IT Risk Assessment and Mitigation Report for ABC Fitness Gym
VerifiedAdded on 2022/10/02
|13
|2932
|414
Report
AI Summary
This report provides a comprehensive risk assessment of ABC Fitness Gym's technology environment. It identifies key threats related to the IT control framework, such as software and hardware failures, data backup issues, security breaches, and inadequate IT expertise. The report details the consequences of these threats, including data loss, client confidentiality breaches, and operational disruptions. Mitigation strategies are proposed, including data backups, password protection, employee training, and the recruitment of IT experts. A risk register and matrix are included to prioritize and manage risks. The report concludes with recommendations for improving IT security and ensuring the smooth operation of the gym's IT systems, emphasizing the importance of continuous monitoring and proactive risk management.

Topic
Name of the Student:
Student ID:
Subject Code:
Subject Code:
Subject Name:
Assessment Item Number and Name:
Lecturer Name:
Name of the Student:
Student ID:
Subject Code:
Subject Code:
Subject Name:
Assessment Item Number and Name:
Lecturer Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
Table of Contents
Executive summery.................................................................................................................................................2
Risk assessment.......................................................................................................................................................2
The threats related to the IT control framework:.................................................................................................2
Consequences of the threats:...............................................................................................................................3
Risk mitigation.....................................................................................................................................................4
Risk register.........................................................................................................................................................4
Risk Matrix..........................................................................................................................................................8
Protection mechanism..............................................................................................................................................8
Conclusion and Recommendation...........................................................................................................................9
Reference...............................................................................................................................................................10
Table of Contents
Executive summery.................................................................................................................................................2
Risk assessment.......................................................................................................................................................2
The threats related to the IT control framework:.................................................................................................2
Consequences of the threats:...............................................................................................................................3
Risk mitigation.....................................................................................................................................................4
Risk register.........................................................................................................................................................4
Risk Matrix..........................................................................................................................................................8
Protection mechanism..............................................................................................................................................8
Conclusion and Recommendation...........................................................................................................................9
Reference...............................................................................................................................................................10

Subject Code Subject Name Semester Number
Executive summery
In 1997, the owner of ABC Fitness gym started this gym and it acquired a small area in the beginning. It
used to have 20 members in the overall gym and gradually they expanded their premises that contains 50
employees who are working full time and 150 employee those are working for part-time. Subscription plans for
members are initiated and it is revised every year. The gym contains two types of equipment one for weight
machine and other one is of cardiovascular machine. The company aims to provide several services related to
information system such as, automated membership renewal, maintenance of the equipment, updating the
equipment to their latest features, maintenance of the details of the employees with highest confidentiality.
Routine backup of data, use of updated software and hardware.
The recommendation to the management of the gym is to introduce latest devices into the system in
order to maintain details of employees, prevention of the information system department. Recruitment of IT
experts in the gym will benefit the company the most as they can keep track of all the malicious attack into the
IT system as well as IT related malfunction to the equipment (Peute et al., 2014). The data storage system of the
company is a vital part as it contains all the details of the employees, members and stakeholders along with
company details, therefore specific software and experts must be assigned in order to protect that.
Risk assessment
The ABC fitness gym consists of several employees and members are categories in two groups. The
equipment in the gym are of two type one is of weight machines and other one is cardiovascular machines all
the equipment have Information technological functionalities. For the new company several IT framework-
based systems are introduced such as automated membership renewal process, keeping track of the health of the
members of the gym, maintenance of the client details in the IT system, updating software and hardware for
data storage, backup of data, secured computer systems (Koehler et al., 2014).
Executive summery
In 1997, the owner of ABC Fitness gym started this gym and it acquired a small area in the beginning. It
used to have 20 members in the overall gym and gradually they expanded their premises that contains 50
employees who are working full time and 150 employee those are working for part-time. Subscription plans for
members are initiated and it is revised every year. The gym contains two types of equipment one for weight
machine and other one is of cardiovascular machine. The company aims to provide several services related to
information system such as, automated membership renewal, maintenance of the equipment, updating the
equipment to their latest features, maintenance of the details of the employees with highest confidentiality.
Routine backup of data, use of updated software and hardware.
The recommendation to the management of the gym is to introduce latest devices into the system in
order to maintain details of employees, prevention of the information system department. Recruitment of IT
experts in the gym will benefit the company the most as they can keep track of all the malicious attack into the
IT system as well as IT related malfunction to the equipment (Peute et al., 2014). The data storage system of the
company is a vital part as it contains all the details of the employees, members and stakeholders along with
company details, therefore specific software and experts must be assigned in order to protect that.
Risk assessment
The ABC fitness gym consists of several employees and members are categories in two groups. The
equipment in the gym are of two type one is of weight machines and other one is cardiovascular machines all
the equipment have Information technological functionalities. For the new company several IT framework-
based systems are introduced such as automated membership renewal process, keeping track of the health of the
members of the gym, maintenance of the client details in the IT system, updating software and hardware for
data storage, backup of data, secured computer systems (Koehler et al., 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Subject Code Subject Name Semester Number
The threats related to the IT control framework:
Failure of software and hardware- The software and hardware which are maintain the data of the
organisation may fail due to malicious attacks (Arulraj et al., 2014).
