Advanced Network Topics, Management & Security Project Report
VerifiedAdded on 2020/05/04
|17
|3472
|72
Project
AI Summary
This project report focuses on the implementation of an advanced network system for STP Ltd, addressing key aspects of network security, management, and business continuity. The report begins with an introduction to the company's adoption of modern technologies, including cloud-based backup mechanisms. It outlines the project's background, scope, and goals, emphasizing the need for an integrated information management system to handle a growing customer base and enhance sales control. The project's strategic alignment is analyzed using a SWOT analysis, identifying strengths, weaknesses, opportunities, and threats. The report delves into network security, covering data security measures like encryption, mobile device security, and hardware procurement strategies, including inventory management. Furthermore, it addresses business continuity through data backup, physical security, and succession planning. Risk management is also discussed, outlining various potential risks and mitigation strategies. The project aims to enhance STP Ltd's operational efficiency and customer service through a secure and robust network infrastructure.

Advanced Network Topics, Management & Security 1
ADVANCED NETWORK TOPICS, MANAGEMENT & SECURITY
Course:
Tutor
University:
University location:
Date:
ADVANCED NETWORK TOPICS, MANAGEMENT & SECURITY
Course:
Tutor
University:
University location:
Date:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Topics, Management & Security 2
1.0 Introduction
Organizations are fast switching to technology in order to meet the current market demands.
Modern technologies include; the use of social media for advertisements, websites for online
purchases, and network systems to make internal operations of the organization efficient. STP ltd
has not been left behind; the organization has adopted a network system to integrate their
services. In order to manage the bulging customer base the organization has also adopted the
cloud based backup mechanisms for large data storage.
2.0 Project background
Information regarding project background is essential in establishing the core goal necessary for
coming up with a project report (Gruba 2017). STP limited has resorted to upgrading their
manual system to modern technological systems. The owner of the company, Mr. Joe Smith, has
invested heavily in the upgrading of the network system; in return, he wants an assurance that the
network will increase sales hence more returns to the company. The new network system,
intends to take into consideration of the state of equipment management, the stock in store, up to
date information from the stores in Sydney, Bathurst and Lithgow. The advancement of the
company is good, thus a need for an integrated information management system. A customer
who wants to order goods online will be in a position to navigate on the website and enquire
about the real location of the furniture that he/she is looking for. Once furniture has been
ordered, the system updates the particular item in real time to avoid transfers.
2.1 Project scope
The project has advocated for a distributed system in each of the locations. Store managers at
every location will be periodically analyze daily data on sales, deliveries and installations then
1.0 Introduction
Organizations are fast switching to technology in order to meet the current market demands.
Modern technologies include; the use of social media for advertisements, websites for online
purchases, and network systems to make internal operations of the organization efficient. STP ltd
has not been left behind; the organization has adopted a network system to integrate their
services. In order to manage the bulging customer base the organization has also adopted the
cloud based backup mechanisms for large data storage.
2.0 Project background
Information regarding project background is essential in establishing the core goal necessary for
coming up with a project report (Gruba 2017). STP limited has resorted to upgrading their
manual system to modern technological systems. The owner of the company, Mr. Joe Smith, has
invested heavily in the upgrading of the network system; in return, he wants an assurance that the
network will increase sales hence more returns to the company. The new network system,
intends to take into consideration of the state of equipment management, the stock in store, up to
date information from the stores in Sydney, Bathurst and Lithgow. The advancement of the
company is good, thus a need for an integrated information management system. A customer
who wants to order goods online will be in a position to navigate on the website and enquire
about the real location of the furniture that he/she is looking for. Once furniture has been
ordered, the system updates the particular item in real time to avoid transfers.
2.1 Project scope
The project has advocated for a distributed system in each of the locations. Store managers at
every location will be periodically analyze daily data on sales, deliveries and installations then

Advanced Network Topics, Management & Security 3
synchronize it to the headquarters at Wollongong. The owner will then be in a position to
ascertain whether the business is picking well or not. Asymmetric Digital Subscriber Line
(ADSL) network will be used. Each office has a modem and switch with workers free to use
Bring Your Own Device (BYOD). The project owner will be in a position to monitor the
business from anywhere.
