Accounting Information System: Revenue Cycle and Controls
VerifiedAdded on 2020/03/28
|9
|1690
|42
Report
AI Summary
This report provides an in-depth analysis of Accounting Information Systems (AIS), focusing on the revenue cycle, internal controls, and the impact of ransomware attacks. It begins with an overview of the revenue cycle, explaining its physical and financial phases and the associated subsystems. The report then identifies weaknesses in internal controls that could affect Motherboards and More Pty Ltd, analyzing their impacts and recommending risk mitigation strategies. A significant portion of the report is dedicated to the disruptive effects of ransomware attacks, specifically the 'Wannacry' incident, offering practical advice for Motherboards and More Pty Ltd to protect against future attacks. The report emphasizes the importance of data security, including data backup, encryption, and limiting user access. In conclusion, the report stresses the crucial role of AIS in data management and decision-making and the need for proactive measures to safeguard against cyber threats.

1Accounting Information System
Running head: ACCOUNTING INFORMATION SYSTEM
Accounting Information System
Author’s Name
Institution
Supervisor’s Name
Course
Running head: ACCOUNTING INFORMATION SYSTEM
Accounting Information System
Author’s Name
Institution
Supervisor’s Name
Course
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2Accounting Information System
Executive Summary
Accounting Information System has developed as one of the most important elements of
modern era, which helps to maintain the records for effective decision-making processes in the
future. Moreover, the concept of revenue cycle was discussed in the study, wherein the relation
of physical phase and financial phase with the product and the consumer was explained briefly.
The paper provides an in-depth understanding of the weaknesses that may affect Motherboards
and More Pty Ltd specifically in controlling its internal activities. Moreover, the impacts were
analyzed as well the risk mitigating factors were recommended in the paper. Additionally, it
comprised the consequences of the disruptive attack of Ransomware attack that have been
descriptively discussed in the study with suggestions provided for Motherboards and More Pty
Ltd to prevent themselves from this attack in the future.
Executive Summary
Accounting Information System has developed as one of the most important elements of
modern era, which helps to maintain the records for effective decision-making processes in the
future. Moreover, the concept of revenue cycle was discussed in the study, wherein the relation
of physical phase and financial phase with the product and the consumer was explained briefly.
The paper provides an in-depth understanding of the weaknesses that may affect Motherboards
and More Pty Ltd specifically in controlling its internal activities. Moreover, the impacts were
analyzed as well the risk mitigating factors were recommended in the paper. Additionally, it
comprised the consequences of the disruptive attack of Ransomware attack that have been
descriptively discussed in the study with suggestions provided for Motherboards and More Pty
Ltd to prevent themselves from this attack in the future.

3Accounting Information System
Table of Contents
Introduction......................................................................................................................................4
Overview of Revenue Cycle............................................................................................................4
Identification of Practical Controls..................................................................................................6
Overview of Ransom-ware attack...................................................................................................7
Recommendations and Conclusion..................................................................................................8
References........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................4
Overview of Revenue Cycle............................................................................................................4
Identification of Practical Controls..................................................................................................6
Overview of Ransom-ware attack...................................................................................................7
Recommendations and Conclusion..................................................................................................8
References........................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4Accounting Information System
Accounting Information System
Introduction
Accounting information systems play an essential role in collection, storing, processing
as well as recording of data for providing information during the process of decision making.
These systems are made up of interrelated components, where it is divided into smaller sub-
systems helping to achieve the organizational objective. The key characteristics of accounting
information system are relevance, completeness, timeliness, verifiability, accessibility,
understandability as well as reliability. Web-based systems and its wide-spread usage have
helped the accounting information systems to identify organizational risks along with the
creation of accounting procedures for maintaining optimum control over risk (Belfo & Trigo,
2013; Accounting Information Systems, 2013). The key objective of the paper is to discuss the
revenue cycle, weaknesses related to internal control along with the processes to mitigate the
risks arising due to the weaknesses. Additionally, Ransom-ware attack and its brief overview
have been explained in this paper.
