Advanced Network Security Assignment: COIT20262, Term 2, 2017
VerifiedAdded on 2020/03/23
|16
|3113
|132
Homework Assignment
AI Summary
This document presents a detailed solution to an advanced network security assignment (COIT20262, Term 2, 2017). The assignment covers various aspects of network security, including firewalls (network diagrams, firewall rules, and default policies), Wi-Fi security (WPA, antenna usage, RADIUS, and rogue AP detection), access control (file systems, password storage in Linux, and administrator challenges), HTTPS and certificates (certificate verification, signature generation, and potential attacks), and internet privacy (web proxies, VPNs, and Tor). The solution provides explanations, diagrams, and code snippets where necessary, offering a comprehensive understanding of the topics covered. The assignment explores practical security measures and theoretical concepts to provide a thorough overview of network security principles.

Running head: ADVANCED NETWORK SECURITY
COIT20262 - Advanced Network Security
Term 2, 2017
Student Name:
University Name:
COIT20262 - Advanced Network Security
Term 2, 2017
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ADVANCED NETWORK SECURITY
Table of Contents
Answer to Question 1: Firewalls.....................................................................................................3
a. Network diagram.....................................................................................................................3
b. Firewall rules...........................................................................................................................3
c. Explanation on two common default policies..........................................................................4
Answer to Question 2: Wi-Fi Security............................................................................................5
a. WPA.........................................................................................................................................5
b. Using antennas, transmit power and AP positioning to control radio range...........................5
c. RADIUS...................................................................................................................................6
d. Manual detection of rogue Aps................................................................................................6
Answer to Question 3: Access Control............................................................................................7
a. Files using topology 1..............................................................................................................7
b. Storage of password information in Linux..............................................................................7
c. Explanation on the difficulty of an administrator....................................................................8
d. Explanation on difficulty of finding users’ actual passwords.................................................8
Answer to Question 4: HTTPS and Certificates..............................................................................8
a. Certificate certificate.pem and HTTPS traffic capture https.pcap file.....................................9
b. Explanation on how the client obtains the certificate of the web server...............................10
c. Explanation on how client verifies the certificate of the web server.....................................10
d. Explanation on how signature is generated...........................................................................11
Table of Contents
Answer to Question 1: Firewalls.....................................................................................................3
a. Network diagram.....................................................................................................................3
b. Firewall rules...........................................................................................................................3
c. Explanation on two common default policies..........................................................................4
Answer to Question 2: Wi-Fi Security............................................................................................5
