Wireless Network Security Configuration Report: ABC-XYZ Education
VerifiedAdded on 2020/04/07
|19
|2483
|61
Report
AI Summary
This report details the design and implementation of a secure wireless network for ABC-XYZ Education. It covers the requirements of the network, including the use of a domain controller with services like NPS and Certificate Authority. The report explains the configuration of two SSIDs, one for students and staff and another for guests, including WLAN and VLAN settings. Security configurations, such as firewall authentication and enterprise-level security, are discussed. Furthermore, the report addresses access point placement with two different RF ranges, outlining the RF plan and equipment used, such as firewalls, ADDS controllers, DNS servers, and routers. The report also provides configuration details for the SSIDs, including IP addresses and subnet masks, and justifies the placement of two access points based on the site plan and user count. Finally, the report includes network diagrams and a conclusion summarizing the key findings.

Wireless Network Security
i
i
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction...........................................................................................................................2
2. Requirements of network and network planning..................................................................2
3. Configuration of WLAN settings for SSID 1(student and staff) and SSID2 (Guest).............3
4. Configuration of VLAN settings for SSID 1(student and staff) and SSID2 (Guest)..............6
5. Configuration of security settings..........................................................................................7
6. Placement of Access points with two different RF range.....................................................11
7. Network diagrams...............................................................................................................14
8. Conclusion...........................................................................................................................16
References...................................................................................................................................17
1
1. Introduction...........................................................................................................................2
2. Requirements of network and network planning..................................................................2
3. Configuration of WLAN settings for SSID 1(student and staff) and SSID2 (Guest).............3
4. Configuration of VLAN settings for SSID 1(student and staff) and SSID2 (Guest)..............6
5. Configuration of security settings..........................................................................................7
6. Placement of Access points with two different RF range.....................................................11
7. Network diagrams...............................................................................................................14
8. Conclusion...........................................................................................................................16
References...................................................................................................................................17
1

1. Introduction
Wireless network is one type LAN (Local Area Network). It has high radio wave
frequency compared to the wires. AP (Access Point) is one of the hardware device. It is used
for wireless communication. It makes a bridge between wired and wireless devices for
communication. The wireless Local Area Network security plan will be designed and
researched for the ABC-XYZ Education. The active authority will be made for students and
staffs to activate the wireless network in their own mobile devices also, at the ABC-XYZ
Education. Additionally ABC-XYZ Education will provide the internet access for the guest
user, but the guest user could not require the ABC-XYZ Certificate Authority. The guest user
only access the internet in the ABC-XYZ Education location. The strategy plan will be
designed for overall deployment, management and control of the wireless network by
management of ABC-XYZ Education. For security purpose the firewall authentication will
be created to access the internet access. It will allow staffs to the all access except the FTP,
Telnet and ICMP. But it will provide the permission for guest to access the HTTPS/HTTP
and DNS.
2. Requirements of network and network planning
The server has been designed to act as domain controller for ABC-XYZ education. It
could be run the below services
1) NPS
2) Certificate Authority
3) DNS
DNS
Domain Name System is a protocol.it changes the domain names into IP addresses. It
control the website, email settings and domain name. Some of the factors affect the DNS
propagation time that are domain name's registry, ISP and TTL.
Certificate Authority
CA is an active directory domain. It need authentication to access the internet. By
using this only the staff and students could access the internet in the education location.
2
Wireless network is one type LAN (Local Area Network). It has high radio wave
frequency compared to the wires. AP (Access Point) is one of the hardware device. It is used
for wireless communication. It makes a bridge between wired and wireless devices for
communication. The wireless Local Area Network security plan will be designed and
researched for the ABC-XYZ Education. The active authority will be made for students and
staffs to activate the wireless network in their own mobile devices also, at the ABC-XYZ
Education. Additionally ABC-XYZ Education will provide the internet access for the guest
user, but the guest user could not require the ABC-XYZ Certificate Authority. The guest user
only access the internet in the ABC-XYZ Education location. The strategy plan will be
designed for overall deployment, management and control of the wireless network by
management of ABC-XYZ Education. For security purpose the firewall authentication will
be created to access the internet access. It will allow staffs to the all access except the FTP,
Telnet and ICMP. But it will provide the permission for guest to access the HTTPS/HTTP
and DNS.