Failure of data backup- The data backup process can be stopped due to system failure or unwanted
malware attacks.
Security of the information- The details related to the employees and members must be secure inside the
system of the organisation.
Confidentiality of client details- The details of the clients such as organisation that have membership of
the gym must be well secure (Pattenden & Sheehan, 2016).
Functionality of gym equipment- The gym equipment must be maintained so that the functionality run
smoothly.
Human mishandling of IT system- The members, employees, and other clients may not know all the
functionalities of the equipment or IT system of the gym (Omar et al.,2017). Therefore, inadequate
knowledge of the advanced system may lead to mishandling of the system.
Inadequate IT experts- The unavailability of the IT expert in the company will increase the IT threats
more (Ammenwerth et al., 2014). The system will become more vulnerable to attacks.
Consequences of the threats:
The consequences of the above can be vast, the consequences of the threats are identified by analysing
them properly. The failure of hardware may lead to repurchase of cuter system into the business and the softer
failure may cause due to malicious attacks that may result in data breach, loss of data, data manipulation (Sen
& Borle, 2015). The consequence of data backup failure will lead to loss of data, that may affect the database of
the company that contain all the details of the employees, members, as well as the details of the equipment
present in the gym, payment details etc. (Xia et al., 2013) The compromise in the confidentiality of the clients
may cause large loss to the business, the clients may cancel further contract with the company. The faults in the
gym equipment will stop the functionality of the gym. The consequence of mishandling of the IT system of the
gym can cause leakage of information from the internal information system. The consequence of have
The threats related to the IT control framework:
Failure of software and hardware- The software and hardware which are maintain the data of the
organisation may fail due to malicious attacks (Arulraj et al., 2014).
Failure of data backup- The data backup process can be stopped due to system failure or unwanted
malware attacks.
Security of the information- The details related to the employees and members must be secure inside the
system of the organisation.
Confidentiality of client details- The details of the clients such as organisation that have membership of
the gym must be well secure (Pattenden & Sheehan, 2016).
Functionality of gym equipment- The gym equipment must be maintained so that the functionality run
smoothly.
Human mishandling of IT system- The members, employees, and other clients may not know all the
functionalities of the equipment or IT system of the gym (Omar et al.,2017). Therefore, inadequate
knowledge of the advanced system may lead to mishandling of the system.
Inadequate IT experts- The unavailability of the IT expert in the company will increase the IT threats
more (Ammenwerth et al., 2014). The system will become more vulnerable to attacks.
Consequences of the threats:
The consequences of the above can be vast, the consequences of the threats are identified by analysing
them properly. The failure of hardware may lead to repurchase of cuter system into the business and the softer
failure may cause due to malicious attacks that may result in data breach, loss of data, data manipulation (Sen
& Borle, 2015). The consequence of data backup failure will lead to loss of data, that may affect the database of
the company that contain all the details of the employees, members, as well as the details of the equipment
present in the gym, payment details etc. (Xia et al., 2013) The compromise in the confidentiality of the clients
may cause large loss to the business, the clients may cancel further contract with the company. The faults in the
gym equipment will stop the functionality of the gym. The consequence of mishandling of the IT system of the
gym can cause leakage of information from the internal information system. The consequence of have
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
inadequate IT expert in the company will lead to problematic situation, when any IT related issue comes up if
no IT expert is present to resolve the issue the company will face loss in their business. These consequences are
measured in three levels, such as, LOW, MEDIUM, and HIGH. The threats that cause extreme loss in the
business is categorized under HIGH. The threats that cause issue in the company and hence can be fixed within
some period of time it comes under MEDIUM. Finally, the threats that causes very little loss to the company
can be put under LOW.
Risk mitigation
The risks or threats to the IT related framework of the company can be mitigated by analysing all the
threats to the IT system of the company and then taking actions accordingly. Firstly, the risk of system failure
can be avoided by keeping a backup device if the system fails (Talluri et al., 2013). The software must be
updated as per requirement, and all the malicious attacks must be recorded so that later attacks can be prevented
whenever occurs. The failure of data backup can be prevented by monthly routine of data back up and data
update session. One IT expert must be assigned with this job (Aqlan & Lam, 2015). The information of the
business must be password protected, so that the security of the information is not compromised. All the
individual member, employees and stakeholders must be allotted with unique pass-word of their own
information. Therefore, except the person and the gym no other person can access them (Hajmohammad &
Vachon, 2016). The functionalities of the equipment inside the gym must be maintained by information system
experts so that the gym runs smoothly, weekly check-up for any dis-functionality must be avoided as soon as
detected. All the members of the gym must be given training of the equipment handling relate to information
technology (Coras & Tantau, 2013). More experts in IT must be appointed so that any IT related issue can be
resolved.
Risk register
Sl.
No
.