a. WPA.........................................................................................................................................5
b. Using antennas, transmit power and AP positioning to control radio range...........................5
c. RADIUS...................................................................................................................................6
d. Manual detection of rogue Aps................................................................................................6
Answer to Question 3: Access Control............................................................................................7
a. Files using topology 1..............................................................................................................7
b. Storage of password information in Linux..............................................................................7
c. Explanation on the difficulty of an administrator....................................................................8
d. Explanation on difficulty of finding users’ actual passwords.................................................8
Answer to Question 4: HTTPS and Certificates..............................................................................8
a. Certificate certificate.pem and HTTPS traffic capture https.pcap file.....................................9
b. Explanation on how the client obtains the certificate of the web server...............................10
c. Explanation on how client verifies the certificate of the web server.....................................10
d. Explanation on how signature is generated...........................................................................11

2ADVANCED NETWORK SECURITY
e. Explanation on the attack that can be performed by a malicious user...................................11
Answer to Question 5: Internet Privacy.........................................................................................12
a. Web proxies...........................................................................................................................12
b. VPNs......................................................................................................................................12
c. Tor..........................................................................................................................................12
Bibliography..................................................................................................................................14
e. Explanation on the attack that can be performed by a malicious user...................................11
Answer to Question 5: Internet Privacy.........................................................................................12
a. Web proxies...........................................................................................................................12
b. VPNs......................................................................................................................................12
c. Tor..........................................................................................................................................12
Bibliography..................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3ADVANCED NETWORK SECURITY
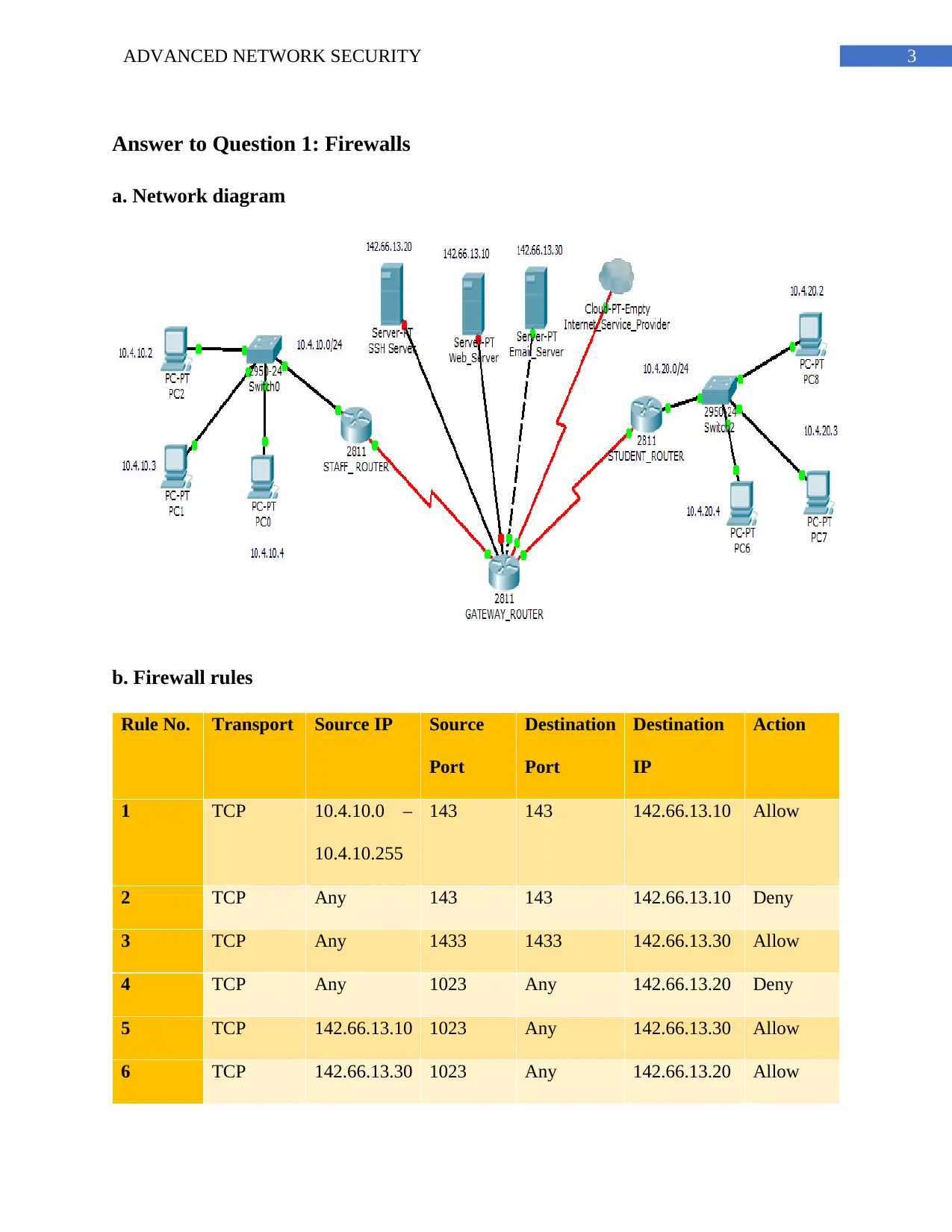
Answer to Question 1: Firewalls
a. Network diagram
b. Firewall rules
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
2 TCP Any 143 143 142.66.13.10 Deny
3 TCP Any 1433 1433 142.66.13.30 Allow
4 TCP Any 1023 Any 142.66.13.20 Deny
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
Answer to Question 1: Firewalls
a. Network diagram
b. Firewall rules
Rule No. Transport Source IP Source
Port
Destination
Port
Destination
IP
Action
1 TCP 10.4.10.0 –
10.4.10.255
143 143 142.66.13.10 Allow
2 TCP Any 143 143 142.66.13.10 Deny
3 TCP Any 1433 1433 142.66.13.30 Allow
4 TCP Any 1023 Any 142.66.13.20 Deny
5 TCP 142.66.13.10 1023 Any 142.66.13.30 Allow
6 TCP 142.66.13.30 1023 Any 142.66.13.20 Allow
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4ADVANCED NETWORK SECURITY
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
Rule 1 and 2: It is made to impede the outside access to the framework.
