Comprehensive Analysis of 5G Network Security and its Vulnerabilities
VerifiedAdded on 2022/09/29
|11
|2655
|23
Report
AI Summary
This report offers a detailed analysis of 5G network security, comparing it with 2G, 3G, and 4G technologies. It explores the motivations behind adopting 5G, highlighting its advantages such as improved data speed, low latency, and increased capacity. The report then presents a comparative analysis of the four cellular networks, focusing on factors like security techniques, network speed, and modulation techniques. It delves into the architecture of 5G networks, including CRN-based, two-tier, and cloud-based architectures. Furthermore, the report identifies and analyzes potential 5G attacks, such as configuration attacks, DoS attacks, and security key exposures, along with the limitations of 5G in terms of network coverage. The conclusion summarizes the key benefits and challenges, proposing solutions to address security issues and limitations. The report emphasizes the importance of 5G in supporting advanced technologies like VR, AR, and IoT, and its role in the future of communication.

Running Head: NETWORKING
0
Networking
5G Network and Security
(Student Details: )
8/27/2019
0
Networking
5G Network and Security
(Student Details: )
8/27/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
1
Contents
Wireless Networks and Security................................................................................................2
Introduction................................................................................................................................2
Motivation..................................................................................................................................2
Comparison of four cellular networks........................................................................................3
2G Cellular Network..............................................................................................................4
3G Cellular Network..............................................................................................................4
4G-LTE Cellular Network.....................................................................................................5
5G Cellular Network..............................................................................................................5
5G Architecture..........................................................................................................................5
Identification and Analysis of 5G Attacks.................................................................................7
Identification and Analysis of 5G limitation in-network coverage............................................8
Conclusion..................................................................................................................................8
References..................................................................................................................................9
1
Contents
Wireless Networks and Security................................................................................................2
Introduction................................................................................................................................2
Motivation..................................................................................................................................2
Comparison of four cellular networks........................................................................................3
2G Cellular Network..............................................................................................................4
3G Cellular Network..............................................................................................................4
4G-LTE Cellular Network.....................................................................................................5
5G Cellular Network..............................................................................................................5
5G Architecture..........................................................................................................................5
Identification and Analysis of 5G Attacks.................................................................................7
Identification and Analysis of 5G limitation in-network coverage............................................8
Conclusion..................................................................................................................................8
References..................................................................................................................................9

Networking
2
Wireless Networks and Security
Introduction
The research report is emphasized on evaluating different wireless networks and security
systems include 2G, 3G, 4G, and 5G wireless networks. In this context, the paper is
particularly focused to compare the 5G wireless communication technologies with all of the
existing cellular network technologies in the literature of wireless networks. In this way, with
the help of this discussion, a detailed evaluation of the 5G network security will take place.
Generally, 5G network us the new cellular network which is going to replace the present 4G
cellular network technology. It has been found that 5G generation owns greater energy
savings, data rates, reduced latency, higher system capacity, reduced cost as well as massive
device connectivity while offering network services 1. Thus, here the discussion will cover a
comparison of many wireless technologies which are being used presently. While motivating
the readers, a summary will be added at the end of this research report.
Motivation
This discussion is containing the number of reasons why the world should use 5G network
services for high data rates while using the internet during their daily-life. Therefore, such
reasons why we require moving to 5th generation during upcoming years are as follows:
The new 5G technology owns an improved data speed than 4G technology
The new 5G technology is capable to offer incredibly low latency
The new 5G technology carries larger data capacity than any other wireless network
Lastly, the new 5G technology marks a huge step from the predecessor 2.
Recent surveys are suggesting that 5G cellular networks are capable to offer enhanced
efficiency which is the positive point leading us towards using 5th generation over 4G.
Besides, 5G is able to unleash the opportunities for automation area in future. Therefore, it
has been revealed that 5G cellular network technology should be used presently as well as in
future as it will allow the whole world to use and leverage advanced technologies such as
virtual reality (VR) and augmented reality (AR) 3. Hence, the readers should see 5G as the
2
Wireless Networks and Security
Introduction
The research report is emphasized on evaluating different wireless networks and security
systems include 2G, 3G, 4G, and 5G wireless networks. In this context, the paper is
particularly focused to compare the 5G wireless communication technologies with all of the
existing cellular network technologies in the literature of wireless networks. In this way, with
the help of this discussion, a detailed evaluation of the 5G network security will take place.
