Diploma in Engineering (Aviation) Project: 9/11 Security Analysis
VerifiedAdded on 2023/04/21
|11
|1745
|322
Project
AI Summary
This project delves into the aviation security incident of the 9/11 attacks, providing a comprehensive analysis as per the project brief. It starts with an introduction to the aviation industry's challenges stemming from geopolitical risks and terror attacks. The project then outlines the incident itself, detailing the events of September 11, 2001, and the impact on the United States. A key focus is on the threats posed, including anger management issues, disregard for authority, and insufficient security measures. The report examines existing control measures such as passenger and baggage screening, access control, and perimeter security. It also highlights vulnerabilities, risks, and the consequences of the attacks, including the loss of life and economic damage. Immediate recovery measures, such as enhanced passenger screening and baggage security, are discussed, along with preventive control measures. The project concludes by summarizing the key findings and emphasizing the importance of aviation management and security. The Bowtie Analysis method is applied to identify security incidents, threats, existing control measures, vulnerabilities, risks, consequences, and preventive control measures.

Running head: AVIATION MANAGEMENT
Aviation Management
(9/11 attacks in US)
Name of the Student
Name of the University
Author Note:
Aviation Management
(9/11 attacks in US)
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1AVIATION MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Project Brief.....................................................................................................................................2
Aviation Security Incident...........................................................................................................2
Threats.........................................................................................................................................2
Existing Control Measures..........................................................................................................3
Passenger Screening................................................................................................................3
Baggage Screening..................................................................................................................3
Access Control.........................................................................................................................4
Perimeter Security...................................................................................................................4
Vulnerabilities..............................................................................................................................4
Risks............................................................................................................................................4
Consequences..............................................................................................................................5
Immediate Recovery Measurers..................................................................................................5
Passenger Screening................................................................................................................5
Baggage Screening..................................................................................................................5
Access Control.........................................................................................................................5
Perimeter Security...................................................................................................................6
Preventive Control Measures.......................................................................................................6
Passenger Screening................................................................................................................6
Baggage Screening..................................................................................................................6
Access Control.........................................................................................................................6
Perimeter Security...................................................................................................................6
Conclusion.......................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Introduction......................................................................................................................................2
Project Brief.....................................................................................................................................2
Aviation Security Incident...........................................................................................................2
Threats.........................................................................................................................................2
Existing Control Measures..........................................................................................................3
Passenger Screening................................................................................................................3
Baggage Screening..................................................................................................................3
Access Control.........................................................................................................................4
Perimeter Security...................................................................................................................4
Vulnerabilities..............................................................................................................................4
Risks............................................................................................................................................4
Consequences..............................................................................................................................5
Immediate Recovery Measurers..................................................................................................5
Passenger Screening................................................................................................................5
Baggage Screening..................................................................................................................5
Access Control.........................................................................................................................5
Perimeter Security...................................................................................................................6
Preventive Control Measures.......................................................................................................6
Passenger Screening................................................................................................................6
Baggage Screening..................................................................................................................6
Access Control.........................................................................................................................6
Perimeter Security...................................................................................................................6
Conclusion.......................................................................................................................................7
References........................................................................................................................................8

2AVIATION MANAGEMENT
Introduction
The aviation industry is encountering huge number of issues due to geopolitical risk. It
has mainly resulted from terror attacks [1] . It is increasing as a result of complex methods of
people trafficking. Political flux in the present market has resulted in poor compliance with the
present standard. The threats in aviation environment is constantly developing by the use of
sophisticated and physical attacks.
In the coming pages of the report one aviation security incident that is 9/11 attack in US
has been discussed in details.
Project Brief
Aviation Security Incident
On 11 September 2001, around 19 militants who are attached with Islamic group hacked
four airplanes and made a suicide attack in US. Two airplanes flown into the towers of world
trade center in New York City [7]. Around 3,000 people are killed during this attack of 9/11
which created initiatives for US for combating terrorism. The impact or effect of this attack left a
burning hole near the 80th floor of this building. It has ultimately killed more than 100 of people
and trapping hundred more in the high floors.
Threats
The key threats in this attack are anger management issues, disregard for Authority and
lastly not accepting feedback of the airport employees [4] . The security measures were not
uniform in nature. It is merely due governance and budgeting. In many places of Mexico, the
aviation security funding is every seen from of the general achieved revenues.
