American Public University Wireless Technology Security Report
VerifiedAdded on 2023/04/21
|20
|4914
|323
Report
AI Summary
This report delves into the critical domain of wireless technology security, offering a comprehensive analysis of the vulnerabilities and threats that plague modern wireless networks. It begins by defining wireless security and its importance in protecting sensitive data and systems from unauthorized access. The report then identifies key security issues, including the weaknesses of WEP and WPA protocols, and the various types of attacks that exploit these flaws. It explores the reasons behind these security issues, such as weak key management, small initialization vectors, and the application of RC4. The report also examines the role of social engineering in wireless attacks, highlighting the need for user awareness and robust security practices. Furthermore, the report provides recommendations for improving wireless security, such as making networks invisible, renaming networks, encrypting traffic, and changing default passwords. It also addresses the need for network monitoring and authentication tools. The report concludes by emphasizing the importance of staying informed about emerging threats and implementing proactive security measures to safeguard wireless networks. This report is a valuable resource for anyone seeking to understand and enhance the security of their wireless infrastructure.

Running head: WIRELESS TECHNOLOGY SECURITY
WIRELESS TECHNOLOGY SECURITY
Matthew Gibson
American Public University
Doctor Harry Cooper
WIRELESS TECHNOLOGY SECURITY
Matthew Gibson
American Public University
Doctor Harry Cooper
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS TECHNOLOGY SECURITY
Table of Contents
Introduction......................................................................................................................................2
Problem Statement...........................................................................................................................2
Relevance and Significance.............................................................................................................2
Reason behind the security issues of Wi-Fi.....................................................................................5
Needs of a successful attack from social engineering perspective..............................................7
Reason behind the security issue of WEP.......................................................................................7
Security issues of shared key authentication.................................................................................10
Reason behind real world security attacks.....................................................................................10
Improve issues associated with TKIP............................................................................................11
WPA Security Flaws......................................................................................................................12
WEP security flaws........................................................................................................................13
Recommendations..........................................................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................16
Table of Contents
Introduction......................................................................................................................................2
Problem Statement...........................................................................................................................2
Relevance and Significance.............................................................................................................2
Reason behind the security issues of Wi-Fi.....................................................................................5
Needs of a successful attack from social engineering perspective..............................................7
Reason behind the security issue of WEP.......................................................................................7
Security issues of shared key authentication.................................................................................10
Reason behind real world security attacks.....................................................................................10
Improve issues associated with TKIP............................................................................................11
WPA Security Flaws......................................................................................................................12
WEP security flaws........................................................................................................................13
Recommendations..........................................................................................................................13
Conclusion.....................................................................................................................................14
References......................................................................................................................................16

2WIRELESS TECHNOLOGY SECURITY
Introduction
Wireless technology security is defined as the prevention of any kinds of access or
damage to the systems or information which are unauthorized by utilizing the wireless networks.
Some of the most common types of wireless security are WPA or Wi-Fi Protected Access and
WEP or Wired Equivalent Privacy. The main purpose of the study is to develop a concept on the
wireless technology security. It can also be considered as a subset of the security of network
which is capable of adding protection for a wireless network of computer. Such a security is
delivered with the help of some wireless devices like a wireless switch or router which is capable
of encrypting as well as securing all communications which are wireless by default.
Problem Statement
Wireless networking is seen to have been prone to several issues of security. Hackers
have been able to found that wireless networks are easier to break into and uses wireless
technology for hacking into the networks which are wired (Jing et al., 2014). Therefore, it is very
much important for the enterprises in defining effective wireless technology security policies for
guarding against access to important resources which are unauthorized.
Relevance and Significance
Wireless technology security is capable of primarily protecting a wireless network from
any type of attempts of access which are both unauthorized as well as malicious (Borgohain,
Kumar & Sanyal, 2015). The security of wireless technology is offered through devices which
are mainly wireless like a switch or a router. These devices just encrypts and protects wireless
sharing of information by default. Even if the security of wireless technology is compromised,
Introduction
Wireless technology security is defined as the prevention of any kinds of access or
damage to the systems or information which are unauthorized by utilizing the wireless networks.
