Advanced Network and Infrastructure Security Report - CCNA Security
VerifiedAdded on 2023/06/04
|11
|966
|122
Report
AI Summary
This report provides a detailed analysis of network security, covering key aspects such as network security policies, including password policies, acceptable use policies, and device management. It also outlines network equipment security guidelines, specifically for routers and switches, referencing CCNA Security labs. The report emphasizes the importance of establishing robust security measures to protect organizational assets and data. The content includes practical configurations and security best practices, offering insights into securing network devices and infrastructure. The document presents information on security policies, password construction, and acceptable use policies, providing comprehensive coverage of network security principles. The report concludes with a focus on configuring and securing network devices such as routers and switches to ensure a secure and reliable network environment.

Advanced Network and Infrastructure Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Task - 1 Network Security Policy...............................................................................................2
2. Task - 2 Security Policies.............................................................................................................2
3. Task - 3 Network Equipment Security Guidelines....................................................................3
References............................................................................................................................................9
1
1. Task - 1 Network Security Policy...............................................................................................2
2. Task - 2 Security Policies.............................................................................................................2
3. Task - 3 Network Equipment Security Guidelines....................................................................3
References............................................................................................................................................9
1

1. Task - 1 Network Security Policy
Basically, network security policy must be include the various key sections which can be
used to identify the potential issues for device access, network access, users access and other
areas. The basic security policy for an organizations are listed below 1:
Password policy
Acceptable use policy
Virtual network private policy
Extranet policy
Physical device security policy
Remote access policy
Encryption policy
Device management policy
Identity policy
Email and communications activities
Antivirus policy
The set of policies are requires the time and effort to provide the useful and effective tool
which can be administered and implemented. The well-structured security policy included the
below aspects.
Provides the procedures to follow in case of a security incident.
Provides the targets and process to audit the previous security.
Provides the next step base line in the network security evolution
Defines the overall organization responsibility for implementation, funding,
monitoring and supporting the policies.
Creates the basic for an actions of legal enforcement.
1 A. Jesin, Packet Tracer Network Simulator (2014).
2
Basically, network security policy must be include the various key sections which can be
used to identify the potential issues for device access, network access, users access and other
areas. The basic security policy for an organizations are listed below 1:
Password policy
Acceptable use policy
Virtual network private policy
Extranet policy
Physical device security policy
Remote access policy
Encryption policy
Device management policy
Identity policy
Email and communications activities
Antivirus policy
The set of policies are requires the time and effort to provide the useful and effective tool
which can be administered and implemented. The well-structured security policy included the
below aspects.
Provides the procedures to follow in case of a security incident.
Provides the targets and process to audit the previous security.
Provides the next step base line in the network security evolution
Defines the overall organization responsibility for implementation, funding,
monitoring and supporting the policies.
Creates the basic for an actions of legal enforcement.
1 A. Jesin, Packet Tracer Network Simulator (2014).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Task - 2 Security Policies
Each organization has something that another person needs. In organization, the proper
responses are differenced by resources like databases, web servers, shared drives,
indispensable organization client and representative data, imperative applications, email
servers and business data. Basically, security policies are involves the organization security
policy and principle of conduct the executives and clients and prerequisites for administration
and framework that all in guarantee the system security and computer system in an
organization 2.
Password Policy
A password policy is a policy of principles and it is used to improve the computer
security by advising clients to utilize the solid passwords. The password security is play a
important role on organization authentication management. The password policy is instructed
as a computer security mindfulness preparing. It first provide the just warning to conform that
client or not. Generally, most of the organization have national validation structures that
characterize the necessities for client verification to supported organizations including
perquisites for the password 3.
Password Construction Requirements
Be a base length of eight (8) characters on all frameworks.
Not be a lexicon word or legitimate name.
Not be the equivalent as the User ID.
Expire inside a most extreme of 90 schedule days.
Not be indistinguishable to the past ten (10) passwords.
Not be transmitted free or plaintext outside the protected area.
Not be shown when entered.
Ensure passwords are reset for approved client Rick Graziani and Bob
Vachon, Routing Protocols 4.
