Wireshark: Practical Analysis of Network Traffic and Protocols
VerifiedAdded on 2023/04/21
|23
|1709
|177
Practical Assignment
AI Summary
This assignment provides a comprehensive overview of Wireshark, a powerful network analysis tool. It begins with the installation of Wireshark and WinPcap, followed by an exploration of the GUI, including packet filtering and live capture functionalities. The assignment details the assessment of Wireshark, including packet sniffing, protocols, protocol analyzers, packets, packet filters, and live capture. It also covers the assessment of TCP/IP, including TCP, IP, network stack, packet headers, and packet structure. The practical part of the assignment involves capturing live network traffic, analyzing the captured data, and exploring the Wireshark GUI, including filter bars, packet lists, packet details, and individual packet bytes. The analysis includes examining UDP packets, average IP packet size, packet drops, and flow graphs. The assignment concludes with a bibliography of relevant sources. This assignment is designed to provide a practical understanding of network traffic analysis using Wireshark.

Running Head: WIRESHARK
Wireshark
Wireshark
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
WIRESHARK
(Encrypted-Internet)+Privacy== Oxymoron
Objectives:
The following paper aims to achieve/establish the significant objectives. Firstly, the
procedure of download and installation of Wireshark and WinpCap is recorded. Next,
Wireshark’s GUI (Graphical User Interface) is explored. Then, the process of sniffing and
filtering traffic is also evaluated with Wireshark. Lastly, the obtained data from Wireshark is
analysed.
Introduction:
Wireshark is recognized as a software which strengthens security with respect to any
organizational usage. The software is free-to-use, open sourced analyser of network traffic. In
an organization, it is used by security professionals for monitoring and analysis of network
vulnerabilities, attacks and threats. However, the same software is used to provide scopes to
an attackers for sniffing of passwords or any information, affecting any unsuspecting and
innocent victim. Thus, it is both considered as blessing and bane, from the perspective of any
security official.
Assessment of Wireshark:
i. Sniffer- Packet sniffing is used in Ethernet as a utility. This allows users in
capturing data during transmission over a network. Sniffing is used by
professional network security individuals to diagnose network risks. However, the
same is used by unethical and immoral users to steal unencrypted data, like
usernames and profile information to other users. Wireshark has been an effective
tool to enhance the procedure of packet sniffing.
ii. Protocol- A network protocol are the standard set of rules and convections that
build a communication channel between network devices. The packaging of data
WIRESHARK
(Encrypted-Internet)+Privacy== Oxymoron
Objectives:
The following paper aims to achieve/establish the significant objectives. Firstly, the
procedure of download and installation of Wireshark and WinpCap is recorded. Next,
Wireshark’s GUI (Graphical User Interface) is explored. Then, the process of sniffing and
filtering traffic is also evaluated with Wireshark. Lastly, the obtained data from Wireshark is
analysed.
Introduction:
Wireshark is recognized as a software which strengthens security with respect to any
organizational usage. The software is free-to-use, open sourced analyser of network traffic. In
an organization, it is used by security professionals for monitoring and analysis of network
vulnerabilities, attacks and threats. However, the same software is used to provide scopes to
an attackers for sniffing of passwords or any information, affecting any unsuspecting and
innocent victim. Thus, it is both considered as blessing and bane, from the perspective of any
security official.
Assessment of Wireshark:
i. Sniffer- Packet sniffing is used in Ethernet as a utility. This allows users in
capturing data during transmission over a network. Sniffing is used by
professional network security individuals to diagnose network risks. However, the
same is used by unethical and immoral users to steal unencrypted data, like
usernames and profile information to other users. Wireshark has been an effective
tool to enhance the procedure of packet sniffing.
ii. Protocol- A network protocol are the standard set of rules and convections that
build a communication channel between network devices. The packaging of data

