Wireless Security: Analysis of a Hacking Incident in an Organization
VerifiedAdded on 2023/06/13
|16
|2669
|339
AI Summary
This report provides a full documentation of a live packet capture which got intercepted in relationship to a suspected member of the organization to be linked with some kind of “organized crime”. The report includes the websites accessed by the suspect, files downloaded, videos accessed, analysis of the files and videos accessed with relation to hacking, how the suspect gained access to the FTP server, commands run by the suspect on the FTP server, files on FTP server accessed/viewed by the suspect, files on FTP server modified/deleted by the suspect, information to suggest the suspect was working alone or as part of a team, and files timestamps before and after access to FTP server.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Wireless Security
[Student University]
[Student Name]
[Date]
[Student University]
[Student Name]
[Date]
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Executive Summary
When summoned upon ass wireless network forensic expert, our task is often to analyze the
incident that has transpired in the organization. The approach to such is by reviewing, analyzing and
providing enough evidence to prove presence or absence of a breach to the system. In our case, we
are to provide a full report and documentation of the live packet capture which got intercepted in
relationship to a suspected member of the organization to be linked with some kind of “organized
crime”. Wireshark was used to read and analyze the captured packets. From the analysis, files were
found that suggest a member ‘flynn’ of the organization was behind the hacking incident. The
suspect accessed the ftp server, downloaded files from it and modified others using owns logging
credentials. The suspect sent the data to colleague on the darkweb.(Tor Network)
mysterious_auto_companyX@darkwebsite.onion using the smtp protocol after the files on the ftp
server had been compromised.
When summoned upon ass wireless network forensic expert, our task is often to analyze the
incident that has transpired in the organization. The approach to such is by reviewing, analyzing and
providing enough evidence to prove presence or absence of a breach to the system. In our case, we
are to provide a full report and documentation of the live packet capture which got intercepted in
relationship to a suspected member of the organization to be linked with some kind of “organized
crime”. Wireshark was used to read and analyze the captured packets. From the analysis, files were
found that suggest a member ‘flynn’ of the organization was behind the hacking incident. The
suspect accessed the ftp server, downloaded files from it and modified others using owns logging
credentials. The suspect sent the data to colleague on the darkweb.(Tor Network)
mysterious_auto_companyX@darkwebsite.onion using the smtp protocol after the files on the ftp
server had been compromised.

Contents
Executive Summary.............................................................................................................................2
Contents................................................................................................................................................3
Introduction..........................................................................................................................................4
Websites Accessed By The Suspect.................................................................................................4
Files Downloaded By The Suspect...................................................................................................6
Executable Files:..........................................................................................................................6
Zip Files:.......................................................................................................................................6
Text Files:.....................................................................................................................................6
Videos Access By The Suspect.........................................................................................................6
Analysis Of The Files & Videos Accessed With Relation To Hacking............................................7
FTP Server........................................................................................................................................8
How The Suspect Gained Access To The FTP Server..................................................................8
Commands Run By The Suspect On The FTP Server & Description..........................................8
Files on FTP Server Modified / Deleted By The Suspect............................................................9
Information To Suggest The Suspect Was Working Alone Or As Part Of A Team......................9
Files Timestamps Before And After Access To FTP Server.......................................................11
Chain Of Custody For The Accessed And Downloaded Files.......................................................13
Chain Of Custody.......................................................................................................................13
Conclusion..........................................................................................................................................14
Appendix 1.........................................................................................................................................16
Executive Summary.............................................................................................................................2
Contents................................................................................................................................................3
Introduction..........................................................................................................................................4
Websites Accessed By The Suspect.................................................................................................4
Files Downloaded By The Suspect...................................................................................................6
Executable Files:..........................................................................................................................6
Zip Files:.......................................................................................................................................6
Text Files:.....................................................................................................................................6
Videos Access By The Suspect.........................................................................................................6
Analysis Of The Files & Videos Accessed With Relation To Hacking............................................7
FTP Server........................................................................................................................................8
How The Suspect Gained Access To The FTP Server..................................................................8
Commands Run By The Suspect On The FTP Server & Description..........................................8
Files on FTP Server Modified / Deleted By The Suspect............................................................9
Information To Suggest The Suspect Was Working Alone Or As Part Of A Team......................9
Files Timestamps Before And After Access To FTP Server.......................................................11
Chain Of Custody For The Accessed And Downloaded Files.......................................................13
Chain Of Custody.......................................................................................................................13
Conclusion..........................................................................................................................................14
Appendix 1.........................................................................................................................................16
Introduction
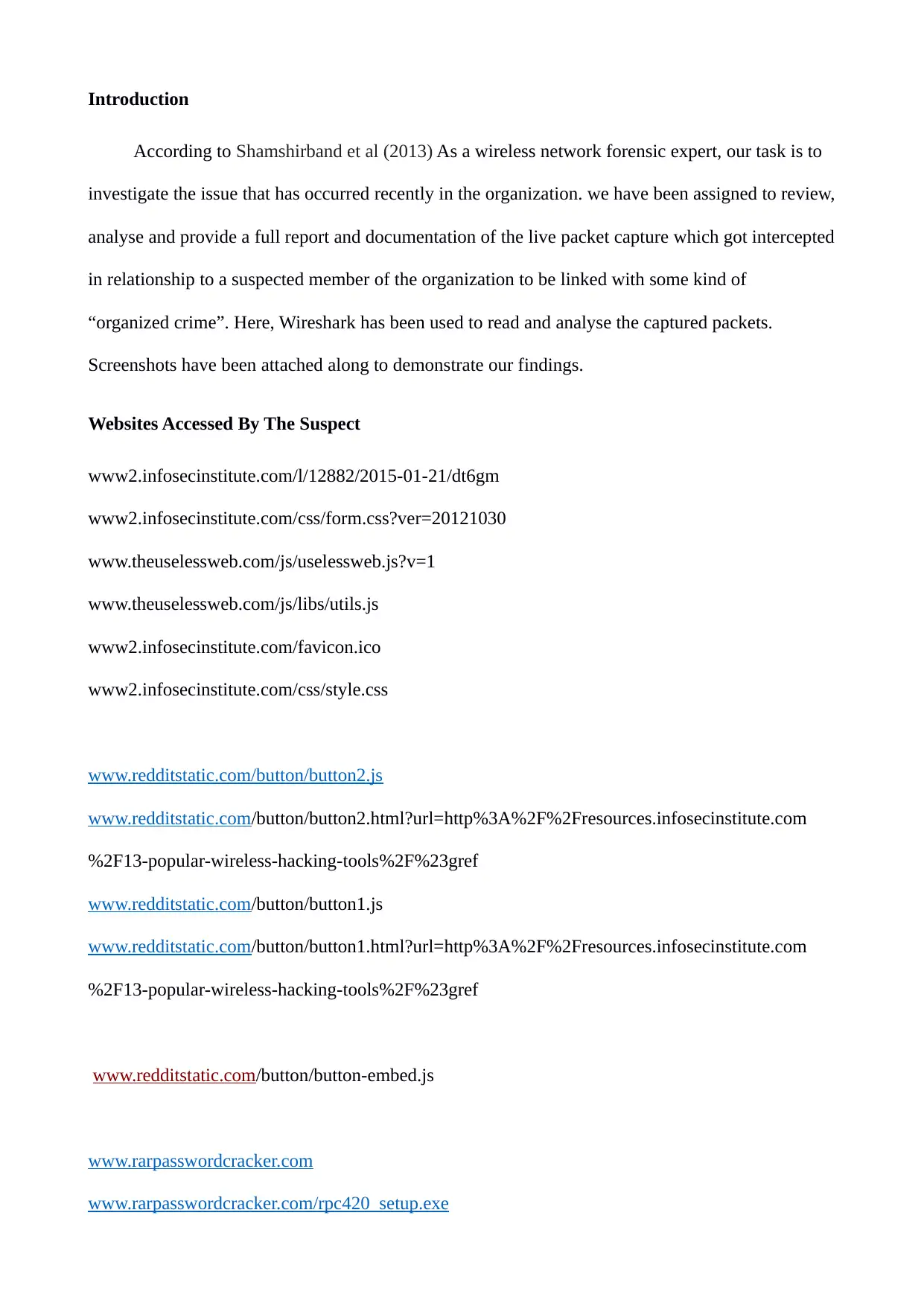
According to Shamshirband et al (2013) As a wireless network forensic expert, our task is to
investigate the issue that has occurred recently in the organization. we have been assigned to review,
analyse and provide a full report and documentation of the live packet capture which got intercepted
in relationship to a suspected member of the organization to be linked with some kind of
“organized crime”. Here, Wireshark has been used to read and analyse the captured packets.