Rule 3: This rule would preclude the investigators and the understudies from getting to
the mail server.
Rule 4: This rule would hinder the other host delivers from getting to the web server.
Rule 5: This rule grants endorsement for the request that are outside the framework.
Rule 6: This rule portrays the accessibility of the web server.
Rule 7 and 8 and 9: This rule is used to enable the SSH accessibility of the server.
c. Explanation on two common default policies
Intrusion Prevention policy: The Intrusion Prevention arrangement consequently
distinguishes and pieces organize assaults and assaults on programs and also shields applications
from vulnerabilities.
Application and Device Control: The Application and Device Control arrangement
shields a framework's assets from applications and deals with the fringe gadgets that can append
to PCs.
7 TCP 10.40.10.2 1234 1234 10.4.10.4 Allow
8 TCP 10.40.20.2 1234 1234 10.40.10.3 Allow
9 TCP 10.40.10.3 1234 1234 Any Deny
Rule 1 and 2: It is made to impede the outside access to the framework.
Rule 3: This rule would preclude the investigators and the understudies from getting to
the mail server.
Rule 4: This rule would hinder the other host delivers from getting to the web server.
Rule 5: This rule grants endorsement for the request that are outside the framework.
Rule 6: This rule portrays the accessibility of the web server.
Rule 7 and 8 and 9: This rule is used to enable the SSH accessibility of the server.
c. Explanation on two common default policies
Intrusion Prevention policy: The Intrusion Prevention arrangement consequently
distinguishes and pieces organize assaults and assaults on programs and also shields applications
from vulnerabilities.
Application and Device Control: The Application and Device Control arrangement
shields a framework's assets from applications and deals with the fringe gadgets that can append
to PCs.

5ADVANCED NETWORK SECURITY
Answer to Question 2: Wi-Fi Security
a. WPA
WPA expands upon WEP, influencing it more to secure by including additional security
calculations and systems to battle interruption. Maybe the most essential change over WEP is a
dynamic security key trade instrument and considerably more enhanced confirmation and
encryption systems.
WPA makes use of essentially extra grounded encryption estimations than its
predecessor. WPA makes use of a transient Key Integrity Protocol (TKIP), which intensely
changes the key as information groups are dispatched over the framework for the reason that
key's constantly converting, it makes breaking the key altogether greater troublesome than that of
WEP. If the need develops to alternate the overall key, WPA will normally plug the new key to
all gadgets at the framework without having to physically change them.
Weights to the usage of WPA are few, with the great trouble being incongruence with
legacy hardware and greater settled working systems. WPA similarly has a greater execution
overhead and grows data package measure provoking longer transmission.
b. Using antennas, transmit power and AP positioning to control radio range
Remote switches, get to focuses, and connectors send and get radio wave motions
through reception apparatuses. Most switches and access focuses have outside obvious receiving
wires, however some are housed inside. Radio waves can be engaged like a light, and like light, a
few materials diminish or stop radio waves. While light engaged from a few light sources is
brighter and makes it simpler to see, a few reception apparatuses in a similar territory cause
obstruction. This diminishes radio flag lucidity and adequacy.
