ACC 203: Accounting Information Systems - Internal Audit and Controls
VerifiedAdded on 2022/09/02
|7
|974
|19
Homework Assignment
AI Summary
This assignment delves into the realm of accounting information systems, focusing on internal audit procedures within a manufacturing business context. The student's work addresses a scenario where a junior internal auditor identifies suspicious inventory purchases for a new subsidiary, prompting verification steps such as confirming the subsidiary's existence, assessing changes in standard procedures, and verifying vendors. The assignment also examines a case of potential financial controller fraud, analyzing implications and breaches of internal controls. Furthermore, it explores access control levels within the system for various user roles, including customers, and outlines the procedures for acquiring expensive assets, emphasizing the role of internal auditors in ensuring adherence to company policies and verification of financial and technical specifications. The assignment provides a comprehensive overview of the internal audit process in the context of accounting and financial management.

Running head: ACC 203 ACCOUNTING INFORMATION SYSTEMS
ACC 203 Accounting Information Systems
Name of the Student:
Name of the University:
Authors Note:
ACC 203 Accounting Information Systems
Name of the Student:
Name of the University:
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
TAX
Contents
Question 1:.......................................................................................................................................2
Part (a):........................................................................................................................................2
Part (b):........................................................................................................................................3
Part (c):........................................................................................................................................3
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................5
References:......................................................................................................................................6
TAX
Contents
Question 1:.......................................................................................................................................2
Part (a):........................................................................................................................................2
Part (b):........................................................................................................................................3
Part (c):........................................................................................................................................3
Answer 2:.........................................................................................................................................3
Answer 3:.........................................................................................................................................5
References:......................................................................................................................................6

2
TAX
Question 1:
Part (a):
The following checks should be undertaken in relation to the suspicious inventory purchases for
a new subsidiary to verify the transactions:
Verification about the existence of new subsidiary:
The approaching member of the A/P team has clearly stated that the inventory is purchased for a
new subsidiary which no one has heard before to be existed. Hence, firstly, it is important to
verify the existence of the new subsidiary. Discussion and meeting with the Board of Directors
of the company will help the auditor to authenticate the existence of the new subsidiary. In case
the new subsidiary mentioned in the transactions is in existence then the auditor would extend
his checks further to verify the transactions further.
Assess the reasons for the change in standard procedure of inventory receipts and issuance:
As the standard procedure is to receive the inventory in centralized warehouse and to issue these
to the production units the auditor should assess the reason for changes in the standard procedure
in case of the purchase of inventories for the new subsidiary (Cade and McVay, 2018).
Whether the inventory claims to be purchased has actually been received in the subsidiary:
The auditor must check whether the inventory purchased has actually been received by the
subsidiary.
The terms and conditions of purchase shall be verified:
TAX
Question 1:
Part (a):
The following checks should be undertaken in relation to the suspicious inventory purchases for
a new subsidiary to verify the transactions:
Verification about the existence of new subsidiary:
The approaching member of the A/P team has clearly stated that the inventory is purchased for a
new subsidiary which no one has heard before to be existed. Hence, firstly, it is important to
verify the existence of the new subsidiary. Discussion and meeting with the Board of Directors
of the company will help the auditor to authenticate the existence of the new subsidiary. In case
the new subsidiary mentioned in the transactions is in existence then the auditor would extend
his checks further to verify the transactions further.
Assess the reasons for the change in standard procedure of inventory receipts and issuance:
As the standard procedure is to receive the inventory in centralized warehouse and to issue these
to the production units the auditor should assess the reason for changes in the standard procedure
in case of the purchase of inventories for the new subsidiary (Cade and McVay, 2018).
Whether the inventory claims to be purchased has actually been received in the subsidiary:
The auditor must check whether the inventory purchased has actually been received by the
subsidiary.
The terms and conditions of purchase shall be verified:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
TAX
The auditor must check whether the standard procurement procedures have followed in case of
acquisition of inventories for the new subsidiary. If the answer is no then the reasons for not
following the same.
Verifying the vendors:
The vendors from which the purchases have been made must be verified to check their
credentials to deliver goods to the new subsidiary.
Part (b):
It seems that the financial controller has entered in fictitious transactions to make personal gain
at the cost of the company. He has breached his authority and violated the internal controls of the
company.