Introduction
The aviation industry is encountering huge number of issues due to geopolitical risk. It
has mainly resulted from terror attacks [1] . It is increasing as a result of complex methods of
people trafficking. Political flux in the present market has resulted in poor compliance with the
present standard. The threats in aviation environment is constantly developing by the use of
sophisticated and physical attacks.
In the coming pages of the report one aviation security incident that is 9/11 attack in US
has been discussed in details.
Project Brief
Aviation Security Incident
On 11 September 2001, around 19 militants who are attached with Islamic group hacked
four airplanes and made a suicide attack in US. Two airplanes flown into the towers of world
trade center in New York City [7]. Around 3,000 people are killed during this attack of 9/11
which created initiatives for US for combating terrorism. The impact or effect of this attack left a
burning hole near the 80th floor of this building. It has ultimately killed more than 100 of people
and trapping hundred more in the high floors.
Threats
The key threats in this attack are anger management issues, disregard for Authority and
lastly not accepting feedback of the airport employees [4] . The security measures were not
uniform in nature. It is merely due governance and budgeting. In many places of Mexico, the
aviation security funding is every seen from of the general achieved revenues.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3AVIATION MANAGEMENT
Not accepting feedback: Various employee have observed being unwillingly to
acknowledgement of errors or even admitting mistakes. It can help be helpful in overcoming
errors by the help of deceit.
Disagree with authority: Employees come up with disregards rules, authorities and
policies. Employee tends to understand the rule which can be applied to others.
Anger management issues: Employee in most of the cases allow anger to be pent up
inside and employee come up with trouble for managing the anger or even rage.
Existing Control Measures
Passenger Screening
In the verification of passengers in airports is all about understanding the passports and
other identities by the help of facial recognition along with working with enforcement from law
of local airport [5]. FAA is an international body which tends to empower and regulate various
aspects of US civil aviation inclusive of guidelines and proper policy needs. At present, U.S
aviation industry is a part of Public transportation and information sharing and analysis center
which tends to provide 24/7 security operation capability. It is an established sector which tends
to provide requirements for threats and vulnerabilities.
Baggage Screening
As per TSA, the present baggage screening system tends to continue for providing there
is no ability for adaptation or keeping up pace with the changing demand of the present aviation
industry [2]. At the similar instance, the patch work system is bogged down by their own
Not accepting feedback: Various employee have observed being unwillingly to
acknowledgement of errors or even admitting mistakes. It can help be helpful in overcoming
errors by the help of deceit.
Disagree with authority: Employees come up with disregards rules, authorities and
policies. Employee tends to understand the rule which can be applied to others.
Anger management issues: Employee in most of the cases allow anger to be pent up
inside and employee come up with trouble for managing the anger or even rage.
Existing Control Measures
Passenger Screening
In the verification of passengers in airports is all about understanding the passports and
other identities by the help of facial recognition along with working with enforcement from law
of local airport [5]. FAA is an international body which tends to empower and regulate various
aspects of US civil aviation inclusive of guidelines and proper policy needs. At present, U.S
aviation industry is a part of Public transportation and information sharing and analysis center
which tends to provide 24/7 security operation capability. It is an established sector which tends
to provide requirements for threats and vulnerabilities.
Baggage Screening
As per TSA, the present baggage screening system tends to continue for providing there
is no ability for adaptation or keeping up pace with the changing demand of the present aviation
industry [2]. At the similar instance, the patch work system is bogged down by their own
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4AVIATION MANAGEMENT
efficiencies. There has been growing evidence that it does not afford more effect kind of security
screening.
Access Control
The opposed insiders are looking for revenge by the help of cyber means. Inside threats is
mainly inclusive of range of low level employees like baggage handler and IT workers. It is all
about making use of high level managers and officers [3] . This particular incident tends to lack
some of the security measures with respect to access control and privileges based on data need.
Perimeter Security
With respect to 9/11 attack, there are some insider threats for people who physically
focus on to carry out malicious intent [7]. There was lack of proper security control in American
Airports due to which the attack took place. But soon after the cost and effort, proper security
measures were implemented.
Vulnerabilities
The aviation industry totally depends on the latest technologies which ranges from
screening machines to Wi-Fi board based aircrafts. Cyber vulnerabilities are mainly seen in the
equipment and machines like facial recognition which has been exploited by the terrorists [1].