Screenshots have been attached along to demonstrate our findings.
Websites Accessed By The Suspect
www2.infosecinstitute.com/l/12882/2015-01-21/dt6gm
www2.infosecinstitute.com/css/form.css?ver=20121030
www.theuselessweb.com/js/uselessweb.js?v=1
www.theuselessweb.com/js/libs/utils.js
www2.infosecinstitute.com/favicon.ico
www2.infosecinstitute.com/css/style.css
www.redditstatic.com/button/button2.js
www.redditstatic.com/button/button2.html?url=http%3A%2F%2Fresources.infosecinstitute.com
%2F13-popular-wireless-hacking-tools%2F%23gref
www.redditstatic.com/button/button1.js
www.redditstatic.com/button/button1.html?url=http%3A%2F%2Fresources.infosecinstitute.com
%2F13-popular-wireless-hacking-tools%2F%23gref
www.redditstatic.com/button/button-embed.js
www.rarpasswordcracker.com
www.rarpasswordcracker.com/rpc420_setup.exe
According to Shamshirband et al (2013) As a wireless network forensic expert, our task is to
investigate the issue that has occurred recently in the organization. we have been assigned to review,
analyse and provide a full report and documentation of the live packet capture which got intercepted
in relationship to a suspected member of the organization to be linked with some kind of
“organized crime”. Here, Wireshark has been used to read and analyse the captured packets.
Screenshots have been attached along to demonstrate our findings.
Websites Accessed By The Suspect
www2.infosecinstitute.com/l/12882/2015-01-21/dt6gm
www2.infosecinstitute.com/css/form.css?ver=20121030
www.theuselessweb.com/js/uselessweb.js?v=1
www.theuselessweb.com/js/libs/utils.js
www2.infosecinstitute.com/favicon.ico
www2.infosecinstitute.com/css/style.css
www.redditstatic.com/button/button2.js
www.redditstatic.com/button/button2.html?url=http%3A%2F%2Fresources.infosecinstitute.com
%2F13-popular-wireless-hacking-tools%2F%23gref
www.redditstatic.com/button/button1.js
www.redditstatic.com/button/button1.html?url=http%3A%2F%2Fresources.infosecinstitute.com
%2F13-popular-wireless-hacking-tools%2F%23gref
www.redditstatic.com/button/button-embed.js
www.rarpasswordcracker.com
www.rarpasswordcracker.com/rpc420_setup.exe
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
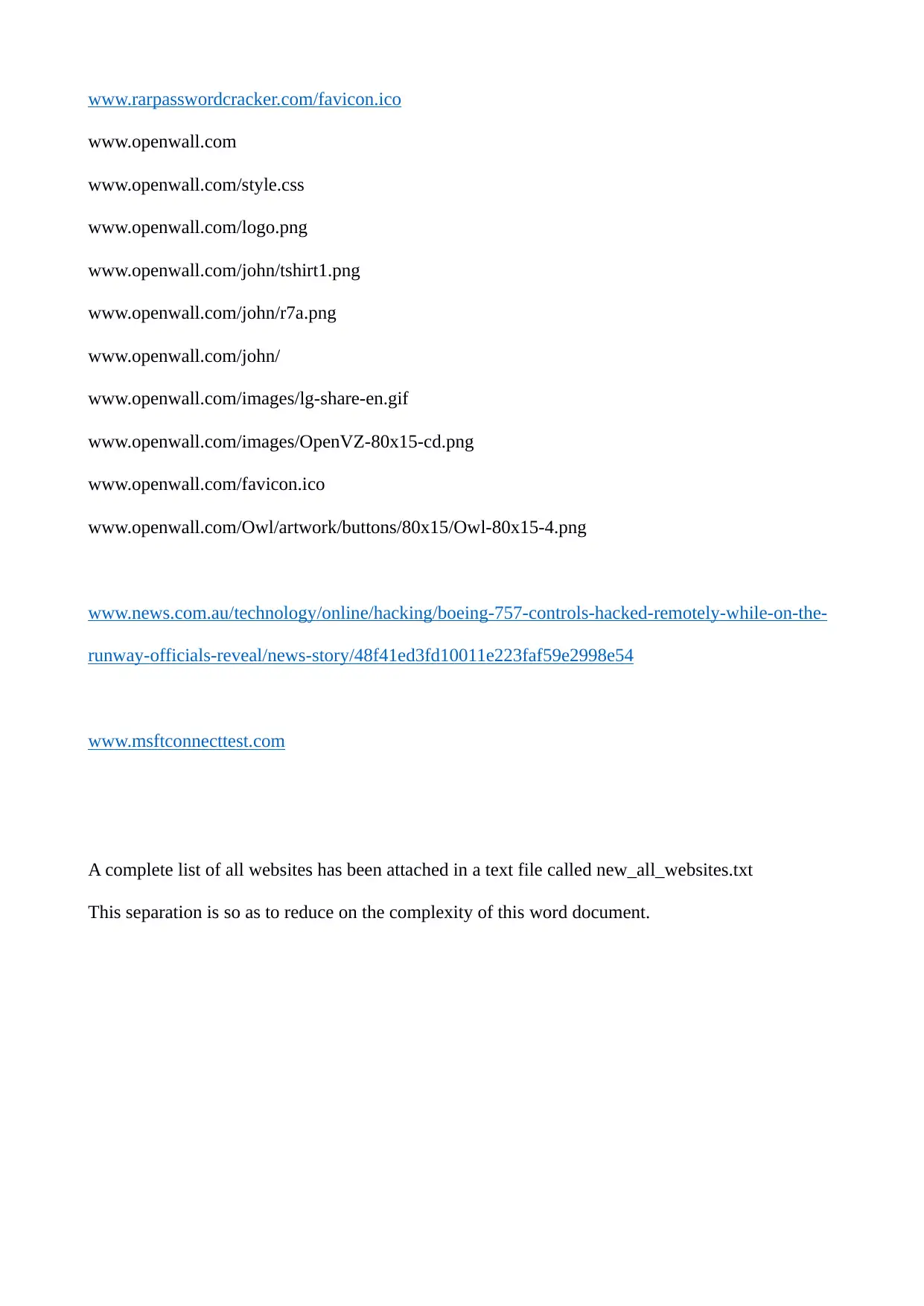
www.rarpasswordcracker.com/favicon.ico
www.openwall.com
www.openwall.com/style.css
www.openwall.com/logo.png
www.openwall.com/john/tshirt1.png
www.openwall.com/john/r7a.png
www.openwall.com/john/
www.openwall.com/images/lg-share-en.gif
www.openwall.com/images/OpenVZ-80x15-cd.png
www.openwall.com/favicon.ico
www.openwall.com/Owl/artwork/buttons/80x15/Owl-80x15-4.png
www.news.com.au/technology/online/hacking/boeing-757-controls-hacked-remotely-while-on-the-
runway-officials-reveal/news-story/48f41ed3fd10011e223faf59e2998e54
www.msftconnecttest.com
A complete list of all websites has been attached in a text file called new_all_websites.txt
This separation is so as to reduce on the complexity of this word document.
