College Dormitory Access Control System Project Plan & Implementation
VerifiedAdded on 2023/06/10
|12
|2150
|469
Case Study
AI Summary
This case study presents a project plan for installing an access control system (ACS) in a college dormitory. The plan includes a project scope statement, five major tasks with subtasks (initialization, installation, configuration, and application), a Gantt chart illustrating the project timeline (June 25, 2018, to August 7, 2018), and a system diagram detailing the equipment and connections required. The ACS aims to enhance dormitory security by automatically unlocking doors via proximity sensors, integrating with existing security cameras, and closely monitoring individuals entering and exiting the premises, thereby ensuring the safety of students, staff, and university assets. The document also outlines the steps involved in testing, deployment, and notification to stakeholders.

Running head: ACCESS CONTROL SYSTEM
ACCESS CONTROL SYSTEM
Name of the Student
Name of the University
Course Code
ACCESS CONTROL SYSTEM
Name of the Student
Name of the University
Course Code
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1DESIGNING THE ACCESS CONTROL SYSTEM
Abstract:
In the United States, the month of August is the busiest time for the colleges or the
universities as this is the time for admission of new students in the colleges. Hence, the
parents are very much worried about their children about making them habituated with the
college-going atmosphere. Now, as their will be a stuffing of more than thousands of
students, teachers and parents in the campus of the Universities so it is needed to install a
very tight security system which will closely monitor activities of each person within the
campus and will report to the college security authority if anything suspicious is found. This
includes looking after the assets of the universities also. Parents also feel some hesitations
about sending their children to colleges alone as they are going to some different states. As
most of them come along with their children so a restroom is also provided for their safety
and rest purpose. Hence, to ensure complete safety of the students and parents a new type of
security system known as access control system is needed to be installed in the dormitories.
The objective of this project is to ensure that only the authorized individuals will have access
to the dormitories and all the visitors in that room will be properly protected.
Abstract:
In the United States, the month of August is the busiest time for the colleges or the
universities as this is the time for admission of new students in the colleges. Hence, the
parents are very much worried about their children about making them habituated with the
college-going atmosphere. Now, as their will be a stuffing of more than thousands of
students, teachers and parents in the campus of the Universities so it is needed to install a
very tight security system which will closely monitor activities of each person within the
campus and will report to the college security authority if anything suspicious is found. This
includes looking after the assets of the universities also. Parents also feel some hesitations
about sending their children to colleges alone as they are going to some different states. As
most of them come along with their children so a restroom is also provided for their safety
and rest purpose. Hence, to ensure complete safety of the students and parents a new type of
security system known as access control system is needed to be installed in the dormitories.
The objective of this project is to ensure that only the authorized individuals will have access
to the dormitories and all the visitors in that room will be properly protected.

2DESIGNING THE ACCESS CONTROL SYSTEM
Table of Contents
Introduction:...............................................................................................................................3
Project statement:.......................................................................................................................3
Tasks of the project:...................................................................................................................4
Table for Gantt chart:.................................................................................................................6
Gantt chart:.................................................................................................................................9
Conclusion:..............................................................................................................................10
Reference list:...........................................................................................................................11
Table of Contents
Introduction:...............................................................................................................................3
Project statement:.......................................................................................................................3
Tasks of the project:...................................................................................................................4
Table for Gantt chart:.................................................................................................................6
Gantt chart:.................................................................................................................................9
Conclusion:..............................................................................................................................10
Reference list:...........................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3DESIGNING THE ACCESS CONTROL SYSTEM
Introduction:
The beginning of the access control system is started in the year 1960’s for
eliminating the problems that are associated with the replacement of locks and cases of losing
the keys. All the systems will have an interface with the keyboard where a unique PIN
(Personal Identification Number) will be entered by each individual after inserting their
security card. Alternatively, the non-contact “proximity cards” can also be used which use the
RFID technology that was very popular during the period 1970 to 1980. One of the best
advantages of this technology of the access control system is that the access cards can be used
with the help of the card reader that is installed at the entrance of the dormitory (Sahani et al.,
2015). The electronic door installed at the entrance of the dormitory contains necessary
information about the Identification numbers of the persons who are allowed inside the
dormitory. Also, other functions like the entrance and exit times are recorded in the system so
that the duration each person stays inside the room can be known (Mei Yin et al., 2016). The
history of the presence of the individuals throughout the month or year can also be generated
through this access control software. Furthermore, the access control system can be integrated
with the surveillance cameras that can provide a live visual of the activities of the different
individuals within and just outside the dormitory and safety of persons and university
properties can be assured (Shebaro, Oluwatimi & Bertino, 2015). Hence, an ultimate level of
security can be provided to staffs, faculties and the students if the access control system is
installed in the college campus. The management, control and dynamic monitoring of the
access of the students and the faculties can be properly achieved by this access control
system.
