Wireless Networks: Overview, Comparison, Evaluation, and Analysis
VerifiedAdded on 2019/09/30
|11
|4299
|214
Report
AI Summary
This report provides a comprehensive overview of wireless networks, encompassing various types such as WLAN, WPAN, WWAN, and WMAN, along with cellular network technologies. It delves into the different protocols, including GSM, GPRS, CDMA, Wi-Fi, and WiMAX, comparing their features and applications. The report explores recent trends like Li-Fi, security enhancements, and the use of LANs for rural broadband. It further discusses physical layer strategies such as spread spectrum and OFDM, and access techniques including TDMA, FDMA, CDMA, and ALOHA. The report evaluates network performance based on parameters like throughput, media access delay, and network load, providing a detailed comparison of different wireless protocols based on IEEE standards. This report also includes comparisons of WLAN, WPAN, WWAN, and WMAN on the basis of coverage and applications, and on the basis of different parameters including bit error rate and packet loss rate. The evaluation section analyzes the performance of 802.11b, 802.11n, and 802.11e networks, providing valuable insights into the practical aspects of wireless network implementation and performance.

Wireless Networks: Overview, Comparison and Evaluation
Authors Name/s per 1st Affiliation (Author)
line 1 (of Affiliation): dept. name of organization
line 2-name of organization, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Authors Name/s per 2nd Affiliation (Author)
line 1 (of Affiliation): dept. name of organization
line 2-name of organization, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Abstract— A cluster of two or more computer
systems when connected with each other, forms a
network. Network types include LAN, WAN,
CAN, MAN and HAN. LAN (Local Area
Network) is where geographically, computer
systems are placed very close to each other, most
probably in a same building. WANs (Wide Area
Network) are computers connected with
telephone lines or radio waves. CANs (Campus
Area Network) are limited confined to one area
such as a military camp or a campus. MANs
(Metropolitan Area Network) are network for a
town or city. HANs (Home Area Network) are
small home network with users’ personal devices
connected to each other.
I. WIRELESS NETWORK OVERVIEW
In communications sector, wireless
communication is the widely increasing technology
with great future imaginations. It has gained focus of
media and mass imagination. Moreover, WANs
have taken place of all the wired networks in offices
and even homes and campuses. Many new
innovations are been made to ease human life by
applying wireless communication in factories and
homes. These innovations include automated
highways and smart home solutions.
Following are the types of wireless network
based on its speed of transferring data and their
ranges.
1. Wireless PAN –
These are Wireless Personal Area Networks with
small network within the person’s reach usually an
infrared light. WPAN lets a Bluetooth
communication radio to connect to the laptop via a
headphone.
2. Wireless LAN –
Wireless Local Area Network is interconnection
of network devices that provide a wide internet
connection by making use of access point. Spread-
spectrum aka OFDM technologies let clients to
access and move within the range of coverage area
while they are connected to the network. It holds 10
Mbps Ethernet speed and 1 Gbps Gigabit Ethernet
speed. WLANs can connect hundreds or even one
thousand users.
3. Wireless MAN
Many WLANs connected to each other forms a
WMAN network. The different WLANs are
required to geographically close to each other
usually just few miles away from each other. The
devices in WMAN connect and communicate in
such way as if they are placed in same LAN. This is
made possible by using high speed and high range
routers, switches and links like fiber optic cables.
The most popular WMAN network is WiMAX.
4. Wireless WAN
WWAN usually connects large outdoor areas. It
is used in interconnecting different branches of the
business widely away from each other. The speed
usually depends on the connection cost that
increases due to increase in distance. The most
prominent example of WWAN is internet.
II. CELLULAR NETWORK OVERVIEW
Cellular network popularly known as mobile
network is the widely used communication network
where last link is wireless. The network is spread
Authors Name/s per 1st Affiliation (Author)
line 1 (of Affiliation): dept. name of organization
line 2-name of organization, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Authors Name/s per 2nd Affiliation (Author)
line 1 (of Affiliation): dept. name of organization
line 2-name of organization, acronyms acceptable
line 3-City, Country
line 4-e-mail address if desired
Abstract— A cluster of two or more computer
systems when connected with each other, forms a
network. Network types include LAN, WAN,
CAN, MAN and HAN. LAN (Local Area
Network) is where geographically, computer
systems are placed very close to each other, most
probably in a same building. WANs (Wide Area
Network) are computers connected with
telephone lines or radio waves. CANs (Campus
Area Network) are limited confined to one area
such as a military camp or a campus. MANs
(Metropolitan Area Network) are network for a
town or city. HANs (Home Area Network) are
small home network with users’ personal devices
connected to each other.
I. WIRELESS NETWORK OVERVIEW
In communications sector, wireless
communication is the widely increasing technology
with great future imaginations. It has gained focus of
media and mass imagination. Moreover, WANs
have taken place of all the wired networks in offices
and even homes and campuses. Many new
innovations are been made to ease human life by
applying wireless communication in factories and
homes. These innovations include automated
highways and smart home solutions.
Following are the types of wireless network
based on its speed of transferring data and their
ranges.
1. Wireless PAN –
These are Wireless Personal Area Networks with
small network within the person’s reach usually an
infrared light. WPAN lets a Bluetooth
communication radio to connect to the laptop via a
headphone.
2. Wireless LAN –
Wireless Local Area Network is interconnection
of network devices that provide a wide internet
connection by making use of access point. Spread-
spectrum aka OFDM technologies let clients to
access and move within the range of coverage area
while they are connected to the network. It holds 10
Mbps Ethernet speed and 1 Gbps Gigabit Ethernet
speed. WLANs can connect hundreds or even one
thousand users.
3. Wireless MAN
Many WLANs connected to each other forms a
WMAN network. The different WLANs are
required to geographically close to each other
usually just few miles away from each other. The
devices in WMAN connect and communicate in
such way as if they are placed in same LAN. This is
made possible by using high speed and high range
routers, switches and links like fiber optic cables.
The most popular WMAN network is WiMAX.
4. Wireless WAN
WWAN usually connects large outdoor areas. It
is used in interconnecting different branches of the
business widely away from each other. The speed
usually depends on the connection cost that
increases due to increase in distance. The most
prominent example of WWAN is internet.
II. CELLULAR NETWORK OVERVIEW
Cellular network popularly known as mobile
network is the widely used communication network
where last link is wireless. The network is spread
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

over lands (cells), each containing a transceiver at
fixed location to manage the network on that cell
and base stations. The base stations are used for
voice and data transfer in cellular network. To avoid
interference, a cell uses different frequencies than
their neighboring cells which ensure quality of
service on that cell. In last decade, mobile network
has gained more popularity due to ease of
communication. Now cellular network users have
increased to 2 billion in number.
Cellular network Types
A. Global System for Mobile Communications
GSM delivers data services within the network. It
also offers voice service through digital network.
B. General Packet Radio Service
GPRS outspreads the GSM network by allowing
innovative data services. The transmission of data is
faster than GSM which is upto 54 kbps.
C. Code Division Multiple Access
Qualcomm presented the CDMA technology. It is
expensive to implement as compared to GSM and
GPRS. Its processor is slow than that of GSM /
GPRS. It delivers 300 kbps of speed.
D. Mobitex (Two-way packet-switch network)
Mobitex was Originally designed for covering
metropolitan areas. BlackBerry 95x and 85x uses
Mobitex. The Radio uses less power which results in
long battery lives for several long weeks.
E. EDGE (Enhanced Data for Global Evolution)
EDGE is extended version to the GSM / GPRS
networks. It is 3x faster than GPRS network. It
offers download speed of 100-130 kbps.
