University Report: Evaluation of 5G Network and Security (MN603)
VerifiedAdded on 2022/09/17
|18
|3007
|22
Report
AI Summary
This report provides a comprehensive overview of 5G network technology and its associated security aspects. It begins with an introduction to the evolution of cellular networks, highlighting the importance of 5G in the current market, emphasizing its high speed and capabilities. The report then delves into a comparative analysis of various generations of mobile technology (1G to 5G), examining their communication spectrum, modulation techniques, medium access control mechanisms, network speeds, and security techniques. A detailed discussion of 5G architecture follows, including a breakdown of its core components and network slicing. The report also identifies potential 5G attacks, such as DDoS attacks, and explores network coverage issues. Finally, it concludes by offering potential solutions to mitigate the identified security threats and network coverage challenges, providing a comprehensive analysis of the current state and future of 5G technology.

Running head: WIRELESS NETWORK AND SECURITY
WIRELESS NETWORK AND SECURITY: 5G
Name of the Student:
Name of the University:
Author Note:
WIRELESS NETWORK AND SECURITY: 5G
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1WIRELESS NETWORK AND SECURITY
Table of Contents
Introduction..........................................................................................................................2
Importance of 5G.................................................................................................................2
Various generations in the mobile technology....................................................................4
5g architecture.....................................................................................................................6
5G attacks............................................................................................................................9
Network Coverage Issues in 5G........................................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................14
Table of Contents
Introduction..........................................................................................................................2
Importance of 5G.................................................................................................................2
Various generations in the mobile technology....................................................................4
5g architecture.....................................................................................................................6
5G attacks............................................................................................................................9
Network Coverage Issues in 5G........................................................................................12
Conclusion.........................................................................................................................13
References..........................................................................................................................14

2WIRELESS NETWORK AND SECURITY
Introduction
Cellular networks evolved in a gigantic manner in these last few decades. The wireless
cellular generation (G) is referred to the development in the network with respect to the latency,
frequency, technology, speed and data capacity. Every generation comprises of various
capacities, new technology, well developed platform and innovative features. The first
generation cellular network used analog connection and are used for only voice calls. Second
generation is the digital version of the first one and also supports the messaging facility while the
third generation of the cellular network give high data transmission rate with rised capacity as
well as support multimedia factor. Fourth generation is the upgraded version of the third
generation while this generation provides fixed internet which is a great evolution in the wireless
communication sector. The fifth generation of the mobile technology is the new revolution of the
wireless communication and uses high frequency. The primary focus of this generation is to
support the WWWW (Wireless World Wide Web). The report mainly focuses on the fifth
generation of the wireless mobile communication. The report briefly describes the importance of
5g in this market, the comparison between the various generations of the mobile technology,
architecture of 5g, various 5g attacks and lastly the possible issues in the network coverage of the
5g. The report also showcases some mitigating steps that can be used to decrease all the
identified issues in the network coverage.
Importance of 5G
The main purpose of the fifth generation is to achieve the transmission speed of 20 – 30
Gbps that is almost equal to 50 times the speed of 4G [1]. From the customer view 5G has many
advantages like
Introduction
Cellular networks evolved in a gigantic manner in these last few decades. The wireless
cellular generation (G) is referred to the development in the network with respect to the latency,
frequency, technology, speed and data capacity. Every generation comprises of various
capacities, new technology, well developed platform and innovative features. The first
generation cellular network used analog connection and are used for only voice calls. Second
generation is the digital version of the first one and also supports the messaging facility while the
third generation of the cellular network give high data transmission rate with rised capacity as
well as support multimedia factor. Fourth generation is the upgraded version of the third
generation while this generation provides fixed internet which is a great evolution in the wireless
communication sector. The fifth generation of the mobile technology is the new revolution of the
wireless communication and uses high frequency. The primary focus of this generation is to
support the WWWW (Wireless World Wide Web). The report mainly focuses on the fifth
generation of the wireless mobile communication. The report briefly describes the importance of
5g in this market, the comparison between the various generations of the mobile technology,
architecture of 5g, various 5g attacks and lastly the possible issues in the network coverage of the
5g. The report also showcases some mitigating steps that can be used to decrease all the
identified issues in the network coverage.
