IT Risk Management Report: Assessing IT Risks at ABC Organization
VerifiedAdded on 2023/04/04
|8
|1806
|475
Report
AI Summary
This report provides a comprehensive IT risk assessment for ABC organization, a software company facing significant security vulnerabilities. The report identifies critical risks stemming from open internet access, inadequate server security, lack of security policies, and poor employee practices. It categorizes assets, conducts a qualitative risk analysis, and presents a risk register detailing potential impacts and mitigation strategies. The report highlights vulnerabilities in data, physical, individual, intangible, and digital assets. It recommends implementing strict administrative practices, password protections, data encryption, network security, VPNs, strong work-from-home policies, security software, and employee training. The report concludes with a recommendation for the appointment of a Chief Information Security Officer (CISO) to oversee and manage the organization's overall security strategy, ensuring data protection and business continuity.

IT RISK MANAGEMENT
Executive summary:
ABC organization (Tentative name) is a software company that works on innovative software
designs that are expected to be sold in the near future. Most of the company's work such as
Executive summary:
ABC organization (Tentative name) is a software company that works on innovative software
designs that are expected to be sold in the near future. Most of the company's work such as
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

coding and other documentation are stored on the servers on cloud that can be accessed by
internet by anyone from anywhere (Risk). This data is of immense importance for the company
as the company has invested considerable amount on it and thus it is important that the data
should be secured from any confidentiality or integrity breach. The management of the server
infrastructure are in hands of a number of staff, and so the administration which are handled by
different peoples having incomplete knowledge of stuffs, moreover many of the employees have
administrative access (Vulnerability). Company provides open, unrestricted and free internet
service to the employees which they even no need for their jobs as they only have to limited
requirement of web activities (Vulnerability). The company has following departments:
1. Research and development.
2. Management
3. Human Resources and legal
4. Finance
The organization is not abide by any policy framework (Vulnerability). And also there are no
onboarding and off boarding processes for the employees. There are in total six servers in the
organization and each of them are independent having vanilla operating system installed on
them. These servers are neither up to date nor they have patched since long (Vulnerability). The
addresses of the machines are publicly accessible and anyone can access them from internet. The
commodities or servers are obtained from random places wherever the employees feel good
(Vulnerability). The hardware and the software are not maintained at all, even some of them are
very old. The servers store all of the company's data, files, directories and other intellectual
properties. Most of the corporate data are stored on the oracle database. (Research on
Vulnerability). The employees work from home from their personal computers and access all the
organization's data and use some of the services such as CVS from their home. Data redundancy
and fail over is not implemented and hence even a small change in the data can result in loss of
data and services. The root/administrative password of the servers is known to almost every staff
member (Vulnerability). Moreover every user of the server has an account on it irrespective of
them being the admin. Lots of unused accounts that are still active. The machines have been
hacked in the past however they do not seem to bother about that much. There is no security
software such as firewall or antivirus in place similarly there is not security system for shielding
online activities as well. No network security is in place and the server and other workstation
works on the same network. Additionally the server are placed in the physical location which is
accessible by the employees easily. There are no strict password protection policy and most of
the system uses same password which are also easy to identify. Since there seems too many
vulnerability in the security architecture of the company, they should have basic security policies
in place such as Strict administrative practices, Password protections, Encryption of data in rest
and in motion, Network Security, VPN, Strong Work from Home policies, security software and
training to their employees and staff regarding the best practices in handling company's data and
assets
internet by anyone from anywhere (Risk). This data is of immense importance for the company
as the company has invested considerable amount on it and thus it is important that the data
should be secured from any confidentiality or integrity breach. The management of the server
infrastructure are in hands of a number of staff, and so the administration which are handled by
different peoples having incomplete knowledge of stuffs, moreover many of the employees have
administrative access (Vulnerability). Company provides open, unrestricted and free internet
service to the employees which they even no need for their jobs as they only have to limited
requirement of web activities (Vulnerability). The company has following departments:
