Project Plan: Implementation of Wireless Technology and Security
VerifiedAdded on 2023/05/30
|15
|2379
|236
Project
AI Summary
This project plan outlines the implementation of wireless technology, addressing key challenges and providing a structured approach to successful deployment. The plan begins with a project blog and weekly progress reports, followed by a detailed rationale, including the purpose, justification, and research questions. The conceptual framework identifies crucial variables for implementation, and the methodology includes qualitative research methods for analysis. The project addresses the problems of radio spectrum, manual interference, and power consumption. The plan also covers data collection methods (secondary data), ethical issues related to wireless technology security, and compliance requirements. A comprehensive work breakdown structure, risk analysis, and Gantt chart are included to manage the project's duration and tasks. The project aims to improve network security, enhance communication between devices, and reduce energy consumption, making it a valuable resource for students and professionals seeking to understand and implement wireless technology effectively. The project utilizes a poster and references to support its findings and recommendations.

Running head: EMERGING TECHNOLOGIES
EMERGING TECHNOLOGIES
Name of the Student
Name of the University
Author Note
EMERGING TECHNOLOGIES
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1EMERGING TECHNOLOGIES
Table of Contents
Title:...........................................................................................................................................3
Project Blog:...............................................................................................................................3
Weekly Progress reports plan.....................................................................................................3
Rationale....................................................................................................................................6
Purpose and justification............................................................................................................6
Research question.......................................................................................................................6
Conceptual Framework..............................................................................................................7
Methodology..............................................................................................................................7
Analysis..................................................................................................................................7
Research methods...................................................................................................................8
Data collection.......................................................................................................................9
Ethical issues..........................................................................................................................9
Compliance requirements.......................................................................................................9
Project plan...............................................................................................................................10
Poster....................................................................................................................................10
Work Breakdown Structure..................................................................................................11
Risk Analysis.......................................................................................................................11
Duration................................................................................................................................11
Gantt chart............................................................................................................................14
References................................................................................................................................15
Table of Contents
Title:...........................................................................................................................................3
Project Blog:...............................................................................................................................3
Weekly Progress reports plan.....................................................................................................3
Rationale....................................................................................................................................6
Purpose and justification............................................................................................................6
Research question.......................................................................................................................6
Conceptual Framework..............................................................................................................7
Methodology..............................................................................................................................7
Analysis..................................................................................................................................7
Research methods...................................................................................................................8
Data collection.......................................................................................................................9
Ethical issues..........................................................................................................................9
Compliance requirements.......................................................................................................9
Project plan...............................................................................................................................10
Poster....................................................................................................................................10
Work Breakdown Structure..................................................................................................11
Risk Analysis.......................................................................................................................11
Duration................................................................................................................................11
Gantt chart............................................................................................................................14
References................................................................................................................................15
2EMERGING TECHNOLOGIES
Title: Implementation of wireless technology
Project Blog:
<Please provide the address>
Weekly Progress reports plan
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 7 Date: <Please Fill>
Planning
Milestone Planned Actual Comment
Assessment 3
completion
the collected
resources is being
analyzed with the
use of annotated
bibliography
Analysis is being
completed
I completed my
project successfully
and delivered the
analysis using
annotated
bibliography
Issues
Description Date Action results Finished
Quality of the
analysis might lack
as compared to
expectation
<Please fill> - Y
Title: Implementation of wireless technology
Project Blog:
<Please provide the address>
Weekly Progress reports plan
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 7 Date: <Please Fill>
Planning
Milestone Planned Actual Comment
Assessment 3
completion
the collected
resources is being
analyzed with the
use of annotated
bibliography
Analysis is being
completed
I completed my
project successfully
and delivered the
analysis using
annotated
bibliography
Issues
Description Date Action results Finished
Quality of the
analysis might lack
as compared to
expectation
<Please fill> - Y
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3EMERGING TECHNOLOGIES
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 8 Date: <Please Fill>
Planning
Milestone Planned Actual Comment
Assessment 3 upload Keep up to date with
the lectures and
knowledge gained in
the class
Uploaded
assessment 3
I get to know about
the criticalness of
the annotated
bibliography and
data analysis
Issues
Description Date Action results Finished
Less reliable papers <Please fill> Annotated
bibliography is done
for completing the
research
Y
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 9 Date: <Please Fill>
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 8 Date: <Please Fill>
Planning
Milestone Planned Actual Comment
Assessment 3 upload Keep up to date with
the lectures and
knowledge gained in
the class
Uploaded
assessment 3
I get to know about
the criticalness of
the annotated
bibliography and
data analysis
Issues
Description Date Action results Finished
Less reliable papers <Please fill> Annotated
bibliography is done
for completing the
research
Y
Name: <Please Fill>
Project title: Implementation of wireless technology
Week No: 9 Date: <Please Fill>
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4EMERGING TECHNOLOGIES
Planning
Milestone Planned Actual Comment
Complete Quiz The gathered
knowledge will help
in gaining better
marks
Completed online
quiz
-
Issues
Description Date Action results Finished
Less marks <Please fill> Done the online quiz Y
Rationale
The aim of the report is to develop a project plan that will be able to meet the
requirements and needs associated with implementation of a wireless technologies. The
project plan will describe a plan that will organize the implementation process in an effective
way. With a good implementation technology the project can be successfully completed.