2. Requirements of network and network planning
The server has been designed to act as domain controller for ABC-XYZ education. It
could be run the below services
1) NPS
2) Certificate Authority
3) DNS
DNS
Domain Name System is a protocol.it changes the domain names into IP addresses. It
control the website, email settings and domain name. Some of the factors affect the DNS
propagation time that are domain name's registry, ISP and TTL.
Certificate Authority
CA is an active directory domain. It need authentication to access the internet. By
using this only the staff and students could access the internet in the education location.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NPS
NPS stands for Network Policy Server. When the staffs and student are access the
wireless access point for network connectivity in their education location that occasion NPS
is used to manage, enforce and create the network policies. It is also used to find out whether
the computer and users could access the internet.
Two Service Set Identifier is used in the project.it is a character unique identifier.
When the mobile is connected to a BSS (basic service set), it act as a password. These two
SSID's are run by Aruba IAP. In this, one guest network and one employee network using
WPA2 enterprise.
The firewall authentication is made for the security purpose. It would permit the staffs
to access the internet except the Telnet, FTP and ICMP. FTP is a File Transfer Protocol. It is
used to transfer the files. ICMP is an Internet Control Message Protocol that is used in
network devices. It could sent error messages. The firewall authentication could permits the
guest only to access the HTTPs/HTTP and DNS. The native VLAN and IP addresses are
identified for master controller and access point. The WLAN subnet is identified for the
network. The site survey and RF plan showed the AP placement and suggested channel
pattern for 2.4GHz and 5GHz.
3. Configuration of WLAN settings for SSID 1(student and staff) and
SSID2 (Guest)
WLAN
Wireless Local Area Network (WLAN) is a network that is used to establish
communication between two or more devices over limited area. Wireless communication
network seems to be more open than wired LANs. Encryption methodologies are followed to
encrypt the wireless LAN communications. Such encryptions differ in types. Such encrypted
WLANs are WEPs, WPAs. Wi-Fi can be setup both in residential area and also in
commercial areas. Wireless networks sets access point over a particular bandwidth in RF
frequency range and cover decided area.
Step1
The first step in setting up WLAN is the opening of WLAN settings tab. Instant UI is
used in the setting up of a wireless Local Area Network. Open Instant UI. Open the Networks
3
NPS stands for Network Policy Server. When the staffs and student are access the
wireless access point for network connectivity in their education location that occasion NPS
is used to manage, enforce and create the network policies. It is also used to find out whether
the computer and users could access the internet.
Two Service Set Identifier is used in the project.it is a character unique identifier.
When the mobile is connected to a BSS (basic service set), it act as a password. These two
SSID's are run by Aruba IAP. In this, one guest network and one employee network using
WPA2 enterprise.
The firewall authentication is made for the security purpose. It would permit the staffs
to access the internet except the Telnet, FTP and ICMP. FTP is a File Transfer Protocol. It is
used to transfer the files. ICMP is an Internet Control Message Protocol that is used in
network devices. It could sent error messages. The firewall authentication could permits the
guest only to access the HTTPs/HTTP and DNS. The native VLAN and IP addresses are
identified for master controller and access point. The WLAN subnet is identified for the
network. The site survey and RF plan showed the AP placement and suggested channel
pattern for 2.4GHz and 5GHz.
3. Configuration of WLAN settings for SSID 1(student and staff) and
SSID2 (Guest)
WLAN
Wireless Local Area Network (WLAN) is a network that is used to establish
communication between two or more devices over limited area. Wireless communication
network seems to be more open than wired LANs. Encryption methodologies are followed to
encrypt the wireless LAN communications. Such encryptions differ in types. Such encrypted
WLANs are WEPs, WPAs. Wi-Fi can be setup both in residential area and also in
commercial areas. Wireless networks sets access point over a particular bandwidth in RF
frequency range and cover decided area.
