Practical Implementation: Access Control and PKI on Windows Server
VerifiedAdded on 2023/05/29
|14
|1942
|467
Practical Assignment
AI Summary
This practical assignment delves into access control and Public Key Infrastructure (PKI) within a Windows Server environment. It covers the configuration of Active Directory Domain Services (ADDS) and DNS server, user entity verification, and analysis of user records including attributes like name, description, and organizational details. The assignment explores shared folder permissions, administrator properties, and the creation of key pairs. Security aspects, such as the importance of authentication through ADDS and the role of PKI in securing data exchange, are also highlighted. Furthermore, the document touches on challenges and risks in account management, including monitoring, password management, scalability, and the enforcement of access control policies, alongside a discussion on encryption, key management, and security considerations within Infrastructure as a Service (IaaS) cloud computing.

Access Control and PKI
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
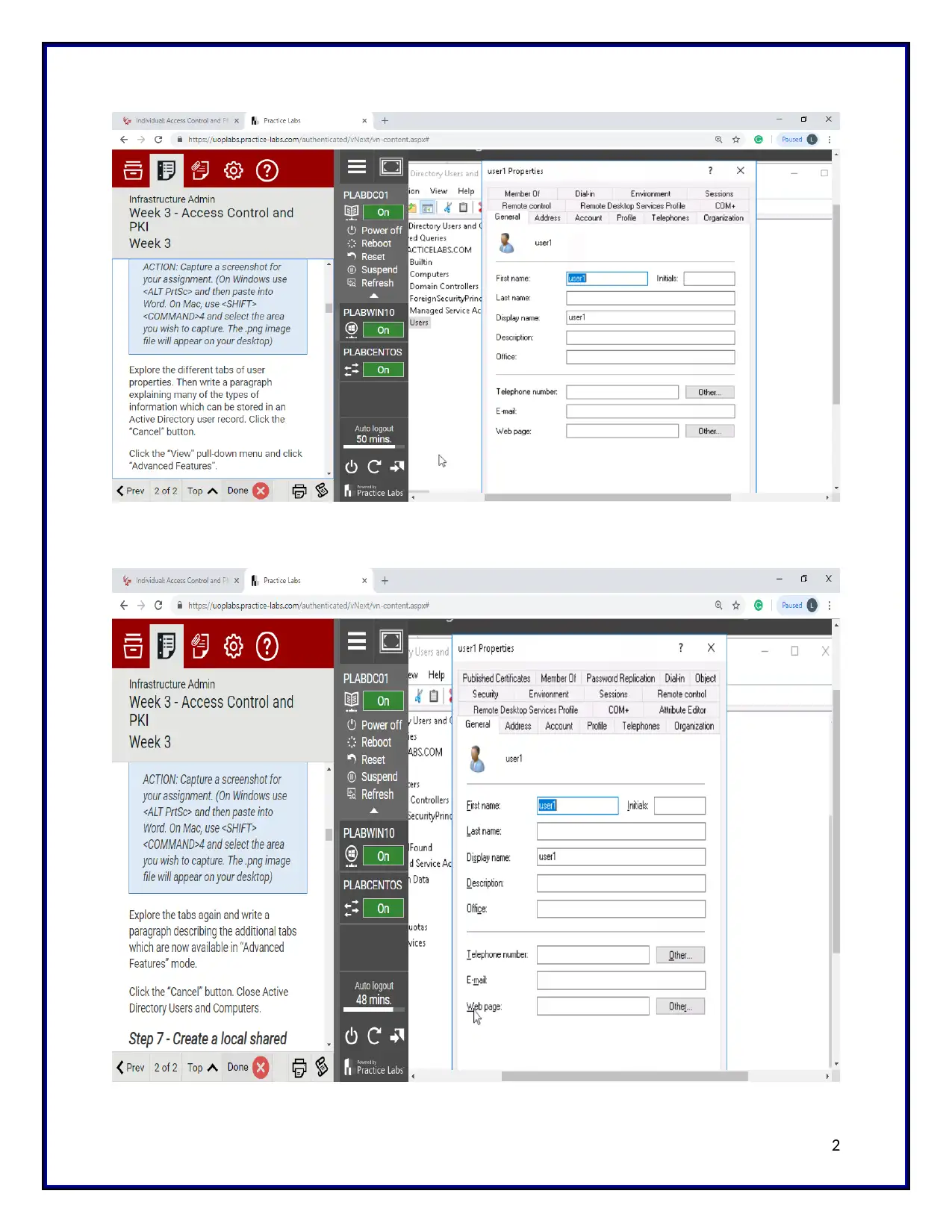
The tabs are different because
Generally the user properties will be appeared by holding down the shift or control key
when selecting the user record. But here the three tabs are different. There are two reasons.
