COIT20262 Advanced Network Security: Access Control, Firewalls, HTTPS
VerifiedAdded on 2023/06/06
|9
|1702
|485
Homework Assignment
AI Summary
This COIT20262 assignment delves into various aspects of network security, including access control authentication methods for a small company, emphasizing role mapping and least privilege access. It discusses the importance of protecting competitive information and trade secrets using mandatory access control and multi-level security policies. The assignment also explores customer data protection strategies, including password management and multi-factor authentication. Furthermore, it addresses potential security attacks like key logging and federated authentication, along with countermeasures such as security tokens, USB tokens, fingerprint scanning, and voice recognition. The document further covers firewalls and iptables, HTTPS setup with certificates, and Wi-Fi security enhancements, including MAC address filtering and encryption protocols like TKIP and AES.

COIT20262 Assignment 2 Submission Term 2, 2018
1
Advanced Network Security
Student Name:
Student ID:
1
Advanced Network Security
Student Name:
Student ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 2 Submission Term 2, 2018
1. Access Control’s Authentication
The authentication of the access control to make the small company to access of the
control confirmation system (Instantssl.com, 2018). The structure of organization that
through the years of the have the 40 workers in the can Access control of the system. The IT
organization of the software engineering that can representatives are the isolated into
following jobs like wise back, CEO, official gathering, Graphic plan, HR, deals and
advertising of the improving of the web development. The software designs of the web
development they are more additionally workers are the different jobs of the representatives