III. RECENT TRENDS IN WIRELESS
NETWROKING
A. Li-Fi
Li-Fi uses light to carry information rather than
radio frequency. It is believed that light is capable
of holding more information than RF since it has
comparatively higher frequency and bandwidth. The
belief has been portrayed since from decades but it
has never brought into practice. Data rates are high
in Li-Fi, but there comes a drawback that the data
can be send to only that place where light can go.
Hence it cannot pass through walls but through
windows.
B. Better security
The wireless communication has made human life
much easier than expectations. But with good there
always comes a little bad. In wireless
communication, it is security. RF usually is not
limited to walls which make intruders to easily hack
the network through any seeped radio frequency. As
the enormous growth in wireless communication,
security layers are needed to build.
C. Rapid growth in medical monitoring
applications
The medical monitoring system is most widely used
application of wireless communication. Initially
unsuitable sensors and network devices was the
foremost reason for suffering of such applications.
But with high speed and range devices, medical
applications have been grown in use.
D. Use of LANs for rural broadband coverage
The rural parts were not included in internet
coverage. But with use of new technologies and
innovations it has become possible to provide
internet coverage to rural areas.
E. Wireless Peripherals
With everything wireless, there comes a wireless
mouse which enabled the user to connect a
computer in wireless link with mouse. Also one
more trend has been emerged, the wireless power.
When laptops discharges the user need to plug in
wire to charge it up, the researchers are now finding
ways to supply power wirelessly to the devices to
ease the physical connection.
fixed location to manage the network on that cell
and base stations. The base stations are used for
voice and data transfer in cellular network. To avoid
interference, a cell uses different frequencies than
their neighboring cells which ensure quality of
service on that cell. In last decade, mobile network
has gained more popularity due to ease of
communication. Now cellular network users have
increased to 2 billion in number.
Cellular network Types
A. Global System for Mobile Communications
GSM delivers data services within the network. It
also offers voice service through digital network.
B. General Packet Radio Service
GPRS outspreads the GSM network by allowing
innovative data services. The transmission of data is
faster than GSM which is upto 54 kbps.
C. Code Division Multiple Access
Qualcomm presented the CDMA technology. It is
expensive to implement as compared to GSM and
GPRS. Its processor is slow than that of GSM /
GPRS. It delivers 300 kbps of speed.
D. Mobitex (Two-way packet-switch network)
Mobitex was Originally designed for covering
metropolitan areas. BlackBerry 95x and 85x uses
Mobitex. The Radio uses less power which results in
long battery lives for several long weeks.
E. EDGE (Enhanced Data for Global Evolution)
EDGE is extended version to the GSM / GPRS
networks. It is 3x faster than GPRS network. It
offers download speed of 100-130 kbps.
III. RECENT TRENDS IN WIRELESS
NETWROKING
A. Li-Fi
Li-Fi uses light to carry information rather than
radio frequency. It is believed that light is capable
of holding more information than RF since it has
comparatively higher frequency and bandwidth. The
belief has been portrayed since from decades but it
has never brought into practice. Data rates are high
in Li-Fi, but there comes a drawback that the data
can be send to only that place where light can go.
Hence it cannot pass through walls but through
windows.
B. Better security
The wireless communication has made human life
much easier than expectations. But with good there
always comes a little bad. In wireless
communication, it is security. RF usually is not
limited to walls which make intruders to easily hack
the network through any seeped radio frequency. As
the enormous growth in wireless communication,
security layers are needed to build.
C. Rapid growth in medical monitoring
applications
The medical monitoring system is most widely used
application of wireless communication. Initially
unsuitable sensors and network devices was the
foremost reason for suffering of such applications.
But with high speed and range devices, medical
applications have been grown in use.
D. Use of LANs for rural broadband coverage
The rural parts were not included in internet
coverage. But with use of new technologies and
innovations it has become possible to provide
internet coverage to rural areas.
E. Wireless Peripherals
With everything wireless, there comes a wireless
mouse which enabled the user to connect a
computer in wireless link with mouse. Also one
more trend has been emerged, the wireless power.
When laptops discharges the user need to plug in
wire to charge it up, the researchers are now finding
ways to supply power wirelessly to the devices to
ease the physical connection.

F. Data Security and Privacy on public networks
The electronic transactions have been an
important part of many people. These
transactions should be very secure and to be used
by the authorized people. Virtual Private
Network (VPN) provides good level of privacy.
Also one can create a safe tunnel for sending
messages on public network by using VPN.
IV. PHYSICAL LAYER STRATEGIES FOR
WIRELESS COMMUNICATION
Following are the techniques widely used for
wireless communications:
1. Spread spectrum: This strategy is applied
to Wi-Fi and in some mobile network to
gain benefit of enhance reliability which
lessens the interference of wireless
communication channel. It also increases
bandwidth which results in achieving
wireless spectrum for efficient sharing and
utilization of bandwidth between multiple
channels. Moreover, spread spectrum
increases security by limiting the
transmissions from attackers.
2. OFDM: Orthogonal Frequency Division
Multiples is a type of multicarrier
modulation that consists of several closely
placed carriers. On application of
modulation to the carrier, the side bands
spread to both the respective sides. With this
there is a challenge for the receiver to
receive whole data and demodulate it. But
this challenge is overcome in OFDM, on the
overlapping of sidebands; the receiver still
can distinguish data without interference.
3. Forward Error Correction: This is the
strategy to obtain error control in
transmission of data where transmitter sends
redundant data to the receiver. With FEC
receiver detects data that is free of errors.
FEC can also be used for broadcasting
purpose, since it does not require
handshaking between transmitter and
receiver.
V. FIXED AND RANDOM ACCESS
TECHNIQUES
Fixed Access Techniques
So as to connect subscribers to the telephone
network, the wireless technology that uses copper is
said to be fixed wireless technique. The fixed
assigned access techniques mainly include TDMA,
FDMA and CDMA.
1. Time Division Multiple Access (TDMA):
This technique is a digital wireless
telephony transmission technique. It assigns
a different time slot to different user on a
determined frequency. It divides the channel
into three slots so as to carry large amount
of data at one access. TDMA can transmit
both data and voice with 64 kbps to 128
Mbps of data rates. TDMA is very cost
efficient in terms of converting analog to
digital signals. Since TDMA provides the
fixed time slot to users, migrating from one
cell, to another may cause disruption of
services. Multipath distortion is highly
observed in TDMA.
2. Frequency Division Multiple Access
(FDMA): A channel is considered as a
frequency in FDMA where different signals
are allocated to different channels. Each
channel is assigned to only one user at one
time.
3. Code Division Multiple Access (CDMA):
This technology uses spread spectrum
technique where a specific frequency is
allocated to every user. CDMA is a platform
for voice and data communication for 3G
technologies. It has high capacity to serve
more users per MHz of bandwidth.
Random access Techniques:
Random access techniques include ALOHA,
CSMA, CSMA/CD, CSMA/CA
Aloha Protocol
In this protocol, whenever a sender has to send data,
it sends it over the channel regardless of who is
currently using the channel. If the frame is
successfully sent, it sends another frame to the
The electronic transactions have been an
important part of many people. These
transactions should be very secure and to be used
by the authorized people. Virtual Private
Network (VPN) provides good level of privacy.
Also one can create a safe tunnel for sending
messages on public network by using VPN.
IV. PHYSICAL LAYER STRATEGIES FOR
WIRELESS COMMUNICATION
Following are the techniques widely used for
wireless communications:
1. Spread spectrum: This strategy is applied
to Wi-Fi and in some mobile network to
gain benefit of enhance reliability which
lessens the interference of wireless
communication channel. It also increases
bandwidth which results in achieving
wireless spectrum for efficient sharing and
utilization of bandwidth between multiple
channels. Moreover, spread spectrum
increases security by limiting the
transmissions from attackers.