First one is the properties options which are extended in the normal state. Because
initially it is in the hidden state.
Second reason is the advanced features option is selected. So the additional tabs
are appeared while taking the third tab.
Because of these reasons the tabs are appeared differently.
Usually, the windows server has four property tabs regarding the user accounts. They are
sessions, environment, remote control, and terminal services profile. These boxes are represented
to control the settings of the terminal services per user basis. Here, the bottom profile contains
important checkboxes. Here, the top boxes are represented to locate the options such as home
directory and the profile. But default it is empty. Here, the profile tab is mentioned to identify the
location of the profile and home directory. It will show only when the user logged in locally.
3
Generally the user properties will be appeared by holding down the shift or control key
when selecting the user record. But here the three tabs are different. There are two reasons.
First one is the properties options which are extended in the normal state. Because
initially it is in the hidden state.
Second reason is the advanced features option is selected. So the additional tabs
are appeared while taking the third tab.
Because of these reasons the tabs are appeared differently.
Usually, the windows server has four property tabs regarding the user accounts. They are
sessions, environment, remote control, and terminal services profile. These boxes are represented
to control the settings of the terminal services per user basis. Here, the bottom profile contains
important checkboxes. Here, the top boxes are represented to locate the options such as home
directory and the profile. But default it is empty. Here, the profile tab is mentioned to identify the
location of the profile and home directory. It will show only when the user logged in locally.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Generally, the user record has many types to store the information. They are first name,
initials, last name, display name, description, office, telephone number, and email. These type of
information’s are established in the active directory user record. These type of information are
placed under the general category. Apart from the general category, there are many types of
information. They are address, profile, remote control, account, organization, environment, and
remote desktop services profile. Additionally, it has options such as published certificates,
object, and security.
Usually, the active directory computers and users have some features. They are named as
built-in, computers, domain controllers, foreign security principles, managed service accounts,
and users. Also, it has some advanced features. They are listed below.
Advanced features
Lost and found
Program data
System
TPM devices (Trusted platform modules)
NTDS Quotas
The challenges and risks of account management are described here. The account
management is considered as a key part to the organizations regarding security. The accounts
should access the sensitive data and the systems. But here many challenges are involved
regarding the account management. They are listed below.
Monitoring and auditing
Password management
Managing the access
Security
7
initials, last name, display name, description, office, telephone number, and email. These type of
information’s are established in the active directory user record. These type of information are
placed under the general category. Apart from the general category, there are many types of
information. They are address, profile, remote control, account, organization, environment, and
remote desktop services profile. Additionally, it has options such as published certificates,
object, and security.
Usually, the active directory computers and users have some features. They are named as
built-in, computers, domain controllers, foreign security principles, managed service accounts,
and users. Also, it has some advanced features. They are listed below.
Advanced features
Lost and found
Program data
System
TPM devices (Trusted platform modules)
NTDS Quotas
The challenges and risks of account management are described here. The account
management is considered as a key part to the organizations regarding security. The accounts
should access the sensitive data and the systems. But here many challenges are involved
regarding the account management. They are listed below.
Monitoring and auditing
Password management
Managing the access
Security
7

Scalability
A lot of users may have the same passwords. There must be a security issue regarding
the password. So the password management is represented as the challenge for account
management. Here the password management helps to change the passwords to the random
values. For that, password management needs infrastructure and policies. These policies are used
for authentication and access control (Younglove, 2001).
Managing access is used to minimize the risk of internal and external threats. Allowing
freedom may increase the risks of the company. The development of a dynamic system is needed
for the organizations for managing the access. Generally, the account management needs the
monitoring and auditing process to identify the potential issues. The monitoring process will
need when the irregular usage is detected. Also, the monitoring is need against the unauthorized
access.
Also, this is used to catch the serious breaches. Auditing is considered as one of the
challenges. According to auditing, logging in the system is considered an important one.
Scalability is also considered as the problem regarding account management. This is used to
increase the growth of the organization. For the security, the access needs to be restricted for the
unscrupulous people. The automated management programs need to be established for the
security regarding account management (Shimonski, 2003).
Access control is a selective restriction of data access. In access control, there are two
major components. They are authorization and authentication. Authentication is used for
verification of the user. It is not efficient to protect the data. So, the authorization is needed. The
authorization determines whether the user is allowed to access the data or not. If there is no
access control means, then there is no authentication and authorization. If there is no
authentication and authorization, then there is no data security. If there is no security on the
information, then the attackers or hackers can easily access the data and may misuse them. So,
inadequate access control will leave critical information vulnerable (Wang & Wang, 2013).
