Accounting Information Systems Report for ACC202, T1 2019, Coca-Cola
VerifiedAdded on 2022/11/24
|13
|2584
|467
Report
AI Summary
This report provides a comprehensive analysis of accounting information systems (AIS), focusing on key business processes within organizations and the importance of business ethics. The report uses Coca-Cola as a case study to illustrate the application of AIS, including its ERP system, sales, purchase, and inventory management. It also examines internal controls and the role of technology in AIS. Furthermore, the report delves into business ethics, using Facebook's data breach as a case study. It discusses the impact of the breach, the importance of trust, and the steps organizations should take to promote ethical practices and data security. The report also includes figures and diagrams to support the analysis, covering topics such as software, IT infrastructure, and the ethical implications of data breaches. The report highlights the significance of AIS in ensuring financial accuracy and ethical conduct within organizations.

Running head: ACCOUNTING INFORMATION SYSTEM
ACCOUNTING INFORMATION SYSTEM
Name of the Student
Name of the University
Author Note
ACCOUNTING INFORMATION SYSTEM
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
ACCOUNTING INFORMATION SYSTEM 1
Question 1:
Accounting information system:
For getting success in any of the industry, extensive research is needed for bringing
the suitable service. There are three types of bottling relationships in the Coca-Cola
Company. The partners of the coca cola company are having the authority to manufacture as
well as package the products.
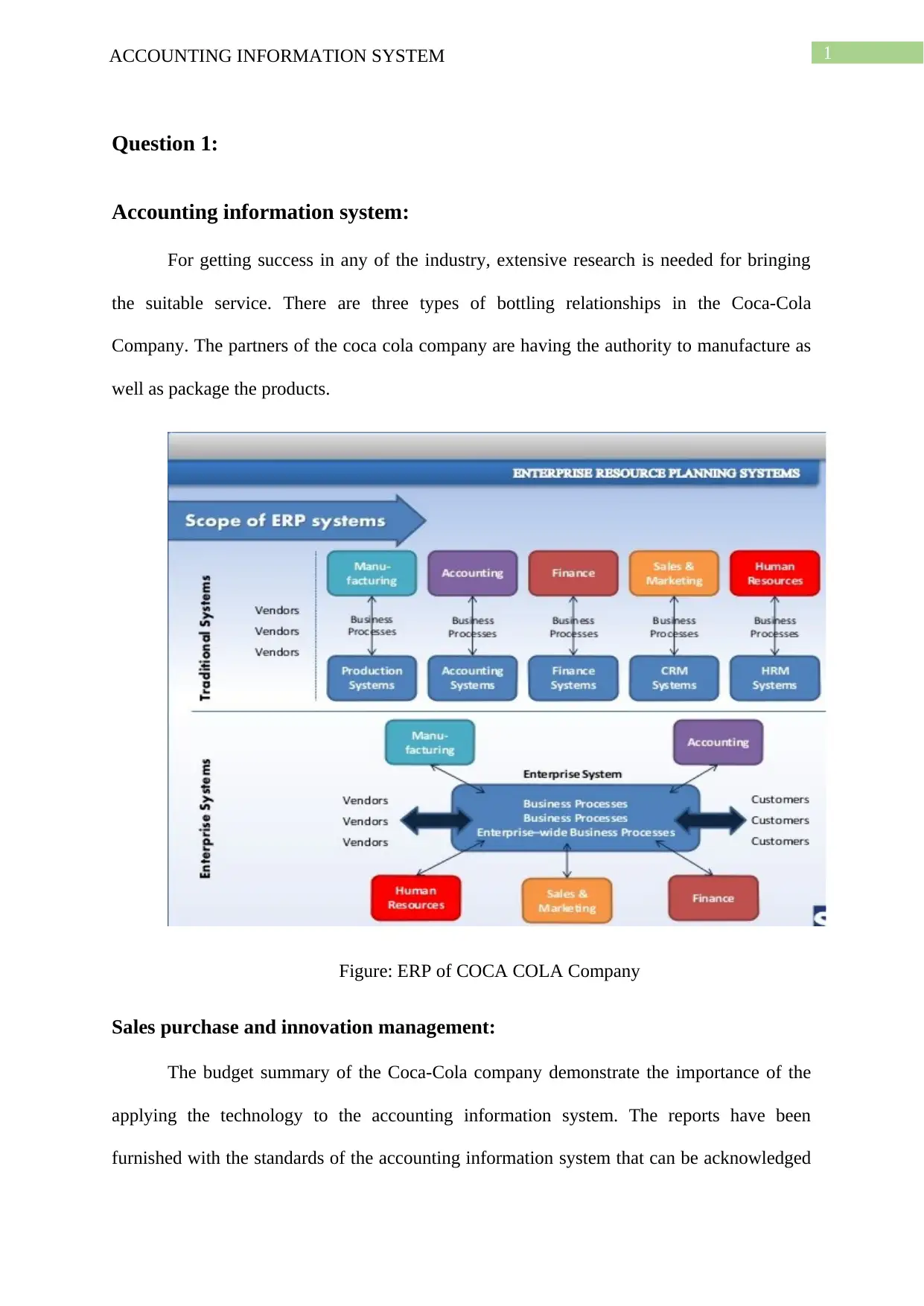
Figure: ERP of COCA COLA Company
Sales purchase and innovation management:
The budget summary of the Coca-Cola company demonstrate the importance of the
applying the technology to the accounting information system. The reports have been
furnished with the standards of the accounting information system that can be acknowledged
Question 1:
Accounting information system:
For getting success in any of the industry, extensive research is needed for bringing
the suitable service. There are three types of bottling relationships in the Coca-Cola
Company. The partners of the coca cola company are having the authority to manufacture as
well as package the products.
Figure: ERP of COCA COLA Company
Sales purchase and innovation management:
The budget summary of the Coca-Cola company demonstrate the importance of the
applying the technology to the accounting information system. The reports have been
furnished with the standards of the accounting information system that can be acknowledged

2ACCOUNTING INFORMATION SYSTEM
commonly in the United States. The rules that can be applied for AIS in the United States
provides the alternative to the elements for utilizing the cash related investments.
Figure: Company logo
As indicated by the comparable yearly report of the Coca Cola Company (2006), the