2
WIRESHARK
(sent and received) are identified and connected to each other using the protocol
layer. Modern protocols includes packet switching mechanism to communicate
data in form of packets. The same is identified to Wireshark’s mechanism of
protocols. Moreover, the frequently identified protocols in Wireshark are known
to be Transmission Control Protocol (TCP) and Internet Control Message
Protocol.
iii. Protocol Analyzer- This is defined as a combination of programming and
hardware devices that is installed in a computer environment for enhancement of
protection against network-related threats and maliciousness. These analyzers
support firewalls, spyware-detection and anti-virus programs. Protocol analyzers
provide extended statistics to recent network activities; testing of anti-virus
programs and identification of vulnerabilities; usual network traffic detection, and
more features are also recorded.
iv. Packet- Packets, in computer network’s language, is defined as the collection of
data used by computing systems during communication under a network. A packet
contains two types of data: packet data and packet information. This is the most
basic element of transmission under a packet-switching network.
v. Packet Filter: This feature is used to display filters according to requirement from
the user, operating under a designated network. Specific attributes are searched on
the search bar of Wireshark, and the program autocompletes the filter by
justifying the identifiable identities according to the user’s choice.
vi. Live Capture- Wireshark provides this major feature of capturing live network
data. Live capturing allows data sniffing under a network which is live and, in real
time. It also supports offline analysis of protocol, enrichens the UI and, mainly
WIRESHARK
(sent and received) are identified and connected to each other using the protocol
layer. Modern protocols includes packet switching mechanism to communicate
data in form of packets. The same is identified to Wireshark’s mechanism of
protocols. Moreover, the frequently identified protocols in Wireshark are known
to be Transmission Control Protocol (TCP) and Internet Control Message
Protocol.
iii. Protocol Analyzer- This is defined as a combination of programming and
hardware devices that is installed in a computer environment for enhancement of
protection against network-related threats and maliciousness. These analyzers
support firewalls, spyware-detection and anti-virus programs. Protocol analyzers
provide extended statistics to recent network activities; testing of anti-virus
programs and identification of vulnerabilities; usual network traffic detection, and
more features are also recorded.
iv. Packet- Packets, in computer network’s language, is defined as the collection of
data used by computing systems during communication under a network. A packet
contains two types of data: packet data and packet information. This is the most
basic element of transmission under a packet-switching network.
v. Packet Filter: This feature is used to display filters according to requirement from
the user, operating under a designated network. Specific attributes are searched on
the search bar of Wireshark, and the program autocompletes the filter by
justifying the identifiable identities according to the user’s choice.
vi. Live Capture- Wireshark provides this major feature of capturing live network
data. Live capturing allows data sniffing under a network which is live and, in real
time. It also supports offline analysis of protocol, enrichens the UI and, mainly
You're viewing a preview
Unlock full access by subscribing today!