Introduction:
The beginning of the access control system is started in the year 1960’s for
eliminating the problems that are associated with the replacement of locks and cases of losing
the keys. All the systems will have an interface with the keyboard where a unique PIN
(Personal Identification Number) will be entered by each individual after inserting their
security card. Alternatively, the non-contact “proximity cards” can also be used which use the
RFID technology that was very popular during the period 1970 to 1980. One of the best
advantages of this technology of the access control system is that the access cards can be used
with the help of the card reader that is installed at the entrance of the dormitory (Sahani et al.,
2015). The electronic door installed at the entrance of the dormitory contains necessary
information about the Identification numbers of the persons who are allowed inside the
dormitory. Also, other functions like the entrance and exit times are recorded in the system so
that the duration each person stays inside the room can be known (Mei Yin et al., 2016). The
history of the presence of the individuals throughout the month or year can also be generated
through this access control software. Furthermore, the access control system can be integrated
with the surveillance cameras that can provide a live visual of the activities of the different
individuals within and just outside the dormitory and safety of persons and university
properties can be assured (Shebaro, Oluwatimi & Bertino, 2015). Hence, an ultimate level of
security can be provided to staffs, faculties and the students if the access control system is
installed in the college campus. The management, control and dynamic monitoring of the
access of the students and the faculties can be properly achieved by this access control
system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4DESIGNING THE ACCESS CONTROL SYSTEM
Project statement:
The objective of this project is that the access control system will unlock the
electronic doors in the dormitory automatically when the presence of the individual is sensed
by the proximity sensor and the cameras installed with the system will closely monitor
individuals while inserting their cards in the door-lock and each of the cameras are designed
to rotate from face to face of the individuals. The cameras will also look after the persons
who are inside the room.
Tasks of the project:
The total project of installing the access control system can be subdivided in four
segments. Each of the segment have different parts also as given below.
1. Initialization of the ACS
i. Making a team for performing the project objective.
ii. Performing the survey of the college dormitory.
a. Finding the location of the control panel
b. Finding the location of the reader’s
c. Finding the location of the cameras
iii. ACS design
a. Computer drawing of the exterior of college dormitory
b. Computer drawing of the interior of the college dormitory
iv. Examining the present security system for integrating it with ACS
a. Examining the cameras to check damage during operation
b. Checking whether the old cameras are compatible with the ACS
v. Making the project proposal to the management
Project statement:
The objective of this project is that the access control system will unlock the
electronic doors in the dormitory automatically when the presence of the individual is sensed
by the proximity sensor and the cameras installed with the system will closely monitor
individuals while inserting their cards in the door-lock and each of the cameras are designed
to rotate from face to face of the individuals. The cameras will also look after the persons
who are inside the room.
Tasks of the project:
The total project of installing the access control system can be subdivided in four
segments. Each of the segment have different parts also as given below.
1. Initialization of the ACS
i. Making a team for performing the project objective.
ii. Performing the survey of the college dormitory.
a. Finding the location of the control panel
b. Finding the location of the reader’s
c. Finding the location of the cameras
iii. ACS design
a. Computer drawing of the exterior of college dormitory
b. Computer drawing of the interior of the college dormitory
iv. Examining the present security system for integrating it with ACS
a. Examining the cameras to check damage during operation
b. Checking whether the old cameras are compatible with the ACS
v. Making the project proposal to the management

5DESIGNING THE ACCESS CONTROL SYSTEM
a. Providing an estimate of the total cost of ACS software, hardware and
materials needed.
b. Estimating the cost of Labor.
c. Estimating the detail timeline of the total project
2. Installing the ACS
i. Installing the control panel
ii. Making the wire connections by R456 lines of communication
iii. Installing sensors on the doors (maintenance room, bedrooms, back, main and
Utility closets rooms)
iv. Installing the sensors on the exterior walls
v. Installing the sensors on the interior walls
vi. Restructuring the position of the cameras to face them on the faces of the
individuals.