www.openwall.com
www.openwall.com/style.css
www.openwall.com/logo.png
www.openwall.com/john/tshirt1.png
www.openwall.com/john/r7a.png
www.openwall.com/john/
www.openwall.com/images/lg-share-en.gif
www.openwall.com/images/OpenVZ-80x15-cd.png
www.openwall.com/favicon.ico
www.openwall.com/Owl/artwork/buttons/80x15/Owl-80x15-4.png
www.news.com.au/technology/online/hacking/boeing-757-controls-hacked-remotely-while-on-the-
runway-officials-reveal/news-story/48f41ed3fd10011e223faf59e2998e54
www.msftconnecttest.com
A complete list of all websites has been attached in a text file called new_all_websites.txt
This separation is so as to reduce on the complexity of this word document.
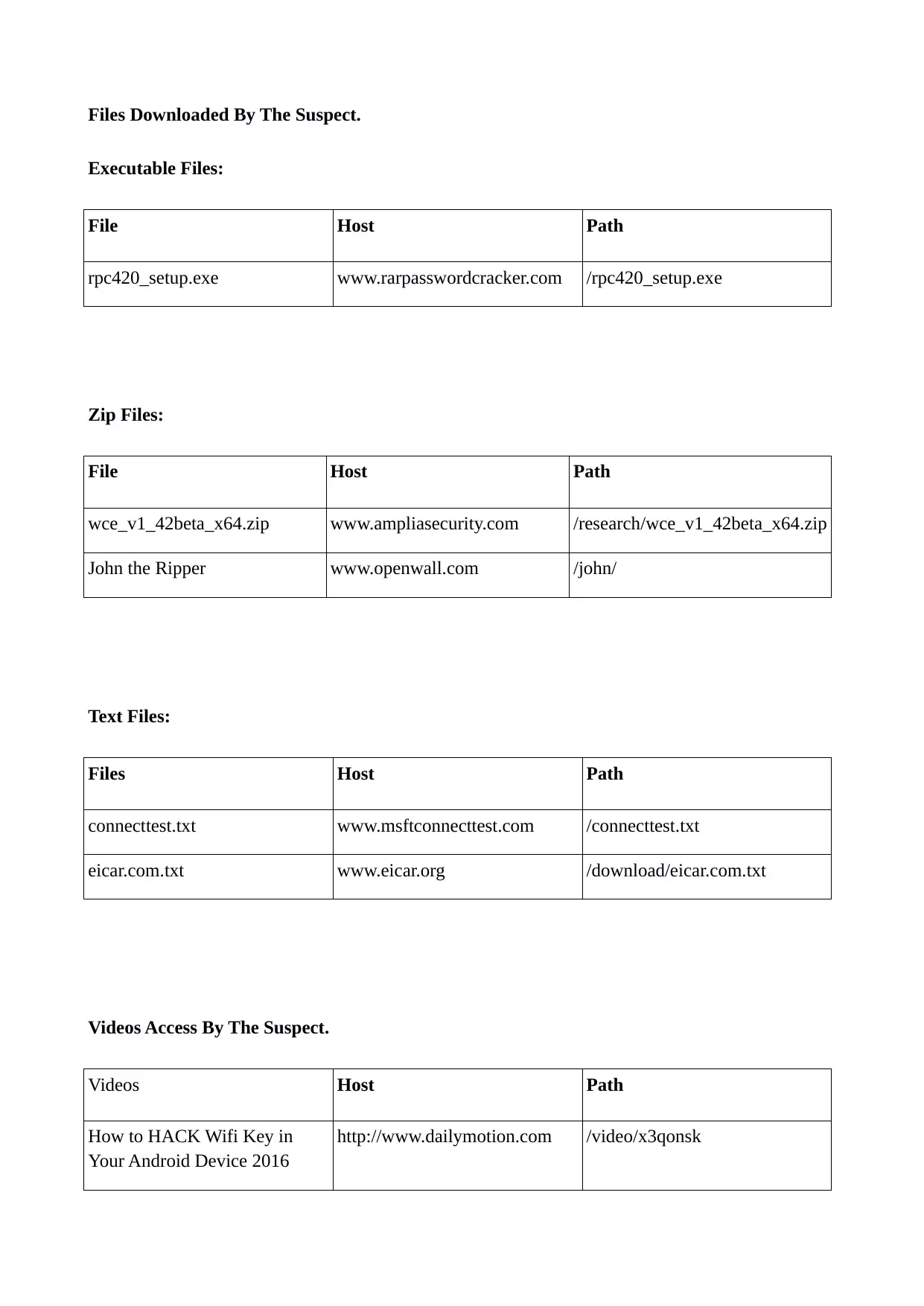
Files Downloaded By The Suspect.
Executable Files:
File Host Path
rpc420_setup.exe www.rarpasswordcracker.com /rpc420_setup.exe
Zip Files:
File Host Path
wce_v1_42beta_x64.zip www.ampliasecurity.com /research/wce_v1_42beta_x64.zip
John the Ripper www.openwall.com /john/
Text Files:
Files Host Path
connecttest.txt www.msftconnecttest.com /connecttest.txt
eicar.com.txt www.eicar.org /download/eicar.com.txt
Videos Access By The Suspect.
