Wireless Networks Assignment
12 Pages2732 Words95 Views
Added on 2020-03-16
Wireless Networks Assignment
Added on 2020-03-16
ShareRelated Documents
Running head: WIRELESS NETWORKSAssignment[Student Name Here][Institution’s Name Here][Professor’s Name Here][Date Here]

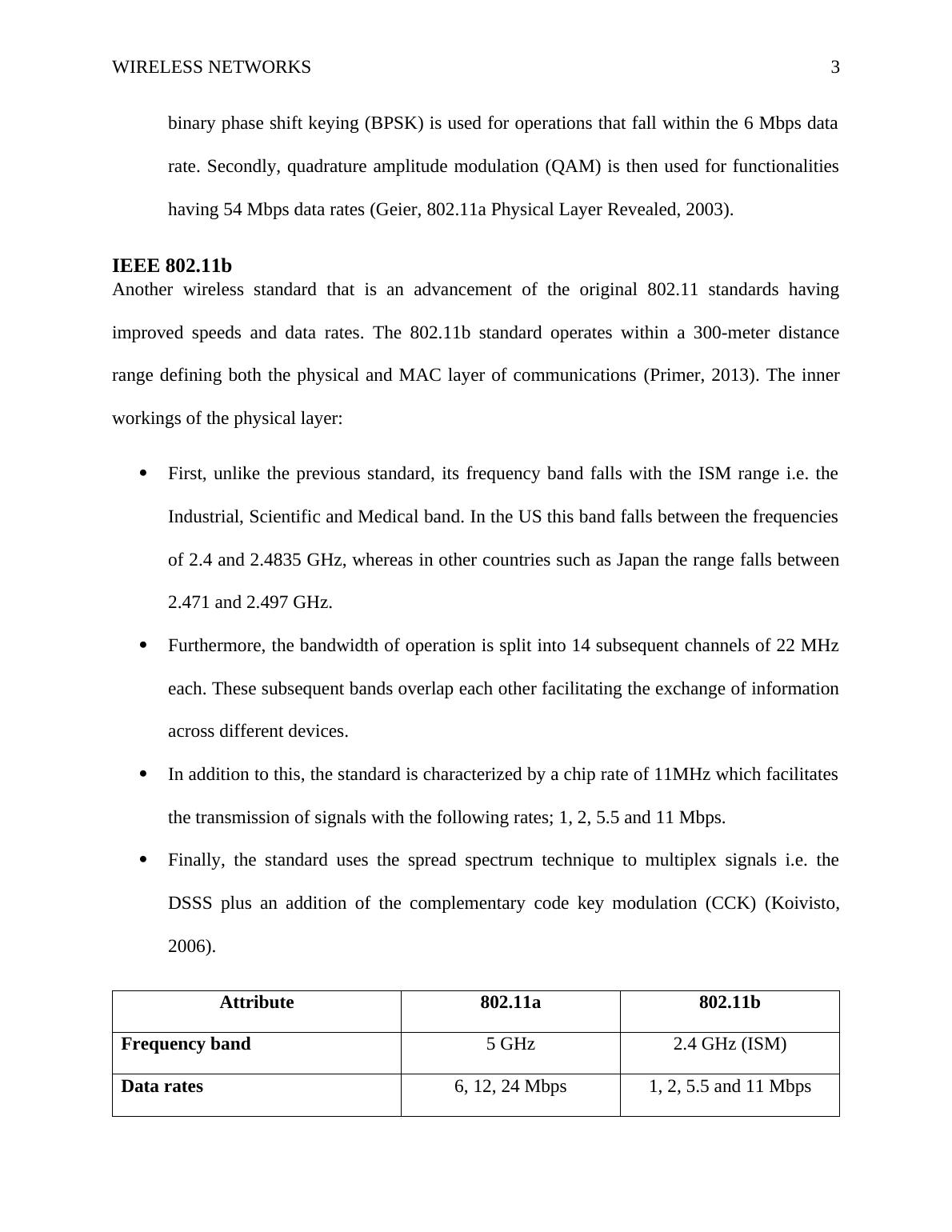
WIRELESS NETWORKS2Question 1The inner workings of the physical layer of the standards IEEE 802.11a and 802.11bThe physical layer is the lowest layer of the OSI communication model and it majorly isinvolved with the transmission of data across devices having different specification andoperation parameters. In essence, it supports the transmission of signals across electrical andmechanical systems offering a means to transport the 802.11 frame in this instance[ CITATIONPea17 \l 1033 ].IEEE 802.11aThis standard offers a competitive alternative to wired communication where data is transferredacross the electromagnetic spectrum. Now, as a wireless technology, the standard ischaracterized by the OFDM multiplexing technique that increases the bandwidth of transmission.In essence, OFDM (Orthogonal frequency division multiplexing) facilitates the diversification ofthe communication channel by splitting it based on the operational frequency[ CITATION RFw17 \l1033 ]. Nevertheless, its inner workings of the physical layer are as shown below:First, the layer operates with a 54 Mbps data rate that is supported by a 5 GHz frequencyband.This operational band is then usually diversified by the OFDM technique which splits thetransmission channel (radio spectrum) into 48 different subsections. These sections arethen spread across the wider channel width of 20 MHzNow, following this separation, several data rates are offered to the users including; 6, 12and 24 Mbps.Moreover, due to the variations in operational speeds, the standard applies other extendedmodulation techniques which supplement the original multiple access method. First, the