2.2 Project goal
The major goal that the project seeks to achieve is for STP limited to be in a capacity to handle
the bulging customer number and enhance efficient control of sales records. STP limited has
been having large mixed opinions on how to handle orders and deliveries properly. Instead of the
company using vans as sales points, the system will address this by offering online sales.
Another objective is to have a clear inventory of all the equipment, staff, stock and customers.
The company currently does not have an up to date records of data regarding customer base,
sales and equipment.
2.3 Strategic alignment of project
Considering the recent rapid business growth within STP ltd, the company has resolved to
increase capitation in order to improve service delivery. The business plan will be essential in
maintaining sustainable development and adoption of favorable business policies. The network
business plan can be analyzed using the Strengths, Weaknesses, Opportunities and Threats
(SWOT) network analysis tool. This is a structured method of business planning that evaluates
the four elements to realize a good alignment for a project. This SWOT analysis is as shown in
the table below:
synchronize it to the headquarters at Wollongong. The owner will then be in a position to
ascertain whether the business is picking well or not. Asymmetric Digital Subscriber Line
(ADSL) network will be used. Each office has a modem and switch with workers free to use
Bring Your Own Device (BYOD). The project owner will be in a position to monitor the
business from anywhere.
2.2 Project goal
The major goal that the project seeks to achieve is for STP limited to be in a capacity to handle
the bulging customer number and enhance efficient control of sales records. STP limited has
been having large mixed opinions on how to handle orders and deliveries properly. Instead of the
company using vans as sales points, the system will address this by offering online sales.
Another objective is to have a clear inventory of all the equipment, staff, stock and customers.
The company currently does not have an up to date records of data regarding customer base,
sales and equipment.
2.3 Strategic alignment of project
Considering the recent rapid business growth within STP ltd, the company has resolved to
increase capitation in order to improve service delivery. The business plan will be essential in
maintaining sustainable development and adoption of favorable business policies. The network
business plan can be analyzed using the Strengths, Weaknesses, Opportunities and Threats
(SWOT) network analysis tool. This is a structured method of business planning that evaluates
the four elements to realize a good alignment for a project. This SWOT analysis is as shown in
the table below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Advanced Network Topics, Management & Security 4
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Expanding customer base
Improving sales targets
Staff who know customers
Cloud based software that allows
growth
Dedicated staff
Customized network system
Staff that are inexperienced in
computerised systems
Lack of policies and procedures
Lack of technically qualified staff
Insider threat
Espionage
External
Opportunities Threats
Connect with customers using
intelligent systems management
Increase market share
Hire a sales representative
Integration of systems
Staff empowerment
Carry out online advertisement.
Competitors agility
Information leaks
Cyber attacks
Natural disasters
System breakdown.
Table 1.0 SWOT analysis of STP ltd networks project
Internal
POSITIVE NEGATIVE
Strengths Weaknesses
Expanding customer base
Improving sales targets
Staff who know customers
Cloud based software that allows
growth
Dedicated staff
Customized network system
Staff that are inexperienced in
computerised systems
Lack of policies and procedures
Lack of technically qualified staff
Insider threat
Espionage
External
Opportunities Threats
Connect with customers using
intelligent systems management
Increase market share
Hire a sales representative
Integration of systems
Staff empowerment
Carry out online advertisement.
Competitors agility
Information leaks
Cyber attacks
Natural disasters
System breakdown.
Table 1.0 SWOT analysis of STP ltd networks project
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Topics, Management & Security 5
3.0 Network Security
Network security involves practices aimed at preventing, detecting and stopping attempts by
malicious users gaining unauthorized access into the system (Acemoglu 2016). The STP ltd
network system is newly installed; configuration of the network to ensure security is above
board. Accessing information in the system by the company employees can be made possible
through use of modern technological devices and logistics like Virtual Private Network (VPN)
and creating of subnets. The computers will be installed with antivirus software that will be
updated periodically to ensure no installation of suspicious software.
