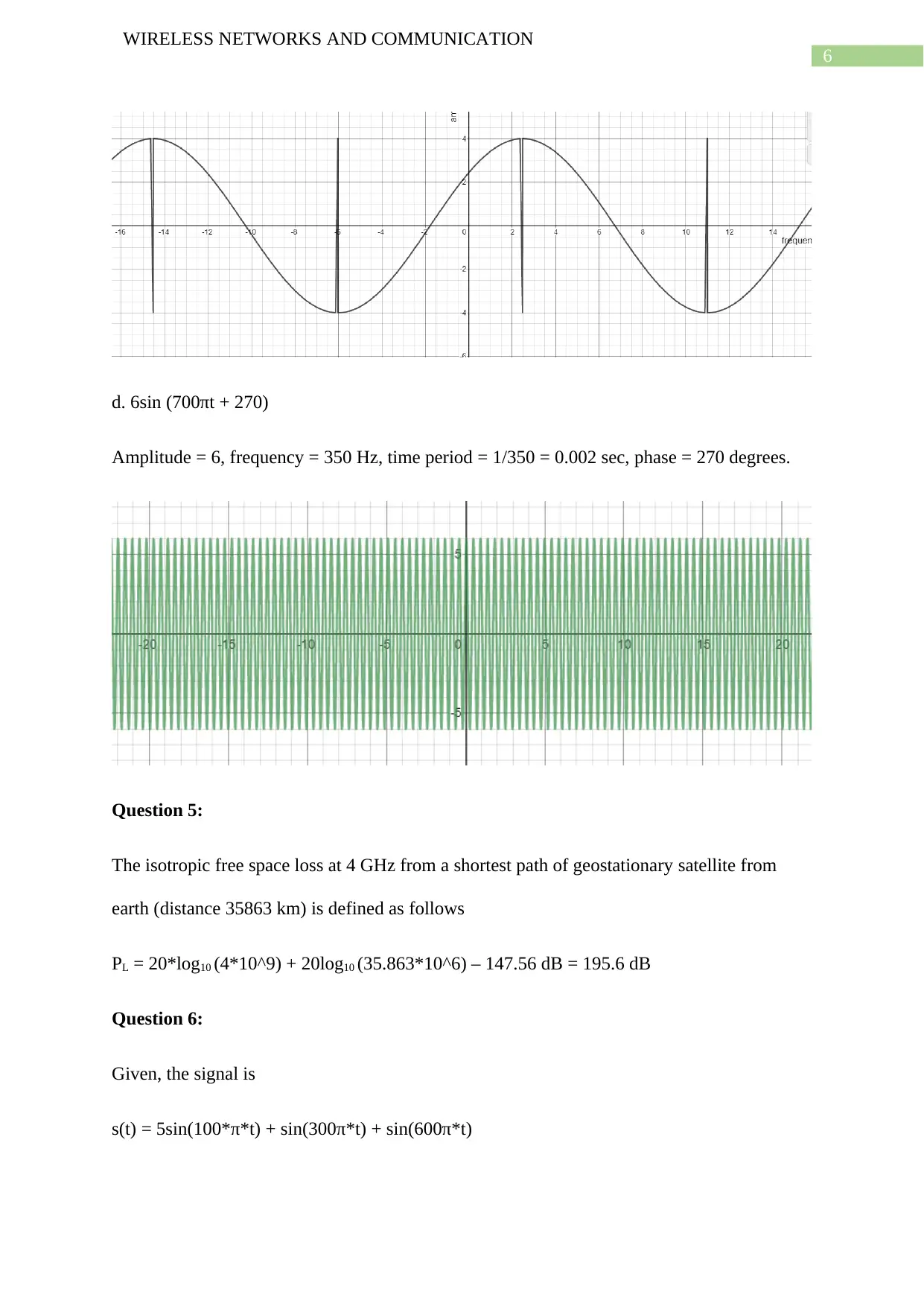
d. 6sin (700πt + 270)
Amplitude = 6, frequency = 350 Hz, time period = 1/350 = 0.002 sec, phase = 270 degrees.
Question 5:
The isotropic free space loss at 4 GHz from a shortest path of geostationary satellite from
earth (distance 35863 km) is defined as follows
PL = 20*log10 (4*10^9) + 20log10 (35.863*10^6) – 147.56 dB = 195.6 dB
Question 6:
Given, the signal is
s(t) = 5sin(100*π*t) + sin(300π*t) + sin(600π*t)
WIRELESS NETWORKS AND COMMUNICATION
d. 6sin (700πt + 270)
Amplitude = 6, frequency = 350 Hz, time period = 1/350 = 0.002 sec, phase = 270 degrees.
Question 5:
The isotropic free space loss at 4 GHz from a shortest path of geostationary satellite from
earth (distance 35863 km) is defined as follows
PL = 20*log10 (4*10^9) + 20log10 (35.863*10^6) – 147.56 dB = 195.6 dB
Question 6:
Given, the signal is
s(t) = 5sin(100*π*t) + sin(300π*t) + sin(600π*t)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
WIRELESS NETWORKS AND COMMUNICATION
s(t) therefore has three frequencies that are 100 Hz, 300 Hz and 600Hz respectively.
If f0 refers to the fundamental frequency of s(t), then 100 = n1*f0 and 300 = n2*f0 and 600 =
n3*f0
Hence, GCD(100,300, 600) = 100 Hz refers to the fundamental frequency of s(t).
