Evaluation of Wireless Networks
11 Pages4299 Words214 Views
Added on 2019-09-30
Evaluation of Wireless Networks
Added on 2019-09-30
ShareRelated Documents
Wireless Networks: Overview, Comparison and EvaluationAuthors Name/s per 1st Affiliation (Author)line 1 (of Affiliation): dept. name of organizationline 2-name of organization, acronyms acceptableline 3-City, Countryline 4-e-mail address if desiredAuthors Name/s per 2nd Affiliation (Author)line 1 (of Affiliation): dept. name of organizationline 2-name of organization, acronyms acceptableline 3-City, Countryline 4-e-mail address if desiredAbstract— A cluster of two or more computersystems when connected with each other, forms anetwork. Network types include LAN, WAN,CAN, MAN and HAN. LAN (Local AreaNetwork) is where geographically, computersystems are placed very close to each other, mostprobably in a same building. WANs (Wide AreaNetwork) are computers connected withtelephone lines or radio waves. CANs (CampusArea Network) are limited confined to one areasuch as a military camp or a campus. MANs(Metropolitan Area Network) are network for atown or city. HANs (Home Area Network) aresmall home network with users’ personal devicesconnected to each other.I.WIRELESSNETWORKOVERVIEWIn communications sector, wirelesscommunication is the widely increasing technologywith great future imaginations. It has gained focus ofmedia and mass imagination. Moreover, WANshave taken place of all the wired networks in officesand even homes and campuses. Many newinnovations are been made to ease human life byapplying wireless communication in factories andhomes. These innovations include automatedhighways and smart home solutions.Following are the types of wireless networkbased on its speed of transferring data and theirranges.1.Wireless PAN –These are Wireless Personal Area Networks withsmall network within the person’s reach usually aninfrared light. WPAN lets a Bluetoothcommunication radio to connect to the laptop via aheadphone.2.Wireless LAN –Wireless Local Area Network is interconnectionof network devices that provide a wide internetconnection by making use of access point. Spread-spectrum aka OFDM technologies let clients toaccess and move within the range of coverage areawhile they are connected to the network. It holds 10Mbps Ethernet speed and 1 Gbps Gigabit Ethernetspeed. WLANs can connect hundreds or even onethousand users.3.Wireless MAN Many WLANs connected to each other forms aWMAN network. The different WLANs arerequired to geographically close to each otherusually just few miles away from each other. Thedevices in WMAN connect and communicate insuch way as if they are placed in same LAN. This ismade possible by using high speed and high rangerouters, switches and links like fiber optic cables.The most popular WMAN network is WiMAX.4.Wireless WANWWAN usually connects large outdoor areas. Itis used in interconnecting different branches of thebusiness widely away from each other. The speedusually depends on the connection cost thatincreases due to increase in distance. The mostprominent example of WWAN is internet.II.CELLULAR NETWORK OVERVIEWCellular network popularly known as mobilenetwork is the widely used communication networkwhere last link is wireless. The network is spread

over lands (cells), each containing a transceiver atfixed location to manage the network on that celland base stations. The base stations are used forvoice and data transfer in cellular network. To avoidinterference, a cell uses different frequencies thantheir neighboring cells which ensure quality ofservice on that cell. In last decade, mobile networkhas gained more popularity due to ease ofcommunication. Now cellular network users haveincreased to 2 billion in number. Cellular network TypesA.Global System for Mobile CommunicationsGSM delivers data services within the network. Italso offers voice service through digital network.B.General Packet Radio ServiceGPRS outspreads the GSM network by allowinginnovative data services. The transmission of data isfaster than GSM which is upto 54 kbps.C.Code Division Multiple AccessQualcomm presented the CDMA technology. It isexpensive to implement as compared