3. Configuring the ACS
i. The software installed in the ACS system will be connected to the ACS server
in order to compare the entered credentials by the individuals with the
information present in the server (Li et al., 2016).
ii. For secure access of the student the student IDs must be sent to the ACS
server and during entering or existing from the dormitory room the student
must insert his/her proximity card in the system to gain access.
4. Applying or Executing the ACS
i. Period of transition: Performing enough test runs on the system before
deploying it for work.
ii. Mini-deployment: test run done by the staff member of the college to
understand the whole procedures.
a. Providing an estimate of the total cost of ACS software, hardware and
materials needed.
b. Estimating the cost of Labor.
c. Estimating the detail timeline of the total project
2. Installing the ACS
i. Installing the control panel
ii. Making the wire connections by R456 lines of communication
iii. Installing sensors on the doors (maintenance room, bedrooms, back, main and
Utility closets rooms)
iv. Installing the sensors on the exterior walls
v. Installing the sensors on the interior walls
vi. Restructuring the position of the cameras to face them on the faces of the
individuals.
3. Configuring the ACS
i. The software installed in the ACS system will be connected to the ACS server
in order to compare the entered credentials by the individuals with the
information present in the server (Li et al., 2016).
ii. For secure access of the student the student IDs must be sent to the ACS
server and during entering or existing from the dormitory room the student
must insert his/her proximity card in the system to gain access.
4. Applying or Executing the ACS
i. Period of transition: Performing enough test runs on the system before
deploying it for work.
ii. Mini-deployment: test run done by the staff member of the college to
understand the whole procedures.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6DESIGNING THE ACCESS CONTROL SYSTEM
iii. Notification: Notifying all the students, faculties and staffs in the college by
email about the new ACS system that will be effective from a particular date.
iv. Final deployment: ACS activation and the access cards distribution.
Table for Gantt chart:
Task Name Duratio
n
Start Finish Predecessors
Initialization
of the ACS
27 days Mon
6/25/18
Tue
7/31/18
Team
making
2 days Wed
6/27/18
Thu
6/28/18
Performing
the survey
5 days Fri
6/29/18
Thu
7/5/18
2
ACS
design
5 days Fri
7/6/18
Thu
7/12/18
3
Present
security
system
examination
6 days Fri
7/13/18
Fri
7/20/18
4
Creating
project
proposal
7 days Mon
7/23/18
Tue
7/31/18
5
Installing
the ACS
30 days Tue
7/10/18
Mon
8/20/18
6
Control 1 day Fri Fri
iii. Notification: Notifying all the students, faculties and staffs in the college by
email about the new ACS system that will be effective from a particular date.
iv. Final deployment: ACS activation and the access cards distribution.