Project problem domain
The problem related to the Capstone project includes
Radio spectrum
Manual interference
Power consumption relating to storage device
Planning
Milestone Planned Actual Comment
Complete Quiz The gathered
knowledge will help
in gaining better
marks
Completed online
quiz
-
Issues
Description Date Action results Finished
Less marks <Please fill> Done the online quiz Y
Rationale
The aim of the report is to develop a project plan that will be able to meet the
requirements and needs associated with implementation of a wireless technologies. The
project plan will describe a plan that will organize the implementation process in an effective
way. With a good implementation technology the project can be successfully completed.
Project problem domain
The problem related to the Capstone project includes
Radio spectrum
Manual interference
Power consumption relating to storage device

5EMERGING TECHNOLOGIES
Purpose and justification
The aim of the report is to solve the problem faced with the implementation of
wireless technology. The main problem faced with the implementation of this project is with
the security of radio spectrum and manual interferences directly effects the user. Apart from
this another problem that can affect the domain is related to the power consumption. This
report will help in understanding and facilitating the enhanced way of communicating
without any kind of barrier involved in this sector.
Research question
Question 1: how the energy consumption can be decreased in sector of implementation?
Question 2: how the communication would be prevailing between different devices?
Conceptual Framework
Conceptual framework is used to represent the researcher’s way of examining the
phenomenon. This will describe the actions taken by the researcher in order to frame the
requirements needed to complete the study. The framework includes identifying the specific
variables important for implementation of wireless technology. There are total 8 categories
that lies within the conceptual framework, this includes:
The experience of presence faced within the environment
Environment itself
The task that is on focus
The activities performed by each participants associated with the project
The rules followed by the members while interacting within the environment
Purpose and justification
The aim of the report is to solve the problem faced with the implementation of
wireless technology. The main problem faced with the implementation of this project is with
the security of radio spectrum and manual interferences directly effects the user. Apart from
this another problem that can affect the domain is related to the power consumption. This
report will help in understanding and facilitating the enhanced way of communicating
without any kind of barrier involved in this sector.
Research question
Question 1: how the energy consumption can be decreased in sector of implementation?
Question 2: how the communication would be prevailing between different devices?
Conceptual Framework
Conceptual framework is used to represent the researcher’s way of examining the
phenomenon. This will describe the actions taken by the researcher in order to frame the
requirements needed to complete the study. The framework includes identifying the specific
variables important for implementation of wireless technology. There are total 8 categories
that lies within the conceptual framework, this includes:
The experience of presence faced within the environment
Environment itself
The task that is on focus
The activities performed by each participants associated with the project
The rules followed by the members while interacting within the environment
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6EMERGING TECHNOLOGIES
Methodology
Analysis
Wireless technology is used for dynamic research domain. With the implementation
of wireless technology the network security can be improved. Another reason of
implementing wireless technology are it offers latest encryption. The problems like hacking
snooping can be avoided with the use of strong password and with implementation of better
hardware and software security (Wang, et al., 2014). The amount of mobility gets increased
with the use of wireless technology. With the use of wireless technology productivity can be
increased as well. Moreover as there is no wires involved in the connection of this network
the chances of getting tripped over any cables reduces. The aim of the report is to analyse the
process of implementing wireless communication in the network (Smith, 2015). There are
several technology included within the wireless protocols. This includes WLAN, WPA,
WEP, Wi-Fi and other wireless broadband. Wireless technologies are used to describe the
communication in which the electromagnetic waves are used rather than wires. There are
several protocols that are needed to be maintained while implementing wireless technologies.