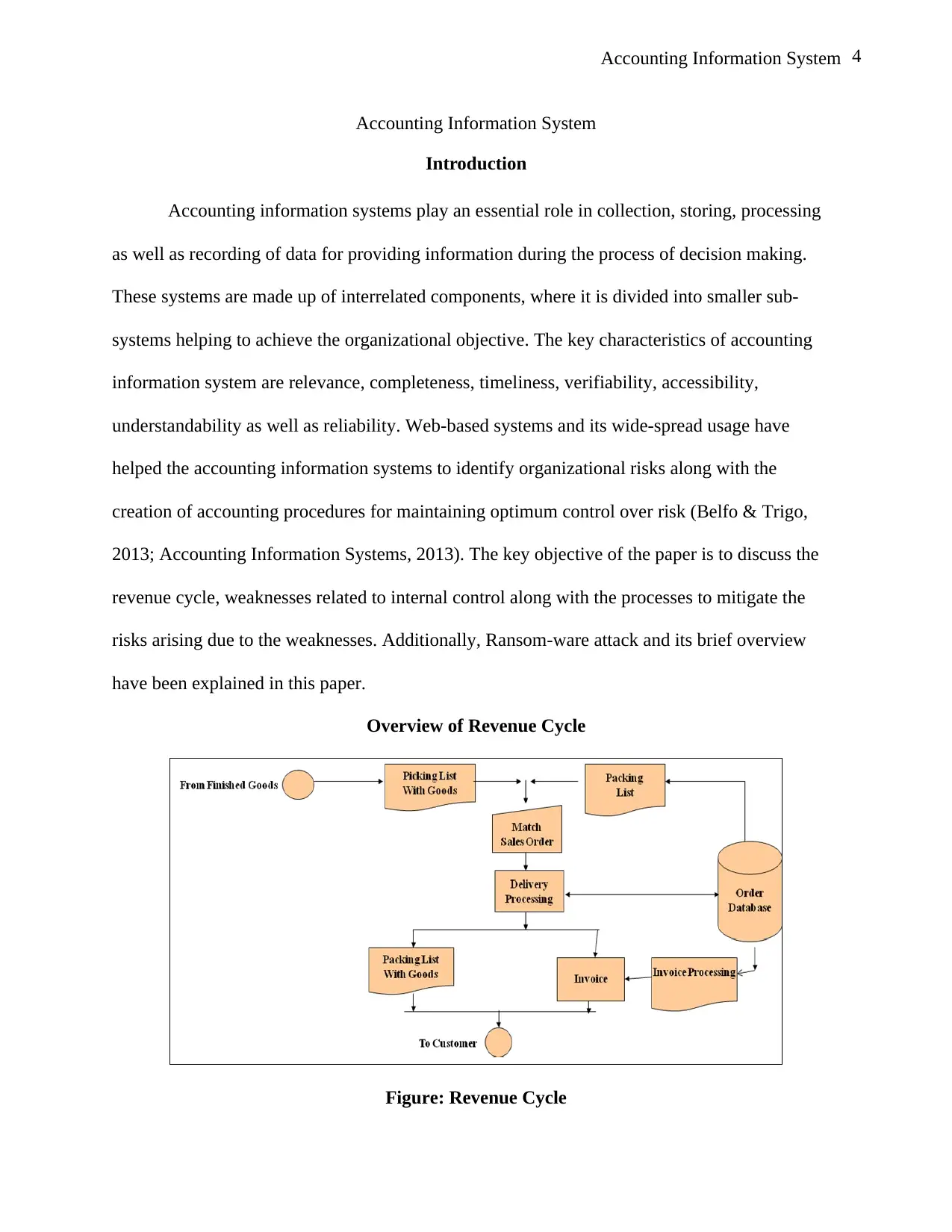
Overview of Revenue Cycle
Figure: Revenue Cycle
Accounting Information System
Introduction
Accounting information systems play an essential role in collection, storing, processing
as well as recording of data for providing information during the process of decision making.
These systems are made up of interrelated components, where it is divided into smaller sub-
systems helping to achieve the organizational objective. The key characteristics of accounting
information system are relevance, completeness, timeliness, verifiability, accessibility,
understandability as well as reliability. Web-based systems and its wide-spread usage have
helped the accounting information systems to identify organizational risks along with the
creation of accounting procedures for maintaining optimum control over risk (Belfo & Trigo,
2013; Accounting Information Systems, 2013). The key objective of the paper is to discuss the
revenue cycle, weaknesses related to internal control along with the processes to mitigate the
risks arising due to the weaknesses. Additionally, Ransom-ware attack and its brief overview
have been explained in this paper.