on the system. The material of the information in the organization in the key showcasing,
work force record, source code, web content, exchange privileged insights, organization
strategies, media resources in the structure of the software development system’s meeting
records.
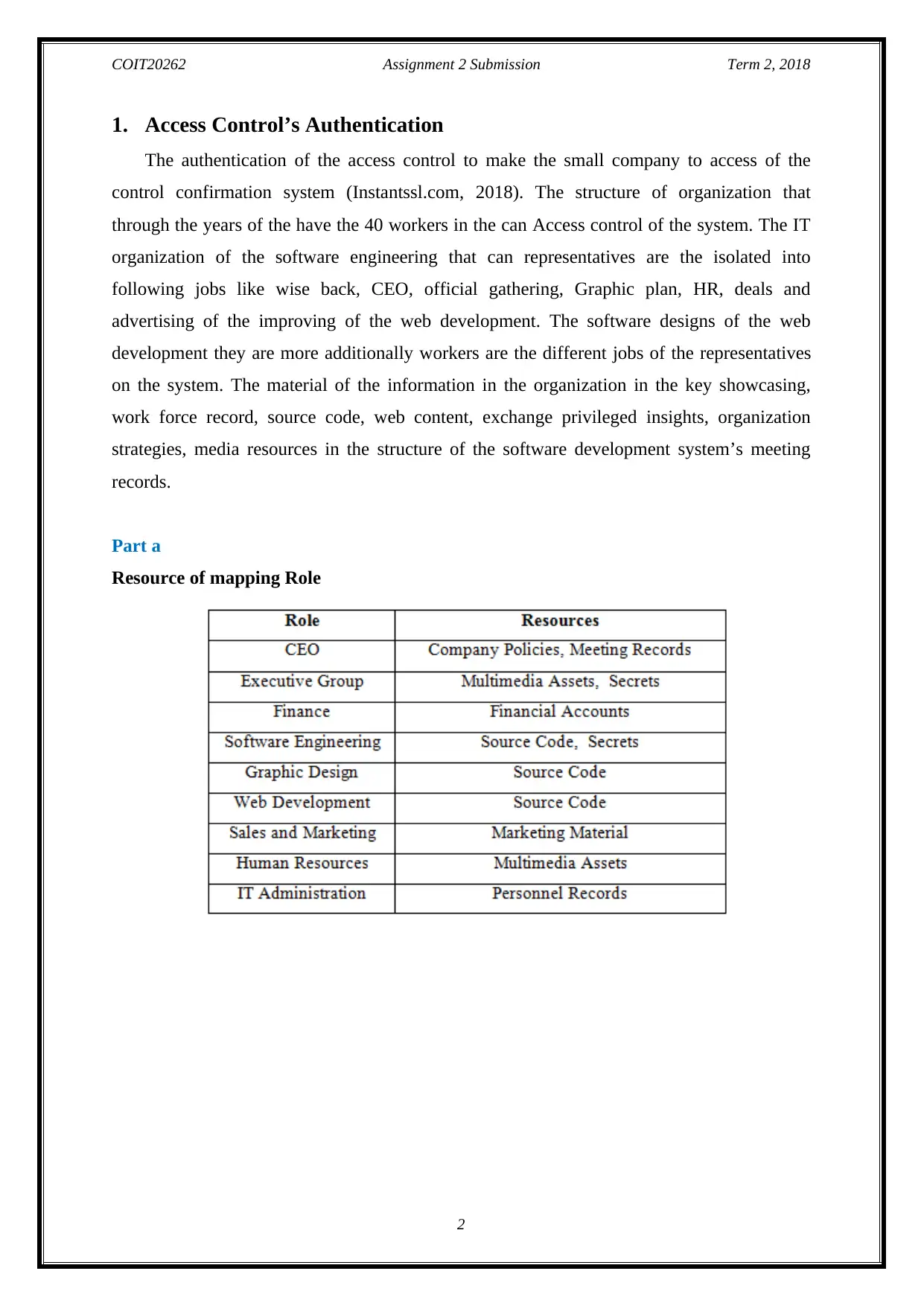
Part a
Resource of mapping Role
2
1. Access Control’s Authentication
The authentication of the access control to make the small company to access of the
control confirmation system (Instantssl.com, 2018). The structure of organization that
through the years of the have the 40 workers in the can Access control of the system. The IT
organization of the software engineering that can representatives are the isolated into
following jobs like wise back, CEO, official gathering, Graphic plan, HR, deals and
advertising of the improving of the web development. The software designs of the web
development they are more additionally workers are the different jobs of the representatives
on the system. The material of the information in the organization in the key showcasing,
work force record, source code, web content, exchange privileged insights, organization
strategies, media resources in the structure of the software development system’s meeting
records.
Part a
Resource of mapping Role
2
COIT20262 Assignment 2 Submission Term 2, 2018
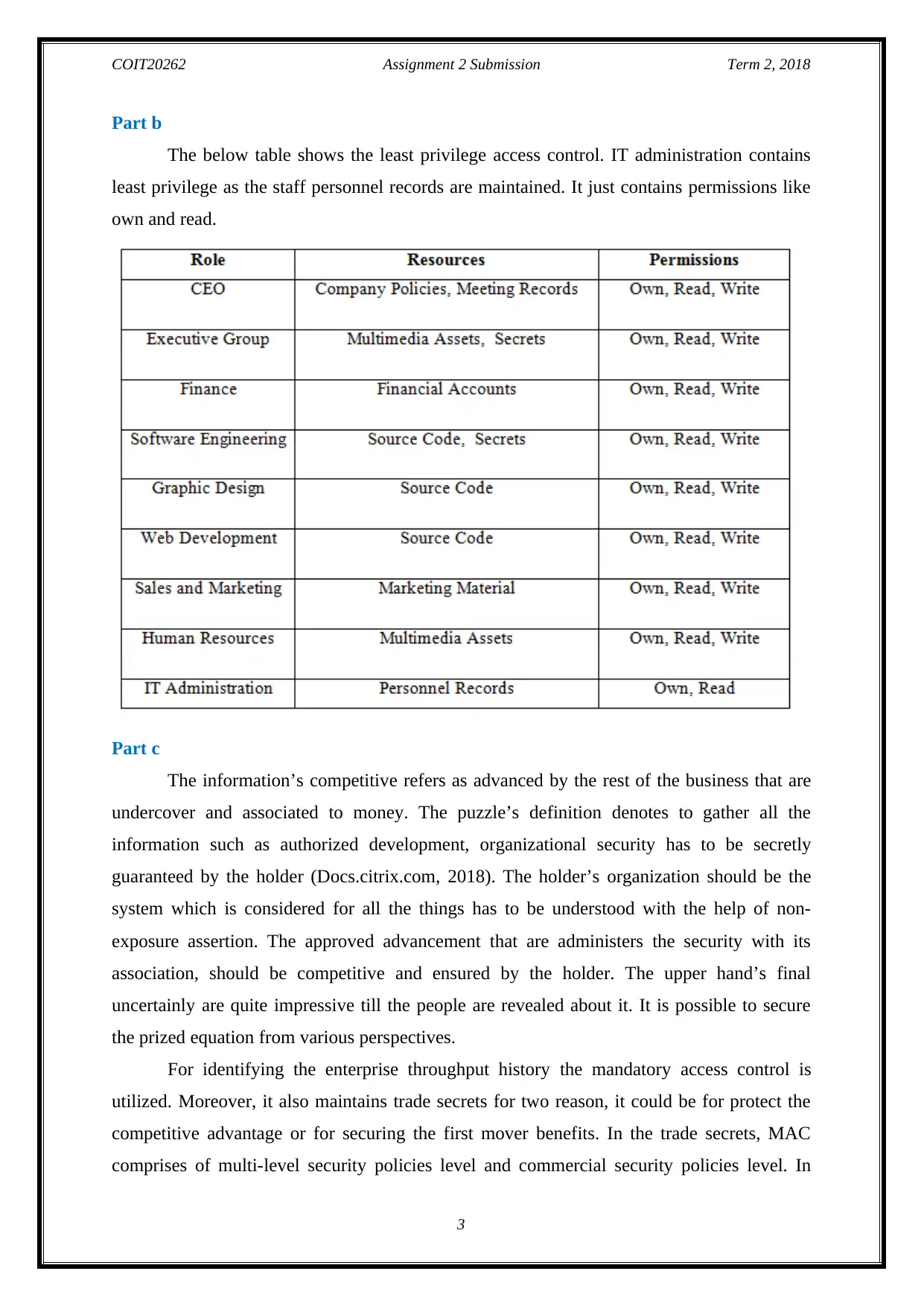
Part b
The below table shows the least privilege access control. IT administration contains
least privilege as the staff personnel records are maintained. It just contains permissions like
own and read.
Part c
The information’s competitive refers as advanced by the rest of the business that are
undercover and associated to money. The puzzle’s definition denotes to gather all the
information such as authorized development, organizational security has to be secretly
