T2 2019 MN603 Wireless Networks and Security: 5G Security Evaluation
VerifiedAdded on 2022/09/14
|13
|2823
|11
Report
AI Summary
This report provides an in-depth evaluation of 5G network security, comparing it with 2G, 3G, and 4G technologies. It begins with an introduction to the subject, outlining the motivation for studying 5G networks and their advantages, such as high data capacity and low latency. The report then offers a detailed comparison of various wireless mobile networks, examining factors like MAC mechanisms, security techniques, and communication spectrum. A significant portion of the report is dedicated to analyzing 5G architecture and identifying potential security attacks, including hijacking, signaling storms, and user identity theft. Furthermore, the report addresses the limitations of 5G network coverage, particularly its reliance on millimeter wavelengths, and proposes solutions such as deploying a greater network of antennas and implementing traffic isolation. The report concludes by summarizing the benefits and challenges of 5G technology and highlighting key solutions for addressing the identified issues.

Running Head: NETWORKING
0
Networking
Evaluation and Assessment of 5G Network and Security
(Student Details: )
8/29/2019
0
Networking
Evaluation and Assessment of 5G Network and Security
(Student Details: )
8/29/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
1
Contents
Introduction................................................................................................................................2
Motivation..................................................................................................................................2
A Detailed Comparison of wireless mobile networks................................................................3
2G Mobile Network...............................................................................................................4
3G Mobile Network...............................................................................................................4
4G Mobile Network...............................................................................................................5
5G Mobile Network...............................................................................................................5
5G Architecture..........................................................................................................................6
Identification and Analysis of 5G Attacks.................................................................................7
Identification and Analysis of 5G limitation in-network coverage............................................9
Conclusion................................................................................................................................10
References................................................................................................................................11
1
Contents
Introduction................................................................................................................................2
Motivation..................................................................................................................................2
A Detailed Comparison of wireless mobile networks................................................................3
2G Mobile Network...............................................................................................................4
3G Mobile Network...............................................................................................................4
4G Mobile Network...............................................................................................................5
5G Mobile Network...............................................................................................................5
5G Architecture..........................................................................................................................6
Identification and Analysis of 5G Attacks.................................................................................7
Identification and Analysis of 5G limitation in-network coverage............................................9
Conclusion................................................................................................................................10
References................................................................................................................................11

Networking
2
Evaluation of 5G Network and the Security
Introduction
This research paper is focused on wireless networks and security as well as risk associated
with them. The purpose of conducting research on various wireless networks is to compare
the 5G cellular network technology with the already existing mobile network technologies in
the literature. Besides, the report is going to evaluate the 5G wireless network security with
the help of testing many types of wireless networks’ performance as compared to each other.
In addition to that, the comparison of the standard-based technologies used by the various
networks will be done on the basis of some pre-defined factors such as communication
spectrum. In this context, this study will explore the 5G network architecture for further
researching more about 5G wireless networks 1. Apart from this, with the help of this study,
identification and analysis of the 5G attacks over the access as well as core networks will be
done. In addition to that, this report will also identify and analyze the issues in relation to 5G
network coverage. Furthermore, a solution to address this limitation will also be discussed in
detail. In this way, a summary will be provided at the end of this report.
Motivation
This is necessary to know the reason why using 5G network is necessary. Therefore, this
section will include a discussion on why utilizing the 5G network is suggested for data
services and other mobile services. In this context, the features of 5G wireless network are
helpful, as follows:
It has been found that 5G owns huge data capacity, which is the first key reason to use
it over 4G.
As the 4G network is having less speed hence 5G should be used over 4G
From the perspective of latency, it has been found that 5G offers really low latency
Lastly, a 5G cellular network marks a big step by the predecessor 2.
