Design and Report: Active Directory for College Campus
VerifiedAdded on 2019/11/25
|8
|1319
|348
Report
AI Summary
This report outlines the design and implementation of a Windows Server Active Directory for a large, distributed college campus environment. It details the analysis of organizational requirements, the development and configuration of group policies for different user types, and the benefits of using Windows Server, such as remote user management and ease of administration. The report covers the design strategy, including considerations for data center locations, group policy enforcement by the general manager, and the use of a single domain for Active Directory management. It also discusses the configuration of group policies for remote access, password settings, and mandatory corporate wallpapers for staff computers. Furthermore, it explores the installation of application software from the server and the implementation of authentication techniques using a DNS server, as well as the placement of the domain controller and the management of network node connectivity. The report concludes with a summary of the design, highlighting the importance of group policy management, the benefits of a single domain for efficient workflow, and the cost-effective server organization for secure network performance.

Running head: DESIGN AND REPORT
Design and Report
Name of the Student
Name of the University
Author’s Note
Design and Report
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DESIGN AND REPORT
Table of Contents
Introduction..........................................................................................................................2
Design of the active Directory.............................................................................................2
Discussion............................................................................................................................3
Configuration of the group policies.................................................................................3
Installation of application software.................................................................................3
Conclusion...........................................................................................................................4
Bibliography........................................................................................................................6
DESIGN AND REPORT
Table of Contents
Introduction..........................................................................................................................2
Design of the active Directory.............................................................................................2
Discussion............................................................................................................................3
Configuration of the group policies.................................................................................3
Installation of application software.................................................................................3
Conclusion...........................................................................................................................4
Bibliography........................................................................................................................6
2
DESIGN AND REPORT
Introduction
The report is prepared to propose a corporate structure of a large distributed environment
of a college campus using a windows server active directory. The design is prepared after
analysis of the requirement of the organization and development of the group policies for the
different types of users. The facility that the organization can gain such as the management of the
remote users, ease of administration, etc. with the deployment of the windows server is given in
the report. The strategy used for the design of the Microsoft Windows Active Directory is also
