ADS612 Active Directory: VPN Configuration in Windows Server 2012 R2
VerifiedAdded on 2023/01/20
|14
|1502
|55
Case Study
AI Summary
This case study provides an overview of VPN configuration within Windows Server 2012 R2, emphasizing secure remote access and network security. It covers the structure and features of Active Directory Services (ADS), including domains, trees, and forests, and explains how Remote Access (RA) features facilitate office VPN connections. The study also differentiates between Share and NTFS permissions and outlines the steps for configuring a VPN, including enabling IPv4 forwarding, SSL certificates, and authentication methods. It further discusses the use of PowerShell for modifying remote access information and highlights the importance of logging for troubleshooting. The document concludes by reiterating the benefits of VPN implementations in Windows Server 2012 R2, offering a cost-effective and manageable solution for secure remote access.

TITLE: VPN configuration in Windows Server 2012 R2
VPN configuration in Windows Server 2012 R2
Student’s ID:
VPN configuration in Windows Server 2012 R2
Student’s ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
The VPN server is always advisable to configure it internal and external interfaces. This
configurations enhances a very good security setup since in most cases external network interface
have restricted firewalls as compared to the internal interface. It also requires more attention since
the configuration of the two networks require great attention on the server for security purposes.
(Subandi, & Aryani, 2019).
Introduction
VPN implementations using Windows Server 2012 R2 for secure remote access comes with so
many positive implications. The security is always assured on client-based VPN solution. Besides,
Windows-based VPN servers are flexible in terms of deployment, cost effective in installations and
maintenance, and also the manage is very easy since it requires less attention. The VPN server is
always advisable to configure it internal and external interfaces. This configurations enhances a
very good security setup since in most cases external network interface have restricted firewalls as
compared to the internal interface. It also requires more attention since the configuration of the two
networks require great attention on the server for security purposes. (Velayudhan, Vattem, &
Ghanwani, 2019).
The VPN server is always advisable to configure it internal and external interfaces. This
configurations enhances a very good security setup since in most cases external network interface
have restricted firewalls as compared to the internal interface. It also requires more attention since
the configuration of the two networks require great attention on the server for security purposes.
(Subandi, & Aryani, 2019).
Introduction
VPN implementations using Windows Server 2012 R2 for secure remote access comes with so
many positive implications. The security is always assured on client-based VPN solution. Besides,
Windows-based VPN servers are flexible in terms of deployment, cost effective in installations and
maintenance, and also the manage is very easy since it requires less attention. The VPN server is
always advisable to configure it internal and external interfaces. This configurations enhances a
very good security setup since in most cases external network interface have restricted firewalls as
compared to the internal interface. It also requires more attention since the configuration of the two
networks require great attention on the server for security purposes. (Velayudhan, Vattem, &
Ghanwani, 2019).

TASK 1
Structure and features of AD Services
An Active Directory Service (ADS) is a Microsoft database services which run on the window
server to mainly control the access to the network resources. It stores data as objects, that is, user,
group or devices like printers as objects. It also enhances security through authentication and also
management is assured (Bhatnagar, Som, & Khatri, 2019, April).
Active Directory Domain Services utilizes the structure of the domains, trees and the forests to
coordinate and ensure proper network elements. The objects will share AD database because they
are under one directory under the same domain name. Domains have a domain name system (DNS)
structure (Lermant, P. 2019).
A tree is a structure consisting of one or more domains grouped together and it uses name-space to
collect the domains in the logical hierarchy. Tree structure allows two domains to securely connects
and have a very good relations in terms of functionality. By use of this criteria, so many domains
can be trusted because the first one trust the second and the second trust the third and the chains just
continues like that (Velayudhan, Vattem, & Ghanwani, 2019).
A forest is a group of multiple trees. It consists of a shared catalogs, domain configurations, and
even directory schema which defines class and characteristic of the object in the forest structure.
Moreover, catalog servers will provide the list of all the objects in a forest (Lermant, P. 2019).
Structure and features of AD Services
An Active Directory Service (ADS) is a Microsoft database services which run on the window
server to mainly control the access to the network resources. It stores data as objects, that is, user,
group or devices like printers as objects. It also enhances security through authentication and also
management is assured (Bhatnagar, Som, & Khatri, 2019, April).
Active Directory Domain Services utilizes the structure of the domains, trees and the forests to
coordinate and ensure proper network elements. The objects will share AD database because they
are under one directory under the same domain name. Domains have a domain name system (DNS)
structure (Lermant, P. 2019).
A tree is a structure consisting of one or more domains grouped together and it uses name-space to
collect the domains in the logical hierarchy. Tree structure allows two domains to securely connects
and have a very good relations in terms of functionality. By use of this criteria, so many domains
can be trusted because the first one trust the second and the second trust the third and the chains just
continues like that (Velayudhan, Vattem, & Ghanwani, 2019).
A forest is a group of multiple trees. It consists of a shared catalogs, domain configurations, and
even directory schema which defines class and characteristic of the object in the forest structure.
Moreover, catalog servers will provide the list of all the objects in a forest (Lermant, P. 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TASK 2
RA feature and how it helps in office through VPN
Remote access server is mainly used to group all the technology features of the server. Technical it
is like a pool where it contains all the necessary features of the server. In windows server 2012 R2,
utilizes this features as the gateway hence it will enhance the functionality. VPN is very simple and
direct to installation and configuration on Windows Server 2012 R2. You can either run manually or
use Powershell Anywhere Access wizard set up and just select the VPN option on the screen. All the
clients inside the company can join the server but also those who are outside can join using Remote
Domain Join. It will only happen if you enable VPN on servers essentials (Subandi, & Aryani,
2019).
RA feature and how it helps in office through VPN
Remote access server is mainly used to group all the technology features of the server. Technical it
is like a pool where it contains all the necessary features of the server. In windows server 2012 R2,
utilizes this features as the gateway hence it will enhance the functionality. VPN is very simple and
direct to installation and configuration on Windows Server 2012 R2. You can either run manually or
use Powershell Anywhere Access wizard set up and just select the VPN option on the screen. All the
clients inside the company can join the server but also those who are outside can join using Remote
Domain Join. It will only happen if you enable VPN on servers essentials (Subandi, & Aryani,
2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 3
Share and NTFS permissions
Data sharing is a process of moving data from one place to another place where the second party
need that data to use. Share and NTFS is very different from one another but they perform the same
function. NTFS permissions is a technique where the file system knows how to organize the data,
and how to store them in an attached files. It is a new technology used by windows to store there
files. Share permissions is just simple sharing of a file from one folder to the other one. However,
share permissions and NTFS permissions can work together without any interference but different
functionality (Subandi, & Aryani, 2019).
Share and NTFS permissions
Data sharing is a process of moving data from one place to another place where the second party
need that data to use. Share and NTFS is very different from one another but they perform the same
function. NTFS permissions is a technique where the file system knows how to organize the data,
and how to store them in an attached files. It is a new technology used by windows to store there
files. Share permissions is just simple sharing of a file from one folder to the other one. However,
share permissions and NTFS permissions can work together without any interference but different
functionality (Subandi, & Aryani, 2019).