2. OFDM: Orthogonal Frequency Division
Multiples is a type of multicarrier
modulation that consists of several closely
placed carriers. On application of
modulation to the carrier, the side bands
spread to both the respective sides. With this
there is a challenge for the receiver to
receive whole data and demodulate it. But
this challenge is overcome in OFDM, on the
overlapping of sidebands; the receiver still
can distinguish data without interference.
3. Forward Error Correction: This is the
strategy to obtain error control in
transmission of data where transmitter sends
redundant data to the receiver. With FEC
receiver detects data that is free of errors.
FEC can also be used for broadcasting
purpose, since it does not require
handshaking between transmitter and
receiver.
V. FIXED AND RANDOM ACCESS
TECHNIQUES
Fixed Access Techniques
So as to connect subscribers to the telephone
network, the wireless technology that uses copper is
said to be fixed wireless technique. The fixed
assigned access techniques mainly include TDMA,
FDMA and CDMA.
1. Time Division Multiple Access (TDMA):
This technique is a digital wireless
telephony transmission technique. It assigns
a different time slot to different user on a
determined frequency. It divides the channel
into three slots so as to carry large amount
of data at one access. TDMA can transmit
both data and voice with 64 kbps to 128
Mbps of data rates. TDMA is very cost
efficient in terms of converting analog to
digital signals. Since TDMA provides the
fixed time slot to users, migrating from one
cell, to another may cause disruption of
services. Multipath distortion is highly
observed in TDMA.
2. Frequency Division Multiple Access
(FDMA): A channel is considered as a
frequency in FDMA where different signals
are allocated to different channels. Each
channel is assigned to only one user at one
time.
3. Code Division Multiple Access (CDMA):
This technology uses spread spectrum
technique where a specific frequency is
allocated to every user. CDMA is a platform
for voice and data communication for 3G
technologies. It has high capacity to serve
more users per MHz of bandwidth.
Random access Techniques:
Random access techniques include ALOHA,
CSMA, CSMA/CD, CSMA/CA
Aloha Protocol
In this protocol, whenever a sender has to send data,
it sends it over the channel regardless of who is
currently using the channel. If the frame is
successfully sent, it sends another frame to the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
channel. But if the transmission fails, the transmitter
sends the frame again. This protocol has a drawback
of collisions of data if multiple sources are sending
data to one destination.
CSMA Protocol
This protocol allows sender to first sense the
channel to avoid collisions. Carrier Sense Multiple
Access with Collision Detection (CSMA/CD) and
Carrier Sense Multiple Access with Collision
Avoidance (CSMA/CA) are two variations of this
protocol as discussed below:
CSMA CD (Carrier Sense multiple Access
Collision Detection)
CSMA CD is widely used by IEEE 802.3 standard
Ethernet network where the traffic is monitored by
each device in the network. If channel is not
carrying any data then the particular sender
transmits the data.
CSMA CA (Carrier Sense multiple Access
Collision Avoidance)
In this protocol multiple senders sends data
simultaneously on the channel. Each node is
evaluates the channel state at first. If the channel is
idle, it can transmit data else the channel is stated to
be busy and then sender has to wait for channel to
become idle. This protocol is implemented in IEEE
802.11 wireless Local Area Network (LANs).
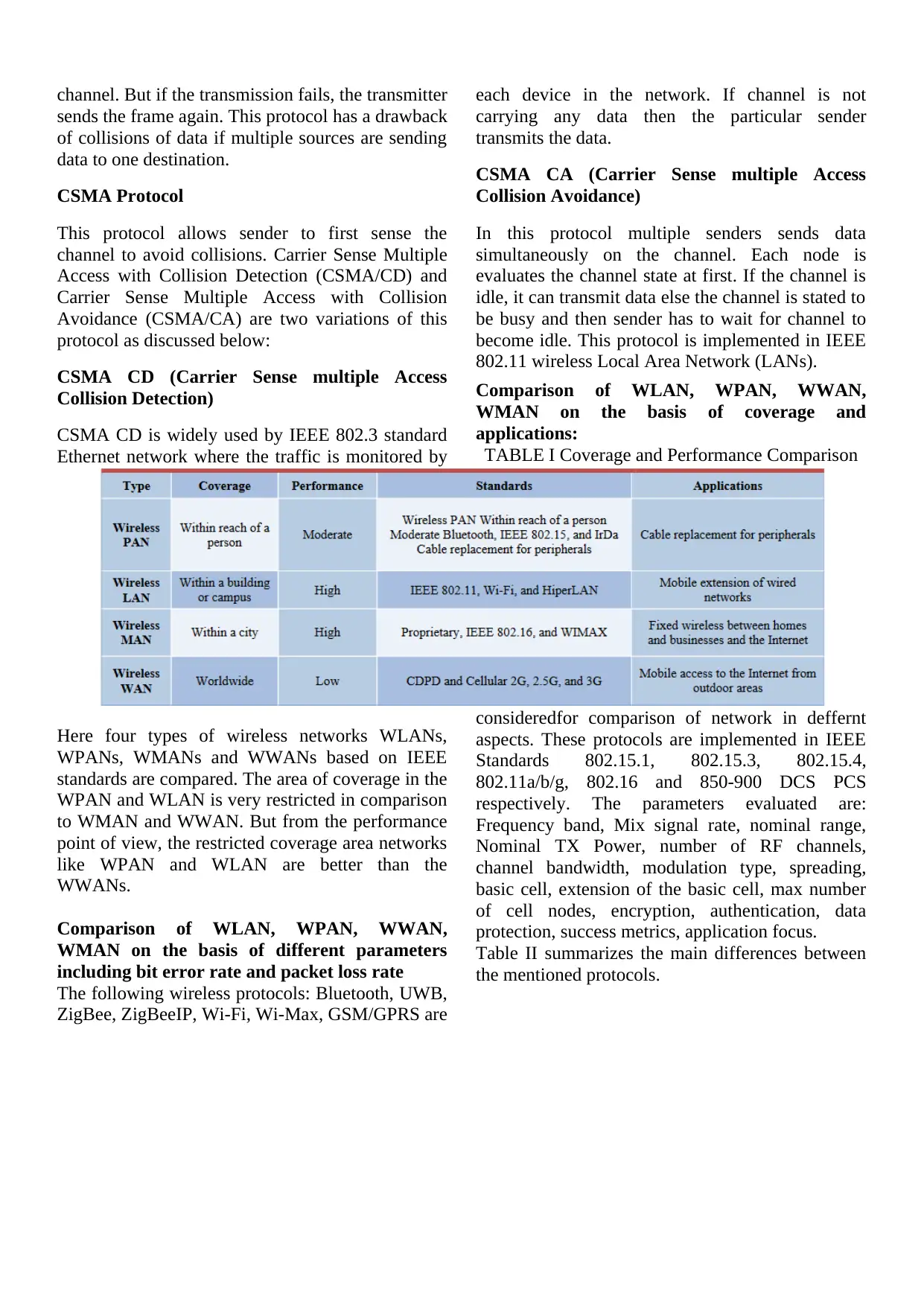
Comparison of WLAN, WPAN, WWAN,
WMAN on the basis of coverage and
applications:
TABLE I Coverage and Performance Comparison
Here four types of wireless networks WLANs,
WPANs, WMANs and WWANs based on IEEE
standards are compared. The area of coverage in the
WPAN and WLAN is very restricted in comparison
to WMAN and WWAN. But from the performance
point of view, the restricted coverage area networks
like WPAN and WLAN are better than the
WWANs.