Answer to Question 2: Wi-Fi Security
a. WPA
WPA expands upon WEP, influencing it more to secure by including additional security
calculations and systems to battle interruption. Maybe the most essential change over WEP is a
dynamic security key trade instrument and considerably more enhanced confirmation and
encryption systems.
WPA makes use of essentially extra grounded encryption estimations than its
predecessor. WPA makes use of a transient Key Integrity Protocol (TKIP), which intensely
changes the key as information groups are dispatched over the framework for the reason that
key's constantly converting, it makes breaking the key altogether greater troublesome than that of
WEP. If the need develops to alternate the overall key, WPA will normally plug the new key to
all gadgets at the framework without having to physically change them.
Weights to the usage of WPA are few, with the great trouble being incongruence with
legacy hardware and greater settled working systems. WPA similarly has a greater execution
overhead and grows data package measure provoking longer transmission.
b. Using antennas, transmit power and AP positioning to control radio range
Remote switches, get to focuses, and connectors send and get radio wave motions
through reception apparatuses. Most switches and access focuses have outside obvious receiving
wires, however some are housed inside. Radio waves can be engaged like a light, and like light, a
few materials diminish or stop radio waves. While light engaged from a few light sources is
brighter and makes it simpler to see, a few reception apparatuses in a similar territory cause
obstruction. This diminishes radio flag lucidity and adequacy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ADVANCED NETWORK SECURITY
c. RADIUS
RADIUS is a client/server tradition. The RADIUS customer is often a NAS and the
RADIUS server is generally a daemon method going for walks on a UNIX or Windows NT
device. The patron passes consumer records to appoint RADIUS servers and follows up at the
response this is returned variety servers get client affiliation requests, affirm the patron, and after
that access the setup facts critical for the purchaser to bypass on enterprise to the consumer. A
RADIUS server can go approximately as a go-between consumer to various RADIUS servers or
numerous styles of confirmation servers. Useful for littler situations in which just a couple of
Active Directory or RADIUS accounts are included. PS Series Group Administrator controls
which client accounts are in the gathering.
In the event that clients are expelled from the Active Directory Group, the records stay in
the PS Series Group, meaning something negative for the most extreme number of client
accounts. The gathering manager should physically expel unused Active Directory and LDAP
accounts.
d. Manual detection of rogue Aps
One of the essential worries that security experts express concerning WLANs is rebel
APs. Maverick APs can be APs that are associated with the endeavor wired LAN without
approval or APs that are not associated with the wired LAN but rather that acknowledge
relationship from customers. Rebel APs can even be APs with a remote card and an
extraordinary programming bundle that influences them to go about as an AP. The maverick APs
that are associated with the wired LAN are a security concern since they will not be secured by a
partnership's security approach; this thus makes a defenselessness in the venture arrange. The
c. RADIUS
RADIUS is a client/server tradition. The RADIUS customer is often a NAS and the
RADIUS server is generally a daemon method going for walks on a UNIX or Windows NT
device. The patron passes consumer records to appoint RADIUS servers and follows up at the
response this is returned variety servers get client affiliation requests, affirm the patron, and after
that access the setup facts critical for the purchaser to bypass on enterprise to the consumer. A
RADIUS server can go approximately as a go-between consumer to various RADIUS servers or
numerous styles of confirmation servers. Useful for littler situations in which just a couple of
Active Directory or RADIUS accounts are included. PS Series Group Administrator controls
which client accounts are in the gathering.
