ACCT6001 Accounting Information Systems: Database Application Report
VerifiedAdded on 2023/06/12
|9
|1708
|286
Report
AI Summary
This report provides a comprehensive overview of a database application design for an accounting information system, beginning with a normalized database and ER diagram to illustrate key entities and relationships. It details the conversion of the ER diagram into a relational schema, specifying primary and foreign keys, followed by its implementation in Microsoft Access, including queries and reports. The report justifies the use of a database management system over a file system, highlighting advantages such as efficient data storage, easy data retrieval, and enhanced data management. It addresses IT controls for data integrity and availability, including data backup, access controls, and database standards, while also exploring ethical, privacy, and security issues, such as email monitoring, copyright protection, and data encryption, to safeguard sensitive information. The report concludes by emphasizing the importance of antivirus software and security standards to protect the company's data and maintain stakeholder trust. Desklib provides access to similar solved assignments and resources for students.

Student ID –
Student Name -
Date -
ACCT6001 Accounting Information Systems
Assessment 4: Database Application
Module Tutor -
Student Name -
Date -
ACCT6001 Accounting Information Systems
Assessment 4: Database Application
Module Tutor -
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Report
Introduction
The report is showing the complete database designing of the complete system. Firstly the
normalized database is created to understand the complete database. The ER diagram is showing
all important entities and relationship between them.
The relational schema is converted from the ER diagram to clearly specify the primary keys,
foreign keys etc.
After database designing, the database is implemented in the Microsoft Access database. All
important queries, reports etc. are built into the database.
Justification of the Use of the Database
The database is very important in every business whether it is big or small. It is very difficult to
store the database into the file system. The relational database is highly efficient in storing the
data in a proper manner.
The relational database management system stores the data in a tabular format and each table is
linked with another table to relate the data. The data can be searched easily within a very less
time than the file system. It is very time saving technique. The important data that is required by
the admin can be seen in the form of reports very easily at any time.
That is why; the relational database management system is the best way to store the data in a very
efficient manner.
Introduction
The report is showing the complete database designing of the complete system. Firstly the
normalized database is created to understand the complete database. The ER diagram is showing
all important entities and relationship between them.
The relational schema is converted from the ER diagram to clearly specify the primary keys,
foreign keys etc.
After database designing, the database is implemented in the Microsoft Access database. All
important queries, reports etc. are built into the database.
Justification of the Use of the Database
The database is very important in every business whether it is big or small. It is very difficult to
store the database into the file system. The relational database is highly efficient in storing the
data in a proper manner.
The relational database management system stores the data in a tabular format and each table is
linked with another table to relate the data. The data can be searched easily within a very less
time than the file system. It is very time saving technique. The important data that is required by
the admin can be seen in the form of reports very easily at any time.
That is why; the relational database management system is the best way to store the data in a very
efficient manner.
There are so many problems in the file system that can be resolved by the relational database
management system like below-
Problem in Searching
It is very difficult to search a specific employee detail in the file system e.g. to search about the
employee, its department etc. If the department information is stored in separate file and employee
information is stored in the separate file, then it is very difficult.
The relational database management system resolved this issue as separate table is created for
employee and department and there is relational in between the tables. When the employee will
be searched in the employee table, the related department can also be fetched very easily.
Time Consuming
Old File System is very time consuming. It takes so much time in searching an employee from the
Employee file but in the relational database management system, this process can be found very
easily.
Difficult to Manage
Old File System is very difficult to manage, if the database grows. All the records will be stored in a single
file. This problem can be easily resolved in the relational database management system by making
separate tables. The similar data will be stored in specific tables e.g. employee detail will be
stored into the employee table; department data will be stored into the department table etc.
