Active Directory Security: Windows Server & Domain Controller Report
VerifiedAdded on 2020/05/11
|6
|923
|74
Report
AI Summary
This report provides an overview of Active Directory and its crucial role in Windows security. It delves into the core aspects of Active Directory security, including administrative security, account password and group security, and domain controller security. The report highlights key features such as Privileged Access Management (PAM), Azure Active Directory join, and Microsoft passport, emphasizing their contributions to enhancing security in modern IT environments. It also addresses the evolution of File Replication Services (FRS) and the importance of maintaining up-to-date Windows 10 security measures. A lab activity is described, guiding the reader through the process of setting up a virtual machine and installing Windows Server with a domain controller to practically study Active Directory services. The report concludes by underscoring the significance of Active Directory in system administration and its role in simplifying computer management within a given environment.

Running head: Active Directory and its Security 1
ACTIVE DIRECTORY AND ITS SECURITY
Author’s name
Institution affiliation
ACTIVE DIRECTORY AND ITS SECURITY
Author’s name
Institution affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Active Directory and its Security 2
Introduction
Active directory is a directory service developed by Microsoft corporation for windows domain
network services (Edger Jr, 2015). It was invented by Microsoft and presently operates on
Microsoft Windows server platform and Microsoft Azure which is the Microsoft cloud platform.
It though can be used flawlessly to assimilate various versions of windows operating system, this
is based on the fact that, Microsoft structured and designed it on open standards (Hassan, 2017).
Active directory is therefore essential for ensuring windows security and improving performance
on several other related operating systems upon incorporation. Windows server can be steadily
hosted both in the clouds and on premises; this is made possible by the new features employed
by the Active Directory Domain Services (ADDS) (Li, C. (2015)).
Active directory security is in terms of Administrative security, Account password and group
security and Domain controller security.
Active directory has brought about dependable new features that have impressively made
Microsoft cloud platform to be right-hand (Babin, R., & Halilovic, B. (2017)). The features such
as Privileged Access Management (PAM) help in extenuating security disquiets for Active
Security environments, especially the spear phishing theft techniques and bouts. It is through
PAM that the solicitation of administrative policies and configuration was put into practice using
Microsoft Identity Manager (MIM). Another feature is the Azure active directory join; this
feature encompasses identity proficiency for enterprise or commercial customer experiences to
customize personal devices (Hassan, N. A. (2017)).
Active directory also fetched on course the Microsoft passport feature for key based
authentication methodology organization for users, this feature goes beyond passwords. It mostly
Introduction
Active directory is a directory service developed by Microsoft corporation for windows domain
network services (Edger Jr, 2015). It was invented by Microsoft and presently operates on
Microsoft Windows server platform and Microsoft Azure which is the Microsoft cloud platform.
It though can be used flawlessly to assimilate various versions of windows operating system, this
is based on the fact that, Microsoft structured and designed it on open standards (Hassan, 2017).
Active directory is therefore essential for ensuring windows security and improving performance
on several other related operating systems upon incorporation. Windows server can be steadily
hosted both in the clouds and on premises; this is made possible by the new features employed
by the Active Directory Domain Services (ADDS) (Li, C. (2015)).
Active directory security is in terms of Administrative security, Account password and group
security and Domain controller security.
Active directory has brought about dependable new features that have impressively made
Microsoft cloud platform to be right-hand (Babin, R., & Halilovic, B. (2017)). The features such
as Privileged Access Management (PAM) help in extenuating security disquiets for Active
Security environments, especially the spear phishing theft techniques and bouts. It is through
PAM that the solicitation of administrative policies and configuration was put into practice using
Microsoft Identity Manager (MIM). Another feature is the Azure active directory join; this
feature encompasses identity proficiency for enterprise or commercial customer experiences to
customize personal devices (Hassan, N. A. (2017)).
Active directory also fetched on course the Microsoft passport feature for key based
authentication methodology organization for users, this feature goes beyond passwords. It mostly

Active Directory and its Security 3
relies on theft and phish-resistant badges. File Replication Services (FRS) has been saved from
depreciating and total dis-functioning, windows server 2003 operating system is nowadays not
functional, active directory helped in raising the non- braced windows server to windows server
2008 hence preventing domain controller from being added to the environment. Distributed File
Service replication is used to replicate System Volume (SYSVOL) innards amongst domain
controllers. This has brought creditable improvements on the ease to upgrade domain controllers
of various versions of windows operating system.