Videos Host Path
How to HACK Wifi Key in
Your Android Device 2016
http://www.dailymotion.com /video/x3qonsk
Executable Files:
File Host Path
rpc420_setup.exe www.rarpasswordcracker.com /rpc420_setup.exe
Zip Files:
File Host Path
wce_v1_42beta_x64.zip www.ampliasecurity.com /research/wce_v1_42beta_x64.zip
John the Ripper www.openwall.com /john/
Text Files:
Files Host Path
connecttest.txt www.msftconnecttest.com /connecttest.txt
eicar.com.txt www.eicar.org /download/eicar.com.txt
Videos Access By The Suspect.
Videos Host Path
How to HACK Wifi Key in
Your Android Device 2016
http://www.dailymotion.com /video/x3qonsk
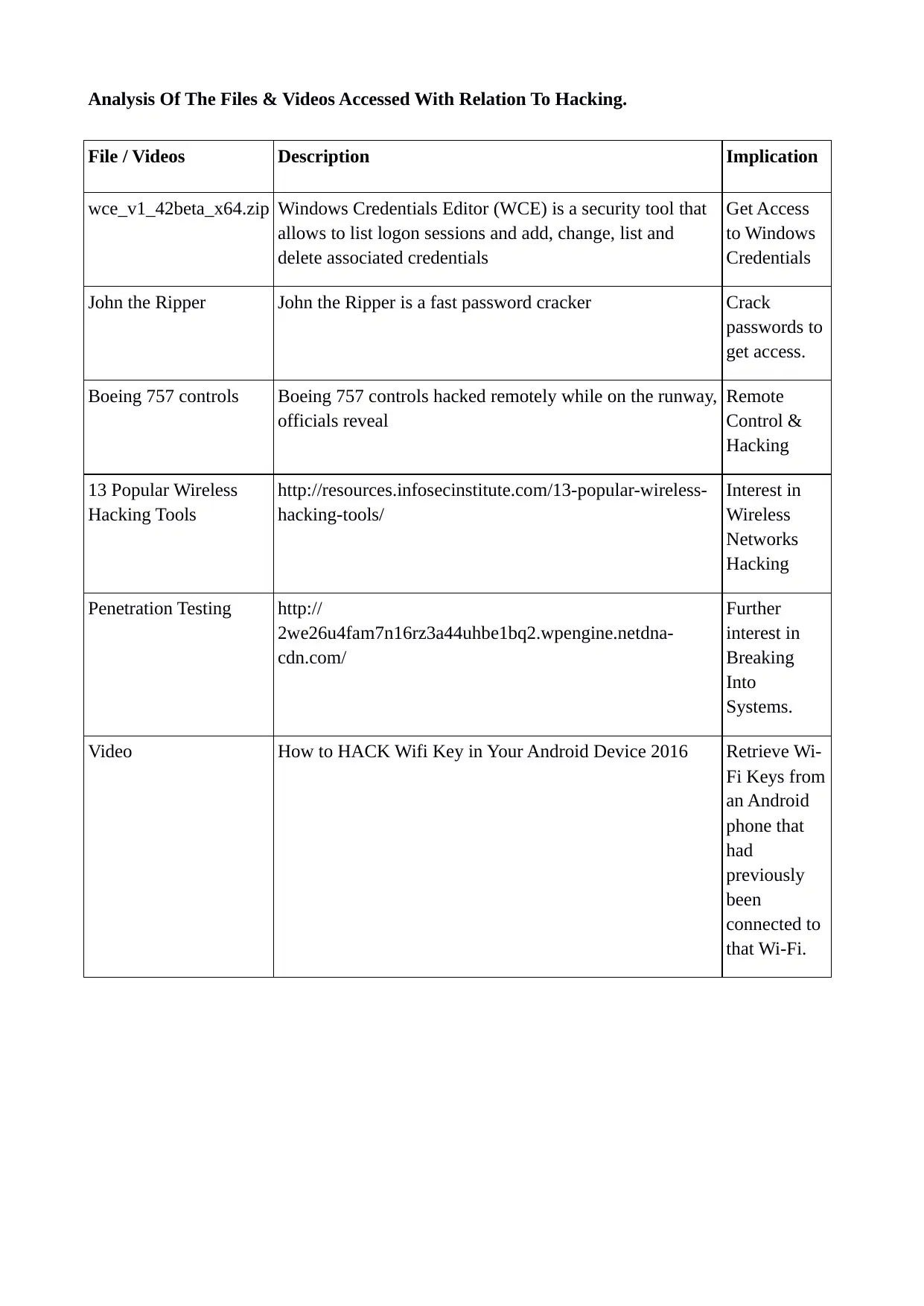
Analysis Of The Files & Videos Accessed With Relation To Hacking.
File / Videos Description Implication
wce_v1_42beta_x64.zip Windows Credentials Editor (WCE) is a security tool that
allows to list logon sessions and add, change, list and
delete associated credentials
Get Access
to Windows
Credentials
John the Ripper John the Ripper is a fast password cracker Crack
passwords to
get access.
Boeing 757 controls Boeing 757 controls hacked remotely while on the runway,
officials reveal
Remote
Control &
Hacking
13 Popular Wireless
Hacking Tools
http://resources.infosecinstitute.com/13-popular-wireless-
hacking-tools/
Interest in
Wireless
Networks
Hacking
Penetration Testing http://
2we26u4fam7n16rz3a44uhbe1bq2.wpengine.netdna-
cdn.com/
Further
interest in
Breaking
Into
Systems.
Video How to HACK Wifi Key in Your Android Device 2016 Retrieve Wi-
Fi Keys from
an Android
phone that
had
previously
been
connected to
that Wi-Fi.
File / Videos Description Implication
wce_v1_42beta_x64.zip Windows Credentials Editor (WCE) is a security tool that
allows to list logon sessions and add, change, list and
delete associated credentials
Get Access
to Windows
Credentials
John the Ripper John the Ripper is a fast password cracker Crack
passwords to
get access.
Boeing 757 controls Boeing 757 controls hacked remotely while on the runway,
officials reveal
Remote
Control &
Hacking
13 Popular Wireless
Hacking Tools
http://resources.infosecinstitute.com/13-popular-wireless-
hacking-tools/
Interest in
Wireless
Networks
Hacking
Penetration Testing http://
2we26u4fam7n16rz3a44uhbe1bq2.wpengine.netdna-
cdn.com/
Further
interest in
Breaking
Into
Systems.