organization makes suspicions and decisions in how much reasonable incentive to pronounce.
For this situation, the intranet system can be especially useful since this might extension
accomplices with the administration just as the bottling accomplices to the workers making
the appraisal. The intranet framework as a component of the learning management is an
accounting manager for making the correct suppositions and decisions. Without the correct
information or consistence of certain AIS standards, the fiscal summary of the organization
may not in any way, shape or form be acknowledged as reasonable.
Extraordinarily the work of the trained accountants that is in depth with the AIS for
guaranteeing the elevated most amount of the perfections in one organisation's finance related
exchanges as well as the record-keeping, just as create the budgetary information that also
effectively accessible for the consumers who really need the accessibility to that, all of the
keeping information is flawless as well as secure (Alles et al., 2018). The normal people in
the AIS that are just the system users. The experts who are needed for utilizing an
organisation AIS incorporate accountants, business investigators, specialists, directors, CFOs,
commonly in the United States. The rules that can be applied for AIS in the United States
provides the alternative to the elements for utilizing the cash related investments.
Figure: Company logo
As indicated by the comparable yearly report of the Coca Cola Company (2006), the
organization makes suspicions and decisions in how much reasonable incentive to pronounce.
For this situation, the intranet system can be especially useful since this might extension
accomplices with the administration just as the bottling accomplices to the workers making
the appraisal. The intranet framework as a component of the learning management is an
accounting manager for making the correct suppositions and decisions. Without the correct
information or consistence of certain AIS standards, the fiscal summary of the organization
may not in any way, shape or form be acknowledged as reasonable.
Extraordinarily the work of the trained accountants that is in depth with the AIS for
guaranteeing the elevated most amount of the perfections in one organisation's finance related
exchanges as well as the record-keeping, just as create the budgetary information that also
effectively accessible for the consumers who really need the accessibility to that, all of the
keeping information is flawless as well as secure (Alles et al., 2018). The normal people in
the AIS that are just the system users. The experts who are needed for utilizing an
organisation AIS incorporate accountants, business investigators, specialists, directors, CFOs,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3ACCOUNTING INFORMATION SYSTEM
and evaluators. An AIS enables the various organisations which are situated within an
organisation to cooperate.