Moreover, 5G mobile networks are significantly capable to optimize efficiency through
revealing the opportunities like new technologies and automation. Recent surveys show that
5G will allow the world to use advanced technologies such as augmented reality (AR) and
virtual reality (VR). Therefore, the target audience and readers should note that using 5G
2
Evaluation of 5G Network and the Security
Introduction
This research paper is focused on wireless networks and security as well as risk associated
with them. The purpose of conducting research on various wireless networks is to compare
the 5G cellular network technology with the already existing mobile network technologies in
the literature. Besides, the report is going to evaluate the 5G wireless network security with
the help of testing many types of wireless networks’ performance as compared to each other.
In addition to that, the comparison of the standard-based technologies used by the various
networks will be done on the basis of some pre-defined factors such as communication
spectrum. In this context, this study will explore the 5G network architecture for further
researching more about 5G wireless networks 1. Apart from this, with the help of this study,
identification and analysis of the 5G attacks over the access as well as core networks will be
done. In addition to that, this report will also identify and analyze the issues in relation to 5G
network coverage. Furthermore, a solution to address this limitation will also be discussed in
detail. In this way, a summary will be provided at the end of this report.
Motivation
This is necessary to know the reason why using 5G network is necessary. Therefore, this
section will include a discussion on why utilizing the 5G network is suggested for data
services and other mobile services. In this context, the features of 5G wireless network are
helpful, as follows:
It has been found that 5G owns huge data capacity, which is the first key reason to use
it over 4G.
As the 4G network is having less speed hence 5G should be used over 4G
From the perspective of latency, it has been found that 5G offers really low latency
Lastly, a 5G cellular network marks a big step by the predecessor 2.
Moreover, 5G mobile networks are significantly capable to optimize efficiency through
revealing the opportunities like new technologies and automation. Recent surveys show that
5G will allow the world to use advanced technologies such as augmented reality (AR) and
virtual reality (VR). Therefore, the target audience and readers should note that using 5G
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking
3
networks will offer next-generation network connectivity to all of them. In this way, 5G must
be used for reinventing the world in the following mentioned ways:
Autonomous vehicles in the future
Immersive amusement
IoT technologies 3.
Smart cities 4.
Better communication
Better collaboration among global people
From this above discussion, it can be said that the 5G network can definitely help us in future
through supporting remote-place working. Thus, 5G will be helpful for the public for
working effectively and efficiently on cloud-based platforms in real 3.
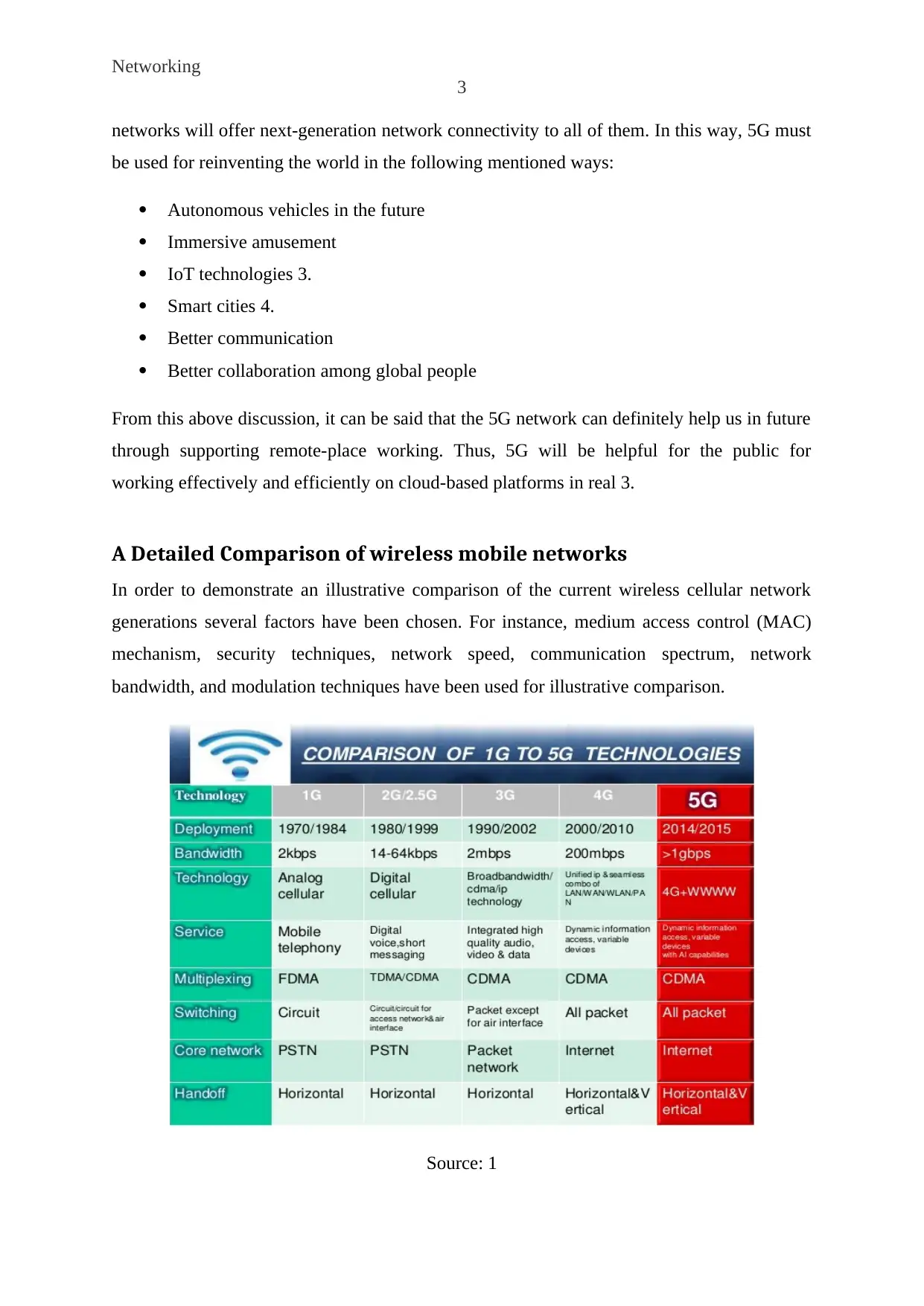
A Detailed Comparison of wireless mobile networks
In order to demonstrate an illustrative comparison of the current wireless cellular network
generations several factors have been chosen. For instance, medium access control (MAC)
mechanism, security techniques, network speed, communication spectrum, network
bandwidth, and modulation techniques have been used for illustrative comparison.
Source: 1
3
networks will offer next-generation network connectivity to all of them. In this way, 5G must
be used for reinventing the world in the following mentioned ways:
Autonomous vehicles in the future
Immersive amusement
IoT technologies 3.
Smart cities 4.
Better communication
Better collaboration among global people
From this above discussion, it can be said that the 5G network can definitely help us in future
through supporting remote-place working. Thus, 5G will be helpful for the public for
working effectively and efficiently on cloud-based platforms in real 3.
A Detailed Comparison of wireless mobile networks
In order to demonstrate an illustrative comparison of the current wireless cellular network
generations several factors have been chosen. For instance, medium access control (MAC)
mechanism, security techniques, network speed, communication spectrum, network
bandwidth, and modulation techniques have been used for illustrative comparison.
Source: 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
4
The above-mentioned figure is motivating the readers to perceive an overview of all 5
wireless networks so that implementation of 5G can be successful in the near future. Here,
‘G’ in the name of 2G, 3G, and 4G stands for ‘generation’. In this context, the purpose of
wireless communication is to offer reliable, high-quality communication similar to wired
communication. Besides, every new wireless network generation denotes a huge step in the
relevant direction. In this way, for comparing mobile communication technologies first we
need to know the key attributes of all of these cellular technologies.