The bandwidth refers to the difference that is defined between highest and lowest frequency =
600 – 100 = 500 Hz.
Now, the capacity of channel is given by
C = 2*B*log2M
Where, B = bandwidth, 2B = highest signal rate, M = number of levels.
Hence, M= 2 => C = 2*B = 2*500 = 1000 Hz.
M = 4 => C = 2*500*2 = 2000 Hz.
M= 8 => C = 2*500*3 = 3000 Hz.
Question 7:
According to the nyquist theorem, it is possible to increase channel capacity without any
requirement of increasing bandwidth and it only requires to increase the level of modulation
of the signal.
The main disadvantage of this approach is that due to increase in modulation level, it is not
easy for the receiver to ensure effective interpretation and if the level is significantly
increased, then it is not possible to ensure accuracy of bit interpretation by the receiver.
Question 8:
WIRELESS NETWORKS AND COMMUNICATION
s(t) therefore has three frequencies that are 100 Hz, 300 Hz and 600Hz respectively.
If f0 refers to the fundamental frequency of s(t), then 100 = n1*f0 and 300 = n2*f0 and 600 =
n3*f0
Hence, GCD(100,300, 600) = 100 Hz refers to the fundamental frequency of s(t).
The bandwidth refers to the difference that is defined between highest and lowest frequency =
600 – 100 = 500 Hz.
Now, the capacity of channel is given by
C = 2*B*log2M
Where, B = bandwidth, 2B = highest signal rate, M = number of levels.
Hence, M= 2 => C = 2*B = 2*500 = 1000 Hz.
M = 4 => C = 2*500*2 = 2000 Hz.
M= 8 => C = 2*500*3 = 3000 Hz.
Question 7:
According to the nyquist theorem, it is possible to increase channel capacity without any
requirement of increasing bandwidth and it only requires to increase the level of modulation
of the signal.
The main disadvantage of this approach is that due to increase in modulation level, it is not
easy for the receiver to ensure effective interpretation and if the level is significantly
increased, then it is not possible to ensure accuracy of bit interpretation by the receiver.
Question 8:

8
WIRELESS NETWORKS AND COMMUNICATION
Packet switching refers to the process of combining data into different packets with different
length and then the packets are send over the network for communication.
Circuit switching refers to the process of implementing dedicated communication networks
between two specific network nodes in the telecommunication network.
Packet switching is efficient compared to the circuit switching because in circuit switching
when a dedicated communication network is established between two networks nodes, no
other nodes are allowed to communicate through that communication network. Therefore,
there is loss of bandwidth in circuit switching. However, in packet switching there is no such
limitation and any host is allowed to communicate with other host in the network.
Question 9:
d = √2 rh+ h2 (every term is in meters)
r = radius of earth = 6371000 m.
d = √2 rh [ h2 is negligible compared to 2rh]
If it is considered that the two towers is at a height of h1 and h2 and their distances to the
horizon is d1 and d2 respectively.
Then, d1 + d2 = √2 rh1 + √ 2 rh2
d = √ 2 rh1 + √2 rh2
It is provided that the distance between them is d = 60 km = 60*10^3 = 60000 m.
It is provided that, h1=4h2
Hence, 60000 = √2 r∗4∗h 2 + √2 rh2 => √h 2 (2√ 2 √ r +√2 r) = 60000
h2 = (6 0000 /((2 √ 2 √ 6371000+√ (2∗6371000))))2= 31.392 m.
WIRELESS NETWORKS AND COMMUNICATION
Packet switching refers to the process of combining data into different packets with different
length and then the packets are send over the network for communication.
Circuit switching refers to the process of implementing dedicated communication networks
between two specific network nodes in the telecommunication network.
Packet switching is efficient compared to the circuit switching because in circuit switching
when a dedicated communication network is established between two networks nodes, no
other nodes are allowed to communicate through that communication network. Therefore,
there is loss of bandwidth in circuit switching. However, in packet switching there is no such
limitation and any host is allowed to communicate with other host in the network.
Question 9:
d = √2 rh+ h2 (every term is in meters)
r = radius of earth = 6371000 m.
d = √2 rh [ h2 is negligible compared to 2rh]
If it is considered that the two towers is at a height of h1 and h2 and their distances to the
horizon is d1 and d2 respectively.
Then, d1 + d2 = √2 rh1 + √ 2 rh2
d = √ 2 rh1 + √2 rh2
It is provided that the distance between them is d = 60 km = 60*10^3 = 60000 m.
It is provided that, h1=4h2
Hence, 60000 = √2 r∗4∗h 2 + √2 rh2 => √h 2 (2√ 2 √ r +√2 r) = 60000
h2 = (6 0000 /((2 √ 2 √ 6371000+√ (2∗6371000))))2= 31.392 m.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
WIRELESS NETWORKS AND COMMUNICATION
h1 = 2*h2 = 31.392*4 = 125.568 m.
Therefore, the approximate heights of the tower needs to be 31.392 meters and 125.568
meters respectively.
WIRELESS NETWORKS AND COMMUNICATION
h1 = 2*h2 = 31.392*4 = 125.568 m.
Therefore, the approximate heights of the tower needs to be 31.392 meters and 125.568
meters respectively.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