The human problem for terrorism requires human solution along with proper technology.
Risks
There are large inside threats which triggered this event of 9/11 attack like
Disregard with authority
efficiencies. There has been growing evidence that it does not afford more effect kind of security
screening.
Access Control
The opposed insiders are looking for revenge by the help of cyber means. Inside threats is
mainly inclusive of range of low level employees like baggage handler and IT workers. It is all
about making use of high level managers and officers [3] . This particular incident tends to lack
some of the security measures with respect to access control and privileges based on data need.
Perimeter Security
With respect to 9/11 attack, there are some insider threats for people who physically
focus on to carry out malicious intent [7]. There was lack of proper security control in American
Airports due to which the attack took place. But soon after the cost and effort, proper security
measures were implemented.
Vulnerabilities
The aviation industry totally depends on the latest technologies which ranges from
screening machines to Wi-Fi board based aircrafts. Cyber vulnerabilities are mainly seen in the
equipment and machines like facial recognition which has been exploited by the terrorists [1].
The human problem for terrorism requires human solution along with proper technology.
Risks
There are large inside threats which triggered this event of 9/11 attack like
Disregard with authority

5AVIATION MANAGEMENT
Performance
Stress
Lack of dependability
Consequences
The overall consequence of this attack (9/11) resulted in the death of more than 3000
people making one of the deadliest attack in US. 9/11 attack is considered to be symbolic just
because of twin towers which is considered to be symbol of American power [8]. U.S and global
markets tends experienced huge amount of damage. It is considered to be one of the fatal
attacks till date.
Immediate Recovery Measurers
Passenger Screening
Soon after the fact, DHS main mission is to prevent terrorism and develop security
measures. It ultimately allocated proper kind of funding which is required for sustainable
aviation security along with align of screening of passenger resources which are based on risk
[3]. A risk based security tends to assumes the huge amount of passenger security which is there
with low risk and security.
Baggage Screening
Soon after the attack, proper equipment’s were installed so that this kind of attack can be
further prevented in the near future. This particular step was taken more specifically for the
various employees.
Performance
Stress
Lack of dependability
Consequences
The overall consequence of this attack (9/11) resulted in the death of more than 3000
people making one of the deadliest attack in US. 9/11 attack is considered to be symbolic just
because of twin towers which is considered to be symbol of American power [8]. U.S and global
markets tends experienced huge amount of damage. It is considered to be one of the fatal
attacks till date.
Immediate Recovery Measurers
Passenger Screening
Soon after the fact, DHS main mission is to prevent terrorism and develop security
measures. It ultimately allocated proper kind of funding which is required for sustainable
aviation security along with align of screening of passenger resources which are based on risk
[3]. A risk based security tends to assumes the huge amount of passenger security which is there
with low risk and security.
Baggage Screening
Soon after the attack, proper equipment’s were installed so that this kind of attack can be
further prevented in the near future. This particular step was taken more specifically for the
various employees.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6AVIATION MANAGEMENT
Access Control
Inside threats mainly comprises from lower employees like baggage handlers and other
IT based workers [2]. It also includes high level of managers and other associated officers. After
that this attack proper security measures were taken.
Perimeter Security
After this attack, the total ground security of all the airports of America were improved so
that this type of attack does not take place in the coming days.
Preventive Control Measures
Passenger Screening
There was proper funding for sustainable aviation security so that it can align with the
resources based on risk [6]. A proper risk based approach is all about understanding the security
measures so that it can represent low risk for the passengers of airline.
Baggage Screening
Various American officials highlighted the need of proper security measures for aviation
attacks and foiled plots [2]. These measures were inclusive of baggage screening and other kind
of programs on domestic flights.
Access Control
There were some restriction and new laws for the access control to flights of America.
The access control to flights were limited due to increasing global security issues worldwide [4].
Access Control
Inside threats mainly comprises from lower employees like baggage handlers and other
IT based workers [2]. It also includes high level of managers and other associated officers. After
that this attack proper security measures were taken.
Perimeter Security
After this attack, the total ground security of all the airports of America were improved so
that this type of attack does not take place in the coming days.
Preventive Control Measures
Passenger Screening
There was proper funding for sustainable aviation security so that it can align with the
resources based on risk [6]. A proper risk based approach is all about understanding the security
measures so that it can represent low risk for the passengers of airline.