Importance of 5G
The main purpose of the fifth generation is to achieve the transmission speed of 20 – 30
Gbps that is almost equal to 50 times the speed of 4G [1]. From the customer view 5G has many
advantages like
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3WIRELESS NETWORK AND SECURITY
Low latency
Support devices in Internet of Things
Greater capacity than the 4G network
Developed coverage
Simultaneous huge number of connections for the Wireless sensors
Provides data rates of approx. 100 Mbps.
Developed efficiency of signaling
Support Smart beam antenna system
Low outage issues [2]
Cheaper traffic fees
Harmless with respect to the human health
Wireless World Wide Web
Low battery Consumption
Numerous concurrent information transfer paths
Beneficial for the artificial Intelligence tools or devices [3]
5G aims to provide unified standard globally that will help in service portability
and global mobility
Provides service personalization which means that the 5G networks or the stations
also gives services that are not dependent on the capabilities.
It aims to give the download speed of greater than 1Gbps in LAN and above 500
Mbps in WAN which is considered as 40 times above the 4G mobile networks.
It is believed that it will consume less power which in turn helps the consumer to
save the power of his or her device.
Low latency
Support devices in Internet of Things
Greater capacity than the 4G network
Developed coverage
Simultaneous huge number of connections for the Wireless sensors
Provides data rates of approx. 100 Mbps.
Developed efficiency of signaling
Support Smart beam antenna system
Low outage issues [2]
Cheaper traffic fees
Harmless with respect to the human health
Wireless World Wide Web
Low battery Consumption
Numerous concurrent information transfer paths
Beneficial for the artificial Intelligence tools or devices [3]
5G aims to provide unified standard globally that will help in service portability
and global mobility
Provides service personalization which means that the 5G networks or the stations
also gives services that are not dependent on the capabilities.
It aims to give the download speed of greater than 1Gbps in LAN and above 500
Mbps in WAN which is considered as 40 times above the 4G mobile networks.
It is believed that it will consume less power which in turn helps the consumer to
save the power of his or her device.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4WIRELESS NETWORK AND SECURITY
It provides high bandwidth due to which the network coverage is wide too.
Thus, it is believed that people use this mobile network technology and will enhance their
network by using 5G [4]. This enhanced and developed generation of the mobile network will
help the people to gather information instantaneously and will also help the user to communicate
seamlessly and efficiently.
Various generations in the mobile technology
Communication Spectrum
1G used analog signals for the communication purpose which is established in 1980s.
The basic difference among 1G and 2G is the type of radio signal used by them. 1G used analog
type radio signal while the 2G used digital type radio signal. 1G only allowed to call but in 2G it
supported text messaging facility too. In case of 3G it supported the mobile facility. 4G
introduces the LTE version in the wireless mobile technology [5]. 5G application will need using
innovative bands of greater than 6GHz to 100 GHz using the millimeter and sub millimeter
waveforms.
Modulation techniques
Modulation is the phenomenon of altering a single or many property of one periodic
waveform with respect to a single modulating signal which is comprised of some data that is to
be transmitted. In 1990ss 2G evolved out with GSM standard. The modulation techniques used
in the digital communication is the phase shift keying method [6]. In case of 2G it uses TDMA
(Time Division Multiple Access) or CDMA (Code Division Multiple Access) and all the next
generation of 2G uses CDMA (Code Division Multiple Access).
It provides high bandwidth due to which the network coverage is wide too.
Thus, it is believed that people use this mobile network technology and will enhance their
network by using 5G [4]. This enhanced and developed generation of the mobile network will
help the people to gather information instantaneously and will also help the user to communicate
seamlessly and efficiently.
Various generations in the mobile technology
Communication Spectrum
1G used analog signals for the communication purpose which is established in 1980s.
The basic difference among 1G and 2G is the type of radio signal used by them. 1G used analog
type radio signal while the 2G used digital type radio signal. 1G only allowed to call but in 2G it
supported text messaging facility too. In case of 3G it supported the mobile facility. 4G
introduces the LTE version in the wireless mobile technology [5]. 5G application will need using
innovative bands of greater than 6GHz to 100 GHz using the millimeter and sub millimeter
waveforms.
Modulation techniques
Modulation is the phenomenon of altering a single or many property of one periodic
waveform with respect to a single modulating signal which is comprised of some data that is to
be transmitted. In 1990ss 2G evolved out with GSM standard. The modulation techniques used
in the digital communication is the phase shift keying method [6]. In case of 2G it uses TDMA
(Time Division Multiple Access) or CDMA (Code Division Multiple Access) and all the next
generation of 2G uses CDMA (Code Division Multiple Access).