Table for Gantt chart:
Task Name Duratio
n
Start Finish Predecessors
Initialization
of the ACS
27 days Mon
6/25/18
Tue
7/31/18
Team
making
2 days Wed
6/27/18
Thu
6/28/18
Performing
the survey
5 days Fri
6/29/18
Thu
7/5/18
2
ACS
design
5 days Fri
7/6/18
Thu
7/12/18
3
Present
security
system
examination
6 days Fri
7/13/18
Fri
7/20/18
4
Creating
project
proposal
7 days Mon
7/23/18
Tue
7/31/18
5
Installing
the ACS
30 days Tue
7/10/18
Mon
8/20/18
6
Control 1 day Fri Fri
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7DESIGNING THE ACCESS CONTROL SYSTEM
panel
installation
7/13/18 7/13/18
Making the
wire
connections
3 days Mon
7/16/18
Wed
7/18/18
8
Installing
sensors on
the doors
5 days Thu
7/19/18
Wed
7/25/18
9
Installing
the sensors
on the
exterior walls
5 days Thu
7/26/18
Wed
8/1/18
10
Installing
the sensors
on the
interior walls
6 days Thu
8/2/18
Thu
8/9/18
11
Restructuri
ng the
position of
the cameras
7 days Fri
8/10/18
Mon
8/20/18
12
Configuring
the ACS
11 days Mon
7/23/18
Mon
8/6/18
13
Connecting
ACS
software to
4 days Thu
7/26/18
Tue
7/31/18
panel
installation
7/13/18 7/13/18
Making the
wire
connections
3 days Mon
7/16/18
Wed
7/18/18
8
Installing
sensors on
the doors
5 days Thu
7/19/18
Wed
7/25/18
9
Installing
the sensors
on the
exterior walls
5 days Thu
7/26/18
Wed
8/1/18
10
Installing
the sensors
on the
interior walls
6 days Thu
8/2/18
Thu
8/9/18
11
Restructuri
ng the
position of
the cameras
7 days Fri
8/10/18
Mon
8/20/18
12
Configuring
the ACS
11 days Mon
7/23/18
Mon
8/6/18
13
Connecting
ACS
software to
4 days Thu
7/26/18
Tue
7/31/18
8DESIGNING THE ACCESS CONTROL SYSTEM
the ACS
server
Sending the
student IDs
in the ACS
server
4 days Wed
8/1/18
Mon
8/6/18
15
Applying or
Executing
the ACS
4 days Thu
8/2/18
Tue
8/7/18
16
Period of
transition
1 day Thu
8/2/18
Thu
8/2/18
Mini-
deployment
1 day Fri
8/3/18
Fri
8/3/18
18
Notificatio
n
1 day Mon
8/6/18
Mon
8/6/18
19
Final
deployment
1 day Tue
8/7/18
Tue
8/7/18
20
the ACS
server
Sending the
student IDs
in the ACS
server
4 days Wed
8/1/18
Mon
8/6/18
15
Applying or
Executing
the ACS
4 days Thu
8/2/18
Tue
8/7/18
16
Period of
transition
1 day Thu
8/2/18
Thu
8/2/18
Mini-
deployment
1 day Fri
8/3/18
Fri
8/3/18
18
Notificatio
n
1 day Mon
8/6/18
Mon
8/6/18
19
Final
deployment
1 day Tue
8/7/18
Tue
8/7/18
20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9DESIGNING THE ACCESS CONTROL SYSTEM
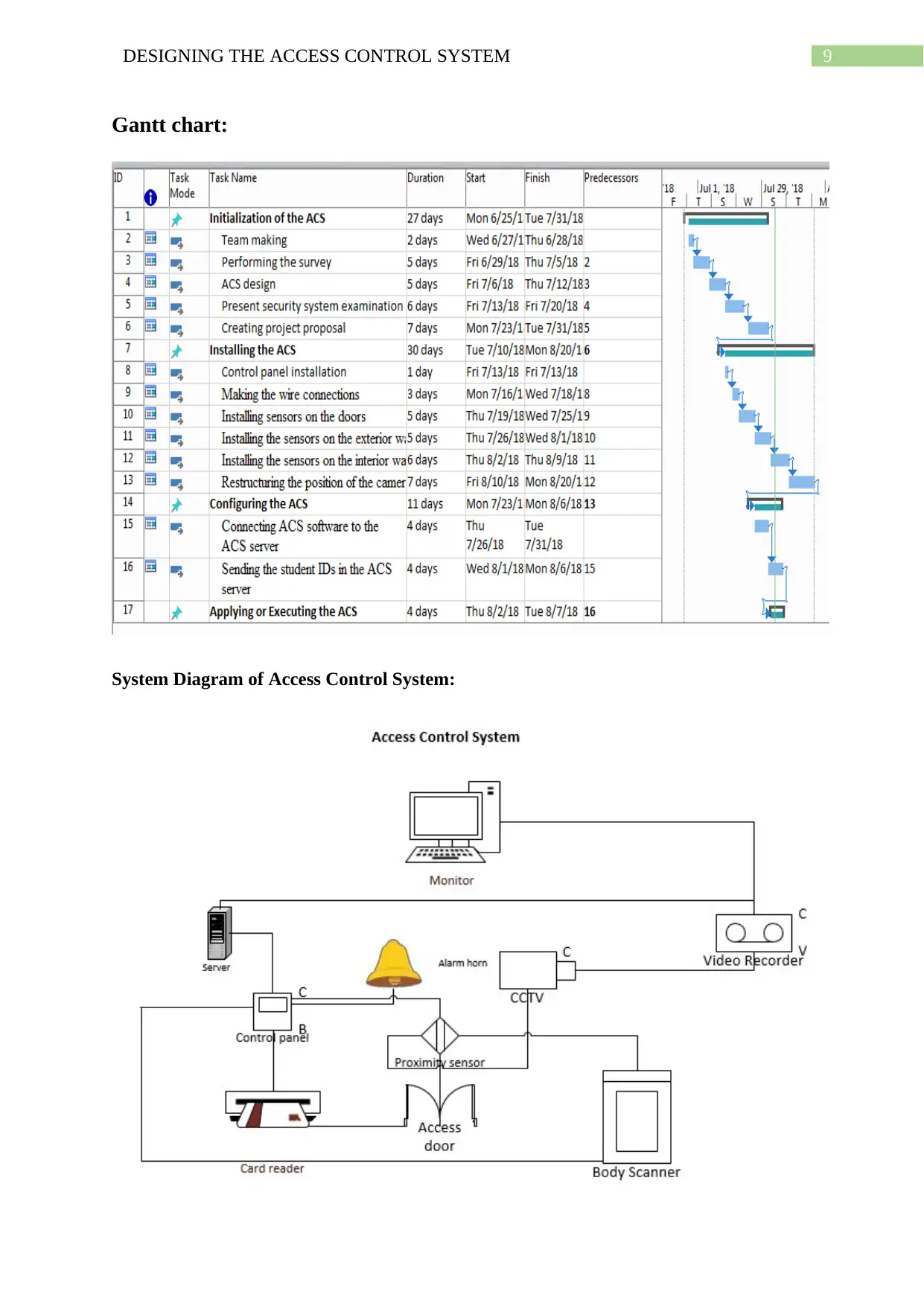
Gantt chart:
System Diagram of Access Control System:
Gantt chart:
System Diagram of Access Control System:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10DESIGNING THE ACCESS CONTROL SYSTEM
In the system diagram of the Access Control System, the operation of the system is