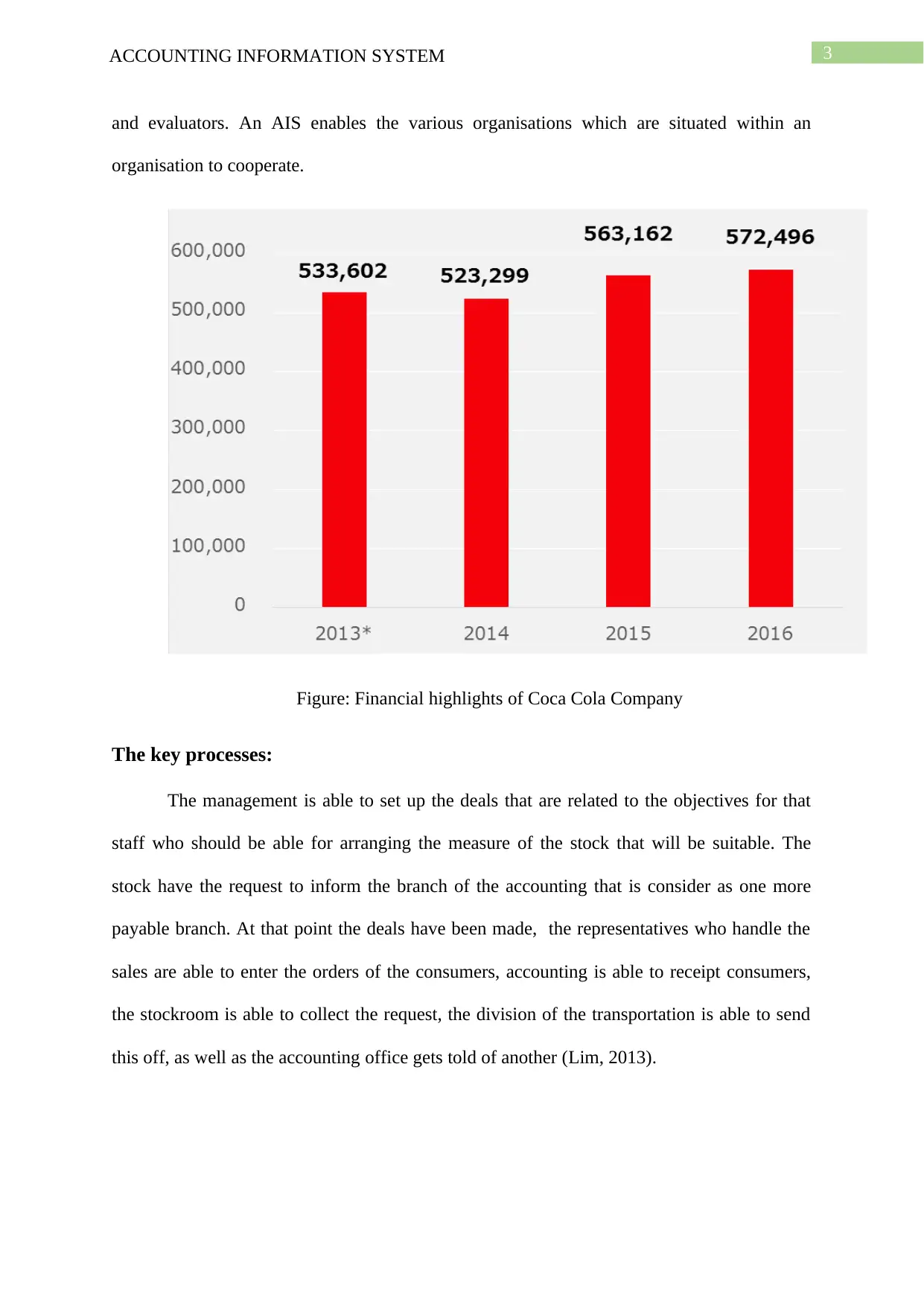
Figure: Financial highlights of Coca Cola Company
The key processes:
The management is able to set up the deals that are related to the objectives for that
staff who should be able for arranging the measure of the stock that will be suitable. The
stock have the request to inform the branch of the accounting that is consider as one more
payable branch. At that point the deals have been made, the representatives who handle the
sales are able to enter the orders of the consumers, accounting is able to receipt consumers,
the stockroom is able to collect the request, the division of the transportation is able to send
this off, as well as the accounting office gets told of another (Lim, 2013).
and evaluators. An AIS enables the various organisations which are situated within an
organisation to cooperate.