Baggage Screening
Various American officials highlighted the need of proper security measures for aviation
attacks and foiled plots [2]. These measures were inclusive of baggage screening and other kind
of programs on domestic flights.
Access Control
There were some restriction and new laws for the access control to flights of America.
The access control to flights were limited due to increasing global security issues worldwide [4].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7AVIATION MANAGEMENT
Perimeter Security
New rules and regulation were made for the American flights so that this type of attack
does not place in near future[2].
Conclusion
From the above pages, it can be easily stated that this report is all about aviation
management. In the above pages, the case study of 9/11 has been discussed in details. After that
Bowtie Analysis method has been used for identifying various kind of security incident like
aviation security incident, threats and existing control measures, vulnerabilities, risk,
consequences, preventive control measures have been discussed in details.
Perimeter Security
New rules and regulation were made for the American flights so that this type of attack
does not place in near future[2].
Conclusion
From the above pages, it can be easily stated that this report is all about aviation
management. In the above pages, the case study of 9/11 has been discussed in details. After that
Bowtie Analysis method has been used for identifying various kind of security incident like
aviation security incident, threats and existing control measures, vulnerabilities, risk,
consequences, preventive control measures have been discussed in details.

8AVIATION MANAGEMENT
References
[1] T.H, Hall and A.A, Ross. Affective politics after 9/11. International Organization, 69(4),
pp.847-879, 2015.
[2] P.,Gill, J., Silver, J. Horgan, and E. Corner, Shooting alone: The pre‐attack experiences and
behaviors of US solo mass murderers. Journal of forensic sciences, 62(3), pp.710-714, 2017.
[3] B.J, Phillips. Deadlier in the US? On lone wolves, terrorist groups, and attack
lethality. Terrorism and political violence, 29(3), pp.533-549, 2017.
[4] W., Hirst, E.A., Phelps, R., Meksin, C.J., Vaidya, M.K., Johnson, K.J., Mitchell, R.L.,
Buckner, A.E., J.D., Budson, Gabrieli, C. Lustig, and M., Mather. A ten-year follow-up of a
study of memory for the attack of September 11, 2001: Flashbulb memories and memories for
flashbulb events. Journal of Experimental Psychology: General, 144(3), p.604, 2015.
[5] J., Mueller and M.G, Stewart. American Public Opinion on Terrorism Since 9/11: Trends and
Puzzles. In International Studies Association Convention Paper. Available on the Web, 2016,
March.
[6] E., Lichtblau. Hate crimes against American Muslims most since post-9/11 era. The New
York Times, 17, 2016.
[7] T., Elliott. Complex Coordinated Terrorist Attack: Considerations for Practical Emergency
Preparedness and Resiliency Exercises, 2017.
[8] E.W., Prehoda, C., Schelly and J.M, Pearce. US strategic solar photovoltaic-powered
microgrid deployment for enhanced national security. Renewable and Sustainable Energy
Reviews, 78, pp.167-175, 2017.
References
[1] T.H, Hall and A.A, Ross. Affective politics after 9/11. International Organization, 69(4),
pp.847-879, 2015.
[2] P.,Gill, J., Silver, J. Horgan, and E. Corner, Shooting alone: The pre‐attack experiences and
behaviors of US solo mass murderers. Journal of forensic sciences, 62(3), pp.710-714, 2017.
[3] B.J, Phillips. Deadlier in the US? On lone wolves, terrorist groups, and attack
lethality. Terrorism and political violence, 29(3), pp.533-549, 2017.
[4] W., Hirst, E.A., Phelps, R., Meksin, C.J., Vaidya, M.K., Johnson, K.J., Mitchell, R.L.,
Buckner, A.E., J.D., Budson, Gabrieli, C. Lustig, and M., Mather. A ten-year follow-up of a
study of memory for the attack of September 11, 2001: Flashbulb memories and memories for
flashbulb events. Journal of Experimental Psychology: General, 144(3), p.604, 2015.
[5] J., Mueller and M.G, Stewart. American Public Opinion on Terrorism Since 9/11: Trends and
Puzzles. In International Studies Association Convention Paper. Available on the Web, 2016,
March.
[6] E., Lichtblau. Hate crimes against American Muslims most since post-9/11 era. The New
York Times, 17, 2016.
[7] T., Elliott. Complex Coordinated Terrorist Attack: Considerations for Practical Emergency
Preparedness and Resiliency Exercises, 2017.
