COIT20262 Term 1, 2019: Advanced Network Security Assignment 2
VerifiedAdded on 2023/03/31
|7
|1530
|156
Homework Assignment
AI Summary
This document presents a comprehensive solution to Assignment 2 for the COIT20262 Advanced Network Security course. The assignment delves into several critical areas of network security, beginning with HTTPS and certificates, exploring the hash and encryption algorithms used, and addressing security concerns in certificate authorities. The solution then examines authentication and access control, discussing password storage methods and security measures to enhance password strength. Furthermore, the assignment investigates firewalls and iptables, analyzing security implications of SSH server access and strategies for securing such servers. Finally, the assignment addresses internet privacy, comparing web proxy servers and VPNs, and evaluating their respective security and convenience limitations for both general and home user scenarios. The document provides detailed answers to each question, offering insights into network security principles and best practices.
COIT20262 Assignment 2 Submission Term 1, 2019
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 2 Submission
Due date: 5pm Friday 7 June 2019 (Week 12) ASSESSMENT
Weighting: 45%
2Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
COIT20262 - Advanced Network Security, Term 1, 2019
Assignment 2 Submission
Due date: 5pm Friday 7 June 2019 (Week 12) ASSESSMENT
Weighting: 45%
2Length: N/A
Student Name: enter your name
Student ID: id
Campus: campus
Tutor: tutor
Advanced Network Security Page 1 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 2 Submission Term 1, 2019
Question 1. HTTPS and Certificates
Part (d)
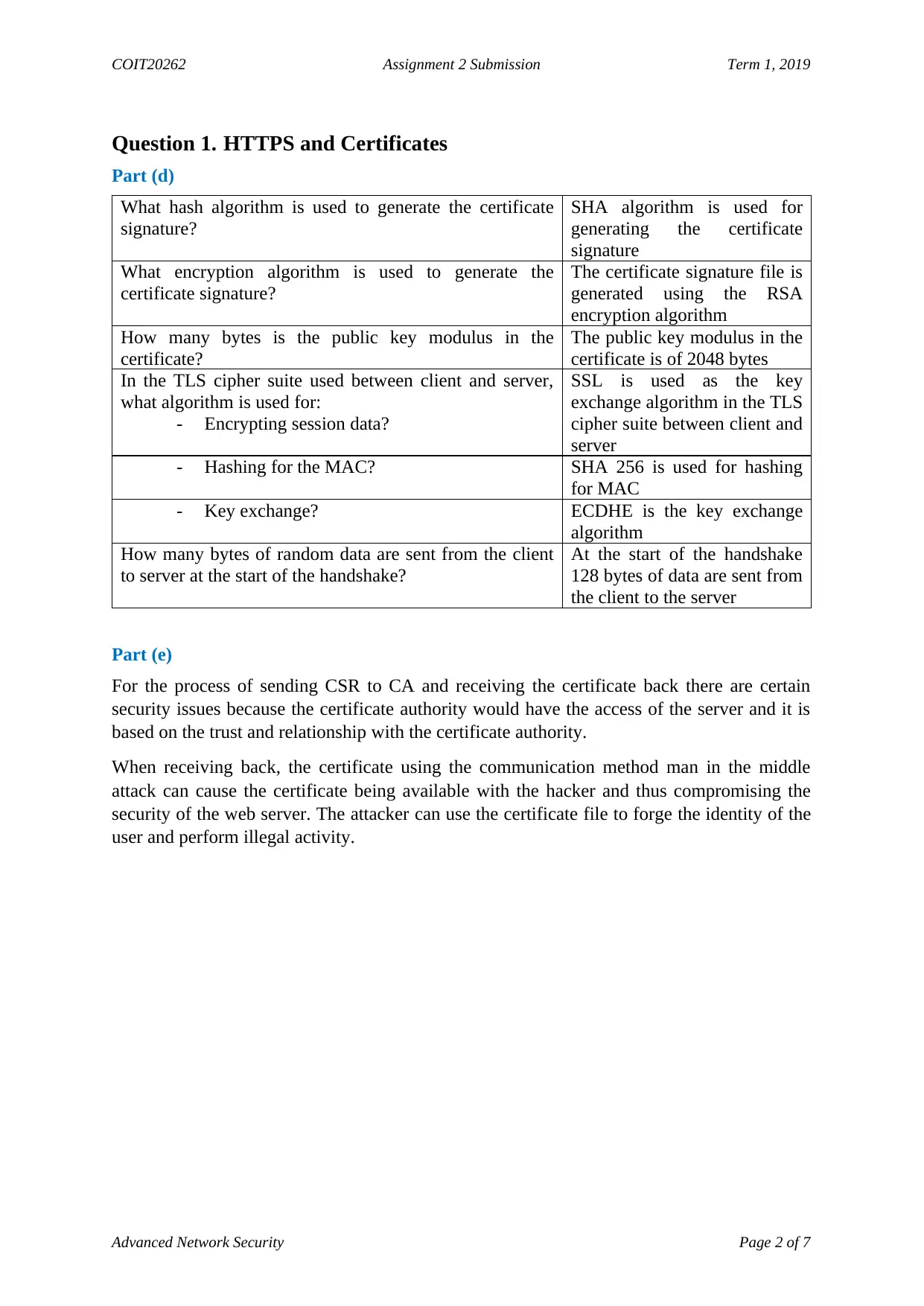
What hash algorithm is used to generate the certificate
signature?