According to the journal (Zhou 2016), most threats to network security arise from authentication
loopholes, when company staffs fail to properly follow authentication policies like passwords
and logon and logout measures, it creates a chance for attackers to easily gain access into the
system. STP ltd staff will receive periodical training on how to make the network system leak-
proof. Information security and mobile device security is discussed in detail below.
3.1 Data security
Information is power. Once information gets into wrong hands then be sure of frustration
(Sathyadevan 2017). Owing to the fact that STP ltd has just installed a new networking system,
the integrity of the data is at stake. The system will ensure efficient transfer of data from the
manual system to the computerized and networked system. STP is surrounded by competitors
who may be yearning to get detailed information on how STP operates. The employees will be
trained on how to use the data safeguarding devices like USB disks, large storage hard disks and
the backup server. The three security layers will be implemented to make data recovery easier in
case of loss.
3.0 Network Security
Network security involves practices aimed at preventing, detecting and stopping attempts by
malicious users gaining unauthorized access into the system (Acemoglu 2016). The STP ltd
network system is newly installed; configuration of the network to ensure security is above
board. Accessing information in the system by the company employees can be made possible
through use of modern technological devices and logistics like Virtual Private Network (VPN)
and creating of subnets. The computers will be installed with antivirus software that will be
updated periodically to ensure no installation of suspicious software.
According to the journal (Zhou 2016), most threats to network security arise from authentication
loopholes, when company staffs fail to properly follow authentication policies like passwords
and logon and logout measures, it creates a chance for attackers to easily gain access into the
system. STP ltd staff will receive periodical training on how to make the network system leak-
proof. Information security and mobile device security is discussed in detail below.
3.1 Data security
Information is power. Once information gets into wrong hands then be sure of frustration
(Sathyadevan 2017). Owing to the fact that STP ltd has just installed a new networking system,
the integrity of the data is at stake. The system will ensure efficient transfer of data from the
manual system to the computerized and networked system. STP is surrounded by competitors
who may be yearning to get detailed information on how STP operates. The employees will be
trained on how to use the data safeguarding devices like USB disks, large storage hard disks and
the backup server. The three security layers will be implemented to make data recovery easier in
case of loss.

Advanced Network Topics, Management & Security 6
The company has stores distributed across their territory, with the alternate site data security
techniques, data can be safeguarded. The technique works in a way that, data in one station is
mirrored to another station, thus, if there is damage on one station the other station acts a backup
(Gounares 2016). The system will also include application of data encryption and decryption,
data being sent from Sydney to Wollongong should be encrypted and once it reaches the
destination, it is decrypted by use of decryption software.
3.2 Mobile device security
In the current time, mobile phones have become one of the most used and efficient devices for
both small and big businesses (Ramalingam 2016). Using mobile devices has however been
subject to network security threats. Poor signals due to physical location and application
installation have rendered the devices unacceptable (Gupta n.d.). STP ltd will resort to BYOD
network for communication and network simulated communications within the network.
4.0 Plan for hardware purchases
In order to enhance backup and proper continuous running of business operations, companies
acquire hardware for purposes of future plans, it is costly to purchase technological equipment
buy very helpful whenever there is a breakdown or change in positive market value. STP ltd has
plans to increase number of stores in Sydney in the near future, it is therefore advisable to
purchase the required hardware now and for all. According to the journal (Verma 2017),
hardware repairs and maintenance upon purchase should be under the suppliers charge.
The company has stores distributed across their territory, with the alternate site data security
techniques, data can be safeguarded. The technique works in a way that, data in one station is
mirrored to another station, thus, if there is damage on one station the other station acts a backup
(Gounares 2016). The system will also include application of data encryption and decryption,
data being sent from Sydney to Wollongong should be encrypted and once it reaches the
destination, it is decrypted by use of decryption software.