[8] E.W., Prehoda, C., Schelly and J.M, Pearce. US strategic solar photovoltaic-powered
microgrid deployment for enhanced national security. Renewable and Sustainable Energy
Reviews, 78, pp.167-175, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
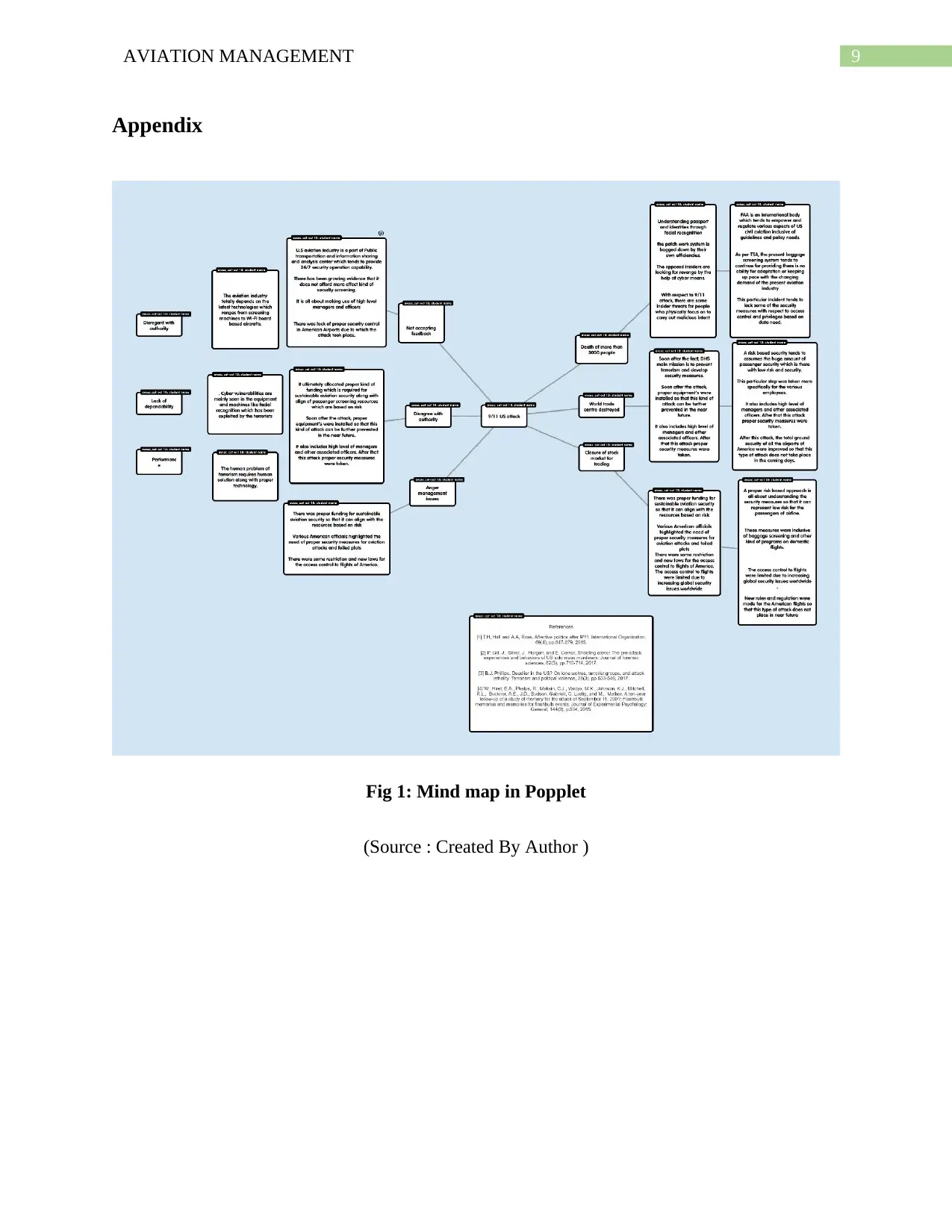
9AVIATION MANAGEMENT
Appendix
Fig 1: Mind map in Popplet
(Source : Created By Author )
Appendix
Fig 1: Mind map in Popplet
(Source : Created By Author )
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10AVIATION MANAGEMENT
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