With the use of wireless infrastructure networks can be managed efficiently. Before
implementing wireless technology, this becomes necessary to understand about the benefits
offered by these technology. The way wireless technology will help in increasing the
productivity needs to be clear. Wireless technology offers many benefits such as flexible,
affordable and efficient. Secondly, it is necessary to plan the implementation of wireless
technology. These includes understanding the investment and calculating the profits they may
return. After assessing the implementation features and the necessary capabilities, the plan
needs to be implemented. The wireless communication after implementation needs to include
some security features that will help in protecting the technology and will secure the
communication. This includes WEP encryption, MAC addressing and traditional VPN
Methodology
Analysis
Wireless technology is used for dynamic research domain. With the implementation
of wireless technology the network security can be improved. Another reason of
implementing wireless technology are it offers latest encryption. The problems like hacking
snooping can be avoided with the use of strong password and with implementation of better
hardware and software security (Wang, et al., 2014). The amount of mobility gets increased
with the use of wireless technology. With the use of wireless technology productivity can be
increased as well. Moreover as there is no wires involved in the connection of this network
the chances of getting tripped over any cables reduces. The aim of the report is to analyse the
process of implementing wireless communication in the network (Smith, 2015). There are
several technology included within the wireless protocols. This includes WLAN, WPA,
WEP, Wi-Fi and other wireless broadband. Wireless technologies are used to describe the
communication in which the electromagnetic waves are used rather than wires. There are
several protocols that are needed to be maintained while implementing wireless technologies.
With the use of wireless infrastructure networks can be managed efficiently. Before
implementing wireless technology, this becomes necessary to understand about the benefits
offered by these technology. The way wireless technology will help in increasing the
productivity needs to be clear. Wireless technology offers many benefits such as flexible,
affordable and efficient. Secondly, it is necessary to plan the implementation of wireless
technology. These includes understanding the investment and calculating the profits they may
return. After assessing the implementation features and the necessary capabilities, the plan
needs to be implemented. The wireless communication after implementation needs to include
some security features that will help in protecting the technology and will secure the
communication. This includes WEP encryption, MAC addressing and traditional VPN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7EMERGING TECHNOLOGIES
securities control. The report has discussed about the problem domains associated with the
implementation of wireless technology. This becomes essential to develop a wireless
technology that will energy efficient. The need to maintain the energy efficiency in wireless
technology are due to the design problem, green technology policy and cost (Marinčić,
Kerner & Šimunić, 2016). The way energy can be saved includes active/sleep modes,
directional antenna, schedule management, interference management, cognitive radio and
high transmission speed. In order to improve the communication between different devices
implementation of internet of things will be beneficial.
Research methods
There are two types of research method qualitative and quantitative. Qualitative
research is a research that includes investigative research. This includes providing a solution
to the problem faced while working with this project. The research includes collection of data
that varies from semi structured to unstructured techniques. This includes looking at the non-
numerical data. There are several sources that incudes artifacts, participant’s observation and
archival records. Quantitative research is done with the help of statistical data and with
developing questionaries’ and conducting surveys (Lewis, 2015). There are four types of
quantitative research this are experimental, descriptive, correlation and quasi experimental. In
this project qualitative research method is being used. This report has included the budget for
developing the plan in detail with Gantt chart.
Data collection
Data collection method used in this report is secondary. In this method the analysis is
doe on already collected data (Hanvey, 2018). The sources used for secondary data method
collection includes data collected from research papers, organizational departments and
information collected by governments.
securities control. The report has discussed about the problem domains associated with the
implementation of wireless technology. This becomes essential to develop a wireless
technology that will energy efficient. The need to maintain the energy efficiency in wireless
technology are due to the design problem, green technology policy and cost (Marinčić,
Kerner & Šimunić, 2016). The way energy can be saved includes active/sleep modes,
directional antenna, schedule management, interference management, cognitive radio and
high transmission speed. In order to improve the communication between different devices
implementation of internet of things will be beneficial.
Research methods
There are two types of research method qualitative and quantitative. Qualitative
research is a research that includes investigative research. This includes providing a solution
to the problem faced while working with this project. The research includes collection of data
that varies from semi structured to unstructured techniques. This includes looking at the non-
numerical data. There are several sources that incudes artifacts, participant’s observation and
archival records. Quantitative research is done with the help of statistical data and with
developing questionaries’ and conducting surveys (Lewis, 2015). There are four types of
quantitative research this are experimental, descriptive, correlation and quasi experimental. In
this project qualitative research method is being used. This report has included the budget for
developing the plan in detail with Gantt chart.