Generally, 5G network us the new cellular network which is going to replace the present 4G
cellular network technology. It has been found that 5G generation owns greater energy
savings, data rates, reduced latency, higher system capacity, reduced cost as well as massive
device connectivity while offering network services 1. Thus, here the discussion will cover a
comparison of many wireless technologies which are being used presently. While motivating
the readers, a summary will be added at the end of this research report.
Motivation
This discussion is containing the number of reasons why the world should use 5G network
services for high data rates while using the internet during their daily-life. Therefore, such
reasons why we require moving to 5th generation during upcoming years are as follows:
The new 5G technology owns an improved data speed than 4G technology
The new 5G technology is capable to offer incredibly low latency
The new 5G technology carries larger data capacity than any other wireless network
Lastly, the new 5G technology marks a huge step from the predecessor 2.
Recent surveys are suggesting that 5G cellular networks are capable to offer enhanced
efficiency which is the positive point leading us towards using 5th generation over 4G.
Besides, 5G is able to unleash the opportunities for automation area in future. Therefore, it
has been revealed that 5G cellular network technology should be used presently as well as in
future as it will allow the whole world to use and leverage advanced technologies such as
virtual reality (VR) and augmented reality (AR) 3. Hence, the readers should see 5G as the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking
3
next-generation network whose connectivity is the source for reinventing the world in the
below-listed ways:
Autonomous vehicles
IoT technologies and ICT 4.
Enriched communication and collaboration
Immersive amusement
Smart cities 5.
In a nutshell, the 5G cellular network is definitely going to support remote place working,
and thereby it will remove the barriers of the distance working and education as well. The
cloud-based collaborative documents along with real-time platforms, 5G will take the whole
world to the next level of future opportunities 6.
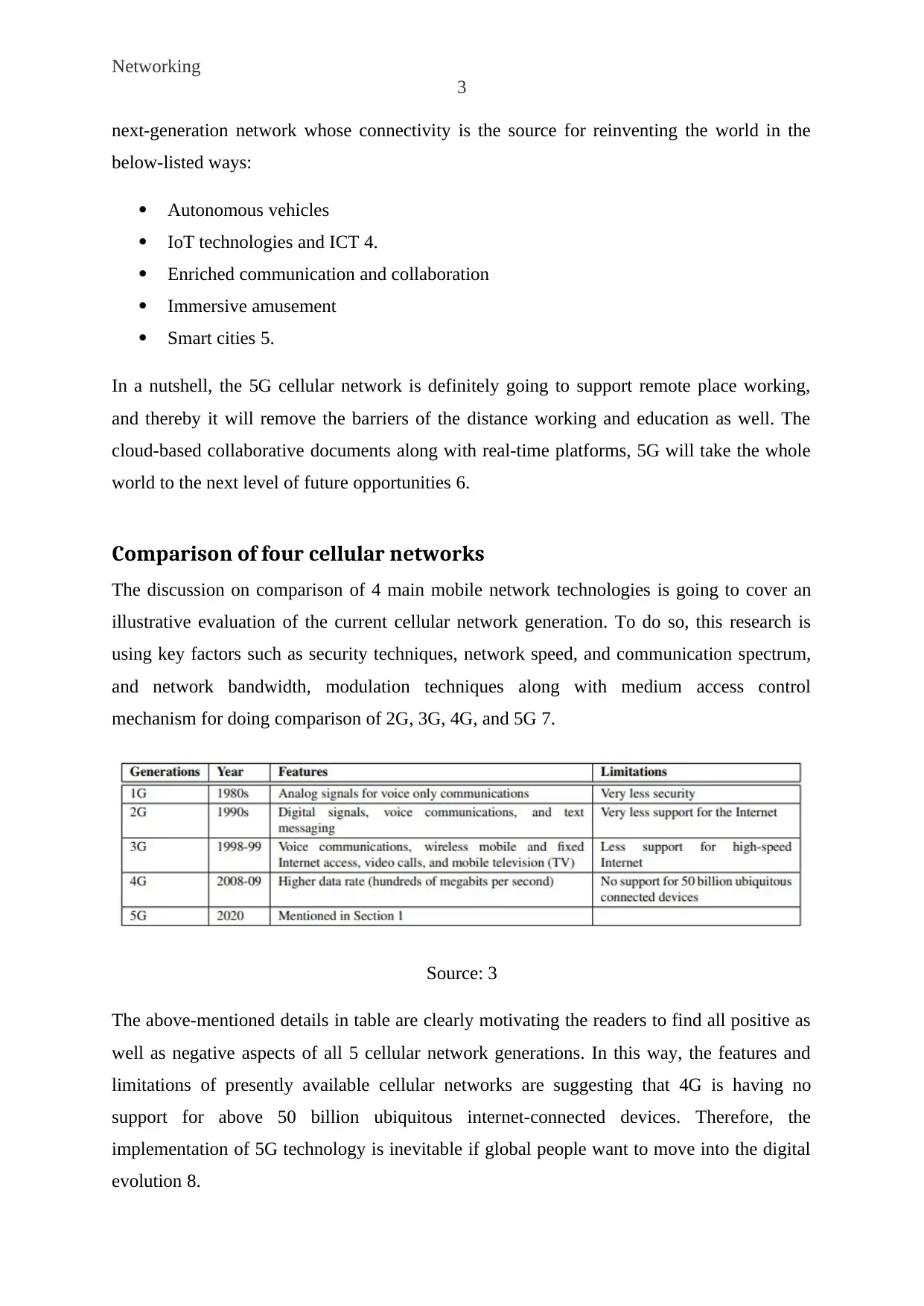
Comparison of four cellular networks
The discussion on comparison of 4 main mobile network technologies is going to cover an
illustrative evaluation of the current cellular network generation. To do so, this research is
using key factors such as security techniques, network speed, and communication spectrum,
and network bandwidth, modulation techniques along with medium access control
mechanism for doing comparison of 2G, 3G, 4G, and 5G 7.
