Comprehensive Analysis of Advanced Network Security Concepts
VerifiedAdded on 2020/03/23
|17
|2110
|63
Homework Assignment
AI Summary
This document presents a comprehensive analysis of advanced network security concepts. It begins with an examination of firewall rules, detailing their function in controlling network traffic and preventing unauthorized access. The assignment then delves into WiFi security, discussing WPA encryption, antenna configurations, RADIUS authentication, and manual rogue AP detection. Access control mechanisms, including password storage and security in active directories, are also explored. Furthermore, the document addresses HTTPS and certificates, explaining their role in securing web communications. Finally, it covers internet privacy, comparing and contrasting web proxies, VPNs, and Tor, highlighting their respective strengths and weaknesses in protecting user anonymity and data security. The assignment provides detailed explanations, practical examples, and references to relevant literature, offering a thorough understanding of the key aspects of network security.

Running head: ADVANCED NETWORK SECURITY
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK SECURITY
Table of Contents
Answer to Question 1: Firewalls.........................................................................................2
Answer to Question 2: WiFi Security..................................................................................3
a. WPA.............................................................................................................................3
b. Antennas, transmit power and AP positioning for controlling range of radio.............4
c. RADIUS.......................................................................................................................4
d. Manual detection of rogue Aps....................................................................................5
Answer to Question 3: Access Control................................................................................6
Answer to Question 4: HTTPS and Certificates................................................................11
Answer to Question 5: Internet Privacy.............................................................................13