Some of the most common types of wireless security are WPA or Wi-Fi Protected Access and
WEP or Wired Equivalent Privacy. The main purpose of the study is to develop a concept on the
wireless technology security. It can also be considered as a subset of the security of network
which is capable of adding protection for a wireless network of computer. Such a security is
delivered with the help of some wireless devices like a wireless switch or router which is capable
of encrypting as well as securing all communications which are wireless by default.
Problem Statement
Wireless networking is seen to have been prone to several issues of security. Hackers
have been able to found that wireless networks are easier to break into and uses wireless
technology for hacking into the networks which are wired (Jing et al., 2014). Therefore, it is very
much important for the enterprises in defining effective wireless technology security policies for
guarding against access to important resources which are unauthorized.
Relevance and Significance
Wireless technology security is capable of primarily protecting a wireless network from
any type of attempts of access which are both unauthorized as well as malicious (Borgohain,
Kumar & Sanyal, 2015). The security of wireless technology is offered through devices which
are mainly wireless like a switch or a router. These devices just encrypts and protects wireless
sharing of information by default. Even if the security of wireless technology is compromised,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WIRELESS TECHNOLOGY SECURITY
the hackers are unable to view the traffic or the packet content in transit (Pathan, 2016).
Detection of wireless intrusion and systems of prevention also helps in protecting a wireless
network by directly giving alerts to the administrator of the wireless network in case of any kind
of security breach (Osseiran, Monserrat & Marsch, 2016). Both WEP and WPA are common
algorithms or rather standards which are capable of ensuring wireless technology security. It has
been observed that WEP is a bit weak standard of security as the password which it uses can be
cracked within a few minutes with a variety of available tools of software. On the other hand,
WPA is a much quicker alternative for improving the security over WEP. The recent standard
which is being used is WPA2 but some of the hardware cannot support SWPA2 if upgrade of
firmware is not done. It can be used as a device of encryption which can encrypt the network
with the help of a key of 256 bit. Longer is the length of the key, more is the improvement over
WEP (Rhodes-Ousley, 2013). Some of the most common policies of wireless security within
enterprises include Wireless Prevention Systems or Wireless Detection Systems of Intrusion.
While using wireless technology, it is to be known that there are several wireless threats
at home which may be encountered. Some of them are piggybacking, wardriving or any other
unauthorized access of computer. For providing wireless technology security several steps are to
be undertaken. They are:
Wireless Network made invisible: It is very much important to keep the wireless
network invisible to others (Xiao, 2016). This is done by seeing the user manual of access point
for instructions on making the identifier broadcasting disabled.
the hackers are unable to view the traffic or the packet content in transit (Pathan, 2016).
Detection of wireless intrusion and systems of prevention also helps in protecting a wireless
network by directly giving alerts to the administrator of the wireless network in case of any kind
of security breach (Osseiran, Monserrat & Marsch, 2016). Both WEP and WPA are common
algorithms or rather standards which are capable of ensuring wireless technology security. It has
been observed that WEP is a bit weak standard of security as the password which it uses can be
cracked within a few minutes with a variety of available tools of software. On the other hand,
WPA is a much quicker alternative for improving the security over WEP. The recent standard
which is being used is WPA2 but some of the hardware cannot support SWPA2 if upgrade of
firmware is not done. It can be used as a device of encryption which can encrypt the network
with the help of a key of 256 bit. Longer is the length of the key, more is the improvement over
WEP (Rhodes-Ousley, 2013). Some of the most common policies of wireless security within
enterprises include Wireless Prevention Systems or Wireless Detection Systems of Intrusion.
While using wireless technology, it is to be known that there are several wireless threats
at home which may be encountered. Some of them are piggybacking, wardriving or any other
unauthorized access of computer. For providing wireless technology security several steps are to
be undertaken. They are:
Wireless Network made invisible: It is very much important to keep the wireless
network invisible to others (Xiao, 2016). This is done by seeing the user manual of access point
for instructions on making the identifier broadcasting disabled.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS TECHNOLOGY SECURITY
Renaming the wireless network: It is very much important to rename the default name
with such a name which cannot be guessed easily. This will help in preventing an unauthorized
access to the network.