5WIRELESS NETWORK AND SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6WIRELESS NETWORK AND SECURITY
Medium access control mechanism
Medium Access Control or MAC is defined as the layer which handles hardware of a
device that are responsible for the interaction with wireless transmission medium. The core
network type used in 2G is PSTN (Public Switched Telephonic Network) and in case of 3G is
packet Internet. 4G and 5G uses the Internet core network type. 4G provides unified IP as well as
seamless mixture of broadband such as PAN, LAN, WAN and WLAN [7]. In case of 5G, it
provides with unified IP and also provides mixture of broad bands like 4G such as WAN, LAN,
PAN, WLAN and WWWW. The technologies used in 2G is IS-95, GSM. 3G uses IMT2000
WCDMA technology and in 4G it support LTE and WiMAX technologies while 5G supports
VOLTE technology.
Network speed and bandwidth utilization
Bandwidth is the primary factor in wireless mobile technology. It is the capacity of data
that can be transferred from one point to other in given interval of time. The network speed is
totally different with the bandwidth. The bandwidth used in 2G is 900 MHz and it utilized the
narrow band type. 3G has the bandwidth of 100 MHz and uses the Wide bandwidth type [8]. 4G
has the bandwidth of 100 MHz and utilizes the ultra - wide bandwidth type. 5g is supposed to
have a bandwidth of (1000 X BW) per unit area.
Network speed is the important factor from a customer perspective. Thus, the network
speed of 2G is 64 Kbps and 3G is between 144 Kbps to 2 Mbps [9]. The network speed is
developed in the fourth and fifth generation of the wireless communication industry where the
4G provides a network speed of 100 Mbps to 1Gbps while 5G provides a network speed of more
than 1Gbps.
Medium access control mechanism
Medium Access Control or MAC is defined as the layer which handles hardware of a
device that are responsible for the interaction with wireless transmission medium. The core
network type used in 2G is PSTN (Public Switched Telephonic Network) and in case of 3G is
packet Internet. 4G and 5G uses the Internet core network type. 4G provides unified IP as well as
seamless mixture of broadband such as PAN, LAN, WAN and WLAN [7]. In case of 5G, it
provides with unified IP and also provides mixture of broad bands like 4G such as WAN, LAN,
PAN, WLAN and WWWW. The technologies used in 2G is IS-95, GSM. 3G uses IMT2000
WCDMA technology and in 4G it support LTE and WiMAX technologies while 5G supports
VOLTE technology.
Network speed and bandwidth utilization
Bandwidth is the primary factor in wireless mobile technology. It is the capacity of data
that can be transferred from one point to other in given interval of time. The network speed is
totally different with the bandwidth. The bandwidth used in 2G is 900 MHz and it utilized the
narrow band type. 3G has the bandwidth of 100 MHz and uses the Wide bandwidth type [8]. 4G
has the bandwidth of 100 MHz and utilizes the ultra - wide bandwidth type. 5g is supposed to
have a bandwidth of (1000 X BW) per unit area.
Network speed is the important factor from a customer perspective. Thus, the network
speed of 2G is 64 Kbps and 3G is between 144 Kbps to 2 Mbps [9]. The network speed is
developed in the fourth and fifth generation of the wireless communication industry where the
4G provides a network speed of 100 Mbps to 1Gbps while 5G provides a network speed of more
than 1Gbps.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7WIRELESS NETWORK AND SECURITY

8WIRELESS NETWORK AND SECURITY
Security techniques and risk
Various security issues related to the wireless mobile network technology are data
leakage, Unsecured Wi–Fi, Network Spoofing, Phishing attack, Spyware, broken cryptography
and improper session handling. Data leakage is one of the primary issues of the wireless mobile
network technology. This can be mitigated by giving permissions to a valid mobile application.
A Wi-Fi network can be vulnerable for some devices. It can extract all data from the connected
device. This can be mitigated by using the mobile data and avoiding connecting to an unaware
Wi-Fi connection. Network spoofing is set by the hackers by providing fake access points [10].
This is avoided by nit providing the credentials to an outsiders. This security technique can also
be used to stop or avoiding the phishing attack.
