Accounting Information Systems Database Report - Security and Ethics
VerifiedAdded on 2021/05/31
|5
|610
|92
Report
AI Summary
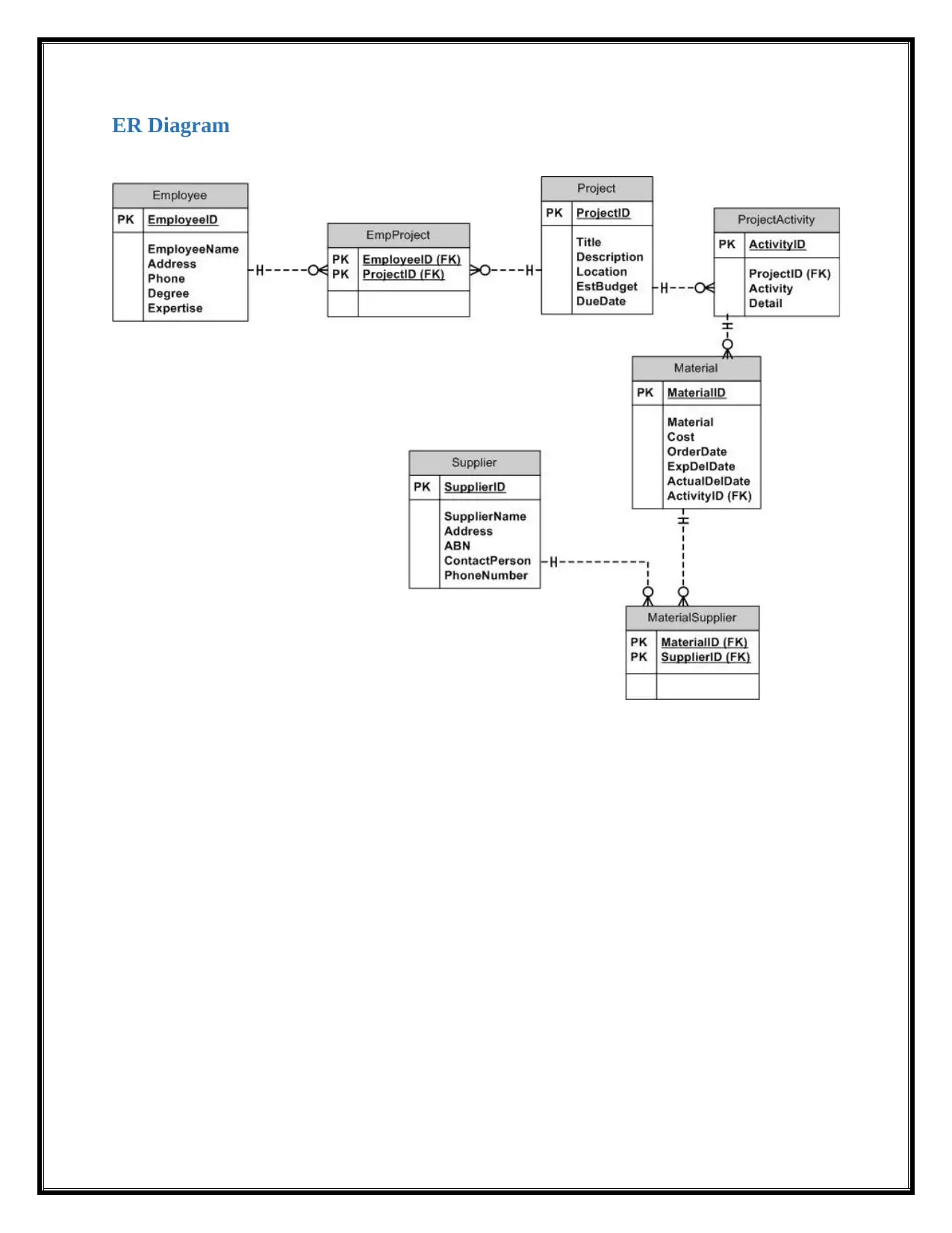
This report provides an overview of database management, focusing on the application of a Relational Database Management System (RDBMS) within the context of accounting information systems. It explores the importance of databases, the features of RDBMS, and the use of IT controls such as access control and data integrity to ensure data security and efficient management. The report also addresses ethical, privacy, and security issues, discussing measures such as restricting access, employing firewalls, and using encryption to protect sensitive data. It references sources on RDBMS and database concepts, highlighting the significance of database management in modern organizations. The report emphasizes the need for robust security and ethical practices to safeguard data and maintain data integrity.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)