The following are the challenges which arise while enforcing access control.
8
A lot of users may have the same passwords. There must be a security issue regarding
the password. So the password management is represented as the challenge for account
management. Here the password management helps to change the passwords to the random
values. For that, password management needs infrastructure and policies. These policies are used
for authentication and access control (Younglove, 2001).
Managing access is used to minimize the risk of internal and external threats. Allowing
freedom may increase the risks of the company. The development of a dynamic system is needed
for the organizations for managing the access. Generally, the account management needs the
monitoring and auditing process to identify the potential issues. The monitoring process will
need when the irregular usage is detected. Also, the monitoring is need against the unauthorized
access.
Also, this is used to catch the serious breaches. Auditing is considered as one of the
challenges. According to auditing, logging in the system is considered an important one.
Scalability is also considered as the problem regarding account management. This is used to
increase the growth of the organization. For the security, the access needs to be restricted for the
unscrupulous people. The automated management programs need to be established for the
security regarding account management (Shimonski, 2003).
Access control is a selective restriction of data access. In access control, there are two
major components. They are authorization and authentication. Authentication is used for
verification of the user. It is not efficient to protect the data. So, the authorization is needed. The
authorization determines whether the user is allowed to access the data or not. If there is no
access control means, then there is no authentication and authorization. If there is no
authentication and authorization, then there is no data security. If there is no security on the
information, then the attackers or hackers can easily access the data and may misuse them. So,
inadequate access control will leave critical information vulnerable (Wang & Wang, 2013).
The following are the challenges which arise while enforcing access control.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Persistent policies are needed.
Deciding appropriate control model
For access control, multiple solutions are needed.
Authorization
Dynamically changing policies
If there is no sufficient access control policies, then the valuable data or information in the
system will become vulnerable to attacks.
The encryption offers data protection and security. The encryption keeps the data private,
maintains the accuracy of the data, keeps the web server online, and keeps the data available.
The key management is important to secure the encrypted system. Most commonly SSL
certificates are used to protect the confidential data. In SSL certificate, there are two key
components. They are private and public key. The public key is used to encrypt the data and this
key can be used by the public. The private key is used to decrypt the data and this is used by a
company to read the encrypted data. The private keys are used for secure communication, SSL
and encryption. If an attacker knows the private key, then the attacker has full access. The
attacker can decrypt all the important files and know all other information. The user must store
their private keys within a secure and well-managed infrastructure. Otherwise, it is easy for
attackers to read the encrypted traffic. Because of this, the private keys must be protected to
prevent this kind of threats. So, the key management is important to keep the encryption system
in secured manner.
9
Deciding appropriate control model
For access control, multiple solutions are needed.
Authorization
Dynamically changing policies
If there is no sufficient access control policies, then the valuable data or information in the
system will become vulnerable to attacks.
The encryption offers data protection and security. The encryption keeps the data private,
maintains the accuracy of the data, keeps the web server online, and keeps the data available.
The key management is important to secure the encrypted system. Most commonly SSL
certificates are used to protect the confidential data. In SSL certificate, there are two key
components. They are private and public key. The public key is used to encrypt the data and this
key can be used by the public. The private key is used to decrypt the data and this is used by a
company to read the encrypted data. The private keys are used for secure communication, SSL
and encryption. If an attacker knows the private key, then the attacker has full access. The
attacker can decrypt all the important files and know all other information. The user must store
their private keys within a secure and well-managed infrastructure. Otherwise, it is easy for
attackers to read the encrypted traffic. Because of this, the private keys must be protected to
prevent this kind of threats. So, the key management is important to keep the encryption system
in secured manner.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In cloud computing architecture, IaaS is at the lowest level. Full form of IaaS is
Infrastructure as a Service. Through the virtualized interface, the IaaS will provide the
configured and pre-installed software or hardware (B. & D., 2018). Developing the environments
and managed hosting are the offerings provided by the IaaS.
Advantages of IaaS
The following are the advantages of IaaS (Infrastructure as a Service) Cloud.
Flexibility – The IaaS can be accessed remotely.
It minimizes the maintenance of the hardware. It also reduces the money and time spent
on maintenance.
The IaaS systems can be scaled up efficiently and quickly.
This reduces the downtime.
The user can only pay what they are using.
Cost-efficiently
Security issues in IaaS
End-to-End logging and reporting
End-to-End encryption
Data leakage protection
Usage Monitoring
Authorization
Authentication
Hardening of infrastructure
Misconfiguration
Shadow-IT
Vulnerabilities
These are the security issues present in the IaaS cloud.