Part (c):
Implications are as following:
I. Fraud to the company.
II. Loss to the company.
III. Issues in management of the company.
Answer 2:
Area of the system
Level of
access
(1 mark
each)
Example
(3 marks for the first area, then 2 marks for
each successive area (2 - 7)
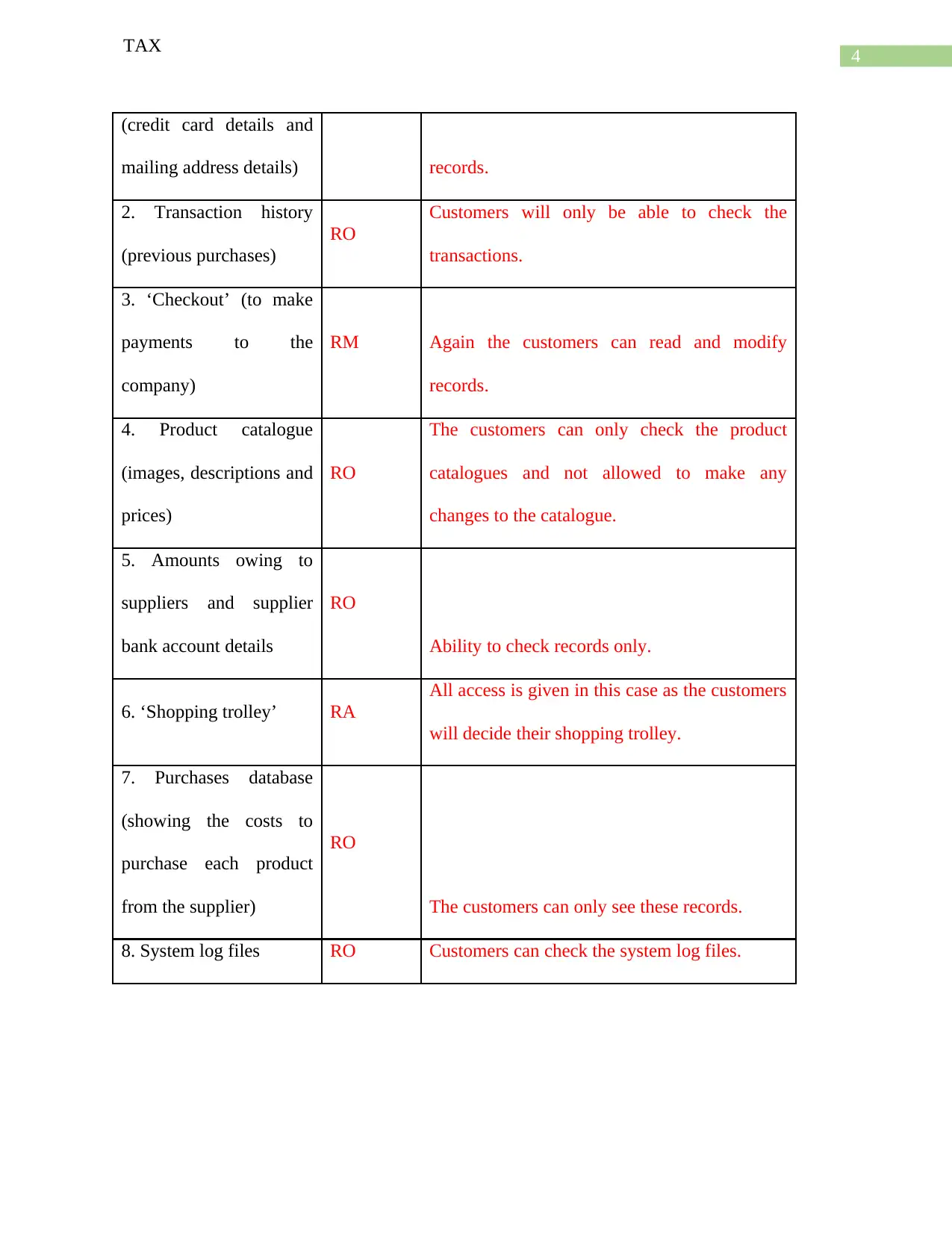
1. Customer details RM
Customer will be able to read and modify
TAX
The auditor must check whether the standard procurement procedures have followed in case of
acquisition of inventories for the new subsidiary. If the answer is no then the reasons for not
following the same.
Verifying the vendors:
The vendors from which the purchases have been made must be verified to check their
credentials to deliver goods to the new subsidiary.
Part (b):
It seems that the financial controller has entered in fictitious transactions to make personal gain
at the cost of the company. He has breached his authority and violated the internal controls of the
company.
Part (c):
Implications are as following:
I. Fraud to the company.
II. Loss to the company.
III. Issues in management of the company.
Answer 2:
Area of the system
Level of
access
(1 mark
each)
Example
(3 marks for the first area, then 2 marks for
each successive area (2 - 7)
1. Customer details RM
Customer will be able to read and modify
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
TAX
(credit card details and
mailing address details) records.