Video How to HACK Wifi Key in Your Android Device 2016 Retrieve Wi-
Fi Keys from
an Android
phone that
had
previously
been
connected to
that Wi-Fi.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
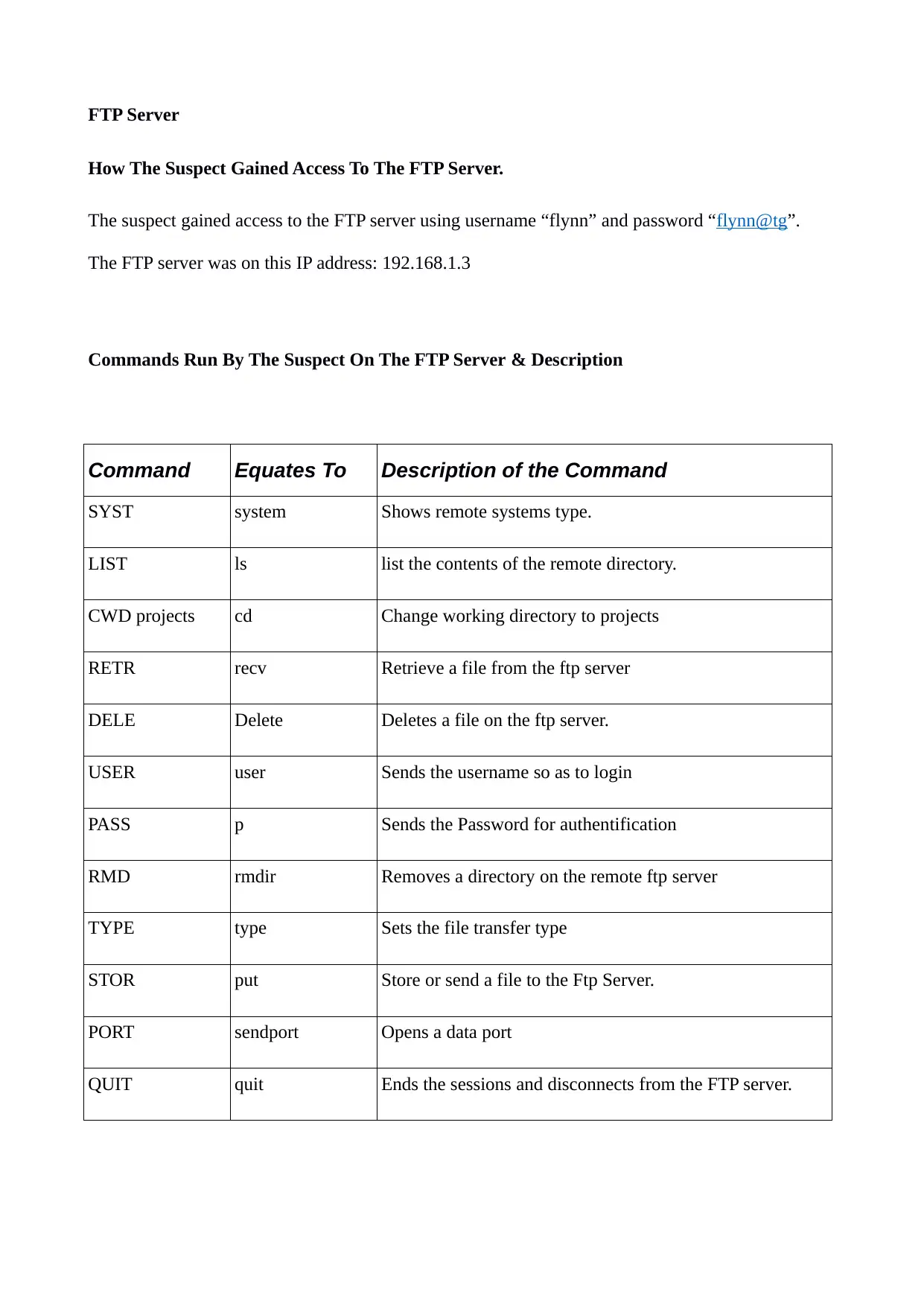
FTP Server
How The Suspect Gained Access To The FTP Server.
The suspect gained access to the FTP server using username “flynn” and password “flynn@tg”.
The FTP server was on this IP address: 192.168.1.3
Commands Run By The Suspect On The FTP Server & Description
Command Equates To Description of the Command
SYST system Shows remote systems type.
LIST ls list the contents of the remote directory.
CWD projects cd Change working directory to projects
RETR recv Retrieve a file from the ftp server
DELE Delete Deletes a file on the ftp server.
USER user Sends the username so as to login
PASS p Sends the Password for authentification
RMD rmdir Removes a directory on the remote ftp server
TYPE type Sets the file transfer type
STOR put Store or send a file to the Ftp Server.
PORT sendport Opens a data port
QUIT quit Ends the sessions and disconnects from the FTP server.
How The Suspect Gained Access To The FTP Server.
The suspect gained access to the FTP server using username “flynn” and password “flynn@tg”.
The FTP server was on this IP address: 192.168.1.3
Commands Run By The Suspect On The FTP Server & Description
Command Equates To Description of the Command
SYST system Shows remote systems type.
LIST ls list the contents of the remote directory.
CWD projects cd Change working directory to projects
RETR recv Retrieve a file from the ftp server
DELE Delete Deletes a file on the ftp server.
USER user Sends the username so as to login
PASS p Sends the Password for authentification
RMD rmdir Removes a directory on the remote ftp server
TYPE type Sets the file transfer type
STOR put Store or send a file to the Ftp Server.
PORT sendport Opens a data port
QUIT quit Ends the sessions and disconnects from the FTP server.

These commands have been derived from the ‘ftp_commands’ file, which contains commands that
the suspect used to access, copy, delete and upload files to and from the ftp server.
Files On FTP Server Accessed / Viewed By The Suspect.
i. Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
ii. rainbowfish-schematic.gif
iii. suppliers
iv. suppliers.txt
v. message.txt
Files on FTP Server Modified / Deleted By The Suspect.
i. Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg :deleted
ii. rainbowfish-schematic.gif :delete
iii. suppliers.txt :delete
iv. message.txt : :modified/uploaded
Information To Suggest The Suspect Was Working Alone Or As Part Of A Team.
evidence of suspicious emails
From The email sent to mysterious_auto_companyX@darkwebsite.onion, It is evident that the
suspect is part of a Team. The content of the suspicious email is as follows.
MAIL FROM: <cake@topgear.com>[46 bytes missing in capture file].DATA
SMTP 1542 C: les (disabled - work = | in progress).
…
…
the suspect used to access, copy, delete and upload files to and from the ftp server.
Files On FTP Server Accessed / Viewed By The Suspect.
i. Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
ii. rainbowfish-schematic.gif
iii. suppliers
iv. suppliers.txt
v. message.txt
Files on FTP Server Modified / Deleted By The Suspect.
i. Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg :deleted
ii. rainbowfish-schematic.gif :delete
iii. suppliers.txt :delete
iv. message.txt : :modified/uploaded
Information To Suggest The Suspect Was Working Alone Or As Part Of A Team.
evidence of suspicious emails
From The email sent to mysterious_auto_companyX@darkwebsite.onion, It is evident that the
suspect is part of a Team. The content of the suspicious email is as follows.