Comparison of WLAN, WPAN, WWAN,
WMAN on the basis of different parameters
including bit error rate and packet loss rate
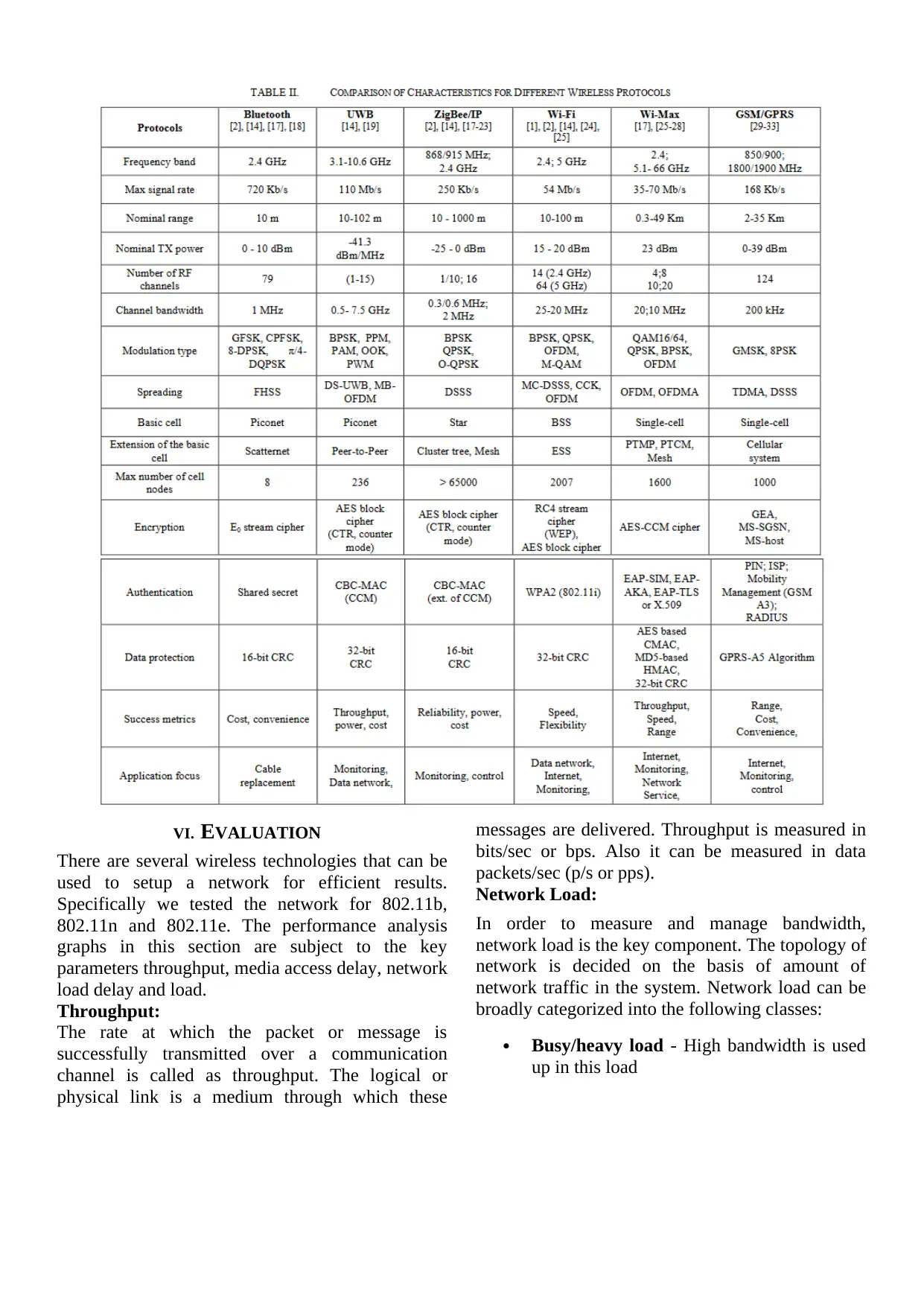
The following wireless protocols: Bluetooth, UWB,
ZigBee, ZigBeeIP, Wi-Fi, Wi-Max, GSM/GPRS are
consideredfor comparison of network in deffernt
aspects. These protocols are implemented in IEEE
Standards 802.15.1, 802.15.3, 802.15.4,
802.11a/b/g, 802.16 and 850-900 DCS PCS
respectively. The parameters evaluated are:
Frequency band, Mix signal rate, nominal range,
Nominal TX Power, number of RF channels,
channel bandwidth, modulation type, spreading,
basic cell, extension of the basic cell, max number
of cell nodes, encryption, authentication, data
protection, success metrics, application focus.
Table II summarizes the main differences between
the mentioned protocols.
sends the frame again. This protocol has a drawback
of collisions of data if multiple sources are sending
data to one destination.
CSMA Protocol
This protocol allows sender to first sense the
channel to avoid collisions. Carrier Sense Multiple
Access with Collision Detection (CSMA/CD) and
Carrier Sense Multiple Access with Collision
Avoidance (CSMA/CA) are two variations of this
protocol as discussed below:
CSMA CD (Carrier Sense multiple Access
Collision Detection)
CSMA CD is widely used by IEEE 802.3 standard
Ethernet network where the traffic is monitored by
each device in the network. If channel is not
carrying any data then the particular sender
transmits the data.
CSMA CA (Carrier Sense multiple Access
Collision Avoidance)
In this protocol multiple senders sends data
simultaneously on the channel. Each node is
evaluates the channel state at first. If the channel is
idle, it can transmit data else the channel is stated to
be busy and then sender has to wait for channel to
become idle. This protocol is implemented in IEEE
802.11 wireless Local Area Network (LANs).
Comparison of WLAN, WPAN, WWAN,
WMAN on the basis of coverage and
applications:
TABLE I Coverage and Performance Comparison
Here four types of wireless networks WLANs,
WPANs, WMANs and WWANs based on IEEE
standards are compared. The area of coverage in the
WPAN and WLAN is very restricted in comparison
to WMAN and WWAN. But from the performance
point of view, the restricted coverage area networks
like WPAN and WLAN are better than the
WWANs.
Comparison of WLAN, WPAN, WWAN,
WMAN on the basis of different parameters
including bit error rate and packet loss rate
The following wireless protocols: Bluetooth, UWB,
ZigBee, ZigBeeIP, Wi-Fi, Wi-Max, GSM/GPRS are
consideredfor comparison of network in deffernt
aspects. These protocols are implemented in IEEE
Standards 802.15.1, 802.15.3, 802.15.4,
802.11a/b/g, 802.16 and 850-900 DCS PCS
respectively. The parameters evaluated are:
Frequency band, Mix signal rate, nominal range,
Nominal TX Power, number of RF channels,
channel bandwidth, modulation type, spreading,
basic cell, extension of the basic cell, max number
of cell nodes, encryption, authentication, data
protection, success metrics, application focus.
Table II summarizes the main differences between
the mentioned protocols.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
VI. EVALUATION
There are several wireless technologies that can be
used to setup a network for efficient results.
Specifically we tested the network for 802.11b,
802.11n and 802.11e. The performance analysis
graphs in this section are subject to the key
parameters throughput, media access delay, network
load delay and load.
Throughput:
The rate at which the packet or message is
successfully transmitted over a communication
channel is called as throughput. The logical or
physical link is a medium through which these
messages are delivered. Throughput is measured in
bits/sec or bps. Also it can be measured in data
packets/sec (p/s or pps).
Network Load:
In order to measure and manage bandwidth,
network load is the key component. The topology of
network is decided on the basis of amount of
network traffic in the system. Network load can be
broadly categorized into the following classes:
Busy/heavy load - High bandwidth is used
up in this load
There are several wireless technologies that can be
used to setup a network for efficient results.
Specifically we tested the network for 802.11b,
802.11n and 802.11e. The performance analysis
graphs in this section are subject to the key
parameters throughput, media access delay, network
load delay and load.
Throughput:
The rate at which the packet or message is
successfully transmitted over a communication
channel is called as throughput. The logical or
physical link is a medium through which these
messages are delivered. Throughput is measured in
bits/sec or bps. Also it can be measured in data
packets/sec (p/s or pps).
