University Accounting Information System: Ransomware Analysis Report
VerifiedAdded on 2020/04/07
|8
|1378
|51
Report
AI Summary
This report examines a ransomware attack on an accounting information system, focusing on a company's revenue cycle and the vulnerabilities that led to the attack. The report begins with an overview of the revenue cycle, detailing the company's processes from order placement to fulfillment. It then identifies internal control weaknesses, such as the lack of physical inventory counting and inadequate customer data management, and assesses their impact. The core of the report analyzes the ransomware attack, describing its method of operation, the ransom demands, and the vulnerabilities exploited. Recommendations are provided to mitigate future attacks, including the use of RFID tags for inventory tracking. The report concludes with a summary of the findings and references relevant academic sources.

Running head: ACCOUNTING INFORMATION SYSTEM
ACCOUNTING INFORMATION SYSTEM
Name of the Student
Name of the University
Author Note
ACCOUNTING INFORMATION SYSTEM
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2ACCOUNTING INFORMATION SYSTEM
Table of Contents
Introduction................................................................................................................................3
Overview of the Revenue Cycle................................................................................................3
Identification of threats..............................................................................................................4
Impact of the weakness..............................................................................................................5
Overview of the Ransom ware attack........................................................................................5
Recommendations......................................................................................................................5
Conclusion..................................................................................................................................5
References..................................................................................................................................7
Table of Contents
Introduction................................................................................................................................3
Overview of the Revenue Cycle................................................................................................3
Identification of threats..............................................................................................................4
Impact of the weakness..............................................................................................................5
Overview of the Ransom ware attack........................................................................................5
Recommendations......................................................................................................................5
Conclusion..................................................................................................................................5
References..................................................................................................................................7

3ACCOUNTING INFORMATION SYSTEM
Introduction
The main aim of the report is to focus on the aspect of ransomware attack which has
recently. The working of the threat of the ransom ware attack and with the attack the
recommendation for the company is put forward. The main emphasis of the report is a
detailed description of the revenue cycle that is mainly followed by the organizations with it
identification of the threads which is incorporated in the system which is followed by the
organization.
Overview of the Revenue Cycle
The main functionality of the company is the manufacture of motherboard, card and
microchips graphics repairs across the Australia in a central city and the departments are
located on the outskirts of the town (Wells &Bravender, 2016). Being a small enterprise
company the revenue system which is followed by the company is very much precise.
The main feature which is incorporated by the company involve payment through a
credit card with the use of the online website of the company. The order is invoiced and the
main order is send to the ware house in order to the packing of the goods. The service of the
customer is mainly done through the alphabetical manner. The source number is usually
twenty in number and the overall orders which are going out is mainly more than that. When
there is loss of any product the process which is incurred is that the item is logged into a log
book in order to get updated into the record.
Introduction
The main aim of the report is to focus on the aspect of ransomware attack which has
recently. The working of the threat of the ransom ware attack and with the attack the
recommendation for the company is put forward. The main emphasis of the report is a
detailed description of the revenue cycle that is mainly followed by the organizations with it
identification of the threads which is incorporated in the system which is followed by the
organization.
Overview of the Revenue Cycle
The main functionality of the company is the manufacture of motherboard, card and
microchips graphics repairs across the Australia in a central city and the departments are
located on the outskirts of the town (Wells &Bravender, 2016). Being a small enterprise
company the revenue system which is followed by the company is very much precise.