SHA algorithm is used for
generating the certificate
signature
What encryption algorithm is used to generate the
certificate signature?
The certificate signature file is
generated using the RSA
encryption algorithm
How many bytes is the public key modulus in the
certificate?
The public key modulus in the
certificate is of 2048 bytes
In the TLS cipher suite used between client and server,
what algorithm is used for:
- Encrypting session data?
SSL is used as the key
exchange algorithm in the TLS
cipher suite between client and
server
- Hashing for the MAC? SHA 256 is used for hashing
for MAC
- Key exchange? ECDHE is the key exchange
algorithm
How many bytes of random data are sent from the client
to server at the start of the handshake?
At the start of the handshake
128 bytes of data are sent from
the client to the server
Part (e)
For the process of sending CSR to CA and receiving the certificate back there are certain
security issues because the certificate authority would have the access of the server and it is
based on the trust and relationship with the certificate authority.
When receiving back, the certificate using the communication method man in the middle
attack can cause the certificate being available with the hacker and thus compromising the
security of the web server. The attacker can use the certificate file to forge the identity of the
user and perform illegal activity.
Advanced Network Security Page 2 of 7
Question 1. HTTPS and Certificates
Part (d)
What hash algorithm is used to generate the certificate
signature?
SHA algorithm is used for
generating the certificate
signature
What encryption algorithm is used to generate the
certificate signature?
The certificate signature file is
generated using the RSA
encryption algorithm
How many bytes is the public key modulus in the
certificate?
The public key modulus in the
certificate is of 2048 bytes
In the TLS cipher suite used between client and server,
what algorithm is used for:
- Encrypting session data?
SSL is used as the key
exchange algorithm in the TLS
cipher suite between client and
server
- Hashing for the MAC? SHA 256 is used for hashing
for MAC
- Key exchange? ECDHE is the key exchange
algorithm
How many bytes of random data are sent from the client
to server at the start of the handshake?
At the start of the handshake
128 bytes of data are sent from
the client to the server
Part (e)
For the process of sending CSR to CA and receiving the certificate back there are certain
security issues because the certificate authority would have the access of the server and it is
based on the trust and relationship with the certificate authority.
When receiving back, the certificate using the communication method man in the middle
attack can cause the certificate being available with the hacker and thus compromising the
security of the web server. The attacker can use the certificate file to forge the identity of the
user and perform illegal activity.
Advanced Network Security Page 2 of 7

COIT20262 Assignment 2 Submission Term 1, 2019
Question 2. Authentication and Access Control
Part (e)
The security and convenience issues of the three different password that is selected by web
developers are given below:
/etc/shadow –
- is used for storing the password details of the user
- It is readable for the root account
- It stores the password in encrypted format
- It can be generated from the passwd file using the command pwconv
- The information changes frequently as it is related to password and password of
the user can be changed frequently.
/etc/passwd –
- is used for storing the details of the user accounts
- It stores the details in readable format for all the users
- It exists by default in the system
- It is static
/etc/groups –
- It is readable top all the users and contains the details of the group
- Commands can be used for changing the membership of the group
- Additional permission can be provided by changing the group membership
Part (f)
For increasing the chances that the user selects a good password a checking is needed to be
done for the minimum characters used for the password and search for letters, digits and a
symbol in the string used as the password. The use of common words is also checked and a
checking is needed to be done for the simultaneous three character in alphabetic order and if
one of the condition matches the password should not be accepted.