Window 10 securities is standard, but cyber-attacks cannot be ruled out, with the current
advancements in the hacking and penetration field, Microsoft has not taken chance to expose any
loophole for attacks (Hassan, N. A. (2017)). Attacks can be viruses, spyware, worms and adware.
A Windows 10 security feature involves installation of the latest version of Microsoft defender
anti-virus software that keeps malicious software off wherever an attack is eminent. Microsoft
defender protects windows from an attack by prevention and also by detecting the virus then
removing it.
Lab activity
When conducting a lab activity on windows security basing arguments on the role of active
directory services, we first need a copy of windows server which can be downloaded. The
second thing we need it some visualization software, preferably virtual box. After getting all the
above; we will then open the visualization software, click on ‘network’ in the Virtual Box
preferences.
relies on theft and phish-resistant badges. File Replication Services (FRS) has been saved from
depreciating and total dis-functioning, windows server 2003 operating system is nowadays not
functional, active directory helped in raising the non- braced windows server to windows server
2008 hence preventing domain controller from being added to the environment. Distributed File
Service replication is used to replicate System Volume (SYSVOL) innards amongst domain
controllers. This has brought creditable improvements on the ease to upgrade domain controllers
of various versions of windows operating system.
Window 10 securities is standard, but cyber-attacks cannot be ruled out, with the current
advancements in the hacking and penetration field, Microsoft has not taken chance to expose any
loophole for attacks (Hassan, N. A. (2017)). Attacks can be viruses, spyware, worms and adware.
A Windows 10 security feature involves installation of the latest version of Microsoft defender
anti-virus software that keeps malicious software off wherever an attack is eminent. Microsoft
defender protects windows from an attack by prevention and also by detecting the virus then
removing it.
Lab activity
When conducting a lab activity on windows security basing arguments on the role of active
directory services, we first need a copy of windows server which can be downloaded. The
second thing we need it some visualization software, preferably virtual box. After getting all the
above; we will then open the visualization software, click on ‘network’ in the Virtual Box
preferences.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Active Directory and its Security 4
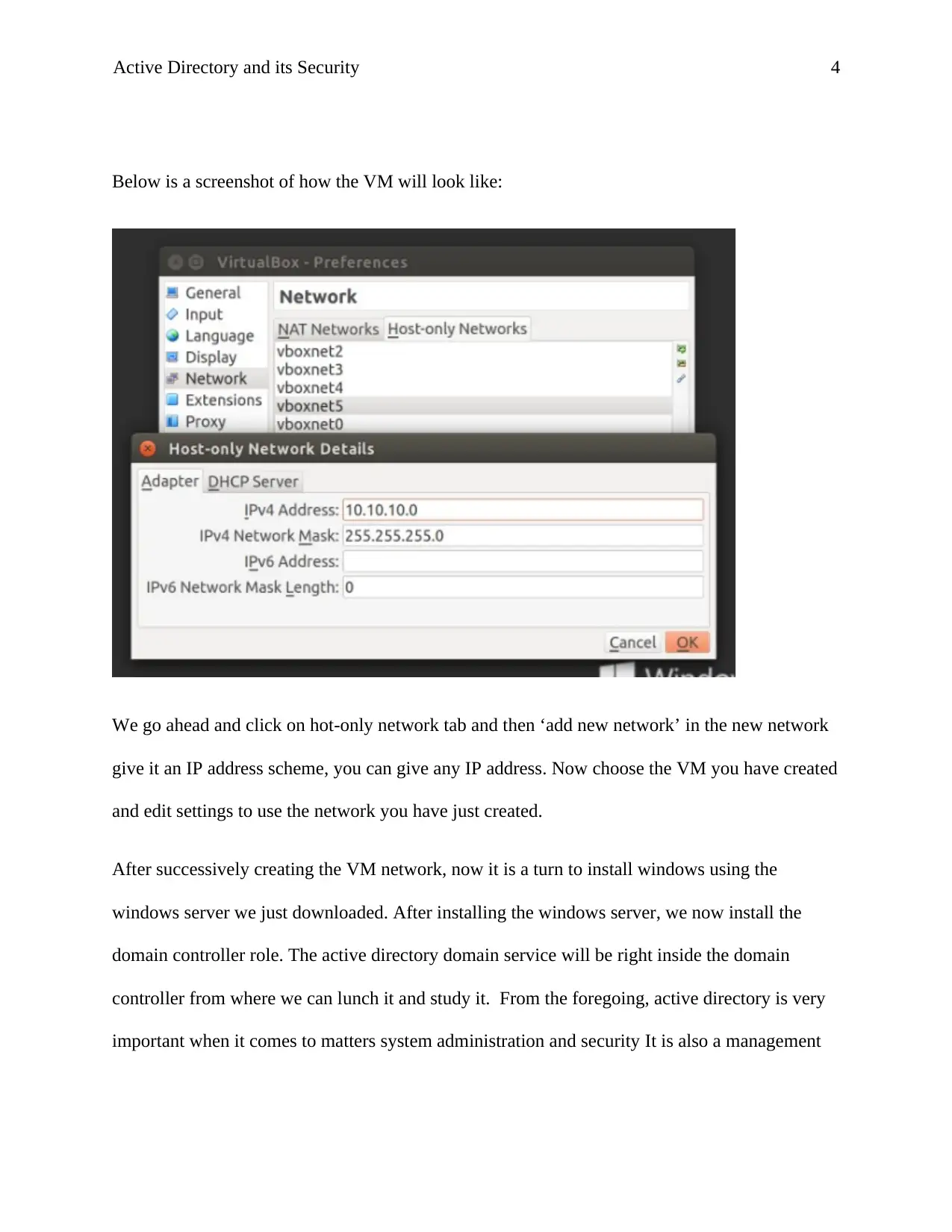
Below is a screenshot of how the VM will look like:
We go ahead and click on hot-only network tab and then ‘add new network’ in the new network
give it an IP address scheme, you can give any IP address. Now choose the VM you have created
and edit settings to use the network you have just created.
After successively creating the VM network, now it is a turn to install windows using the