Challenges in IaaS related to key management
Availability
Governance
General security issues
10
Infrastructure as a Service. Through the virtualized interface, the IaaS will provide the
configured and pre-installed software or hardware (B. & D., 2018). Developing the environments
and managed hosting are the offerings provided by the IaaS.
Advantages of IaaS
The following are the advantages of IaaS (Infrastructure as a Service) Cloud.
Flexibility – The IaaS can be accessed remotely.
It minimizes the maintenance of the hardware. It also reduces the money and time spent
on maintenance.
The IaaS systems can be scaled up efficiently and quickly.
This reduces the downtime.
The user can only pay what they are using.
Cost-efficiently
Security issues in IaaS
End-to-End logging and reporting
End-to-End encryption
Data leakage protection
Usage Monitoring
Authorization
Authentication
Hardening of infrastructure
Misconfiguration
Shadow-IT
Vulnerabilities
These are the security issues present in the IaaS cloud.
Challenges in IaaS related to key management
Availability
Governance
General security issues
10

Management of all keys
The keys may be stolen and these can be vulnerable to attack or it can be compromised. To
handle lots of keys, the IaaS needs to be scaled linearly. Only allow the authorized user to use the
keys in order to access the data. Define the policy, usage, protection, and access to maintain
governance.
Here, the practical work is made regarding the access control and public key
infrastructure. Access control is considered as an integral part of computer security. And the
public key infrastructure is used to distribute and identify the public encryption keys. By using
this public key infrastructure, the user and computer can exchange the data with security.
The windows server is used as the tool for access control and public key infrastructure.
The ADDS server is installed and configured in the windows server. The active directory domain
services are used for the authentication purpose. And the DNS server is installed for setting the
domain name. The domain name is practicelabs.com.