Part (g)
In Linux password is stored in the shadow file in encrypted format such that it is not available
to the people trying to break into the system. The user information as well as passwords are
kept in the system file named /etc/passwd where the passwords are stored in encrypted
format.
An encryption key or a randomly generated value between 1 to 4096 is used for encrypting
the original password. A one way hashing functionality is applied for arriving at the encoded
password for storing it in the system file. The key also known as salt is stored with encoded
password and the key cannot be used for decoding encrypted password as the encryption is a
single way.
Advanced Network Security Page 3 of 7
Question 2. Authentication and Access Control
Part (e)
The security and convenience issues of the three different password that is selected by web
developers are given below:
/etc/shadow –
- is used for storing the password details of the user
- It is readable for the root account
- It stores the password in encrypted format
- It can be generated from the passwd file using the command pwconv
- The information changes frequently as it is related to password and password of
the user can be changed frequently.
/etc/passwd –
- is used for storing the details of the user accounts
- It stores the details in readable format for all the users
- It exists by default in the system
- It is static
/etc/groups –
- It is readable top all the users and contains the details of the group
- Commands can be used for changing the membership of the group
- Additional permission can be provided by changing the group membership
Part (f)
For increasing the chances that the user selects a good password a checking is needed to be
done for the minimum characters used for the password and search for letters, digits and a
symbol in the string used as the password. The use of common words is also checked and a
checking is needed to be done for the simultaneous three character in alphabetic order and if
one of the condition matches the password should not be accepted.
Part (g)
In Linux password is stored in the shadow file in encrypted format such that it is not available
to the people trying to break into the system. The user information as well as passwords are