Encryption of Network Traffic: The access point device which is wireless must allow
encryption of passing traffic in between the device and the customers. With the help of such an
encryption, wireless traffic is being converted into a code which can be understood only with an
appropriate key to that particular code.
Changing the password of the Admin: All the default passwords are needed to be
changed and the new password must be long and must comprise several characters which are
non-alphanumeric. It should not contain any type of personal information like birthdate, name or
birth year. Such a password will prevent any kind of unauthorized access to the wireless
network.
Keeping the software of access point both patched and up to date: It is very much
important to check the website of the manufacturer regularly for any kind of updates for the
software of the device.
Checking the wireless security options of the IP: The ISP may give information regarding
securing the wireless network at home. Therefore, it is essential to check the support area of the
customer of the website of the provider or rather contact the customer support group of the
provider.
The other security measures in order to deal with the security issues of WEP and WPA
are as followings:
Renaming the wireless network: It is very much important to rename the default name
with such a name which cannot be guessed easily. This will help in preventing an unauthorized
access to the network.
Encryption of Network Traffic: The access point device which is wireless must allow
encryption of passing traffic in between the device and the customers. With the help of such an
encryption, wireless traffic is being converted into a code which can be understood only with an
appropriate key to that particular code.
Changing the password of the Admin: All the default passwords are needed to be
changed and the new password must be long and must comprise several characters which are
non-alphanumeric. It should not contain any type of personal information like birthdate, name or
birth year. Such a password will prevent any kind of unauthorized access to the wireless
network.
Keeping the software of access point both patched and up to date: It is very much
important to check the website of the manufacturer regularly for any kind of updates for the
software of the device.
Checking the wireless security options of the IP: The ISP may give information regarding
securing the wireless network at home. Therefore, it is essential to check the support area of the
customer of the website of the provider or rather contact the customer support group of the
provider.
The other security measures in order to deal with the security issues of WEP and WPA
are as followings:

5WIRELESS TECHNOLOGY SECURITY
Raising the security awareness among all the users of the wireless technologies. The
wireless technologies which are extensively used in homes as well as in the business
organizations.
Employing network monitoring to oversee connected devices and web traffic.
Authentication tools are also very much important to secure the wireless technologies.
The role of the network administrators are also very much important to deal with the
security issues of the wireless technologies used in the business organizations.
Reason behind the security issues of Wi-Fi
There are lots of security issues associated with the use of the Wi-Fi in both business
organizations as well as in the society. The public Wi-Fi have lots of security issues in terms of
the pre-shared keys (Strohmeier et al., 2017). The re-shared keys are very much vulnerable in
nature and are quite easily intercepted by the social engineers. The retails stores of the society
have no real legal obligations associated with the Wi-Fi services they provide to their consumers.
There are no level of assurance provided by the network service providers of the public Wi-Fi.
The extensive development in the field of Information Technology has resulted in the
development of new techniques and technologies such as the SQL injection attack (Aras et al.,
2017). The Wi-Fi services are very much vulnerable to these cyber security issues. With the help
of these cyber security issues the social engineers can alter or modify any data which are
circulated within a private network (Wan, Lopez & Al Faruque, 2016). The concept of data
mining are also used by the hackers regarding the alteration or modification of the business data.
There are security concerns regarding the use of the Virtual Private Network also such as the
connectivity issues (Borgohain, Kumar & Sanyal, 2015). There are different types of Wi-Fi
Raising the security awareness among all the users of the wireless technologies. The
wireless technologies which are extensively used in homes as well as in the business
organizations.
Employing network monitoring to oversee connected devices and web traffic.
Authentication tools are also very much important to secure the wireless technologies.
The role of the network administrators are also very much important to deal with the
security issues of the wireless technologies used in the business organizations.
Reason behind the security issues of Wi-Fi
There are lots of security issues associated with the use of the Wi-Fi in both business
organizations as well as in the society. The public Wi-Fi have lots of security issues in terms of
the pre-shared keys (Strohmeier et al., 2017). The re-shared keys are very much vulnerable in
nature and are quite easily intercepted by the social engineers. The retails stores of the society
have no real legal obligations associated with the Wi-Fi services they provide to their consumers.
There are no level of assurance provided by the network service providers of the public Wi-Fi.
