Advanced Network and Infrastructure Security Report
VerifiedAdded on 2023/01/11
|8
|1055
|26
Report
AI Summary
This report examines the application of blockchain technology in enhancing network infrastructure security. It begins with an abstract highlighting the importance of network security in the face of increasing cyber threats and the role of blockchain in addressing these concerns. The introduction emphasizes the significance of network security management and the adoption of blockchain as a revolutionary technology. The report reviews related works, discussing how blockchain's immutable nature contributes to improved security. The research methodology involves a qualitative analysis of secondary data, reviewing 30 studies on blockchain's implementation in network security. The results and analysis section summarizes findings, highlighting blockchain's utility in handling processes like public key infrastructure and data privacy, particularly with devices that have weak security configurations. The conclusion emphasizes the ongoing evolution of blockchain in network infrastructure and recommends that future research focus on practical applications and integration for better security solutions. References include books and journals that support the research.

Advanced Network and Infrastructure
Security
1
Security
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT
Security is based on the fundamental component in term of computing and networking
technology. It is everything of network designing, planning, building and operating a network. It
has become more important to protect personal computer users, organizations. With advent of
internet, security is becoming a major concern due to intellectual property which can easily
acquire through internet. Therefore, networking infrastructure worldwide and needed to different
security mechanism. Furthermore, research study is adapting the block chain technology in term
of network infrastructure security. This paper looked at several use of block chain in network
security within industry. In order to examine the way to highlight through study which block
chain can afford security. Lastly, the paper recommended that future researcher focus on the
blockchain on which to develop applications and allow for integration, uniformity among
solution.
2
Security is based on the fundamental component in term of computing and networking
technology. It is everything of network designing, planning, building and operating a network. It
has become more important to protect personal computer users, organizations. With advent of
internet, security is becoming a major concern due to intellectual property which can easily
acquire through internet. Therefore, networking infrastructure worldwide and needed to different
security mechanism. Furthermore, research study is adapting the block chain technology in term
of network infrastructure security. This paper looked at several use of block chain in network
security within industry. In order to examine the way to highlight through study which block
chain can afford security. Lastly, the paper recommended that future researcher focus on the
blockchain on which to develop applications and allow for integration, uniformity among
solution.
2

Contents
ABSTRACT....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
Related work................................................................................................................................4
Research methodology.................................................................................................................5
Result and analysis......................................................................................................................5
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................7
3
ABSTRACT....................................................................................................................................2
INTRODUCTION...........................................................................................................................4
Related work................................................................................................................................4
Research methodology.................................................................................................................5
Result and analysis......................................................................................................................5
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................7
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
Network security management is another kind of situation or condition which require for
growing use of internet. Many industries are essential to concern about the basic security aspects.
In order to prevent against malicious attack from hacking and spamming. IT professional has
adapted the blockchain as a revolutionary technology. It is the set to change future of computing
and disrupt several industries with more innovative solution. This technology is based on the
immutable and distributed (You, Oh and Lee, 2018). Thus, practically applicable in many
environment or culture. The modern technology has gained massive appeal from translating
cryptographically chained blocks. Therefore, network infrastructure can be highly beneficial in
offering solution by adapting block chain technology. In order to secure or protect in proper
manner.
Related work
According to Gritzalis, Theocharidou and Stergiopoulos (2019) the blocks in blockchain
can never be modified since doing and affects the integrity of all subsequent blocks. It implies
that causes to be taken when adding blocks to chain and ensure that there will be require to
change it. On the other hand, blockchain network that can add more block by broadcasting it to
another nodes. It allows them to see entire block chain at specific time intervals. The work is
generally set of complex calculation whereas each nodes maintain the security aspects in proper
manner. This can be done by computational power which always supports for maintaining
network and infrastructure of industries.
4
Network security management is another kind of situation or condition which require for
growing use of internet. Many industries are essential to concern about the basic security aspects.
In order to prevent against malicious attack from hacking and spamming. IT professional has
adapted the blockchain as a revolutionary technology. It is the set to change future of computing
and disrupt several industries with more innovative solution. This technology is based on the
immutable and distributed (You, Oh and Lee, 2018). Thus, practically applicable in many
environment or culture. The modern technology has gained massive appeal from translating
cryptographically chained blocks. Therefore, network infrastructure can be highly beneficial in
offering solution by adapting block chain technology. In order to secure or protect in proper
manner.