Network Load:
In order to measure and manage bandwidth,
network load is the key component. The topology of
network is decided on the basis of amount of
network traffic in the system. Network load can be
broadly categorized into the following classes:
Busy/heavy load - High bandwidth is used
up in this load

Non-real-time load - Consumption of
bandwidth during working hours
Interactive load - Is focused on competition
for bandwidth and may consequence in poor
response times.
Latency-sensitive load - Is focused on
competition for bandwidth and may
consequence in poor response times
Media Access Delay:
The time period between data reception at MAC
Layer and transmission on wireless medium is
referred to as media access delay. There is a need
for of fewer delays for real-time data flow hence
this metrics is very vital to analyze. Because once
the packets are delayed for more time, they may
become useless.
Load:
The distribution of processing and communication
activity over the network should be evenly across
the network so as to avoid overwhelming of a single
device in the network. Load calculation is a very
crucial metrics for quality of service in the network.
Load balancing is the process of distributing the
amount of job that a computer has to perform
between two or more computers in order to
complete more work in same amount of time. And
eventually all the users get served faster.
Delay:
A computer network is analyzed on one more
important metrics called as network delay. The
network delay defines the time required for bit of
data takes to transit within the network from source
to destination. Delay is usually measured in
multiples or factions of second. It is affected by the
physical distance between source and destination in
the network.
802.11b 11mbps
The very first wave of wireless networking was
possible with 802.11b technology. 802.11b made it
possible for the new technology to emerge as W-Fi.
1) Performance of 802.11b
The maximum data rate supported by 802.11b is 11
Mbps. In comparison with Ethernet which supports
10 Mbps, 802.11b performs slower than all newer
communication technologies.
2) 802.11b and Wireless Interference
802.11b transmitters support 2.4GHz frequency
range. While communicating within this range they
may interfere with other wireless products in the
house. These products includes cordless telephones,
garage openers, baby monitors, etc..
Following are the individual performance analysis
graphs for this technology on the designed network.
The graphs depict the 802.11b performance over the
designed network.
Figure 1 shows the throughput obtained by using
802.11b protocol. It is clearly observed from the
graph that the throughput suddenly increases after
the 40-45 sec and reaches at its peak on around
650000 bits at 01:50 approx. time.
Figure 1 WLAN Throughput for 802.11b
bandwidth during working hours
Interactive load - Is focused on competition
for bandwidth and may consequence in poor
response times.
Latency-sensitive load - Is focused on
competition for bandwidth and may
consequence in poor response times
Media Access Delay:
The time period between data reception at MAC
Layer and transmission on wireless medium is
referred to as media access delay. There is a need
for of fewer delays for real-time data flow hence
this metrics is very vital to analyze. Because once
the packets are delayed for more time, they may
become useless.
Load:
The distribution of processing and communication
activity over the network should be evenly across
the network so as to avoid overwhelming of a single
device in the network. Load calculation is a very
crucial metrics for quality of service in the network.
Load balancing is the process of distributing the
amount of job that a computer has to perform
between two or more computers in order to
complete more work in same amount of time. And
eventually all the users get served faster.
Delay:
A computer network is analyzed on one more
important metrics called as network delay. The
network delay defines the time required for bit of
data takes to transit within the network from source
to destination. Delay is usually measured in
multiples or factions of second. It is affected by the
physical distance between source and destination in
the network.
802.11b 11mbps
The very first wave of wireless networking was
possible with 802.11b technology. 802.11b made it
possible for the new technology to emerge as W-Fi.
1) Performance of 802.11b
The maximum data rate supported by 802.11b is 11
Mbps. In comparison with Ethernet which supports
10 Mbps, 802.11b performs slower than all newer
communication technologies.
2) 802.11b and Wireless Interference
802.11b transmitters support 2.4GHz frequency
range. While communicating within this range they
may interfere with other wireless products in the
house. These products includes cordless telephones,
garage openers, baby monitors, etc..
Following are the individual performance analysis
graphs for this technology on the designed network.
The graphs depict the 802.11b performance over the
designed network.
Figure 1 shows the throughput obtained by using
802.11b protocol. It is clearly observed from the
graph that the throughput suddenly increases after
the 40-45 sec and reaches at its peak on around
650000 bits at 01:50 approx. time.
Figure 1 WLAN Throughput for 802.11b
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 2 Network Load for 802.11b
Figure 2 shows the network load by using 802.11b
protocol. As discussed in previous section, the
network load is an important metric for analyzing
the network performance. The graph shows that
high delay is observed at 40 sec of the data
transmission and it reached till 2,500K bits which is
very high. Then the network load is normalized and
it became constant for rest of the time.
Figure 3 Media Access Delay for 802.11b
Figure 3 shows the media access delay by using
802.11b protocol for the designed network. It can be
seen from graph that initially delay is not observed
at all but it is delayed after 50th second of data
transmission.
Figure 4 on next page shows load by using 802.11b
protocol for the designed network. The graph shows
that the load remains constant at 4,500 K bits after
some point of time. Load in the network should be
less for the efficient operation of network.
Figure 4 Load for 802.11b
Figure 5 Delay for 802.11b
Figure 5 shows Delay by using 802.11b protocol for
the designed network. Once the network is busy
with transmitting many data packets, the delay is
observed for around 11 seconds.
802.11n 2.4GHz 60 mbps
Wireless N aka 802.11n is a wireless technology to
improve 802.11 other technologies such as b and g
by supporting multiple wireless signals and
antennas instead of one. It supports 300 Mbps
bandwidth which is much higher than 802.11b
Figure 2 shows the network load by using 802.11b
protocol. As discussed in previous section, the
network load is an important metric for analyzing
the network performance. The graph shows that
high delay is observed at 40 sec of the data
transmission and it reached till 2,500K bits which is
very high. Then the network load is normalized and
it became constant for rest of the time.
Figure 3 Media Access Delay for 802.11b
Figure 3 shows the media access delay by using
802.11b protocol for the designed network. It can be
seen from graph that initially delay is not observed
at all but it is delayed after 50th second of data
transmission.
Figure 4 on next page shows load by using 802.11b
protocol for the designed network. The graph shows
that the load remains constant at 4,500 K bits after
some point of time. Load in the network should be
less for the efficient operation of network.
Figure 4 Load for 802.11b
Figure 5 Delay for 802.11b
Figure 5 shows Delay by using 802.11b protocol for
the designed network. Once the network is busy
with transmitting many data packets, the delay is
observed for around 11 seconds.
802.11n 2.4GHz 60 mbps
Wireless N aka 802.11n is a wireless technology to
improve 802.11 other technologies such as b and g
by supporting multiple wireless signals and
antennas instead of one. It supports 300 Mbps
bandwidth which is much higher than 802.11b
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Advantages of 802.11n
o It has fastest speed
o It has finest signal range
o It is more resistant to interference of
signals from other sources.
Disadvantages of 802.11n
o The 802.11n standard is not yet
confirmed.
o It is costly than 802.11g and 802.11b
Important Wireless Technologies in 802.11n
It requires several wireless antennas so as to send
and receive data. It uses MINO technology,
Multiple Input, Multiple Output which coordinates
multiple radio signals at one time. MIMO is proved
to increase the range as well as throughput of a
wireless network.
802.11n also employed a new technique that
increases channel bandwidth. All the 802.11n
devices use a predefined Wi-Fi channel. These
devices also uses larger frequency range than other
standards which results in increased throughput.
3) Performance of 802.11n
The maximum supported bandwidth of 802.11n is
300 Mbps which depend primarily on the number of
receivers assembled within the devices. Following
section shows the network performance when using
802.11n wireless technology for the proposed
network design.