Data collection
Data collection method used in this report is secondary. In this method the analysis is
doe on already collected data (Hanvey, 2018). The sources used for secondary data method
collection includes data collected from research papers, organizational departments and
information collected by governments.

8EMERGING TECHNOLOGIES
Ethical issues
There are several ethical issues that are faced while implementing wireless
technology. Wireless technology are does not provide much security, thus they are vulnerable
to attack. This becomes essential to maintain the security otherwise unauthorized person will
get access to the information transmitted within the devices (Yang, et al., 2015). This act is
unethical and thus needs to be taken care. Apart from these squatters impact the wireless
networks a lot. While implementing wireless technologies the organization needs to
understand that it is being ethically used and efficiently implemented.
Compliance requirements
Compliance requirements are referred to working by the rule such as following some
policy, specification, law or standard. Violation of this requirements may lead to legal
punishments and also includes federal fines. There are several laws and regulations that are
applicable for federal assistance. There are several compliance requirements this includes:
activities allowed or unallowed, allowable cost principles, cash management, Davis Bacon
Act, eligibility equipment and real property management , matching, level of effort,
marketing, period of availability of federal funds, procurement and suspension and
debarment, program income , real property acquisition and reallocation assistance ,
reporting , sub recipient monitoring and special tests and provisions. If the project
implemented in this report fulfil all the requirements than only it is eligible to be
implemented. As violation of this may will lead to legal actions on the project managers.
Ethical issues
There are several ethical issues that are faced while implementing wireless
technology. Wireless technology are does not provide much security, thus they are vulnerable
to attack. This becomes essential to maintain the security otherwise unauthorized person will
get access to the information transmitted within the devices (Yang, et al., 2015). This act is
unethical and thus needs to be taken care. Apart from these squatters impact the wireless
networks a lot. While implementing wireless technologies the organization needs to
understand that it is being ethically used and efficiently implemented.
Compliance requirements
Compliance requirements are referred to working by the rule such as following some
policy, specification, law or standard. Violation of this requirements may lead to legal
punishments and also includes federal fines. There are several laws and regulations that are
applicable for federal assistance. There are several compliance requirements this includes:
activities allowed or unallowed, allowable cost principles, cash management, Davis Bacon
Act, eligibility equipment and real property management , matching, level of effort,
marketing, period of availability of federal funds, procurement and suspension and