Acceptable use policy
Acceptable use policy is a Policy of principles connected by the supervisor of a system,
site or extensive PC framework that confine the manners by which the system, site or
framework might be utilized. Acceptable Use Policy records are composed for partnerships,
organizations, colleges, schools, web access suppliers, and site proprietors regularly to
2 Connecting Networks Companion Guide (Cisco Press, 2014).
3 George Eliot, The Mill On The Floss (BiblioLife, 2009).
4 Rick Graziani and Bob Vachon, Routing Protocols (Cisco Press, 2014).
3
Each organization has something that another person needs. In organization, the proper
responses are differenced by resources like databases, web servers, shared drives,
indispensable organization client and representative data, imperative applications, email
servers and business data. Basically, security policies are involves the organization security
policy and principle of conduct the executives and clients and prerequisites for administration
and framework that all in guarantee the system security and computer system in an
organization 2.
Password Policy
A password policy is a policy of principles and it is used to improve the computer
security by advising clients to utilize the solid passwords. The password security is play a
important role on organization authentication management. The password policy is instructed
as a computer security mindfulness preparing. It first provide the just warning to conform that
client or not. Generally, most of the organization have national validation structures that
characterize the necessities for client verification to supported organizations including
perquisites for the password 3.
Password Construction Requirements
Be a base length of eight (8) characters on all frameworks.
Not be a lexicon word or legitimate name.
Not be the equivalent as the User ID.
Expire inside a most extreme of 90 schedule days.
Not be indistinguishable to the past ten (10) passwords.
Not be transmitted free or plaintext outside the protected area.
Not be shown when entered.
Ensure passwords are reset for approved client Rick Graziani and Bob
Vachon, Routing Protocols 4.
Acceptable use policy
Acceptable use policy is a Policy of principles connected by the supervisor of a system,
site or extensive PC framework that confine the manners by which the system, site or
framework might be utilized. Acceptable Use Policy records are composed for partnerships,
organizations, colleges, schools, web access suppliers, and site proprietors regularly to
2 Connecting Networks Companion Guide (Cisco Press, 2014).
3 George Eliot, The Mill On The Floss (BiblioLife, 2009).
4 Rick Graziani and Bob Vachon, Routing Protocols (Cisco Press, 2014).
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

decrease the potential for lawful move that might be made by a client. Acceptable Use
Policies are a necessary piece of the structure of data security strategies; usually regular
practice to solicit new individuals from an organization to sign such a report before they are
offered access to its data frameworks. Therefore, an AUP must be compact and clear, while
in the meantime covering the most critical focuses about what clients are, and are not,
permitted to do with the IT frameworks of an organization Network Basics Companion Guide
5.
3. Task - 3 Network Equipment Security Guidelines
This task is used to create the network equipment security guidelines. So, user needs to
review the objective from the previous CCNA security labs. After, create the network device
security guideless document for router and switch security. This task must reinforce and
supplement the information presented in a basic security policy and it depends on the
previous CCNA security labs.
On Switch Device
The network security for switch devices is illustrated as below.
For Switch 1,
5 Network Basics Companion Guide (2013).
4
Policies are a necessary piece of the structure of data security strategies; usually regular
practice to solicit new individuals from an organization to sign such a report before they are
offered access to its data frameworks. Therefore, an AUP must be compact and clear, while
in the meantime covering the most critical focuses about what clients are, and are not,
permitted to do with the IT frameworks of an organization Network Basics Companion Guide
5.
3. Task - 3 Network Equipment Security Guidelines
This task is used to create the network equipment security guidelines. So, user needs to
review the objective from the previous CCNA security labs. After, create the network device
security guideless document for router and switch security. This task must reinforce and
supplement the information presented in a basic security policy and it depends on the
previous CCNA security labs.
On Switch Device
The network security for switch devices is illustrated as below.