Source: 3
The above-mentioned details in table are clearly motivating the readers to find all positive as
well as negative aspects of all 5 cellular network generations. In this way, the features and
limitations of presently available cellular networks are suggesting that 4G is having no
support for above 50 billion ubiquitous internet-connected devices. Therefore, the
implementation of 5G technology is inevitable if global people want to move into the digital
evolution 8.
3
next-generation network whose connectivity is the source for reinventing the world in the
below-listed ways:
Autonomous vehicles
IoT technologies and ICT 4.
Enriched communication and collaboration
Immersive amusement
Smart cities 5.
In a nutshell, the 5G cellular network is definitely going to support remote place working,
and thereby it will remove the barriers of the distance working and education as well. The
cloud-based collaborative documents along with real-time platforms, 5G will take the whole
world to the next level of future opportunities 6.
Comparison of four cellular networks
The discussion on comparison of 4 main mobile network technologies is going to cover an
illustrative evaluation of the current cellular network generation. To do so, this research is
using key factors such as security techniques, network speed, and communication spectrum,
and network bandwidth, modulation techniques along with medium access control
mechanism for doing comparison of 2G, 3G, 4G, and 5G 7.
Source: 3
The above-mentioned details in table are clearly motivating the readers to find all positive as
well as negative aspects of all 5 cellular network generations. In this way, the features and
limitations of presently available cellular networks are suggesting that 4G is having no
support for above 50 billion ubiquitous internet-connected devices. Therefore, the
implementation of 5G technology is inevitable if global people want to move into the digital
evolution 8.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Networking
4
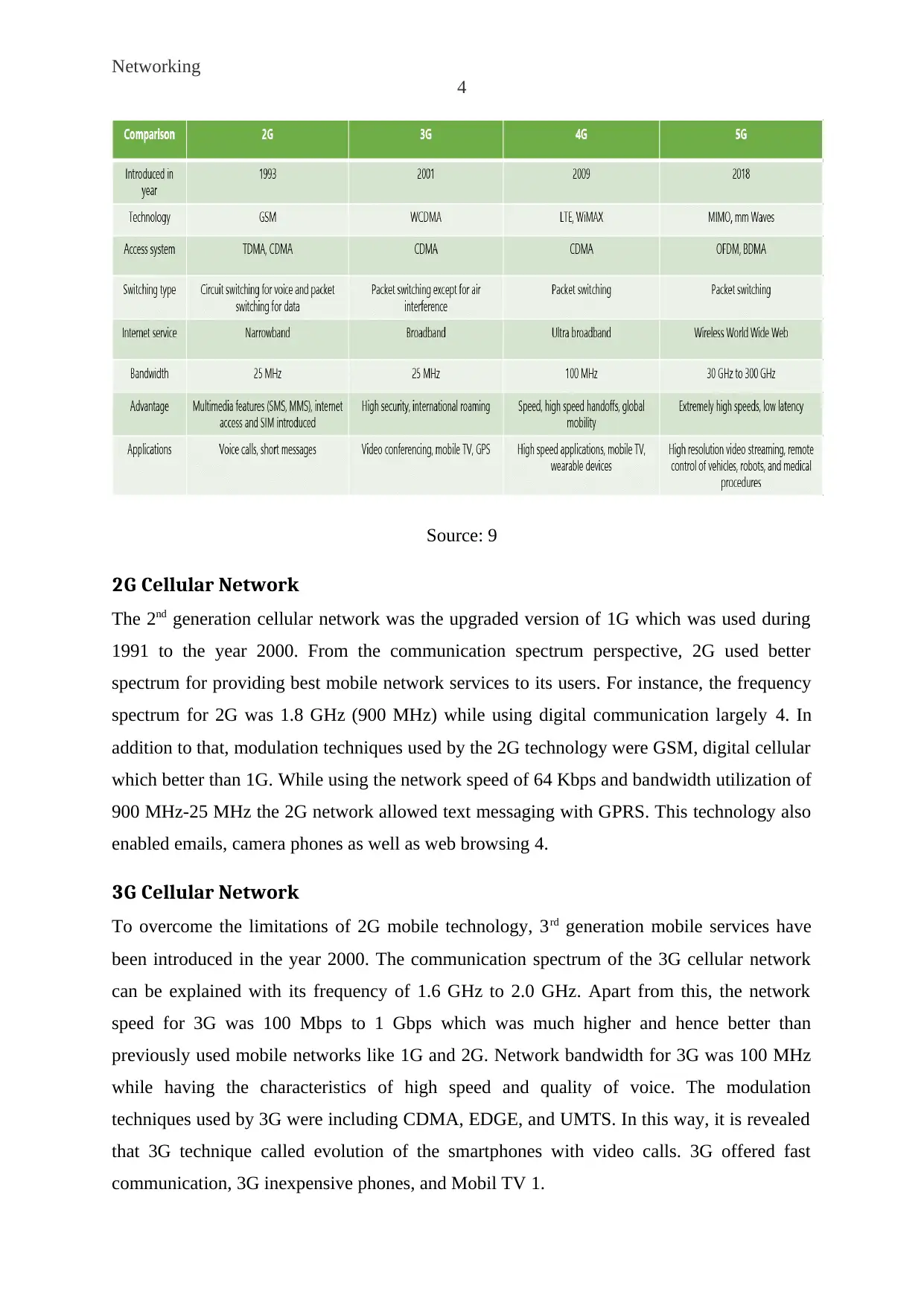
Source: 9
2G Cellular Network
The 2nd generation cellular network was the upgraded version of 1G which was used during
1991 to the year 2000. From the communication spectrum perspective, 2G used better
spectrum for providing best mobile network services to its users. For instance, the frequency
spectrum for 2G was 1.8 GHz (900 MHz) while using digital communication largely 4. In
addition to that, modulation techniques used by the 2G technology were GSM, digital cellular
