Report on Advanced Network Security: Implementation and Analysis
VerifiedAdded on 2021/06/17
|10
|1144
|216
Report
AI Summary
This report provides a comprehensive overview of advanced network security concepts. It begins with cryptographic operations using OpenSSL, detailing key generation, encryption, and signing processes. The report then explores HTTPS and certificates, including the creation of virtual network topologies, web server setup, and analysis of HTTPS connections. Access control mechanisms within Linux, including user and group management, file permissions, and password configurations, are also examined. Furthermore, the report delves into firewall implementations, presenting network diagrams, firewall rules, and default policies. Finally, it discusses wireless network security, offering recommendations for secure organization networks and evaluating the security features of D-Link wireless access points. The report references relevant academic sources to support its analysis.

ADVANCED NETWORK SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Cryptographic Operations with Open SSL...............................................................................3
2. HTTPS and Certificates............................................................................................................3
3. Access Control.........................................................................................................................5
4. Firewalls...................................................................................................................................7
5. Wireless Network Security.......................................................................................................8
References......................................................................................................................................10
2
1. Cryptographic Operations with Open SSL...............................................................................3
2. HTTPS and Certificates............................................................................................................3
3. Access Control.........................................................................................................................5
4. Firewalls...................................................................................................................................7
5. Wireless Network Security.......................................................................................................8
References......................................................................................................................................10
2

1. Cryptographic Operations with Open SSL
It performs the following operations (Xiao, Shen & Du, 2011),
Extract user public key
Generate the 128 bit random value
Create new message or plain text
Sign the created message file.
Record the commands
Encrypt the message file
Also, encrypt the key text file using RAS algorithms.
Generate the RSA key pair
These file are attached in below.
2. HTTPS and Certificates
It performs the various operations like,
Create topology 4 in virtual network.
Setup the web server to support the HTTPS
Capture the traffic from web server
Analyze and test HTTPS connection.
Deploy the website
The setup web server is used to obtaining the certificate authority and it involves the following
activities (Quirolgico, Hu & Karygiannis, 2011).
Generate the Signing Request
Send the certificate signing request.
a)
The setup web server files are attached here.
b) Message Sequence Diagram
3
It performs the following operations (Xiao, Shen & Du, 2011),
Extract user public key
Generate the 128 bit random value
Create new message or plain text