Step1
The first step in setting up WLAN is the opening of WLAN settings tab. Instant UI is
used in the setting up of a wireless Local Area Network. Open Instant UI. Open the Networks
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
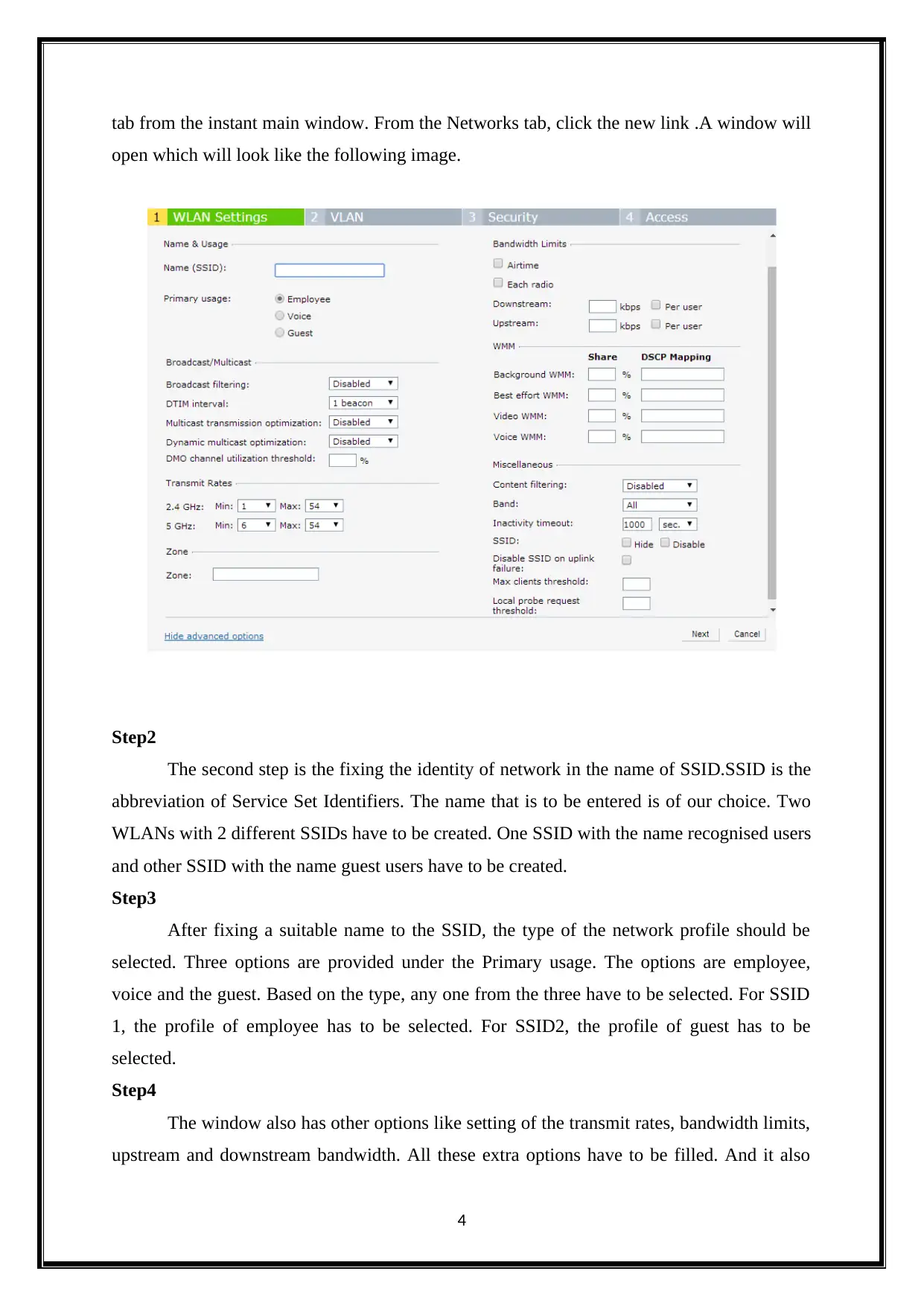
tab from the instant main window. From the Networks tab, click the new link .A window will
open which will look like the following image.