windows server we just downloaded. After installing the windows server, we now install the
domain controller role. The active directory domain service will be right inside the domain
controller from where we can lunch it and study it. From the foregoing, active directory is very
important when it comes to matters system administration and security It is also a management
Below is a screenshot of how the VM will look like:
We go ahead and click on hot-only network tab and then ‘add new network’ in the new network
give it an IP address scheme, you can give any IP address. Now choose the VM you have created
and edit settings to use the network you have just created.
After successively creating the VM network, now it is a turn to install windows using the
windows server we just downloaded. After installing the windows server, we now install the
domain controller role. The active directory domain service will be right inside the domain
controller from where we can lunch it and study it. From the foregoing, active directory is very
important when it comes to matters system administration and security It is also a management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Active Directory and its Security 5
solution that allows for easier management all of the computers in a particular given
environment and therefore an important system administration factor.
The various models should be implemented effectively in accordance with policies most so on
system security to enhance better administration of a particular system.
The third and fourth references are peer reviewed.
solution that allows for easier management all of the computers in a particular given
environment and therefore an important system administration factor.
The various models should be implemented effectively in accordance with policies most so on
system security to enhance better administration of a particular system.
The third and fourth references are peer reviewed.

Active Directory and its Security 6
References
Edger Jr, C. S. (2015). Active Directory. Enterprise Mac Administrator's Guide , pp. 91-134.
Hassan, N. A. (2017). Windows Security. In Digital Privacy and Security Using Windos, pp.
103-122.
Babin, R., & Halilovic, B. (2017). Cloud Computing e-Communication Services in the
University Environment. Information Systems Education Journal, 15(1), 55.
Li, C. (2015). Penetration Testing Curriculum Development in Practice. Journal of Information
Technology Education: Innovations in Practice, 14, 85-99.
References
Edger Jr, C. S. (2015). Active Directory. Enterprise Mac Administrator's Guide , pp. 91-134.
Hassan, N. A. (2017). Windows Security. In Digital Privacy and Security Using Windos, pp.
103-122.
Babin, R., & Halilovic, B. (2017). Cloud Computing e-Communication Services in the
University Environment. Information Systems Education Journal, 15(1), 55.
Li, C. (2015). Penetration Testing Curriculum Development in Practice. Journal of Information
Technology Education: Innovations in Practice, 14, 85-99.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