In the event that clients are expelled from the Active Directory Group, the records stay in
the PS Series Group, meaning something negative for the most extreme number of client
accounts. The gathering manager should physically expel unused Active Directory and LDAP
accounts.
d. Manual detection of rogue Aps
One of the essential worries that security experts express concerning WLANs is rebel
APs. Maverick APs can be APs that are associated with the endeavor wired LAN without
approval or APs that are not associated with the wired LAN but rather that acknowledge
relationship from customers. Rebel APs can even be APs with a remote card and an
extraordinary programming bundle that influences them to go about as an AP. The maverick APs
that are associated with the wired LAN are a security concern since they will not be secured by a
partnership's security approach; this thus makes a defenselessness in the venture arrange. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ADVANCED NETWORK SECURITY
maverick APs that are not associated with the wired LAN may acknowledge affiliation demands
from customers, which can hamper or deny venture customers' entrance to the corporate WLAN.
In the event that true blue neighbor APs change their remote side settings or if new
amicable neighbor APs are sent, they will not fit the pre-arranged format for inviting neighbors.
So turning on programmed aversion is a hazard and in addition visit manual examination will be
required.
Answer to Question 3: Access Control
a. Files using topology 1
b. Storage of password information in Linux
Linux passwords are stored in the /etc/shadow file. They are salted and the calculation
being utilized relies upon the specific dispersion and is configurable.
maverick APs that are not associated with the wired LAN may acknowledge affiliation demands
from customers, which can hamper or deny venture customers' entrance to the corporate WLAN.
In the event that true blue neighbor APs change their remote side settings or if new
amicable neighbor APs are sent, they will not fit the pre-arranged format for inviting neighbors.
So turning on programmed aversion is a hazard and in addition visit manual examination will be
required.
Answer to Question 3: Access Control
a. Files using topology 1
b. Storage of password information in Linux
Linux passwords are stored in the /etc/shadow file. They are salted and the calculation
being utilized relies upon the specific dispersion and is configurable.

8ADVANCED NETWORK SECURITY
c. Explanation on the difficulty of an administrator
Overseeing customer records and social affairs is a basic bit of system association inside
an affiliation. However, to do this sufficiently, an extraordinary system regulator should first
appreciate what customer records and social events are and how they work.
The fundamental reason behind customer accounts is to check the character of each
individual using a PC system. An assistant (yet in the meantime imperative) reason behind
customer accounts is to permit the per-particular fitting of advantages and access benefits.
Resources can fuse records, lists, and devices. Controlling access to these benefits is a far
reaching bit of a structure official's step by step plan; routinely the passage to an advantage is
controlled by social occasions. Social affairs are cognizant forms that can be used to bunch
customer accounts together for a regular reason. For example, if an affiliation has different
system administrators, they would all have the capacity to be set in one structure manager
gathering. The social occasion would then have the capacity to be offered agree to get the
opportunity to key structure resources. Along these lines, gatherings can be an effective device
for overseeing assets and access.
d. Explanation on difficulty of finding users’ actual passwords
A chance to break a mystery key is related to bit quality (see watchword quality), which
is a measure of the mystery key's entropy, and the purposes of enthusiasm of how the mystery
word is secured. Most procedures for mystery word breaking require the PC to convey various
confident passwords, each of which is checked. One representation is savage power part, in
which a PC tries each possible key or mystery key until the point that it succeeds. More run of
the mill strategies for watchword part, for instance, dictionary ambushes, plan checking, word
c. Explanation on the difficulty of an administrator
Overseeing customer records and social affairs is a basic bit of system association inside
an affiliation. However, to do this sufficiently, an extraordinary system regulator should first
appreciate what customer records and social events are and how they work.
The fundamental reason behind customer accounts is to check the character of each
individual using a PC system. An assistant (yet in the meantime imperative) reason behind
customer accounts is to permit the per-particular fitting of advantages and access benefits.