Step2
The second step is the fixing the identity of network in the name of SSID.SSID is the
abbreviation of Service Set Identifiers. The name that is to be entered is of our choice. Two
WLANs with 2 different SSIDs have to be created. One SSID with the name recognised users
and other SSID with the name guest users have to be created.
Step3
After fixing a suitable name to the SSID, the type of the network profile should be
selected. Three options are provided under the Primary usage. The options are employee,
voice and the guest. Based on the type, any one from the three have to be selected. For SSID
1, the profile of employee has to be selected. For SSID2, the profile of guest has to be
selected.
Step4
The window also has other options like setting of the transmit rates, bandwidth limits,
upstream and downstream bandwidth. All these extra options have to be filled. And it also
4
open which will look like the following image.
Step2
The second step is the fixing the identity of network in the name of SSID.SSID is the
abbreviation of Service Set Identifiers. The name that is to be entered is of our choice. Two
WLANs with 2 different SSIDs have to be created. One SSID with the name recognised users
and other SSID with the name guest users have to be created.
Step3
After fixing a suitable name to the SSID, the type of the network profile should be
selected. Three options are provided under the Primary usage. The options are employee,
voice and the guest. Based on the type, any one from the three have to be selected. For SSID
1, the profile of employee has to be selected. For SSID2, the profile of guest has to be
selected.
Step4
The window also has other options like setting of the transmit rates, bandwidth limits,
upstream and downstream bandwidth. All these extra options have to be filled. And it also
4

has some advanced options. The advanced options include broadcast filtering and DTIM
interval.
Step5
And then click next for the purpose of configuration of VLAN settings.
In the CLI, type the following commands for the configuration of the WLAN.
5
interval.
Step5
And then click next for the purpose of configuration of VLAN settings.
In the CLI, type the following commands for the configuration of the WLAN.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