2G Mobile Network
Here, 2G refers to second generation of cellular networks on the basis of GSM. In this
context, the radio signals or modulation techniques used in 1G network were analog in
nature, on the other hand 2G networks were digital in nature. Additionally, 2G cellular
network qualities were attained while allowing multiple users over a sole channel through
multiplexing. The key features of 2G are as follows:
2G uses digital signals in place of analog signals
2G has a data speed of up to 64 Kbps
2G brought a revolution for its users with SMS and MMS services
The bandwidth of 2G is 30-200 kHz
2G has a communication spectrum of 1.8 GHz, digital communication
2G uses modulation techniques of GSM and digital cellular
Security techniques and risks in 2G are WPA authentication that is Wi-Fi protected
access
Security risks are DoS, physical and man-in-the-middle attacks
3G Mobile Network
The 3G mobile network often uses UMTS (universal mobile telecommunications system)
because it is core network architecture. It has been found that 3G technologies comprise
various aspects of the 2G network with novel technologies as well as protocols for delivering
a faster data rate. The features are as follows:
3G uses network speed of up to 2Mbps
3G network technology uses communication spectrum as its operating rand which is
2100 MHz
3G technology has a network bandwidth of 15-20 MHz.
4
The above-mentioned figure is motivating the readers to perceive an overview of all 5
wireless networks so that implementation of 5G can be successful in the near future. Here,
‘G’ in the name of 2G, 3G, and 4G stands for ‘generation’. In this context, the purpose of
wireless communication is to offer reliable, high-quality communication similar to wired
communication. Besides, every new wireless network generation denotes a huge step in the
relevant direction. In this way, for comparing mobile communication technologies first we
need to know the key attributes of all of these cellular technologies.
2G Mobile Network
Here, 2G refers to second generation of cellular networks on the basis of GSM. In this
context, the radio signals or modulation techniques used in 1G network were analog in
nature, on the other hand 2G networks were digital in nature. Additionally, 2G cellular
network qualities were attained while allowing multiple users over a sole channel through
multiplexing. The key features of 2G are as follows:
2G uses digital signals in place of analog signals
2G has a data speed of up to 64 Kbps
2G brought a revolution for its users with SMS and MMS services
The bandwidth of 2G is 30-200 kHz
2G has a communication spectrum of 1.8 GHz, digital communication
2G uses modulation techniques of GSM and digital cellular
Security techniques and risks in 2G are WPA authentication that is Wi-Fi protected
access
Security risks are DoS, physical and man-in-the-middle attacks
3G Mobile Network
The 3G mobile network often uses UMTS (universal mobile telecommunications system)
because it is core network architecture. It has been found that 3G technologies comprise
various aspects of the 2G network with novel technologies as well as protocols for delivering
a faster data rate. The features are as follows:
3G uses network speed of up to 2Mbps
3G network technology uses communication spectrum as its operating rand which is
2100 MHz
3G technology has a network bandwidth of 15-20 MHz.

Networking
5
The bandwidth and data transfer rates are improved as compared to 2G and 1G.
3G has the capability to send or receive huge email messages
3G uses digital signals in place of analog signals
The bandwidth of 3G is 15-20 MHz
3G has a communication spectrum of 2100 MHz
3G uses modulation techniques of UMTS
Security techniques in 3G are Wide Band Wireless Network (WBWN) which
increases the clarity of voice
Security risks are user identity theft, DoS, data breach, physical and man-in-the-
middle attacks and many more
4G Mobile Network
The key difference between 3G and 4G technology is the data rate. The key modulation
technologies which have created 4G are MIMO (Multiple Input Multiple Output) as well as
OFDM (Orthogonal Frequency Division Multiplexing). In addition to that, 4G standards are
WiMAX and LTE. It has been found that 4G LTE is the key improvement over 3G speeds.
The 4G network can be seen as a predetermined standard for mobile network generations.
Besides, the features of 4G LTE are as follows:
4G uses CDMA while using technologies like LTE
4G has a data speed of the network as 1 Gbps-50 Gbps
4G brought a revolution with Ad hoc as well as multi-hop networks
The bandwidth of 4G is 100 MHz
4G has a communication spectrum of packet switching and ultra-broadband
4G uses modulation techniques of VOLTE and WiMAX
Security techniques in 4G are encryption
Security risks are saturation, penetration, complexity, high bandwidth, scanning
issues, data theft and many more
5G Mobile Network
In this context, 5G mobile network will be introduced in near future most probably in 2020.