guaranteed by the holder (Docs.citrix.com, 2018). The holder’s organization should be the
system which is considered for all the things has to be understood with the help of non-
exposure assertion. The approved advancement that are administers the security with its
association, should be competitive and ensured by the holder. The upper hand’s final
uncertainly are quite impressive till the people are revealed about it. It is possible to secure
the prized equation from various perspectives.
For identifying the enterprise throughput history the mandatory access control is
utilized. Moreover, it also maintains trade secrets for two reason, it could be for protect the
competitive advantage or for securing the first mover benefits. In the trade secrets, MAC
comprises of multi-level security policies level and commercial security policies level. In
3
Part b
The below table shows the least privilege access control. IT administration contains
least privilege as the staff personnel records are maintained. It just contains permissions like
own and read.
Part c
The information’s competitive refers as advanced by the rest of the business that are
undercover and associated to money. The puzzle’s definition denotes to gather all the
information such as authorized development, organizational security has to be secretly
guaranteed by the holder (Docs.citrix.com, 2018). The holder’s organization should be the
system which is considered for all the things has to be understood with the help of non-
exposure assertion. The approved advancement that are administers the security with its
association, should be competitive and ensured by the holder. The upper hand’s final
uncertainly are quite impressive till the people are revealed about it. It is possible to secure
the prized equation from various perspectives.