Figure: Financial highlights of Coca Cola Company
The key processes:
The management is able to set up the deals that are related to the objectives for that
staff who should be able for arranging the measure of the stock that will be suitable. The
stock have the request to inform the branch of the accounting that is consider as one more
payable branch. At that point the deals have been made, the representatives who handle the
sales are able to enter the orders of the consumers, accounting is able to receipt consumers,
the stockroom is able to collect the request, the division of the transportation is able to send
this off, as well as the accounting office gets told of another (Lim, 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ACCOUNTING INFORMATION SYSTEM
Software:
The software part of an AIS is the PC software’s that are utilized for storing, recover,
process, as well as investigates the organisation's finance related data. Before the existence
were PCs, the AIS was a manual and paper based framework, however at present, most of the
organisations are utilizing PC related programming like the premise of AIS. The companies
that are Private has been able to utilize the Sage 50 Accounting, but there have been others.
Small to the organisations can use the Business One of SAP. Moderate sized and enormous
organisations are able to utilize Microsoft's Dynamics GP, Sage Group's MAS 90 or MAS
200, Oracle's PeopleSoft or EPCOR Financial Management (Belfo and Trigo, 2013). The
Quality, security and the reliability are the major parts of compelling AIS programming.
Supervisors who are depending on the information that yields for settling on choices for the
organisation, as well as they required top notch data for settling on trustworthy choices.
IT Infrastructure:
The normal people in the AIS that are just the system users. The experts who are
needed for utilizing an organisation AIS incorporate accountants, business investigators,
specialists, directors, CFOs, and evaluators. An AIS has been enabled the various offices
which are situated inside an organisation to cooperate. The stock have the request informs the
accounting branch that is consider as one more payable branch. At the point the deals have
been made, the representatives who handle the sales are able to enter the orders of the
consumers, accounting is able to receipt consumers, the stockroom is able to collect the
request, the transportation division is able to send this off, as well as the accounting office
gets told of one more receivable (Lim, 2013). The client administration division should then
they are able for following shipments of the consumers as well as the framework is able to
make deals that will produce reports for the management. Administrators can also the observe
stock costs, the shipping costs, producing costs, etc.
Software:
The software part of an AIS is the PC software’s that are utilized for storing, recover,
process, as well as investigates the organisation's finance related data. Before the existence
were PCs, the AIS was a manual and paper based framework, however at present, most of the
organisations are utilizing PC related programming like the premise of AIS. The companies
that are Private has been able to utilize the Sage 50 Accounting, but there have been others.
Small to the organisations can use the Business One of SAP. Moderate sized and enormous
organisations are able to utilize Microsoft's Dynamics GP, Sage Group's MAS 90 or MAS
200, Oracle's PeopleSoft or EPCOR Financial Management (Belfo and Trigo, 2013). The
Quality, security and the reliability are the major parts of compelling AIS programming.
Supervisors who are depending on the information that yields for settling on choices for the
organisation, as well as they required top notch data for settling on trustworthy choices.
IT Infrastructure:
The normal people in the AIS that are just the system users. The experts who are
needed for utilizing an organisation AIS incorporate accountants, business investigators,
specialists, directors, CFOs, and evaluators. An AIS has been enabled the various offices
which are situated inside an organisation to cooperate. The stock have the request informs the
accounting branch that is consider as one more payable branch. At the point the deals have
been made, the representatives who handle the sales are able to enter the orders of the
consumers, accounting is able to receipt consumers, the stockroom is able to collect the
request, the transportation division is able to send this off, as well as the accounting office
gets told of one more receivable (Lim, 2013). The client administration division should then
they are able for following shipments of the consumers as well as the framework is able to
make deals that will produce reports for the management. Administrators can also the observe
stock costs, the shipping costs, producing costs, etc.

5ACCOUNTING INFORMATION SYSTEM
Internal Controls:
The controls that can be done internally of the AIS are the safety majors, this contains
for ensuring the delicate information. Those are able to be as basic as the passcodes or as the
unpredictable like the biometric distinguishing proof (Ismail and King, 2014). The AIS must
be having inner controls for ensuring against the pc that is infected for get to as well as for
constraining access for the approved consumers, that incorporates a few consumers who were
inside the organisation. This would also anticipate unapproved accounts for accessing by the
people who have been permitted to get to just the chosen portions that are belonged to the
system.
Question 2:
Business ethics:
It is ensured by the Business ethics that a fundamental dimension that is specific for
the trust exists among customers as well as several types of members of the market of the
organisations. For example, one administrator of the portfolio have to provide a same thought
for the arrangement of the relatives as well as the individual experts of the finance. These
sorts of practices ensures that the social network will get a treatment that is reasonable.