5g architecture
5G architecture is highly developed as the network elements as well as different terminals
are upgraded to afford the new situation. These upgrade is dependent on the cognitive radio
technology which comprises of many important factors like weather, temperature and GPRS
facility. The entire architecture of 5G is based on the IP model.
Security techniques and risk
Various security issues related to the wireless mobile network technology are data
leakage, Unsecured Wi–Fi, Network Spoofing, Phishing attack, Spyware, broken cryptography
and improper session handling. Data leakage is one of the primary issues of the wireless mobile
network technology. This can be mitigated by giving permissions to a valid mobile application.
A Wi-Fi network can be vulnerable for some devices. It can extract all data from the connected
device. This can be mitigated by using the mobile data and avoiding connecting to an unaware
Wi-Fi connection. Network spoofing is set by the hackers by providing fake access points [10].
This is avoided by nit providing the credentials to an outsiders. This security technique can also
be used to stop or avoiding the phishing attack.
5g architecture
5G architecture is highly developed as the network elements as well as different terminals
are upgraded to afford the new situation. These upgrade is dependent on the cognitive radio
technology which comprises of many important factors like weather, temperature and GPRS
facility. The entire architecture of 5G is based on the IP model.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
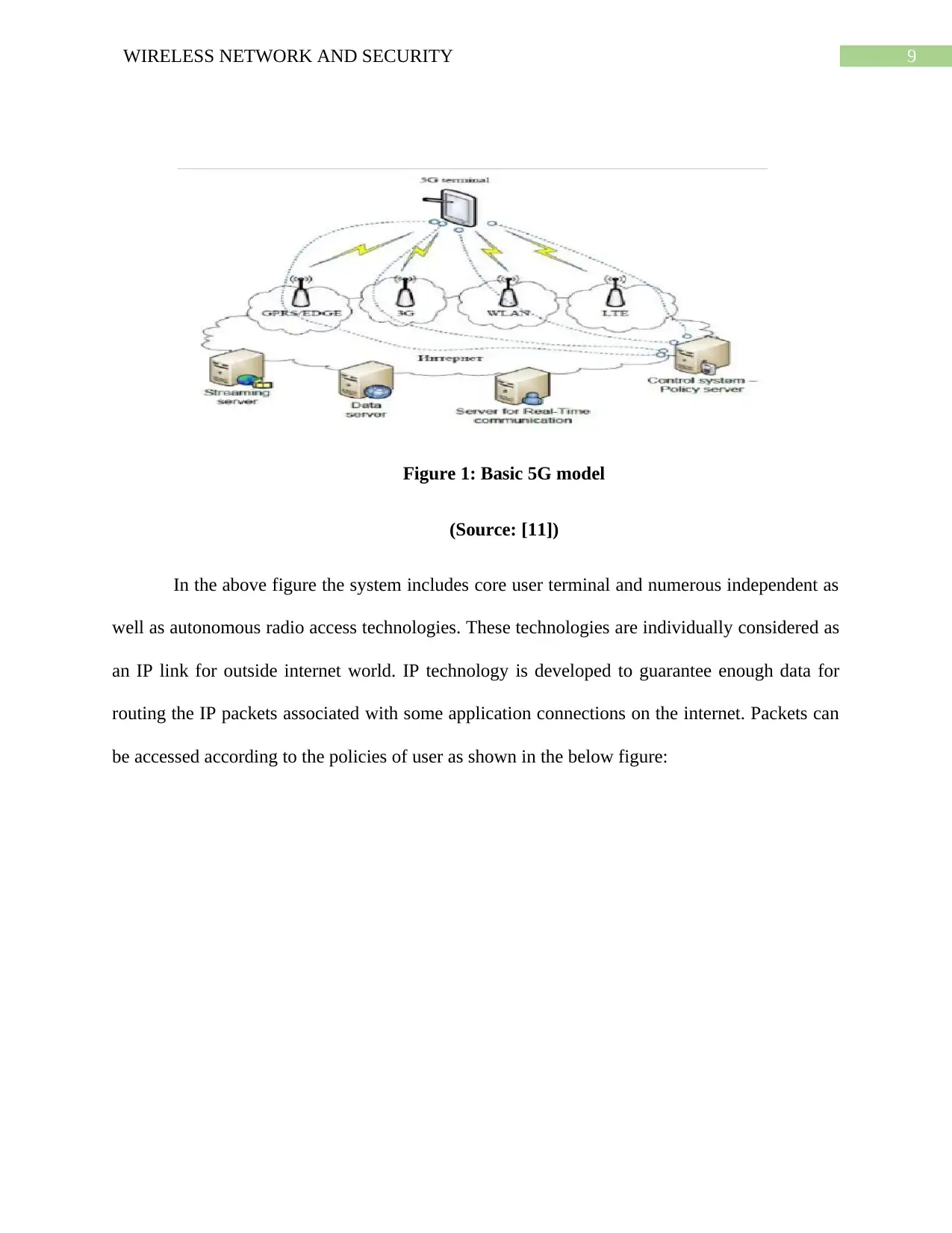
9WIRELESS NETWORK AND SECURITY
Figure 1: Basic 5G model
(Source: [11])
In the above figure the system includes core user terminal and numerous independent as
well as autonomous radio access technologies. These technologies are individually considered as
an IP link for outside internet world. IP technology is developed to guarantee enough data for
routing the IP packets associated with some application connections on the internet. Packets can
be accessed according to the policies of user as shown in the below figure:
Figure 1: Basic 5G model
(Source: [11])
In the above figure the system includes core user terminal and numerous independent as
well as autonomous radio access technologies. These technologies are individually considered as