The main feature which is incorporated by the company involve payment through a
credit card with the use of the online website of the company. The order is invoiced and the
main order is send to the ware house in order to the packing of the goods. The service of the
customer is mainly done through the alphabetical manner. The source number is usually
twenty in number and the overall orders which are going out is mainly more than that. When
there is loss of any product the process which is incurred is that the item is logged into a log
book in order to get updated into the record.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
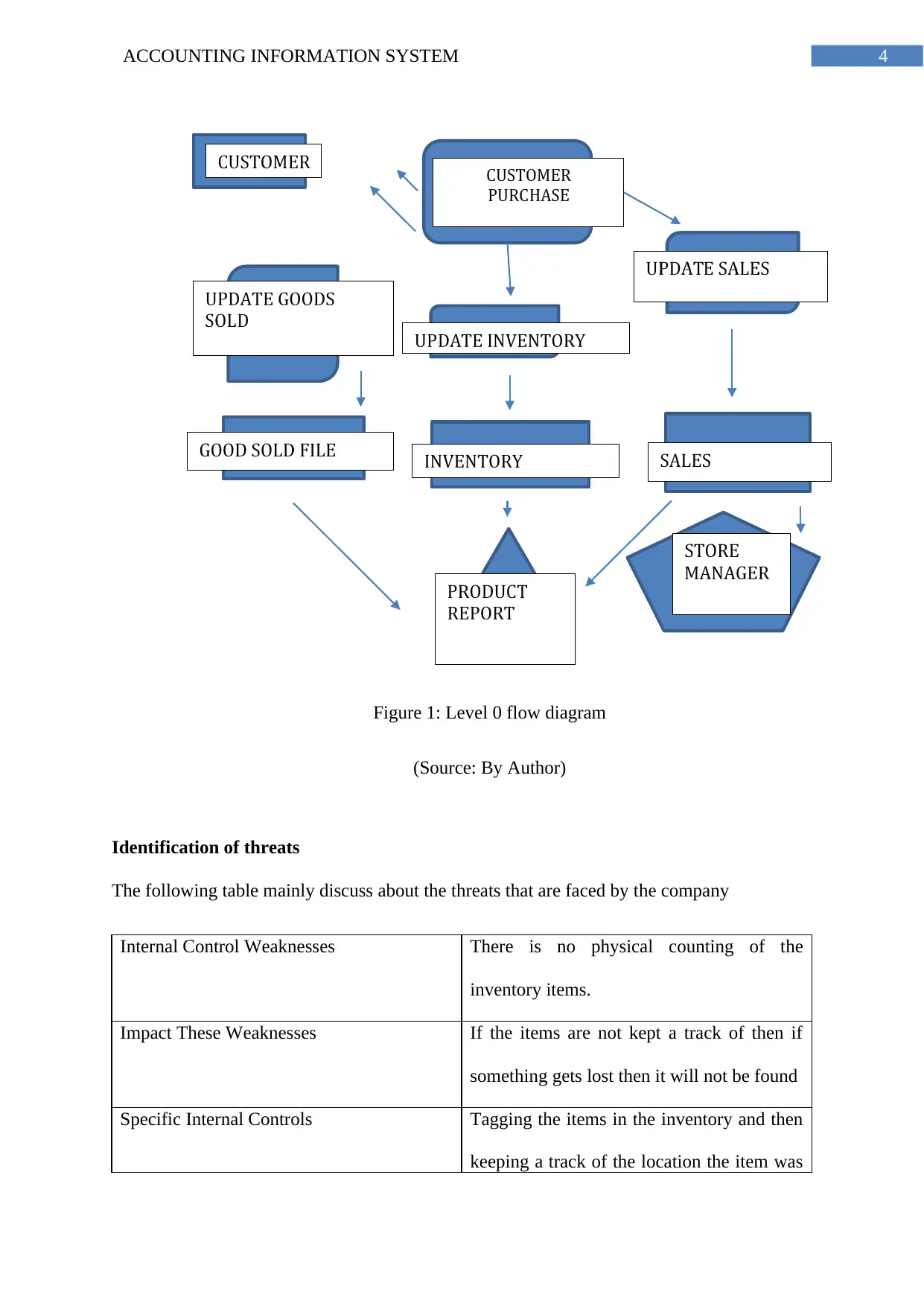
4ACCOUNTING INFORMATION SYSTEM
Figure 1: Level 0 flow diagram
(Source: By Author)
Identification of threats
The following table mainly discuss about the threats that are faced by the company
Internal Control Weaknesses There is no physical counting of the
inventory items.