Bibliography......................................................................................................................15
ADVANCED NETWORK SECURITY
Table of Contents
Answer to Question 1: Firewalls.........................................................................................2
Answer to Question 2: WiFi Security..................................................................................3
a. WPA.............................................................................................................................3
b. Antennas, transmit power and AP positioning for controlling range of radio.............4
c. RADIUS.......................................................................................................................4
d. Manual detection of rogue Aps....................................................................................5
Answer to Question 3: Access Control................................................................................6
Answer to Question 4: HTTPS and Certificates................................................................11
Answer to Question 5: Internet Privacy.............................................................................13
Bibliography......................................................................................................................15
2
ADVANCED NETWORK SECURITY
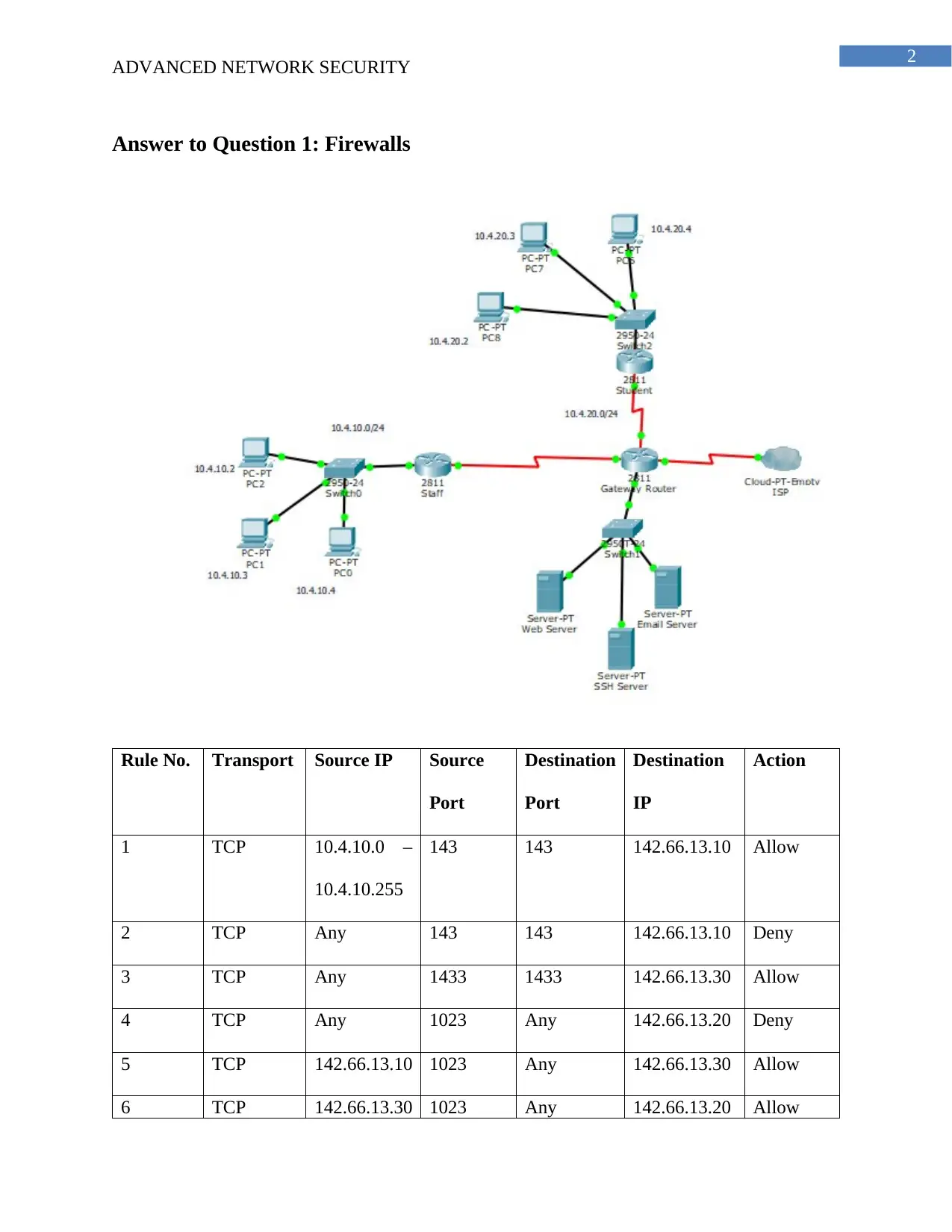
Answer to Question 1: Firewalls
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
2 TCP Any 143 143 142.66.13.10 Deny
3 TCP Any 1433 1433 142.66.13.30 Allow
4 TCP Any 1023 Any 142.66.13.20 Deny
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
ADVANCED NETWORK SECURITY
Answer to Question 1: Firewalls
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
2 TCP Any 143 143 142.66.13.10 Deny
3 TCP Any 1433 1433 142.66.13.30 Allow
4 TCP Any 1023 Any 142.66.13.20 Deny
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ADVANCED NETWORK SECURITY
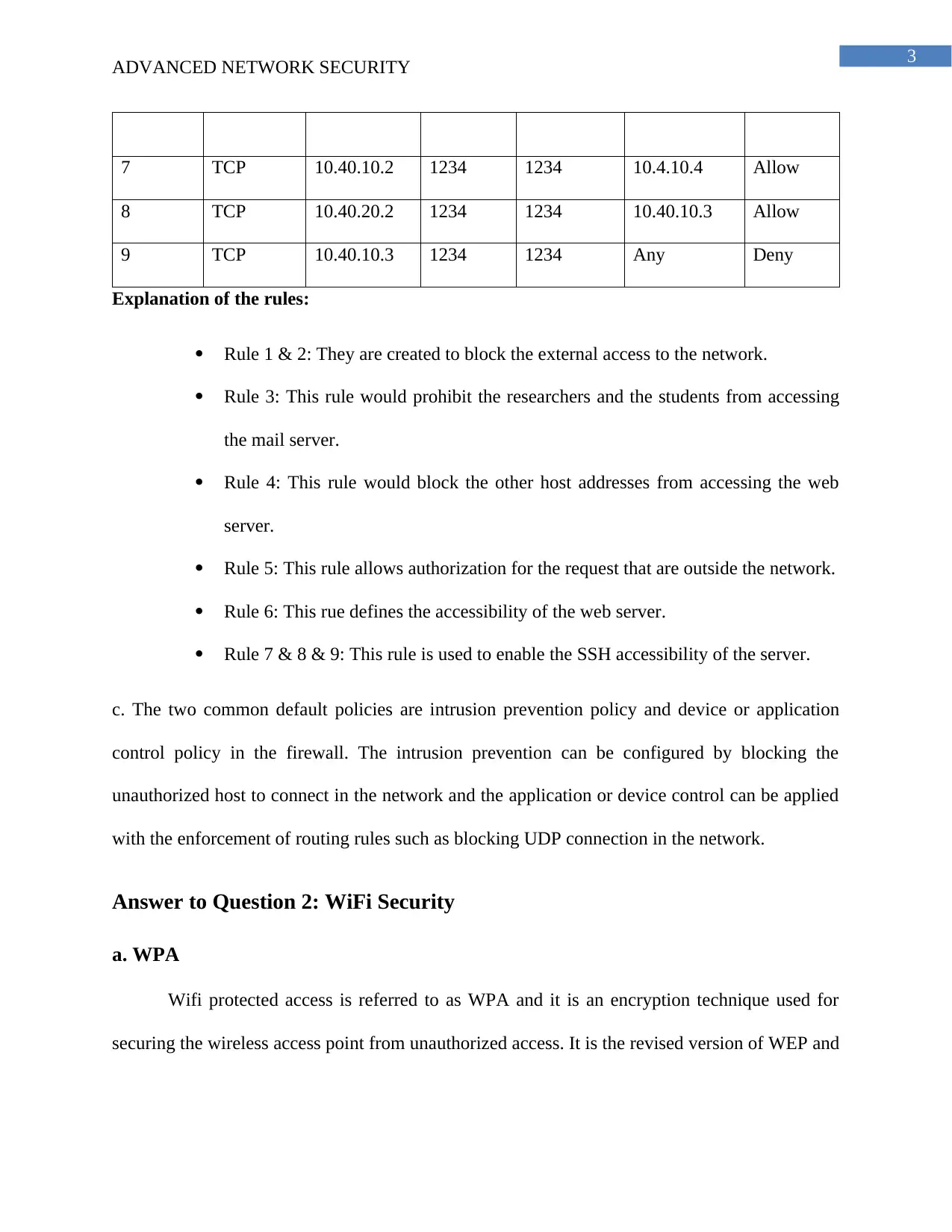
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
Explanation of the rules:
Rule 1 & 2: They are created to block the external access to the network.
Rule 3: This rule would prohibit the researchers and the students from accessing
the mail server.