5G technology will use MIMO with mm Waves. The access system in the case of 5G is
OFDM and BDMA. The switching type which 5G uses is packet switching. Most
importantly, 5G uses WWWW internet service technology that stands for the wireless world
wide web. Network bandwidth for 5G is 30 GHz-300 GHz. The key merits of 5G technology
5
The bandwidth and data transfer rates are improved as compared to 2G and 1G.
3G has the capability to send or receive huge email messages
3G uses digital signals in place of analog signals
The bandwidth of 3G is 15-20 MHz
3G has a communication spectrum of 2100 MHz
3G uses modulation techniques of UMTS
Security techniques in 3G are Wide Band Wireless Network (WBWN) which
increases the clarity of voice
Security risks are user identity theft, DoS, data breach, physical and man-in-the-
middle attacks and many more
4G Mobile Network
The key difference between 3G and 4G technology is the data rate. The key modulation
technologies which have created 4G are MIMO (Multiple Input Multiple Output) as well as
OFDM (Orthogonal Frequency Division Multiplexing). In addition to that, 4G standards are
WiMAX and LTE. It has been found that 4G LTE is the key improvement over 3G speeds.
The 4G network can be seen as a predetermined standard for mobile network generations.
Besides, the features of 4G LTE are as follows:
4G uses CDMA while using technologies like LTE
4G has a data speed of the network as 1 Gbps-50 Gbps
4G brought a revolution with Ad hoc as well as multi-hop networks
The bandwidth of 4G is 100 MHz
4G has a communication spectrum of packet switching and ultra-broadband
4G uses modulation techniques of VOLTE and WiMAX
Security techniques in 4G are encryption
Security risks are saturation, penetration, complexity, high bandwidth, scanning
issues, data theft and many more
5G Mobile Network
In this context, 5G mobile network will be introduced in near future most probably in 2020.
5G technology will use MIMO with mm Waves. The access system in the case of 5G is
OFDM and BDMA. The switching type which 5G uses is packet switching. Most
importantly, 5G uses WWWW internet service technology that stands for the wireless world
wide web. Network bandwidth for 5G is 30 GHz-300 GHz. The key merits of 5G technology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking
6
will be low latency and extremely high speeds. The key application of 5G technologies can
be:
Remote control of autonomous cars
Remote place working in the business
High-resolution video streaming
Medical field progress
5G Architecture
The discussion conducted in this section of the report is containing the 5G architecture. There
can be the number of architectures proposed for 5G networks such as cognitive radio-based,
multi-tier, cloud-based, energy-efficient architectures and device proximity-based ones. In
this way, some important architectures of the future or 5G mobile networks are as follows:
1. CRN-based 5th generation architectures: this is based on how CRNs are usually
deployed within a macro-cell of 5G system.
2. Two-tier 5th generation architectures: this one is based on how small cells are
deployed under macro-cells.
3. D2D Communication 5th generation architectures: this 5G architecture is based on
how devices communicate to the closest devices while not involving an MBS.
4. Energy-efficient 5th generation architectures: the 5G architecture is containing the
mechanism of saving energy in future 5G networks.
Cloud-based 5th generation architectures: if we talk about, cloud-based 5G architecture, then
it is based on how cloud typically facilitates effective communication within future 5G
networks 5.
6
will be low latency and extremely high speeds. The key application of 5G technologies can
be:
Remote control of autonomous cars
Remote place working in the business
High-resolution video streaming
Medical field progress
5G Architecture
The discussion conducted in this section of the report is containing the 5G architecture. There
can be the number of architectures proposed for 5G networks such as cognitive radio-based,
multi-tier, cloud-based, energy-efficient architectures and device proximity-based ones. In
this way, some important architectures of the future or 5G mobile networks are as follows:
1. CRN-based 5th generation architectures: this is based on how CRNs are usually
deployed within a macro-cell of 5G system.