which better than 1G. While using the network speed of 64 Kbps and bandwidth utilization of
900 MHz-25 MHz the 2G network allowed text messaging with GPRS. This technology also
enabled emails, camera phones as well as web browsing 4.
3G Cellular Network
To overcome the limitations of 2G mobile technology, 3rd generation mobile services have
been introduced in the year 2000. The communication spectrum of the 3G cellular network
can be explained with its frequency of 1.6 GHz to 2.0 GHz. Apart from this, the network
speed for 3G was 100 Mbps to 1 Gbps which was much higher and hence better than
previously used mobile networks like 1G and 2G. Network bandwidth for 3G was 100 MHz
while having the characteristics of high speed and quality of voice. The modulation
techniques used by 3G were including CDMA, EDGE, and UMTS. In this way, it is revealed
that 3G technique called evolution of the smartphones with video calls. 3G offered fast
communication, 3G inexpensive phones, and Mobil TV 1.
4
Source: 9
2G Cellular Network
The 2nd generation cellular network was the upgraded version of 1G which was used during
1991 to the year 2000. From the communication spectrum perspective, 2G used better
spectrum for providing best mobile network services to its users. For instance, the frequency
spectrum for 2G was 1.8 GHz (900 MHz) while using digital communication largely 4. In
addition to that, modulation techniques used by the 2G technology were GSM, digital cellular
which better than 1G. While using the network speed of 64 Kbps and bandwidth utilization of
900 MHz-25 MHz the 2G network allowed text messaging with GPRS. This technology also
enabled emails, camera phones as well as web browsing 4.
3G Cellular Network
To overcome the limitations of 2G mobile technology, 3rd generation mobile services have
been introduced in the year 2000. The communication spectrum of the 3G cellular network
can be explained with its frequency of 1.6 GHz to 2.0 GHz. Apart from this, the network
speed for 3G was 100 Mbps to 1 Gbps which was much higher and hence better than
previously used mobile networks like 1G and 2G. Network bandwidth for 3G was 100 MHz
while having the characteristics of high speed and quality of voice. The modulation
techniques used by 3G were including CDMA, EDGE, and UMTS. In this way, it is revealed
that 3G technique called evolution of the smartphones with video calls. 3G offered fast
communication, 3G inexpensive phones, and Mobil TV 1.