Since that the timespan, the idea of ethics of the business has been advanced. The ethics of
the Business goes past only one of the code of the ethical of good as well as bad; it projects
for accommodating that the organisations have to do the legitimately like opposed for
keeping up an upper hand on various organisation. It is shown by the organisation, the ethics
of the business in a few different ways.
Internal Controls:
The controls that can be done internally of the AIS are the safety majors, this contains
for ensuring the delicate information. Those are able to be as basic as the passcodes or as the
unpredictable like the biometric distinguishing proof (Ismail and King, 2014). The AIS must
be having inner controls for ensuring against the pc that is infected for get to as well as for
constraining access for the approved consumers, that incorporates a few consumers who were
inside the organisation. This would also anticipate unapproved accounts for accessing by the
people who have been permitted to get to just the chosen portions that are belonged to the
system.
Question 2:
Business ethics:
It is ensured by the Business ethics that a fundamental dimension that is specific for
the trust exists among customers as well as several types of members of the market of the
organisations. For example, one administrator of the portfolio have to provide a same thought
for the arrangement of the relatives as well as the individual experts of the finance. These
sorts of practices ensures that the social network will get a treatment that is reasonable.
Since that the timespan, the idea of ethics of the business has been advanced. The ethics of
the Business goes past only one of the code of the ethical of good as well as bad; it projects
for accommodating that the organisations have to do the legitimately like opposed for
keeping up an upper hand on various organisation. It is shown by the organisation, the ethics
of the business in a few different ways.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ACCOUNTING INFORMATION SYSTEM
Facebook data breach incident:
In any relationship, most of the analysts should concur that the trust is at the bleeding
edge of the importance. It is the basic. At the time someone lost the trust shall be so many
people who may infer that, into the contrast for the money related transaction, this may never
be recovered.
Figure: Facebook data breach
Among all the patients as well as the therapeutic experts, this have been an
understanding that is composed where quiet information may stay privately as well as
undisclosed for the other people.
Let Imagining one scenario where the relationship that is between one of the
association as well as 50 million consumers. The outcomes are able to be disastrous. For
looking after trust, the organisations are regularly putting the resources into the controls of
the security with the end goal to relieve the information that is potential that was for a breach
of data; what happens and what was time something escapes everyone's notice? On
Facebook data breach incident:
In any relationship, most of the analysts should concur that the trust is at the bleeding
edge of the importance. It is the basic. At the time someone lost the trust shall be so many
people who may infer that, into the contrast for the money related transaction, this may never
be recovered.
Figure: Facebook data breach
Among all the patients as well as the therapeutic experts, this have been an
understanding that is composed where quiet information may stay privately as well as
undisclosed for the other people.
Let Imagining one scenario where the relationship that is between one of the
association as well as 50 million consumers. The outcomes are able to be disastrous. For
looking after trust, the organisations are regularly putting the resources into the controls of
the security with the end goal to relieve the information that is potential that was for a breach
of data; what happens and what was time something escapes everyone's notice? On
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ACCOUNTING INFORMATION SYSTEM
September 25, 2018, internet based life goliath, Facebook, advised consumers of an
enormous information break influencing more than 50 million people.
How the incident happened:
The incident that is including the inadequacies in the "View As" feature of the
Facebook. The Facebook utilized regularly the component enables consumers for seeing how
the profiles of the users of Facebook appear for the different consumers. It is figured out that
how the usefulness can be utilize for taking get to the tokens that are from the accounts of the
consumers whose accounts were looked at by utilizing the all of the component. From there,
the assault daisy-anchored beginning with one companion of the Facebook of the consumers
then onto the next accomplishing for accessing tokens for en routing.
Figure: Facebook logo
Luckily, at the time it is found, the Facebook have rapidly acted for fixing the helplessness.
Shockingly, presently this was gone the point to no return. In an organisation as huge like the
Facebook, the damage had already been done.
September 25, 2018, internet based life goliath, Facebook, advised consumers of an
enormous information break influencing more than 50 million people.