3
WIRESHARK
supports all the network like application and transport protocols. Mainly,
Wireshark utilizes the libpcap filter language to capture the filters.
Assessment of TCP/IP:
i. Transport Control Protocol (TCP) - TCP is identified as the standard which
defines the way of establishment and maintenance of a network communication
under which the exchange of data is accomplished. The working of TCP with IP
(Internet Protocol) defines the way of data-transmission through packets between
a set of end-users (system). It also establishes- TCP port multiplexing; logical
connection against issues to DuplicatePackets, PacketLoss and more. Moreover,
transfer of small byte number will allocate them to the remote host yet, no extra or
missing bytes are added or removed, respectively to the application which is
receiving.
ii. Internet Protocol (IP) - IP is defined as the protocol through which the transfer
of data over two or more computer system is observed, under an internet
connection. Each computer on internet contains a unique IP address to
appropriately identify it from other computer systems.
iii. Network Stack- Network or Protocol stack are the set of protocols that used in a
network to show the software layers hierarchy. The hierarchy starts from
application layer (at the top) to the data link layer (at the bottom). It is also noticed
that the stack resides in both server and client. The layered method controls
different protocols to adjust and accommodate alike network architectures.
iv. Packet- It is the basic unit of gathering information in a network transmission.
Due to structure of TCP/IP being laminated to use packets, it is considered as
packet-switching technology. Every packet in such a packet switching network is
constructed of two significant pieces: the data and the package header. Generally,
WIRESHARK
supports all the network like application and transport protocols. Mainly,
Wireshark utilizes the libpcap filter language to capture the filters.
Assessment of TCP/IP:
i. Transport Control Protocol (TCP) - TCP is identified as the standard which
defines the way of establishment and maintenance of a network communication
under which the exchange of data is accomplished. The working of TCP with IP
(Internet Protocol) defines the way of data-transmission through packets between
a set of end-users (system). It also establishes- TCP port multiplexing; logical
connection against issues to DuplicatePackets, PacketLoss and more. Moreover,
transfer of small byte number will allocate them to the remote host yet, no extra or
missing bytes are added or removed, respectively to the application which is
receiving.
ii. Internet Protocol (IP) - IP is defined as the protocol through which the transfer
of data over two or more computer system is observed, under an internet
connection. Each computer on internet contains a unique IP address to
appropriately identify it from other computer systems.
iii. Network Stack- Network or Protocol stack are the set of protocols that used in a
network to show the software layers hierarchy. The hierarchy starts from
application layer (at the top) to the data link layer (at the bottom). It is also noticed
that the stack resides in both server and client. The layered method controls
different protocols to adjust and accommodate alike network architectures.
iv. Packet- It is the basic unit of gathering information in a network transmission.
Due to structure of TCP/IP being laminated to use packets, it is considered as
packet-switching technology. Every packet in such a packet switching network is
constructed of two significant pieces: the data and the package header. Generally,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
WIRESHARK
the packets fit into the standard networking model, which is also known as Open
System Interconnection (OSI model) (at the network level). Hereafter, they
packets are configured/transferred to bits, and then passed down to data link layer.
It reaches the physical layer (actual medium of transmission) for the insertion of
frames (from the packets) in the next step. Moreover, the structure of packet-
switching networks and packets approves fast, efficient and reliable data
transmission.
v. Packet Header- As mentioned before, a packet consists of a packet header and
the data. However, packet header plays a major role during transmission of
information between computer systems under a network. The header of a packet
contains protocol version (IPv4 or IPv6), packet’s length, total number of packets,
the address of the source and destination, a checksum to correct the error
calculations and lastly, the TTL (Time to Live) data, that defines the number of
devices the packets will be transferred along. Additionally, the information from
the header defines the type, number and error correction databits with respect to
the packet provides information to other packet about the whole message under an
easier correction and reconstruction. This is far more reliable than circuit-
switching transmission techniques.
WIRESHARK
the packets fit into the standard networking model, which is also known as Open
System Interconnection (OSI model) (at the network level). Hereafter, they
packets are configured/transferred to bits, and then passed down to data link layer.
It reaches the physical layer (actual medium of transmission) for the insertion of
frames (from the packets) in the next step. Moreover, the structure of packet-
switching networks and packets approves fast, efficient and reliable data
transmission.
v. Packet Header- As mentioned before, a packet consists of a packet header and
the data. However, packet header plays a major role during transmission of
information between computer systems under a network. The header of a packet
contains protocol version (IPv4 or IPv6), packet’s length, total number of packets,
the address of the source and destination, a checksum to correct the error
calculations and lastly, the TTL (Time to Live) data, that defines the number of
devices the packets will be transferred along. Additionally, the information from
the header defines the type, number and error correction databits with respect to
the packet provides information to other packet about the whole message under an
easier correction and reconstruction. This is far more reliable than circuit-
switching transmission techniques.

5
WIRESHARK
Procedure
Download and Install WinPcap
WIRESHARK
Procedure
Download and Install WinPcap
You're viewing a preview
Unlock full access by subscribing today!

6
WIRESHARK
WIRESHARK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
WIRESHARK
2. Download and Install Wireshark
WIRESHARK
2. Download and Install Wireshark

8
WIRESHARK
WIRESHARK
You're viewing a preview
Unlock full access by subscribing today!

9
WIRESHARK
WIRESHARK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
WIRESHARK
WIRESHARK

11
WIRESHARK
3. Start Sniffing: Perform a Live Capture of Network Traffic
WIRESHARK
3. Start Sniffing: Perform a Live Capture of Network Traffic
You're viewing a preview
Unlock full access by subscribing today!