Risk Risk
Description
Impact Likelihoo
d
Responsible
people
Consequenc
e of Risks
Mitigation
inadequate IT expert in the company will lead to problematic situation, when any IT related issue comes up if
no IT expert is present to resolve the issue the company will face loss in their business. These consequences are
measured in three levels, such as, LOW, MEDIUM, and HIGH. The threats that cause extreme loss in the
business is categorized under HIGH. The threats that cause issue in the company and hence can be fixed within
some period of time it comes under MEDIUM. Finally, the threats that causes very little loss to the company
can be put under LOW.
Risk mitigation
The risks or threats to the IT related framework of the company can be mitigated by analysing all the
threats to the IT system of the company and then taking actions accordingly. Firstly, the risk of system failure
can be avoided by keeping a backup device if the system fails (Talluri et al., 2013). The software must be
updated as per requirement, and all the malicious attacks must be recorded so that later attacks can be prevented
whenever occurs. The failure of data backup can be prevented by monthly routine of data back up and data
update session. One IT expert must be assigned with this job (Aqlan & Lam, 2015). The information of the
business must be password protected, so that the security of the information is not compromised. All the
individual member, employees and stakeholders must be allotted with unique pass-word of their own
information. Therefore, except the person and the gym no other person can access them (Hajmohammad &
Vachon, 2016). The functionalities of the equipment inside the gym must be maintained by information system
experts so that the gym runs smoothly, weekly check-up for any dis-functionality must be avoided as soon as
detected. All the members of the gym must be given training of the equipment handling relate to information
technology (Coras & Tantau, 2013). More experts in IT must be appointed so that any IT related issue can be
resolved.
Risk register
Sl.
No
.
Risk Risk
Description
Impact Likelihoo
d
Responsible
people
Consequenc
e of Risks
Mitigation
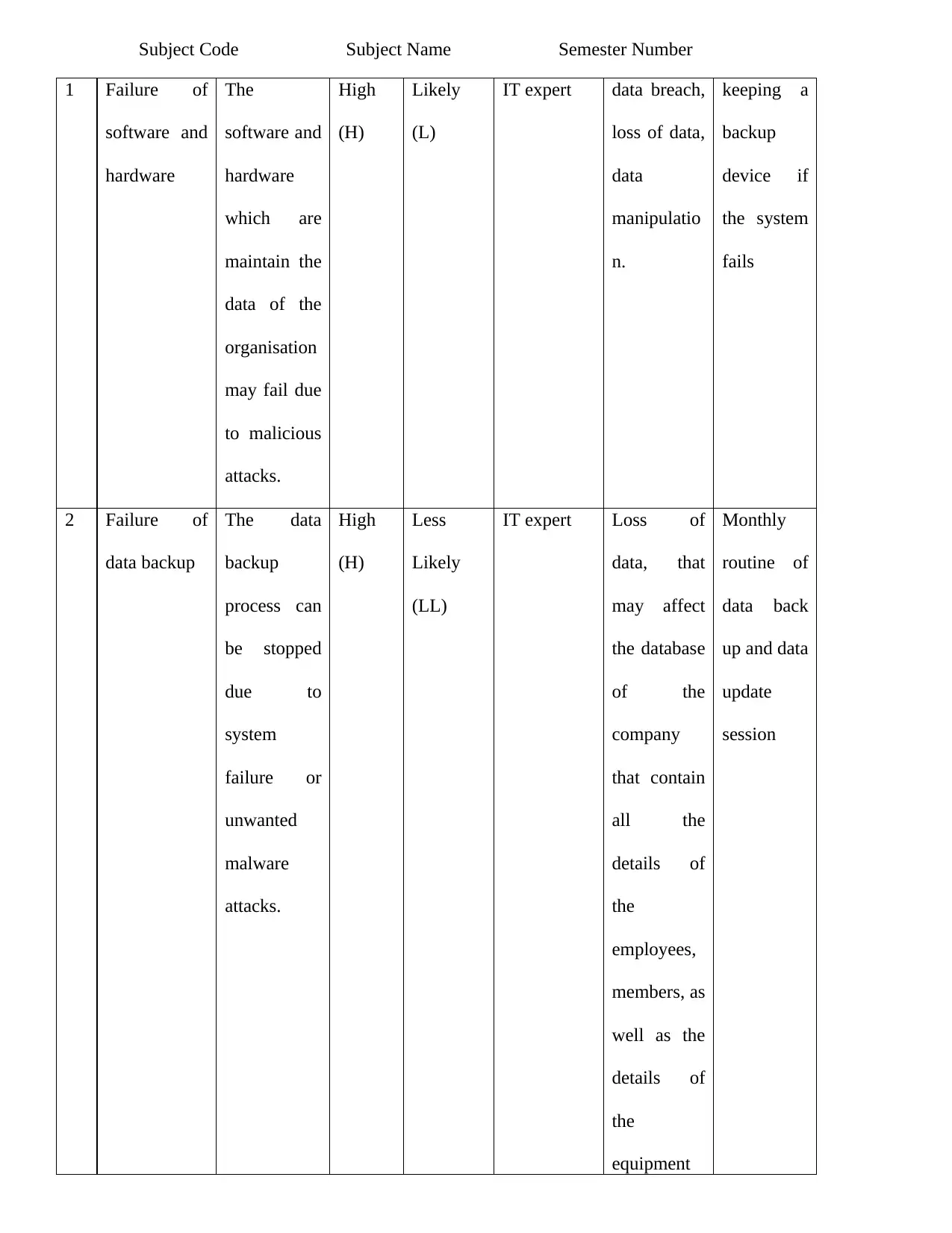
Subject Code Subject Name Semester Number
1 Failure of
software and
hardware
The
software and
hardware
which are
maintain the
data of the
organisation
may fail due
to malicious
attacks.