Overview of Revenue Cycle
Figure: Revenue Cycle
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5Accounting Information System
Revenue Cycle is referred as a set of business activities, helping to exchange goods as
well as services for cash with the customers. Maximum of the transactions in today’s business
takes place on credit, where the amount is paid after the goods are shipped on time to the
consumers. There are two key phases in the revenue cycle, which starts with the physical phase,
where the good is received by the buyer and ends with the financial phase, where the buyer pays
the cash for the delivered product. As mentioned in the accounting information system, there are
two subsystems handling the above mentioned phases (Hall, 2008; Hall, 2012). The subsystems
include processing of sales order for the physical phase while cash receipts look after the
financial phase. Additionally, activities of revenue cycle are divided into two major categories
including manual system and computerized system. Manual systems follow the manual
procedures of sales, billing, warehouse, credit, shipping, general ledger, accounts receivable as
well as inventory control. Moreover, sales returns, cash receipts, control of revenue cycle are
parts of manual system. Accounting system based on computers start with automating the
process of sales order through batch technology and reengineering the same with real-time
technology. The procedures of manual systems are enhanced with the use of information
technology, where procedures of cash receipts get automated and reengineered. Usage of Point-
of-sale (POS) systems as well as reengineering through EDI along with Internet has made the
process of revenue cycle easier than before (Hall, 2008; Hall, 2012).
Revenue Cycle is referred as a set of business activities, helping to exchange goods as
well as services for cash with the customers. Maximum of the transactions in today’s business
takes place on credit, where the amount is paid after the goods are shipped on time to the
consumers. There are two key phases in the revenue cycle, which starts with the physical phase,
where the good is received by the buyer and ends with the financial phase, where the buyer pays
the cash for the delivered product. As mentioned in the accounting information system, there are
two subsystems handling the above mentioned phases (Hall, 2008; Hall, 2012). The subsystems
include processing of sales order for the physical phase while cash receipts look after the
financial phase. Additionally, activities of revenue cycle are divided into two major categories
including manual system and computerized system. Manual systems follow the manual
procedures of sales, billing, warehouse, credit, shipping, general ledger, accounts receivable as