kept in the system file named /etc/passwd where the passwords are stored in encrypted
format.
An encryption key or a randomly generated value between 1 to 4096 is used for encrypting
the original password. A one way hashing functionality is applied for arriving at the encoded
password for storing it in the system file. The key also known as salt is stored with encoded
password and the key cannot be used for decoding encrypted password as the encryption is a
single way.
Advanced Network Security Page 3 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
COIT20262 Assignment 2 Submission Term 1, 2019
Question 3. Firewalls and iptables
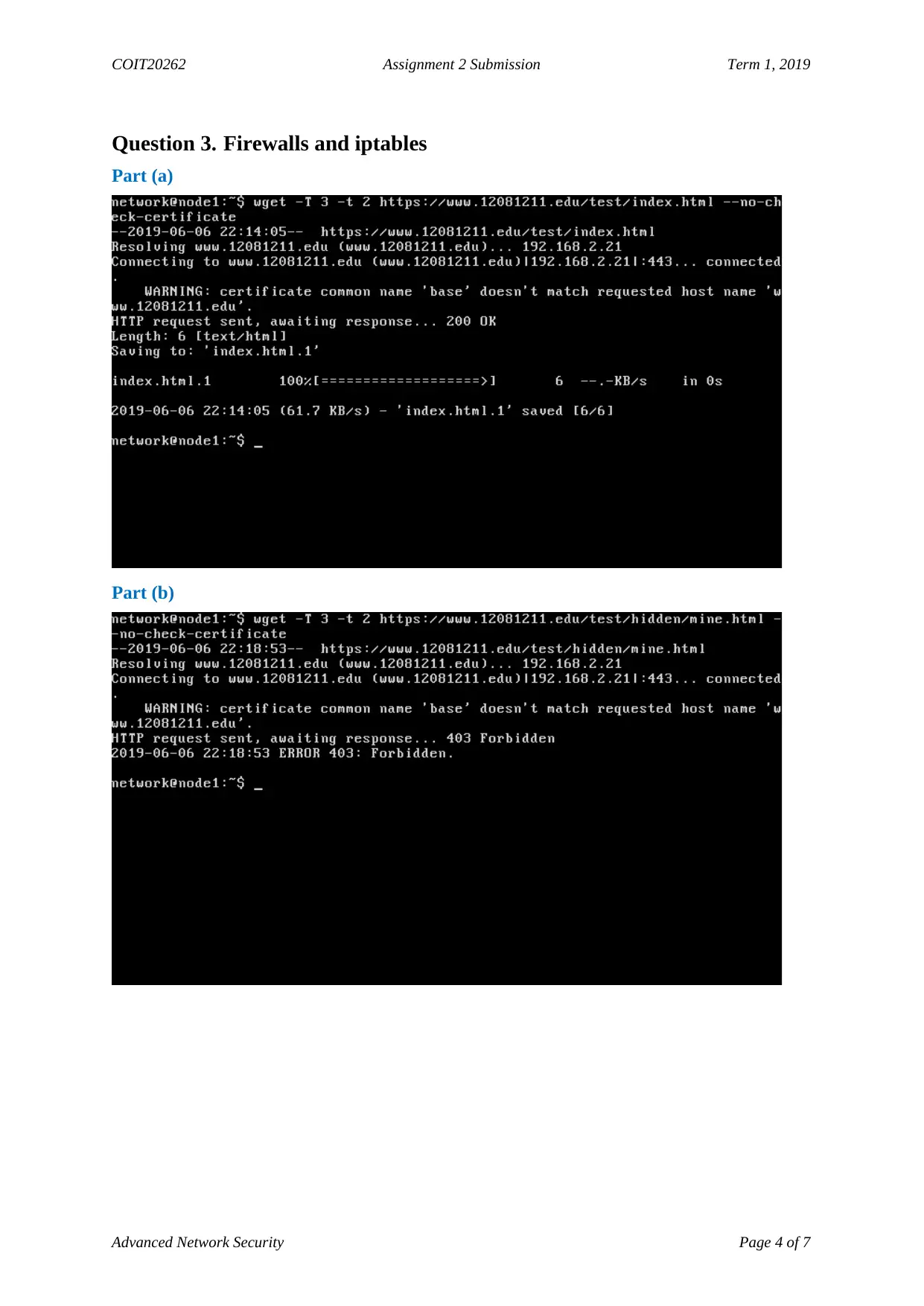
Part (a)
Part (b)
Advanced Network Security Page 4 of 7
Question 3. Firewalls and iptables
Part (a)
Part (b)
Advanced Network Security Page 4 of 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COIT20262 Assignment 2 Submission Term 1, 2019
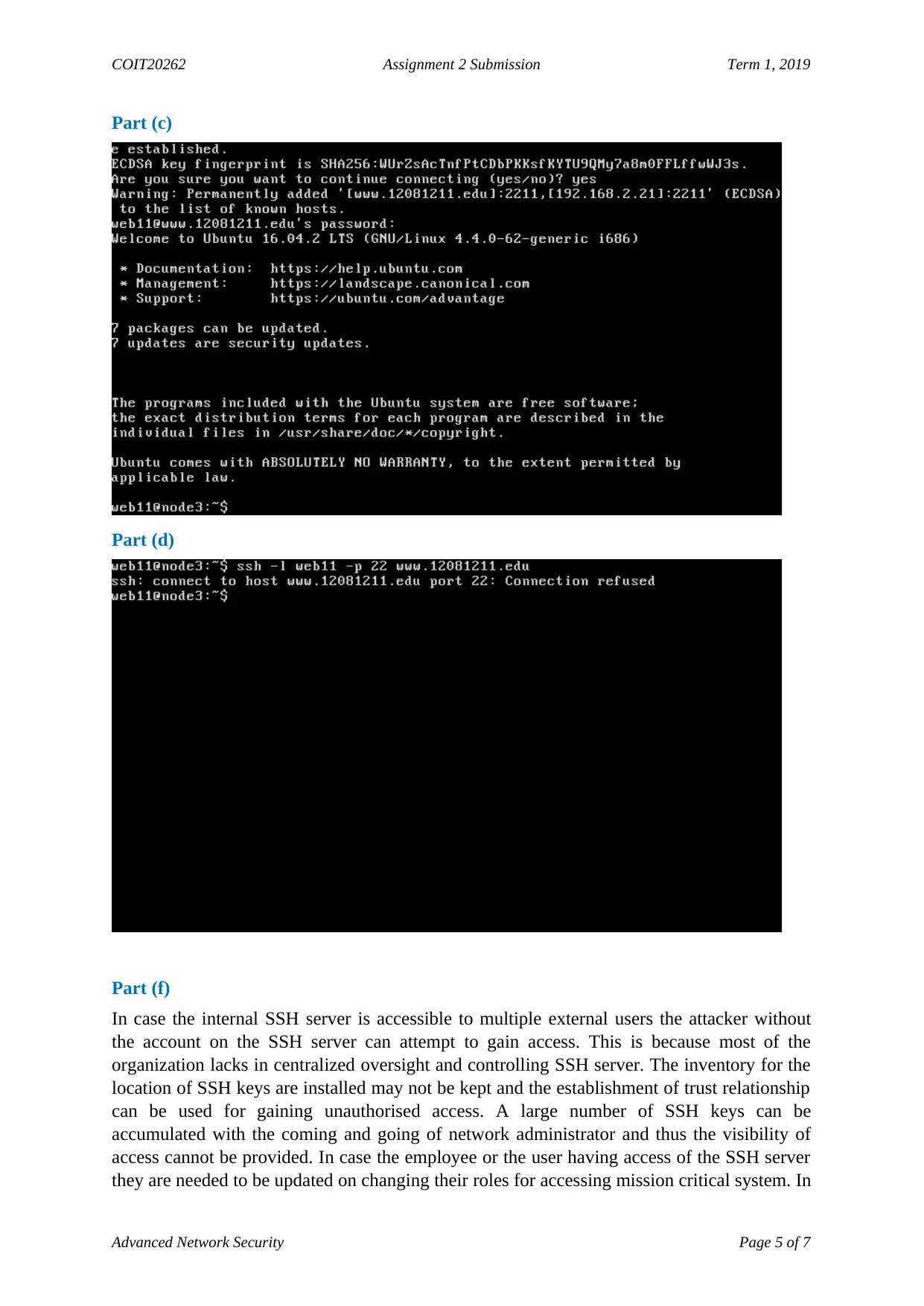
Part (c)
Part (d)
Part (f)
In case the internal SSH server is accessible to multiple external users the attacker without
the account on the SSH server can attempt to gain access. This is because most of the
organization lacks in centralized oversight and controlling SSH server. The inventory for the
location of SSH keys are installed may not be kept and the establishment of trust relationship
can be used for gaining unauthorised access. A large number of SSH keys can be
accumulated with the coming and going of network administrator and thus the visibility of
access cannot be provided. In case the employee or the user having access of the SSH server
they are needed to be updated on changing their roles for accessing mission critical system. In
Advanced Network Security Page 5 of 7
Part (c)
Part (d)
Part (f)
In case the internal SSH server is accessible to multiple external users the attacker without
the account on the SSH server can attempt to gain access. This is because most of the
organization lacks in centralized oversight and controlling SSH server. The inventory for the
location of SSH keys are installed may not be kept and the establishment of trust relationship
can be used for gaining unauthorised access. A large number of SSH keys can be
