ACCT6001 Accounting Information Systems: Employee Database Application
VerifiedAdded on 2023/06/12
|6
|731
|73
Report
AI Summary
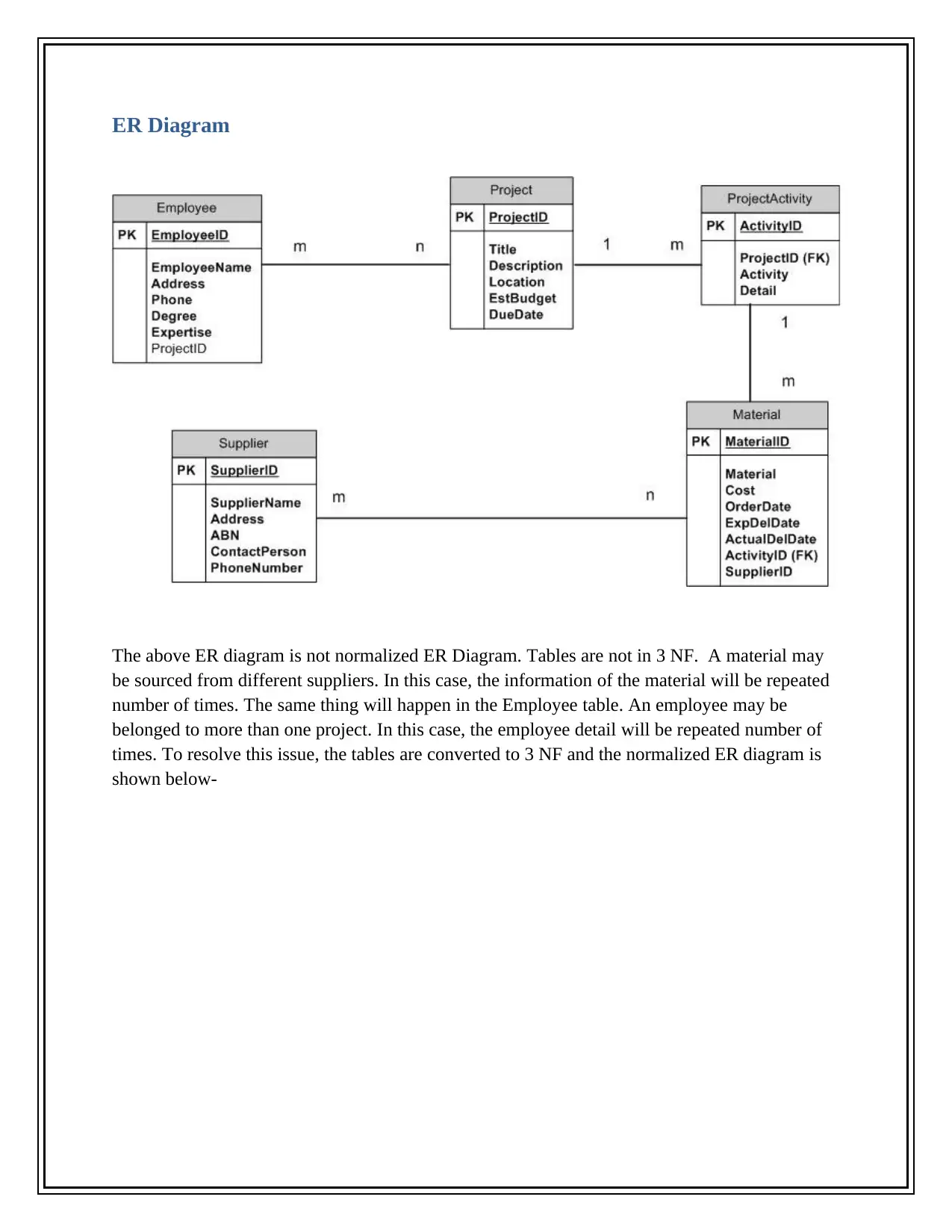
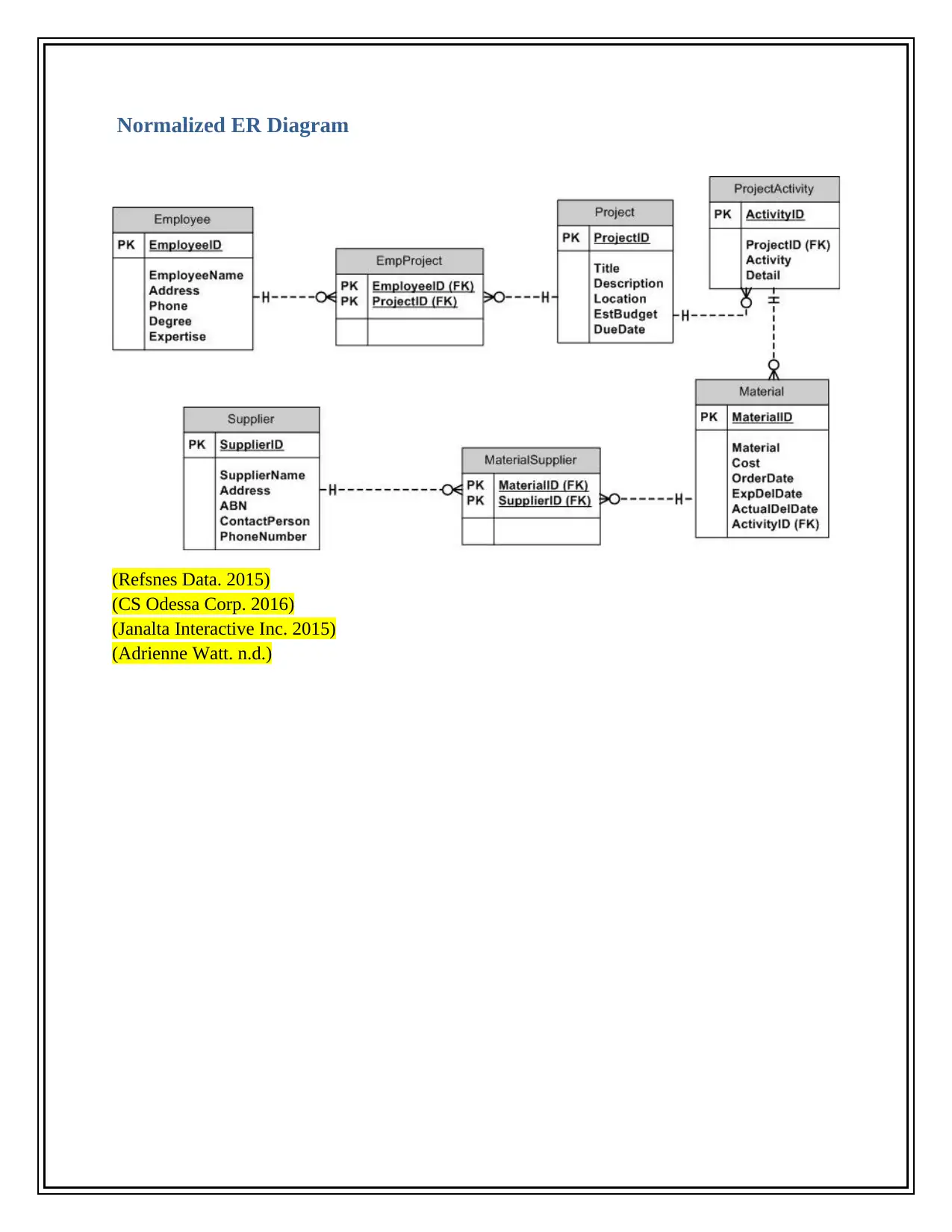
This report provides a comprehensive overview of the database design for an employee database, starting from an unnormalized ER diagram to a normalized relational database in 3NF. It discusses the importance of database usage over file systems, highlighting features like searching, querying, user access control, and performance analysis. The report includes detailed explanations of IT controls such as access control, data backup, recovery techniques, database integrity, security, and authorization. Furthermore, it addresses ethical, privacy, and security issues related to database management, including email monitoring, keyloggers, firewall usage, user access limitations, data encryption, and copyright protection. The report emphasizes the significance of these measures in ensuring data accuracy, reliability, and security within an organization.
1 out of 6










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)