Related work
According to Gritzalis, Theocharidou and Stergiopoulos (2019) the blocks in blockchain
can never be modified since doing and affects the integrity of all subsequent blocks. It implies
that causes to be taken when adding blocks to chain and ensure that there will be require to
change it. On the other hand, blockchain network that can add more block by broadcasting it to
another nodes. It allows them to see entire block chain at specific time intervals. The work is
generally set of complex calculation whereas each nodes maintain the security aspects in proper
manner. This can be done by computational power which always supports for maintaining
network and infrastructure of industries.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
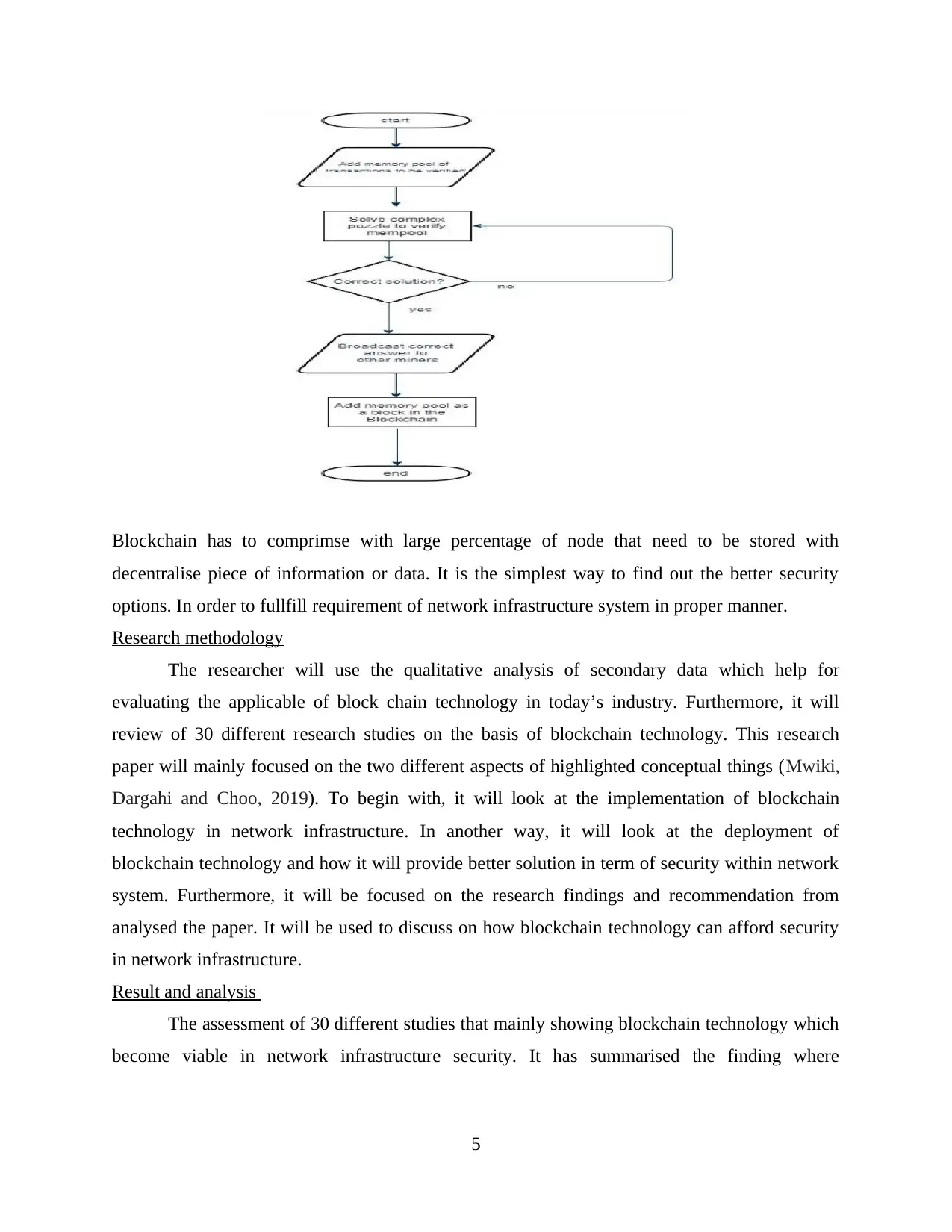
Blockchain has to comprimse with large percentage of node that need to be stored with
decentralise piece of information or data. It is the simplest way to find out the better security
options. In order to fullfill requirement of network infrastructure system in proper manner.
Research methodology
The researcher will use the qualitative analysis of secondary data which help for
evaluating the applicable of block chain technology in today’s industry. Furthermore, it will
review of 30 different research studies on the basis of blockchain technology. This research
paper will mainly focused on the two different aspects of highlighted conceptual things (Mwiki,
Dargahi and Choo, 2019). To begin with, it will look at the implementation of blockchain
technology in network infrastructure. In another way, it will look at the deployment of
blockchain technology and how it will provide better solution in term of security within network
system. Furthermore, it will be focused on the research findings and recommendation from
analysed the paper. It will be used to discuss on how blockchain technology can afford security
in network infrastructure.