Cannot Implement Access Control
The admin can implement access control over specific data if needed in the relational database
management system but this is not possible in the old file system. Sometimes there is some data
that is important and required more security; in that case access control can be set on specific
data for security reasons.
management system like below-
Problem in Searching
It is very difficult to search a specific employee detail in the file system e.g. to search about the
employee, its department etc. If the department information is stored in separate file and employee
information is stored in the separate file, then it is very difficult.
The relational database management system resolved this issue as separate table is created for
employee and department and there is relational in between the tables. When the employee will
be searched in the employee table, the related department can also be fetched very easily.
Time Consuming
Old File System is very time consuming. It takes so much time in searching an employee from the
Employee file but in the relational database management system, this process can be found very
easily.
Difficult to Manage
Old File System is very difficult to manage, if the database grows. All the records will be stored in a single
file. This problem can be easily resolved in the relational database management system by making
separate tables. The similar data will be stored in specific tables e.g. employee detail will be
stored into the employee table; department data will be stored into the department table etc.
Cannot Implement Access Control
The admin can implement access control over specific data if needed in the relational database
management system but this is not possible in the old file system. Sometimes there is some data
that is important and required more security; in that case access control can be set on specific
data for security reasons.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
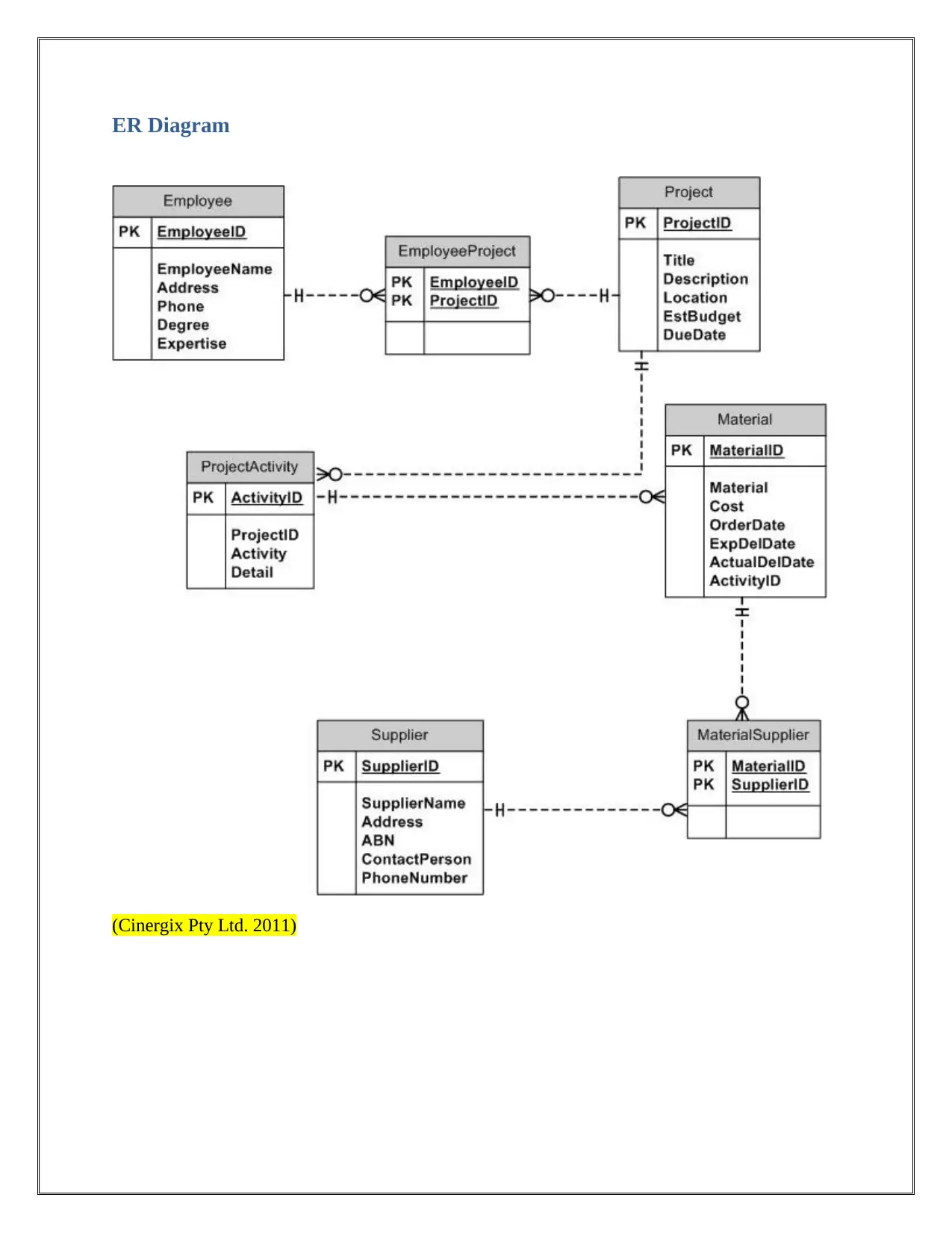
ER Diagram
(Cinergix Pty Ltd. 2011)
(Cinergix Pty Ltd. 2011)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
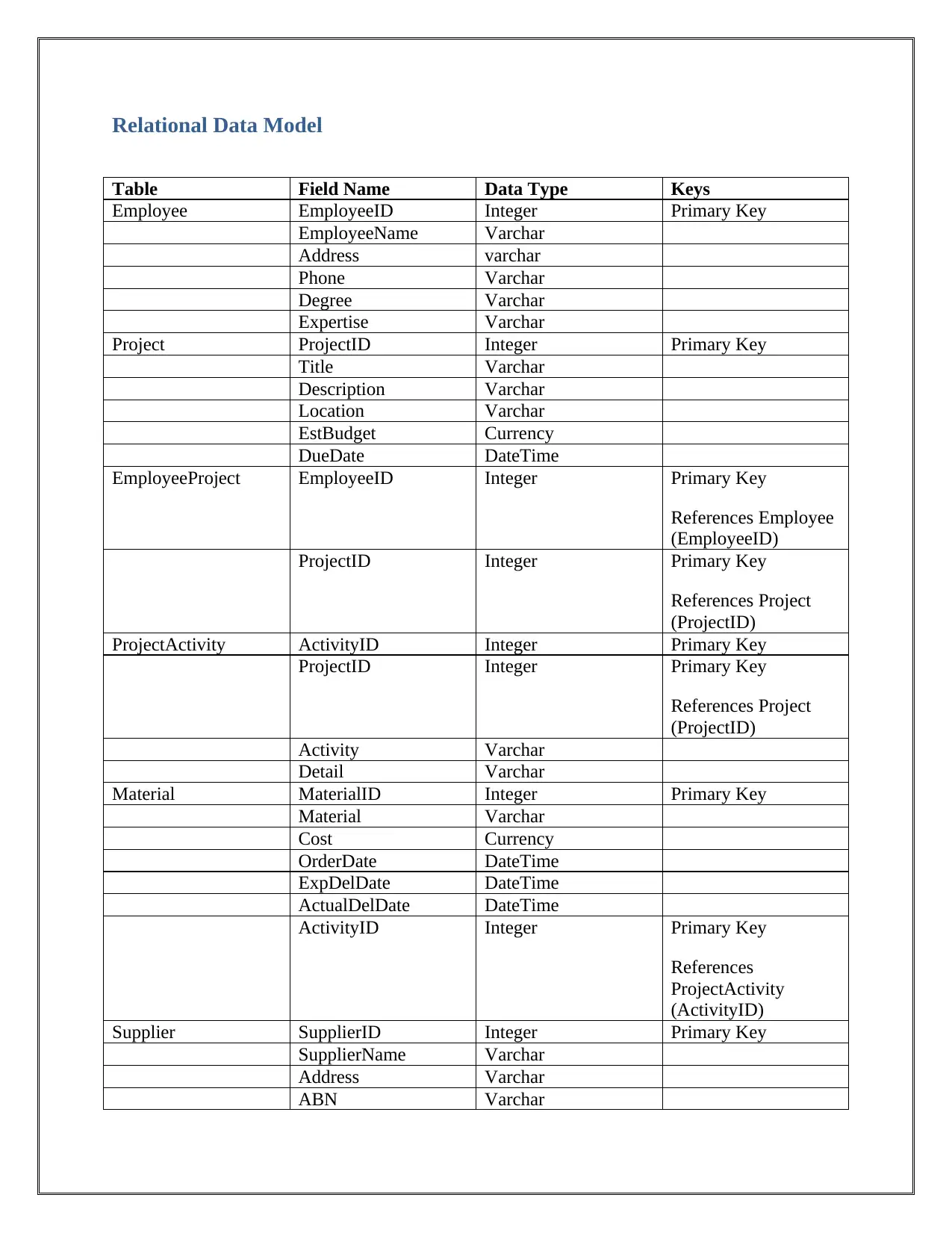
Relational Data Model
Table Field Name Data Type Keys
Employee EmployeeID Integer Primary Key
EmployeeName Varchar
Address varchar
Phone Varchar
Degree Varchar
Expertise Varchar
Project ProjectID Integer Primary Key
Title Varchar
Description Varchar
Location Varchar