given below. The proximity sensor attached to the Access senses the position of the visitor
and sends a signal to the CCTV, the body scanner and the control panel. The CCTV camera
then faces towards the visitor and the video is sent to the video recorder which is connected
to the network server and the monitor. The security person observes the visitor and the video
is stored to the server. Furthermore, the control panel activates the card reader which scans
the visitor's unique personal card ID and sends a signal to the control panel if any
discrepancies are found (Peter et al., 2016). The control panel then activates the security
alarm. The same operation is performed by the body scanner and if any explosives or metal
weapons are found the scanner sends a signal to the control panel, and the control panel
activates the security alarm (Sowjanya & Nagaraju, 2016). The information acquired by the
control panel is also monitored and stored on the network server.
Conclusion:
Hence, the project plan of the ACS installation in the dormitory of the
College/University has been properly addressed in this case study. The parts and subparts of
the project are identified and explained and furthermore the duration of each part completion
is presented in the Gantt chart. Also, the project started on 25th June 2018 and ended on 7th
August 2018 and hence a total of 43 days will take for the completion. It may be noted that
the estimated project duration may vary for 3-4 extension or early completion. Hence, at the
start of August, the University will be able to use the Access Control System in the
dormitory, and the security of staff, students, faculties of the University will be enhanced.
In the system diagram of the Access Control System, the operation of the system is
given below. The proximity sensor attached to the Access senses the position of the visitor
and sends a signal to the CCTV, the body scanner and the control panel. The CCTV camera
then faces towards the visitor and the video is sent to the video recorder which is connected
to the network server and the monitor. The security person observes the visitor and the video
is stored to the server. Furthermore, the control panel activates the card reader which scans
the visitor's unique personal card ID and sends a signal to the control panel if any
discrepancies are found (Peter et al., 2016). The control panel then activates the security
alarm. The same operation is performed by the body scanner and if any explosives or metal
weapons are found the scanner sends a signal to the control panel, and the control panel
activates the security alarm (Sowjanya & Nagaraju, 2016). The information acquired by the
control panel is also monitored and stored on the network server.