to GSM andGPRS. Its processor is slow than that of GSM /GPRS. It delivers 300 kbps of speed.D.Mobitex (Two-way packet-switch network)Mobitex was Originally designed for coveringmetropolitan areas. BlackBerry 95x and 85x usesMobitex. The Radio uses less power which results inlong battery lives for several long weeks. E.EDGE (Enhanced Data for Global Evolution)EDGE is extended version to the GSM / GPRSnetworks. It is 3x faster than GPRS network. Itoffers download speed of 100-130 kbps.III.RECENT TRENDS IN WIRELESSNETWROKINGA.Li-FiLi-Fi uses light to carry information rather thanradio frequency. It is believed that light is capableof holding more information than RF since it hascomparatively higher frequency and bandwidth. Thebelief has been portrayed since from decades but ithas never brought into practice. Data rates are highin Li-Fi, but there comes a drawback that the datacan be send to only that place where light can go.Hence it cannot pass through walls but throughwindows. B.Better security The wireless communication has made human lifemuch easier than expectations. But with good therealways comes a little bad. In wirelesscommunication, it is security. RF usually is notlimited to walls which make intruders to easily hackthe network through any seeped radio frequency. Asthe enormous growth in wireless communication,security layers are needed to build.C.Rapid growth in medical monitoringapplications The medical monitoring system is most widely usedapplication of wireless communication. Initiallyunsuitable sensors and network devices was theforemost reason for suffering of such applications.But with high speed and range devices, medicalapplications have been grown in use.D.Use of LANs for rural broadband coverage The rural parts were not included in internetcoverage. But with use of new technologies andinnovations it has become possible to provideinternet coverage to rural areas. E.Wireless PeripheralsWith everything wireless, there comes a wirelessmouse which enabled the user to connect acomputer in wireless link with mouse. Also onemore trend has been emerged, the wireless power.When laptops discharges the user need to plug inwire to charge it up, the researchers are now findingways to supply power wirelessly to the devices toease the physical connection.

F.Data Security and Privacy on public networksThe electronic transactions have been animportant part of many people. Thesetransactions should be very secure and to be usedby the authorized people. Virtual PrivateNetwork (VPN) provides good level of privacy.Also one can create a safe tunnel for sendingmessages on public network by using VPN. IV.PHYSICAL LAYER STRATEGIESFORWIRELESS COMMUNICATIONFollowing are the techniques widely used forwireless communications:1.Spread spectrum: This strategy is appliedto Wi-Fi and in some mobile network togain benefit of enhance reliability whichlessens the interference of wirelesscommunication channel. It also increasesbandwidth which results in achievingwireless spectrum for efficient sharing andutilization of bandwidth between multiplechannels. Moreover, spread spectrumincreases security by limiting thetransmissions from attackers.2.OFDM: Orthogonal Frequency DivisionMultiples is a type of multicarriermodulation that consists of several closelyplaced carriers. On application ofmodulation to the carrier, the side bandsspread to both the respective sides. With thisthere is a challenge for the receiver toreceive whole data and demodulate it. Butthis challenge is overcome in OFDM, on theoverlapping of sidebands; the receiver stillcan distinguish data without interference.3.Forward Error Correction: This is thestrategy to obtain error control intransmission of data where transmitter sendsredundant data to the receiver. With FECreceiver detects data that is free of errors.FEC can also be used for broadcastingpurpose, since it does not requirehandshaking between transmitter andreceiver.V.FIXEDAND RANDOM ACCESSTECHNIQUESFixed Access TechniquesSo as to connect subscribers to the telephonenetwork, the wireless technology that uses copper issaid to be fixed wireless technique. The fixedassigned access techniques mainly include TDMA,FDMA