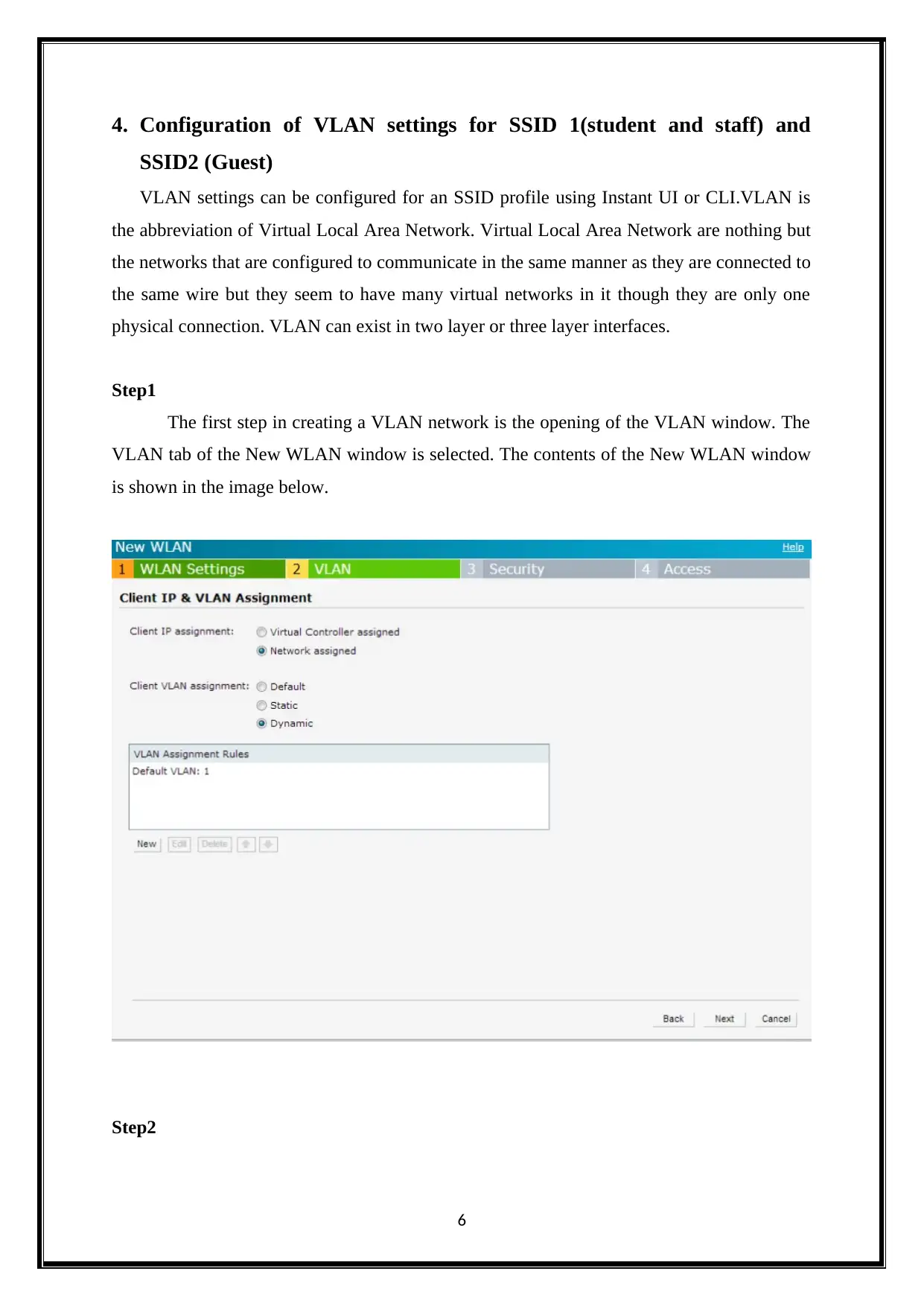
4. Configuration of VLAN settings for SSID 1(student and staff) and
SSID2 (Guest)
VLAN settings can be configured for an SSID profile using Instant UI or CLI.VLAN is
the abbreviation of Virtual Local Area Network. Virtual Local Area Network are nothing but
the networks that are configured to communicate in the same manner as they are connected to
the same wire but they seem to have many virtual networks in it though they are only one
physical connection. VLAN can exist in two layer or three layer interfaces.
Step1
The first step in creating a VLAN network is the opening of the VLAN window. The
VLAN tab of the New WLAN window is selected. The contents of the New WLAN window
is shown in the image below.
Step2
6
SSID2 (Guest)
VLAN settings can be configured for an SSID profile using Instant UI or CLI.VLAN is
the abbreviation of Virtual Local Area Network. Virtual Local Area Network are nothing but
the networks that are configured to communicate in the same manner as they are connected to
the same wire but they seem to have many virtual networks in it though they are only one
physical connection. VLAN can exist in two layer or three layer interfaces.
Step1
The first step in creating a VLAN network is the opening of the VLAN window. The
VLAN tab of the New WLAN window is selected. The contents of the New WLAN window
is shown in the image below.
Step2
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The next step is the assignment of the Client IP. The client IP assignment involves the
process of selection of any one of the two options. One option involves the assignment of IP
using the virtual controller. The other option involves the assignment of IP by the network.
Step3
If one chooses the option Virtual controller assigned, then it has to be specified
whether it is default or custom. If one chooses the option network assigned, then it has to be
specified whether it is static, default or dynamic. Under the dynamic option, there are
attributes that has to be given information. They are attribute, operator, string, VLAN.
Step4
Once the previous step is completed, click next to configure the security settings.