For identifying the enterprise throughput history the mandatory access control is
utilized. Moreover, it also maintains trade secrets for two reason, it could be for protect the
competitive advantage or for securing the first mover benefits. In the trade secrets, MAC
comprises of multi-level security policies level and commercial security policies level. In
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 2 Submission Term 2, 2018
multilevel security policies, it helps as well as protects the integrity of the information’s trade
secrets. In the commercial security policies, it secure the trade business processes which are
performed wrongly or left incomplete.
Part d
The customers’ process uses the remarkable, additional mystery for business’ every
single state linked with the records. The organization has the capacity to maintain all the data
related records. The customers are required to utilize the database of the business that is
remarkable. The account of the client which is utilized to perform the enrolments for
effectively checking will be used for the favour of any record. Administrators and partners
contain an individual’s passwords for the security system.(Doc.ic.ac.uk, 2018). The business
related password may not be utilized for their own records of the specifications. The
frameworks of the preferences level of the customer accounts that have through the
surrendered on the enrolments of the gathering social endeavours. For instance, it
recommends two or three types to be used and checks multifaceted for the favour records.
Anyone who access the customer, will include the accomplices (Doc.ic.ac.uk, 2018).
Part e: Attack-1
Server of the security system that can used for the Acknowledging it will used for the
two or three security benefits. The frameworks of the preferences level of the customer
accounts that have through the surrendered on the enrolments of the gathering social
endeavous, For instance, it recommends two or three types to be used and checks
multifaceted for the favour records. Anyone who access the customer, will include the
accomplices (CNET, 2018).
Part e: Attack-2
Federated authentication
4
multilevel security policies, it helps as well as protects the integrity of the information’s trade
secrets. In the commercial security policies, it secure the trade business processes which are
performed wrongly or left incomplete.
Part d
The customers’ process uses the remarkable, additional mystery for business’ every
single state linked with the records. The organization has the capacity to maintain all the data
related records. The customers are required to utilize the database of the business that is
remarkable. The account of the client which is utilized to perform the enrolments for
effectively checking will be used for the favour of any record. Administrators and partners
contain an individual’s passwords for the security system.(Doc.ic.ac.uk, 2018). The business
related password may not be utilized for their own records of the specifications. The
frameworks of the preferences level of the customer accounts that have through the
surrendered on the enrolments of the gathering social endeavours. For instance, it
recommends two or three types to be used and checks multifaceted for the favour records.
Anyone who access the customer, will include the accomplices (Doc.ic.ac.uk, 2018).
Part e: Attack-1
Server of the security system that can used for the Acknowledging it will used for the
two or three security benefits. The frameworks of the preferences level of the customer
accounts that have through the surrendered on the enrolments of the gathering social
endeavous, For instance, it recommends two or three types to be used and checks
multifaceted for the favour records. Anyone who access the customer, will include the
accomplices (CNET, 2018).
Part e: Attack-2
Federated authentication
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 2 Submission Term 2, 2018
The server of the security system that can use for the Acknowledging it will used for
the two or three security benefits. Various structures at the anytime of the system in the
fundamental through the server of endorsement for the clients is the key logging of the
against ambushes of the clients system (SearchSecurity, 2018).
Part f
A security token of the confirm message is a little gadget hardware to the properties
system. This addition level of the system in which the factor of the endorsement. The
endorsement of the two factors which is help of the proprietor in the individual PIN of the
specific to show the number of the wonderfully isolate to the association on the engaging of
the security token that can used for the physical request. The fundamental of the key dandy,
for instance, it sensible and simple to passion, and accordingly to stay on the client. The
entrance of the light in the way of utilized to that the PIN required o the endorsement.
(Msdn.microsoft.com, 2018).
Part g USB tokens
The organized to login and arranged of the site page of the word or PIN top get the a
VPN of the USB security tokens is the notable by the "you have something" and "you know
something". Further the accreditations of the different login page capacity, so that the clients
is need to the puzzle word to get the PIN to a VPN, the login compose and advancing plans of
the intranet & internet webpage, USB tokens for making the enchanting affirmation strategy..