For Switch 1,
5 Network Basics Companion Guide (2013).
4
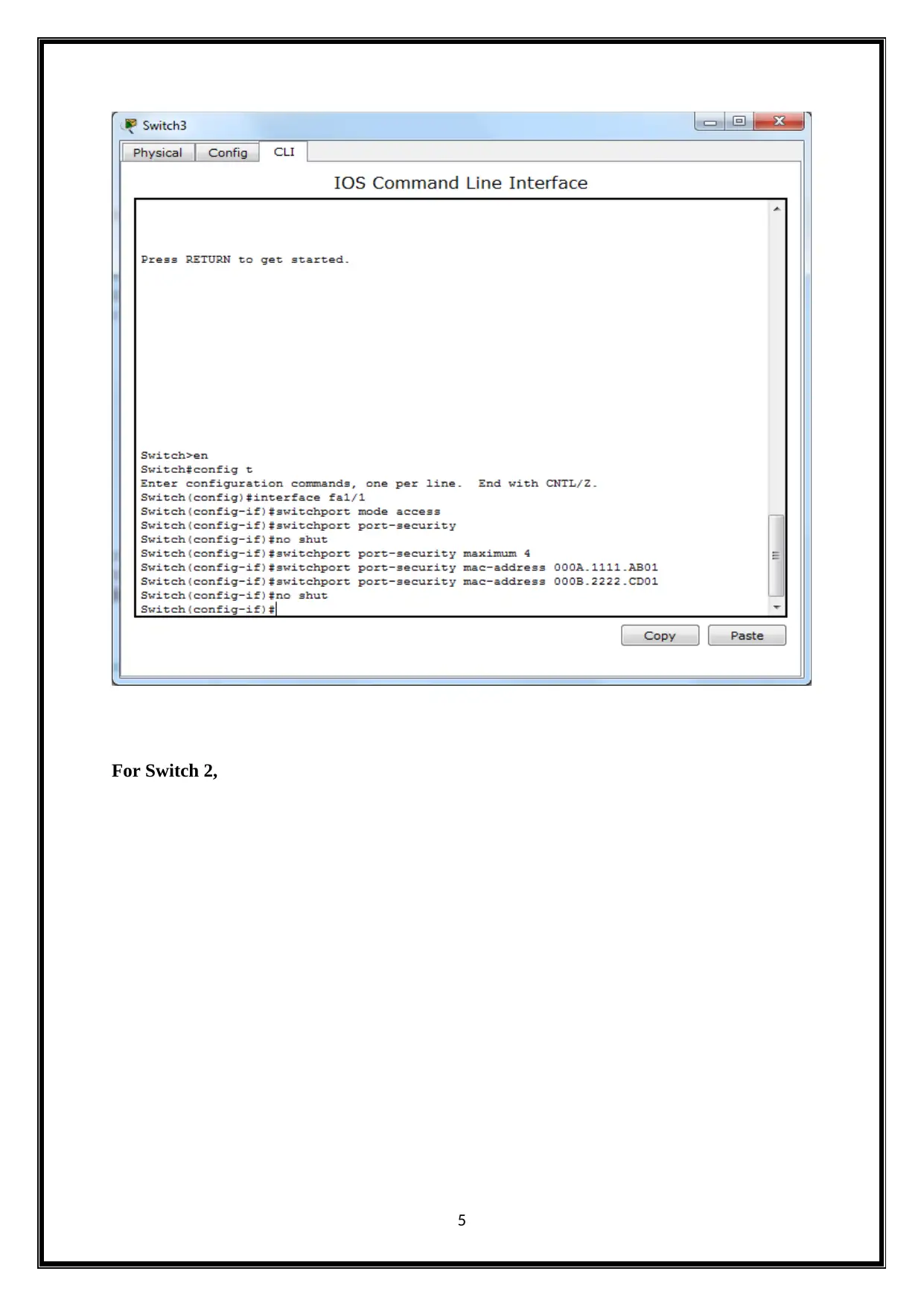
For Switch 2,
5
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
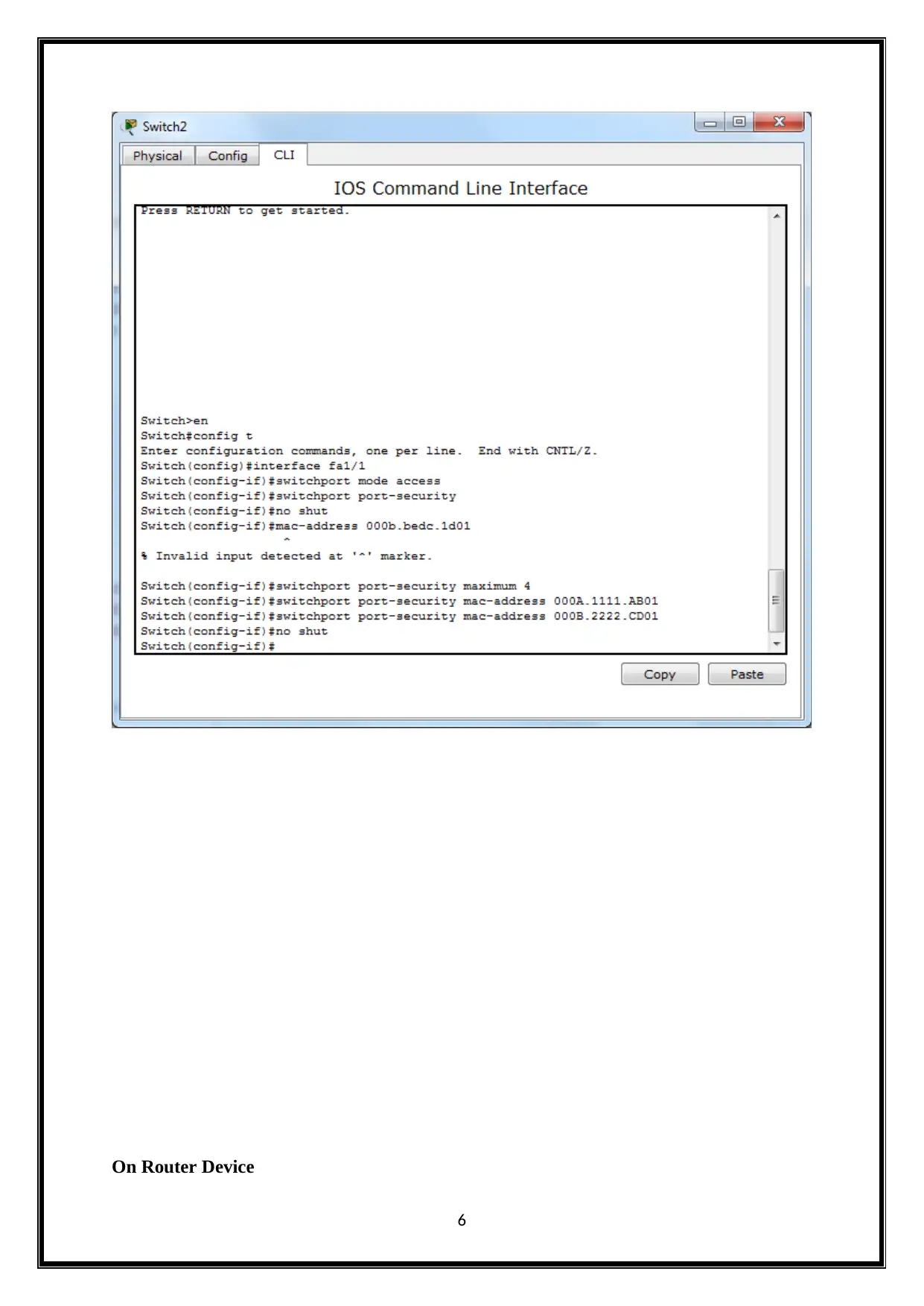