Conclusion:
Hence, the project plan of the ACS installation in the dormitory of the
College/University has been properly addressed in this case study. The parts and subparts of
the project are identified and explained and furthermore the duration of each part completion
is presented in the Gantt chart. Also, the project started on 25th June 2018 and ended on 7th
August 2018 and hence a total of 43 days will take for the completion. It may be noted that
the estimated project duration may vary for 3-4 extension or early completion. Hence, at the
start of August, the University will be able to use the Access Control System in the
dormitory, and the security of staff, students, faculties of the University will be enhanced.

11DESIGNING THE ACCESS CONTROL SYSTEM
Reference list:
Li, W., Xue, K., Xue, Y., & Hong, J. (2016). TMACS: A robust and verifiable threshold
multi-authority access control system in public cloud storage. IEEE Transactions on
parallel and distributed systems, 27(5), 1484-1496.
Mei Yin, D. B., Kamal, M. I., Azmanuddin, N. S., Ali, S. H. S., Othman, A. T., & Chik, R. Z.
W. (2016, January). Electronic Door Access Control using MyAccess Two-Factor
Authentication Scheme featuring Near-Field Communication and Eigenface-based
Face Recognition using Principal Component Analysis. In Proceedings of the 10th
International Conference on Ubiquitous Information Management and
Communication (p. 1). ACM.
Peter, S., Li, J., Zhang, I., Ports, D. R., Woos, D., Krishnamurthy, A., ... & Roscoe, T. (2016).
Arrakis: The operating system is the control plane. ACM Transactions on Computer
Systems (TOCS), 33(4), 11.
Sahani, M., Nanda, C., Sahu, A. K., & Pattnaik, B. (2015, March). Web-based online
embedded door access control and home security system based on face recognition. In
Circuit, Power and Computing Technologies (ICCPCT), 2015 International
Conference on (pp. 1-6). IEEE.
Shebaro, B., Oluwatimi, O., & Bertino, E. (2015). Context-based access control systems for
mobile devices. IEEE Transactions on Dependable and Secure Computing, 12(2),
150-163.
Sowjanya, G., & Nagaraju, S. (2016, August). Design and implementation of door access
control and security system based on IOT. In Inventive Computation Technologies
(ICICT), International Conference on (Vol. 2, pp. 1-4). IEEE.
Reference list:
Li, W., Xue, K., Xue, Y., & Hong, J. (2016). TMACS: A robust and verifiable threshold
multi-authority access control system in public cloud storage. IEEE Transactions on
parallel and distributed systems, 27(5), 1484-1496.
Mei Yin, D. B., Kamal, M. I., Azmanuddin, N. S., Ali, S. H. S., Othman, A. T., & Chik, R. Z.
W. (2016, January). Electronic Door Access Control using MyAccess Two-Factor
Authentication Scheme featuring Near-Field Communication and Eigenface-based
Face Recognition using Principal Component Analysis. In Proceedings of the 10th
International Conference on Ubiquitous Information Management and
Communication (p. 1). ACM.
Peter, S., Li, J., Zhang, I., Ports, D. R., Woos, D., Krishnamurthy, A., ... & Roscoe, T. (2016).
Arrakis: The operating system is the control plane. ACM Transactions on Computer
Systems (TOCS), 33(4), 11.
Sahani, M., Nanda, C., Sahu, A. K., & Pattnaik, B. (2015, March). Web-based online
embedded door access control and home security system based on face recognition. In
Circuit, Power and Computing Technologies (ICCPCT), 2015 International
Conference on (pp. 1-6). IEEE.
Shebaro, B., Oluwatimi, O., & Bertino, E. (2015). Context-based access control systems for
mobile devices. IEEE Transactions on Dependable and Secure Computing, 12(2),
150-163.
Sowjanya, G., & Nagaraju, S. (2016, August). Design and implementation of door access
control and security system based on IOT. In Inventive Computation Technologies
(ICICT), International Conference on (Vol. 2, pp. 1-4). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