How the incident happened:
The incident that is including the inadequacies in the "View As" feature of the
Facebook. The Facebook utilized regularly the component enables consumers for seeing how
the profiles of the users of Facebook appear for the different consumers. It is figured out that
how the usefulness can be utilize for taking get to the tokens that are from the accounts of the
consumers whose accounts were looked at by utilizing the all of the component. From there,
the assault daisy-anchored beginning with one companion of the Facebook of the consumers
then onto the next accomplishing for accessing tokens for en routing.
Figure: Facebook logo
Luckily, at the time it is found, the Facebook have rapidly acted for fixing the helplessness.
Shockingly, presently this was gone the point to no return. In an organisation as huge like the
Facebook, the damage had already been done.
8ACCOUNTING INFORMATION SYSTEM
Still the Facebook isn't sure that the sort of the consumer data that has been undermined; in
any case, the company are sure that the hacking was influenced by the people who utilizes the
Facebook for signing into several accounts, for example, Instagram, Tinder and other third
applications that using the login system.
Facebook Inc. was fined a potential of 1.63 billion dollars as the amount of money as
the EU's security guard explores whether the community of the informal was damaged the
European's Union protection laws, GPDR.
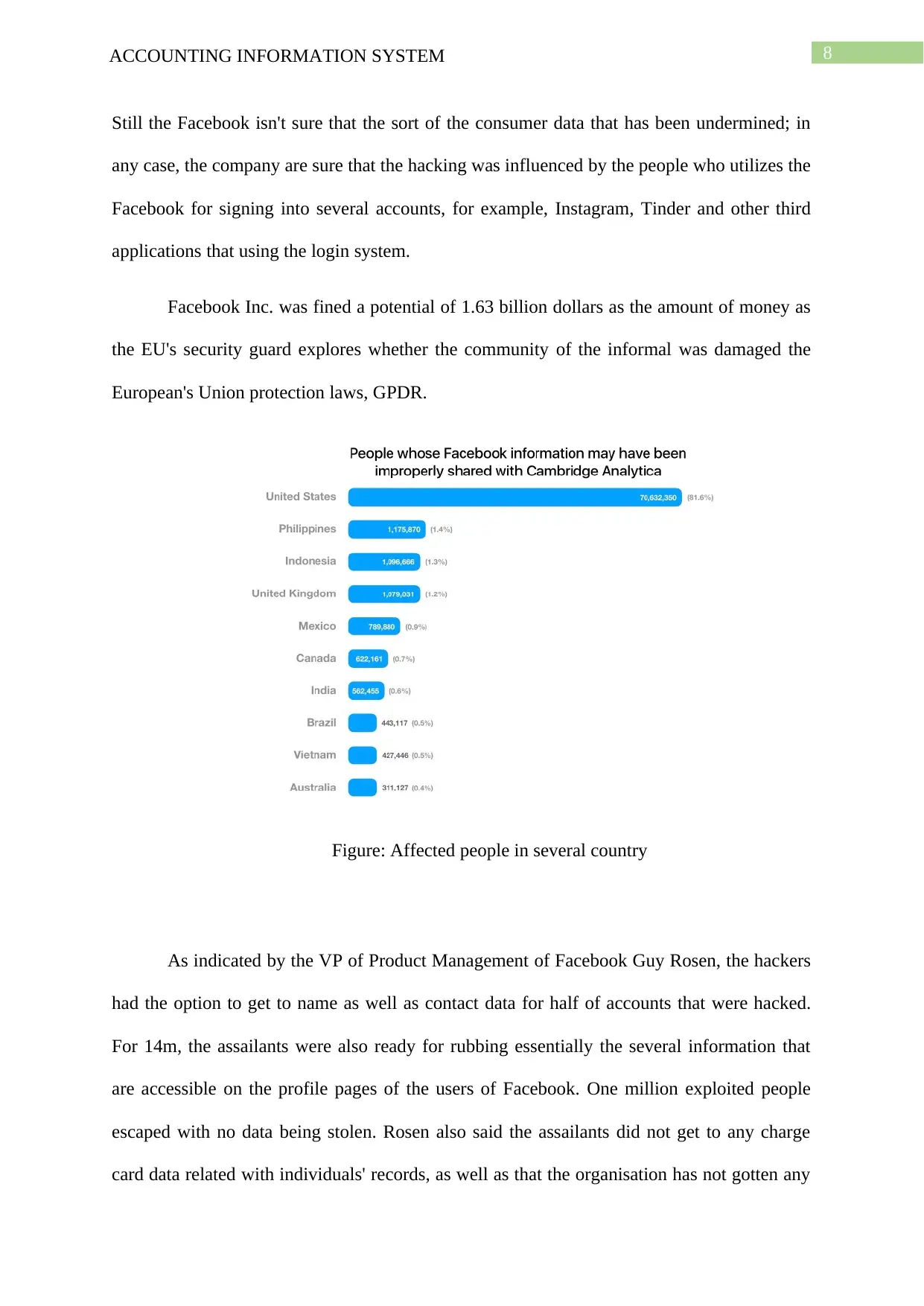
Figure: Affected people in several country
As indicated by the VP of Product Management of Facebook Guy Rosen, the hackers
had the option to get to name as well as contact data for half of accounts that were hacked.