Rule 4: This rule would block the other host addresses from accessing the web
server.
Rule 5: This rule allows authorization for the request that are outside the network.
Rule 6: This rue defines the accessibility of the web server.
Rule 7 & 8 & 9: This rule is used to enable the SSH accessibility of the server.
c. The two common default policies are intrusion prevention policy and device or application
control policy in the firewall. The intrusion prevention can be configured by blocking the
unauthorized host to connect in the network and the application or device control can be applied
with the enforcement of routing rules such as blocking UDP connection in the network.
Answer to Question 2: WiFi Security
a. WPA
Wifi protected access is referred to as WPA and it is an encryption technique used for
securing the wireless access point from unauthorized access. It is the revised version of WEP and
ADVANCED NETWORK SECURITY
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
Explanation of the rules:
Rule 1 & 2: They are created to block the external access to the network.
Rule 3: This rule would prohibit the researchers and the students from accessing
the mail server.
Rule 4: This rule would block the other host addresses from accessing the web
server.
Rule 5: This rule allows authorization for the request that are outside the network.
Rule 6: This rue defines the accessibility of the web server.
Rule 7 & 8 & 9: This rule is used to enable the SSH accessibility of the server.
c. The two common default policies are intrusion prevention policy and device or application
control policy in the firewall. The intrusion prevention can be configured by blocking the
unauthorized host to connect in the network and the application or device control can be applied
with the enforcement of routing rules such as blocking UDP connection in the network.
Answer to Question 2: WiFi Security
a. WPA
Wifi protected access is referred to as WPA and it is an encryption technique used for
securing the wireless access point from unauthorized access. It is the revised version of WEP and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORK SECURITY
it uses the TKIP temporal key integrity protocol for the initialization and checking the integrity
of the authentication.