The extensive development in the field of Information Technology has resulted in the
development of new techniques and technologies such as the SQL injection attack (Aras et al.,
2017). The Wi-Fi services are very much vulnerable to these cyber security issues. With the help
of these cyber security issues the social engineers can alter or modify any data which are
circulated within a private network (Wan, Lopez & Al Faruque, 2016). The concept of data
mining are also used by the hackers regarding the alteration or modification of the business data.
There are security concerns regarding the use of the Virtual Private Network also such as the
connectivity issues (Borgohain, Kumar & Sanyal, 2015). There are different types of Wi-Fi
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6WIRELESS TECHNOLOGY SECURITY
attacks which are a source of concern for all the users of the wireless technologies. The different
types of Wi-Fi attacks are described in the following table.
Name of the Wi-Fi attacks Explanation
War Driving The wireless networks which are used in most
of the residential complexes are very much
vulnerable to this attack. Information are
exposed from the mobile devices which are
connected to the Wi-Fi systems with the help
of the malicious websites which are accessed
by the users. These websites are
recommended by the social engineers as they
travel to the nearest location of their target.
Cracking attacks The portals which are accessed using any
kinds of network having the maximum
chances for these kinds of attacks. During
these attacks the passwords of the portals are
interchanged and new passwords are set by
the social engineers, as a result the users of
these portals are unable to access their portal
(Chen et al., 2015). There are different types
of tools which are used in the cracking attacks
such as Aircrack-ng. These tools are very
much beneficial for the social engineers to
steal the handshake files from the portals.
DDoS The distributed denial of service is one of the
most significant security threat associated
with the W-Fi which are exclusively used in
business organizations. The assets and the
nodes of the private network are
compromised during this security attack. The
vectors of the DDoS attacks are very much
technical in nature.
Karma Attacks The Karma tool are used by the social
engineers from all over the world as they
attack any Wi-Fi network. The method which
are used in the karma attacks is the Man in the
middle method. The configuration of the
devices which are connected in the Wi-Fi are
disrupted in the karma attacks (Steger et al.,
2016). The wireless access pints which are
introduced by the social engineers during this
attacks which are a source of concern for all the users of the wireless technologies. The different
types of Wi-Fi attacks are described in the following table.
Name of the Wi-Fi attacks Explanation
War Driving The wireless networks which are used in most
of the residential complexes are very much
vulnerable to this attack. Information are
exposed from the mobile devices which are
connected to the Wi-Fi systems with the help
of the malicious websites which are accessed
by the users. These websites are
recommended by the social engineers as they
travel to the nearest location of their target.
Cracking attacks The portals which are accessed using any
kinds of network having the maximum
chances for these kinds of attacks. During
these attacks the passwords of the portals are
interchanged and new passwords are set by
the social engineers, as a result the users of
these portals are unable to access their portal
(Chen et al., 2015). There are different types
of tools which are used in the cracking attacks
such as Aircrack-ng. These tools are very
much beneficial for the social engineers to
steal the handshake files from the portals.
DDoS The distributed denial of service is one of the
most significant security threat associated
with the W-Fi which are exclusively used in
business organizations. The assets and the
nodes of the private network are
compromised during this security attack. The
vectors of the DDoS attacks are very much
technical in nature.
Karma Attacks The Karma tool are used by the social
engineers from all over the world as they
attack any Wi-Fi network. The method which
are used in the karma attacks is the Man in the
middle method. The configuration of the
devices which are connected in the Wi-Fi are
disrupted in the karma attacks (Steger et al.,
2016). The wireless access pints which are
introduced by the social engineers during this
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS TECHNOLOGY SECURITY
attack are the airmon-ng and airbase-ng. All
the cellular communications are disrupted as a
result of this security attack.
Table 1: Different types of Wi-Fi attacks
(Source: Created by the author)
Needs of a successful attack from social engineering perspective
Appropriate device with installed tools: These open source tools are readily available
in the market. A Wi-Fi adapter can be very much important to reduce the cost of the
tools.
Traffic on the network: Sniffing of the packets by social engineers are important
retrieve the passwords is also a significant concern regarding the Wi-Fi attacks.