an IP link for outside internet world. IP technology is developed to guarantee enough data for
routing the IP packets associated with some application connections on the internet. Packets can
be accessed according to the policies of user as shown in the below figure:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
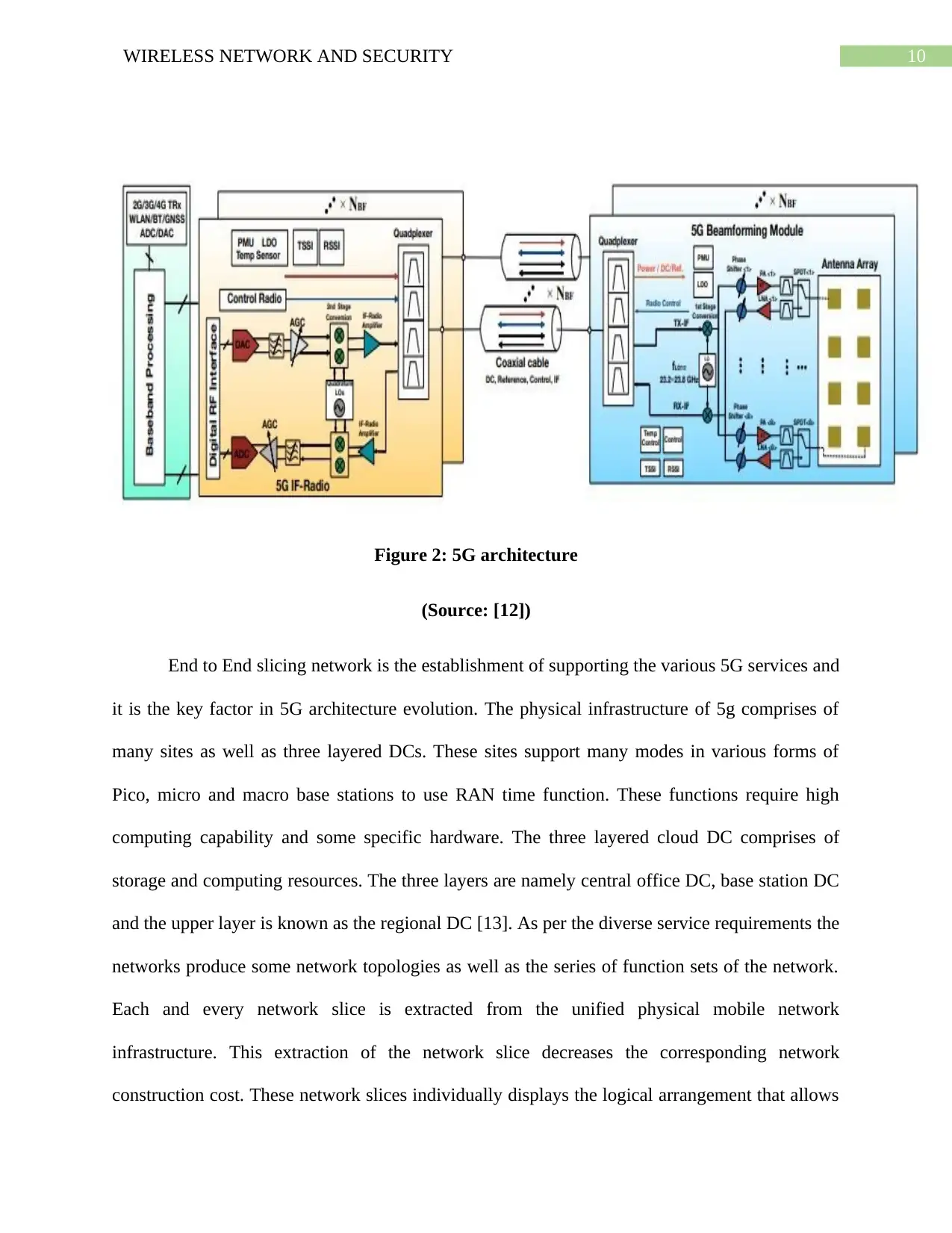
10WIRELESS NETWORK AND SECURITY
Figure 2: 5G architecture
(Source: [12])
End to End slicing network is the establishment of supporting the various 5G services and
it is the key factor in 5G architecture evolution. The physical infrastructure of 5g comprises of
many sites as well as three layered DCs. These sites support many modes in various forms of
Pico, micro and macro base stations to use RAN time function. These functions require high
computing capability and some specific hardware. The three layered cloud DC comprises of
storage and computing resources. The three layers are namely central office DC, base station DC
and the upper layer is known as the regional DC [13]. As per the diverse service requirements the
networks produce some network topologies as well as the series of function sets of the network.
Each and every network slice is extracted from the unified physical mobile network
infrastructure. This extraction of the network slice decreases the corresponding network
construction cost. These network slices individually displays the logical arrangement that allows
Figure 2: 5G architecture
(Source: [12])
End to End slicing network is the establishment of supporting the various 5G services and
it is the key factor in 5G architecture evolution. The physical infrastructure of 5g comprises of
many sites as well as three layered DCs. These sites support many modes in various forms of
Pico, micro and macro base stations to use RAN time function. These functions require high
computing capability and some specific hardware. The three layered cloud DC comprises of
storage and computing resources. The three layers are namely central office DC, base station DC
and the upper layer is known as the regional DC [13]. As per the diverse service requirements the
networks produce some network topologies as well as the series of function sets of the network.
Each and every network slice is extracted from the unified physical mobile network