1. Research and development.
2. Management
3. Human Resources and legal
4. Finance
The organization is not abide by any policy framework (Vulnerability). And also there are no
onboarding and off boarding processes for the employees. There are in total six servers in the
organization and each of them are independent having vanilla operating system installed on
them. These servers are neither up to date nor they have patched since long (Vulnerability). The
addresses of the machines are publicly accessible and anyone can access them from internet. The
commodities or servers are obtained from random places wherever the employees feel good
(Vulnerability). The hardware and the software are not maintained at all, even some of them are
very old. The servers store all of the company's data, files, directories and other intellectual
properties. Most of the corporate data are stored on the oracle database. (Research on
Vulnerability). The employees work from home from their personal computers and access all the
organization's data and use some of the services such as CVS from their home. Data redundancy
and fail over is not implemented and hence even a small change in the data can result in loss of
data and services. The root/administrative password of the servers is known to almost every staff
member (Vulnerability). Moreover every user of the server has an account on it irrespective of
them being the admin. Lots of unused accounts that are still active. The machines have been
hacked in the past however they do not seem to bother about that much. There is no security
software such as firewall or antivirus in place similarly there is not security system for shielding
online activities as well. No network security is in place and the server and other workstation
works on the same network. Additionally the server are placed in the physical location which is
accessible by the employees easily. There are no strict password protection policy and most of
the system uses same password which are also easy to identify. Since there seems too many
vulnerability in the security architecture of the company, they should have basic security policies
in place such as Strict administrative practices, Password protections, Encryption of data in rest
and in motion, Network Security, VPN, Strong Work from Home policies, security software and
training to their employees and staff regarding the best practices in handling company's data and
assets

Security risk to the information technology:
As per industrial definition, Security risk to the IT can be defined as a potential event when
vulnerabilities of a given services are exploited by a threat and thus making potential disaster for
the organization and its business.
Risk: It is the potential reason behind an episode due to which the organization or architecture
can suffer damage.
Vulnerability: It is the weakness in an organization asset or assets which can be misused by
threats.
Threat: It is the potential for damage, problem and/or decimation to the resources or services
during the exploitation of vulnerability (ICT Monitor Worldwide, 2019)
To perform the risk assessment we would first categorize services provided by ABC organization
into the assets given below:
1. Data assets: The Company has both corporate and personal data of the customer. This data is
stored within the Oracle database, company directories, files and folders and hard disk and cloud.
2. Physical assets: These are all the materialistic resources owned by the company such as
property, hardware, inventories, software and cash. These services controls the data. The
company's most important physical assets are the servers and the operating system installed on
them.
3. Individual assets: These are the company's human assets, including the employees, owner,
managerial staff, directors all of which have the required skills and knowledge regarding the
organization and its processes.
4. Intangible assets: These are the intellectual properties of the company, for example, copyright,
confidential information, brand and trademarks etc.
5. Digital assets: These are the media files and other contents that are owned by the company for
their business and marketing purpose.
Risk management approach
To perform risk assessment on the ABC organization, we can chose any one of the following two
methods:
Qualitative Risk Analysis: In this risk analysis, the risk are prioritize for further action by
means of assessing their characteristics such as impact and probability of occurrence.
Quantitative Risk Analysis: In this process the effect of identified risk on the organization
is numerically analyzed of their uncertainty and overall outcomes (Korsakiene,
Smaliukiene & Bileisis, 2018)
For ABC organization we are assessing their risk on the basis of Qualitative risk analysis. The
below diagram clarifies the Qualitative Risk Analysis framework:
As per industrial definition, Security risk to the IT can be defined as a potential event when
vulnerabilities of a given services are exploited by a threat and thus making potential disaster for
the organization and its business.
Risk: It is the potential reason behind an episode due to which the organization or architecture
can suffer damage.
Vulnerability: It is the weakness in an organization asset or assets which can be misused by
threats.
Threat: It is the potential for damage, problem and/or decimation to the resources or services
during the exploitation of vulnerability (ICT Monitor Worldwide, 2019)
To perform the risk assessment we would first categorize services provided by ABC organization
into the assets given below:
1. Data assets: The Company has both corporate and personal data of the customer. This data is
stored within the Oracle database, company directories, files and folders and hard disk and cloud.
2. Physical assets: These are all the materialistic resources owned by the company such as
property, hardware, inventories, software and cash. These services controls the data. The
company's most important physical assets are the servers and the operating system installed on
them.
3. Individual assets: These are the company's human assets, including the employees, owner,
managerial staff, directors all of which have the required skills and knowledge regarding the
organization and its processes.
4. Intangible assets: These are the intellectual properties of the company, for example, copyright,
confidential information, brand and trademarks etc.
5. Digital assets: These are the media files and other contents that are owned by the company for
their business and marketing purpose.
Risk management approach
To perform risk assessment on the ABC organization, we can chose any one of the following two
methods:
Qualitative Risk Analysis: In this risk analysis, the risk are prioritize for further action by
means of assessing their characteristics such as impact and probability of occurrence.