Short passwords: The decryption process by social engineers is the other concern
regarding the use of the Wi-Fi passwords. Shorter password are easier to crack by the
cyber criminals (Sari et al., 2017). The location of the unsecure WEP and WPA 2 can be
easily traced by the social engineers.
The most unsecure wireless connections are generally found in Gas stations, food chains,
motels along the highways, coffee shops, public libraries, and school, Airbnb locations,
Airbnb like apartments, galleries, museums and research centers.
Reason behind the security issue of WEP
There are lots of security issues associated with the Wired Equivalent Privacy which will
be described in this unit of the paper. The key management are not specified in the WEP which
is the most significant reason behind most of the security issues of WEP (Sametinger et al.,
attack are the airmon-ng and airbase-ng. All
the cellular communications are disrupted as a
result of this security attack.
Table 1: Different types of Wi-Fi attacks
(Source: Created by the author)
Needs of a successful attack from social engineering perspective
Appropriate device with installed tools: These open source tools are readily available
in the market. A Wi-Fi adapter can be very much important to reduce the cost of the
tools.
Traffic on the network: Sniffing of the packets by social engineers are important
retrieve the passwords is also a significant concern regarding the Wi-Fi attacks.
Short passwords: The decryption process by social engineers is the other concern
regarding the use of the Wi-Fi passwords. Shorter password are easier to crack by the
cyber criminals (Sari et al., 2017). The location of the unsecure WEP and WPA 2 can be
easily traced by the social engineers.
The most unsecure wireless connections are generally found in Gas stations, food chains,
motels along the highways, coffee shops, public libraries, and school, Airbnb locations,
Airbnb like apartments, galleries, museums and research centers.
Reason behind the security issue of WEP
There are lots of security issues associated with the Wired Equivalent Privacy which will
be described in this unit of the paper. The key management are not specified in the WEP which
is the most significant reason behind most of the security issues of WEP (Sametinger et al.,

8WIRELESS TECHNOLOGY SECURITY
2015). Interoperable key management is the other factors responsible for the security issue of
WEP.
The initialization vector of WEP is very much small which can be a very important
reason behind the encryption techniques adopted by most of the social engineers all around the
world. The Integrity check value algorithm which is incorporated in the WEP is the other
significant reason behind the security issues of WEP. Most of the recent security issues of WEP
are conducted by the social engineers are based on the similar keys (Contreras-Castillo, Zeadally
& Guerrero-Ibañez, 2018). The application of the RC4 is also one of the weakness of WEP
which is one of the main reason behind the security vulnerabilities of WEP. The authentication
messages of the WEP can be easily forged by the social engineers which is the other limitation of
WEP. The shared key authentication techniques which are adopted by the WEP also have
significant security concerns as it is very much vulnerable to the WEP key (Dorri, Kamel &
Kheirkhah, 2015). The security concerns associated with Wired Equivalent Privacy are presented
in the following table.
Concerns Explanation
Passive attacks This security concern are based on statistical
analysis. The traffic of the devices which are
connected to the Wi-Fi are disrupted.
Active Attacks New traffic are injected from unauthorized
mobile stations as a result of this security
concern (Xiao, 2016).
Attack to access points Decryption of the traffic is the impact of this
security concern. The access points of the
systems which are connected to the Wi-Fi are
compromised as a result of this security
concern of WEP
Dictionary building attacks A busy or a congested network are the most
2015). Interoperable key management is the other factors responsible for the security issue of
WEP.
The initialization vector of WEP is very much small which can be a very important
reason behind the encryption techniques adopted by most of the social engineers all around the
world. The Integrity check value algorithm which is incorporated in the WEP is the other
significant reason behind the security issues of WEP. Most of the recent security issues of WEP
are conducted by the social engineers are based on the similar keys (Contreras-Castillo, Zeadally
& Guerrero-Ibañez, 2018). The application of the RC4 is also one of the weakness of WEP
which is one of the main reason behind the security vulnerabilities of WEP. The authentication
messages of the WEP can be easily forged by the social engineers which is the other limitation of
WEP. The shared key authentication techniques which are adopted by the WEP also have
significant security concerns as it is very much vulnerable to the WEP key (Dorri, Kamel &
Kheirkhah, 2015). The security concerns associated with Wired Equivalent Privacy are presented
in the following table.