2. Two-tier 5th generation architectures: this one is based on how small cells are
deployed under macro-cells.
3. D2D Communication 5th generation architectures: this 5G architecture is based on
how devices communicate to the closest devices while not involving an MBS.
4. Energy-efficient 5th generation architectures: the 5G architecture is containing the
mechanism of saving energy in future 5G networks.
Cloud-based 5th generation architectures: if we talk about, cloud-based 5G architecture, then
it is based on how cloud typically facilitates effective communication within future 5G
networks 5.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
7
Source: 6
Identification and Analysis of 5G Attacks
In order to identify and analyze security challenges in 5G mobile network technologies,
several attacks can be discussed as follows:
Hijacking attacks are all about violating security barricades of the wireless network.
These attack targets on the SDN controller and hypervisor while affecting the
technologies include NFV, SDN irrespective of privacy issues 7.
Signaling storms are those attacks that considerably affect 5G core network’s key
elements. It also affects technologies like cloud and channels.
Resource theft is a kind of security attack on mutual cloud resources and hypervisor
of the 5G networks. This kind of 5G attacks affect NFV and cloud elements along
with the technologies associated.
User identity theft is the 5G attack that targets user info databases majorly while also
influencing cloud technology. It is worth knowing that this 5G attack also leaves
impact on the privacy of the users 3.
7
Source: 6
Identification and Analysis of 5G Attacks
In order to identify and analyze security challenges in 5G mobile network technologies,
several attacks can be discussed as follows:
Hijacking attacks are all about violating security barricades of the wireless network.
These attack targets on the SDN controller and hypervisor while affecting the
technologies include NFV, SDN irrespective of privacy issues 7.
Signaling storms are those attacks that considerably affect 5G core network’s key
elements. It also affects technologies like cloud and channels.
Resource theft is a kind of security attack on mutual cloud resources and hypervisor
of the 5G networks. This kind of 5G attacks affect NFV and cloud elements along
with the technologies associated.
User identity theft is the 5G attack that targets user info databases majorly while also
influencing cloud technology. It is worth knowing that this 5G attack also leaves
impact on the privacy of the users 3.

Networking
8
Boundary attacks out of all 5G attacks target subscriber location. Apart from this,
semantic info, as well as timing attack, targets subscriber locations within 5G wireless
networks. Besides, boundary attacks raise privacy issues largely.
IMSI catching are those 5G attacks that affect subscriber identity while mainly
affecting channels of 5G. In addition, IMSI catching type 5G attack significantly
gives rise to privacy issues.
In this way, it can be summarized that 5G attacks such as man-in-the-middle, user identity
theft, scanning attacks, IMSI catching, boundary, timing, and semantic information attacks
critically affect the privacy of the users in 5G mobile networks 8.
Source: 3
8
Boundary attacks out of all 5G attacks target subscriber location. Apart from this,
semantic info, as well as timing attack, targets subscriber locations within 5G wireless
networks. Besides, boundary attacks raise privacy issues largely.
IMSI catching are those 5G attacks that affect subscriber identity while mainly
affecting channels of 5G. In addition, IMSI catching type 5G attack significantly
gives rise to privacy issues.
In this way, it can be summarized that 5G attacks such as man-in-the-middle, user identity
theft, scanning attacks, IMSI catching, boundary, timing, and semantic information attacks
critically affect the privacy of the users in 5G mobile networks 8.