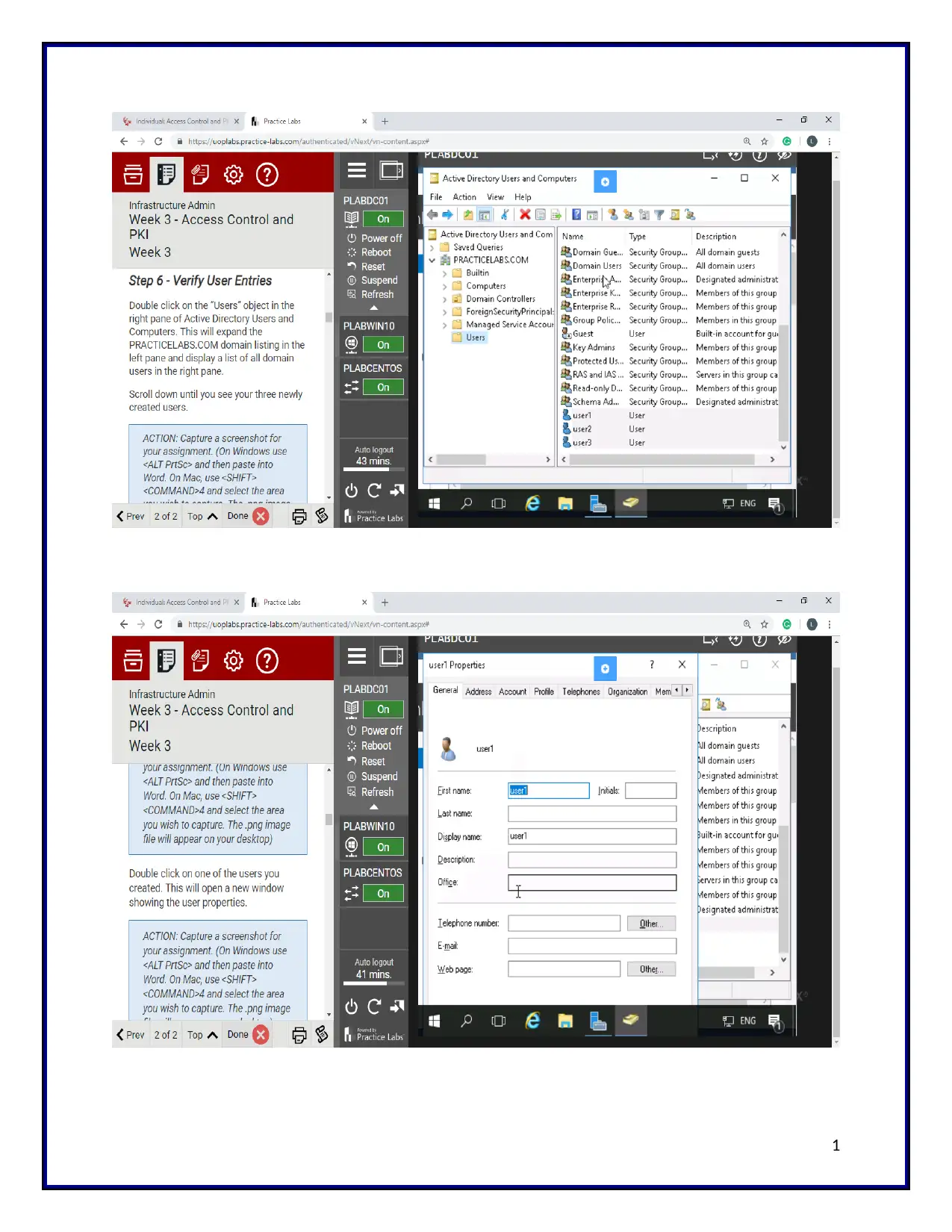
And the configuration is made for the ADDS server. In the configuration, first, the user
entities should be verified. The features are shown regarding the active directory users and
computers. Here totally three users are created. They are named as user1, user2, and user3. Then
the user record is analyzed. The user record contains more type of information regarding the
user. It includes many options such as name, description, office details, email, webpage,
organization, remote control, sessions, and environment. But the user record tabs seems to be
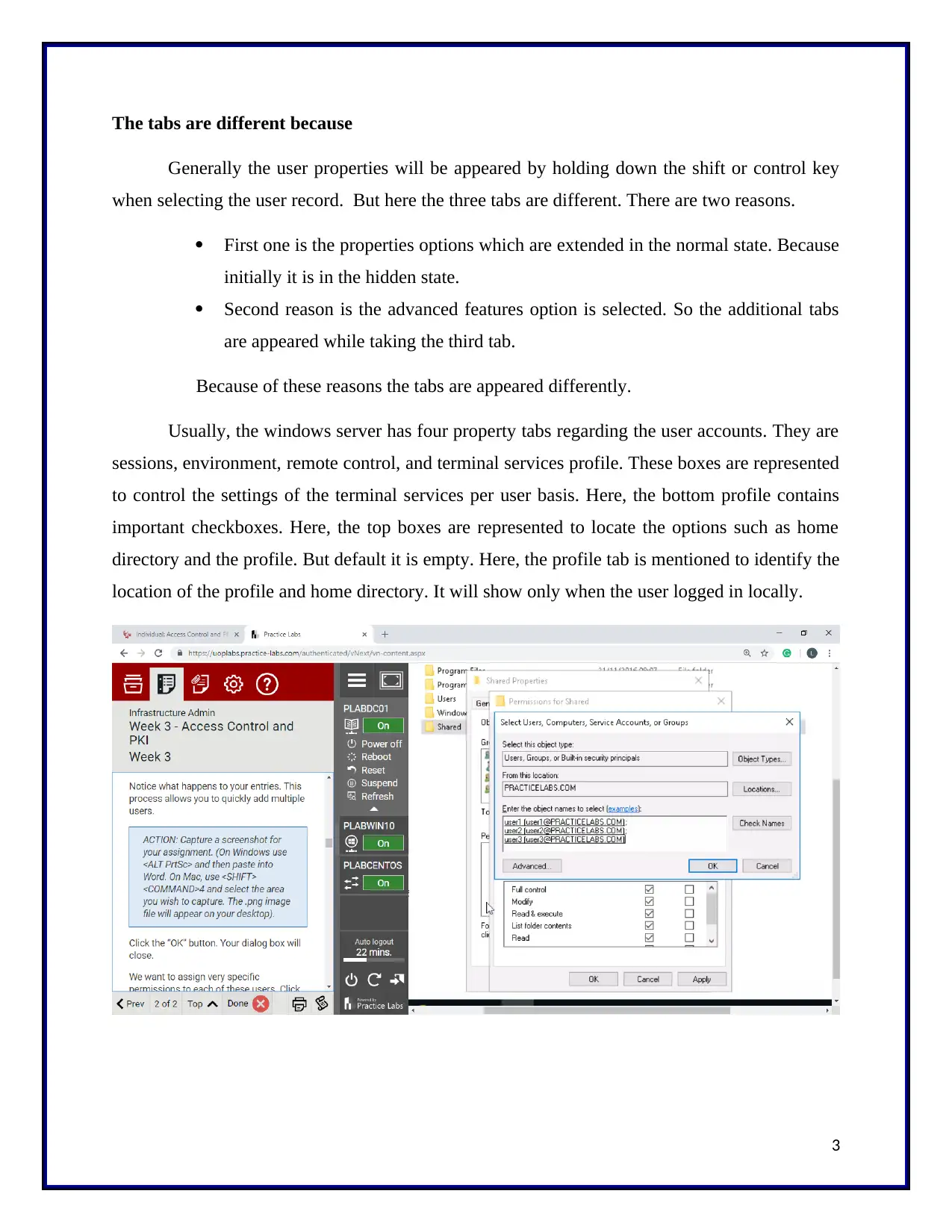
different here. Initially, the shared folder is created and the permissions for the shared folder is
analyzed. Then, the three users are added. And the permissions are checked for three users. And
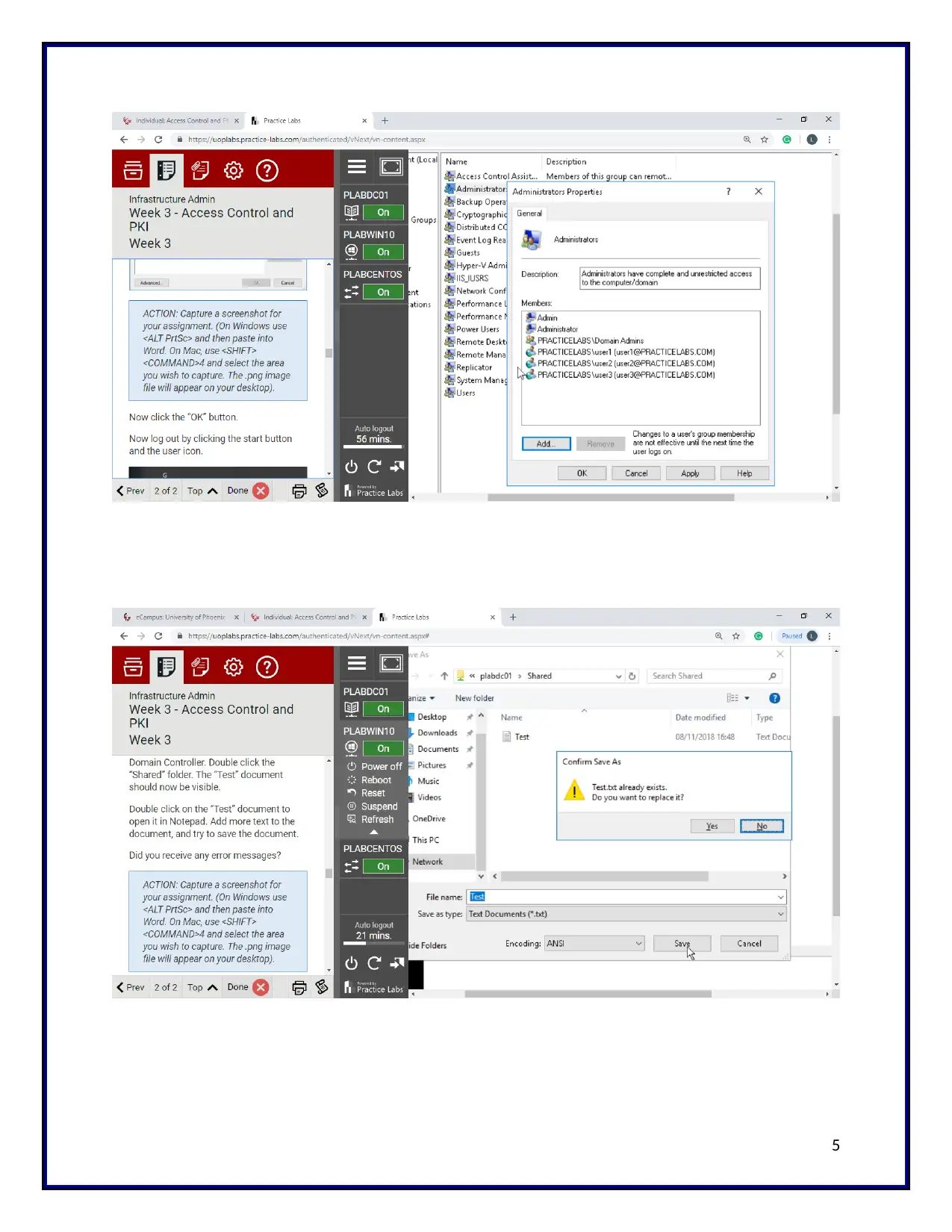
then the administrator properties are verified. The created users are presents under the
administrator members. These user information’s are stored in the text document named as a test.