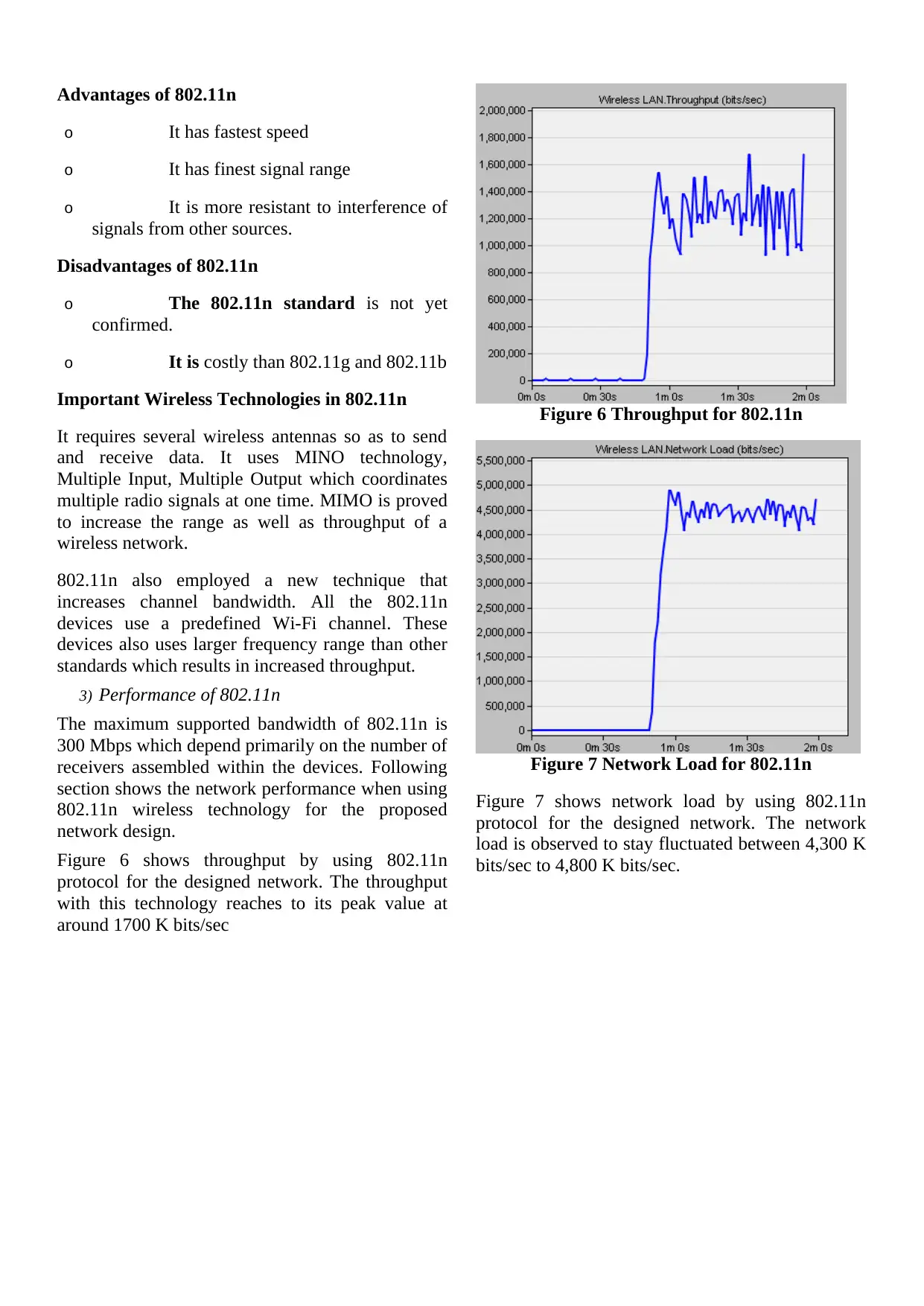
Figure 6 shows throughput by using 802.11n
protocol for the designed network. The throughput
with this technology reaches to its peak value at
around 1700 K bits/sec
Figure 6 Throughput for 802.11n
Figure 7 Network Load for 802.11n
Figure 7 shows network load by using 802.11n
protocol for the designed network. The network
load is observed to stay fluctuated between 4,300 K
bits/sec to 4,800 K bits/sec.
o It has fastest speed
o It has finest signal range
o It is more resistant to interference of
signals from other sources.
Disadvantages of 802.11n
o The 802.11n standard is not yet
confirmed.
o It is costly than 802.11g and 802.11b
Important Wireless Technologies in 802.11n
It requires several wireless antennas so as to send
and receive data. It uses MINO technology,
Multiple Input, Multiple Output which coordinates
multiple radio signals at one time. MIMO is proved
to increase the range as well as throughput of a
wireless network.
802.11n also employed a new technique that
increases channel bandwidth. All the 802.11n
devices use a predefined Wi-Fi channel. These
devices also uses larger frequency range than other
standards which results in increased throughput.
3) Performance of 802.11n
The maximum supported bandwidth of 802.11n is
300 Mbps which depend primarily on the number of
receivers assembled within the devices. Following
section shows the network performance when using
802.11n wireless technology for the proposed
network design.
Figure 6 shows throughput by using 802.11n
protocol for the designed network. The throughput
with this technology reaches to its peak value at
around 1700 K bits/sec
Figure 6 Throughput for 802.11n
Figure 7 Network Load for 802.11n
Figure 7 shows network load by using 802.11n
protocol for the designed network. The network
load is observed to stay fluctuated between 4,300 K
bits/sec to 4,800 K bits/sec.
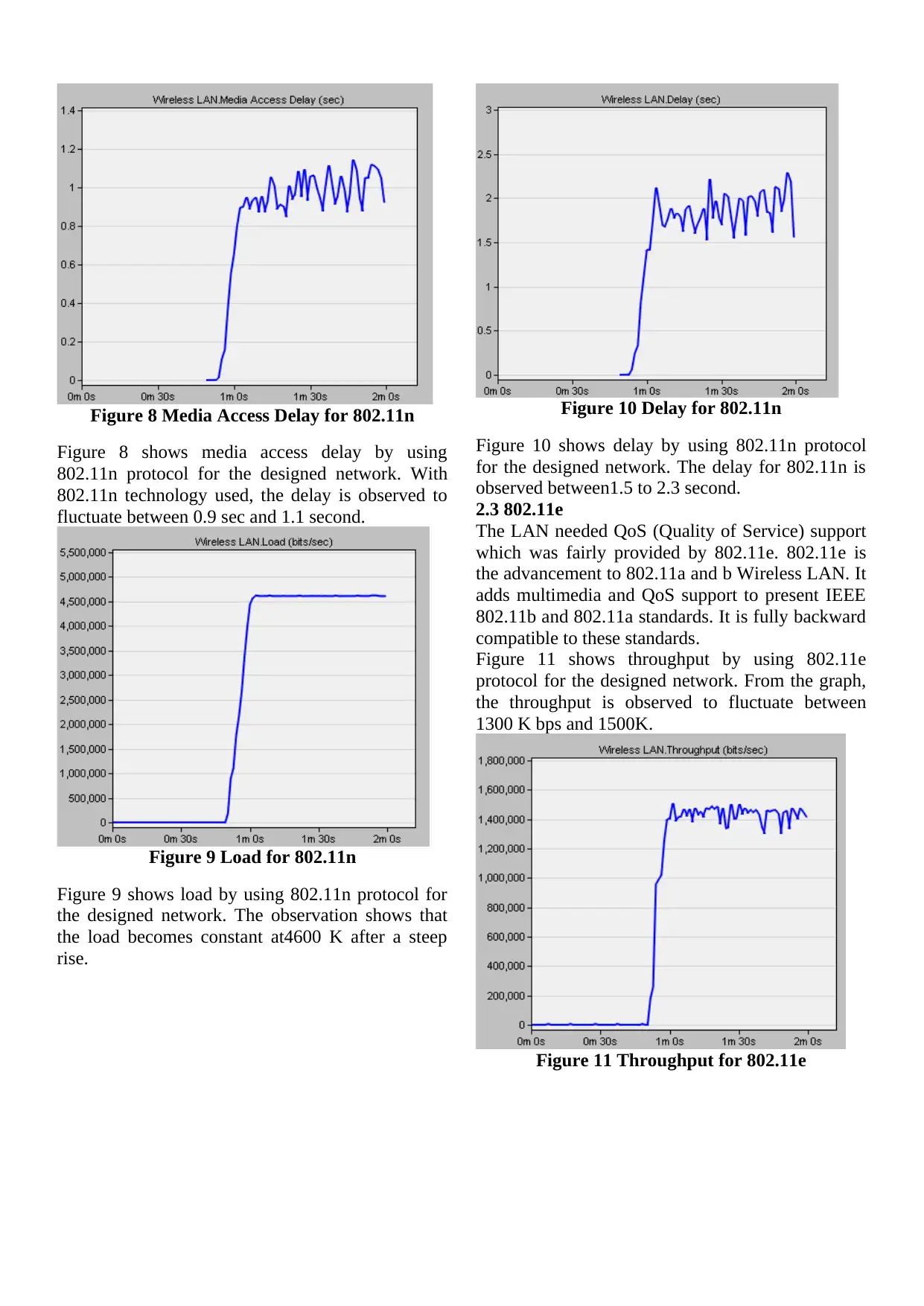
Figure 8 Media Access Delay for 802.11n
Figure 8 shows media access delay by using
802.11n protocol for the designed network. With
802.11n technology used, the delay is observed to
fluctuate between 0.9 sec and 1.1 second.