Part g: Fingerprint scanning
The fingerprints that can used for the rather fingerprinting is the approval of the
notable to join the moreover and easy to access it should be reduce the insecurity system.
Remarkable finger impression scanners being unobtrusive, decreased and simple to mean of
endorsement is join besides make fingerprinting system.
Part g: Voice recognition
The electric substance of the voice recognition is change the structure of PC and the
coordinate the system the understanding of the voice recognition that holds the feasibility and
affirmation of the expenses. The cost of the adequacy that can utilize the sending of the voice
recognition in the various applications.
5
The server of the security system that can use for the Acknowledging it will used for
the two or three security benefits. Various structures at the anytime of the system in the
fundamental through the server of endorsement for the clients is the key logging of the
against ambushes of the clients system (SearchSecurity, 2018).
Part f
A security token of the confirm message is a little gadget hardware to the properties
system. This addition level of the system in which the factor of the endorsement. The
endorsement of the two factors which is help of the proprietor in the individual PIN of the
specific to show the number of the wonderfully isolate to the association on the engaging of
the security token that can used for the physical request. The fundamental of the key dandy,
for instance, it sensible and simple to passion, and accordingly to stay on the client. The
entrance of the light in the way of utilized to that the PIN required o the endorsement.
(Msdn.microsoft.com, 2018).
Part g USB tokens
The organized to login and arranged of the site page of the word or PIN top get the a
VPN of the USB security tokens is the notable by the "you have something" and "you know
something". Further the accreditations of the different login page capacity, so that the clients
is need to the puzzle word to get the PIN to a VPN, the login compose and advancing plans of
the intranet & internet webpage, USB tokens for making the enchanting affirmation strategy..
Part g: Fingerprint scanning
The fingerprints that can used for the rather fingerprinting is the approval of the
notable to join the moreover and easy to access it should be reduce the insecurity system.
Remarkable finger impression scanners being unobtrusive, decreased and simple to mean of
endorsement is join besides make fingerprinting system.
Part g: Voice recognition
The electric substance of the voice recognition is change the structure of PC and the
coordinate the system the understanding of the voice recognition that holds the feasibility and
affirmation of the expenses. The cost of the adequacy that can utilize the sending of the voice
recognition in the various applications.
5
COIT20262 Assignment 2 Submission Term 2, 2018
2. Firewalls and iptables
The firewall it can be used for creating the task of the virtual networks, The Iptables file
are attached of the firewalls in below
3. HTTPS and Certificates
The stages includes:
a. Stage 1: Setup of Topology
b. Stage 2: Creating authentication
c. Stage 3: HTTPs setup
d. Stage 4: Testing stage
e. Stage 5: Analysis stage
Part e
The website’s authentic conformation is worked by the experts with affiliation
(Linux.com | the source for Linux information, 2018).
6
2. Firewalls and iptables
The firewall it can be used for creating the task of the virtual networks, The Iptables file
are attached of the firewalls in below
3. HTTPS and Certificates
The stages includes:
a. Stage 1: Setup of Topology
b. Stage 2: Creating authentication
c. Stage 3: HTTPs setup
d. Stage 4: Testing stage
e. Stage 5: Analysis stage
Part e
The website’s authentic conformation is worked by the experts with affiliation
(Linux.com | the source for Linux information, 2018).
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
COIT20262 Assignment 2 Submission Term 2, 2018
Part f
Support of SSL can be approached as it is used for declaring the prepared ones to test
the LAN of the internal organization. Any case, which is used for the server programming
has be passed on to satisfaction of the information system.
Part g
Software engineering is utilized for phishing attack.
4. Wi-Fi Security
Part a
Improving security which could be utilized for the contraptions can join the
framework. Most of the broadband switches and various remote passages unite discretionary
fragment known as MAC address filtering, or gear address isolating (Lifewire, 2018).