WPA can operate with the WEP and increases the security of Access point. There are
different version of WPA and the most recent version is the WPA 2 and it uses the CCMP
Counter Mode Cipher Block Chaining Message Authentication Code Protocol as the encryption
algorithm for authentication and verification of the integrity of the wireless network. There are
some vulnerability related to WPA 2 such as unauthorized access of the wireless network where
the intruders have the access of the WPS access points. For the removal of the threat the WPS is
required to be disabled and increase the security of the network.
b. Antennas, transmit power and AP positioning for controlling range of radio
The performance of the wireless network depends on different factors such as the range
of the access point and the radio frequency of the wireless signals. The antennas are used for the
propagation of the radio waves and a transmitter is used for transmitting the radio waves. The
transmit power of the antenna should depend on the requirement of the wireless network and the
coverage area of the wireless access point is required to be analyzed for the development of the
wireless network. The wireless access point is required to be installed in the range of the
organization and the obstruction is required to be removed for increasing the efficiency of the
wireless network.
c. RADIUS
RADIUS stands for remote authentication dial in user service and is used for the
management of the client server and enabling remote access of the servers for communicating
with the central server. Dial up connection is used for the communication and access the
ADVANCED NETWORK SECURITY
it uses the TKIP temporal key integrity protocol for the initialization and checking the integrity
of the authentication.
WPA can operate with the WEP and increases the security of Access point. There are
different version of WPA and the most recent version is the WPA 2 and it uses the CCMP
Counter Mode Cipher Block Chaining Message Authentication Code Protocol as the encryption
algorithm for authentication and verification of the integrity of the wireless network. There are
some vulnerability related to WPA 2 such as unauthorized access of the wireless network where
the intruders have the access of the WPS access points. For the removal of the threat the WPS is
required to be disabled and increase the security of the network.
b. Antennas, transmit power and AP positioning for controlling range of radio
The performance of the wireless network depends on different factors such as the range
of the access point and the radio frequency of the wireless signals. The antennas are used for the
propagation of the radio waves and a transmitter is used for transmitting the radio waves. The
transmit power of the antenna should depend on the requirement of the wireless network and the
coverage area of the wireless access point is required to be analyzed for the development of the
wireless network. The wireless access point is required to be installed in the range of the
organization and the obstruction is required to be removed for increasing the efficiency of the
wireless network.
c. RADIUS
RADIUS stands for remote authentication dial in user service and is used for the
management of the client server and enabling remote access of the servers for communicating
with the central server. Dial up connection is used for the communication and access the

5
ADVANCED NETWORK SECURITY
resources of the network. It can be used in an organizational network for the management of the
database and share it with the remote users for maintaining transparency of the network. The
RADIUS servers helps an organization to improve its security and helps to set an organizational
policy for the administration of the single point network. It is an industrial standard and can be
used for tracking the statistics of the network and review the policy of the network.
d. Manual detection of rogue Aps
For the detection of the rogue access point manually the functionality and the ability of
the wireless network is required to be analyzed and if it is found that the wireless access point is
unauthorized and connected with the wired network then it is considered as the rogue. On the
other hand if the access point is found in the RF environment and not connected with the wired
network it is considered as interfering access point. The wireless access point is directly related
with the security threats since it is connected with the wired network. An attacker gaining the
access of the access point can intrude into the network and cause a threat for the organization. A
strong authentication is required to be used for the wireless access point for the mitigation of the
threats and increase the security of the network.
ADVANCED NETWORK SECURITY
resources of the network. It can be used in an organizational network for the management of the
database and share it with the remote users for maintaining transparency of the network. The
RADIUS servers helps an organization to improve its security and helps to set an organizational
policy for the administration of the single point network. It is an industrial standard and can be
used for tracking the statistics of the network and review the policy of the network.
