Deakin University SIT703: Advanced Digital Forensics Assignment
VerifiedAdded on 2019/11/08
|22
|1357
|301
Homework Assignment
AI Summary
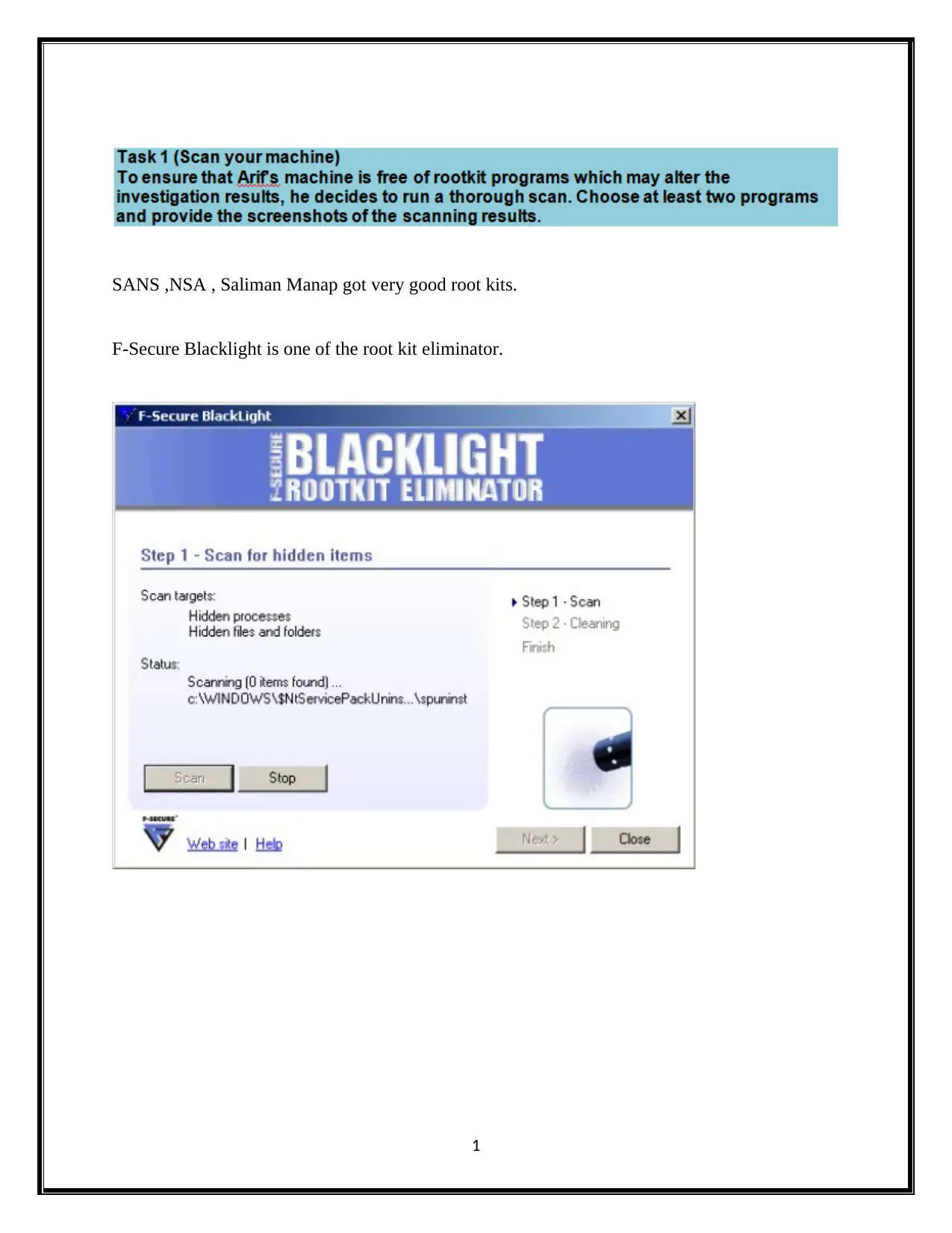
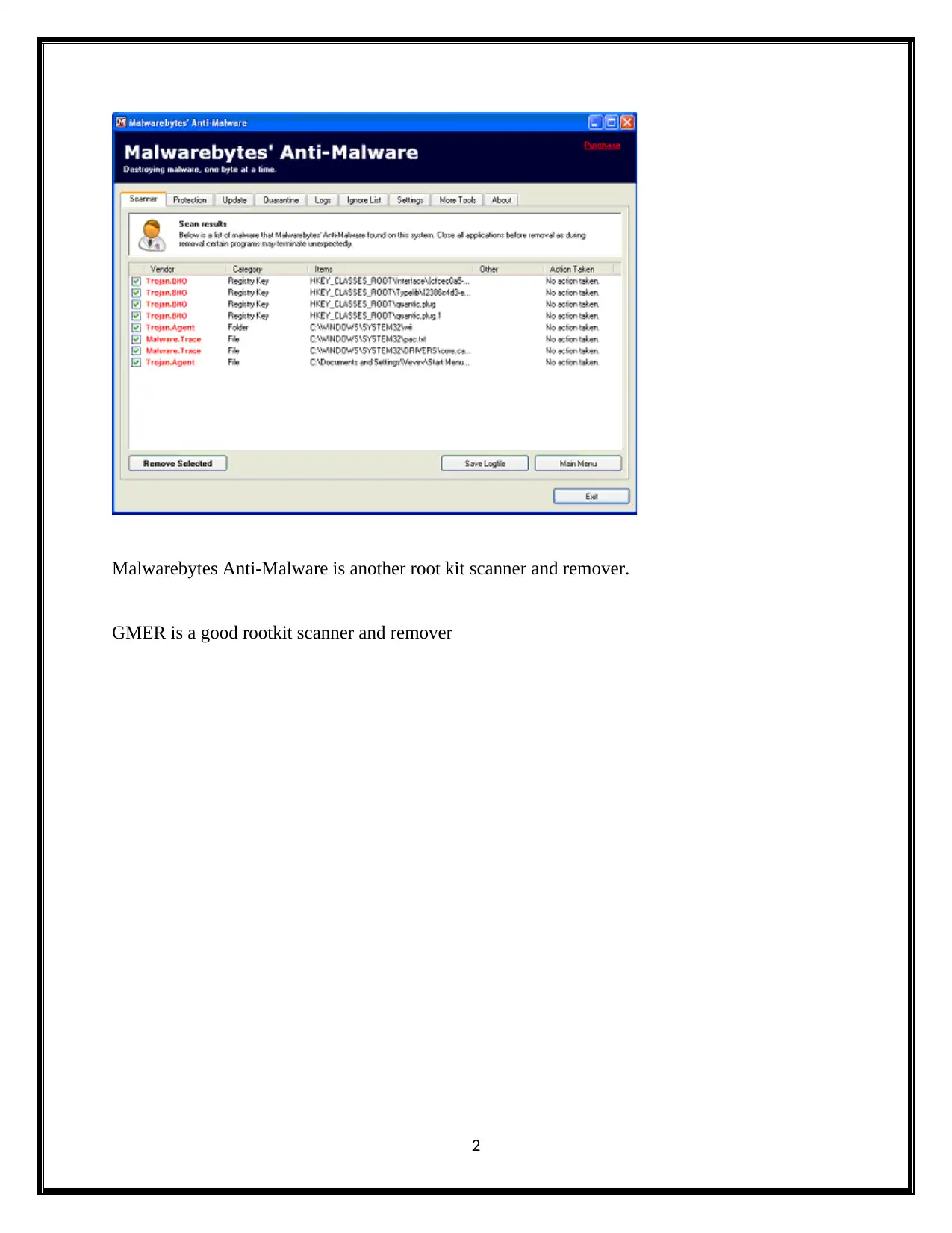
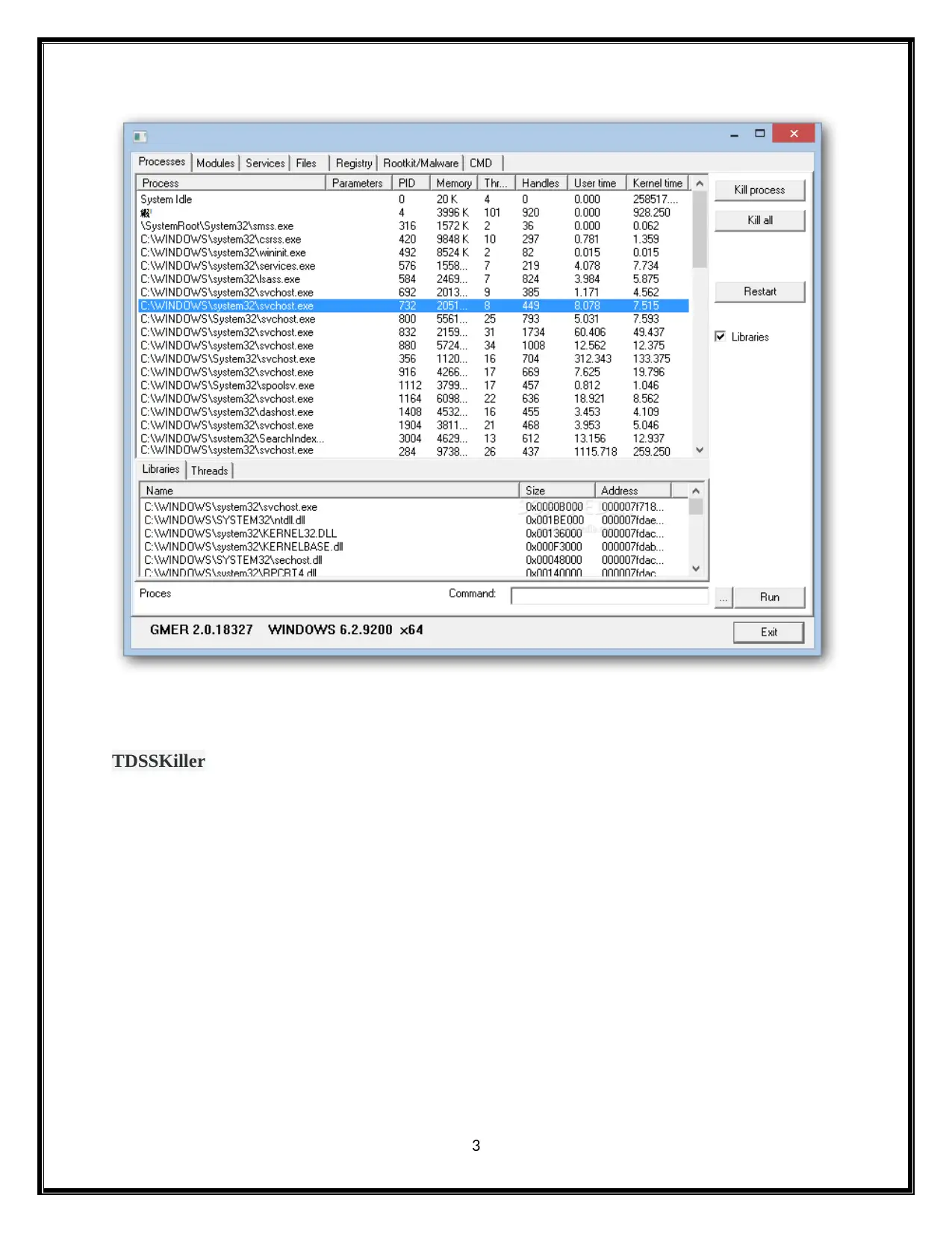
This document presents a comprehensive solution to an advanced digital forensics assignment. It begins by addressing rootkit detection and removal using tools like GMER and F-Secure Blacklight. The solution then analyzes Windows event logs (AppEvent.Evt, Internet.evt, SecEvent.Evt, SysEvent.Evt) to identify security events and user activities. Password cracking techniques using tools such as Ophcrack and free XP cracker are explored, along with methods to identify and analyze bogus user accounts, including the use of the "net user" command. The assignment also covers SQL injection vulnerabilities, registry analysis using RegScanner and MSConfig, and the application of RainbowCrack for password cracking. References to relevant resources are included, providing a detailed and practical approach to digital forensics investigation and analysis.
1 out of 22





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)