Sign the created message file.
Record the commands
Encrypt the message file
Also, encrypt the key text file using RAS algorithms.
Generate the RSA key pair
These file are attached in below.
2. HTTPS and Certificates
It performs the various operations like,
Create topology 4 in virtual network.
Setup the web server to support the HTTPS
Capture the traffic from web server
Analyze and test HTTPS connection.
Deploy the website
The setup web server is used to obtaining the certificate authority and it involves the following
activities (Quirolgico, Hu & Karygiannis, 2011).
Generate the Signing Request
Send the certificate signing request.
a)
The setup web server files are attached here.
b) Message Sequence Diagram
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
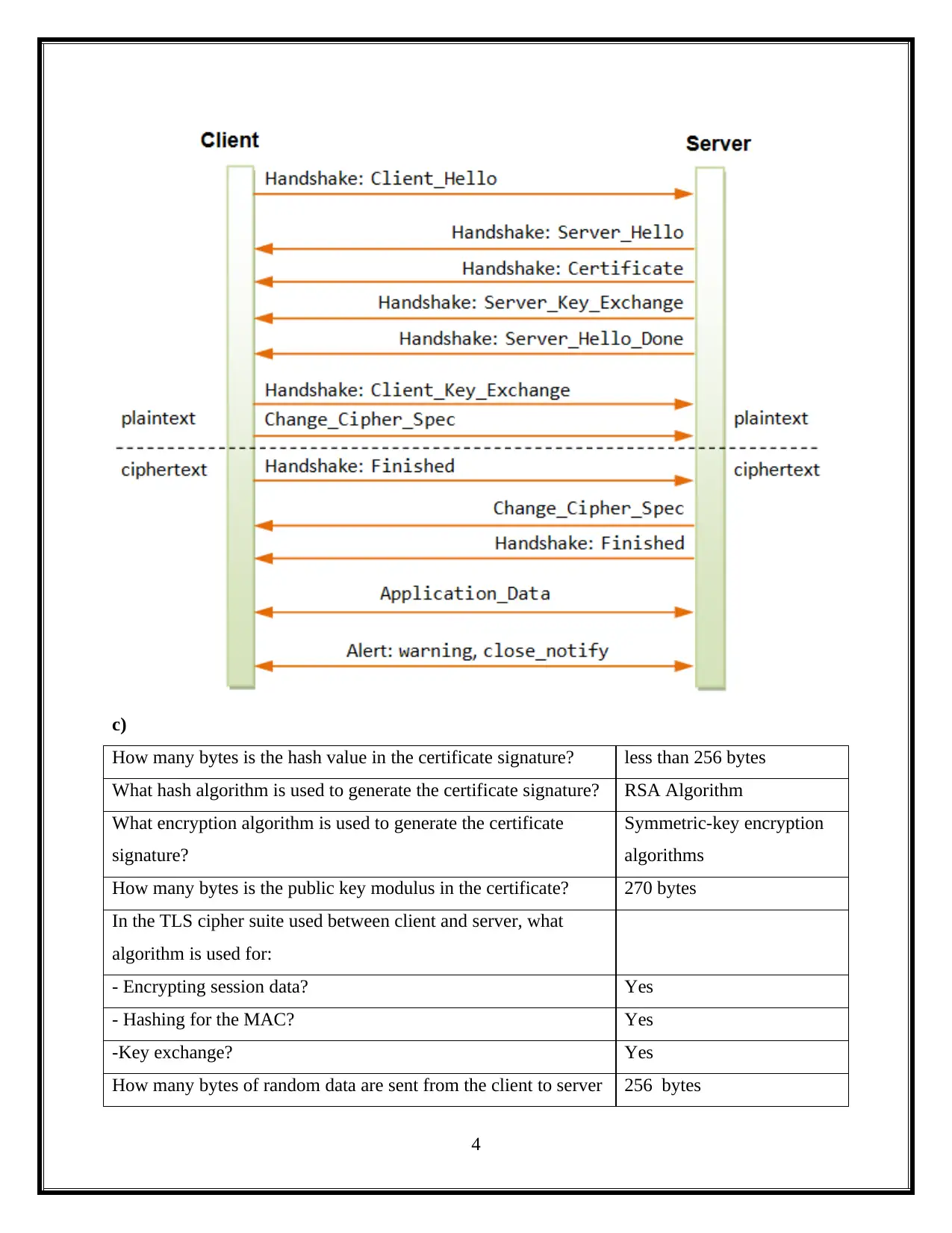
c)
How many bytes is the hash value in the certificate signature? less than 256 bytes
What hash algorithm is used to generate the certificate signature? RSA Algorithm
What encryption algorithm is used to generate the certificate
signature?
Symmetric-key encryption
algorithms
How many bytes is the public key modulus in the certificate? 270 bytes
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
-Key exchange? Yes
How many bytes of random data are sent from the client to server 256 bytes
4
How many bytes is the hash value in the certificate signature? less than 256 bytes
What hash algorithm is used to generate the certificate signature? RSA Algorithm
What encryption algorithm is used to generate the certificate
signature?
Symmetric-key encryption
algorithms
How many bytes is the public key modulus in the certificate? 270 bytes
In the TLS cipher suite used between client and server, what
algorithm is used for:
- Encrypting session data? Yes
- Hashing for the MAC? Yes
-Key exchange? Yes
How many bytes of random data are sent from the client to server 256 bytes
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

at the start of the handshake?
d)
The certificate authorities are using the self signed certificates and it has two major
drawbacks like visitors connection could be hijacked and it cannot be revoked like a trusted
certificate can. So, it needs another certificate authority’s certificate.
e)
The certificate authorities should be providing the security for private keys by storing then
offline in special hardware devices. But, attacker is use the certificate authority private key.
Because, it does not verifies the identity of the certificate applicant. So, malicious users are using
the private key.
3. Access Control
Here also we will use virtual network to study the Linux access control and passwords. It
performs the various operations such as (Pale, 2012),
Create the five new users
Creates the files and directories
Finally, test the access control.
Create two new groups
Provide the access control and rules
Also create the password
Create the new topology
a)
The files are attached here.
b)
5
d)
The certificate authorities are using the self signed certificates and it has two major
drawbacks like visitors connection could be hijacked and it cannot be revoked like a trusted
certificate can. So, it needs another certificate authority’s certificate.
e)
The certificate authorities should be providing the security for private keys by storing then
offline in special hardware devices. But, attacker is use the certificate authority private key.
Because, it does not verifies the identity of the certificate applicant. So, malicious users are using
the private key.
3. Access Control
Here also we will use virtual network to study the Linux access control and passwords. It
performs the various operations such as (Pale, 2012),
Create the five new users
Creates the files and directories
Finally, test the access control.