Concerns Explanation
Passive attacks This security concern are based on statistical
analysis. The traffic of the devices which are
connected to the Wi-Fi are disrupted.
Active Attacks New traffic are injected from unauthorized
mobile stations as a result of this security
concern (Xiao, 2016).
Attack to access points Decryption of the traffic is the impact of this
security concern. The access points of the
systems which are connected to the Wi-Fi are
compromised as a result of this security
concern of WEP
Dictionary building attacks A busy or a congested network are the most
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9WIRELESS TECHNOLOGY SECURITY
vulnerable to this security concern
Table 2: Security concerns of WEP
(Source: Created by the author)
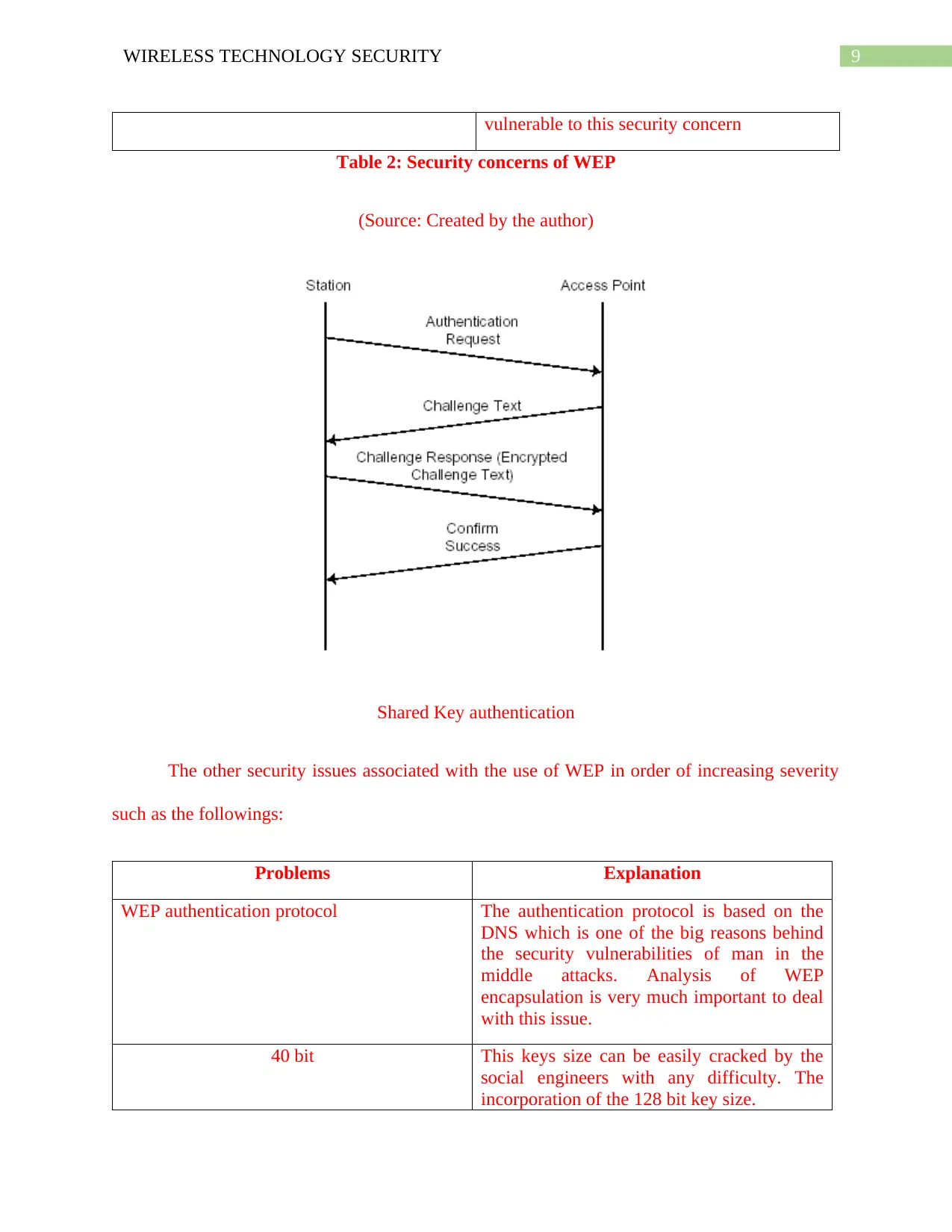
Shared Key authentication
The other security issues associated with the use of WEP in order of increasing severity
such as the followings:
Problems Explanation
WEP authentication protocol The authentication protocol is based on the
DNS which is one of the big reasons behind
the security vulnerabilities of man in the
middle attacks. Analysis of WEP
encapsulation is very much important to deal
with this issue.