Quantitative Risk Analysis: In this process the effect of identified risk on the organization
is numerically analyzed of their uncertainty and overall outcomes (Korsakiene,
Smaliukiene & Bileisis, 2018)
For ABC organization we are assessing their risk on the basis of Qualitative risk analysis. The
below diagram clarifies the Qualitative Risk Analysis framework:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
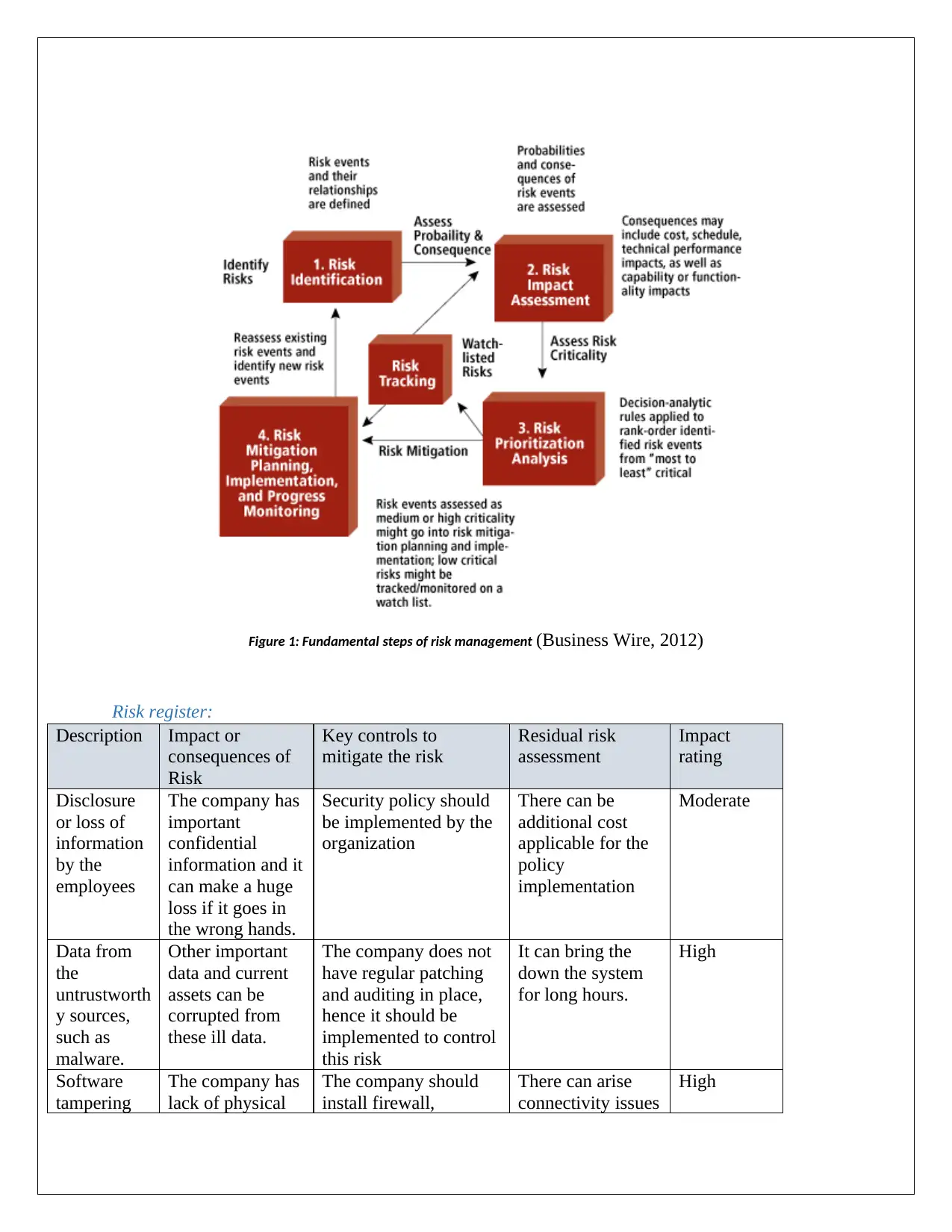
Figure 1: Fundamental steps of risk management (Business Wire, 2012)
Risk register:
Description Impact or
consequences of
Risk
Key controls to
mitigate the risk
Residual risk
assessment
Impact
rating
Disclosure
or loss of
information
by the
employees
The company has
important
confidential
information and it
can make a huge
loss if it goes in
the wrong hands.
Security policy should
be implemented by the
organization
There can be
additional cost
applicable for the
policy
implementation
Moderate
Data from
the
untrustworth
y sources,
such as
malware.
Other important
data and current
assets can be
corrupted from
these ill data.
The company does not
have regular patching
and auditing in place,
hence it should be
implemented to control
this risk
It can bring the
down the system
for long hours.