WIRELESS NETWORKS3binary phase shift keying (BPSK) is used for operations that fall within the 6 Mbps datarate. Secondly, quadrature amplitude modulation (QAM) is then used for functionalitieshaving 54 Mbps data rates[ CITATION Gei031 \l 1033 ].IEEE 802.11bAnother wireless standard that is an advancement of the original 802.11 standards havingimproved speeds and data rates. The 802.11b standard operates within a 300-meter distancerange defining both the physical and MAC layer of communications[ CITATION Pri13 \l 1033 ]. Theinner workings of the physical layer:First, unlike the previous standard, its frequency band falls with the ISM range i.e. theIndustrial, Scientific and Medical band. In the US this band falls between the frequenciesof 2.4 and 2.4835 GHz, whereas in other countries such as Japan the range falls between2.471 and 2.497 GHz.Furthermore, the bandwidth of operation is split into 14 subsequent channels of 22 MHzeach. These subsequent bands overlap each other facilitating the exchange of informationacross different devices.In addition to this, the standard is characterized by a chip rate of 11MHz which facilitatesthe transmission of signals with the following rates; 1, 2, 5.5 and 11 Mbps.Finally, the standard uses the spread spectrum technique to multiplex signals i.e. theDSSS plus an addition of the complementary code key modulation (CCK)[ CITATIONKoi06 \l 1033 ].Attribute802.11a802.11bFrequency band 5 GHz2.4 GHz (ISM)Data rates 6, 12, 24 Mbps1, 2, 5.5 and 11 MbpsMultiplexing technique OFDMDSSSModulation technique BPSK and QAMCCK
WIRELESS NETWORKS4Question 2a. 802.11i authenticationIn general, the 802.11 standard is a specification for implementing wireless networks (WLANs)that defines both the media access control (MAC) and the physical layer. The original standardoperated with a 900 MHz frequency band that extended to cover up to 60 GHz range. Moreover,the 802.11 standards used basic authentication and encryption techniques more so the WPA(WiFi protection access) and the WEP (wired equivalent privacy)[ CITATION Cha05 \l 1033 ].These standard were both weak and were easily cracked which led to the development of the802.11i standard that operates with higher security standards including the application of theWPA2, which above its better authentication structure is supported by AES (advancedencryption standard). Nevertheless, during the authentication of devices across networks (clients to servers) a robustand resilient procedure is followed through the application of a four-way handshake. Thishandshake operates with a group keying systems that involves three elements; the supplicant(client), the authentication server and the general authenticators (i.e. the relaying party)[ CITATIONLat12 \l 1033 ]. Furthermore, the extensible authentication protocol (EAP) is usually the definingprotocol for the 4-way handshake as outlined below (The process):First, the client sends a notification to the server in the of an EAP message.The access port then sends an EAP request to the authenticators in an attempt to relaycommunications.

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Inner Workings of the Physical Layer of IEEElg...
|11
|2500
|82
Wireless Digital Communications Assignmentlg...
|9
|1877
|266
Outlines a Wireless Local Area Networklg...
|9
|2033
|187
Wireless Connectivity- Assignmentlg...
|9
|2154
|31
Networking Assignment | Wireless Sensor Networklg...
|13
|2886
|64
The Operational Range of Frequencylg...
|8
|1886
|54