For 14m, the assailants were also ready for rubbing essentially the several information that
are accessible on the profile pages of the users of Facebook. One million exploited people
escaped with no data being stolen. Rosen also said the assailants did not get to any charge
card data related with individuals' records, as well as that the organisation has not gotten any
Still the Facebook isn't sure that the sort of the consumer data that has been undermined; in
any case, the company are sure that the hacking was influenced by the people who utilizes the
Facebook for signing into several accounts, for example, Instagram, Tinder and other third
applications that using the login system.
Facebook Inc. was fined a potential of 1.63 billion dollars as the amount of money as
the EU's security guard explores whether the community of the informal was damaged the
European's Union protection laws, GPDR.
Figure: Affected people in several country
As indicated by the VP of Product Management of Facebook Guy Rosen, the hackers
had the option to get to name as well as contact data for half of accounts that were hacked.
For 14m, the assailants were also ready for rubbing essentially the several information that
are accessible on the profile pages of the users of Facebook. One million exploited people
escaped with no data being stolen. Rosen also said the assailants did not get to any charge
card data related with individuals' records, as well as that the organisation has not gotten any
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ACCOUNTING INFORMATION SYSTEM
reports that are related to the stolen data being accessible on the dull web – bits of the web
requiring exceptional programming for reaching.
The social networking organisation likewise found no proof which was utilized by the
hackers, the tokens that were stolen for getting to any third party applications, includes that
Facebook's utilization single-sign-in to sign in. this also did not effect the consumers on other
properties that are related to the Facebook, for example, Messenger, Instagram, WhatsApp, or
Oculus.
The critical programmers have started by utilizing one of the progression that is
related to the seed the Facebook accounts as well as by assaulting all of the accounts of
companions, at that point companions of companions, etc. down that line, in the end storing
up a gathering of 400,000 traded off related accounts (Das et al., 2014). Utilizing one of the
portion of these accounts, it has been figured out how it can be taken for getting to the tokens
that was for extra 30m before the attackers were halted.
Rosen also said that Facebook first saw the spike in unordinary action on 14
September. By the 25th, this had recognized that movement as an assault (Kuyumdzhiev,
2014). After two days, Facebook had stopped the gap and reset consumers' tokens, keeping
assailants from getting to any additional data. By at that point, the disaster had just been
finished.
Upon solicitation from the FBI, Facebook declined for providing any data with
respect to whom may be behind the assault, or the consumers in explicit locales were focused
on. On the off chance that any of the unfortunate casualties live in Europe, this might trigger
noteworthy punishments under the EU's General Data Protection Regulation, Pravin Kothari,
and CEO of security firm Cipher Cloud. "Not knowing the majority of the insights
reports that are related to the stolen data being accessible on the dull web – bits of the web
requiring exceptional programming for reaching.
The social networking organisation likewise found no proof which was utilized by the
hackers, the tokens that were stolen for getting to any third party applications, includes that
Facebook's utilization single-sign-in to sign in. this also did not effect the consumers on other
properties that are related to the Facebook, for example, Messenger, Instagram, WhatsApp, or
Oculus.
The critical programmers have started by utilizing one of the progression that is
related to the seed the Facebook accounts as well as by assaulting all of the accounts of
companions, at that point companions of companions, etc. down that line, in the end storing
up a gathering of 400,000 traded off related accounts (Das et al., 2014). Utilizing one of the
portion of these accounts, it has been figured out how it can be taken for getting to the tokens
that was for extra 30m before the attackers were halted.
Rosen also said that Facebook first saw the spike in unordinary action on 14
September. By the 25th, this had recognized that movement as an assault (Kuyumdzhiev,
2014). After two days, Facebook had stopped the gap and reset consumers' tokens, keeping
assailants from getting to any additional data. By at that point, the disaster had just been
finished.