Networking
5
4G-LTE Cellular Network
It is the mobile network service that is being currently used by the whole world. In this
context, 4G cellular networks significantly enabled the proliferation of multimedia traffic,
smart devices as well as new services into present mobile domain. Thus, the development of
4G has led to much complicated as well as dynamic threat landscapes. This wireless network
service is known for higher data rates of 100 Mbps normally. While comparing 4G and 5G,
the research has used factors like data traffic, latency, peak data rates, connection density, and
available spectrum. While talking about latency, then 4G is having 10 ms latency whereas
5G’s latency is less than 1 ms. On the other hand, data traffic of the 4G network is 7.2
Exabytes per month while 5G is anticipated to have 50 Exabytes per month in the year 2021
7.
5G Cellular Network
There are some limitations of the presently available wireless network as 4G, which needs to
be addressed by launching and thereby using 5G cellular network, as follows:
4G incurs inefficient use of processing abilities of a base station
4G provides no support for bulky data traffics
4G introduces co-channel interference
4G gives no support to heterogeneous wireless networks
4G shows latency issues
4G incurs no separation amid indoor and outdoor users
The mobile service providers of present era are planning the transition to 5G technology for
effectively supporting the increased number of devices that require internet access all the
time. In order to address the demand for high bandwidth by the millennial users for
functioning smoothly, 5G network technology is being suggested within this research paper.
However, with the advent of 5G wireless networks, the security issues, threat vectors will
become bigger than ever before with enhanced privacy concerns 6.
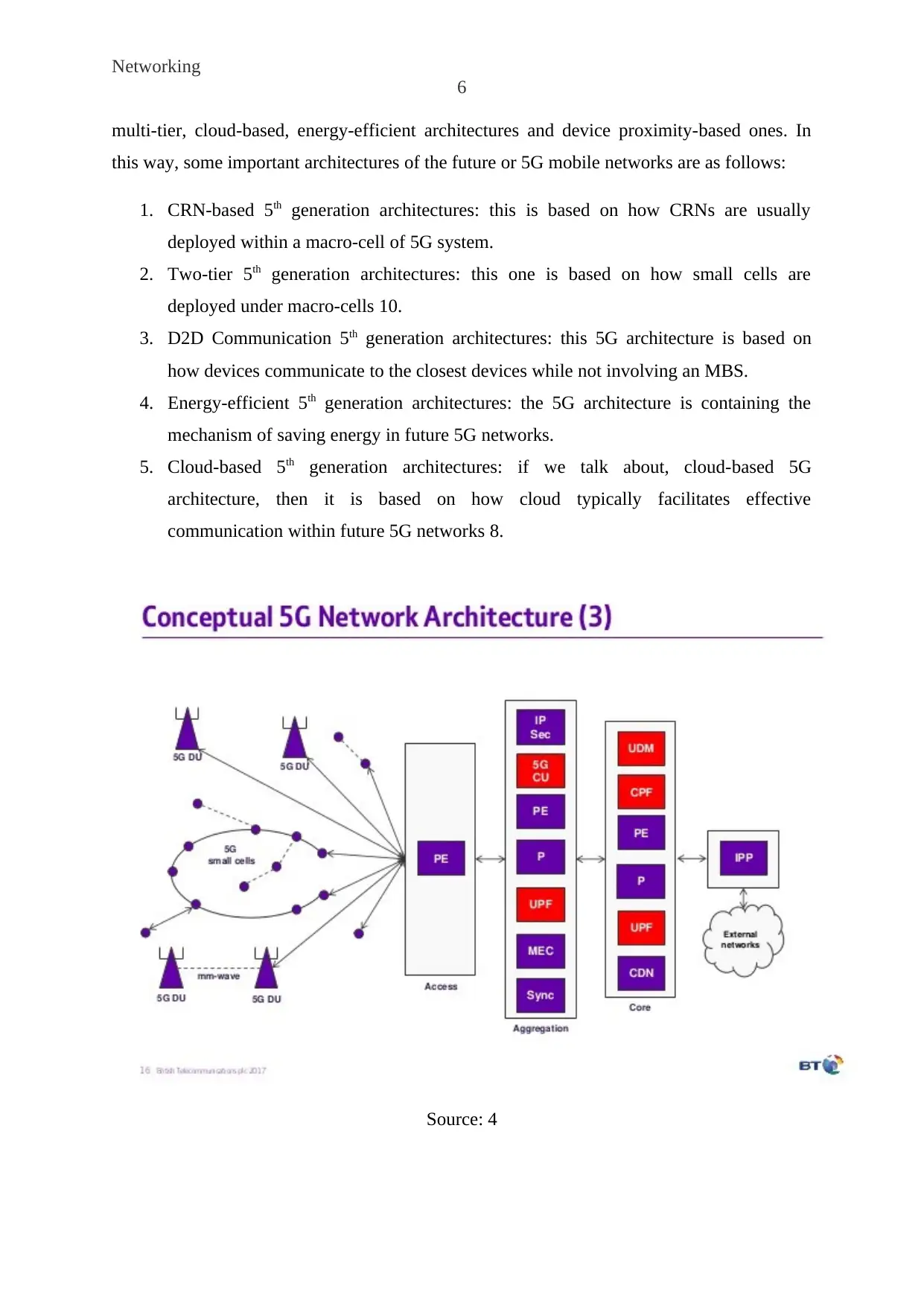
5th Generation Architecture
The discussion conducted in this section of the report is containing the 5G architecture. There
can be number of architectures proposed for 5G networks such as cognitive radio-based,
5
4G-LTE Cellular Network
It is the mobile network service that is being currently used by the whole world. In this
context, 4G cellular networks significantly enabled the proliferation of multimedia traffic,
smart devices as well as new services into present mobile domain. Thus, the development of
4G has led to much complicated as well as dynamic threat landscapes. This wireless network
service is known for higher data rates of 100 Mbps normally. While comparing 4G and 5G,
the research has used factors like data traffic, latency, peak data rates, connection density, and
available spectrum. While talking about latency, then 4G is having 10 ms latency whereas
5G’s latency is less than 1 ms. On the other hand, data traffic of the 4G network is 7.2
Exabytes per month while 5G is anticipated to have 50 Exabytes per month in the year 2021
7.
5G Cellular Network
There are some limitations of the presently available wireless network as 4G, which needs to