High
Software
tampering
The company has
lack of physical
The company should
install firewall,
There can arise
connectivity issues
High
Risk register:
Description Impact or
consequences of
Risk
Key controls to
mitigate the risk
Residual risk
assessment
Impact
rating
Disclosure
or loss of
information
by the
employees
The company has
important
confidential
information and it
can make a huge
loss if it goes in
the wrong hands.
Security policy should
be implemented by the
organization
There can be
additional cost
applicable for the
policy
implementation
Moderate
Data from
the
untrustworth
y sources,
such as
malware.
Other important
data and current
assets can be
corrupted from
these ill data.
The company does not
have regular patching
and auditing in place,
hence it should be
implemented to control
this risk
It can bring the
down the system
for long hours.
High
Software
tampering
The company has
lack of physical
The company should
install firewall,
There can arise
connectivity issues
High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
security and
strong password
practices in place
and this the
tampering can
result in complete
system
breakdown,
improper
functioning and
malicious attack
by the insider.
antivirus and other
security systems to
protect their
Software and data from
breached or corrupted.
with the
implementation of
security software.
Tampering
with
hardware
Again the
accessibility of
the servers can
allow tampering
with them
resulting in
information
damaged that is
stored within
them (Ghana
News Agency,
2017)
The servers should be
placed in the secure
area which are only
accessed by authorized
users.
The hardware can
render unavailable
if there is any error
in the physical
security of the
same.
Moderate
Data
corruption
The lack of
recovery
procedures in
place can cause
huge loss to the
company from
data corruption
The company should
ensure backup and
recovery procedures in
place focusing on vital
resources.
The backup
resources can be
vulnerable if not
handled properly.
Low
Unauthentic
ated access
There are no
official signing
off from the
former employees
of the company
and also they
have accounts on
server which can
be accessed from
their home, this
can result in
information
tampering and
leak.
The company should
implement strong
password and
authorization policies
for all the employees.
Highly strong
password has the
risk to be forgotten
which can
disallow the
employee from
using their system.
High
Eavesdroppi The company has The company should There may be High
strong password
practices in place
and this the
tampering can
result in complete
system
breakdown,
improper
functioning and
malicious attack
by the insider.
antivirus and other
security systems to
protect their
Software and data from
breached or corrupted.
with the
implementation of
security software.
Tampering
with
hardware
Again the
accessibility of
the servers can
allow tampering
with them
resulting in
information
damaged that is
stored within
them (Ghana
News Agency,
2017)
The servers should be
placed in the secure
area which are only
accessed by authorized
users.
The hardware can
render unavailable
if there is any error
in the physical
security of the
same.
Moderate
Data
corruption
The lack of
recovery
procedures in
place can cause
huge loss to the
company from
data corruption
The company should
ensure backup and
recovery procedures in
place focusing on vital
resources.
The backup
resources can be
vulnerable if not
handled properly.
Low
Unauthentic
ated access
There are no
official signing
off from the
former employees
of the company
and also they
have accounts on
server which can
be accessed from
their home, this
can result in
information
tampering and
leak.
The company should
implement strong
password and
authorization policies
for all the employees.
Highly strong
password has the
risk to be forgotten
which can
disallow the
employee from
using their system.
High
Eavesdroppi The company has The company should There may be High
ng lack of network
security, and the
servers and other
workstations
work on the same
network, this can
result in
eavesdropping
into the network
to get and misuse
important
information.
adopt encryption and
cryptographic
techniques.
danger of loss of
keys
The server
are used by
unauthorize
d
individuals
It can harm the
integrity,
confidentiality
and availability of
corporate as well
as personal data
of the company.
There should be
adequate physical
security and
authorization check.
In case
authorization keys
are lost it can
abandon legitimate
users.
Moderate
Lack of
formal
procedures
in
employees
on boarding
and off
boarding
process.
This increase the
risk of attack
from outside the
organization.
There should be proper
on boarding and off
boarding procedures in
place along with
practices such as
identity proofing.
--- High
Insecure
network
architecture
Network hopping Virtual Private
Network VPN should
be setup
For VPN
additional
maintence and
security is
required.
High
(Global Data Point, 2016)
Recommendation:
Since the company lacks in adequate policies and procedure in place to secure their assets and
resources from security risk, threats and attacks, it is required that the company should
completely revise their security infrastructure from root. The company should have basic
security policies in place such as Strict administrative practices, Password protections,
Encryption of data in rest and in motion, Network Security, VPN, Strong Work from Home
policies, security software and training to their employees and staff regarding the best practices
security, and the
servers and other
workstations
work on the same
network, this can
result in
eavesdropping
into the network
to get and misuse
important
information.
adopt encryption and
cryptographic
techniques.
danger of loss of
keys
The server
are used by
unauthorize
d
individuals
It can harm the
integrity,
confidentiality
and availability of
corporate as well
as personal data
of the company.