EstBudget Currency
DueDate DateTime
EmployeeProject EmployeeID Integer Primary Key
References Employee
(EmployeeID)
ProjectID Integer Primary Key
References Project
(ProjectID)
ProjectActivity ActivityID Integer Primary Key
ProjectID Integer Primary Key
References Project
(ProjectID)
Activity Varchar
Detail Varchar
Material MaterialID Integer Primary Key
Material Varchar
Cost Currency
OrderDate DateTime
ExpDelDate DateTime
ActualDelDate DateTime
ActivityID Integer Primary Key
References
ProjectActivity
(ActivityID)
Supplier SupplierID Integer Primary Key
SupplierName Varchar
Address Varchar
ABN Varchar
Table Field Name Data Type Keys
Employee EmployeeID Integer Primary Key
EmployeeName Varchar
Address varchar
Phone Varchar
Degree Varchar
Expertise Varchar
Project ProjectID Integer Primary Key
Title Varchar
Description Varchar
Location Varchar
EstBudget Currency
DueDate DateTime
EmployeeProject EmployeeID Integer Primary Key
References Employee
(EmployeeID)
ProjectID Integer Primary Key
References Project
(ProjectID)
ProjectActivity ActivityID Integer Primary Key
ProjectID Integer Primary Key
References Project
(ProjectID)
Activity Varchar
Detail Varchar
Material MaterialID Integer Primary Key
Material Varchar