In the CLI, the following commands have to be entered for VLAN setting
5. Configuration of security settings
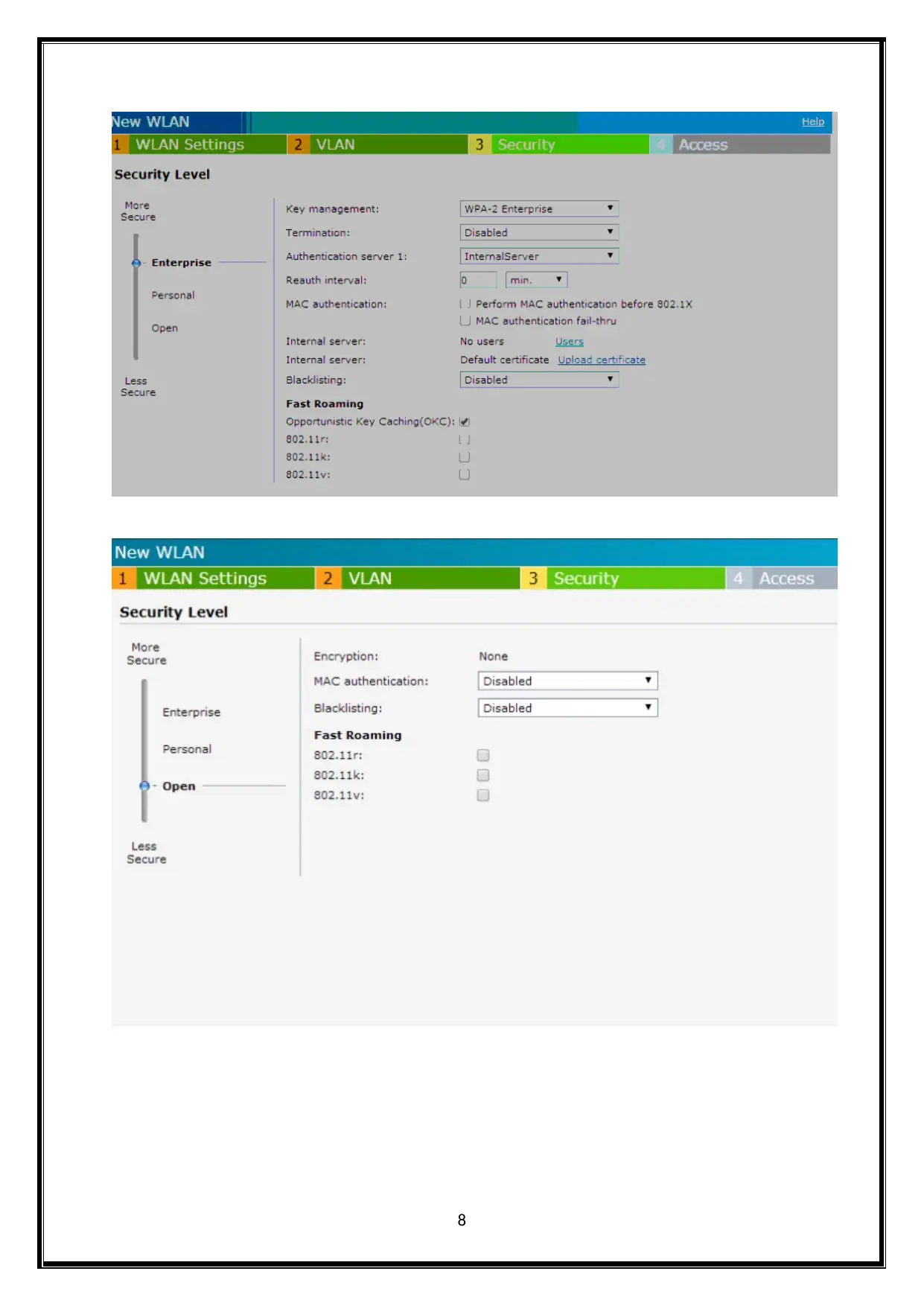
Using the Instant UI the security settings could be configured for the employee.
Choose any of the security level in the security tab by scrolling. One could choose the
enterprise level for the accessing the enterprise network. The default setting is personal.
7
process of selection of any one of the two options. One option involves the assignment of IP
using the virtual controller. The other option involves the assignment of IP by the network.
Step3
If one chooses the option Virtual controller assigned, then it has to be specified
whether it is default or custom. If one chooses the option network assigned, then it has to be
specified whether it is static, default or dynamic. Under the dynamic option, there are
attributes that has to be given information. They are attribute, operator, string, VLAN.