High
(H)
Likely
(L)
IT expert data breach,
loss of data,
data
manipulatio
n.
keeping a
backup
device if
the system
fails
2 Failure of
data backup
The data
backup
process can
be stopped
due to
system
failure or
unwanted
malware
attacks.
High
(H)
Less
Likely
(LL)
IT expert Loss of
data, that
may affect
the database
of the
company
that contain
all the
details of
the
employees,
members, as
well as the
details of
the
equipment
Monthly
routine of
data back
up and data
update
session
1 Failure of
software and
hardware
The
software and
hardware
which are
maintain the
data of the
organisation
may fail due
to malicious
attacks.
High
(H)
Likely
(L)
IT expert data breach,
loss of data,
data
manipulatio
n.
keeping a
backup
device if
the system
fails
2 Failure of
data backup
The data
backup
process can
be stopped
due to
system
failure or
unwanted
malware
attacks.
High
(H)
Less
Likely
(LL)
IT expert Loss of
data, that
may affect
the database
of the
company
that contain
all the
details of
the
employees,
members, as
well as the
details of
the
equipment
Monthly
routine of
data back
up and data
update
session
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
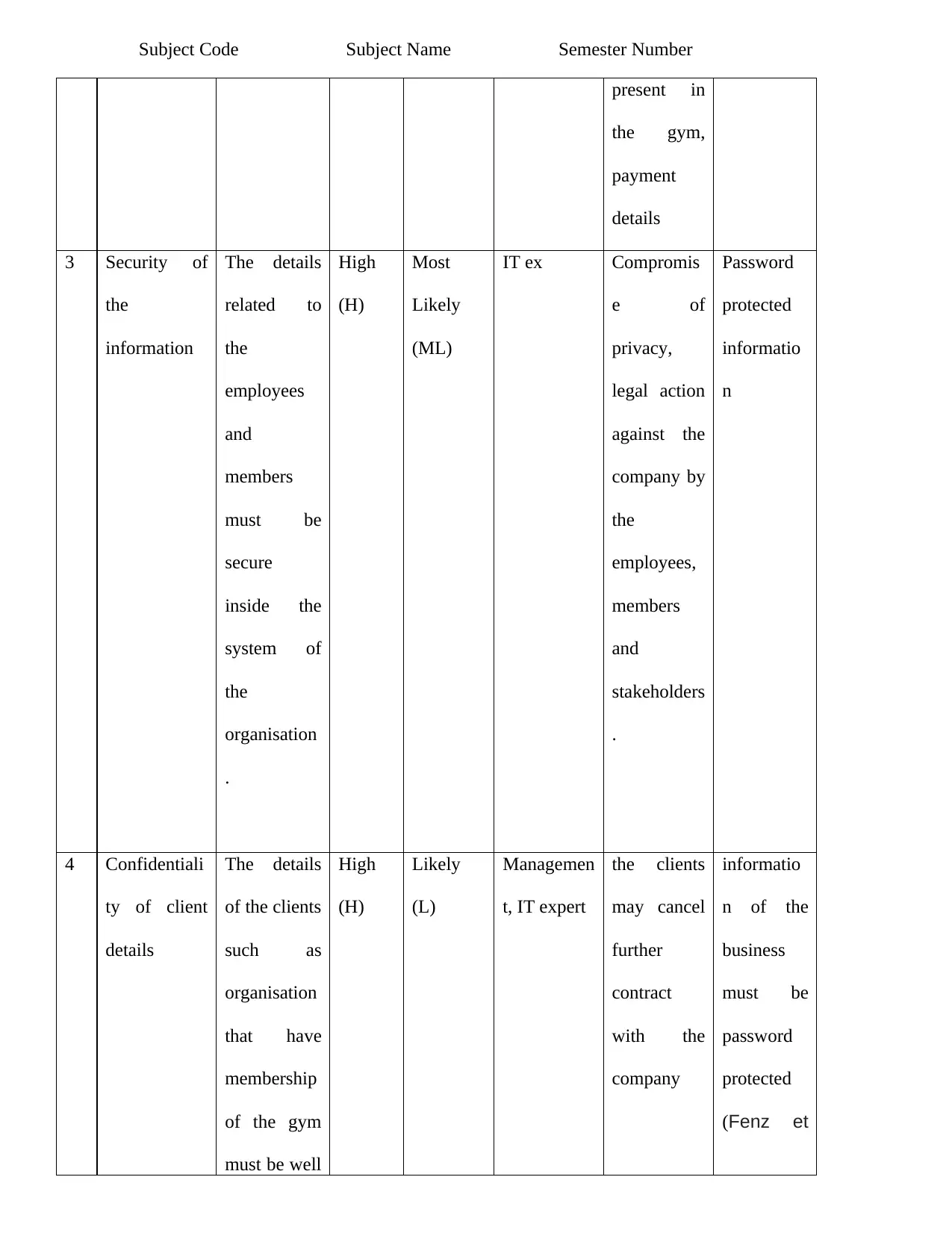
Subject Code Subject Name Semester Number
present in
the gym,
payment
details
3 Security of
the
information
The details
related to
the
employees
and
members
must be
secure
inside the
system of
the
organisation
.