given in the report. The cost of deployment of the design is estimated and the authentication
methods used for
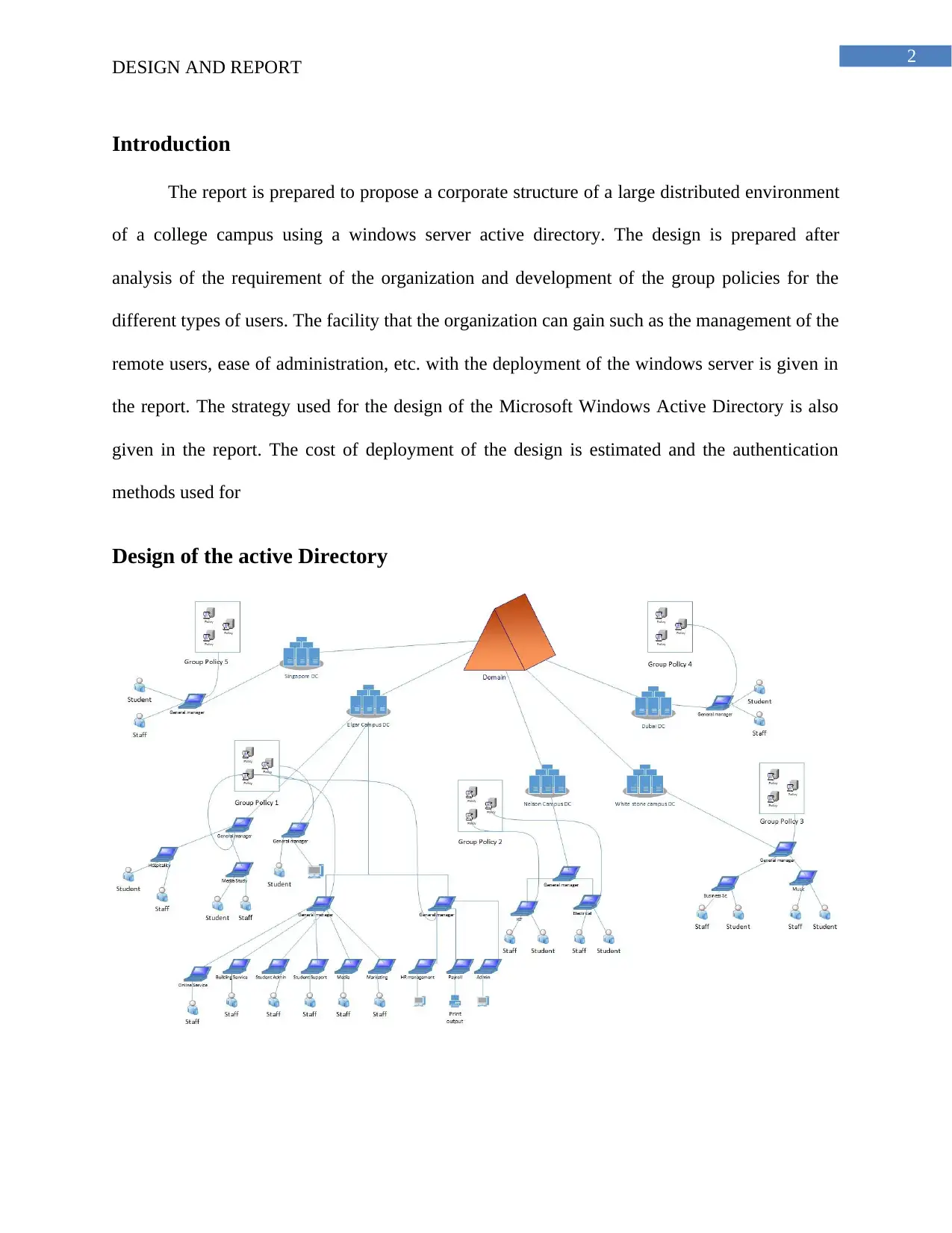
Design of the active Directory
DESIGN AND REPORT
Introduction
The report is prepared to propose a corporate structure of a large distributed environment
of a college campus using a windows server active directory. The design is prepared after
analysis of the requirement of the organization and development of the group policies for the
different types of users. The facility that the organization can gain such as the management of the
remote users, ease of administration, etc. with the deployment of the windows server is given in
the report. The strategy used for the design of the Microsoft Windows Active Directory is also
given in the report. The cost of deployment of the design is estimated and the authentication
methods used for
Design of the active Directory
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DESIGN AND REPORT
Discussion
The data centers are installed in different location of the college and the general manager
is responsible for the configuration of the group policy. Each of the campus have different group
policy and it is maintained for securing the data center from unauthorized access in the network.
Different group policy is used for different location and it is the responsibility of the general
manager to enforce the group policy for the management of the campus network. The active
directory is designed for the management of the windows server using a single domain. There are
different constraints that are required for designing the active directory such as setting the
wallpaper and a special software is installed in the server for removing the needs of deployment
of the software manually. The group policy is developed for the management of the print queues
and remote management of the authentication of the users using the windows server.
Configuration of the group policies
The group policies are required to be configured for the enabling remote access to the
windows server and setting up password for connecting with the network. The group policy is
required to be setup for different users of the network such as the student and the staffs. The staff
computers should have mandatory corporate wallpapers and this can be applied using the
“prevent changing wallpaper” option in the group policy. The wallpaper that is required to be
used for the PCs is required to be specified otherwise the user can right click on any picture and
set it as the wallpaper of the PC. The wallpaper that is to be set should have proper resolution or
it is required to be fixed using the Easy fix option available on the windows server 2012.
Installation of application software
Special software should be installed in the server in order to manage the finance and the
payroll of the organization. The application can be installed in the client nodes from the windows
DESIGN AND REPORT
Discussion
The data centers are installed in different location of the college and the general manager
is responsible for the configuration of the group policy. Each of the campus have different group
policy and it is maintained for securing the data center from unauthorized access in the network.
Different group policy is used for different location and it is the responsibility of the general
manager to enforce the group policy for the management of the campus network. The active
directory is designed for the management of the windows server using a single domain. There are
different constraints that are required for designing the active directory such as setting the
wallpaper and a special software is installed in the server for removing the needs of deployment
of the software manually. The group policy is developed for the management of the print queues
and remote management of the authentication of the users using the windows server.