Step4
Once the previous step is completed, click next to configure the security settings.
In the CLI, the following commands have to be entered for VLAN setting
5. Configuration of security settings
Using the Instant UI the security settings could be configured for the employee.
Choose any of the security level in the security tab by scrolling. One could choose the
enterprise level for the accessing the enterprise network. The default setting is personal.
7
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
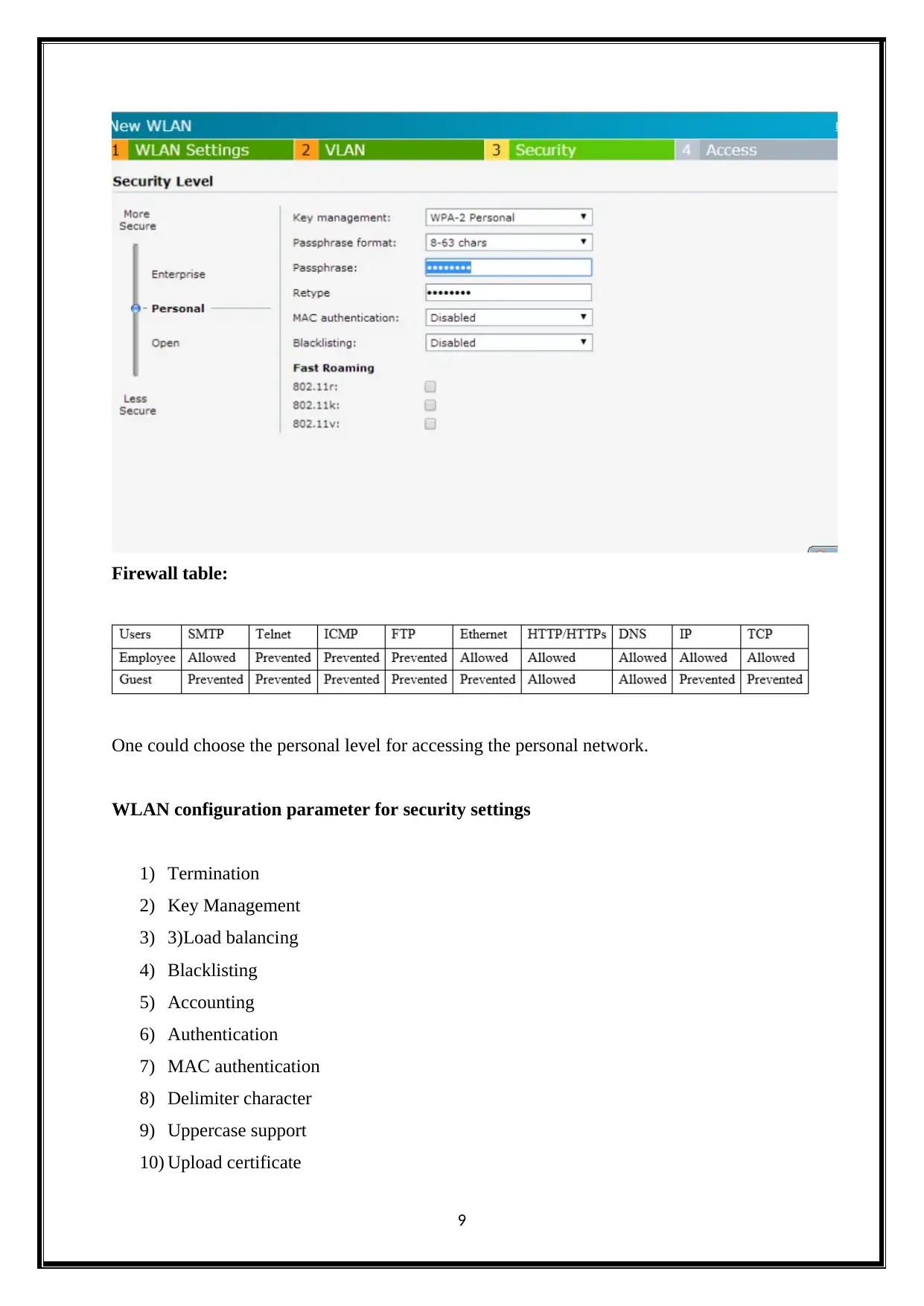
Firewall table:
One could choose the personal level for accessing the personal network.