accumulated with the coming and going of network administrator and thus the visibility of
access cannot be provided. In case the employee or the user having access of the SSH server
they are needed to be updated on changing their roles for accessing mission critical system. In
Advanced Network Security Page 5 of 7

COIT20262 Assignment 2 Submission Term 1, 2019
case the attacker has the access of the SSH server the server can elevate the privilege and the
user can maintain persistent access in the system.
As an SSH server administrator there are certain countermeasures that can be applied for
increasing the security such as:
Application two layer of control for getting access of administrative console
Providing multiple layer of defence in depth
Use of standard port
Using private key pair
The limitation and negative side effect is the proper use of the technology and risk associated
with different protocols and causing the server to restrict its from connecting with rest of the
network.
Part (g)
The use of non-standard port but using high ports can keep the server out of sight from the
bots but it cannot prevent the employee to connect with internal network and transferring
virus, worms and backdoors.
Part (h)
The attacker can use different penetration testing tool for identifying the hosts active in the
network and identify the open ports and the service running on the port. Masscan can also be
used for identifying the services running on the port for a targeted IP address. The traffic
flowing in the network can also be captured for getting the information about the client and
server and identifying the servers that are blocked by the firewall.
Question 4. Internet Privacy
Part (a)
The web proxy server acts as the gateway between the client and the internet and it separates
the client from the website browsed by them. The proxy is used for providing different level
of privacy, security and privacy depending on the requirement and policy of the organization.
In case of using the proxy server the traffic flows via the proxy to reach the targeted address.
During the usage of proxy server, a user needs to configure the browser settings and input the
IP address and port number of the proxy server under the option “Manual proxy
Configuration”.