Impact These Weaknesses If the items are not kept a track of then if
something gets lost then it will not be found
Specific Internal Controls Tagging the items in the inventory and then
keeping a track of the location the item was
Figure 1: Level 0 flow diagram
(Source: By Author)
Identification of threats
The following table mainly discuss about the threats that are faced by the company
Internal Control Weaknesses There is no physical counting of the
inventory items.
Impact These Weaknesses If the items are not kept a track of then if
something gets lost then it will not be found
Specific Internal Controls Tagging the items in the inventory and then
keeping a track of the location the item was
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5ACCOUNTING INFORMATION SYSTEM
last stored can help in the tracking of the
lost items. Also keeping an active
connective closed circuit camera would help
in looking after the warehouse floor (Sittig&
Singh, 2016).
Impact of the weakness
In any organization the database in order to keep the record of the customers plays a
vital role, the company lags behind in this field (Kharraz et al., 2015). In the process of not
keeping the record when the size of the item increase. On the other hand, the customers get a
free trial of 30days this puts high stress on the working team and also on the financial aspect
of the company. The use of dock for the outgoing and incoming delivery of the item can be
stated as a point of concern.
Overview of the Ransom ware attack
The main factor which caused the problem was a self-replicating software piece that
mainly took advantage of the different vulnerabilities with the main focus on older versions
of Microsoft windows. Finding an exposed target, it spreads from system to system. the
attack of the ransom ware resulted in demand of ransom which varied from an amount of
$US300 and it mainly accompanied increase in amount on an hourly basis. The security holes
where disclosed several weeks after by the shadow brokers, this group was a mysterious
group that mainly published different hacking tools which was used by the NSA (Collier,
2017). Right after the discloser the Microsoft company issued software’s which mainly
last stored can help in the tracking of the
lost items. Also keeping an active
connective closed circuit camera would help
in looking after the warehouse floor (Sittig&
Singh, 2016).
Impact of the weakness
In any organization the database in order to keep the record of the customers plays a
vital role, the company lags behind in this field (Kharraz et al., 2015). In the process of not
keeping the record when the size of the item increase. On the other hand, the customers get a
free trial of 30days this puts high stress on the working team and also on the financial aspect
of the company. The use of dock for the outgoing and incoming delivery of the item can be
stated as a point of concern.
Overview of the Ransom ware attack
The main factor which caused the problem was a self-replicating software piece that
mainly took advantage of the different vulnerabilities with the main focus on older versions
of Microsoft windows. Finding an exposed target, it spreads from system to system. the
attack of the ransom ware resulted in demand of ransom which varied from an amount of
$US300 and it mainly accompanied increase in amount on an hourly basis. The security holes
where disclosed several weeks after by the shadow brokers, this group was a mysterious
group that mainly published different hacking tools which was used by the NSA (Collier,
2017). Right after the discloser the Microsoft company issued software’s which mainly

6ACCOUNTING INFORMATION SYSTEM
included the patches which was made for the loop holes. On the other hand, it can also be
stated that many companies did bot install the patches or used older versions of the operating
system which did not support the patches which was oriented to protect the system
(Mohurle&Patil, 2017).
The most disruptive kind of attack was targeted towards the clinics and the hospital
which were in Britain. The case forced to turn away patients after the access of the computer
system was not allowed due to the attack. There were many other countries which were
involved in the attack for example Spain, Russia, Portugal. Cyber extortionist mainly ticked
the victims in order to open malicious attachment which had the malware in order to spam
emails that mainly appear to be contained in job offers, invoices, warning which are related to
security and other files of legitimate.
Recommendations
From the above discussion it can be stated that the most important aspect that is
related to the problem is that is the company Motherboard and Pvt Ltd faces problem with the
tracking of the goods in their warehouse. The items have been tagged and kept in the shelf.