Upon solicitation from the FBI, Facebook declined for providing any data with
respect to whom may be behind the assault, or the consumers in explicit locales were focused
on. On the off chance that any of the unfortunate casualties live in Europe, this might trigger
noteworthy punishments under the EU's General Data Protection Regulation, Pravin Kothari,
and CEO of security firm Cipher Cloud. "Not knowing the majority of the insights
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ACCOUNTING INFORMATION SYSTEM
concerning when the break was found and who was affected, the potential results might be
more awful than we know today," he says. "We'll need to perceive what Facebook unveils
about potential obligation, if any exists. The computations of the potential fines under GDPR
are a bit staggering."
Since the helplessness has existed since July 2017, Facebook has not decided out the
likelihood that littler assaults on the token of its framework went non-detected before
September (Jabee and Afshar, 2016). It is right now examining. However, Facebook has
made a security see page where consumers are able to check whether their record was
affected by the information rupture.
concerning when the break was found and who was affected, the potential results might be
more awful than we know today," he says. "We'll need to perceive what Facebook unveils
about potential obligation, if any exists. The computations of the potential fines under GDPR
are a bit staggering."
Since the helplessness has existed since July 2017, Facebook has not decided out the
likelihood that littler assaults on the token of its framework went non-detected before
September (Jabee and Afshar, 2016). It is right now examining. However, Facebook has
made a security see page where consumers are able to check whether their record was
affected by the information rupture.

11ACCOUNTING INFORMATION SYSTEM
References:
Alles, M., Brennan, G., Kogan, A. and Vasarhelyi, M.A., 2018. Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald Publishing
Li
Belfo, F. and Trigo, A., 2013. Accounting information systems: Tradition and future
directions. Procedia Technology, 9, pp.536-546.
Das, S., Kramer, A.D., Dabbish, L.A. and Hong, J.I., 2014, November. Increasing security
sensitivity with social proof: A large-scale experimental confirmation. In Proceedings of the
2014 ACM SIGSAC conference on computer and communications security (pp. 739-749).
ACM.
Ismail, N.A. and King, M., 2014. Factors influencing the alignment of accounting
information systems in small and medium sized Malaysian manufacturing firms. Journal of
Information Systems and Small Business, 1(1-2), pp.1-20.
Jabee, R. and Afshar, M., 2016. Issues and challenges of cyber security for social networking
sites (Facebook). International Journal of Computer Applications, 144(3), pp.36-40.
Jamal, A., Coughlan, J. and Kamal, M., 2013. Mining social network data for personalisation
and privacy concerns: a case study of Facebook’s Beacon.
Kuyumdzhiev, I.O., 2014. Controls Mitigating the Risk of Confidential Information
Disclosure by Facebook: Essential Concern in Auditing Information Security. TEM
Journal, 3(2), p.113.
References:
Alles, M., Brennan, G., Kogan, A. and Vasarhelyi, M.A., 2018. Continuous monitoring of
business process controls: A pilot implementation of a continuous auditing system at
Siemens. In Continuous Auditing: Theory and Application (pp. 219-246). Emerald Publishing
Li
Belfo, F. and Trigo, A., 2013. Accounting information systems: Tradition and future
directions. Procedia Technology, 9, pp.536-546.
Das, S., Kramer, A.D., Dabbish, L.A. and Hong, J.I., 2014, November. Increasing security
sensitivity with social proof: A large-scale experimental confirmation. In Proceedings of the
2014 ACM SIGSAC conference on computer and communications security (pp. 739-749).
ACM.
Ismail, N.A. and King, M., 2014. Factors influencing the alignment of accounting
information systems in small and medium sized Malaysian manufacturing firms. Journal of
Information Systems and Small Business, 1(1-2), pp.1-20.
Jabee, R. and Afshar, M., 2016. Issues and challenges of cyber security for social networking
sites (Facebook). International Journal of Computer Applications, 144(3), pp.36-40.
Jamal, A., Coughlan, J. and Kamal, M., 2013. Mining social network data for personalisation
and privacy concerns: a case study of Facebook’s Beacon.
Kuyumdzhiev, I.O., 2014. Controls Mitigating the Risk of Confidential Information
Disclosure by Facebook: Essential Concern in Auditing Information Security. TEM
Journal, 3(2), p.113.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.