Cost Currency
OrderDate DateTime
ExpDelDate DateTime
ActualDelDate DateTime
ActivityID Integer Primary Key
References
ProjectActivity
(ActivityID)
Supplier SupplierID Integer Primary Key
SupplierName Varchar
Address Varchar
ABN Varchar
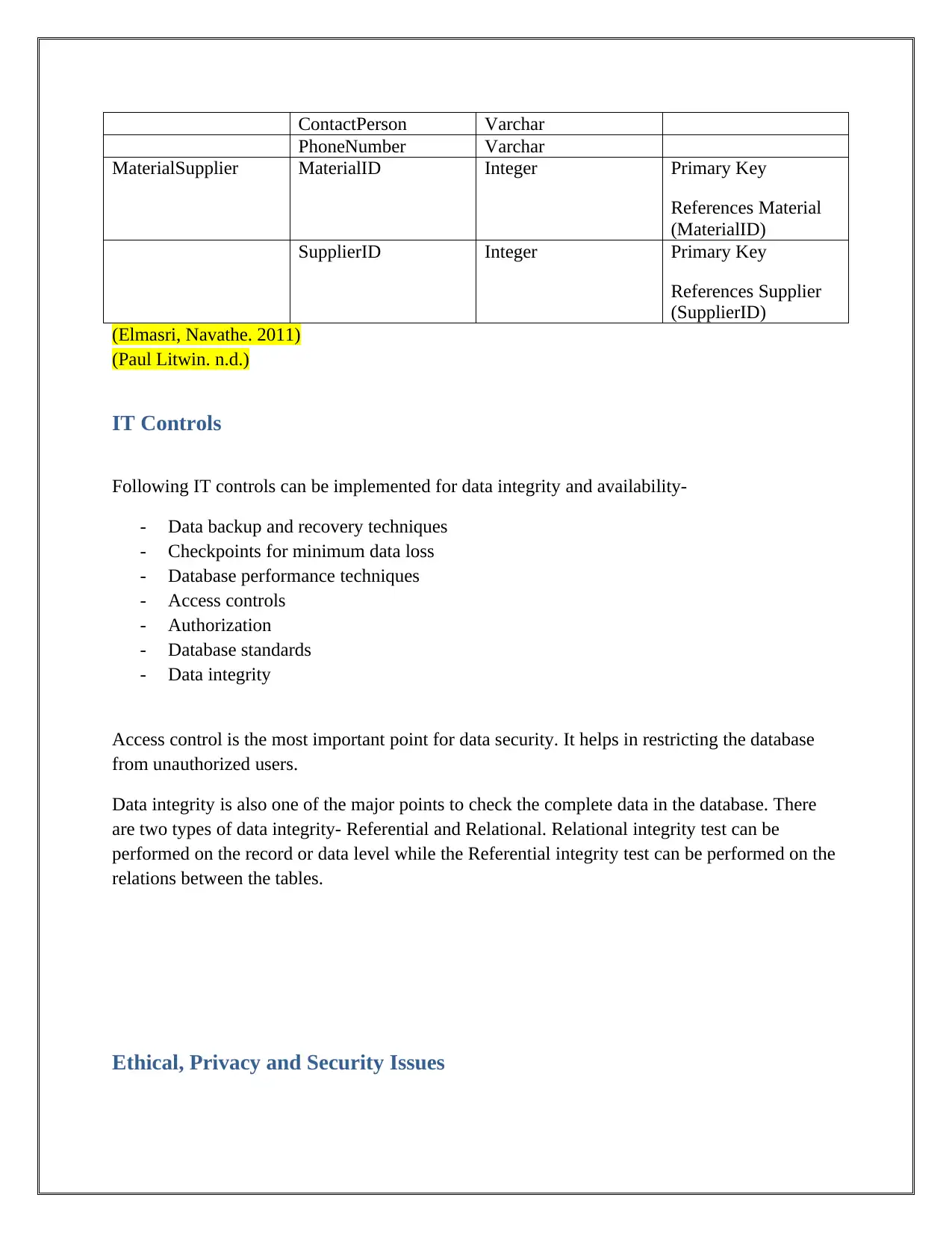
ContactPerson Varchar
PhoneNumber Varchar
MaterialSupplier MaterialID Integer Primary Key
References Material
(MaterialID)
SupplierID Integer Primary Key
References Supplier
(SupplierID)
(Elmasri, Navathe. 2011)
(Paul Litwin. n.d.)
IT Controls
Following IT controls can be implemented for data integrity and availability-
- Data backup and recovery techniques
- Checkpoints for minimum data loss
- Database performance techniques
- Access controls
- Authorization
- Database standards
- Data integrity
Access control is the most important point for data security. It helps in restricting the database
from unauthorized users.
Data integrity is also one of the major points to check the complete data in the database. There
are two types of data integrity- Referential and Relational. Relational integrity test can be
performed on the record or data level while the Referential integrity test can be performed on the
relations between the tables.