be addressed by launching and thereby using 5G cellular network, as follows:
4G incurs inefficient use of processing abilities of a base station
4G provides no support for bulky data traffics
4G introduces co-channel interference
4G gives no support to heterogeneous wireless networks
4G shows latency issues
4G incurs no separation amid indoor and outdoor users
The mobile service providers of present era are planning the transition to 5G technology for
effectively supporting the increased number of devices that require internet access all the
time. In order to address the demand for high bandwidth by the millennial users for
functioning smoothly, 5G network technology is being suggested within this research paper.
However, with the advent of 5G wireless networks, the security issues, threat vectors will
become bigger than ever before with enhanced privacy concerns 6.
5th Generation Architecture
The discussion conducted in this section of the report is containing the 5G architecture. There
can be number of architectures proposed for 5G networks such as cognitive radio-based,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking
6
multi-tier, cloud-based, energy-efficient architectures and device proximity-based ones. In
this way, some important architectures of the future or 5G mobile networks are as follows:
1. CRN-based 5th generation architectures: this is based on how CRNs are usually
deployed within a macro-cell of 5G system.
2. Two-tier 5th generation architectures: this one is based on how small cells are
deployed under macro-cells 10.
3. D2D Communication 5th generation architectures: this 5G architecture is based on
how devices communicate to the closest devices while not involving an MBS.
4. Energy-efficient 5th generation architectures: the 5G architecture is containing the
mechanism of saving energy in future 5G networks.
5. Cloud-based 5th generation architectures: if we talk about, cloud-based 5G
architecture, then it is based on how cloud typically facilitates effective
communication within future 5G networks 8.
Source: 4
6
multi-tier, cloud-based, energy-efficient architectures and device proximity-based ones. In
this way, some important architectures of the future or 5G mobile networks are as follows:
1. CRN-based 5th generation architectures: this is based on how CRNs are usually
deployed within a macro-cell of 5G system.
2. Two-tier 5th generation architectures: this one is based on how small cells are
deployed under macro-cells 10.
3. D2D Communication 5th generation architectures: this 5G architecture is based on
how devices communicate to the closest devices while not involving an MBS.
4. Energy-efficient 5th generation architectures: the 5G architecture is containing the
mechanism of saving energy in future 5G networks.
5. Cloud-based 5th generation architectures: if we talk about, cloud-based 5G
architecture, then it is based on how cloud typically facilitates effective
communication within future 5G networks 8.