Figure 9 Load for 802.11n
Figure 9 shows load by using 802.11n protocol for
the designed network. The observation shows that
the load becomes constant at4600 K after a steep
rise.
Figure 10 Delay for 802.11n
Figure 10 shows delay by using 802.11n protocol
for the designed network. The delay for 802.11n is
observed between1.5 to 2.3 second.
2.3 802.11e
The LAN needed QoS (Quality of Service) support
which was fairly provided by 802.11e. 802.11e is
the advancement to 802.11a and b Wireless LAN. It
adds multimedia and QoS support to present IEEE
802.11b and 802.11a standards. It is fully backward
compatible to these standards.
Figure 11 shows throughput by using 802.11e
protocol for the designed network. From the graph,
the throughput is observed to fluctuate between
1300 K bps and 1500K.
Figure 11 Throughput for 802.11e
Figure 8 shows media access delay by using
802.11n protocol for the designed network. With
802.11n technology used, the delay is observed to
fluctuate between 0.9 sec and 1.1 second.
Figure 9 Load for 802.11n
Figure 9 shows load by using 802.11n protocol for
the designed network. The observation shows that
the load becomes constant at4600 K after a steep
rise.
Figure 10 Delay for 802.11n
Figure 10 shows delay by using 802.11n protocol
for the designed network. The delay for 802.11n is
observed between1.5 to 2.3 second.
2.3 802.11e
The LAN needed QoS (Quality of Service) support
which was fairly provided by 802.11e. 802.11e is
the advancement to 802.11a and b Wireless LAN. It
adds multimedia and QoS support to present IEEE
802.11b and 802.11a standards. It is fully backward
compatible to these standards.
Figure 11 shows throughput by using 802.11e
protocol for the designed network. From the graph,
the throughput is observed to fluctuate between
1300 K bps and 1500K.
Figure 11 Throughput for 802.11e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
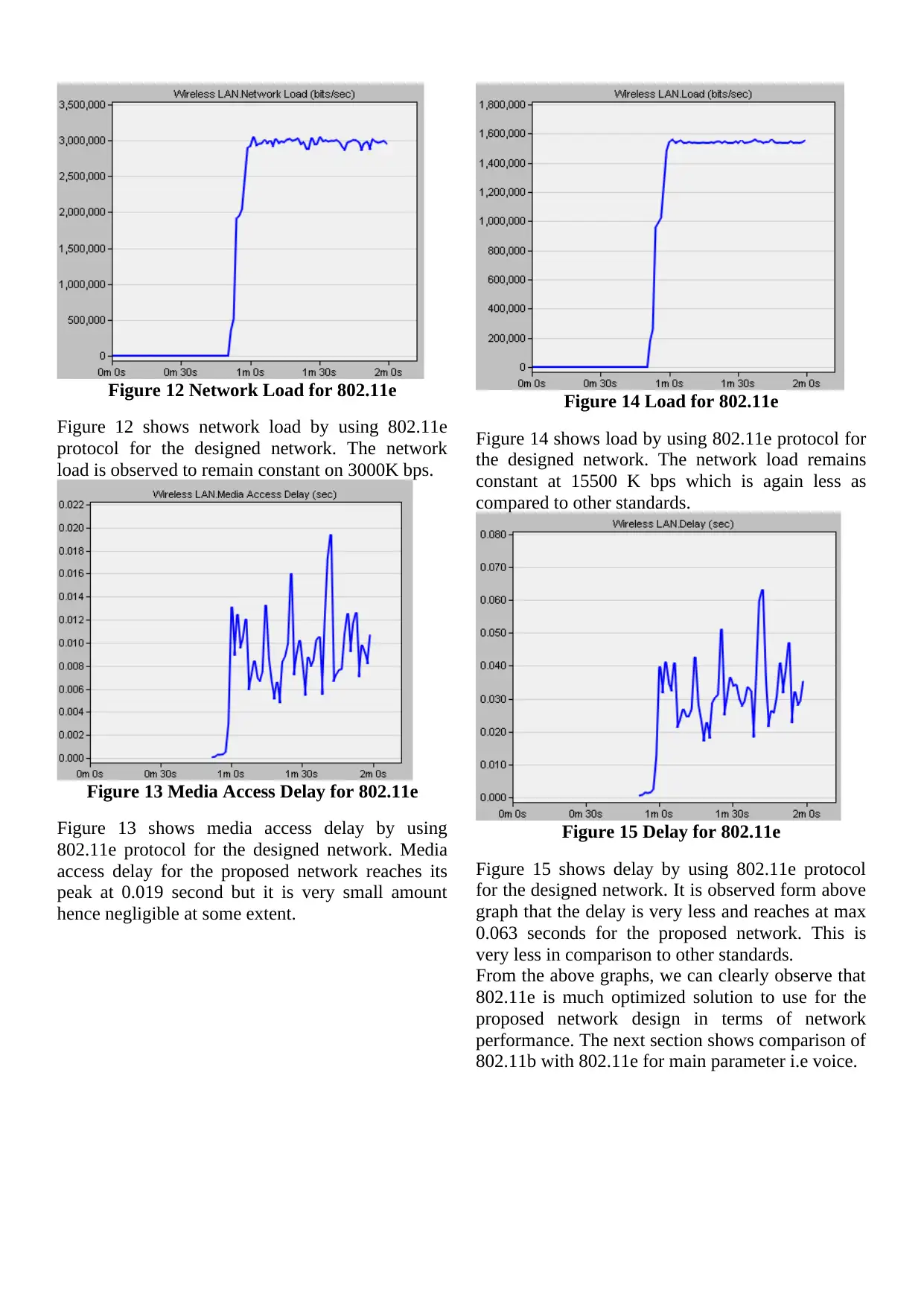
Figure 12 Network Load for 802.11e
Figure 12 shows network load by using 802.11e
protocol for the designed network. The network
load is observed to remain constant on 3000K bps.