3.2 Mobile device security
In the current time, mobile phones have become one of the most used and efficient devices for
both small and big businesses (Ramalingam 2016). Using mobile devices has however been
subject to network security threats. Poor signals due to physical location and application
installation have rendered the devices unacceptable (Gupta n.d.). STP ltd will resort to BYOD
network for communication and network simulated communications within the network.
4.0 Plan for hardware purchases
In order to enhance backup and proper continuous running of business operations, companies
acquire hardware for purposes of future plans, it is costly to purchase technological equipment
buy very helpful whenever there is a breakdown or change in positive market value. STP ltd has
plans to increase number of stores in Sydney in the near future, it is therefore advisable to
purchase the required hardware now and for all. According to the journal (Verma 2017),
hardware repairs and maintenance upon purchase should be under the suppliers charge.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Advanced Network Topics, Management & Security 7
4.1 Acquisition of new hardware
STP limited should put funds aside for more hardware purchases, in order to improve the
network performance; the company should consider acquiring new computers, backups, router
and servers. In order for a purchase to be made, plans are made on how the equipment will get to
the offices; the shipping requirements, adhering to purchase policies and payments method. It is
advisable to purchase more equipment so that incase the existing ones spoils, backups take over
(Zhu 2017). STP ltd should also purpose to buy standby generators in case of power breakdown.
4.2 Purchasing strategies
Procurement strategies should be applied as per the company’s procurement policies (Mahapatra
2017). Big businesses require business plan alignment on basis of prudent put in place. STP ltd
should consider buying the equipment in bulk from a reliable supplier in order to get discounted
prices.
4.3 Hardware Inventory.
Keeping up to date records of hardware in the company is important for project planning and
better decision making (Goh 2017). Keeping inventories in STP ltd will enable IT support
technician to know exactly how many machines need repair and which ones need replacement.
4.1 Acquisition of new hardware
STP limited should put funds aside for more hardware purchases, in order to improve the
network performance; the company should consider acquiring new computers, backups, router
and servers. In order for a purchase to be made, plans are made on how the equipment will get to
the offices; the shipping requirements, adhering to purchase policies and payments method. It is
advisable to purchase more equipment so that incase the existing ones spoils, backups take over
(Zhu 2017). STP ltd should also purpose to buy standby generators in case of power breakdown.
4.2 Purchasing strategies
Procurement strategies should be applied as per the company’s procurement policies (Mahapatra
2017). Big businesses require business plan alignment on basis of prudent put in place. STP ltd
should consider buying the equipment in bulk from a reliable supplier in order to get discounted
prices.
4.3 Hardware Inventory.
Keeping up to date records of hardware in the company is important for project planning and
better decision making (Goh 2017). Keeping inventories in STP ltd will enable IT support
technician to know exactly how many machines need repair and which ones need replacement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Topics, Management & Security 8
Office Machine Age Replacement due
Wollongong 2 warehouse machines 1 years Yes
2 warehouse machines 2 years 2 years
2 Laptops 3years Yes
Accounts machine 1 years 3 years
Sydney 4 warehouse and 1 management
desktop 6 months 3.5 years
Bathurst 2 warehouse machines 5 years 1 year
1 office machine 6 months 3.5 years
Lithgow 2 Counter desktops 5 years Yes
1 office desktop 6 months 3.5 years
Table 2 showing STP hardware inventory
5.0 Business continuity
STP limited needs a clear policy on data backups, succession planning and system physical
security. The application of cloud based technologies as a result of business growth will make
business boom, it is an advancement that reflects the future of the company. The use of cloud
based information storage and retrieval plays a big role business expansion (Bishop 2017, July).
Having a good business continuity plan helps curb loses in case of disasters.