Create two new groups
Provide the access control and rules
Also create the password
Create the new topology
a)
The files are attached here.
b)
5

Generally, the Linux distribution is stored the user information in /etc/passwd and it
contains the user login, optional comment field, unique numerical user id, encrypted password
information and numerical group id. But the encrypted password is not stored in /etc/passwd. It
is stored in /etc/shadow file. The encrypted password also stored in /etc/passwd. It is readable by
the super user only (Sawant, Pelz, Hobson & Leemans, 2017).
c)
The role based access control is used to takes more of a real world approach to structuring
the access control. It based on a user job functions within the organization to which the computer
system belongs. It assigns the permissions to particular roles in an organization.
The mandatory based access control is the strictest of all levels of control. It enforced the
MAC environment access to all the resource objects and it controlled by setting the defined by
the system administrator.
4. Firewalls
a)
Network Diagram
6
contains the user login, optional comment field, unique numerical user id, encrypted password
information and numerical group id. But the encrypted password is not stored in /etc/passwd. It
is stored in /etc/shadow file. The encrypted password also stored in /etc/passwd. It is readable by
the super user only (Sawant, Pelz, Hobson & Leemans, 2017).
c)
The role based access control is used to takes more of a real world approach to structuring
the access control. It based on a user job functions within the organization to which the computer
system belongs. It assigns the permissions to particular roles in an organization.
The mandatory based access control is the strictest of all levels of control. It enforced the
MAC environment access to all the resource objects and it controlled by setting the defined by
the system administrator.
4. Firewalls
a)
Network Diagram
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
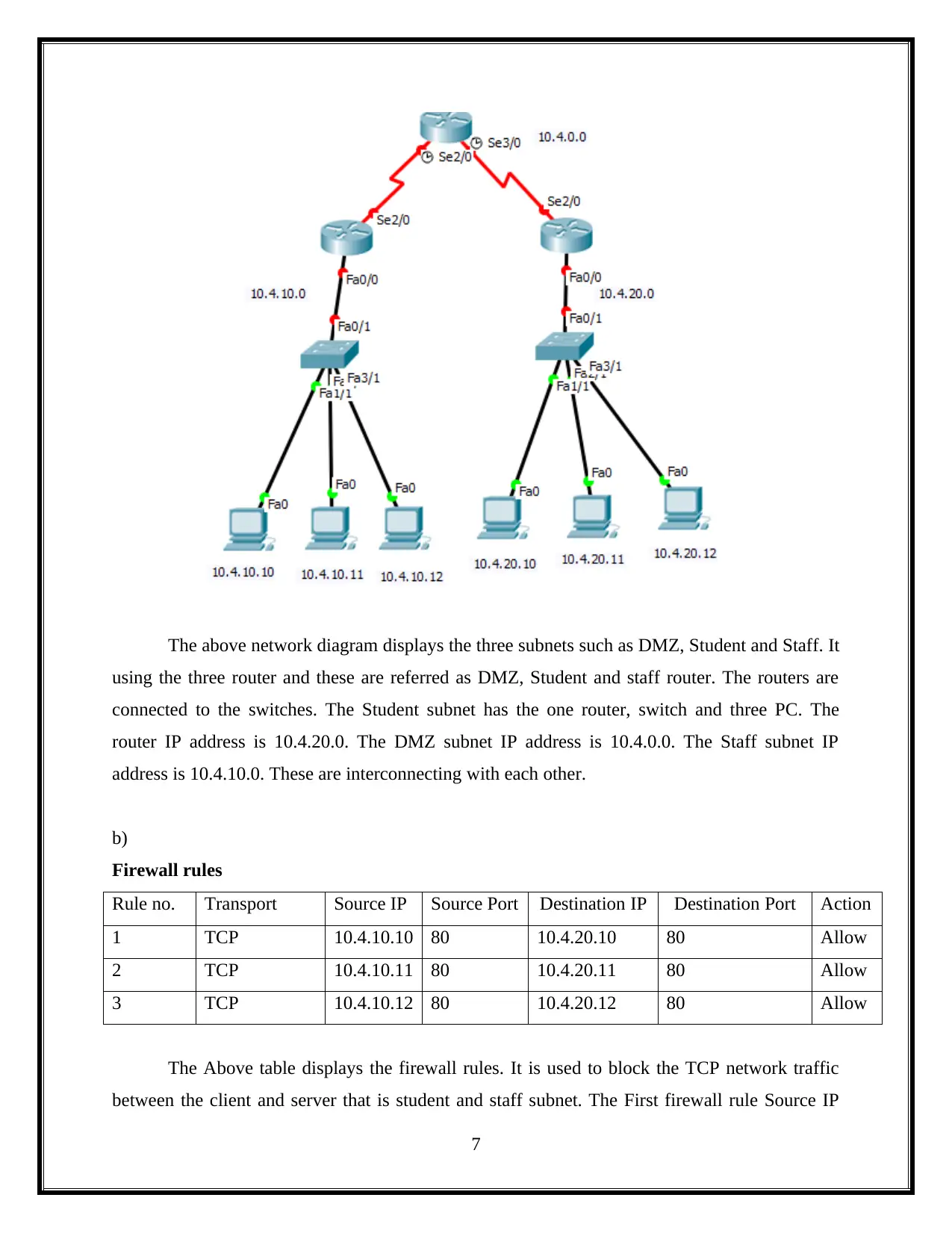
The above network diagram displays the three subnets such as DMZ, Student and Staff. It
using the three router and these are referred as DMZ, Student and staff router. The routers are
connected to the switches. The Student subnet has the one router, switch and three PC. The
router IP address is 10.4.20.0. The DMZ subnet IP address is 10.4.0.0. The Staff subnet IP
address is 10.4.10.0. These are interconnecting with each other.