Configuration of the group policies
The group policies are required to be configured for the enabling remote access to the
windows server and setting up password for connecting with the network. The group policy is
required to be setup for different users of the network such as the student and the staffs. The staff
computers should have mandatory corporate wallpapers and this can be applied using the
“prevent changing wallpaper” option in the group policy. The wallpaper that is required to be
used for the PCs is required to be specified otherwise the user can right click on any picture and
set it as the wallpaper of the PC. The wallpaper that is to be set should have proper resolution or
it is required to be fixed using the Easy fix option available on the windows server 2012.
Installation of application software
Special software should be installed in the server in order to manage the finance and the
payroll of the organization. The application can be installed in the client nodes from the windows
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
DESIGN AND REPORT
server by configuring the group policy from the group policy management console present in the
windows server 2012.
Implementation of the authentication techniques
The deployment of the DNS server is essential for keeping singular verification process
and strategies with specific clients. In the system network, the clients can have tweaked
passphrase and secret key security from pariahs. Besides, the server get to is confined to an
arrangement of managers. The Box Hill Institute ought to have better execution of server
alongside cloud administration of empowering branch savvy movement prioritization and
planning. The cost-viability lies in single windows server organization with numerous client
administration for security, protection, and assurance checking also. There are 1000 staffs inside
a few branches and grounds. Accordingly, windows server with individual DNS arrangement
will help in dividing the whole work process with appropriate and capable way.
Placement of the domain controller
A single domain controller is used for the management of the windows active directory
and the individual forest is controlled using the DNS server. The placement and mapping of the
controller is dependent and it is essential to configure the active directory and the response time
should be improved. The objects should be hided from the access of the users and the
connectivity of the nodes in the network should be controlled.
Conclusion
From the above report it is found that for the designing of the active directory of the
windows server the management of the group policy is important. The dynamic catalog is
generally having motivations to be outlined as it manages disseminated engineering of any
DESIGN AND REPORT
server by configuring the group policy from the group policy management console present in the
windows server 2012.
Implementation of the authentication techniques
The deployment of the DNS server is essential for keeping singular verification process
and strategies with specific clients. In the system network, the clients can have tweaked
passphrase and secret key security from pariahs. Besides, the server get to is confined to an
arrangement of managers. The Box Hill Institute ought to have better execution of server
alongside cloud administration of empowering branch savvy movement prioritization and
planning. The cost-viability lies in single windows server organization with numerous client
administration for security, protection, and assurance checking also. There are 1000 staffs inside
a few branches and grounds. Accordingly, windows server with individual DNS arrangement
will help in dividing the whole work process with appropriate and capable way.
Placement of the domain controller
A single domain controller is used for the management of the windows active directory
and the individual forest is controlled using the DNS server. The placement and mapping of the
controller is dependent and it is essential to configure the active directory and the response time
should be improved. The objects should be hided from the access of the users and the
connectivity of the nodes in the network should be controlled.
Conclusion
From the above report it is found that for the designing of the active directory of the
windows server the management of the group policy is important. The dynamic catalog is
generally having motivations to be outlined as it manages disseminated engineering of any

5
DESIGN AND REPORT
association. The staffs and the student working on the Box Hill Institute can be easily managed
with the implementation of the group policy in the network. The different branches of the
organization can be operated from a central point by implementation of the cloud servers and
enabling remote access of the network resources. Also, the dynamic registry is outlined with DS
in one space; henceforth, the work procedure is fused according to the authoritative structure. At
long last, the structure of the active directory is used for server organization with cost oversaw
framework execution.
DESIGN AND REPORT
association. The staffs and the student working on the Box Hill Institute can be easily managed
with the implementation of the group policy in the network. The different branches of the
organization can be operated from a central point by implementation of the cloud servers and
enabling remote access of the network resources. Also, the dynamic registry is outlined with DS
in one space; henceforth, the work procedure is fused according to the authoritative structure. At
long last, the structure of the active directory is used for server organization with cost oversaw
framework execution.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
DESIGN AND REPORT
Bibliography
[1].Alvarez, R., Mirzoev, T., Gowan, A., Henderson, B., & Kruck, S. E. (2017). Learning
Laboratories as Services in Private Cloud Deployment. Journal of Computer Information
Systems, 1-9.