On Router Device
6
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
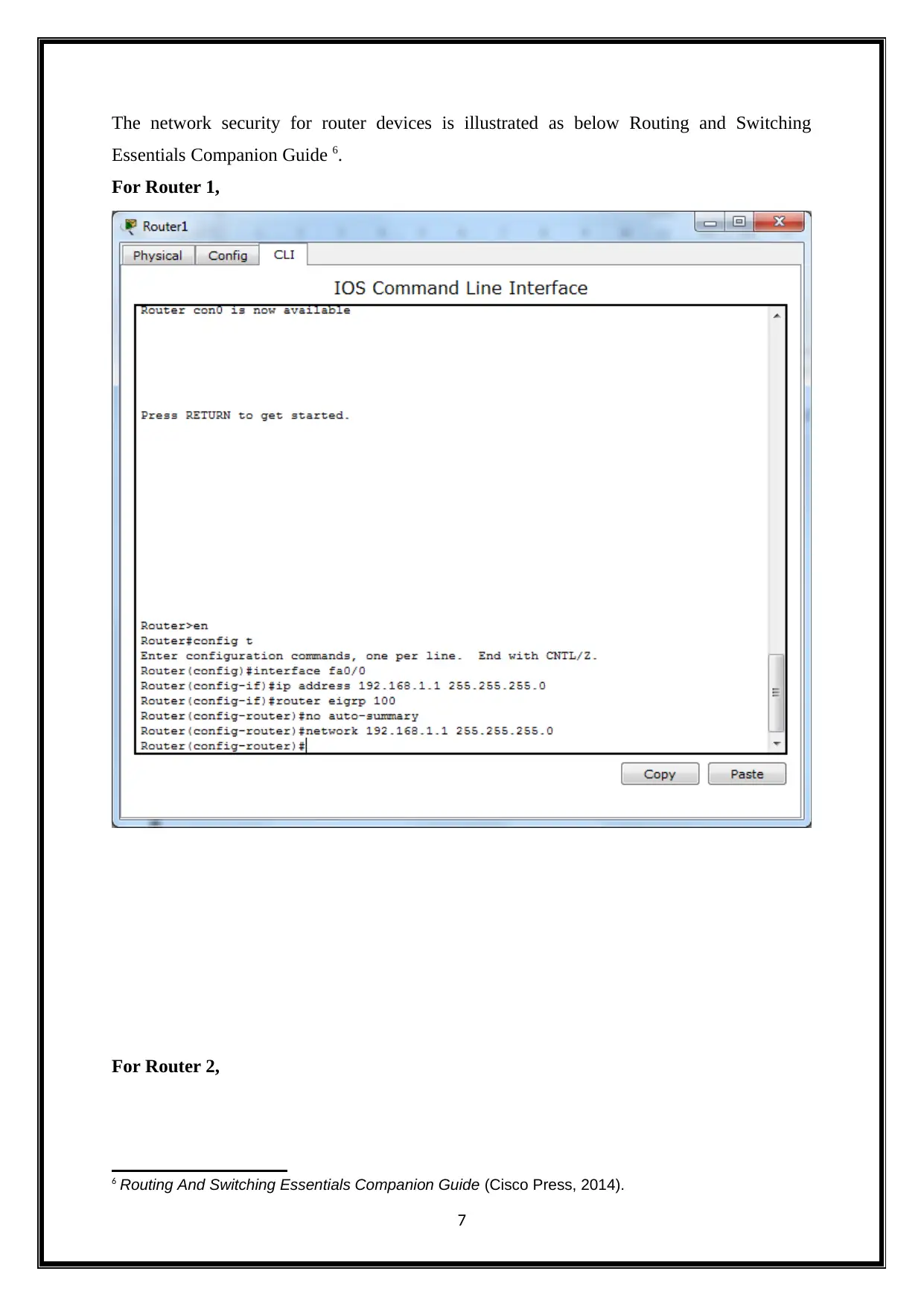
The network security for router devices is illustrated as below Routing and Switching
Essentials Companion Guide 6.
For Router 1,
For Router 2,
6 Routing And Switching Essentials Companion Guide (Cisco Press, 2014).
7
Essentials Companion Guide 6.