WLAN configuration parameter for security settings
1) Termination
2) Key Management
3) 3)Load balancing
4) Blacklisting
5) Accounting
6) Authentication
7) MAC authentication
8) Delimiter character
9) Uppercase support
10) Upload certificate
9
One could choose the personal level for accessing the personal network.
WLAN configuration parameter for security settings
1) Termination
2) Key Management
3) 3)Load balancing
4) Blacklisting
5) Accounting
6) Authentication
7) MAC authentication
8) Delimiter character
9) Uppercase support
10) Upload certificate
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11) Fast Roaming
12) Authentication server1 and Authentication server 2
13) Uppercase support
The above all parameters are applicable for Enterprise level. Using the CLI the
security settings could be configured for the employee.
The enterprise security settings is configured for the employee users of a WLAN SSID
The personal security settings is configured for the personal users of a WLAN SSID
The open security settings is configured for the open users of a WLAN SSID
10
12) Authentication server1 and Authentication server 2
13) Uppercase support
The above all parameters are applicable for Enterprise level. Using the CLI the
security settings could be configured for the employee.
The enterprise security settings is configured for the employee users of a WLAN SSID
The personal security settings is configured for the personal users of a WLAN SSID
The open security settings is configured for the open users of a WLAN SSID
10

6. Placement of Access points with two different RF range
Radio Frequency (RF) plan is a modelling tool for wireless deployment. Which
guides to design the WLAN (Wireless Local Area Network) in efficient manner, which can
optimizes performance and coverage, without difficult WLAN network arrangement. The RF
plan explains the critical functionality.
1. Defines the Wireless Local Area Network coverage.
2. Defines the WLAN environment security coverage.
3. Assesses the equipment requirements.
4. Optimizes the radio resources.
The below screenshot explains the site plan with 2 Access points that support with the
wireless network design. The design contains both Map and dap placement and suggested
channel pattern for 2.4GHz. And also Map with AP placement and suggested channel pattern
for 5GHz.
The Radio Frequency plan contains an outlook of all the floor, and permits to specify how
to provide a wireless coverage for all the area. The Radio Frequency also produce reporting
maps with AM and Access Point (AP) management. To create a building with following
steps
1. Collect the necessary information about building's dimensions and plans for floor.
2. To identify the level of coverage for AM and APs.
3. To create a building and mention the dimensions.
4. Select the parameter for Access Point coverage.
5. Similarly select the parameter for AM coverage.
6. Insert floors to building and import the plans for floor.
7. Determine the special areas.
11
Radio Frequency (RF) plan is a modelling tool for wireless deployment. Which
guides to design the WLAN (Wireless Local Area Network) in efficient manner, which can
optimizes performance and coverage, without difficult WLAN network arrangement. The RF
plan explains the critical functionality.
1. Defines the Wireless Local Area Network coverage.
2. Defines the WLAN environment security coverage.
3. Assesses the equipment requirements.
4. Optimizes the radio resources.
The below screenshot explains the site plan with 2 Access points that support with the
wireless network design. The design contains both Map and dap placement and suggested
channel pattern for 2.4GHz. And also Map with AP placement and suggested channel pattern
for 5GHz.
The Radio Frequency plan contains an outlook of all the floor, and permits to specify how
to provide a wireless coverage for all the area. The Radio Frequency also produce reporting
maps with AM and Access Point (AP) management. To create a building with following
steps
1. Collect the necessary information about building's dimensions and plans for floor.
2. To identify the level of coverage for AM and APs.
3. To create a building and mention the dimensions.
4. Select the parameter for Access Point coverage.
5. Similarly select the parameter for AM coverage.
6. Insert floors to building and import the plans for floor.
7. Determine the special areas.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