12
WIRESHARK
The capture made above has been done for the Ethernet Interface of the network that
is currently being analysed. It can be seen that the pings are sent from a source named
10.10.30.52. Hence, it can be derived that the IP address of the source machine is
10.10.30.52.
WIRESHARK
The capture made above has been done for the Ethernet Interface of the network that
is currently being analysed. It can be seen that the pings are sent from a source named
10.10.30.52. Hence, it can be derived that the IP address of the source machine is
10.10.30.52.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13
WIRESHARK
Various results can be derived from results obtained above. It can be seen that
currently a lot of acknowledgement and push messages are being transferred in the network.
The internet protocol version 4 is being used in the network currently.
WIRESHARK
Various results can be derived from results obtained above. It can be seen that
currently a lot of acknowledgement and push messages are being transferred in the network.
The internet protocol version 4 is being used in the network currently.

14
WIRESHARK
After the continue without saving option was selected a new capture was started and
the capture was stopped in 2 minutes.
It can be seen that around 2400 packets were captured during this 2 minutes.
4. Explore the Wireshark GUI: Four Areas of Interest
4.1 Filter Packets with the Filter Bar
WIRESHARK
After the continue without saving option was selected a new capture was started and
the capture was stopped in 2 minutes.
It can be seen that around 2400 packets were captured during this 2 minutes.
4. Explore the Wireshark GUI: Four Areas of Interest
4.1 Filter Packets with the Filter Bar
You're viewing a preview
Unlock full access by subscribing today!