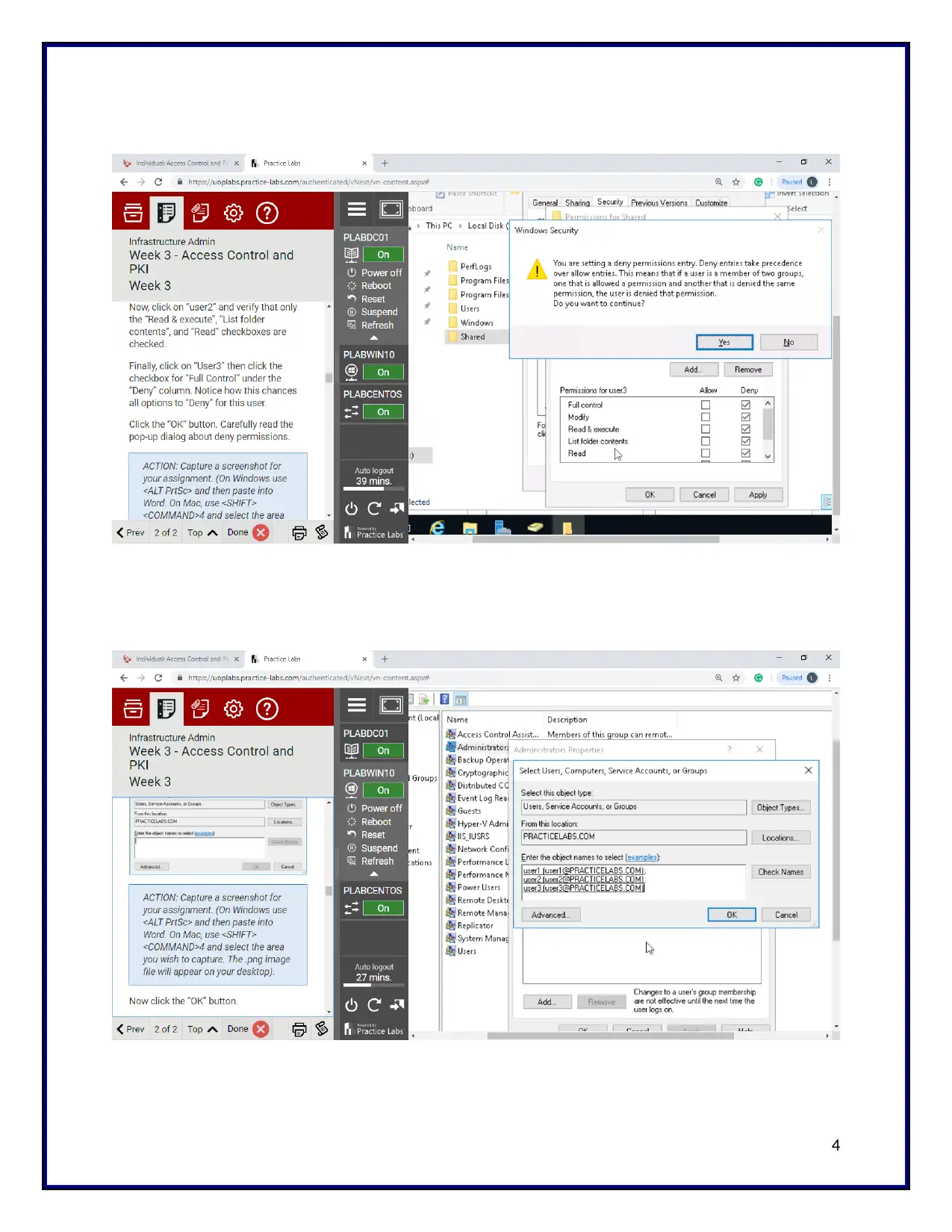
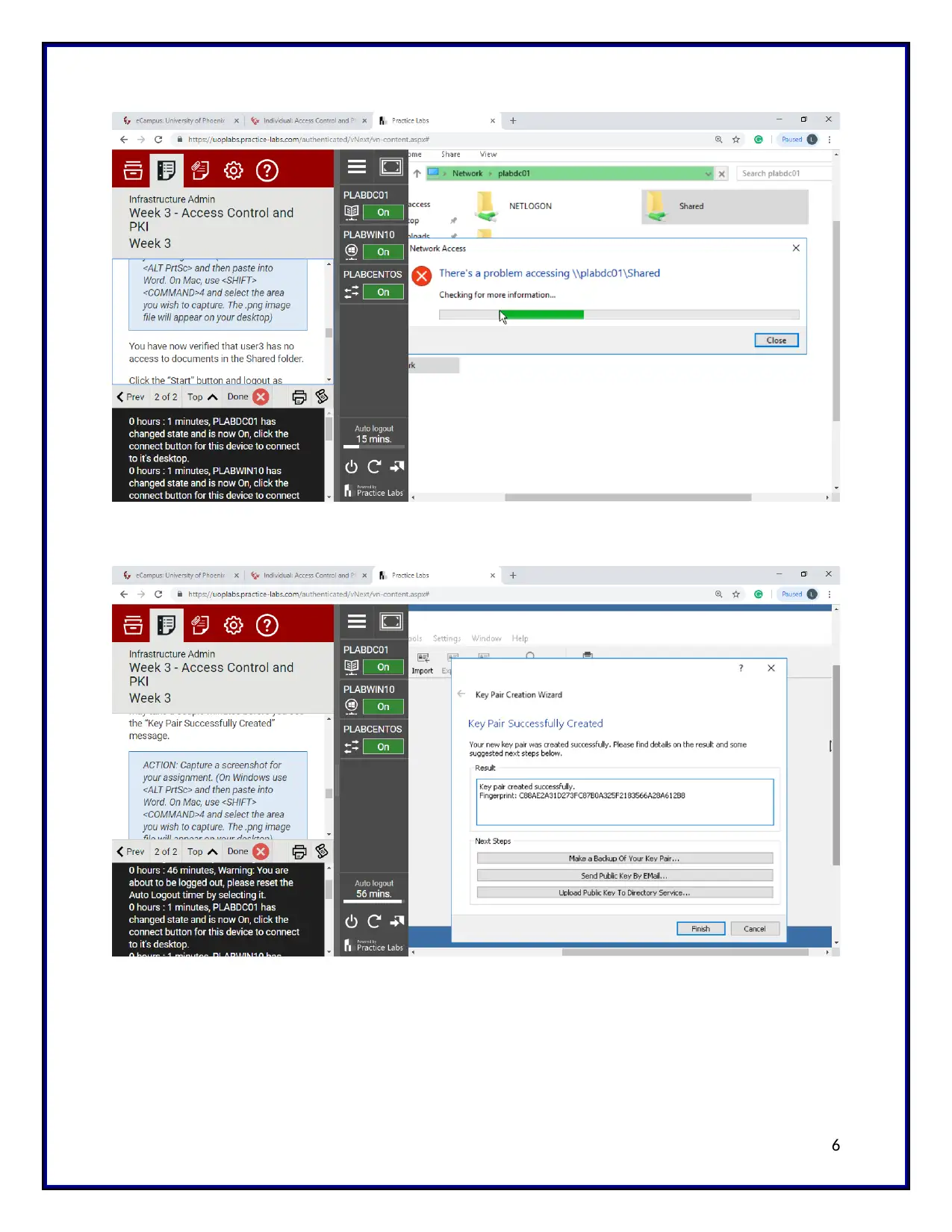
After that, the permission is checked for the shared folder. So the user3 has no access to the
documents which is in the shared folder. Finally, the key pair is created successfully. The id is
shown in the screenshot.
11
The keys may be stolen and these can be vulnerable to attack or it can be compromised. To
handle lots of keys, the IaaS needs to be scaled linearly. Only allow the authorized user to use the
keys in order to access the data. Define the policy, usage, protection, and access to maintain
governance.
Here, the practical work is made regarding the access control and public key
infrastructure. Access control is considered as an integral part of computer security. And the
public key infrastructure is used to distribute and identify the public encryption keys. By using
this public key infrastructure, the user and computer can exchange the data with security.
The windows server is used as the tool for access control and public key infrastructure.
The ADDS server is installed and configured in the windows server. The active directory domain
services are used for the authentication purpose. And the DNS server is installed for setting the
domain name. The domain name is practicelabs.com.
And the configuration is made for the ADDS server. In the configuration, first, the user
entities should be verified. The features are shown regarding the active directory users and
computers. Here totally three users are created. They are named as user1, user2, and user3. Then
the user record is analyzed. The user record contains more type of information regarding the
user. It includes many options such as name, description, office details, email, webpage,
organization, remote control, sessions, and environment. But the user record tabs seems to be
different here. Initially, the shared folder is created and the permissions for the shared folder is
analyzed. Then, the three users are added. And the permissions are checked for three users. And
then the administrator properties are verified. The created users are presents under the
administrator members. These user information’s are stored in the text document named as a test.
After that, the permission is checked for the shared folder. So the user3 has no access to the
documents which is in the shared folder. Finally, the key pair is created successfully. The id is
shown in the screenshot.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