5.1 Data backup
STP limited has resolved to the use of cloud based application like MYOB, SalesForce and
TradeGecko, this applications will go a long way in data protection and backup. Cloud backup
Office Machine Age Replacement due
Wollongong 2 warehouse machines 1 years Yes
2 warehouse machines 2 years 2 years
2 Laptops 3years Yes
Accounts machine 1 years 3 years
Sydney 4 warehouse and 1 management
desktop 6 months 3.5 years
Bathurst 2 warehouse machines 5 years 1 year
1 office machine 6 months 3.5 years
Lithgow 2 Counter desktops 5 years Yes
1 office desktop 6 months 3.5 years
Table 2 showing STP hardware inventory
5.0 Business continuity
STP limited needs a clear policy on data backups, succession planning and system physical
security. The application of cloud based technologies as a result of business growth will make
business boom, it is an advancement that reflects the future of the company. The use of cloud
based information storage and retrieval plays a big role business expansion (Bishop 2017, July).
Having a good business continuity plan helps curb loses in case of disasters.
5.1 Data backup
STP limited has resolved to the use of cloud based application like MYOB, SalesForce and
TradeGecko, this applications will go a long way in data protection and backup. Cloud backup

Advanced Network Topics, Management & Security 9
mechanism is important but risky; it is risky in the sense that, intruders can gain access to stored
data (Jones 2017). Due to these risks, it is advisable to use an offline backup mechanism to avoid
losing data to competitors.
5.2 Physical security.
Physical risks may include risks from within the organization and from outside the company.
Internal physical risks may include human errors like physical machine damage and poor
password application (Jones 2017). STP ltd should consider training their employees on
advanced security measures to curb unauthorized access of data. Another form of physical
security is natural disasters like floods, earthquake and storms that may damage the system
completely; STP limited should provide their workers with insurance covers in case of a disaster
occurrence. Espionage culprits should be prosecuted and dismissed from the company.
5.3 Succession planning
Employees might at one time retire or resign from service, it is important for SPT ltd to put in
place in case such an occurrence happens, new staff can assume duty and cope up as fast as
possible. STP ltd should expect such an occurrence to happen. Planning for such an expectation
should include identifying serious financial or operational needs that will require instance
attention in case it happens (Gruba 2017). It is also important when planning for such an
occurrence, details of a potential successor be discussed.
6.0 Risk management
Risk management is the ability to forecast and evaluate future or potential risks in time in order
to prepare for the risk (Zhou 2016). Foreseeing future risks is important such that, one can lay
mechanism is important but risky; it is risky in the sense that, intruders can gain access to stored
data (Jones 2017). Due to these risks, it is advisable to use an offline backup mechanism to avoid
losing data to competitors.
5.2 Physical security.
Physical risks may include risks from within the organization and from outside the company.
Internal physical risks may include human errors like physical machine damage and poor
password application (Jones 2017). STP ltd should consider training their employees on
advanced security measures to curb unauthorized access of data. Another form of physical
security is natural disasters like floods, earthquake and storms that may damage the system
completely; STP limited should provide their workers with insurance covers in case of a disaster
occurrence. Espionage culprits should be prosecuted and dismissed from the company.
5.3 Succession planning
Employees might at one time retire or resign from service, it is important for SPT ltd to put in
place in case such an occurrence happens, new staff can assume duty and cope up as fast as
possible. STP ltd should expect such an occurrence to happen. Planning for such an expectation
should include identifying serious financial or operational needs that will require instance
attention in case it happens (Gruba 2017). It is also important when planning for such an
occurrence, details of a potential successor be discussed.
6.0 Risk management
Risk management is the ability to forecast and evaluate future or potential risks in time in order
to prepare for the risk (Zhou 2016). Foreseeing future risks is important such that, one can lay
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Advanced Network Topics, Management & Security 10
down mechanisms to avoid then or reduce the impact that might be felt after the risk occurs. It is
also wise to note that risks have different foams responses (Zhou 2016). STP ltd should prepare
to address particular issues like the integration of the system and regulating compliance to risk
avoidance policies.