Figure 13 Media Access Delay for 802.11e
Figure 13 shows media access delay by using
802.11e protocol for the designed network. Media
access delay for the proposed network reaches its
peak at 0.019 second but it is very small amount
hence negligible at some extent.
Figure 14 Load for 802.11e
Figure 14 shows load by using 802.11e protocol for
the designed network. The network load remains
constant at 15500 K bps which is again less as
compared to other standards.
Figure 15 Delay for 802.11e
Figure 15 shows delay by using 802.11e protocol
for the designed network. It is observed form above
graph that the delay is very less and reaches at max
0.063 seconds for the proposed network. This is
very less in comparison to other standards.
From the above graphs, we can clearly observe that
802.11e is much optimized solution to use for the
proposed network design in terms of network
performance. The next section shows comparison of
802.11b with 802.11e for main parameter i.e voice.
Figure 12 shows network load by using 802.11e
protocol for the designed network. The network
load is observed to remain constant on 3000K bps.
Figure 13 Media Access Delay for 802.11e
Figure 13 shows media access delay by using
802.11e protocol for the designed network. Media
access delay for the proposed network reaches its
peak at 0.019 second but it is very small amount
hence negligible at some extent.
Figure 14 Load for 802.11e
Figure 14 shows load by using 802.11e protocol for
the designed network. The network load remains
constant at 15500 K bps which is again less as
compared to other standards.
Figure 15 Delay for 802.11e
Figure 15 shows delay by using 802.11e protocol
for the designed network. It is observed form above
graph that the delay is very less and reaches at max
0.063 seconds for the proposed network. This is
very less in comparison to other standards.
From the above graphs, we can clearly observe that
802.11e is much optimized solution to use for the
proposed network design in terms of network
performance. The next section shows comparison of
802.11b with 802.11e for main parameter i.e voice.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSIONS
We performed simulation of network using
802.11b and 802.11e wireless technologies for
different wireless parameters. The conclusions are as
followed:
1. Throughput: The graphs shown comparison
of both the standards used for the network and it was
observed that the throughput for 802.11e is higher
than 802.11b. It is considerably higher for 802.11e
hence, the standard that can be used for
communication in the network is 802.11e with much
higher throughput.
2. Network Load: The network load is higher
when using 802.11e technology in comparison to
82.11b. This is a pitfall for 802.11e but by observing
other parameters it is worth bearing network load
than to loss for other important parameters.
3. Media Access Delay: It is observed high in
802.11b than 802.11e. Media access delay is very
less in 802.11e which make the communication
faster within the network. It was observed that the
delay is negligibly of small amount as compared to
802.11b.
4. Load: The load in the high while using
802.11b technology as compared to 802.11e. Hence
it is feasible to use 802.11e for the proposed network
design.
5. Delay: The delay is low when we used
802.11e in the network than 802.11b. Similar to
media access delay, here also delay is very less and
hence causes efficient communication.
From the above results we conclude that it is
better to use 802.11e wireless technology in the
network than 802.11b. Both the standards have their
own advantages and limitations but for this proposed
design of the network with many rigid requirements,
802.11e is found as more optimized wireless
technology.
REFERENCES
[1] Andrea Goldsmith, “WIRELESS
COMMUNICATIONS,” Cambridge University
Press, 2005.
[2] “Wireless Technology Trends Understand Them
and Get Ahead Of The Crowd”, [Online]
Available : https://www.wireless-technology-
advisor.com/wireless-technology-trends.html
[3] “TECHNOLOGY OF FIXED WIRELESS
ACCESS”, [Online] Available :
http://www.citi.columbia.edu/wireless/!
citi_fw.htm
[4] CDMA Theory and Nortel Networks Product
Design and Function, Student Guide, July 2000
[5] “Difference Between CSMA and ALOHA”,
[Online] Available :
http://www.differencebetween.com/difference-
between-csma-and-vs-aloha/
[6] “Difference Between CSMA CD and CSMA
CA”, [Online] Available:
http://www.differencebetween.com/difference-
between-csma-cd-and-vs-csma-ca/
[7] “Difference Between Pure ALOHA and Slotted
ALOHA”, [Online] Available :
https://techdifferences.com/difference-between-
pure-aloha-and-slotted-aloha.html
[8] Kanika Sharma, Neha Dhir,” A Study of
Wireless Networks: WLANs, WPANs,
“WMANs, and WWANs with Comparison”,
International Journal of Computer Science and
Information Technologies, Vol. 5 (6), 2014,
7810-7813.
[9] Chakkor Saad, Baghouri Mostafa, El Ahmadi
Cheikh, Hajraoui Abderrahmane, “Comparative
Performance Analysis of Wireless
Communication Protocols for Intelligent
Sensors and Their Applications”, (IJACSA)
International Journal of Advanced Computer
Science and Applications, Vol. 5, No. 4, 2014.
We performed simulation of network using
802.11b and 802.11e wireless technologies for
different wireless parameters. The conclusions are as
followed:
1. Throughput: The graphs shown comparison
of both the standards used for the network and it was
observed that the throughput for 802.11e is higher
than 802.11b. It is considerably higher for 802.11e
hence, the standard that can be used for
communication in the network is 802.11e with much
higher throughput.
2. Network Load: The network load is higher
when using 802.11e technology in comparison to
82.11b. This is a pitfall for 802.11e but by observing
other parameters it is worth bearing network load
than to loss for other important parameters.
3. Media Access Delay: It is observed high in
802.11b than 802.11e. Media access delay is very
less in 802.11e which make the communication
faster within the network. It was observed that the
delay is negligibly of small amount as compared to
802.11b.
4. Load: The load in the high while using
802.11b technology as compared to 802.11e. Hence
it is feasible to use 802.11e for the proposed network
design.
5. Delay: The delay is low when we used
802.11e in the network than 802.11b. Similar to
media access delay, here also delay is very less and
hence causes efficient communication.
From the above results we conclude that it is
better to use 802.11e wireless technology in the
network than 802.11b. Both the standards have their
own advantages and limitations but for this proposed
design of the network with many rigid requirements,
802.11e is found as more optimized wireless
technology.
REFERENCES
[1] Andrea Goldsmith, “WIRELESS
COMMUNICATIONS,” Cambridge University
Press, 2005.
[2] “Wireless Technology Trends Understand Them
and Get Ahead Of The Crowd”, [Online]
Available : https://www.wireless-technology-
advisor.com/wireless-technology-trends.html
[3] “TECHNOLOGY OF FIXED WIRELESS
ACCESS”, [Online] Available :
http://www.citi.columbia.edu/wireless/!
citi_fw.htm
[4] CDMA Theory and Nortel Networks Product
Design and Function, Student Guide, July 2000
[5] “Difference Between CSMA and ALOHA”,
[Online] Available :
http://www.differencebetween.com/difference-
between-csma-and-vs-aloha/
[6] “Difference Between CSMA CD and CSMA
CA”, [Online] Available:
http://www.differencebetween.com/difference-
between-csma-cd-and-vs-csma-ca/
[7] “Difference Between Pure ALOHA and Slotted
ALOHA”, [Online] Available :
https://techdifferences.com/difference-between-
pure-aloha-and-slotted-aloha.html
[8] Kanika Sharma, Neha Dhir,” A Study of
Wireless Networks: WLANs, WPANs,
“WMANs, and WWANs with Comparison”,
International Journal of Computer Science and
Information Technologies, Vol. 5 (6), 2014,
7810-7813.
[9] Chakkor Saad, Baghouri Mostafa, El Ahmadi
Cheikh, Hajraoui Abderrahmane, “Comparative
Performance Analysis of Wireless
Communication Protocols for Intelligent
Sensors and Their Applications”, (IJACSA)
International Journal of Advanced Computer
Science and Applications, Vol. 5, No. 4, 2014.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