Source: 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
7
Analysis and Identification of 5G Attacks
Within this discussion, the report is going to identify as well as analyse the security
challenges in the context of 5G mobile technology 2. While analysing the security threats
caused by the 5G technology, it has been found that following 5G attacks are important to be
addressed while implementing 5G over existing 4G:
Configuration attacks: the network elements or the target points for such 5G attacks
are SDN switches, virtual switches, and routers. Thus, the affected technologies
include NFV and SDN while no privacy issues found 11.
DoS attacks: this 5G attack type is indeed a security threat for the entire system. This
5G attack targets centralized control elements hence it is worst security threat caused
by such cellular networks. Besides, the affected technologies are cloud, NFV, and
SDN. No privacy issues are usually found in the DoS attack.
Saturation attacks: these attacks typically target SDN switches and controllers as well
while affecting the technology SDN 11.
Penetration attacks: this 5G attack mainly influences the network element virtual
resources as well as clouds while affecting the technologies like cloud and NFV.
TCP-level attacks: this kind of 5G attack usually affect switch communication-SDN
controller while influencing the technologies such as channels and SDN.
Security key exposures: this is a 5G attack that majorly targets over unencrypted
channels while affecting the channel's technology within the wireless network 12.
Analysis and Identification of 5G limitation in-network coverage
While presenting the comparison of the already existing cellular network generations include
2G, 3G, 4G, and 5G then the discussion used some specific factors for the comparison 13.
These factors were communication spectrum, modulation techniques, security techniques,
MAC mechanism, and network speed as well as network bandwidth utilisation 7. It has been
identified that 5G has its own limitations in the field of network coverage because 5G is
having millimeter wave (mmWave) technology that needs the deployment of lots of 5G
nodes. It is evident that 5G signals have a short-range and are easily blocked by walls 1.
Apart from this, this research has identified many of the 5G attacks which contain serious
privacy issues along with affected technologies like NFV, SDN, Cloud, and Channels. Such
5G attacks are as follows:
7
Analysis and Identification of 5G Attacks
Within this discussion, the report is going to identify as well as analyse the security
challenges in the context of 5G mobile technology 2. While analysing the security threats
caused by the 5G technology, it has been found that following 5G attacks are important to be
addressed while implementing 5G over existing 4G:
Configuration attacks: the network elements or the target points for such 5G attacks
are SDN switches, virtual switches, and routers. Thus, the affected technologies
include NFV and SDN while no privacy issues found 11.
DoS attacks: this 5G attack type is indeed a security threat for the entire system. This
5G attack targets centralized control elements hence it is worst security threat caused
by such cellular networks. Besides, the affected technologies are cloud, NFV, and
SDN. No privacy issues are usually found in the DoS attack.
Saturation attacks: these attacks typically target SDN switches and controllers as well
while affecting the technology SDN 11.
Penetration attacks: this 5G attack mainly influences the network element virtual
resources as well as clouds while affecting the technologies like cloud and NFV.
TCP-level attacks: this kind of 5G attack usually affect switch communication-SDN
controller while influencing the technologies such as channels and SDN.
Security key exposures: this is a 5G attack that majorly targets over unencrypted
channels while affecting the channel's technology within the wireless network 12.
Analysis and Identification of 5G limitation in-network coverage
While presenting the comparison of the already existing cellular network generations include
2G, 3G, 4G, and 5G then the discussion used some specific factors for the comparison 13.
These factors were communication spectrum, modulation techniques, security techniques,
MAC mechanism, and network speed as well as network bandwidth utilisation 7. It has been
identified that 5G has its own limitations in the field of network coverage because 5G is
having millimeter wave (mmWave) technology that needs the deployment of lots of 5G
nodes. It is evident that 5G signals have a short-range and are easily blocked by walls 1.
Apart from this, this research has identified many of the 5G attacks which contain serious
privacy issues along with affected technologies like NFV, SDN, Cloud, and Channels. Such
5G attacks are as follows:

Networking
8
IMSI catching attacks
Boundary attacks
Timing attacks 14.
Semantic information attacks
Scanning attacks
Man-in-the-middle attacks
User-identity theft attacks 15.
Summary
In whole, the research report has found key benefits and challenges in 5G cellular network
technology as compared to the current wireless communication network technologies. For
doing so, this report has meaningfully proposed key solutions for addressing the 5G
challenges, security issues, and limitations. Moreover, the discussion has successfully
evaluated the wireless communication standards for various wireless cyber-physical systems
as well as IoT. In addition to that, proposed research report on wireless networks and security
has covered all possible features of 5G cellular networks in order to encourage the readers to
utilise 5G technology in the near future.