Resources can fuse records, lists, and devices. Controlling access to these benefits is a far
reaching bit of a structure official's step by step plan; routinely the passage to an advantage is
controlled by social occasions. Social affairs are cognizant forms that can be used to bunch
customer accounts together for a regular reason. For example, if an affiliation has different
system administrators, they would all have the capacity to be set in one structure manager
gathering. The social occasion would then have the capacity to be offered agree to get the
opportunity to key structure resources. Along these lines, gatherings can be an effective device
for overseeing assets and access.
d. Explanation on difficulty of finding users’ actual passwords
A chance to break a mystery key is related to bit quality (see watchword quality), which
is a measure of the mystery key's entropy, and the purposes of enthusiasm of how the mystery
word is secured. Most procedures for mystery word breaking require the PC to convey various
confident passwords, each of which is checked. One representation is savage power part, in
which a PC tries each possible key or mystery key until the point that it succeeds. More run of
the mill strategies for watchword part, for instance, dictionary ambushes, plan checking, word
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9ADVANCED NETWORK SECURITY
list substitution, et cetera try to reduce the amount of trials required and will generally be tried
before creature control. Higher watchword bit quality exponentially extends the amount of
candidate passwords that must be checked, all things considered, to recover the mystery key and
reduces the likelihood that the mystery word will be found in any breaking dictionary.
Answer to Question 4: HTTPS and Certificates
Topology 5
a. Certificate certificate.pem and HTTPS traffic capture https.pcap file
list substitution, et cetera try to reduce the amount of trials required and will generally be tried
before creature control. Higher watchword bit quality exponentially extends the amount of
candidate passwords that must be checked, all things considered, to recover the mystery key and
reduces the likelihood that the mystery word will be found in any breaking dictionary.
Answer to Question 4: HTTPS and Certificates
Topology 5
a. Certificate certificate.pem and HTTPS traffic capture https.pcap file
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ADVANCED NETWORK SECURITY
b. Explanation on how the client obtains the certificate of the web server
Server or SSL Certificates play out an in a general sense the same as part to Client
Certificates, except for the latter is used to recognize the client/individual and the past checks the
proprietor of the site. Server validations normally are issued to hostnames, which could be a
machine name or zone name. A web program accomplishing the server, and endorses that a SSL
server confirmation is true blue. That tells the customer that their association with the site has no
government agents and that the site is exactly who it cases to be. This security is fundamental for
electronic business, which is the reason confirmations are at present in such unlimited use.
c. Explanation on how client verifies the certificate of the web server
Every one of the three conventions give validation using authentications and secure
correspondence through an assortment of conceivable figure suites. The nonspecific term figure
suite alludes to a mix of conventions, for example, key trade, mass encryption, and message
trustworthiness. Since confirmation depends on computerized testaments, accreditation experts
(CAs) like Verisign are a vital piece of Secure Channel (Schannel). A CA is a commonly trusted
outsider that affirms the personality of an endorsement requestor (for the most part a client or
PC), and afterward issues the requestor an authentication. The authentication ties the requestor's
character to an open key. CAs additionally recharge and disavow endorsements as important. For
instance, if a customer is given a server's testament, the customer PC may endeavor to coordinate
the server's CA against the customer's rundown of confided in CAs. On the off chance that the
issuing CA is believed, the customer will confirm that the authentication is real and has not been
messed with. Microsoft Internet Explorer and Internet Information Services (IIS) make
utilization of these conventions, and ideally TLS, for Secure Hypertext Transfer Protocol
(HTTPS).
b. Explanation on how the client obtains the certificate of the web server
Server or SSL Certificates play out an in a general sense the same as part to Client
Certificates, except for the latter is used to recognize the client/individual and the past checks the
proprietor of the site. Server validations normally are issued to hostnames, which could be a
machine name or zone name. A web program accomplishing the server, and endorses that a SSL
server confirmation is true blue. That tells the customer that their association with the site has no
government agents and that the site is exactly who it cases to be. This security is fundamental for
electronic business, which is the reason confirmations are at present in such unlimited use.