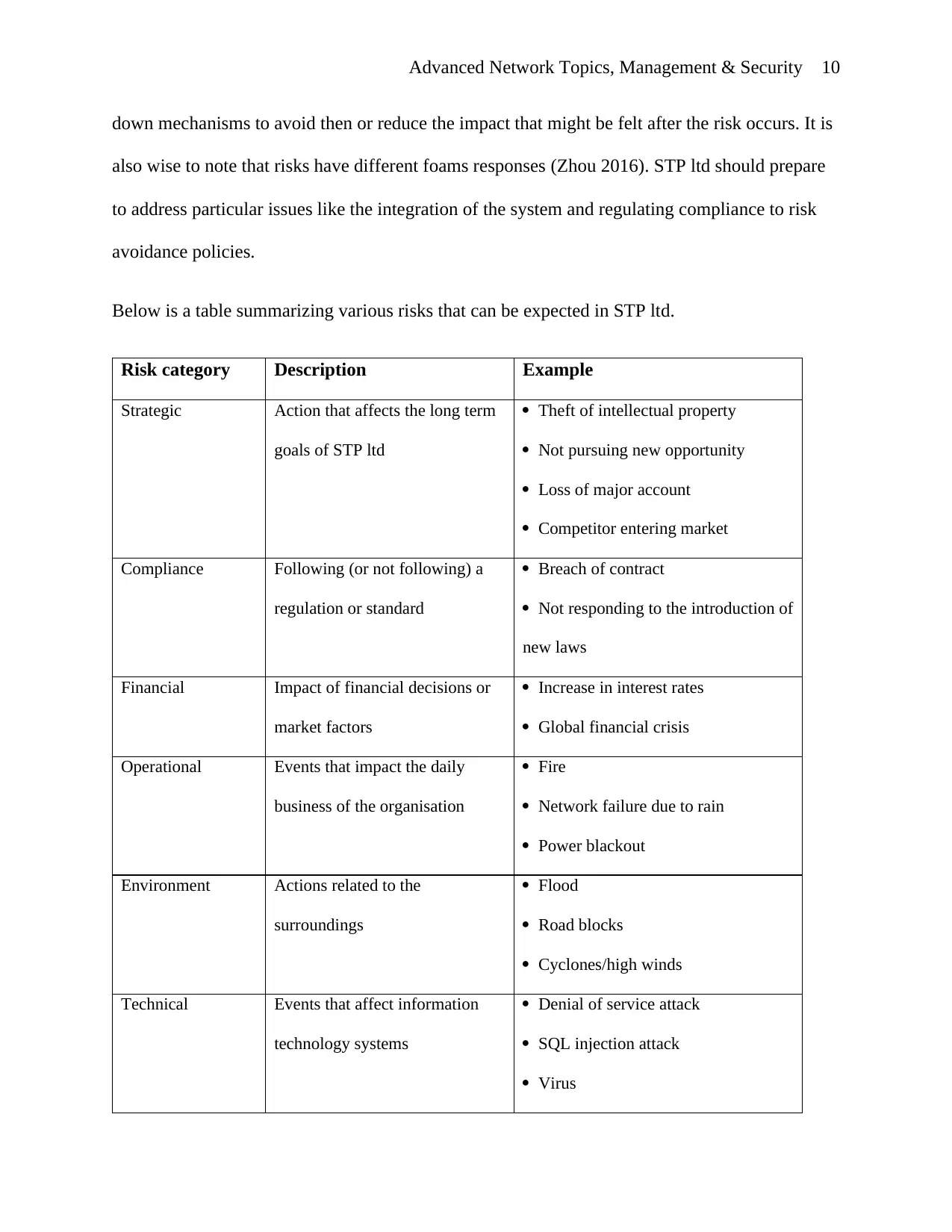
Below is a table summarizing various risks that can be expected in STP ltd.
Risk category Description Example
Strategic Action that affects the long term
goals of STP ltd
Theft of intellectual property
Not pursuing new opportunity
Loss of major account
Competitor entering market
Compliance Following (or not following) a
regulation or standard
Breach of contract
Not responding to the introduction of
new laws
Financial Impact of financial decisions or
market factors
Increase in interest rates
Global financial crisis
Operational Events that impact the daily
business of the organisation
Fire
Network failure due to rain
Power blackout
Environment Actions related to the
surroundings
Flood
Road blocks
Cyclones/high winds
Technical Events that affect information
technology systems
Denial of service attack
SQL injection attack
Virus
down mechanisms to avoid then or reduce the impact that might be felt after the risk occurs. It is
also wise to note that risks have different foams responses (Zhou 2016). STP ltd should prepare
to address particular issues like the integration of the system and regulating compliance to risk
avoidance policies.