well as inventory control. Moreover, sales returns, cash receipts, control of revenue cycle are
parts of manual system. Accounting system based on computers start with automating the
process of sales order through batch technology and reengineering the same with real-time
technology. The procedures of manual systems are enhanced with the use of information
technology, where procedures of cash receipts get automated and reengineered. Usage of Point-
of-sale (POS) systems as well as reengineering through EDI along with Internet has made the
process of revenue cycle easier than before (Hall, 2008; Hall, 2012).
6Accounting Information System
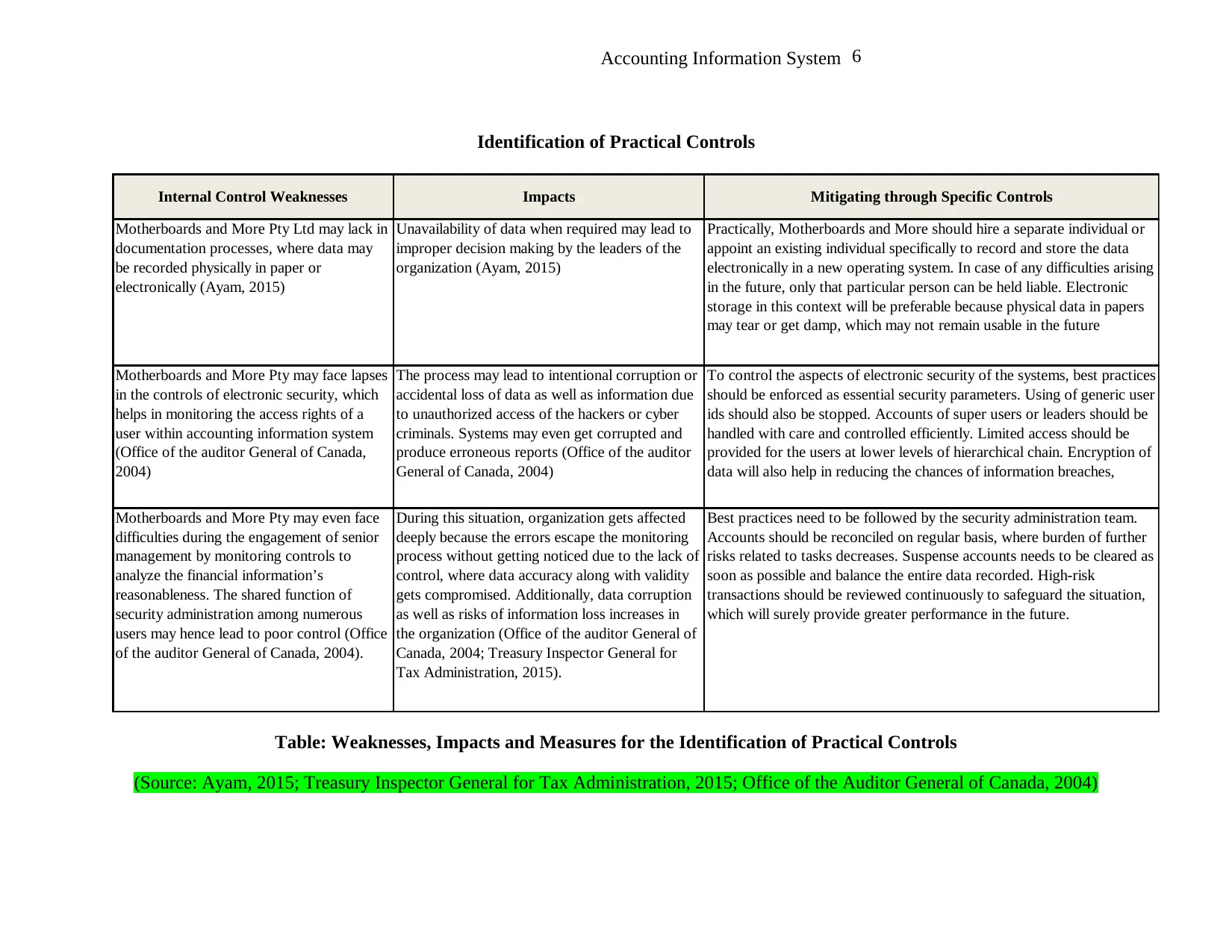
Identification of Practical Controls
Internal Control Weaknesses Impacts Mitigating through Specific Controls
Motherboards and More Pty Ltd may lack in
documentation processes, where data may
be recorded physically in paper or
electronically (Ayam, 2015)
Unavailability of data when required may lead to
improper decision making by the leaders of the
organization (Ayam, 2015)
Practically, Motherboards and More should hire a separate individual or
appoint an existing individual specifically to record and store the data
electronically in a new operating system. In case of any difficulties arising
in the future, only that particular person can be held liable. Electronic
storage in this context will be preferable because physical data in papers
may tear or get damp, which may not remain usable in the future
Motherboards and More Pty may face lapses
in the controls of electronic security, which
helps in monitoring the access rights of a
user within accounting information system
(Office of the auditor General of Canada,
2004)
The process may lead to intentional corruption or
accidental loss of data as well as information due
to unauthorized access of the hackers or cyber
criminals. Systems may even get corrupted and
produce erroneous reports (Office of the auditor
General of Canada, 2004)
To control the aspects of electronic security of the systems, best practices
should be enforced as essential security parameters. Using of generic user
ids should also be stopped. Accounts of super users or leaders should be
handled with care and controlled efficiently. Limited access should be
provided for the users at lower levels of hierarchical chain. Encryption of
data will also help in reducing the chances of information breaches,
Motherboards and More Pty may even face
difficulties during the engagement of senior
management by monitoring controls to
analyze the financial information’s
reasonableness. The shared function of
security administration among numerous
users may hence lead to poor control (Office
of the auditor General of Canada, 2004).