High
(H)
Most
Likely
(ML)
IT ex Compromis
e of
privacy,
legal action
against the
company by
the
employees,
members
and
stakeholders
.
Password
protected
informatio
n
4 Confidentiali
ty of client
details
The details
of the clients
such as
organisation
that have
membership
of the gym
must be well
High
(H)
Likely
(L)
Managemen
t, IT expert
the clients
may cancel
further
contract
with the
company
informatio
n of the
business
must be
password
protected
(Fenz et
present in
the gym,
payment
details
3 Security of
the
information
The details
related to
the
employees
and
members
must be
secure
inside the
system of
the
organisation
.
High
(H)
Most
Likely
(ML)
IT ex Compromis
e of
privacy,
legal action
against the
company by
the
employees,
members
and
stakeholders
.
Password
protected
informatio
n
4 Confidentiali
ty of client
details
The details
of the clients
such as
organisation
that have
membership
of the gym
must be well
High
(H)
Likely
(L)
Managemen
t, IT expert
the clients
may cancel
further
contract
with the
company
informatio
n of the
business
must be
password
protected
(Fenz et
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
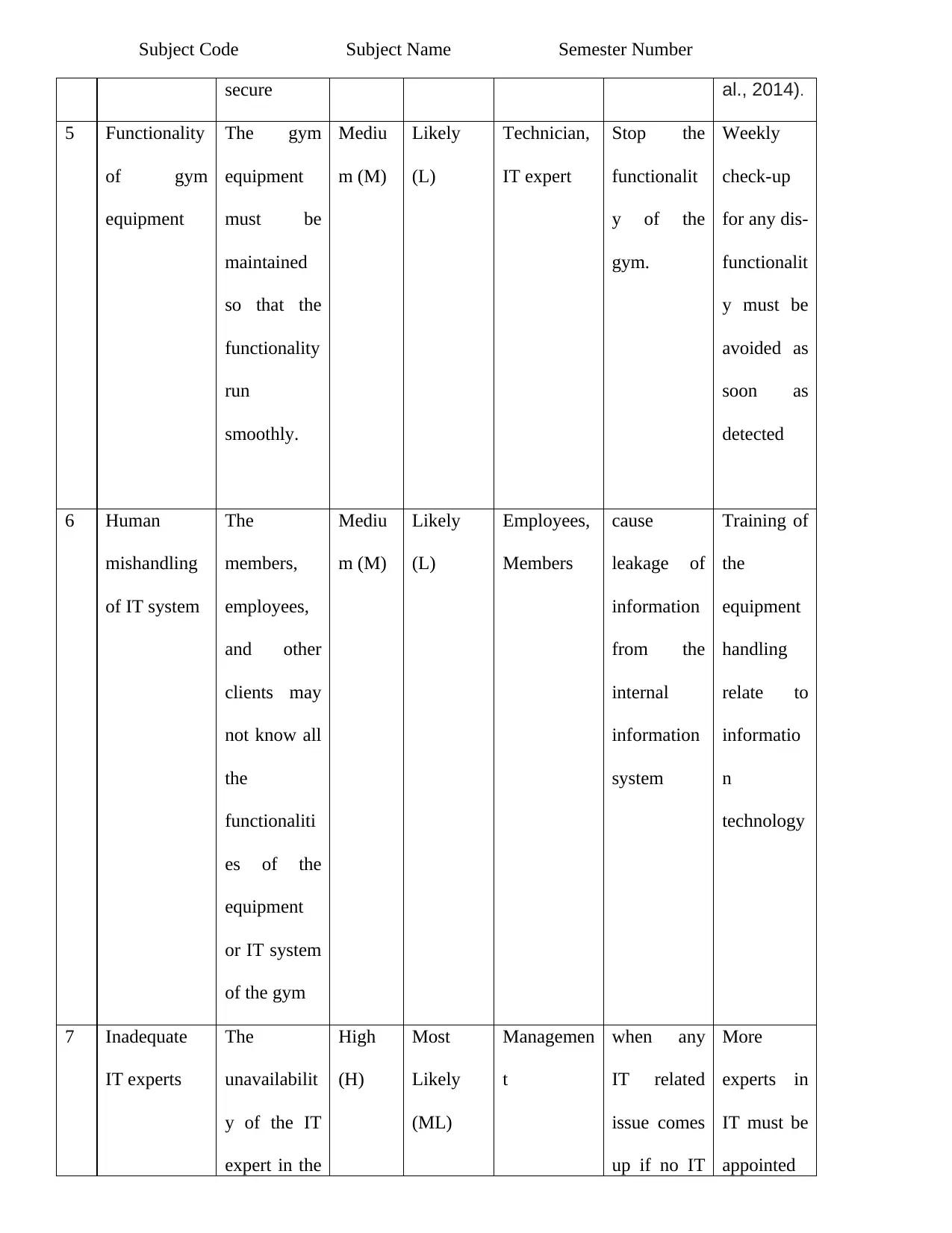
Subject Code Subject Name Semester Number
secure al., 2014).