and CDMA.1.Time Division Multiple Access (TDMA):This technique is a digital wireless telephony transmission technique. It assignsa different time slot to different user on a determined frequency. It divides the channelinto three slots so as to carry large amount of data at one access. TDMA can transmit both data and voice with 64 kbps to 128 Mbps of data rates. TDMA is very cost efficient in terms of converting analog to digital signals. Since TDMA provides the fixed time slot to users, migrating from one cell, to another may cause disruption of services. Multipath distortion is highly observed in TDMA.2.Frequency Division Multiple Access (FDMA): A channel is considered as a frequency in FDMA where different signals are allocated to different channels. Each channel is assigned to only one user at one time.3.Code Division Multiple Access (CDMA): This technology uses spread spectrum technique where a specific frequency is allocated to every user. CDMA is a platformfor voice and data communication for 3G technologies. It has high capacity to serve more users per MHz of bandwidth. Random access Techniques:Random access techniques include ALOHA,CSMA, CSMA/CD, CSMA/CAAloha Protocol In this protocol, whenever a sender has to send data,it sends it over the channel regardless of who iscurrently using the channel. If the frame issuccessfully sent, it sends another frame to the

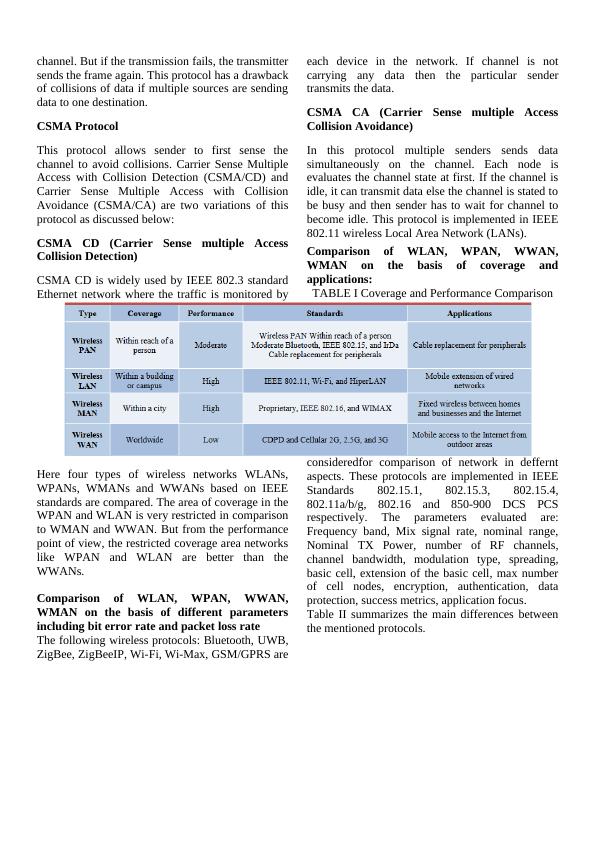
channel. But if the transmission fails, the transmittersends the frame again. This protocol has a drawbackof collisions of data if multiple sources are sendingdata to one destination.CSMA ProtocolThis protocol allows sender to first sense thechannel to avoid collisions. Carrier Sense MultipleAccess with Collision Detection (CSMA/CD) andCarrier Sense Multiple Access with CollisionAvoidance (CSMA/CA) are two variations of thisprotocol as discussed below:CSMA CD (Carrier Sense multiple AccessCollision Detection)CSMA CD is widely used by IEEE 802.3 standardEthernet network where the traffic is monitored byeach device in the network. If channel is notcarrying any data then the particular sendertransmits the data.CSMA CA (Carrier Sense multiple AccessCollision Avoidance)In this protocol multiple senders sends datasimultaneously on the channel. Each node isevaluates the channel state at first. If the channel isidle, it can transmit data else the channel is stated tobe busy and then sender has to wait for channel tobecome idle. This protocol is implemented in IEEE802.11 wireless Local Area Network (LANs).Comparison of WLAN, WPAN, WWAN,WMAN on the basis of coverage andapplications: TABLE I Coverage and Performance ComparisonHere four types of wireless networks WLANs,WPANs, WMANs and WWANs based on IEEEstandards are compared. The area of coverage in theWPAN and WLAN is very restricted in comparisonto WMAN and WWAN. But from the performancepoint of view, the restricted coverage area networkslike WPAN and WLAN are better than theWWANs. Comparison of WLAN, WPAN, WWAN,WMAN on the basis of different parametersincluding bit error rate and packet loss rateThe following wireless protocols: Bluetooth, UWB,ZigBee, ZigBeeIP, Wi-Fi, Wi-Max, GSM/GPRS areconsideredfor comparison of network in defferntaspects. These protocols are implemented in IEEEStandards 802.15.1, 802.15.3, 802.15.4,802.11a/b/g, 802.16 and 850-900 DCS PCSrespectively. The parameters evaluated are:Frequency band, Mix signal rate, nominal range,Nominal TX Power, number of RF channels,channel bandwidth, modulation type, spreading,basic cell, extension of the basic cell, max numberof cell nodes, encryption, authentication, dataprotection, success metrics, application focus.Table II summarizes the main differences betweenthe mentioned protocols.
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
(solved) Assignment on Networkinglg...
|27
|5649
|353
Network Design with Enhanced Securitylg...
|21
|2437
|494
Information Systems Networking Essentials Assignmentlg...
|14
|2601
|29
ISY202 Information System Assignment | Networking Assignmentlg...
|13
|2071
|71
Contrast Frequency Reuse in WLANlg...
|9
|1518
|344
Networking: Computer Networks and Protocolslg...
|32
|1380
|49