Ethical, Privacy and Security Issues
PhoneNumber Varchar
MaterialSupplier MaterialID Integer Primary Key
References Material
(MaterialID)
SupplierID Integer Primary Key
References Supplier
(SupplierID)
(Elmasri, Navathe. 2011)
(Paul Litwin. n.d.)
IT Controls
Following IT controls can be implemented for data integrity and availability-
- Data backup and recovery techniques
- Checkpoints for minimum data loss
- Database performance techniques
- Access controls
- Authorization
- Database standards
- Data integrity
Access control is the most important point for data security. It helps in restricting the database
from unauthorized users.
Data integrity is also one of the major points to check the complete data in the database. There
are two types of data integrity- Referential and Relational. Relational integrity test can be
performed on the record or data level while the Referential integrity test can be performed on the
relations between the tables.
Ethical, Privacy and Security Issues
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
There are so many ethical, privacy and security issues in the relational database management
systems. Following ethical issues can be arise for the security of the database-
- The admin can check the emails of the employees to check that the company’s
information is not going to be disclosed or leaked outside. It is most important point and
it can be done without informing the employees.
- Read the files on the user’s computers without informing them.
- Place the key loggers on the network to check the tying materials of the employees.
All the above ethical issues are legal as the administrator has right to check anything on the
company’s database as everything is related to company. It is completely legal.
The administrator can make other security standards also-
The administrator can limit the features on the user’s machine for the security of
the company’s database
The administrator can block some features that are not useful for all users and can impact on the
security standards. These selected features can be clocked for some users and can be unblocked
for other users. It is the best practise to secure the database from unauthorized users.
Ensure the protection of copyrights
The copyright protection is very important. The admin should notice on this area so that no one
can use the copyright detail anywhere else except the company’s documents. The company can
appoint one person or team to check these standards on regular basis. It is the most important
task as it may down the company’s image also if any wrong user shares the company’s detail for
illegal work.
Limit the access of the database
Complete database is not required for every user. It is important many times to restrict the data
from some users. Some portion of the database can be restricted from some users for the security
concern. The same data portion can be used by other users that have right to access that database.
This can be done by applying the access control technique.
Protect the important data of the users e.g. card details
It is very important to protect the user’s data that is given by users e.g. user’s personnel detail,
user’s card details etc. every user who come on our site have faith that his detail will not be
shared or leaked to anywhere. Therefore, there should be proper technique applied on this
portion in the database. The user’s detail should be protected carefully. It should not be visible to
anyone.
Encrypt the card details and then store into the database
systems. Following ethical issues can be arise for the security of the database-
- The admin can check the emails of the employees to check that the company’s
information is not going to be disclosed or leaked outside. It is most important point and
it can be done without informing the employees.
- Read the files on the user’s computers without informing them.
- Place the key loggers on the network to check the tying materials of the employees.
All the above ethical issues are legal as the administrator has right to check anything on the
company’s database as everything is related to company. It is completely legal.
The administrator can make other security standards also-
The administrator can limit the features on the user’s machine for the security of
the company’s database
The administrator can block some features that are not useful for all users and can impact on the
security standards. These selected features can be clocked for some users and can be unblocked
for other users. It is the best practise to secure the database from unauthorized users.
Ensure the protection of copyrights
The copyright protection is very important. The admin should notice on this area so that no one
can use the copyright detail anywhere else except the company’s documents. The company can
appoint one person or team to check these standards on regular basis. It is the most important
task as it may down the company’s image also if any wrong user shares the company’s detail for
illegal work.
Limit the access of the database
Complete database is not required for every user. It is important many times to restrict the data
from some users. Some portion of the database can be restricted from some users for the security
concern. The same data portion can be used by other users that have right to access that database.
This can be done by applying the access control technique.
Protect the important data of the users e.g. card details
It is very important to protect the user’s data that is given by users e.g. user’s personnel detail,
user’s card details etc. every user who come on our site have faith that his detail will not be
shared or leaked to anywhere. Therefore, there should be proper technique applied on this
portion in the database. The user’s detail should be protected carefully. It should not be visible to
anyone.