debarment, program income , real property acquisition and reallocation assistance ,
reporting , sub recipient monitoring and special tests and provisions. If the project
implemented in this report fulfil all the requirements than only it is eligible to be
implemented. As violation of this may will lead to legal actions on the project managers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9EMERGING TECHNOLOGIES
Project plan
Poster
Project plan
Poster
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10EMERGING TECHNOLOGIES
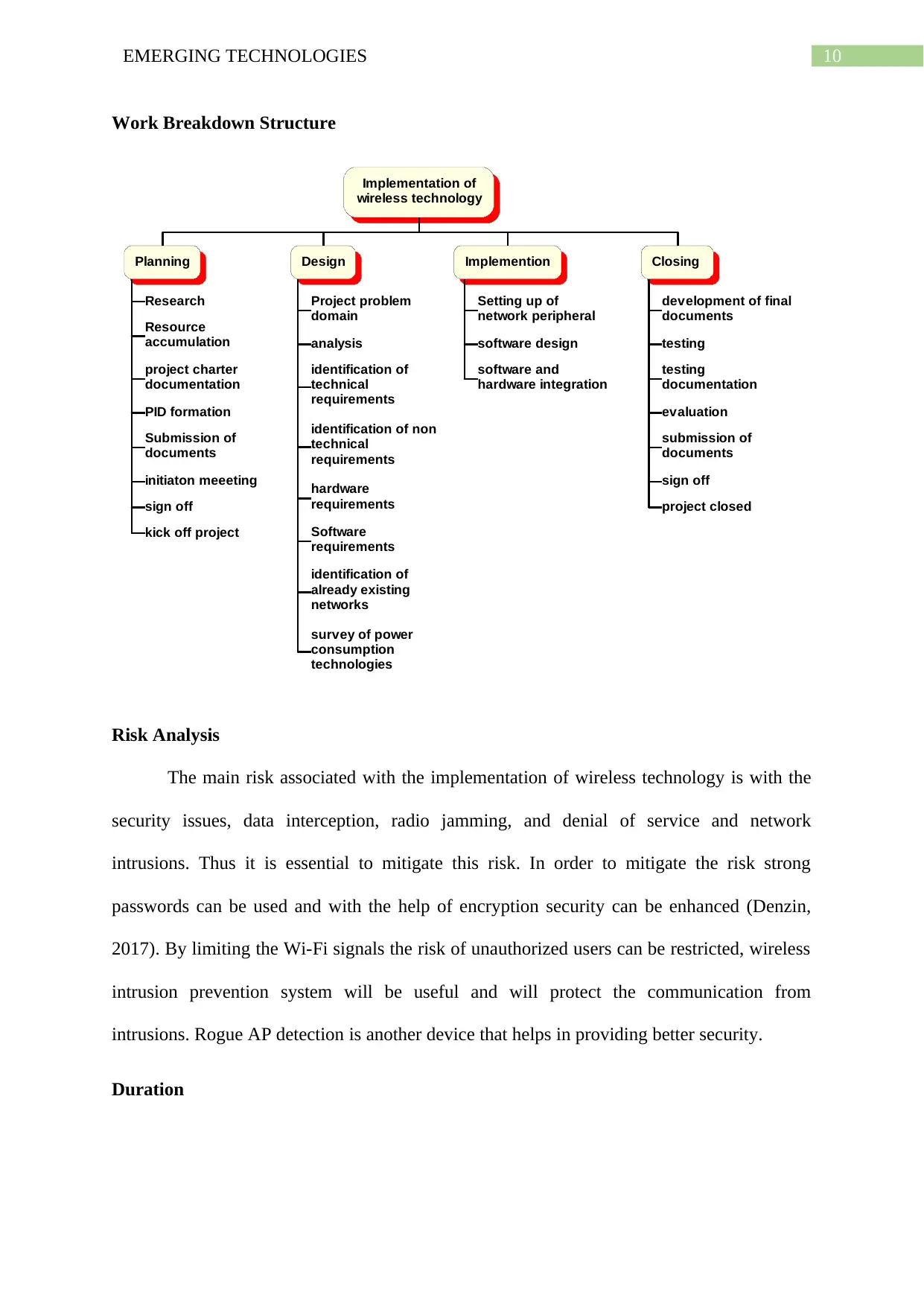
Work Breakdown Structure
Implementation of
wireless technology
Planning
Research
Resource
accumulation
project charter
documentation
PID formation
Submission of
documents
initiaton meeeting
sign off
kick off project
Design
Project problem
domain
analysis
identification of
technical
requirements
identification of non
technical
requirements
hardware
requirements
Software
requirements
identification of
already existing
networks
survey of power
consumption
technologies
Implemention
Setting up of
network peripheral
software design
software and
hardware integration
Closing
development of final
documents
testing
testing
documentation
evaluation
submission of
documents
sign off
project closed
Risk Analysis
The main risk associated with the implementation of wireless technology is with the
security issues, data interception, radio jamming, and denial of service and network
intrusions. Thus it is essential to mitigate this risk. In order to mitigate the risk strong
passwords can be used and with the help of encryption security can be enhanced (Denzin,
2017). By limiting the Wi-Fi signals the risk of unauthorized users can be restricted, wireless
intrusion prevention system will be useful and will protect the communication from
intrusions. Rogue AP detection is another device that helps in providing better security.
Duration
Work Breakdown Structure
Implementation of
wireless technology
Planning
Research
Resource
accumulation
project charter
documentation
PID formation
Submission of
documents
initiaton meeeting
sign off
kick off project
Design
Project problem
domain
analysis
identification of
technical
requirements
identification of non
technical
requirements
hardware
requirements
Software
requirements
identification of
already existing
networks
survey of power
consumption
technologies
Implemention
Setting up of
network peripheral
software design
software and
hardware integration
Closing
development of final
documents
testing
testing
documentation
evaluation
submission of
documents
sign off
project closed
Risk Analysis
The main risk associated with the implementation of wireless technology is with the
security issues, data interception, radio jamming, and denial of service and network
intrusions. Thus it is essential to mitigate this risk. In order to mitigate the risk strong
passwords can be used and with the help of encryption security can be enhanced (Denzin,
2017). By limiting the Wi-Fi signals the risk of unauthorized users can be restricted, wireless
intrusion prevention system will be useful and will protect the communication from
intrusions. Rogue AP detection is another device that helps in providing better security.