5 Functionality
of gym
equipment
The gym
equipment
must be
maintained
so that the
functionality
run
smoothly.
Mediu
m (M)
Likely
(L)
Technician,
IT expert
Stop the
functionalit
y of the
gym.
Weekly
check-up
for any dis-
functionalit
y must be
avoided as
soon as
detected
6 Human
mishandling
of IT system
The
members,
employees,
and other
clients may
not know all
the
functionaliti
es of the
equipment
or IT system
of the gym
Mediu
m (M)
Likely
(L)
Employees,
Members
cause
leakage of
information
from the
internal
information
system
Training of
the
equipment
handling
relate to
informatio
n
technology
7 Inadequate
IT experts
The
unavailabilit
y of the IT
expert in the
High
(H)
Most
Likely
(ML)
Managemen
t
when any
IT related
issue comes
up if no IT
More
experts in
IT must be
appointed
secure al., 2014).
5 Functionality
of gym
equipment
The gym
equipment
must be
maintained
so that the
functionality
run
smoothly.
Mediu
m (M)
Likely
(L)
Technician,
IT expert
Stop the
functionalit
y of the
gym.
Weekly
check-up
for any dis-
functionalit
y must be
avoided as
soon as
detected
6 Human
mishandling
of IT system
The
members,
employees,
and other
clients may
not know all
the
functionaliti
es of the
equipment
or IT system
of the gym
Mediu
m (M)
Likely
(L)
Employees,
Members
cause
leakage of
information
from the
internal
information
system
Training of
the
equipment
handling
relate to
informatio
n
technology
7 Inadequate
IT experts
The
unavailabilit
y of the IT
expert in the
High
(H)
Most
Likely
(ML)
Managemen
t
when any
IT related
issue comes
up if no IT
More
experts in
IT must be
appointed
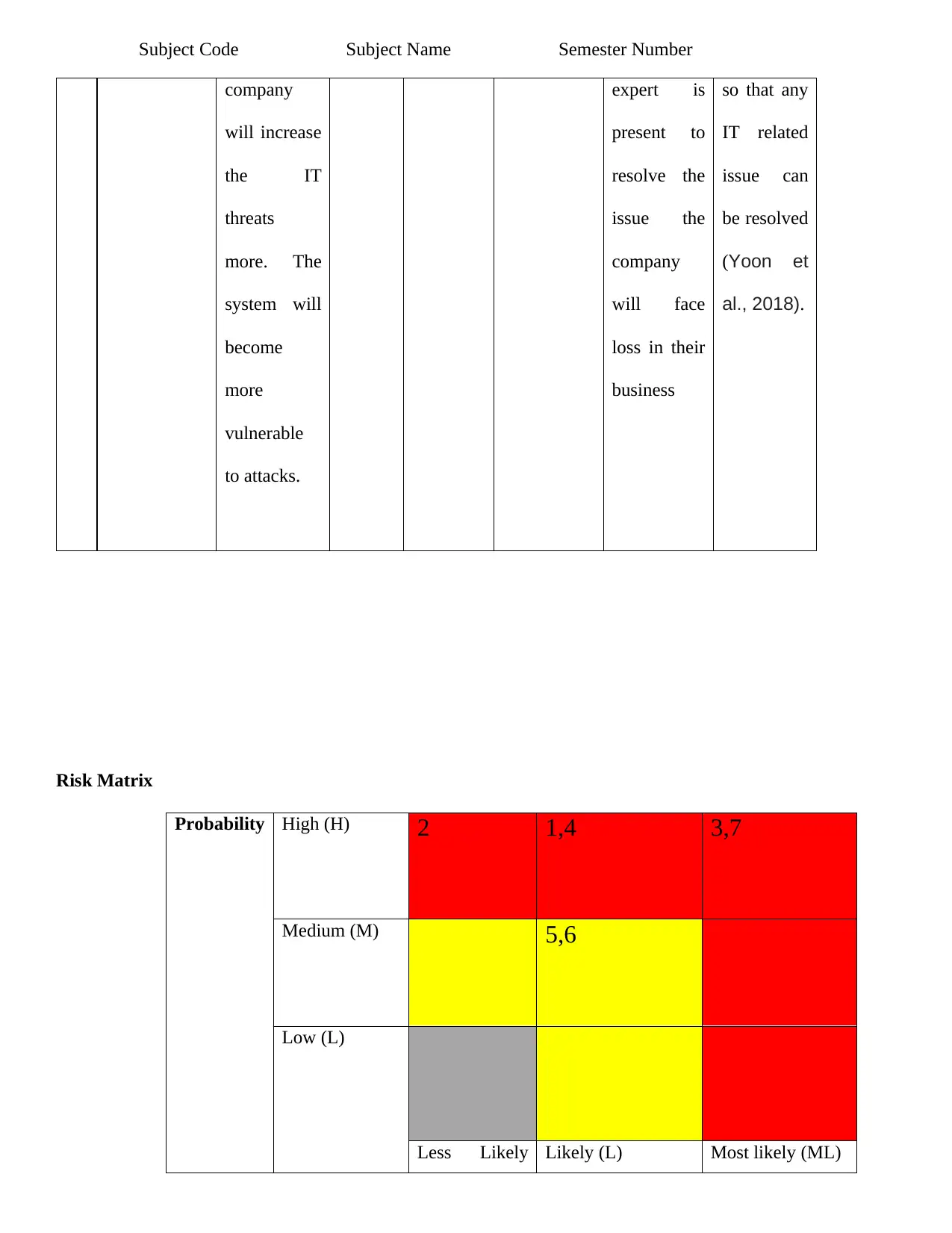
Subject Code Subject Name Semester Number
company
will increase
the IT
threats
more. The
system will
become
more
vulnerable
to attacks.