d. Manual detection of rogue Aps
For the detection of the rogue access point manually the functionality and the ability of
the wireless network is required to be analyzed and if it is found that the wireless access point is
unauthorized and connected with the wired network then it is considered as the rogue. On the
other hand if the access point is found in the RF environment and not connected with the wired
network it is considered as interfering access point. The wireless access point is directly related
with the security threats since it is connected with the wired network. An attacker gaining the
access of the access point can intrude into the network and cause a threat for the organization. A
strong authentication is required to be used for the wireless access point for the mitigation of the
threats and increase the security of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
ADVANCED NETWORK SECURITY
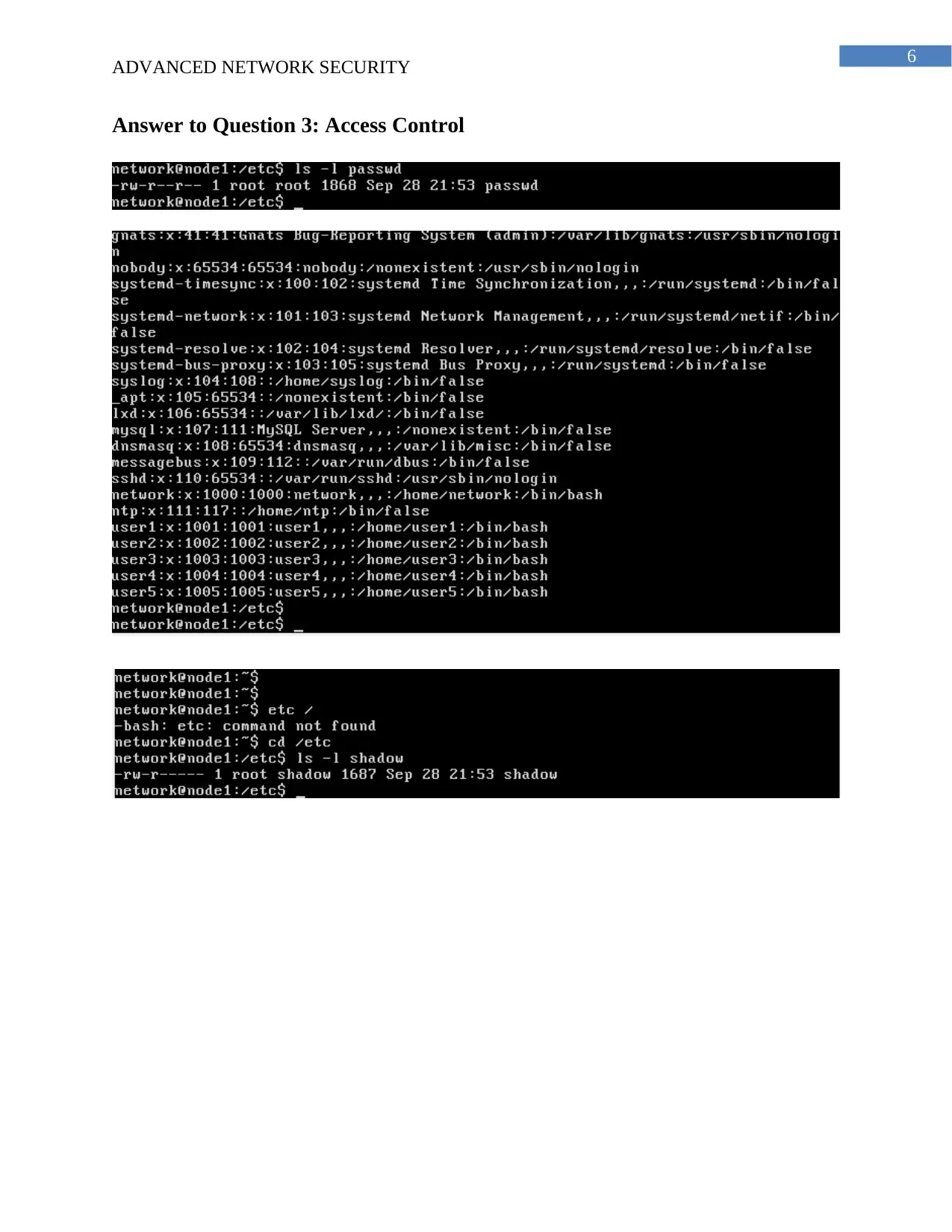
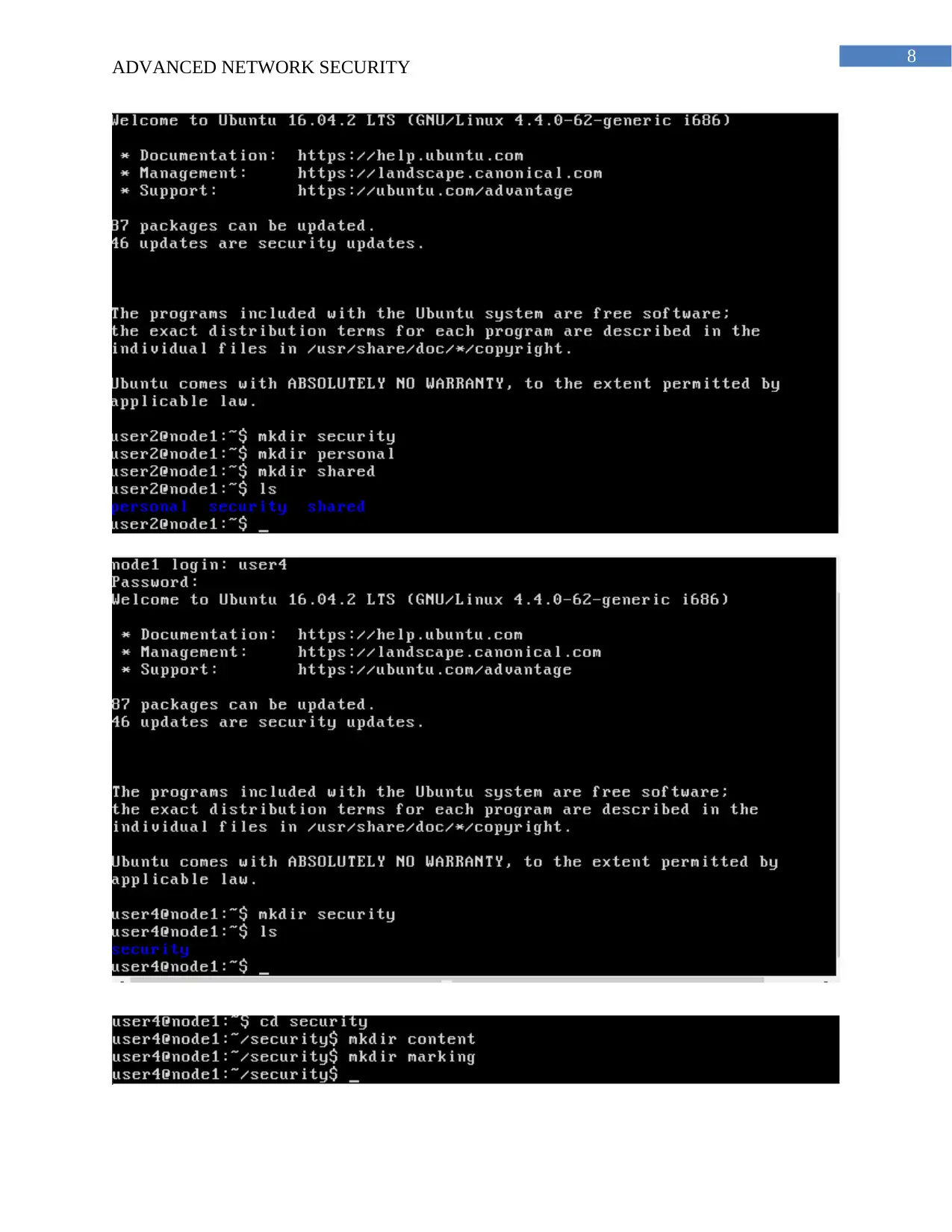
Answer to Question 3: Access Control
ADVANCED NETWORK SECURITY
Answer to Question 3: Access Control
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
8
ADVANCED NETWORK SECURITY
ADVANCED NETWORK SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
ADVANCED NETWORK SECURITY
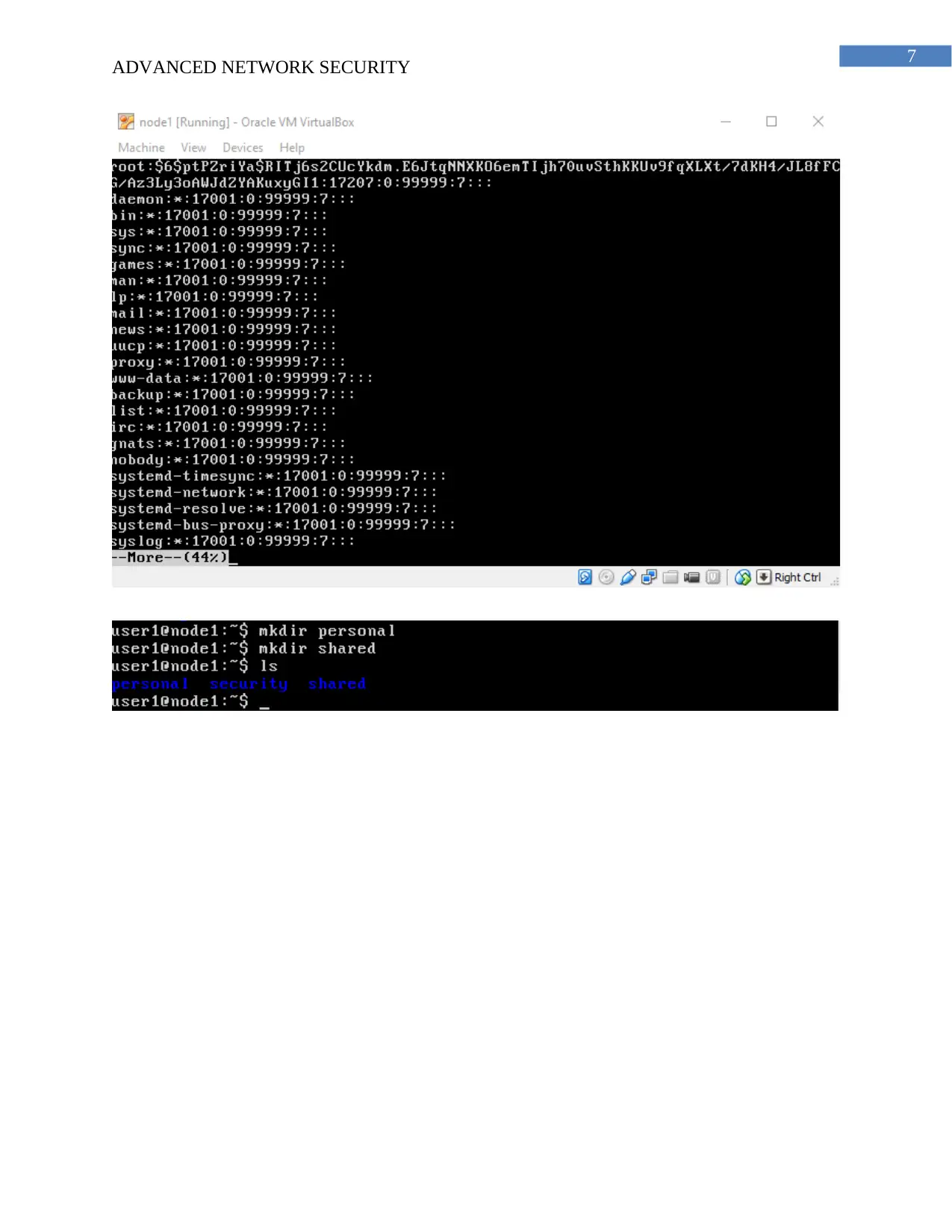
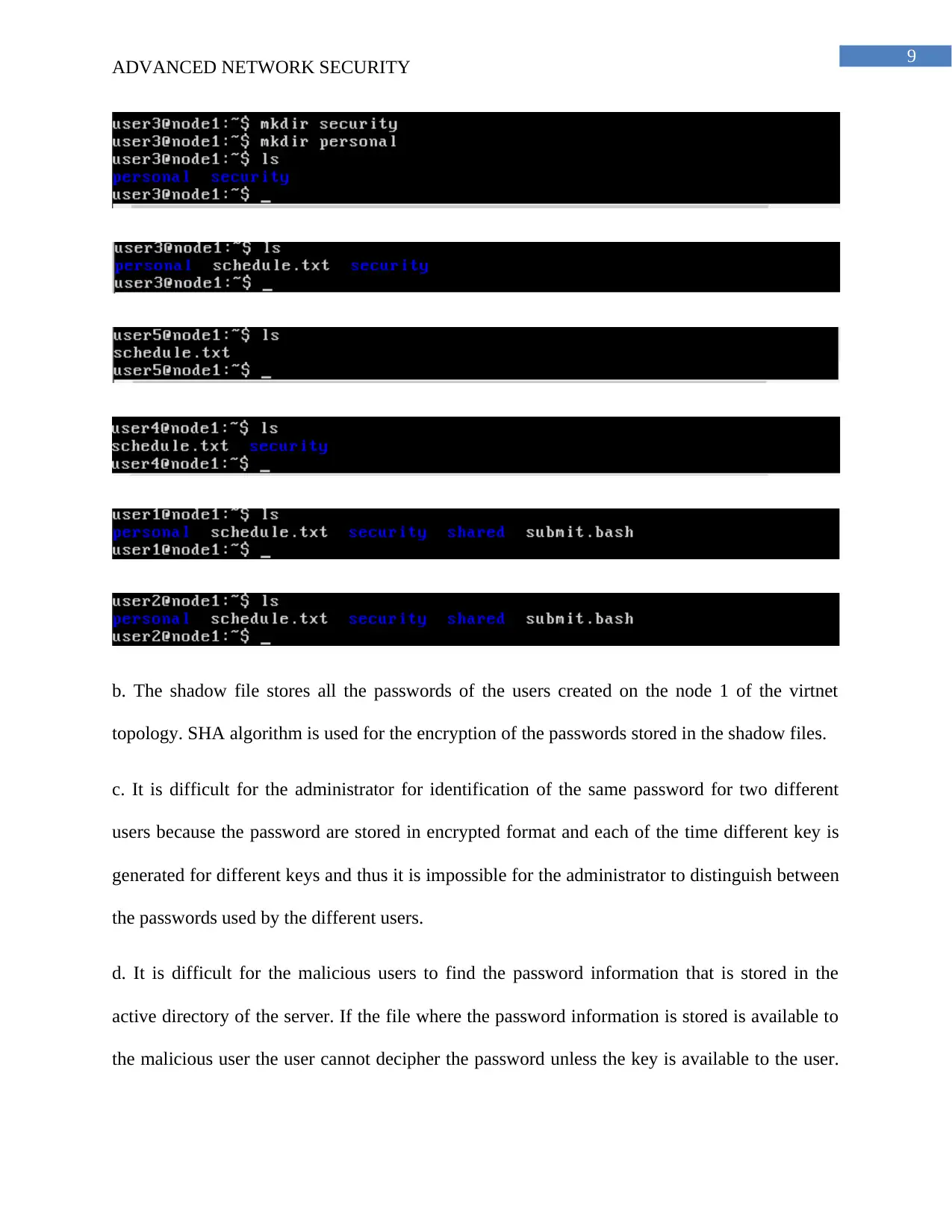
b. The shadow file stores all the passwords of the users created on the node 1 of the virtnet
topology. SHA algorithm is used for the encryption of the passwords stored in the shadow files.
c. It is difficult for the administrator for identification of the same password for two different
users because the password are stored in encrypted format and each of the time different key is
generated for different keys and thus it is impossible for the administrator to distinguish between