MAIL FROM: <cake@topgear.com>[46 bytes missing in capture file].DATA
SMTP 1542 C: les (disabled - work = | in progress).
…
…

MAIL FROM: <flynn.griffen@topgear.com>RCPT TO:
<mysterious_auto_companyX@darkwebsite.onion>From: "Flynn Griffen"
<flynn.griffen@topgear.com>
To: <mysterious_auto_companyX@darkwebsite.onion>
Subject: mission complete
Hello
I have the "package" you asked for, see you at the agreed location for extraction
Regards
F
----------------------------
Dear Top Gear Industries
We heard you have a cool project!
We like cool projects!
This schematic belongs to us now!
Bye!
<mysterious_auto_companyX@darkwebsite.onion>From: "Flynn Griffen"
<flynn.griffen@topgear.com>
To: <mysterious_auto_companyX@darkwebsite.onion>
Subject: mission complete
Hello
I have the "package" you asked for, see you at the agreed location for extraction
Regards
F
----------------------------
Dear Top Gear Industries
We heard you have a cool project!
We like cool projects!
This schematic belongs to us now!
Bye!
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

- Another automotive company...
______________________
< you got hacked, bro! >
Files Timestamps Before And After Access To FTP Server.
1st FTP Convo
738490 2018-03-11 14:45:02.857137 192.168.1.5192.168.1.3 TCP 110 41004 →
21 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=3844581442 TSecr=0
WS=128
Last FTp Convo
756930 2018-03-11 14:46:51.760876 192.168.1.3 192.168.1.5 TCP 102 21 →
41004 [ACK] Seq=3271 Ack=1129 Win=29056 Len=0 TSval=4018330563 TSecr=3844690336
764051 2018-03-11 14:47:06.173615192.168.1.5 74.53.140.153 SMTP 1542 C: les
(disabled - work = | in progress). | | Version 4.9.5.2 | * Added new option in class-browser: Use
colors | (available when right-clicking the class-browser | and selecting "View mode"). | * Dev-
C++ now traps access violation of your programs (and of itself too = | ;) | | Version 4.9.5.1 | *
Implemented the "File/Export/Project to HTML" function. | * Added "Tip of the day" system. | *
When running a source file in explorer, don't spawn new instance. | Instead open the file in an
already launched Dev-C++. | * Class-parser speed-up (50% to 85% improvement timed!!!) | *
Many code-completion updates. Now takes into account context, | class inheritance and visibility
(shows items only from files | #included directly or indirectly)! | * Caching of result set of code-
completion for speed-up. | * New option "Execution/Parameters" (and "Debug/Parameters"). | |
Version 4.9.5.0 (5.0 beta 5): | * CPU Window (still in development) | * ToDo list | * Backtrace in
______________________
< you got hacked, bro! >
Files Timestamps Before And After Access To FTP Server.
1st FTP Convo
738490 2018-03-11 14:45:02.857137 192.168.1.5192.168.1.3 TCP 110 41004 →
21 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=3844581442 TSecr=0
WS=128
Last FTp Convo
756930 2018-03-11 14:46:51.760876 192.168.1.3 192.168.1.5 TCP 102 21 →
41004 [ACK] Seq=3271 Ack=1129 Win=29056 Len=0 TSval=4018330563 TSecr=3844690336
764051 2018-03-11 14:47:06.173615192.168.1.5 74.53.140.153 SMTP 1542 C: les
(disabled - work = | in progress). | | Version 4.9.5.2 | * Added new option in class-browser: Use
colors | (available when right-clicking the class-browser | and selecting "View mode"). | * Dev-
C++ now traps access violation of your programs (and of itself too = | ;) | | Version 4.9.5.1 | *
Implemented the "File/Export/Project to HTML" function. | * Added "Tip of the day" system. | *
When running a source file in explorer, don't spawn new instance. | Instead open the file in an
already launched Dev-C++. | * Class-parser speed-up (50% to 85% improvement timed!!!) | *
Many code-completion updates. Now takes into account context, | class inheritance and visibility
(shows items only from files | #included directly or indirectly)! | * Caching of result set of code-
completion for speed-up. | * New option "Execution/Parameters" (and "Debug/Parameters"). | |
Version 4.9.5.0 (5.0 beta 5): | * CPU Window (still in development) | * ToDo list | * Backtrace in
debugging | * Run to cursor | * Folders in Project and Class Browser | * Send custom commands to
GDB | * Makefile can now be customized. | * Modified the behaviour of the -c param :=20 | -c
<config file directory> | * Saving of custom syntax parameter group | * Possibility of changing
compilers and tools filename. | * Many bug fixes | | | Version 4.9.4.1 (5.0 beta 4.1): | | * back to
gcc 2.95.3 | * Profiling support | * new update/packages checker (vUpdate) | * Lots of bugfixes | |
------=_NextPart_000_00
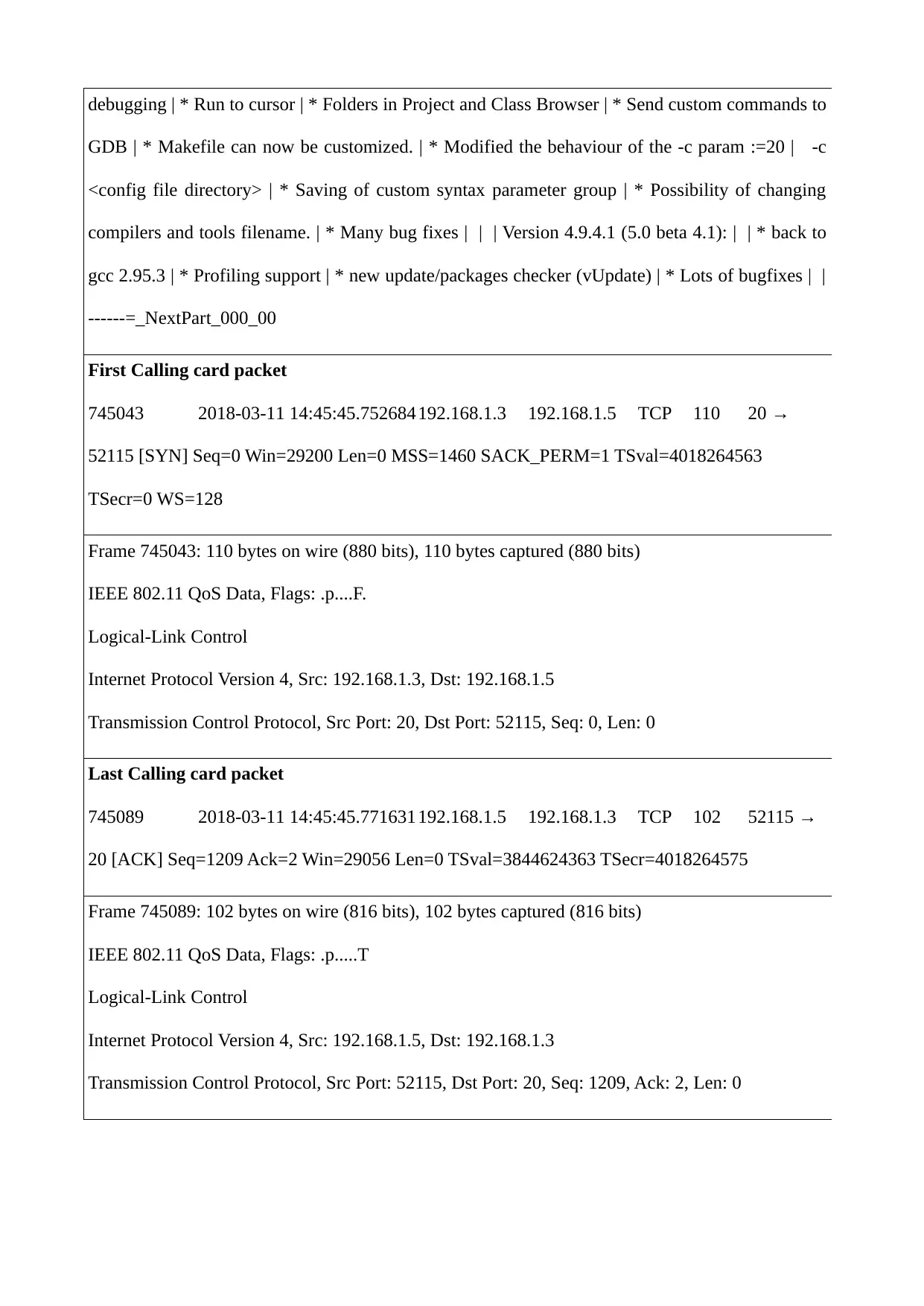
First Calling card packet
745043 2018-03-11 14:45:45.752684192.168.1.3 192.168.1.5 TCP 110 20 →
52115 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=4018264563
TSecr=0 WS=128
Frame 745043: 110 bytes on wire (880 bits), 110 bytes captured (880 bits)
IEEE 802.11 QoS Data, Flags: .p....F.