The proxy server can be used for different types of security such as:
Maintaining transparency by making the original IP address available with the use of
http headers.
Maintaining anonymity by hiding the original IP address
Maintaining distortion by making incorrect IP address available using http header
There are certain security and convenience limitations of the proxy and they are given below:
In some cases, secured data, password can be stored in cache system and looked by
the service provider
Advanced Network Security Page 6 of 7
case the attacker has the access of the SSH server the server can elevate the privilege and the
user can maintain persistent access in the system.
As an SSH server administrator there are certain countermeasures that can be applied for
increasing the security such as:
Application two layer of control for getting access of administrative console
Providing multiple layer of defence in depth
Use of standard port
Using private key pair
The limitation and negative side effect is the proper use of the technology and risk associated
with different protocols and causing the server to restrict its from connecting with rest of the
network.
Part (g)
The use of non-standard port but using high ports can keep the server out of sight from the
bots but it cannot prevent the employee to connect with internal network and transferring
virus, worms and backdoors.
Part (h)
The attacker can use different penetration testing tool for identifying the hosts active in the
network and identify the open ports and the service running on the port. Masscan can also be
used for identifying the services running on the port for a targeted IP address. The traffic
flowing in the network can also be captured for getting the information about the client and
server and identifying the servers that are blocked by the firewall.
Question 4. Internet Privacy
Part (a)
The web proxy server acts as the gateway between the client and the internet and it separates
the client from the website browsed by them. The proxy is used for providing different level
of privacy, security and privacy depending on the requirement and policy of the organization.
In case of using the proxy server the traffic flows via the proxy to reach the targeted address.
During the usage of proxy server, a user needs to configure the browser settings and input the
IP address and port number of the proxy server under the option “Manual proxy
Configuration”.
The proxy server can be used for different types of security such as:
Maintaining transparency by making the original IP address available with the use of
http headers.
Maintaining anonymity by hiding the original IP address
Maintaining distortion by making incorrect IP address available using http header
There are certain security and convenience limitations of the proxy and they are given below:
In some cases, secured data, password can be stored in cache system and looked by
the service provider
Advanced Network Security Page 6 of 7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COIT20262 Assignment 2 Submission Term 1, 2019
Although encrypted connection is used the information may get leaked with the use of
SSL and TLS encrypted connections.
The proxy servers can be used for accessing blocked websites and sometimes the
blocked websites may be offensive or cause harm to the system
Part (b)
The users using the VPN can have the following benefits:
Stay anonymous while browsing different websites
Encryption of internet traffic
Avoiding censorship in the internet
Secure access of the internet irrespective of the type of network (Public or private)
Prevention of bandwidth throttling
The limitations of VPN over web proxy are given below:
It can slow down the speed of internet since it implies more than just a server
Price is needed to be paid for good VPN service
Free VPN can cause sharing of data with 3rd parties
The connection can be recorded in logs thus VPN provider with clear NO LOGS
policy is needed to be selected
Part (c)
The security and convenience weakness for a home user using VPN for private browsing re
given below:
The online speed can be slowed down with the use of VPN
Selection of VPN is important because the wrong VPN can insecure the privacy of the
user
Quality VPN service are paid service
All the devices used for browsing may not support VPNs.
Advanced Network Security Page 7 of 7
Although encrypted connection is used the information may get leaked with the use of
SSL and TLS encrypted connections.
The proxy servers can be used for accessing blocked websites and sometimes the
blocked websites may be offensive or cause harm to the system
Part (b)
The users using the VPN can have the following benefits:
Stay anonymous while browsing different websites
Encryption of internet traffic
Avoiding censorship in the internet
Secure access of the internet irrespective of the type of network (Public or private)
Prevention of bandwidth throttling
The limitations of VPN over web proxy are given below:
It can slow down the speed of internet since it implies more than just a server
Price is needed to be paid for good VPN service
Free VPN can cause sharing of data with 3rd parties
The connection can be recorded in logs thus VPN provider with clear NO LOGS
policy is needed to be selected
Part (c)
The security and convenience weakness for a home user using VPN for private browsing re
given below:
The online speed can be slowed down with the use of VPN
Selection of VPN is important because the wrong VPN can insecure the privacy of the
user
Quality VPN service are paid service
All the devices used for browsing may not support VPNs.
Advanced Network Security Page 7 of 7
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