For Router 1,
For Router 2,
6 Routing And Switching Essentials Companion Guide (Cisco Press, 2014).
7
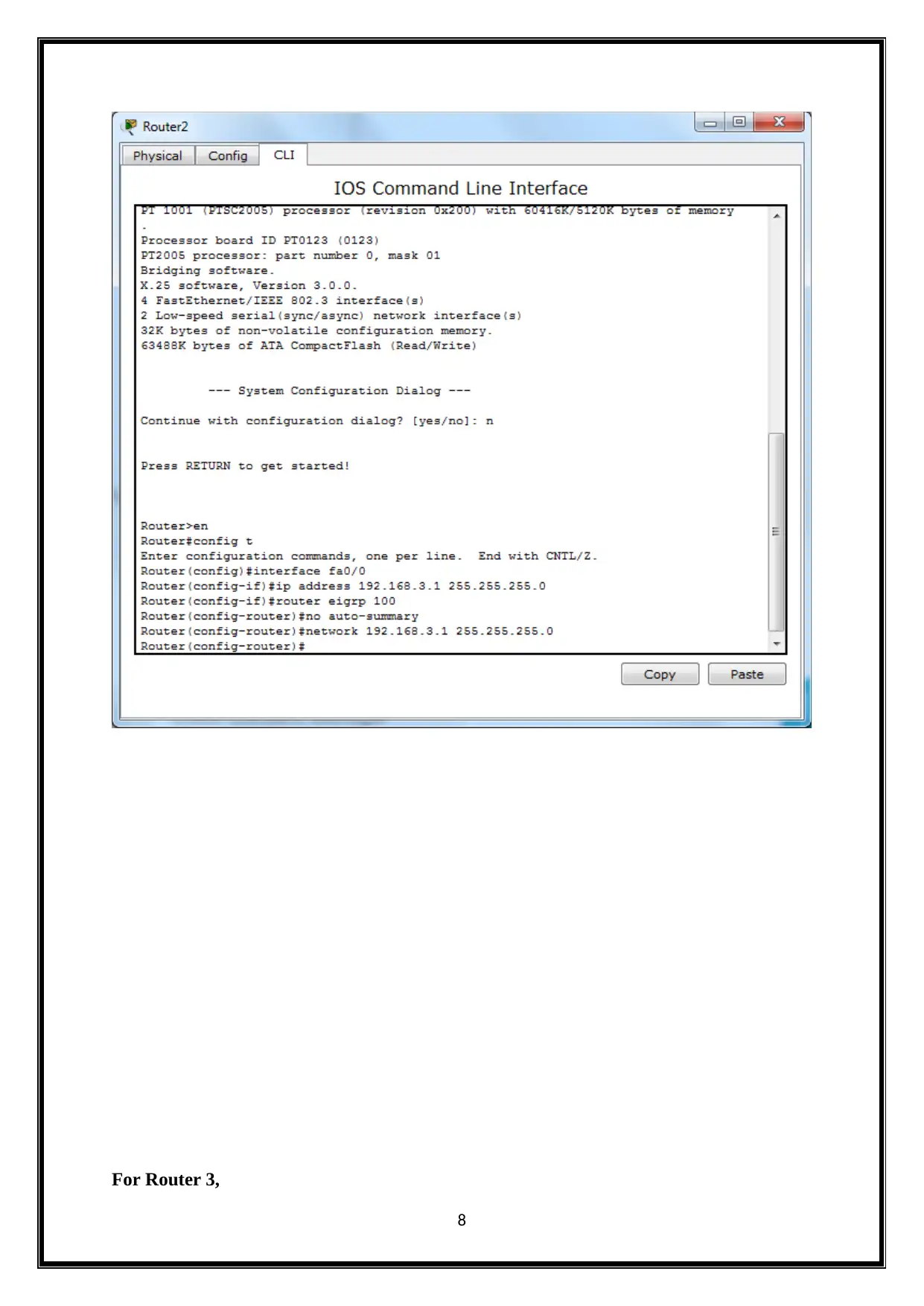
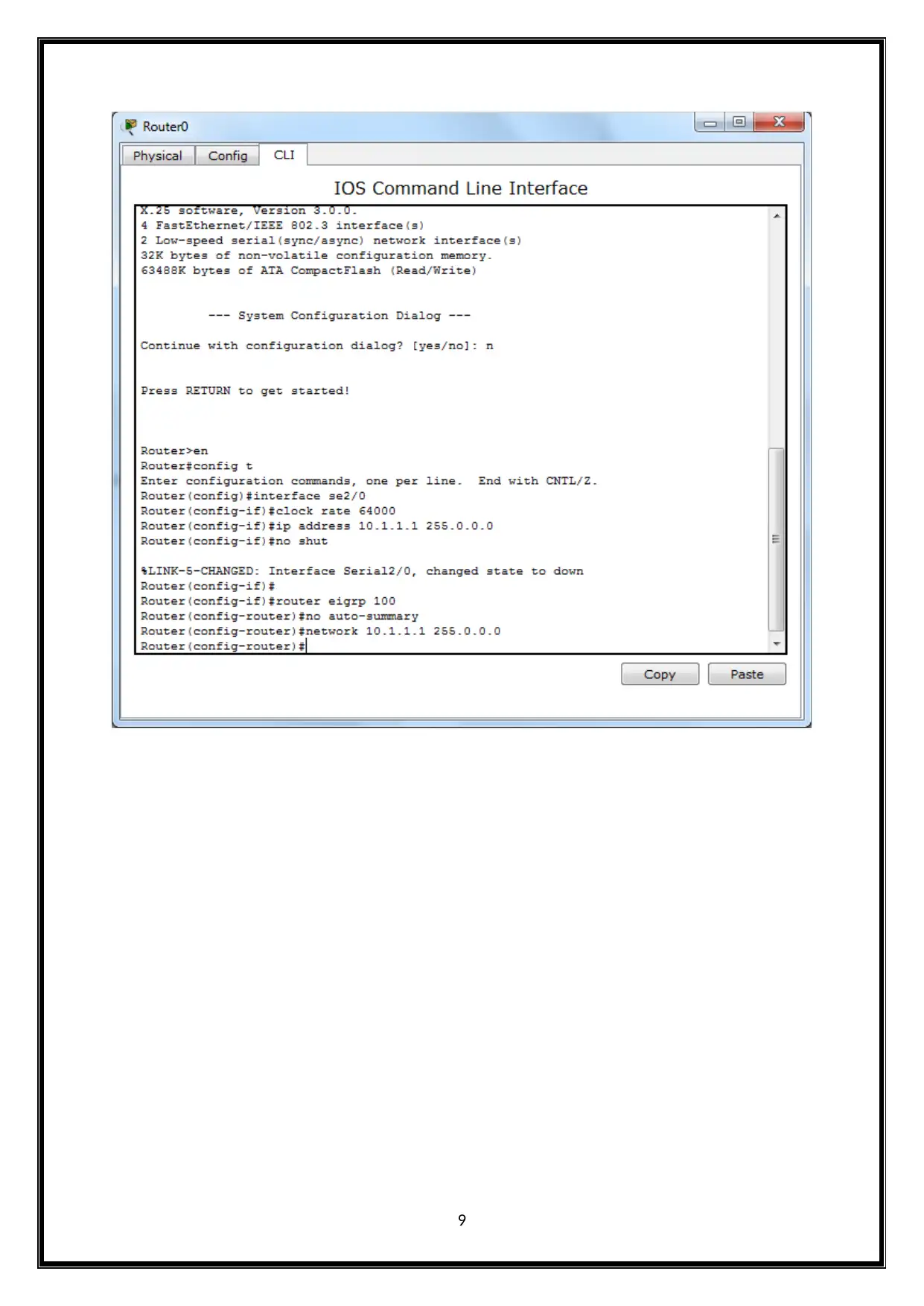
For Router 3,
8
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
A. Jesin, Packet Tracer Network Simulator, 2014.
Connecting Networks Companion Guide, Cisco Press, 2014.
Eliot, George, The Mill On The Floss, BiblioLife, 2009.
Graziani, Rick and Bob Vachon, Routing Protocols, Cisco Press, 2014.
Network Basics Companion Guide, 2013.
Routing And Switching Essentials Companion Guide, Cisco Press, 2014.
10
A. Jesin, Packet Tracer Network Simulator, 2014.
Connecting Networks Companion Guide, Cisco Press, 2014.
Eliot, George, The Mill On The Floss, BiblioLife, 2009.
Graziani, Rick and Bob Vachon, Routing Protocols, Cisco Press, 2014.
Network Basics Companion Guide, 2013.
Routing And Switching Essentials Companion Guide, Cisco Press, 2014.
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