Logical-Link Control
Internet Protocol Version 4, Src: 192.168.1.3, Dst: 192.168.1.5
Transmission Control Protocol, Src Port: 20, Dst Port: 52115, Seq: 0, Len: 0
Last Calling card packet
745089 2018-03-11 14:45:45.771631192.168.1.5 192.168.1.3 TCP 102 52115 →
20 [ACK] Seq=1209 Ack=2 Win=29056 Len=0 TSval=3844624363 TSecr=4018264575
Frame 745089: 102 bytes on wire (816 bits), 102 bytes captured (816 bits)
IEEE 802.11 QoS Data, Flags: .p.....T
Logical-Link Control
Internet Protocol Version 4, Src: 192.168.1.5, Dst: 192.168.1.3
Transmission Control Protocol, Src Port: 52115, Dst Port: 20, Seq: 1209, Ack: 2, Len: 0
GDB | * Makefile can now be customized. | * Modified the behaviour of the -c param :=20 | -c
<config file directory> | * Saving of custom syntax parameter group | * Possibility of changing
compilers and tools filename. | * Many bug fixes | | | Version 4.9.4.1 (5.0 beta 4.1): | | * back to
gcc 2.95.3 | * Profiling support | * new update/packages checker (vUpdate) | * Lots of bugfixes | |
------=_NextPart_000_00
First Calling card packet
745043 2018-03-11 14:45:45.752684192.168.1.3 192.168.1.5 TCP 110 20 →
52115 [SYN] Seq=0 Win=29200 Len=0 MSS=1460 SACK_PERM=1 TSval=4018264563
TSecr=0 WS=128
Frame 745043: 110 bytes on wire (880 bits), 110 bytes captured (880 bits)
IEEE 802.11 QoS Data, Flags: .p....F.
Logical-Link Control
Internet Protocol Version 4, Src: 192.168.1.3, Dst: 192.168.1.5
Transmission Control Protocol, Src Port: 20, Dst Port: 52115, Seq: 0, Len: 0
Last Calling card packet
745089 2018-03-11 14:45:45.771631192.168.1.5 192.168.1.3 TCP 102 52115 →
20 [ACK] Seq=1209 Ack=2 Win=29056 Len=0 TSval=3844624363 TSecr=4018264575
Frame 745089: 102 bytes on wire (816 bits), 102 bytes captured (816 bits)
IEEE 802.11 QoS Data, Flags: .p.....T
Logical-Link Control
Internet Protocol Version 4, Src: 192.168.1.5, Dst: 192.168.1.3
Transmission Control Protocol, Src Port: 52115, Dst Port: 20, Seq: 1209, Ack: 2, Len: 0

Chain Of Custody For The Accessed And Downloaded Files.
Between 738490 2018-03-11 14:45:02.857137 and 2018-03-11 14:46:51.760876,
flynn starts by seeking help on how to crack windows passwords and Wi-Fi keys.
The suspect then views and downloads tools to carry out the work. These tools include ‘John the
Ripper’, wce_v1_42beta_x64.zip and rpc420_setup.exe.
The suspect connects to the ftp server on IP 192.168.1.3 using USER flynn and PASS flynn@tg
Suspect accesses Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
Suspect deletes Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
suspect uploads message.txt
suspect downloads rainbowfish-schematic.gif, suppliers and suppliers.txt
suspect deletes rainbowfish-schematic.gif and suppliers.txt
suspect uploads message.txt
At 14:47:06.173615 2018-03-11:
email sent from IP 92.168.1.5 to 74.53.140.153 with flynn.griffen@topgear.com as sender and
mysterious_auto_companyX@darkwebsite.onion as recipient and “mission complete’ as the subject
and this message “I have the “package” you asked for, see you at the agreed location for extraction”
Chain Of Custody
The Organization(Engineering Department) hands over the live packet
capture(Top_Gear_Eng_WIDS_Capture.pcap) for forensic audit by the wireless network forensic
expert.
Expert analyzes, reports and provides a full documentation of the live packet capture as evidence.
Between 738490 2018-03-11 14:45:02.857137 and 2018-03-11 14:46:51.760876,
flynn starts by seeking help on how to crack windows passwords and Wi-Fi keys.
The suspect then views and downloads tools to carry out the work. These tools include ‘John the
Ripper’, wce_v1_42beta_x64.zip and rpc420_setup.exe.
The suspect connects to the ftp server on IP 192.168.1.3 using USER flynn and PASS flynn@tg
Suspect accesses Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
Suspect deletes Top_Gear_Schematic_Project_Swordfish_Draft_3.jpg
suspect uploads message.txt
suspect downloads rainbowfish-schematic.gif, suppliers and suppliers.txt
suspect deletes rainbowfish-schematic.gif and suppliers.txt
suspect uploads message.txt
At 14:47:06.173615 2018-03-11:
email sent from IP 92.168.1.5 to 74.53.140.153 with flynn.griffen@topgear.com as sender and
mysterious_auto_companyX@darkwebsite.onion as recipient and “mission complete’ as the subject
and this message “I have the “package” you asked for, see you at the agreed location for extraction”
Chain Of Custody
The Organization(Engineering Department) hands over the live packet
capture(Top_Gear_Eng_WIDS_Capture.pcap) for forensic audit by the wireless network forensic
expert.