b)
Firewall rules
Rule no. Transport Source IP Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
2 TCP 10.4.10.11 80 10.4.20.11 80 Allow
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
The Above table displays the firewall rules. It is used to block the TCP network traffic
between the client and server that is student and staff subnet. The First firewall rule Source IP
7
using the three router and these are referred as DMZ, Student and staff router. The routers are
connected to the switches. The Student subnet has the one router, switch and three PC. The
router IP address is 10.4.20.0. The DMZ subnet IP address is 10.4.0.0. The Staff subnet IP
address is 10.4.10.0. These are interconnecting with each other.
b)
Firewall rules
Rule no. Transport Source IP Source Port Destination IP Destination Port Action
1 TCP 10.4.10.10 80 10.4.20.10 80 Allow
2 TCP 10.4.10.11 80 10.4.20.11 80 Allow
3 TCP 10.4.10.12 80 10.4.20.12 80 Allow
The Above table displays the firewall rules. It is used to block the TCP network traffic
between the client and server that is student and staff subnet. The First firewall rule Source IP
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

address is 10.4.10.10 and destination IP address as 10.4.20.10 that means. The Firewall allows
the action to block the TCP network traffic from the source IP address to destination address.
Similarly firewall allows the action between the staff and student subnet.
c)
In IP tables, the default rule is ACCEPT everything. But, this is not secure firewall. So,
set the secure firewall by using another default policies are DROP everything. It is shown below.
5. Wireless Network Security
a)
Recommendation for secure a organization network,
Reduce WLAN transmitter Power
Enable WPA encryption instead of WEP
Secure organization wireless router and access point administration interface
Use MAC filtering for Access control
Disable remote administration
b)
The consult recommended that to select the D - Link wireless access point because it is
used to provide the network connectivity solution to small and medium sized business. It enables
the user to connect the more devices to a single internet. So, it support the small company IT
admin.
c)
Security Features for D - Link
Traffic control
8
the action to block the TCP network traffic from the source IP address to destination address.
Similarly firewall allows the action between the staff and student subnet.
c)
In IP tables, the default rule is ACCEPT everything. But, this is not secure firewall. So,
set the secure firewall by using another default policies are DROP everything. It is shown below.
5. Wireless Network Security
a)
Recommendation for secure a organization network,
Reduce WLAN transmitter Power
Enable WPA encryption instead of WEP
Secure organization wireless router and access point administration interface
Use MAC filtering for Access control
Disable remote administration
b)
The consult recommended that to select the D - Link wireless access point because it is
used to provide the network connectivity solution to small and medium sized business. It enables
the user to connect the more devices to a single internet. So, it support the small company IT
admin.
c)
Security Features for D - Link
Traffic control
8

Quality of services
Web redirection
Network access protection
WLAN partition
ARP spoofing prevention
High performance connectivity
MAC address filtering
References
Pale, P. (2012). Nmap 6. Birmingham: Packt Pub.
Quirolgico, S., Hu, V., & Karygiannis, T. (2011). Access control for SAR systems. Gaithersburg,
MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
9
Web redirection
Network access protection
WLAN partition
ARP spoofing prevention
High performance connectivity
MAC address filtering
References
Pale, P. (2012). Nmap 6. Birmingham: Packt Pub.
Quirolgico, S., Hu, V., & Karygiannis, T. (2011). Access control for SAR systems. Gaithersburg,
MD: U.S. Dept. of Commerce, National Institute of Standards and Technology.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Sawant, U., Pelz, O., Hobson, J., & Leemans, W. (2017). Linux. Birmingham: Packt Publishing.
Xiao, Y., Shen, X., & Du, D. (2011). Wireless network security. New York: Springer.
10
Xiao, Y., Shen, X., & Du, D. (2011). Wireless network security. New York: Springer.
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