The items should be tagged and number with the help of a radio frequency identification tags
(RFID). This would help in knowing the location of the product and if an unauthorized way
were taken up to take the item out of the warehouse then the tags would help in informing the
authorities about the item being taking out of the warehouse (Gupta &Tripathi, 2017).
Conclusion
It can be concluded from the report that the ransom ware attack on the organization
has faced many loss of data in aspect to the financial condition and related to the company.
included the patches which was made for the loop holes. On the other hand, it can also be
stated that many companies did bot install the patches or used older versions of the operating
system which did not support the patches which was oriented to protect the system
(Mohurle&Patil, 2017).
The most disruptive kind of attack was targeted towards the clinics and the hospital
which were in Britain. The case forced to turn away patients after the access of the computer
system was not allowed due to the attack. There were many other countries which were
involved in the attack for example Spain, Russia, Portugal. Cyber extortionist mainly ticked
the victims in order to open malicious attachment which had the malware in order to spam
emails that mainly appear to be contained in job offers, invoices, warning which are related to
security and other files of legitimate.
Recommendations
From the above discussion it can be stated that the most important aspect that is
related to the problem is that is the company Motherboard and Pvt Ltd faces problem with the
tracking of the goods in their warehouse. The items have been tagged and kept in the shelf.
The items should be tagged and number with the help of a radio frequency identification tags
(RFID). This would help in knowing the location of the product and if an unauthorized way
were taken up to take the item out of the warehouse then the tags would help in informing the
authorities about the item being taking out of the warehouse (Gupta &Tripathi, 2017).
Conclusion
It can be concluded from the report that the ransom ware attack on the organization
has faced many loss of data in aspect to the financial condition and related to the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7ACCOUNTING INFORMATION SYSTEM
The detailed study of the case study is mainly based on the drawback which is related to the
technical drawback related to the warehouse.
The detailed study of the case study is mainly based on the drawback which is related to the
technical drawback related to the warehouse.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8ACCOUNTING INFORMATION SYSTEM
References
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting
mobile ransomware. In International Workshop on Recent Advances in Intrusion
Detection (pp. 382-404). Springer International Publishing.
Everett, C. (2016). Ransomware: to pay or not to pay? Computer Fraud & Security, 2016(4),
8-12.
Faruki, P., Laxmi, V., Gaur, M. S., & Vinod, P. (2012, October). Mining control flow graph
as API call-grams to detect portable executable malware. In Proceedings of the Fifth
International Conference on Security of Information and Networks (pp. 130-137).
ACM.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
Techniques for Distributed Objects, Components, and Systems (pp. 212-221).
Springer, Cham.
O'Gorman, G., & McDonald, G. (2012). Ransomware: A growing menace. Symantec
Corporation.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware
growing challenge. International Journal of Advanced Research in Computer
Engineering & Technology (IJARCET) Volume, 5.
References
Andronio, N., Zanero, S., & Maggi, F. (2015, November). Heldroid: Dissecting and detecting
mobile ransomware. In International Workshop on Recent Advances in Intrusion
Detection (pp. 382-404). Springer International Publishing.
Everett, C. (2016). Ransomware: to pay or not to pay? Computer Fraud & Security, 2016(4),
8-12.
Faruki, P., Laxmi, V., Gaur, M. S., & Vinod, P. (2012, October). Mining control flow graph
as API call-grams to detect portable executable malware. In Proceedings of the Fifth
International Conference on Security of Information and Networks (pp. 130-137).
ACM.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
Techniques for Distributed Objects, Components, and Systems (pp. 212-221).
Springer, Cham.
O'Gorman, G., & McDonald, G. (2012). Ransomware: A growing menace. Symantec
Corporation.
Pathak, D. P., & Nanded, Y. M. (2016). A dangerous trend of cybercrime: ransomware
growing challenge. International Journal of Advanced Research in Computer
Engineering & Technology (IJARCET) Volume, 5.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