TASK 6
VPN configuration
VPN implementations using Windows Server 2012 R2 for secure remote access comes with so
many positive implications. The security is always assured on client-based VPN solution. Besides,
Windows-based VPN servers are flexible in terms of deployment, cost effective in installations and
maintenance, and also the manage is very easy since it requires less attention. The VPN server is
always advisable to configure it internal and external interfaces. This configurations enhances a
very good security setup since in most cases external network interface have restricted firewalls as
compared to the internal interface. It also requires more attention since the configuration of the two
networks require great attention on the server for security purposes. (Bhatnagar, Som, & Khatri,
2019, April).
Configuration steps
VPN is very simple and direct in installation and configuration on Windows Server 2012
R2. You can either run manually or use powershell Anywhere Access wizard set up and just
select the VPN option on the screen. All the clients inside the company can join the server
but also those who are outside can join using Remote Domain Join. It will only happen if
you enable VPN on servers essentials (Subandi, & Aryani, 2019).
VPN configuration
VPN implementations using Windows Server 2012 R2 for secure remote access comes with so
many positive implications. The security is always assured on client-based VPN solution. Besides,
Windows-based VPN servers are flexible in terms of deployment, cost effective in installations and
maintenance, and also the manage is very easy since it requires less attention. The VPN server is
always advisable to configure it internal and external interfaces. This configurations enhances a
very good security setup since in most cases external network interface have restricted firewalls as
compared to the internal interface. It also requires more attention since the configuration of the two
networks require great attention on the server for security purposes. (Bhatnagar, Som, & Khatri,
2019, April).
Configuration steps
VPN is very simple and direct in installation and configuration on Windows Server 2012
R2. You can either run manually or use powershell Anywhere Access wizard set up and just
select the VPN option on the screen. All the clients inside the company can join the server
but also those who are outside can join using Remote Domain Join. It will only happen if
you enable VPN on servers essentials (Subandi, & Aryani, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

We have to now check the default settings of VPN on the server. Click on routing and
remote access manager, then you right click on server name. Finally select the properties
and always make sure IPv4 is enabled on general tab (Bhatnagar, Som, & Khatri, 2019,
April).
On the other hand, security tab consists of the Authentication methods ans also SSL
certificates binding (Velayudhan, Vattem, & Ghanwani, 2019).
remote access manager, then you right click on server name. Finally select the properties
and always make sure IPv4 is enabled on general tab (Bhatnagar, Som, & Khatri, 2019,
April).
On the other hand, security tab consists of the Authentication methods ans also SSL
certificates binding (Velayudhan, Vattem, & Ghanwani, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

On the security tab, we can confirm authentication methods by click a tick. We should
enable VPN on SSL because it displays certificate active and we should restrict all ports
except port 443 on the SSL certificate binding section (Lermant, P. 2019).
Next is on IPv4 where you have to enable forwarding. (Lermant, P. 2019).
enable VPN on SSL because it displays certificate active and we should restrict all ports
except port 443 on the SSL certificate binding section (Lermant, P. 2019).
Next is on IPv4 where you have to enable forwarding. (Lermant, P. 2019).