the passwords used by the different users.
d. It is difficult for the malicious users to find the password information that is stored in the
active directory of the server. If the file where the password information is stored is available to
the malicious user the user cannot decipher the password unless the key is available to the user.
ADVANCED NETWORK SECURITY
b. The shadow file stores all the passwords of the users created on the node 1 of the virtnet
topology. SHA algorithm is used for the encryption of the passwords stored in the shadow files.
c. It is difficult for the administrator for identification of the same password for two different
users because the password are stored in encrypted format and each of the time different key is
generated for different keys and thus it is impossible for the administrator to distinguish between
the passwords used by the different users.
d. It is difficult for the malicious users to find the password information that is stored in the
active directory of the server. If the file where the password information is stored is available to
the malicious user the user cannot decipher the password unless the key is available to the user.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ADVANCED NETWORK SECURITY
All the information is stored in cipher text and it requires the public and the private key for
getting the actual content.
ADVANCED NETWORK SECURITY
All the information is stored in cipher text and it requires the public and the private key for
getting the actual content.
11
ADVANCED NETWORK SECURITY
Answer to Question 4: HTTPS and Certificates
Topology 5 in virtnet
Deployment of MyUni demo website
ADVANCED NETWORK SECURITY
Answer to Question 4: HTTPS and Certificates
Topology 5 in virtnet
Deployment of MyUni demo website
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