40 bit This keys size can be easily cracked by the
social engineers with any difficulty. The
incorporation of the 128 bit key size.
vulnerable to this security concern
Table 2: Security concerns of WEP
(Source: Created by the author)
Shared Key authentication
The other security issues associated with the use of WEP in order of increasing severity
such as the followings:
Problems Explanation
WEP authentication protocol The authentication protocol is based on the
DNS which is one of the big reasons behind
the security vulnerabilities of man in the
middle attacks. Analysis of WEP
encapsulation is very much important to deal
with this issue.
40 bit This keys size can be easily cracked by the
social engineers with any difficulty. The
incorporation of the 128 bit key size.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10WIRELESS TECHNOLOGY SECURITY
Key Distribution The weakest link of the WEP protocol is the
key distribution process
Table 2: Security concerns of WEP
(Source: Created by the author)
Security issues of shared key authentication
The security issues with the shared key authentication technique are WEP, MAC address,
SSID, Rogue Access points and War Driving.
War Driving: This is one of the latest hacking procedures adopted by the social
engineers all around the world. The unprotected 802.11 wireless networks are involved in the
war driving attacks (Furht & Ahson, 2016). At the same time, it can be said that there are lots of
several war driving tools which are used in the war driving attacks such as THC-WarDrive,
Sniffer Wireless, Mobile Manager, AiroPeek and the NetStumbler.
Rogue Access points: Installation of the access points without the permission can have a
significant impact of the authentication technique of the shared key authentication. During the
shared key authentication technique (Yang et al., 2015). MAC address can be easily spoofed by
the cyber criminals with the help of the help of software.
SSID: Sorting of specific access points can be very much vulnerable in the shared key
authentication technique as well. The changes in SSID is also very much vulnerable regarding
the shared key authentication.
Key Distribution The weakest link of the WEP protocol is the
key distribution process
Table 2: Security concerns of WEP
(Source: Created by the author)
Security issues of shared key authentication
The security issues with the shared key authentication technique are WEP, MAC address,
SSID, Rogue Access points and War Driving.
War Driving: This is one of the latest hacking procedures adopted by the social
engineers all around the world. The unprotected 802.11 wireless networks are involved in the
war driving attacks (Furht & Ahson, 2016). At the same time, it can be said that there are lots of
several war driving tools which are used in the war driving attacks such as THC-WarDrive,
Sniffer Wireless, Mobile Manager, AiroPeek and the NetStumbler.
Rogue Access points: Installation of the access points without the permission can have a
significant impact of the authentication technique of the shared key authentication. During the
shared key authentication technique (Yang et al., 2015). MAC address can be easily spoofed by
the cyber criminals with the help of the help of software.
SSID: Sorting of specific access points can be very much vulnerable in the shared key
authentication technique as well. The changes in SSID is also very much vulnerable regarding
the shared key authentication.