Source: 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking
9
Source: 5
Identification and Analysis of 5G limitation in-network coverage
The identification and analysis of 5G limitations as network coverage is focused on the issues
related to network coverage in 5G specifically 9. Post identifying the reasons behind the 5G
limitations of network coverage, possible solutions will be discussed. As we know that
5G mobile network uses millimeter wavelengths which are significantly lower than 4G as
well as 3G, thus it is an issue for network coverage 10. The above is the reason that 5G
network waves are not capable to travel as far as 4G and 3G can. In addition to that, the 5G
wireless network coverage profile is less efficient than 4G and 3G, which restricts the
network’s signals to cover much region than 4G network signals can. However,
the 5G signals are capable to store more data than the 3G and 4G networks 11. Consequently,
the remote, as well as rural regions, probably will not able to leverage 5G cellular services in
the near future. Therefore, 5G cellular technologies will provide better network services as
compared to the currently used wireless network generations. On the other hand, as key
limitation proximity in 5G network is a weakness which must be considered by the modern
businesses. In order to address such limitation, 5G network signal carriers should be
continuously planned in a much greater network of antennas for efficiently providing
adequate network coverage to its users 12.
Source: 2
Apart from this, potential security solutions for the 5G limitations are as follows:
9
Source: 5
Identification and Analysis of 5G limitation in-network coverage
The identification and analysis of 5G limitations as network coverage is focused on the issues
related to network coverage in 5G specifically 9. Post identifying the reasons behind the 5G
limitations of network coverage, possible solutions will be discussed. As we know that
5G mobile network uses millimeter wavelengths which are significantly lower than 4G as
well as 3G, thus it is an issue for network coverage 10. The above is the reason that 5G
network waves are not capable to travel as far as 4G and 3G can. In addition to that, the 5G
wireless network coverage profile is less efficient than 4G and 3G, which restricts the
network’s signals to cover much region than 4G network signals can. However,
the 5G signals are capable to store more data than the 3G and 4G networks 11. Consequently,
the remote, as well as rural regions, probably will not able to leverage 5G cellular services in
the near future. Therefore, 5G cellular technologies will provide better network services as
compared to the currently used wireless network generations. On the other hand, as key
limitation proximity in 5G network is a weakness which must be considered by the modern
businesses. In order to address such limitation, 5G network signal carriers should be
continuously planned in a much greater network of antennas for efficiently providing
adequate network coverage to its users 12.
Source: 2
Apart from this, potential security solutions for the 5G limitations are as follows:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
10
Traffic isolation
Access control 11.
Dos and DDoS detection
Link security
Configuration verification
Identity security and verification
Location and IMSI security
Integrity verification
Service access control
HX-Dos mitigation 13.
Conclusion
In conclusion, this report has successfully found important benefits as well as challenges
within 5G mobile network technology as compared to the current wireless network
technologies. Besides, the paper has meaningfully proposed key solutions for addressing the
5G challenges, security issues, and limitations. In addition to that, the discussion has
successfully evaluated the wireless communication standards for various wireless cyber-
physical systems as well as IoT. Moreover, proposed research report on wireless networks
and security has covered all possible features of 5G cellular networks in order to encourage
the readers to utilize 5G technology for efficient business and other operations. Finally, the
research study has successfully engaged the readers and thereby motivated them for using 5G
in the near future.
10
Traffic isolation
Access control 11.
Dos and DDoS detection
Link security
Configuration verification
Identity security and verification
Location and IMSI security
Integrity verification
Service access control
HX-Dos mitigation 13.
Conclusion
In conclusion, this report has successfully found important benefits as well as challenges
within 5G mobile network technology as compared to the current wireless network
technologies. Besides, the paper has meaningfully proposed key solutions for addressing the
5G challenges, security issues, and limitations. In addition to that, the discussion has
successfully evaluated the wireless communication standards for various wireless cyber-
physical systems as well as IoT. Moreover, proposed research report on wireless networks
and security has covered all possible features of 5G cellular networks in order to encourage
the readers to utilize 5G technology for efficient business and other operations. Finally, the
research study has successfully engaged the readers and thereby motivated them for using 5G
in the near future.

Networking
11
References
x
[1] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[2] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[3] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[4] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[5] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[6] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[7] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[8] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[9] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
[10] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
[11] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
11
References
x
[1] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[2] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[3] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[4] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[5] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[6] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[7] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[8] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[9] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
[10] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
[11] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