15
WIRESHARK
WIRESHARK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

16
WIRESHARK
WIRESHARK

17
WIRESHARK
4.2 View Packet Summaries with the Packet List Window
Packet Number: 1
Timestamp: 0.00000
IP Addresses: Source: 10.10.30.148 Destination: 239.255.255.250
Protocols: SSDP
WIRESHARK
4.2 View Packet Summaries with the Packet List Window
Packet Number: 1
Timestamp: 0.00000
IP Addresses: Source: 10.10.30.148 Destination: 239.255.255.250
Protocols: SSDP
You're viewing a preview
Unlock full access by subscribing today!
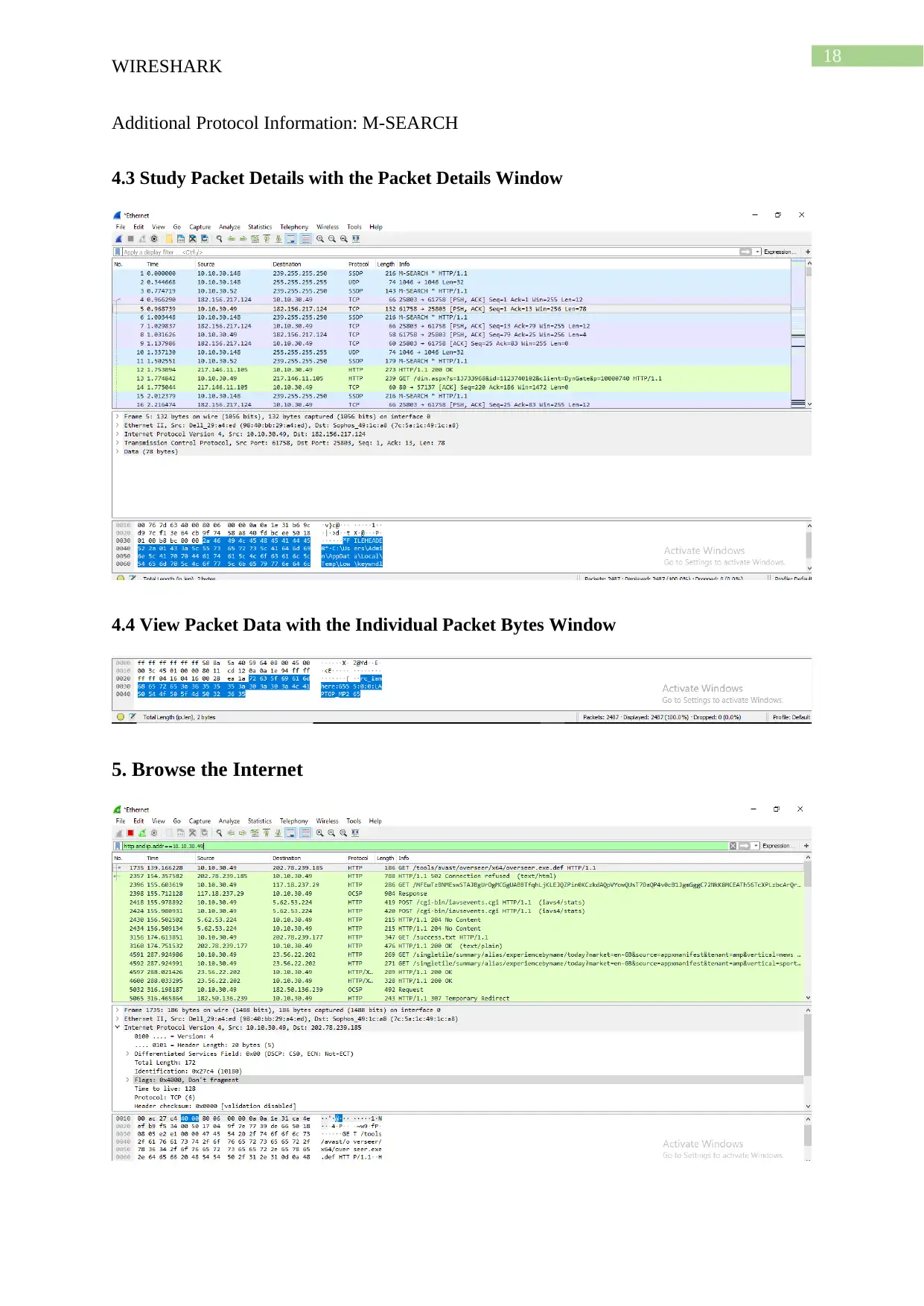
18
WIRESHARK
Additional Protocol Information: M-SEARCH
4.3 Study Packet Details with the Packet Details Window
4.4 View Packet Data with the Individual Packet Bytes Window
5. Browse the Internet
WIRESHARK
Additional Protocol Information: M-SEARCH
4.3 Study Packet Details with the Packet Details Window
4.4 View Packet Data with the Individual Packet Bytes Window
5. Browse the Internet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
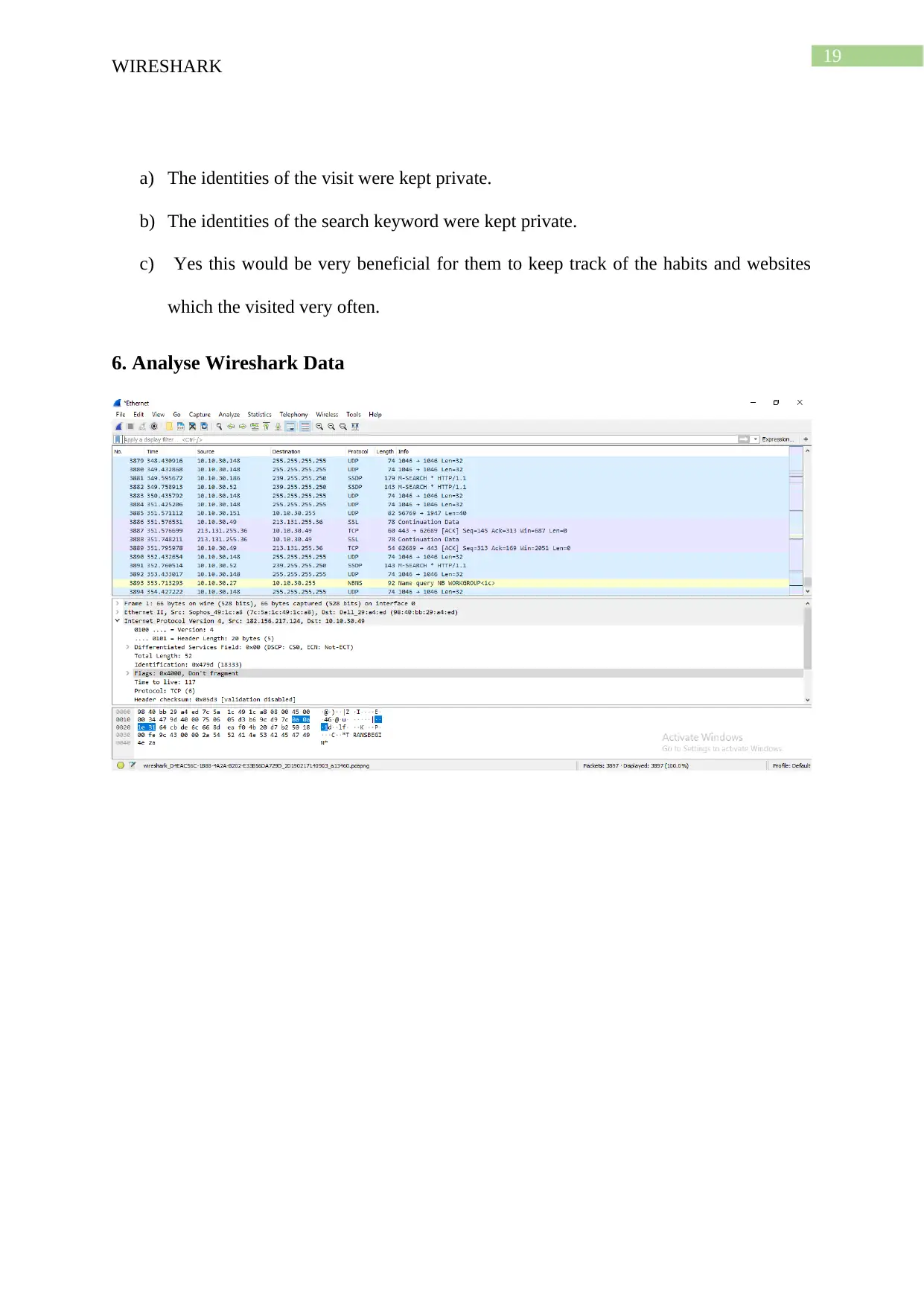
19
WIRESHARK
a) The identities of the visit were kept private.
b) The identities of the search keyword were kept private.
c) Yes this would be very beneficial for them to keep track of the habits and websites
which the visited very often.
6. Analyse Wireshark Data
WIRESHARK
a) The identities of the visit were kept private.
b) The identities of the search keyword were kept private.
c) Yes this would be very beneficial for them to keep track of the habits and websites
which the visited very often.
6. Analyse Wireshark Data