c. Explanation on how client verifies the certificate of the web server
Every one of the three conventions give validation using authentications and secure
correspondence through an assortment of conceivable figure suites. The nonspecific term figure
suite alludes to a mix of conventions, for example, key trade, mass encryption, and message
trustworthiness. Since confirmation depends on computerized testaments, accreditation experts
(CAs) like Verisign are a vital piece of Secure Channel (Schannel). A CA is a commonly trusted
outsider that affirms the personality of an endorsement requestor (for the most part a client or
PC), and afterward issues the requestor an authentication. The authentication ties the requestor's
character to an open key. CAs additionally recharge and disavow endorsements as important. For
instance, if a customer is given a server's testament, the customer PC may endeavor to coordinate
the server's CA against the customer's rundown of confided in CAs. On the off chance that the
issuing CA is believed, the customer will confirm that the authentication is real and has not been
messed with. Microsoft Internet Explorer and Internet Information Services (IIS) make
utilization of these conventions, and ideally TLS, for Secure Hypertext Transfer Protocol
(HTTPS).

11ADVANCED NETWORK SECURITY
d. Explanation on how signature is generated
Usually, approval structures relied upon symmetric figuring’s, for example, at ease hash
computations that require riddle keys. The enterprise and affirmation of the puzzle keys, in any
case, can challenge a mentioned differentiating preference to this modern coordination's problem
is elliptic curve cryptography (ECC), in which each and each taking an intrigue tool have or 3
keys known as "non-public key" and "open key." The personal key is used by the originator to
sign a message, and the recipient makes use of the originator's open key to check the authenticity
of the stamp. In case a message is balanced on its way to the recipient, the stamp take a look at
misses the mark in light of the manner that the primary stamp isn't always true for the modified
message. The virtual Signature general (DSS), issued via the country wide Institute of standards
and technology (NIST), demonstrates appropriate elliptic twists, the estimation of key sets, and
propelled marks.
e. Explanation on the attack that can be performed by a malicious user
A typical misconfiguration is amid PKI evaluations is an endeavor root or undertaking
subordinate CA being keep running on an indistinguishable framework from an area controller.
Running a CA on a similar framework where different parts are facilitated opens the CA to a
more extensive assault surface that presents potential issues with execution and investigating.
Furthermore, this may acquaint issues while endeavoring with update nature later on, as there
might be prerequisites to run distinctive segments at various working framework levels. A CA
framework should keep running with just those parts and highlights introduced that are required
for its operation. Another basic part introduced on a CA is Internet Information Services (IIS) to
help the CA web enlistment pages. Try not to introduce the web enlistment pages or IIS as a
major aspect of a standard CA introduce unless there is a known business prerequisite.
d. Explanation on how signature is generated
Usually, approval structures relied upon symmetric figuring’s, for example, at ease hash
computations that require riddle keys. The enterprise and affirmation of the puzzle keys, in any
case, can challenge a mentioned differentiating preference to this modern coordination's problem
is elliptic curve cryptography (ECC), in which each and each taking an intrigue tool have or 3
keys known as "non-public key" and "open key." The personal key is used by the originator to
sign a message, and the recipient makes use of the originator's open key to check the authenticity
of the stamp. In case a message is balanced on its way to the recipient, the stamp take a look at
misses the mark in light of the manner that the primary stamp isn't always true for the modified
message. The virtual Signature general (DSS), issued via the country wide Institute of standards
and technology (NIST), demonstrates appropriate elliptic twists, the estimation of key sets, and
propelled marks.
e. Explanation on the attack that can be performed by a malicious user
A typical misconfiguration is amid PKI evaluations is an endeavor root or undertaking
subordinate CA being keep running on an indistinguishable framework from an area controller.
Running a CA on a similar framework where different parts are facilitated opens the CA to a
more extensive assault surface that presents potential issues with execution and investigating.
Furthermore, this may acquaint issues while endeavoring with update nature later on, as there
might be prerequisites to run distinctive segments at various working framework levels. A CA
framework should keep running with just those parts and highlights introduced that are required
for its operation. Another basic part introduced on a CA is Internet Information Services (IIS) to
help the CA web enlistment pages. Try not to introduce the web enlistment pages or IIS as a
major aspect of a standard CA introduce unless there is a known business prerequisite.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