infrastructure. This extraction of the network slice decreases the corresponding network
construction cost. These network slices individually displays the logical arrangement that allows

11WIRELESS NETWORK AND SECURITY
customized service functions. MCE or Mobile Cloud Engine is a logical entity of the main
control and management of CloudRAN. The network capacity or the network coverage of 5G is
developed by introducing a new technology namely Cloud base SON (cSON) which ensures the
successful implementation of the slicing management [14]. Numerous services of 5G requires
latency which is provided by downloading the shift towards the central or local office of DC.
5G attacks
The various vulnerable threats of 5G are DDoS attack, Wi-Fi access points, Man in the
Middle attacks and Evil Twins. SDN controller modifies or updates the data flow rules which
can be easily identified by the hacker which helps the hacker to carry DDoS attack efficiently.
Moreover, when the programmability is enabled the network function are implemented d in the
SDN applications and thus if a user grant an access to some unaware software some malicious
activity such as havoc can be spread throughout the network layer of the mobile communication
technology.
customized service functions. MCE or Mobile Cloud Engine is a logical entity of the main
control and management of CloudRAN. The network capacity or the network coverage of 5G is
developed by introducing a new technology namely Cloud base SON (cSON) which ensures the
successful implementation of the slicing management [14]. Numerous services of 5G requires
latency which is provided by downloading the shift towards the central or local office of DC.
5G attacks
The various vulnerable threats of 5G are DDoS attack, Wi-Fi access points, Man in the
Middle attacks and Evil Twins. SDN controller modifies or updates the data flow rules which
can be easily identified by the hacker which helps the hacker to carry DDoS attack efficiently.
Moreover, when the programmability is enabled the network function are implemented d in the
SDN applications and thus if a user grant an access to some unaware software some malicious
activity such as havoc can be spread throughout the network layer of the mobile communication
technology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