During this situation, organization gets affected
deeply because the errors escape the monitoring
process without getting noticed due to the lack of
control, where data accuracy along with validity
gets compromised. Additionally, data corruption
as well as risks of information loss increases in
the organization (Office of the auditor General of
Canada, 2004; Treasury Inspector General for
Tax Administration, 2015).
Best practices need to be followed by the security administration team.
Accounts should be reconciled on regular basis, where burden of further
risks related to tasks decreases. Suspense accounts needs to be cleared as
soon as possible and balance the entire data recorded. High-risk
transactions should be reviewed continuously to safeguard the situation,
which will surely provide greater performance in the future.
Table: Weaknesses, Impacts and Measures for the Identification of Practical Controls
(Source: Ayam, 2015; Treasury Inspector General for Tax Administration, 2015; Office of the Auditor General of Canada, 2004)
Identification of Practical Controls
Internal Control Weaknesses Impacts Mitigating through Specific Controls
Motherboards and More Pty Ltd may lack in
documentation processes, where data may
be recorded physically in paper or
electronically (Ayam, 2015)
Unavailability of data when required may lead to
improper decision making by the leaders of the
organization (Ayam, 2015)
Practically, Motherboards and More should hire a separate individual or
appoint an existing individual specifically to record and store the data
electronically in a new operating system. In case of any difficulties arising
in the future, only that particular person can be held liable. Electronic
storage in this context will be preferable because physical data in papers
may tear or get damp, which may not remain usable in the future
Motherboards and More Pty may face lapses
in the controls of electronic security, which
helps in monitoring the access rights of a
user within accounting information system
(Office of the auditor General of Canada,
2004)
The process may lead to intentional corruption or
accidental loss of data as well as information due
to unauthorized access of the hackers or cyber
criminals. Systems may even get corrupted and
produce erroneous reports (Office of the auditor
General of Canada, 2004)
To control the aspects of electronic security of the systems, best practices
should be enforced as essential security parameters. Using of generic user
ids should also be stopped. Accounts of super users or leaders should be
handled with care and controlled efficiently. Limited access should be
provided for the users at lower levels of hierarchical chain. Encryption of
data will also help in reducing the chances of information breaches,
Motherboards and More Pty may even face
difficulties during the engagement of senior
management by monitoring controls to
analyze the financial information’s
reasonableness. The shared function of
security administration among numerous
users may hence lead to poor control (Office
of the auditor General of Canada, 2004).
During this situation, organization gets affected
deeply because the errors escape the monitoring
process without getting noticed due to the lack of
control, where data accuracy along with validity
gets compromised. Additionally, data corruption
as well as risks of information loss increases in
the organization (Office of the auditor General of
Canada, 2004; Treasury Inspector General for
Tax Administration, 2015).
Best practices need to be followed by the security administration team.
Accounts should be reconciled on regular basis, where burden of further
risks related to tasks decreases. Suspense accounts needs to be cleared as
soon as possible and balance the entire data recorded. High-risk
transactions should be reviewed continuously to safeguard the situation,
which will surely provide greater performance in the future.