Duration
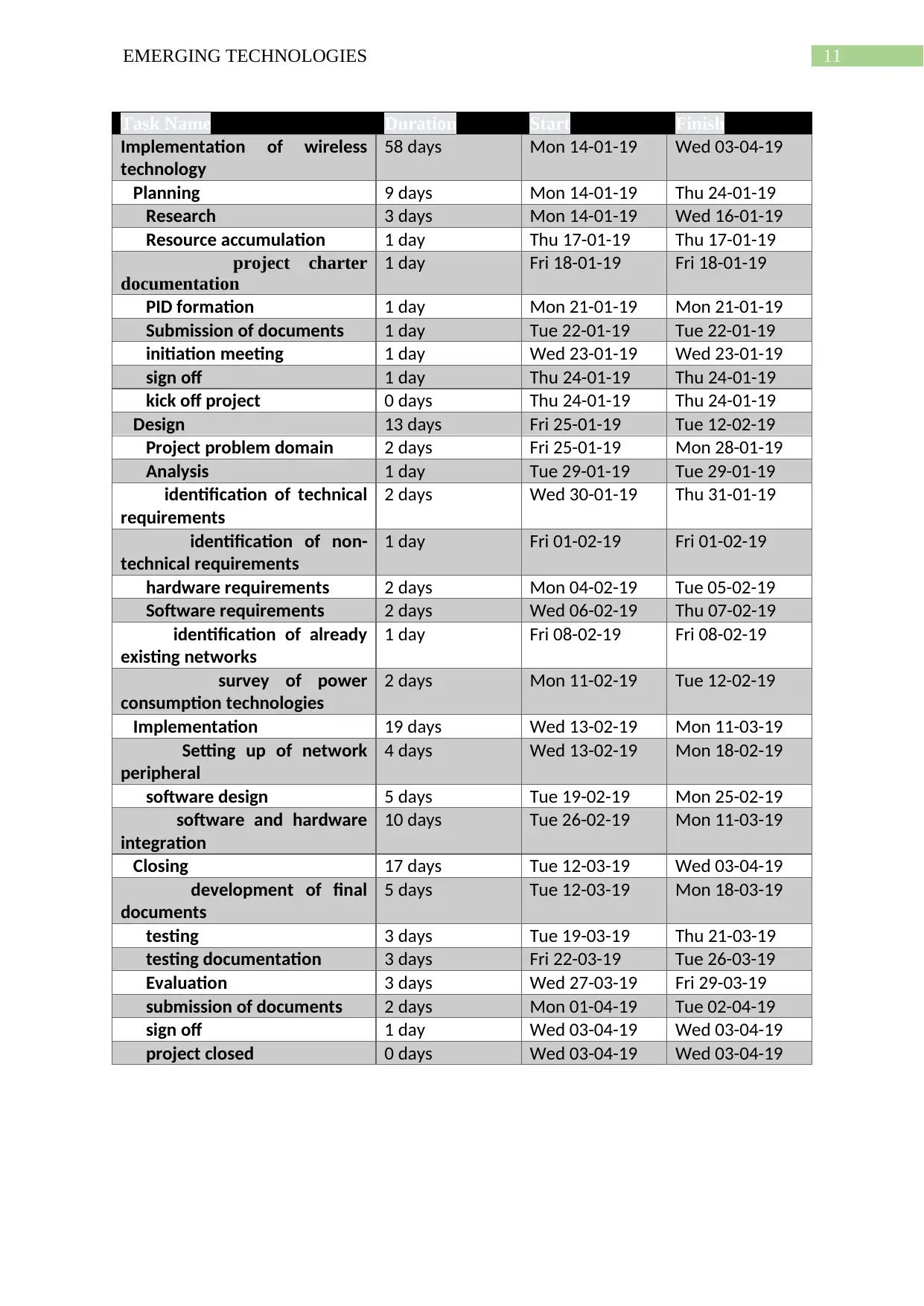
11EMERGING TECHNOLOGIES
Task Name Duration Start Finish
Implementation of wireless
technology
58 days Mon 14-01-19 Wed 03-04-19
Planning 9 days Mon 14-01-19 Thu 24-01-19
Research 3 days Mon 14-01-19 Wed 16-01-19
Resource accumulation 1 day Thu 17-01-19 Thu 17-01-19
project charter
documentation
1 day Fri 18-01-19 Fri 18-01-19
PID formation 1 day Mon 21-01-19 Mon 21-01-19
Submission of documents 1 day Tue 22-01-19 Tue 22-01-19
initiation meeting 1 day Wed 23-01-19 Wed 23-01-19
sign off 1 day Thu 24-01-19 Thu 24-01-19
kick off project 0 days Thu 24-01-19 Thu 24-01-19
Design 13 days Fri 25-01-19 Tue 12-02-19
Project problem domain 2 days Fri 25-01-19 Mon 28-01-19
Analysis 1 day Tue 29-01-19 Tue 29-01-19
identification of technical
requirements
2 days Wed 30-01-19 Thu 31-01-19
identification of non-
technical requirements
1 day Fri 01-02-19 Fri 01-02-19
hardware requirements 2 days Mon 04-02-19 Tue 05-02-19
Software requirements 2 days Wed 06-02-19 Thu 07-02-19
identification of already
existing networks
1 day Fri 08-02-19 Fri 08-02-19
survey of power
consumption technologies
2 days Mon 11-02-19 Tue 12-02-19
Implementation 19 days Wed 13-02-19 Mon 11-03-19
Setting up of network
peripheral
4 days Wed 13-02-19 Mon 18-02-19
software design 5 days Tue 19-02-19 Mon 25-02-19
software and hardware
integration
10 days Tue 26-02-19 Mon 11-03-19
Closing 17 days Tue 12-03-19 Wed 03-04-19
development of final
documents
5 days Tue 12-03-19 Mon 18-03-19
testing 3 days Tue 19-03-19 Thu 21-03-19
testing documentation 3 days Fri 22-03-19 Tue 26-03-19
Evaluation 3 days Wed 27-03-19 Fri 29-03-19
submission of documents 2 days Mon 01-04-19 Tue 02-04-19
sign off 1 day Wed 03-04-19 Wed 03-04-19
project closed 0 days Wed 03-04-19 Wed 03-04-19