Encrypt the card details and then store into the database
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The important detail of the users should be stored into the database in the encrypted form. The
important detail can be encrypted before storing into the database and can be decrypted while
displaying to the users. It is the best practise to secure the important data. The card detail, user’s
password etc. can be stored in the same way.
Protect stakeholder’s detail.
Stakeholders are very important persons for every business. Their details should be protected
from the malicious users. The detail of the stakeholders can also be stored into the encrypted
form.
Use Antivirus
There are more viruses in the market that can damage the company’s data or leak important
information. To secure the database from these malicious programs, the company should buy
important anti viruses to protect the data. It is very important because if the important
information gets leaked outside, no one will trust on the company and the image of the company
will also suffer. Therefore, every organization should work on it and should follow the basic
security standards.
Sometimes hackers hack the detail and get the company’s detail and may get important offers of
the company. There are so many cases of this now a day. To escape from these types of
incidents, every organization should take good antivirus systems to protect the company’s
information.
All the above mentioned security standards may be very helpful to secure the company’s
important data. If all the above standards may be applied, no one can hack the database and
important detail will not be leaved outside. It may reduce the risks in the business. The company
will grow fast if the security standards are high in the company. It is the basic need to increase
the business. Without proper security techniques no one can grow in the IT.
(UKEssays. 2018)
References
important detail can be encrypted before storing into the database and can be decrypted while
displaying to the users. It is the best practise to secure the important data. The card detail, user’s
password etc. can be stored in the same way.
Protect stakeholder’s detail.
Stakeholders are very important persons for every business. Their details should be protected
from the malicious users. The detail of the stakeholders can also be stored into the encrypted
form.
Use Antivirus
There are more viruses in the market that can damage the company’s data or leak important
information. To secure the database from these malicious programs, the company should buy
important anti viruses to protect the data. It is very important because if the important
information gets leaked outside, no one will trust on the company and the image of the company
will also suffer. Therefore, every organization should work on it and should follow the basic
security standards.
Sometimes hackers hack the detail and get the company’s detail and may get important offers of
the company. There are so many cases of this now a day. To escape from these types of
incidents, every organization should take good antivirus systems to protect the company’s
information.
All the above mentioned security standards may be very helpful to secure the company’s
important data. If all the above standards may be applied, no one can hack the database and
important detail will not be leaved outside. It may reduce the risks in the business. The company
will grow fast if the security standards are high in the company. It is the basic need to increase
the business. Without proper security techniques no one can grow in the IT.
(UKEssays. 2018)
References

Paul Litwin. (n.d.). Fundamentals of Relational Database Design. Retrieved from
http://www.deeptraining.com/litwin/dbdesign/FundamentalsOfRelationalDatabaseDesign
.aspx
Elmasri, Navathe. Fundamental of Database Systems Sixth Edition. 2011
Cinergix Pty Ltd. (2011). Ultimate Guide to ER Diagrams. Retrieved from
http://creately.com/blog/diagrams/er-diagrams-tutorial/
UKEssays. (2018). Database Management: Law, Ethics and Security. Retrieved from
https://www.ukessays.com/essays/computer-science/database-management-law-ethics-
9552.php
http://www.deeptraining.com/litwin/dbdesign/FundamentalsOfRelationalDatabaseDesign
.aspx
Elmasri, Navathe. Fundamental of Database Systems Sixth Edition. 2011
Cinergix Pty Ltd. (2011). Ultimate Guide to ER Diagrams. Retrieved from
http://creately.com/blog/diagrams/er-diagrams-tutorial/
UKEssays. (2018). Database Management: Law, Ethics and Security. Retrieved from
https://www.ukessays.com/essays/computer-science/database-management-law-ethics-
9552.php
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