Below is a table summarizing various risks that can be expected in STP ltd.
Risk category Description Example
Strategic Action that affects the long term
goals of STP ltd
Theft of intellectual property
Not pursuing new opportunity
Loss of major account
Competitor entering market
Compliance Following (or not following) a
regulation or standard
Breach of contract
Not responding to the introduction of
new laws
Financial Impact of financial decisions or
market factors
Increase in interest rates
Global financial crisis
Operational Events that impact the daily
business of the organisation
Fire
Network failure due to rain
Power blackout
Environment Actions related to the
surroundings
Flood
Road blocks
Cyclones/high winds
Technical Events that affect information
technology systems
Denial of service attack
SQL injection attack
Virus
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Advanced Network Topics, Management & Security 11
Managerial Actions related to the
management of the organisation
Long term illness of employee
Key employee resigning
Table 3 showing summarized risks expected
6.1 Security policy
Security policy defines an organization’s position about security issues (Zhou 2017). This is an
established order on how security issues will be responded to in order to meet the business
security standard. Application of other risk management techniques such as scene management
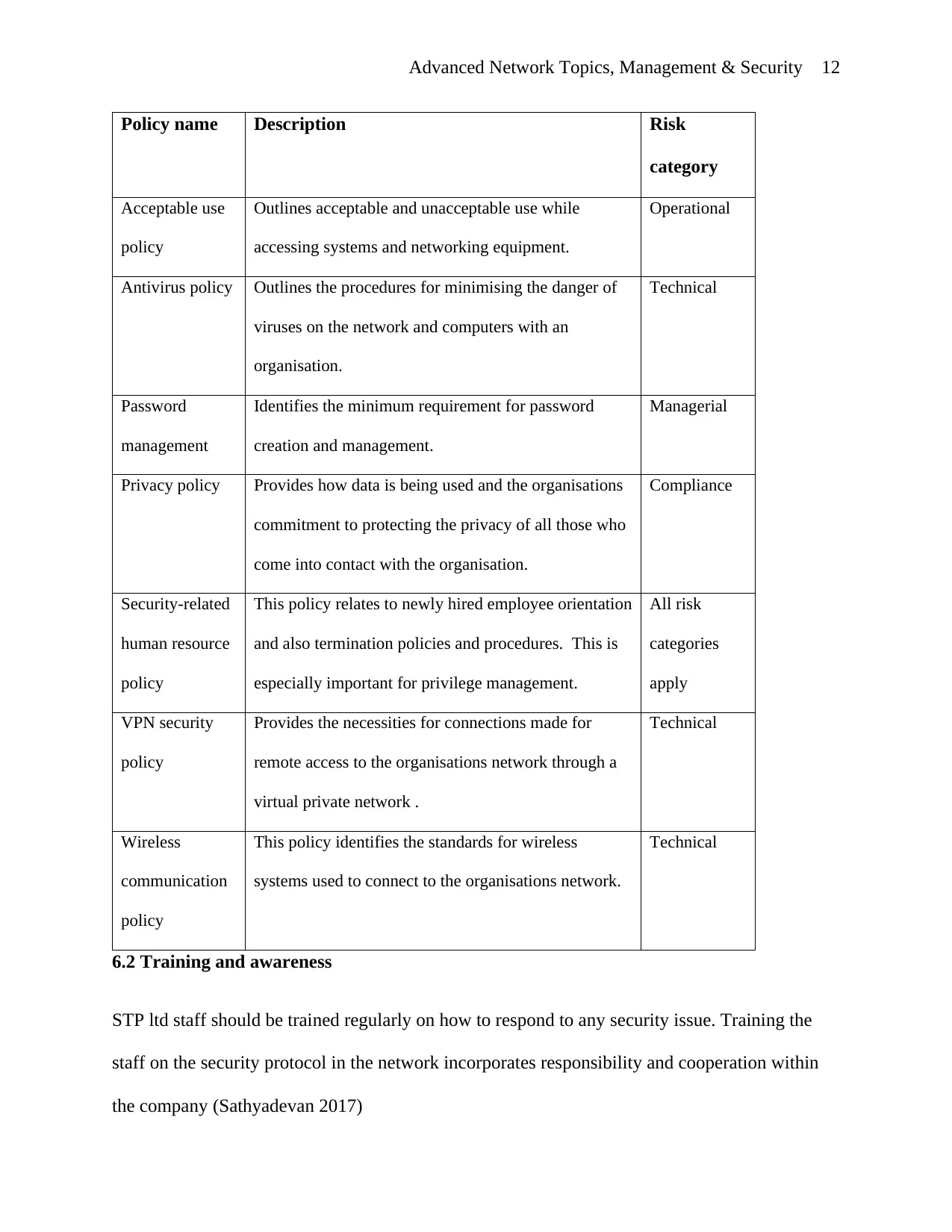
and privilege control will be appropriate for STP ltd. Below is a table summarizing the
recommended security policies for STP ltd.
Table 6.1 Recommended security policies
Managerial Actions related to the
management of the organisation
Long term illness of employee
Key employee resigning
Table 3 showing summarized risks expected
6.1 Security policy
Security policy defines an organization’s position about security issues (Zhou 2017). This is an
established order on how security issues will be responded to in order to meet the business
security standard. Application of other risk management techniques such as scene management
and privilege control will be appropriate for STP ltd. Below is a table summarizing the
recommended security policies for STP ltd.
Table 6.1 Recommended security policies
Advanced Network Topics, Management & Security 12
Policy name Description Risk
category
Acceptable use
policy
Outlines acceptable and unacceptable use while
accessing systems and networking equipment.
Operational
Antivirus policy Outlines the procedures for minimising the danger of