8
IMSI catching attacks
Boundary attacks
Timing attacks 14.
Semantic information attacks
Scanning attacks
Man-in-the-middle attacks
User-identity theft attacks 15.
Summary
In whole, the research report has found key benefits and challenges in 5G cellular network
technology as compared to the current wireless communication network technologies. For
doing so, this report has meaningfully proposed key solutions for addressing the 5G
challenges, security issues, and limitations. Moreover, the discussion has successfully
evaluated the wireless communication standards for various wireless cyber-physical systems
as well as IoT. In addition to that, proposed research report on wireless networks and security
has covered all possible features of 5G cellular networks in order to encourage the readers to
utilise 5G technology in the near future.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking
9
References
x
[1] M. Agiwal, A. Roy, and N. Saxena, "Next generation 5G wireless networks: A
comprehensive survey," IEEE communications surveys and tutorials, vol. 18, no. 3, pp.
1617-1655, 2016.
[2] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
[3] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[4] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[5] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[6] L.C. Wang and S. Rangapillai, "A survey on green 5G cellular networks," in
International conference on Signal Processing and Comunnicatiobs SPCOM, New
York, 2012, pp. 1-5.
[7] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[8] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[9] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[10] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
no. 3, pp. 132-137, 2015.
[11] Y. Huo, X. Dong, and W. Xu, "5G Cellular User Equipment: From Theory to Practical
Hardware Design," IEEE Access, vol. 5, pp. 13992-14010, 2017.
[12] C.X. Mavromoustakis, G. Mastorakis, and J.M. Batalla, Internet of Things (IoT) in 5G
mobile technologies. UK: Springer, 2016.
9
References
x
[1] M. Agiwal, A. Roy, and N. Saxena, "Next generation 5G wireless networks: A
comprehensive survey," IEEE communications surveys and tutorials, vol. 18, no. 3, pp.
1617-1655, 2016.
[2] W. Stallings, Wireless communications & networks.: Pearson Education India, 2009.
[3] N. Ameen and R. Willis, "Current and future challenges facing the mobile
telecommunications industry in the Arab world," in the 3rd world congress on computer
applications and information systems, Dubai, 2016.
[4] X. Foukas, G. Patounas, A. Elmokashfi, and M.K. Marina, "Network slicing in 5G:
Survey and challenges," IEEE Communications Magazine, vol. 55, no. 5, pp. 94-100,
2017.
[5] T. Bakici, E. Almirall, and J. Wareham, "A smart city initiative: the case of Barcelona,"
Journal of the Knowledge Economy, vol. 4, no. 2, pp. 135-148, 2013.
[6] L.C. Wang and S. Rangapillai, "A survey on green 5G cellular networks," in
International conference on Signal Processing and Comunnicatiobs SPCOM, New
York, 2012, pp. 1-5.
[7] A. Gohil, H. Modi, and S.K. Patel, "5G technology of mobile communication: A
survey.," in International conference on intelligent systems and signal processing ISSP,
US, 2013, pp. 288-292.
[8] N. Panwar, S. Sharma, and A.K. Singh, "A survey on 5G: The next generation of mobile
communication," Physical Communication, vol. 18, pp. 64-84, 2016.
[9] S. Bi, Y. Zeng, and R. Zhang, "Wireless powered communication networks: An
overview," IEEE Wireless Communications, vol. 23, no. 2, pp. 10-18, 2016.
[10] R.N. Mitra and D.P. Agarwal, "5G mobile technology: A survey," ICT Express, vol. 1,
no. 3, pp. 132-137, 2015.
[11] Y. Huo, X. Dong, and W. Xu, "5G Cellular User Equipment: From Theory to Practical
Hardware Design," IEEE Access, vol. 5, pp. 13992-14010, 2017.
[12] C.X. Mavromoustakis, G. Mastorakis, and J.M. Batalla, Internet of Things (IoT) in 5G
mobile technologies. UK: Springer, 2016.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking
10
[13] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[14] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[15] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
x
10
[13] A. Gupta and R.K. Jha, "A survey of 5G network: Architecture and emerging
technologies," IEEE access, vol. 3, pp. 1206-1232, 2015.
[14] G. Cecere, N. Corrocher, and R.D. Battaglia, "Innovation and competition in the
smartphone industry: Is there a dominant design?," Telecommunications Policy, vol. 39,
no. 3-4, pp. 162-175, 2015.
[15] D.P. Agarwal and Q.A. Zeng, Introduction to wireless and mobile systems. USA:
Cengage Learning, 2015.
x
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