Table: Weaknesses, Impacts and Measures for the Identification of Practical Controls
(Source: Ayam, 2015; Treasury Inspector General for Tax Administration, 2015; Office of the Auditor General of Canada, 2004)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7Accounting Information System
Overview of Ransom-ware attack
Based on the case study as reported by ABC (2017), it has been found that in May 2017,
57000 organizations in nearly 100 nations suffered cyber attack globally, including Ukraine,
Russia, Taiwan as well as India among others, where the un-patched older versions of Microsoft
windows were commonly used (ABC, 2017). This cyber attack was identified as a ransom-ware
attack named “Wannacry”, which created a flaw in the software of Microsoft Corporation
(McGoogan, Titcomb & Krol, 2017). The cyber attackers took advantage of the vulnerabilities
related to the older version of Windows operating system. Additionally, European nations
including Spain and Portugal among others were forced to turn down the patients in the clinics as
well as hospitals because they lost access due to the cyber extortion of ransomware. According to
British cyber centre, FedEx Corporation, which is the leading shipper globally, was one of the
victims of the attack, where the systems got affected due to the malware entering through spam
mails (ABC, 2017). The National Security Agency identified that hackers were spreading a
ransom-ware that locked up files as well as folders completely. Wannacry ransom-ware
demanded payments during the cyber attack on systems of several users, where hackers used this
trend for quick payout of money. A ransom-ware is described as a cyber attack or virus, which
takes full control of other’s system and blocks away all sources of access to it until and unless
the asked amount is paid (McGoogan et al., 2017; ABC, 2017). Based on the research conducted
by the Kaspersky Lab experts, Ransomware demands nearly $300- $600 for restoring the system,
which increases every two hours if not paid (ABC, 2017). The process starts when a user
unintentionally clicks on a ransom-ware link or downloads it. The hacker through malicious
software enters into the system as soon as the link is opened and launches the attack to lock
down the system as a whole, where access of the owner gets denied. Microsoft had already
Overview of Ransom-ware attack
Based on the case study as reported by ABC (2017), it has been found that in May 2017,
57000 organizations in nearly 100 nations suffered cyber attack globally, including Ukraine,
Russia, Taiwan as well as India among others, where the un-patched older versions of Microsoft
windows were commonly used (ABC, 2017). This cyber attack was identified as a ransom-ware
attack named “Wannacry”, which created a flaw in the software of Microsoft Corporation
(McGoogan, Titcomb & Krol, 2017). The cyber attackers took advantage of the vulnerabilities
related to the older version of Windows operating system. Additionally, European nations
including Spain and Portugal among others were forced to turn down the patients in the clinics as
well as hospitals because they lost access due to the cyber extortion of ransomware. According to
British cyber centre, FedEx Corporation, which is the leading shipper globally, was one of the
victims of the attack, where the systems got affected due to the malware entering through spam
mails (ABC, 2017). The National Security Agency identified that hackers were spreading a
ransom-ware that locked up files as well as folders completely. Wannacry ransom-ware
demanded payments during the cyber attack on systems of several users, where hackers used this
trend for quick payout of money. A ransom-ware is described as a cyber attack or virus, which
takes full control of other’s system and blocks away all sources of access to it until and unless
the asked amount is paid (McGoogan et al., 2017; ABC, 2017). Based on the research conducted
by the Kaspersky Lab experts, Ransomware demands nearly $300- $600 for restoring the system,
which increases every two hours if not paid (ABC, 2017). The process starts when a user
unintentionally clicks on a ransom-ware link or downloads it. The hacker through malicious
software enters into the system as soon as the link is opened and launches the attack to lock
down the system as a whole, where access of the owner gets denied. Microsoft had already
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8Accounting Information System
issued ‘patches’ for the software to fix up the issues but majority of the people were still found
using the same old version (McGoogan, Titcomb & Krol, 2017; ABC, 2017).
Recommendations and Conclusion
Considering the motherboards and More Pty Ltd, such a ransom-ware cyber attack may
occur in the future. Therefore, the company should follow the measures of controlling the
information security, monitoring as well as documentation as mentioned above. Data should
hence be saved in more than one systems, where if one systems gets attacked by the ransom-
ware, the other system can be used for the accessing the data. Encryption of data is compulsory,
which reduces the chances of cyber attack as encrypted data cannot be hacked easily by any
hacker. Day-to-day recording of data should be done by Motherboards and More Pty Ltd., which
will lessen the burden with the passage of time. Access should be made limited for the users,
which will further prevent clicking on dangerous links as well as sites. Additionally,
Motherboards and more Pty Ltd should use latest version of Microsoft windows or any other
operating system with fix-patches installed in it to prevent their system from the disruptive attack
of Ransomware.
Accounting information system plays an important role and simplifies the processes of
collecting, recording as well as handling data and information. Proper techniques used during
electronic data storage will secure the data for a longer duration, where the leaders or managers
can effectively conduct a decision making process. Conclusively, it was found that a ransom-
ware is a dangerous attack and therefore Motherboards and More Pty Ltd should follow the
processes as mentioned in the study.
issued ‘patches’ for the software to fix up the issues but majority of the people were still found
using the same old version (McGoogan, Titcomb & Krol, 2017; ABC, 2017).