expert is
present to
resolve the
issue the
company
will face
loss in their
business
so that any
IT related
issue can
be resolved
(Yoon et
al., 2018).
Risk Matrix
Probability High (H) 2 1,4 3,7
Medium (M) 5,6
Low (L)
Less Likely Likely (L) Most likely (ML)
company
will increase
the IT
threats
more. The
system will
become
more
vulnerable
to attacks.
expert is
present to
resolve the
issue the
company
will face
loss in their
business
so that any
IT related
issue can
be resolved
(Yoon et
al., 2018).
Risk Matrix
Probability High (H) 2 1,4 3,7
Medium (M) 5,6
Low (L)
Less Likely Likely (L) Most likely (ML)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Subject Code Subject Name Semester Number
(LL)
Impact
Protection mechanism
The tools and techniques for identifying risk in an IT framework are given below:
1. Documentation reviewing- All the possible documents related to the IT framework of the
equipment in a gym, security, management must be reviewed, studied thoroughly so that
possible risk can be predicted in the initial stages (McNeil et al., 2015).
2. Delphi technique- This technique involves gathering of information related to the gym related to
the information system and sending those to IT experts so that it could be checked and revert
back with best possible results (Park & Kim, 2015).
3. SWOT analysis- As it stands for Strength, weakness, opportunities and threats, therefor this
analysis can be conducted for the information system of the gym and possible threats of the
system can be obtained.
4. Risk register- The benefits of making risk register is that continuous update of the register keeps
track of all the risk throughout the life (Yoe, 2019). This will also help to prevent the risk that
may occur in the future.
5. Risk analysis- The risks that are obtained in the risk register are analyzed thoroughly with
several methods and thus the intensity, effect and prevention can be done (Sheppard & Crannell,
2013).
Conclusion and Recommendation
It can be concluded from the above that ABC fitness gym has several members, employees and
stakeholders for their gym. The equipment of the gym is functioned with latest IT support. The IT framework of
(LL)
Impact
Protection mechanism
The tools and techniques for identifying risk in an IT framework are given below:
1. Documentation reviewing- All the possible documents related to the IT framework of the
equipment in a gym, security, management must be reviewed, studied thoroughly so that
possible risk can be predicted in the initial stages (McNeil et al., 2015).
2. Delphi technique- This technique involves gathering of information related to the gym related to
the information system and sending those to IT experts so that it could be checked and revert
back with best possible results (Park & Kim, 2015).
3. SWOT analysis- As it stands for Strength, weakness, opportunities and threats, therefor this
analysis can be conducted for the information system of the gym and possible threats of the
system can be obtained.
4. Risk register- The benefits of making risk register is that continuous update of the register keeps
track of all the risk throughout the life (Yoe, 2019). This will also help to prevent the risk that
may occur in the future.
5. Risk analysis- The risks that are obtained in the risk register are analyzed thoroughly with
several methods and thus the intensity, effect and prevention can be done (Sheppard & Crannell,
2013).
Conclusion and Recommendation
It can be concluded from the above that ABC fitness gym has several members, employees and
stakeholders for their gym. The equipment of the gym is functioned with latest IT support. The IT framework of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Subject Code Subject Name Semester Number
the gym is developing with intension of introduction of IT aided membership renewal process, health tracking
devices, maintenance of client details, updated data storage systems, backing up of data and several new
updates. With several IT based devices, several risks and threats also emerge into the system like failure of
software, hardware, data backup, information of the employees and members, gym equipment, mishandling od
IT system, also the absence of IT expert can cause large difficulty into the system.