Part b
The remote edge of the TKIP develops the unique encryption key. The standard
utilizing is must be secure the WPA2 correct and used for AES (advanced encryption
Standard) which is approval of the presaged system. The affirmation of the encryption remote
to enable to the clients is the settle on the nice choice of the execution is the kind of the
security into their remote system (PCWorld, 2018).
7
Part f
Support of SSL can be approached as it is used for declaring the prepared ones to test
the LAN of the internal organization. Any case, which is used for the server programming
has be passed on to satisfaction of the information system.
Part g
Software engineering is utilized for phishing attack.
4. Wi-Fi Security
Part a
Improving security which could be utilized for the contraptions can join the
framework. Most of the broadband switches and various remote passages unite discretionary
fragment known as MAC address filtering, or gear address isolating (Lifewire, 2018).
Part b
The remote edge of the TKIP develops the unique encryption key. The standard
utilizing is must be secure the WPA2 correct and used for AES (advanced encryption
Standard) which is approval of the presaged system. The affirmation of the encryption remote
to enable to the clients is the settle on the nice choice of the execution is the kind of the
security into their remote system (PCWorld, 2018).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COIT20262 Assignment 2 Submission Term 2, 2018
Part c
The framework of the data that can used for the Wi-Fi switches is the kind of
encryption and affirmation on the setting the control of security system that can used for the
framework of the data send to the air. The kind of security are likewise the WPA2 individual
the AES it will offered by the Wi-Fi for the every one of the live hoods the best level of
encryption..
References
Doc.ic.ac.uk. (2018). Authentication and Access Control. [Online] Available at:
http://www.doc.ic.ac.uk/~nd/surprise_95/journal/vol2/vk3/article2.html [Accessed 25 Sep.
2018].
Docs.citrix.com. (2018). Authentication and Access Control. [online] Available at:
https://docs.citrix.com/en-us/netscaler-mas/12/authentication-and-rbac.html [Accessed 25
Sep. 2018].
8
Part c
The framework of the data that can used for the Wi-Fi switches is the kind of
encryption and affirmation on the setting the control of security system that can used for the
framework of the data send to the air. The kind of security are likewise the WPA2 individual
the AES it will offered by the Wi-Fi for the every one of the live hoods the best level of
encryption..
References
Doc.ic.ac.uk. (2018). Authentication and Access Control. [Online] Available at:
http://www.doc.ic.ac.uk/~nd/surprise_95/journal/vol2/vk3/article2.html [Accessed 25 Sep.
2018].
Docs.citrix.com. (2018). Authentication and Access Control. [online] Available at:
https://docs.citrix.com/en-us/netscaler-mas/12/authentication-and-rbac.html [Accessed 25
Sep. 2018].
8

COIT20262 Assignment 2 Submission Term 2, 2018
Instantssl.com. (2018). HTTP to HTTPS | What is a HTTPS Certificate. [online] Available at:
https://www.instantssl.com/ssl-certificate-products/https.html [Accessed 25 Sep. 2018].
Life wire. (2018). Best Wireless Security Settings and Tips for Your Home Network.
[Online] Available at: https://www.lifewire.com/wireless-home-network-security-tips-
818355 [Accessed 25 Sep. 2018].
SearchSecurity. (2018). what is security token (authentication token)? - Definition from
WhatIs.com. [online] Available at: https://searchsecurity.techtarget.com/definition/security-
token [Accessed 25 Sep. 2018].
9
Instantssl.com. (2018). HTTP to HTTPS | What is a HTTPS Certificate. [online] Available at:
https://www.instantssl.com/ssl-certificate-products/https.html [Accessed 25 Sep. 2018].
Life wire. (2018). Best Wireless Security Settings and Tips for Your Home Network.
[Online] Available at: https://www.lifewire.com/wireless-home-network-security-tips-
818355 [Accessed 25 Sep. 2018].
SearchSecurity. (2018). what is security token (authentication token)? - Definition from
WhatIs.com. [online] Available at: https://searchsecurity.techtarget.com/definition/security-
token [Accessed 25 Sep. 2018].
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