viruses on the network and computers with an
organisation.
Technical
Password
management
Identifies the minimum requirement for password
creation and management.
Managerial
Privacy policy Provides how data is being used and the organisations
commitment to protecting the privacy of all those who
come into contact with the organisation.
Compliance
Security-related
human resource
policy
This policy relates to newly hired employee orientation
and also termination policies and procedures. This is
especially important for privilege management.
All risk
categories
apply
VPN security
policy
Provides the necessities for connections made for
remote access to the organisations network through a
virtual private network .
Technical
Wireless
communication
policy
This policy identifies the standards for wireless
systems used to connect to the organisations network.
Technical
6.2 Training and awareness
STP ltd staff should be trained regularly on how to respond to any security issue. Training the
staff on the security protocol in the network incorporates responsibility and cooperation within
the company (Sathyadevan 2017)
Policy name Description Risk
category
Acceptable use
policy
Outlines acceptable and unacceptable use while
accessing systems and networking equipment.
Operational
Antivirus policy Outlines the procedures for minimising the danger of
viruses on the network and computers with an
organisation.
Technical
Password
management
Identifies the minimum requirement for password
creation and management.
Managerial
Privacy policy Provides how data is being used and the organisations
commitment to protecting the privacy of all those who
come into contact with the organisation.
Compliance
Security-related
human resource
policy
This policy relates to newly hired employee orientation
and also termination policies and procedures. This is
especially important for privilege management.
All risk
categories
apply
VPN security
policy
Provides the necessities for connections made for
remote access to the organisations network through a
virtual private network .
Technical
Wireless
communication
policy
This policy identifies the standards for wireless
systems used to connect to the organisations network.
Technical
6.2 Training and awareness
STP ltd staff should be trained regularly on how to respond to any security issue. Training the
staff on the security protocol in the network incorporates responsibility and cooperation within
the company (Sathyadevan 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