2. Transaction history
(previous purchases)
RO
Customers will only be able to check the
transactions.
3. ‘Checkout’ (to make
payments to the
company)
RM Again the customers can read and modify
records.
4. Product catalogue
(images, descriptions and
prices)
RO
The customers can only check the product
catalogues and not allowed to make any
changes to the catalogue.
5. Amounts owing to
suppliers and supplier
bank account details
RO
Ability to check records only.
6. ‘Shopping trolley’ RA
All access is given in this case as the customers
will decide their shopping trolley.
7. Purchases database
(showing the costs to
purchase each product
from the supplier)
RO
The customers can only see these records.
8. System log files RO Customers can check the system log files.
TAX
(credit card details and
mailing address details) records.
2. Transaction history
(previous purchases)
RO
Customers will only be able to check the
transactions.
3. ‘Checkout’ (to make
payments to the
company)
RM Again the customers can read and modify
records.
4. Product catalogue
(images, descriptions and
prices)
RO
The customers can only check the product
catalogues and not allowed to make any
changes to the catalogue.
5. Amounts owing to
suppliers and supplier
bank account details
RO
Ability to check records only.
6. ‘Shopping trolley’ RA
All access is given in this case as the customers
will decide their shopping trolley.
7. Purchases database
(showing the costs to
purchase each product
from the supplier)
RO
The customers can only see these records.
8. System log files RO Customers can check the system log files.

5
TAX
Answer 3:
Generally the procurement of an expensive item needs to go thorough number of checks and
verifications by the management and internal auditors. In case of an internal auditor he is
responsible to check whether the standard procedure of the company has been followed in case
of acquisition of the specific very expensive asset. The internal auditor should check and verify
the following documents in this regard.
I. Invitation of tender document to see whether the company invited tenders from
interested venders to supply the asset.
II. Check the quotations submitted by the vendors against the invitation of tender.
III. Verify the procedure followed by the management in awarding the contract of
supplying the asset to a particular vendor over and above others.
IV. Assess whether technical and financial specifications have been met by the vendor to
whom the contract of supplying the asset has been awarded.
V. Check the terms and conditions of payment.
Generally, the management awards such contract to the vendor who bids lowest amount for such
asset however, it is important for the management to keep in mind the quality of the asset hence,
if the asset offered by the vendors are all similar qualities then the vendor who has quoted the
lowest amount shall be awarded the contract to supply the asset. Thus, the internal auditor must
check and assess the entire procedure of acquiring of very expensive asset by the company
(Arena and Sarens, 2018).
TAX
Answer 3:
Generally the procurement of an expensive item needs to go thorough number of checks and
verifications by the management and internal auditors. In case of an internal auditor he is
responsible to check whether the standard procedure of the company has been followed in case
of acquisition of the specific very expensive asset. The internal auditor should check and verify
the following documents in this regard.
I. Invitation of tender document to see whether the company invited tenders from
interested venders to supply the asset.
II. Check the quotations submitted by the vendors against the invitation of tender.
III. Verify the procedure followed by the management in awarding the contract of
supplying the asset to a particular vendor over and above others.
IV. Assess whether technical and financial specifications have been met by the vendor to
whom the contract of supplying the asset has been awarded.
V. Check the terms and conditions of payment.
Generally, the management awards such contract to the vendor who bids lowest amount for such
asset however, it is important for the management to keep in mind the quality of the asset hence,
if the asset offered by the vendors are all similar qualities then the vendor who has quoted the
lowest amount shall be awarded the contract to supply the asset. Thus, the internal auditor must
check and assess the entire procedure of acquiring of very expensive asset by the company
(Arena and Sarens, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
TAX
References:
Arena, M. and Sarens, G., 2018. Internal Auditing: Creating Stepping Stones for the
Future. International Journal of Auditing, 21(7), pp.131-133.
Cade, N. and McVay, S., 2018. Understanding the Relations Between Internal Controls, Trust,
and Cooperation Within an Organization. SSRN Electronic Journal, 1(1), pp.12-27.
TAX
References:
Arena, M. and Sarens, G., 2018. Internal Auditing: Creating Stepping Stones for the
Future. International Journal of Auditing, 21(7), pp.131-133.
Cade, N. and McVay, S., 2018. Understanding the Relations Between Internal Controls, Trust,
and Cooperation Within an Organization. SSRN Electronic Journal, 1(1), pp.12-27.
1 out of 7
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