Recommendations and Conclusion
Considering the motherboards and More Pty Ltd, such a ransom-ware cyber attack may
occur in the future. Therefore, the company should follow the measures of controlling the
information security, monitoring as well as documentation as mentioned above. Data should
hence be saved in more than one systems, where if one systems gets attacked by the ransom-
ware, the other system can be used for the accessing the data. Encryption of data is compulsory,
which reduces the chances of cyber attack as encrypted data cannot be hacked easily by any
hacker. Day-to-day recording of data should be done by Motherboards and More Pty Ltd., which
will lessen the burden with the passage of time. Access should be made limited for the users,
which will further prevent clicking on dangerous links as well as sites. Additionally,
Motherboards and more Pty Ltd should use latest version of Microsoft windows or any other
operating system with fix-patches installed in it to prevent their system from the disruptive attack
of Ransomware.
Accounting information system plays an important role and simplifies the processes of
collecting, recording as well as handling data and information. Proper techniques used during
electronic data storage will secure the data for a longer duration, where the leaders or managers
can effectively conduct a decision making process. Conclusively, it was found that a ransom-
ware is a dangerous attack and therefore Motherboards and More Pty Ltd should follow the
processes as mentioned in the study.

9Accounting Information System
References
ABC. (2017). Biggest ransomware outbreak in history' hits nearly 100 countries with data held
for ransom Retrieved September 21, 2017, from http://www.abc.net.au/news/2017-05-
13/biggest-ransomware-outbreak-in-history-hits-nearly-100-nations/8523102
Accounting Information Systems. (2013). Accounting Information Systems Explained. Retrieved
September 20, 2017, from http://www.accountinginformationsystems.org/
Ayam, J. R. A. (2015). An analysis of revenue cycle internal controls in Ghanaian universities.
Case Studies in Business and Management, 2(2), 1.
Belfo, F., & Trigo, A. (2013). Accounting information systems: Tradition and future directions.
Procedia Technology, 9, 536-546.
Hall, J. A. (2008). Accounting Information Systems. United States: Cengage learning.
Hall, J. A. (2012). Accounting Information Systems. United States: Cengage learning.
McGoogan, C., Titcomb, J. & Krol, C. (2017). What is WannaCry and how does ransomware
work? Retrieved September 20, 2017, from
http://www.telegraph.co.uk/technology/0/ransomware-does-work/
Office of the auditor General of Canada. (2004). 2004 march report of the auditor general of
canada. Retrieved September 20, 2017, from
http://www.oag-bvg.gc.ca/internet/English/att_20040306xe05_e_13231.html
Treasury Inspector General for Tax Administration. (2015). Annual assessment of the internal
revenue service information technology program. Retrieved September 20, 2017, from
https://www.treasury.gov/tigta/auditreports/2015reports/201520094fr.pdf
References
ABC. (2017). Biggest ransomware outbreak in history' hits nearly 100 countries with data held
for ransom Retrieved September 21, 2017, from http://www.abc.net.au/news/2017-05-
13/biggest-ransomware-outbreak-in-history-hits-nearly-100-nations/8523102
Accounting Information Systems. (2013). Accounting Information Systems Explained. Retrieved
September 20, 2017, from http://www.accountinginformationsystems.org/
Ayam, J. R. A. (2015). An analysis of revenue cycle internal controls in Ghanaian universities.
Case Studies in Business and Management, 2(2), 1.
Belfo, F., & Trigo, A. (2013). Accounting information systems: Tradition and future directions.
Procedia Technology, 9, 536-546.
Hall, J. A. (2008). Accounting Information Systems. United States: Cengage learning.
Hall, J. A. (2012). Accounting Information Systems. United States: Cengage learning.
McGoogan, C., Titcomb, J. & Krol, C. (2017). What is WannaCry and how does ransomware
work? Retrieved September 20, 2017, from
http://www.telegraph.co.uk/technology/0/ransomware-does-work/
Office of the auditor General of Canada. (2004). 2004 march report of the auditor general of
canada. Retrieved September 20, 2017, from
http://www.oag-bvg.gc.ca/internet/English/att_20040306xe05_e_13231.html
Treasury Inspector General for Tax Administration. (2015). Annual assessment of the internal
revenue service information technology program. Retrieved September 20, 2017, from
https://www.treasury.gov/tigta/auditreports/2015reports/201520094fr.pdf
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