20
WIRESHARK
How many udp packets did Wireshark capture?
3897 packets were captured.
What was the average ip packet size?
The average size is 370.
How many packets did Wireshark drop?
0 packets were dropped.
What does a flow graph show?
The flow graph summarizes the traffic flow within the endpoints of a network.
List the flow graph options.
WIRESHARK
How many udp packets did Wireshark capture?
3897 packets were captured.
What was the average ip packet size?
The average size is 370.
How many packets did Wireshark drop?
0 packets were dropped.
What does a flow graph show?
The flow graph summarizes the traffic flow within the endpoints of a network.
List the flow graph options.
You're viewing a preview
Unlock full access by subscribing today!

21
WIRESHARK
WIRESHARK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

22
WIRESHARK
Bibliography
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K., Elamaran,
V., ... & Ramirez-Gonzalez, G. (2018). Network vulnerability analysis on brain
signal/image databases using Nmap and Wireshark tools. IEEE Access, 6, 57144-
57151.
El Sheikh, A. Y. (2018). Evaluation of the capabilities of Wireshark as network intrusion
system. Journal of Global Research in Computer Science, 9(8), 01-08.
Lone, A. H., & Mir, R. N. (2018). Investigating and Analyzing Bitcoin Blockchain Protocol
using Wireshark. International Journal of Computer Network and Information
Security, 10(7), 36.
Ndatinya, V., Xiao, Z., Manepalli, V. R., Meng, K., & Xiao, Y. (2015). Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), 91-
106.
WIRESHARK
Bibliography
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K., Elamaran,
V., ... & Ramirez-Gonzalez, G. (2018). Network vulnerability analysis on brain
signal/image databases using Nmap and Wireshark tools. IEEE Access, 6, 57144-
57151.
El Sheikh, A. Y. (2018). Evaluation of the capabilities of Wireshark as network intrusion
system. Journal of Global Research in Computer Science, 9(8), 01-08.
Lone, A. H., & Mir, R. N. (2018). Investigating and Analyzing Bitcoin Blockchain Protocol
using Wireshark. International Journal of Computer Network and Information
Security, 10(7), 36.
Ndatinya, V., Xiao, Z., Manepalli, V. R., Meng, K., & Xiao, Y. (2015). Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), 91-
106.
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