[2].Bishop, G. H., Boyer, S., Buhler, M., Gerthoffer, A., & Larish, B. (2015). Defending
cyberspace with software-defined networks. Journal of Information Warfare, 14(2), 98-
114.
[3].Ferrara, A. L., Squicciarini, A., Liao, C., & Nguyen, T. L. (2017, July). Toward group-
based user-attribute policies in azure-like access control systems. In IFIP Annual
Conference on Data and Applications Security and Privacy (pp. 349-361). Springer,
Cham.
[4].Hernoud, M. S., Pierce, E. J., & Dunn, D. D. (2017). U.S. Patent Application No.
15/443,796.
[5].Herunde, R., Gonugunta, S., Madden, J., Middleton, E., Vaillancourt, O., & Kamath, V.
T. (2015). U.S. Patent Application No. 14/639,691.
[6].Marcus, J. B., Eldridge, A. D., Kern Jr, D. S., Kerrigan, M. J., Mancuso, P. C., &
Paganetti, R. J. (2017). U.S. Patent No. 9,690,920. Washington, DC: U.S. Patent and
Trademark Office.
[7].Rai, P., Hooda, M., Dhir, S., Bhatia, M., & Garg, A. (2015, March). A prologue of
JENKINS with comparative scrutiny of various software integration tools. In Computing
for Sustainable Global Development (INDIACom), 2015 2nd International Conference
on (pp. 201-205). IEEE.
DESIGN AND REPORT
Bibliography
[1].Alvarez, R., Mirzoev, T., Gowan, A., Henderson, B., & Kruck, S. E. (2017). Learning
Laboratories as Services in Private Cloud Deployment. Journal of Computer Information
Systems, 1-9.
[2].Bishop, G. H., Boyer, S., Buhler, M., Gerthoffer, A., & Larish, B. (2015). Defending
cyberspace with software-defined networks. Journal of Information Warfare, 14(2), 98-
114.
[3].Ferrara, A. L., Squicciarini, A., Liao, C., & Nguyen, T. L. (2017, July). Toward group-
based user-attribute policies in azure-like access control systems. In IFIP Annual
Conference on Data and Applications Security and Privacy (pp. 349-361). Springer,
Cham.
[4].Hernoud, M. S., Pierce, E. J., & Dunn, D. D. (2017). U.S. Patent Application No.
15/443,796.
[5].Herunde, R., Gonugunta, S., Madden, J., Middleton, E., Vaillancourt, O., & Kamath, V.
T. (2015). U.S. Patent Application No. 14/639,691.
[6].Marcus, J. B., Eldridge, A. D., Kern Jr, D. S., Kerrigan, M. J., Mancuso, P. C., &
Paganetti, R. J. (2017). U.S. Patent No. 9,690,920. Washington, DC: U.S. Patent and
Trademark Office.
[7].Rai, P., Hooda, M., Dhir, S., Bhatia, M., & Garg, A. (2015, March). A prologue of
JENKINS with comparative scrutiny of various software integration tools. In Computing
for Sustainable Global Development (INDIACom), 2015 2nd International Conference
on (pp. 201-205). IEEE.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
DESIGN AND REPORT
[8].Voronkov, K. P., Deshevykh, S. N., & Yablokov, V. V. (2014). U.S. Patent No.
8,839,234. Washington, DC: U.S. Patent and Trademark Office.
[9].Weber, J., Nutt, D., Ott, J. S., & Hale, J. M. (2014). U.S. Patent No. 8,762,701.
Washington, DC: U.S. Patent and Trademark Office.
[10]. Wueest, C. (2014). Targeted attacks against the energy sector. Symantec Security
Response, Mountain View, CA.
DESIGN AND REPORT
[8].Voronkov, K. P., Deshevykh, S. N., & Yablokov, V. V. (2014). U.S. Patent No.
8,839,234. Washington, DC: U.S. Patent and Trademark Office.
[9].Weber, J., Nutt, D., Ott, J. S., & Hale, J. M. (2014). U.S. Patent No. 8,762,701.
Washington, DC: U.S. Patent and Trademark Office.
[10]. Wueest, C. (2014). Targeted attacks against the energy sector. Symantec Security
Response, Mountain View, CA.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