Task Name Duration Start Finish
Implementation of wireless
technology
58 days Mon 14-01-19 Wed 03-04-19
Planning 9 days Mon 14-01-19 Thu 24-01-19
Research 3 days Mon 14-01-19 Wed 16-01-19
Resource accumulation 1 day Thu 17-01-19 Thu 17-01-19
project charter
documentation
1 day Fri 18-01-19 Fri 18-01-19
PID formation 1 day Mon 21-01-19 Mon 21-01-19
Submission of documents 1 day Tue 22-01-19 Tue 22-01-19
initiation meeting 1 day Wed 23-01-19 Wed 23-01-19
sign off 1 day Thu 24-01-19 Thu 24-01-19
kick off project 0 days Thu 24-01-19 Thu 24-01-19
Design 13 days Fri 25-01-19 Tue 12-02-19
Project problem domain 2 days Fri 25-01-19 Mon 28-01-19
Analysis 1 day Tue 29-01-19 Tue 29-01-19
identification of technical
requirements
2 days Wed 30-01-19 Thu 31-01-19
identification of non-
technical requirements
1 day Fri 01-02-19 Fri 01-02-19
hardware requirements 2 days Mon 04-02-19 Tue 05-02-19
Software requirements 2 days Wed 06-02-19 Thu 07-02-19
identification of already
existing networks
1 day Fri 08-02-19 Fri 08-02-19
survey of power
consumption technologies
2 days Mon 11-02-19 Tue 12-02-19
Implementation 19 days Wed 13-02-19 Mon 11-03-19
Setting up of network
peripheral
4 days Wed 13-02-19 Mon 18-02-19
software design 5 days Tue 19-02-19 Mon 25-02-19
software and hardware
integration
10 days Tue 26-02-19 Mon 11-03-19
Closing 17 days Tue 12-03-19 Wed 03-04-19
development of final
documents
5 days Tue 12-03-19 Mon 18-03-19
testing 3 days Tue 19-03-19 Thu 21-03-19
testing documentation 3 days Fri 22-03-19 Tue 26-03-19
Evaluation 3 days Wed 27-03-19 Fri 29-03-19
submission of documents 2 days Mon 01-04-19 Tue 02-04-19
sign off 1 day Wed 03-04-19 Wed 03-04-19
project closed 0 days Wed 03-04-19 Wed 03-04-19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