Expert analyzes, reports and provides a full documentation of the live packet capture as evidence.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
From the analysis of the live capture provided by the organization as a potential source of
evidence, files were found that suggest a member of the organization was behind the hacking
incident. It all begun the the member searching for specific tutorials on ethical hacking and cracking
so as to get access to the wireless network by retrieving the password from an android phone that
had previously been connected to that network, Lashkari(2009). The Suspect also browsed several
articles online that touch on the topic of hacking. John The Ripper, Cyborg ,
wce_v1_42beta_x64.zip (Windows Credentials Editor) and rpc420_setup.exe(Rar Password
Cracker) were download by the suspect. All these are tools used in offensive security and thus
imply bad intentions by the suspect. An Email sent to the Darkweb also leaves nothing to be desired
about the suspect.
From the analysis of the live capture provided by the organization as a potential source of
evidence, files were found that suggest a member of the organization was behind the hacking
incident. It all begun the the member searching for specific tutorials on ethical hacking and cracking
so as to get access to the wireless network by retrieving the password from an android phone that
had previously been connected to that network, Lashkari(2009). The Suspect also browsed several
articles online that touch on the topic of hacking. John The Ripper, Cyborg ,
wce_v1_42beta_x64.zip (Windows Credentials Editor) and rpc420_setup.exe(Rar Password
Cracker) were download by the suspect. All these are tools used in offensive security and thus
imply bad intentions by the suspect. An Email sent to the Darkweb also leaves nothing to be desired
about the suspect.

References
Lashkari, A. H., Danesh, M. M. S., & Samadi, B. (2009, August). A survey on wireless security
protocols (WEP, WPA and WPA2/802.11 i). In Computer Science and Information Technology,
2009. ICCSIT 2009. 2nd IEEE International Conference on (pp. 48-52). IEEE.
Shamshirband, S., Anuar, N. B., Kiah, M. L. M., & Patel, A. (2013). An appraisal and design of a
multi-agent system based cooperative wireless intrusion detection computational intelligence
technique. Engineering Applications of Artificial Intelligence, 26(9), 2105-2127.
Bibliography
Ammon, K., O'ferrell, C., Mitzen, W., Frasnelli, D., Wimble, L., Yang, Y., ... & Doten, R.
(2010). U.S. Patent No. 7,778,606. Washington, DC: U.S. Patent and Trademark Office.
Banerjee, U., Vashishtha, A., & Saxena, M. (2010). Evaluation of the Capabilities of WireShark as a
tool for Intrusion Detection. International Journal of computer applications, 6(7).
Casey, E. (2011). Digital evidence and computer crime: Forensic science, computers, and the
internet. Academic press.
Chappell, L., & Combs, G. (2010). Wireshark network analysis: the official Wireshark certified
network analyst study guide. Protocol Analysis Institute, Chappell University.
Hnatyshin, V. Y., & Lobo, A. F. (2008, March). Undergraduate data communications and
networking projects using opnet and wireshark software. In ACM SIGCSE Bulletin (Vol. 40, No. 1,
pp. 241-245). ACM.
López, J., & Zhou, J. (Eds.). (2008). Wireless sensor network security (Vol. 1). Ios Press.
Sanders, C. (2017). Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets & solutions.
McGraw-Hill Education Group.
Lashkari, A. H., Danesh, M. M. S., & Samadi, B. (2009, August). A survey on wireless security
protocols (WEP, WPA and WPA2/802.11 i). In Computer Science and Information Technology,
2009. ICCSIT 2009. 2nd IEEE International Conference on (pp. 48-52). IEEE.
Shamshirband, S., Anuar, N. B., Kiah, M. L. M., & Patel, A. (2013). An appraisal and design of a
multi-agent system based cooperative wireless intrusion detection computational intelligence
technique. Engineering Applications of Artificial Intelligence, 26(9), 2105-2127.
Bibliography
Ammon, K., O'ferrell, C., Mitzen, W., Frasnelli, D., Wimble, L., Yang, Y., ... & Doten, R.
(2010). U.S. Patent No. 7,778,606. Washington, DC: U.S. Patent and Trademark Office.
Banerjee, U., Vashishtha, A., & Saxena, M. (2010). Evaluation of the Capabilities of WireShark as a
tool for Intrusion Detection. International Journal of computer applications, 6(7).
Casey, E. (2011). Digital evidence and computer crime: Forensic science, computers, and the
internet. Academic press.
Chappell, L., & Combs, G. (2010). Wireshark network analysis: the official Wireshark certified
network analyst study guide. Protocol Analysis Institute, Chappell University.
Hnatyshin, V. Y., & Lobo, A. F. (2008, March). Undergraduate data communications and
networking projects using opnet and wireshark software. In ACM SIGCSE Bulletin (Vol. 40, No. 1,
pp. 241-245). ACM.
López, J., & Zhou, J. (Eds.). (2008). Wireless sensor network security (Vol. 1). Ios Press.
Sanders, C. (2017). Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Wright, J., & Cache, J. (2015). Hacking exposed wireless: wireless security secrets & solutions.
McGraw-Hill Education Group.

Appendix 1
1. Wireshark:
A network sniffer & analyser tool used to capture and analyse wired or wireless traffic packets. This
tool can be used by hackers, developers, network sysadmins, security researchers, incident response
or pentesters.
2. Wireless Intrusion Detection System(WIDS):
A WIDS monitors and analyzes user and system activities. It has the ability to recognize patterns of
known attacks, recognize anomalous network activities and detect policy violations for wireless
local area networks.
3. John the Ripper
This is a fast password cracker.
4. SMTP: Simple Mail Transfer Protocol
This is used to send messages from a mail client to a mail server or from one server to another.
5. FTP: File Transfer Protocol.
This is a protocol for exchanging files over the Internet.
6. FTP-Server:
This is a software application running the File Transfer Protocol.
1. Wireshark:
A network sniffer & analyser tool used to capture and analyse wired or wireless traffic packets. This
tool can be used by hackers, developers, network sysadmins, security researchers, incident response
or pentesters.
2. Wireless Intrusion Detection System(WIDS):
A WIDS monitors and analyzes user and system activities. It has the ability to recognize patterns of
known attacks, recognize anomalous network activities and detect policy violations for wireless
local area networks.
3. John the Ripper
This is a fast password cracker.
4. SMTP: Simple Mail Transfer Protocol
This is used to send messages from a mail client to a mail server or from one server to another.
5. FTP: File Transfer Protocol.
This is a protocol for exchanging files over the Internet.
6. FTP-Server:
This is a software application running the File Transfer Protocol.
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