On the IPv6 tab, just click on enable in all the options. (Subandi, & Aryani, 2019).
The IKEv2 table has default options. (Velayudhan, Vattem, & Ghanwani, 2019).
The IKEv2 table has default options. (Velayudhan, Vattem, & Ghanwani, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The PPP tab contains point-to-point protocol settings as shown below (Bhatnagar, Som, &
Khatri, 2019, April):
Khatri, 2019, April):
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The logging is enabled the log files are created which provide more information on
troubleshooting issues. After troubleshooting is complete, we should always disable
additional logging (Bhatnagar, Som, & Khatri, 2019, April).
troubleshooting issues. After troubleshooting is complete, we should always disable
additional logging (Bhatnagar, Som, & Khatri, 2019, April).
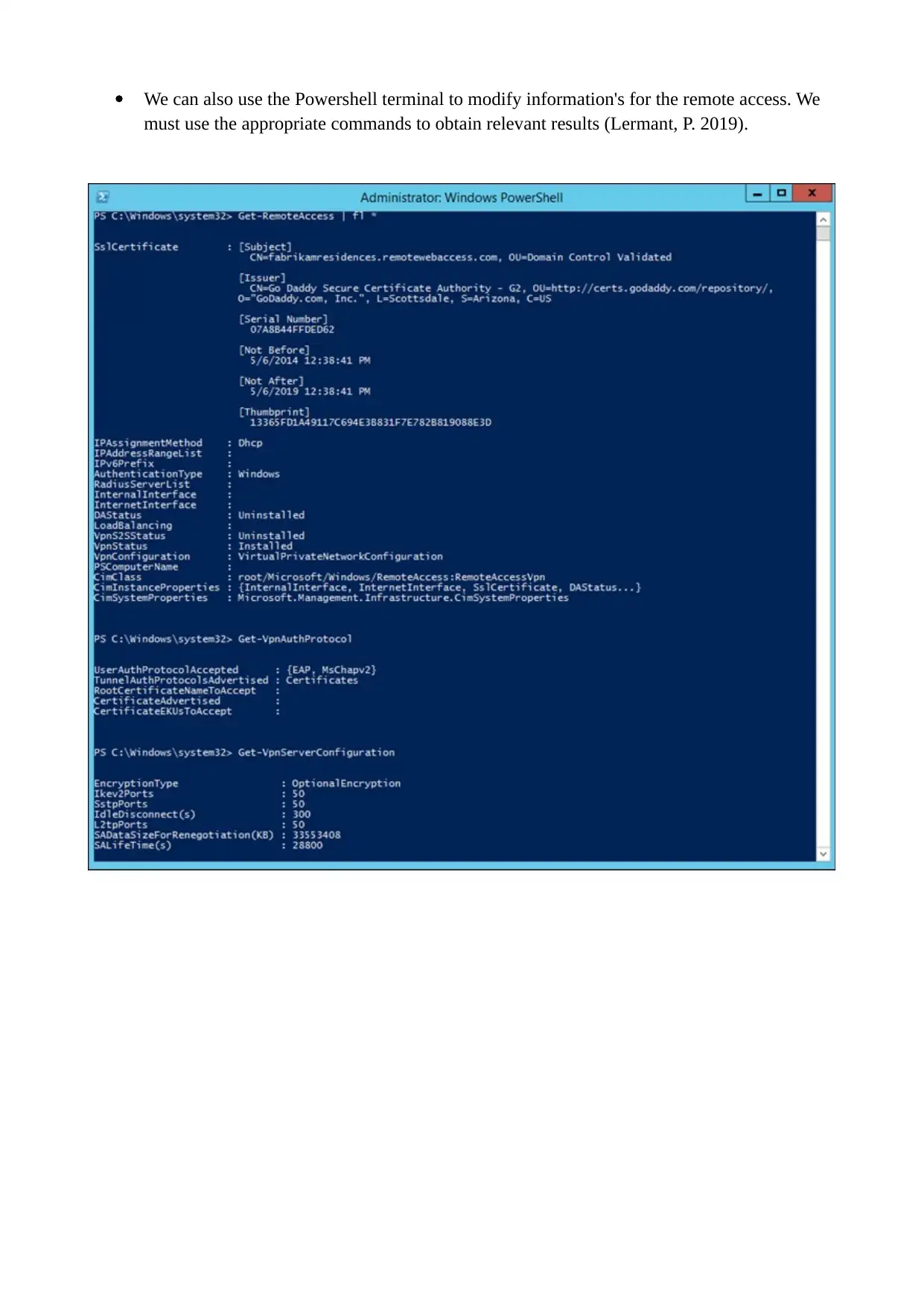
We can also use the Powershell terminal to modify information's for the remote access. We
must use the appropriate commands to obtain relevant results (Lermant, P. 2019).
must use the appropriate commands to obtain relevant results (Lermant, P. 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