There should be
adequate physical
security and
authorization check.
In case
authorization keys
are lost it can
abandon legitimate
users.
Moderate
Lack of
formal
procedures
in
employees
on boarding
and off
boarding
process.
This increase the
risk of attack
from outside the
organization.
There should be proper
on boarding and off
boarding procedures in
place along with
practices such as
identity proofing.
--- High
Insecure
network
architecture
Network hopping Virtual Private
Network VPN should
be setup
For VPN
additional
maintence and
security is
required.
High
(Global Data Point, 2016)
Recommendation:
Since the company lacks in adequate policies and procedure in place to secure their assets and
resources from security risk, threats and attacks, it is required that the company should
completely revise their security infrastructure from root. The company should have basic
security policies in place such as Strict administrative practices, Password protections,
Encryption of data in rest and in motion, Network Security, VPN, Strong Work from Home
policies, security software and training to their employees and staff regarding the best practices
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

in handling company's data and assets. We would recommend that the company should appoint a
security personnel such as Chief Information Security Officer CISO to oversee security of their
assets and resources (PR Newswire, 2018). The security personnel would be in charge of
maintaining and dealing with the overall risk strategy and would implement feasible solutions to
secure from data breach. He/she will help them in supervising majority of the strategies and
techniques for security of the organization. The CISOs have state of the art knowledge and
advances in cyber security to provide the best information and skill to the organization.
security personnel such as Chief Information Security Officer CISO to oversee security of their
assets and resources (PR Newswire, 2018). The security personnel would be in charge of
maintaining and dealing with the overall risk strategy and would implement feasible solutions to
secure from data breach. He/she will help them in supervising majority of the strategies and
techniques for security of the organization. The CISOs have state of the art knowledge and
advances in cyber security to provide the best information and skill to the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References:
AWS security hub centralizes an organization`s cloud security view. (2019, Mar 11). ICT
Monitor Worldwide. Retrieved from https://search.proquest.com/docview/2189405607?
accountid=30552
Ironically, an organization`s security RFP distribution process can be a threat to its security.
(2016, Dec 16). Global Data Point. Retrieved from
https://search.proquest.com/docview/1849434715?accountid=30552
Korsakiene, R., Smaliukiene, R., & Bileisis, M. (2018). Knowledge sharing in defence and
security organisations: Insights into particular practices. Kidmore End: Academic
Conferences International Limited. Retrieved from
https://search.proquest.com/docview/2116815594?accountid=30552
Media organizations' security practices, threats & concerns examined in new akamai research
report: 'the state of media security' survey finds that few media organizations are 'very
confident' in their current security measures. (2018, Apr 04). PR Newswire Retrieved
from https://search.proquest.com/docview/2021246978?accountid=30552
Private security organisations cautioned against wearing state security uniforms. (2017, Aug
03). Ghana News Agency (GNA) Retrieved from
https://search.proquest.com/docview/1925562226?accountid=30552
Survey: Majority of IT security pros believe executives understand their organization's security
posture. (2012, Mar 07). Business Wire. Retrieved from
https://search.proquest.com/docview/926563946?accountid=30552
AWS security hub centralizes an organization`s cloud security view. (2019, Mar 11). ICT
Monitor Worldwide. Retrieved from https://search.proquest.com/docview/2189405607?
accountid=30552
Ironically, an organization`s security RFP distribution process can be a threat to its security.
(2016, Dec 16). Global Data Point. Retrieved from
https://search.proquest.com/docview/1849434715?accountid=30552
Korsakiene, R., Smaliukiene, R., & Bileisis, M. (2018). Knowledge sharing in defence and
security organisations: Insights into particular practices. Kidmore End: Academic
Conferences International Limited. Retrieved from
https://search.proquest.com/docview/2116815594?accountid=30552
Media organizations' security practices, threats & concerns examined in new akamai research
report: 'the state of media security' survey finds that few media organizations are 'very
confident' in their current security measures. (2018, Apr 04). PR Newswire Retrieved
from https://search.proquest.com/docview/2021246978?accountid=30552
Private security organisations cautioned against wearing state security uniforms. (2017, Aug
03). Ghana News Agency (GNA) Retrieved from
https://search.proquest.com/docview/1925562226?accountid=30552
Survey: Majority of IT security pros believe executives understand their organization's security
posture. (2012, Mar 07). Business Wire. Retrieved from
https://search.proquest.com/docview/926563946?accountid=30552
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