11WIRELESS TECHNOLOGY SECURITY
Reason behind real world security attacks
There are lots of real world examples regarding the security issues of WPA and WEP
which will be discussed in this section of the paper. There are lots of protocols which are
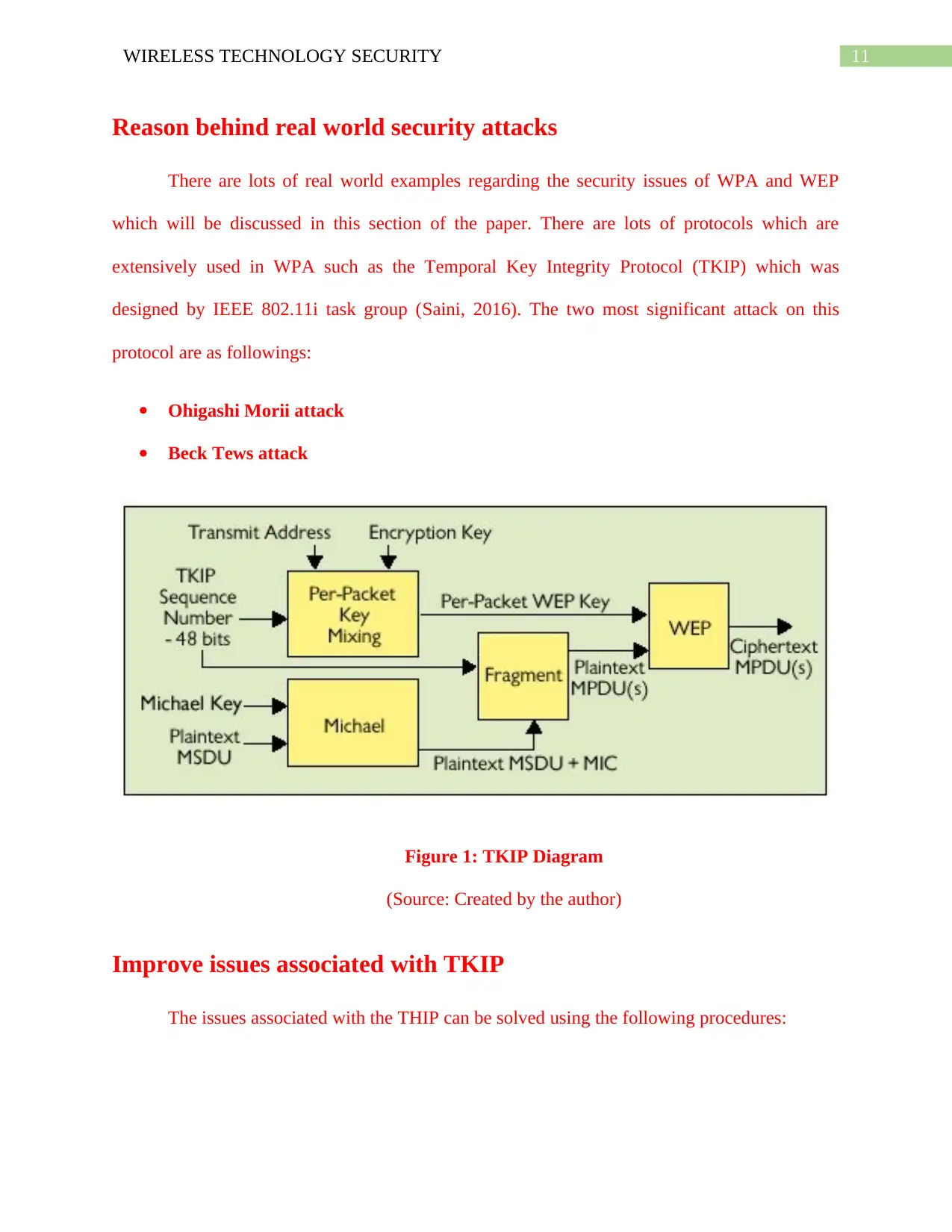
extensively used in WPA such as the Temporal Key Integrity Protocol (TKIP) which was
designed by IEEE 802.11i task group (Saini, 2016). The two most significant attack on this
protocol are as followings:
Ohigashi Morii attack
Beck Tews attack
Figure 1: TKIP Diagram
(Source: Created by the author)
Improve issues associated with TKIP
The issues associated with the THIP can be solved using the following procedures:
Reason behind real world security attacks
There are lots of real world examples regarding the security issues of WPA and WEP
which will be discussed in this section of the paper. There are lots of protocols which are
extensively used in WPA such as the Temporal Key Integrity Protocol (TKIP) which was
designed by IEEE 802.11i task group (Saini, 2016). The two most significant attack on this
protocol are as followings:
Ohigashi Morii attack
Beck Tews attack
Figure 1: TKIP Diagram
(Source: Created by the author)
Improve issues associated with TKIP
The issues associated with the THIP can be solved using the following procedures:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