Result and analysis
The assessment of 30 different studies that mainly showing blockchain technology which
become viable in network infrastructure security. It has summarised the finding where
5
decentralise piece of information or data. It is the simplest way to find out the better security
options. In order to fullfill requirement of network infrastructure system in proper manner.
Research methodology
The researcher will use the qualitative analysis of secondary data which help for
evaluating the applicable of block chain technology in today’s industry. Furthermore, it will
review of 30 different research studies on the basis of blockchain technology. This research
paper will mainly focused on the two different aspects of highlighted conceptual things (Mwiki,
Dargahi and Choo, 2019). To begin with, it will look at the implementation of blockchain
technology in network infrastructure. In another way, it will look at the deployment of
blockchain technology and how it will provide better solution in term of security within network
system. Furthermore, it will be focused on the research findings and recommendation from
analysed the paper. It will be used to discuss on how blockchain technology can afford security
in network infrastructure.
Result and analysis
The assessment of 30 different studies that mainly showing blockchain technology which
become viable in network infrastructure security. It has summarised the finding where
5

blockchain technology useful for handling the overall processing. It should consider the public
key infrastructure, data privacy claim most of recent security implementations.
Furthermore, it is mainly focused on the blockchain security which become sustainable
since there are various devices. They have a weak security configuration and being chances of
hacked into network. Researcher is mainly focused on looking at way in which devices can be
secured and protected from other attackers. This technology is improved the security and privacy
even through existing solution offer commendable level of protection. There are still prone to be
failure.
CONCLUSION
As per analysis, it has been discussed about blockchain technology that continues to
evolve and find the security aspects within network infrastructure protection. It has been studied
and applied the innovative technology. It is highly practical in addressing current security
challenges in the network. Therefore, this paper has evaluated the current applicability of
blockchain technology. It has been observed that Blockchain technology adapting the security
within network infrastructure and data. As discussion done by secure devices which become
more reliable authentication and data transfer mechanism. In this way, it can prevent hackers
from breaching into multiple devices that directly connected with network. It can be said that
well organised manner to secure networks by using blockchain technology. Moreover, it has
recommended that future investigator look into practically way to provide the better security
solution.
6
key infrastructure, data privacy claim most of recent security implementations.
Furthermore, it is mainly focused on the blockchain security which become sustainable
since there are various devices. They have a weak security configuration and being chances of
hacked into network. Researcher is mainly focused on looking at way in which devices can be
secured and protected from other attackers. This technology is improved the security and privacy
even through existing solution offer commendable level of protection. There are still prone to be
failure.
CONCLUSION
As per analysis, it has been discussed about blockchain technology that continues to
evolve and find the security aspects within network infrastructure protection. It has been studied
and applied the innovative technology. It is highly practical in addressing current security
challenges in the network. Therefore, this paper has evaluated the current applicability of
blockchain technology. It has been observed that Blockchain technology adapting the security
within network infrastructure and data. As discussion done by secure devices which become
more reliable authentication and data transfer mechanism. In this way, it can prevent hackers
from breaching into multiple devices that directly connected with network. It can be said that
well organised manner to secure networks by using blockchain technology. Moreover, it has
recommended that future investigator look into practically way to provide the better security
solution.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Book and Journals
Gritzalis, D., Theocharidou, M. and Stergiopoulos, G., 2019. Critical Infrastructure Security and
Resilience. Springer, Cham.
Mwiki, H., Dargahi, T. and Choo, K.K.R., 2019. Analysis and triage of advanced hacking groups
targeting western countries critical national infrastructure: APT28, RED October, and
Regin. In Critical Infrastructure Security and Resilience (pp. 221-244). Springer, Cham.
You, Y., Oh, J. and Lee, K., 2018. Advanced approach to information security management
system utilizing maturity models in critical infrastructure. KSII Transactions on Internet &
Information Systems, 12(10).
7
Book and Journals
Gritzalis, D., Theocharidou, M. and Stergiopoulos, G., 2019. Critical Infrastructure Security and
Resilience. Springer, Cham.
Mwiki, H., Dargahi, T. and Choo, K.K.R., 2019. Analysis and triage of advanced hacking groups
targeting western countries critical national infrastructure: APT28, RED October, and
Regin. In Critical Infrastructure Security and Resilience (pp. 221-244). Springer, Cham.
You, Y., Oh, J. and Lee, K., 2018. Advanced approach to information security management
system utilizing maturity models in critical infrastructure. KSII Transactions on Internet &
Information Systems, 12(10).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