It can be recommended that more IT experts must be recruited for maintenance of the equipment, details
of all the members, employees, and stakeholders, all the members must be trained properly and provide
knowledge of the updated equipment, data storage system, security systems etc. All the software must be
protected from malicious attacks of viruses, anti-viruses must be installed and keep track of the update. The
hardware system must be routinely checked for any kind of malfunction and proper steps must be taken if any
dysfunctionality occurs at the earliest time.
the gym is developing with intension of introduction of IT aided membership renewal process, health tracking
devices, maintenance of client details, updated data storage systems, backing up of data and several new
updates. With several IT based devices, several risks and threats also emerge into the system like failure of
software, hardware, data backup, information of the employees and members, gym equipment, mishandling od
IT system, also the absence of IT expert can cause large difficulty into the system.
It can be recommended that more IT experts must be recruited for maintenance of the equipment, details
of all the members, employees, and stakeholders, all the members must be trained properly and provide
knowledge of the updated equipment, data storage system, security systems etc. All the software must be
protected from malicious attacks of viruses, anti-viruses must be installed and keep track of the update. The
hardware system must be routinely checked for any kind of malfunction and proper steps must be taken if any
dysfunctionality occurs at the earliest time.

Subject Code Subject Name Semester Number
Reference
Ammenwerth, E., Aly, A. F., Bürkle, T., Christ, P., Dormann, H., Friesdorf, W., ... & Menges, K. (2014).
Memorandum on the use of information technology to improve medication safety. Methods of
information in medicine, 53(05), 336-343.
Aqlan, F., & Lam, S. S. (2015). Supply chain risk modelling and mitigation. International Journal of
Production Research, 53(18), 5640-5656.
Arulraj, J., Chang, P. C., Jin, G., & Lu, S. (2013, March). Production-run software failure diagnosis via
hardware performance counters. In Acm Sigplan Notices (Vol. 48, No. 4, pp. 101-112). ACM.
Coras, E. L., & Tantau, A. D. (2013). A risk mitigation model in SME's open innovation projects. Management
& Marketing, 8(2), 303.
Fenz, S., Heurix, J., Neubauer, T., & Pechstein, F. (2014). Current challenges in information security risk
management. Information Management & Computer Security, 22(5), 410-430.
Hajmohammad, S., & Vachon, S. (2016). Mitigation, avoidance, or acceptance? Managing supplier
sustainability risk. Journal of Supply Chain Management, 52(2), 48-65.
Koehler, M. J., Mishra, P., Kereluik, K., Shin, T. S., & Graham, C. R. (2014). The technological pedagogical
content knowledge framework. In Handbook of research on educational communications and
technology (pp. 101-111). Springer, New York, NY.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative Risk Management: Concepts, Techniques and
Tools-revised edition. Princeton university press.
Omar, M. N., Guled, G. Y. M., Zakaria, H., Ampawan, A., & Din, R. (2017). Home-Based Intrusion Detection
System. Journal of Telecommunication, Electronic and Computer Engineering (JTEC), 9(2-4), 107-111.
Park, C. S., & Kim, H. J. (2013). A framework for construction safety management and visualization
system. Automation in Construction, 33, 95-103.
Pattenden, R., & Sheehan, D. (2016). The law of professional-client confidentiality. Oxford University Press.
Reference
Ammenwerth, E., Aly, A. F., Bürkle, T., Christ, P., Dormann, H., Friesdorf, W., ... & Menges, K. (2014).
Memorandum on the use of information technology to improve medication safety. Methods of
information in medicine, 53(05), 336-343.
Aqlan, F., & Lam, S. S. (2015). Supply chain risk modelling and mitigation. International Journal of
Production Research, 53(18), 5640-5656.
Arulraj, J., Chang, P. C., Jin, G., & Lu, S. (2013, March). Production-run software failure diagnosis via
hardware performance counters. In Acm Sigplan Notices (Vol. 48, No. 4, pp. 101-112). ACM.
Coras, E. L., & Tantau, A. D. (2013). A risk mitigation model in SME's open innovation projects. Management
& Marketing, 8(2), 303.
Fenz, S., Heurix, J., Neubauer, T., & Pechstein, F. (2014). Current challenges in information security risk
management. Information Management & Computer Security, 22(5), 410-430.
Hajmohammad, S., & Vachon, S. (2016). Mitigation, avoidance, or acceptance? Managing supplier
sustainability risk. Journal of Supply Chain Management, 52(2), 48-65.
Koehler, M. J., Mishra, P., Kereluik, K., Shin, T. S., & Graham, C. R. (2014). The technological pedagogical
content knowledge framework. In Handbook of research on educational communications and
technology (pp. 101-111). Springer, New York, NY.
McNeil, A. J., Frey, R., & Embrechts, P. (2015). Quantitative Risk Management: Concepts, Techniques and
Tools-revised edition. Princeton university press.
Omar, M. N., Guled, G. Y. M., Zakaria, H., Ampawan, A., & Din, R. (2017). Home-Based Intrusion Detection
System. Journal of Telecommunication, Electronic and Computer Engineering (JTEC), 9(2-4), 107-111.
Park, C. S., & Kim, H. J. (2013). A framework for construction safety management and visualization
system. Automation in Construction, 33, 95-103.
Pattenden, R., & Sheehan, D. (2016). The law of professional-client confidentiality. Oxford University Press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


