Detailed Report on Network Systems Administration for Module 7COM1029
VerifiedAdded on 2022/09/21
|20
|3078
|24
Report
AI Summary
This report, submitted for the 7COM1029 module, provides a comprehensive overview of network systems administration. It begins with an abstract and introduction, followed by background information and a literature review. The report then details the scope and limitations of the project, along with a network diagram illustrating the network setup. A significant portion of the report is dedicated to experimental analysis, including the installation and configuration of DHCP and DNS servers, setting up real and virtual hosts, client/server interactions, implementing Quality of Service (QoS), securing SSH, and configuring the iptables firewall. Testing and evaluation of the implemented configurations are also presented. The report concludes with a summary of the findings and references relevant sources. The assignment showcases practical aspects of network administration, offering insights into securing and optimizing network performance.

Running head: REPORT ON SETTING UP NETWORK
By
Academic Year: 2019-20
Module: Setting up Network
By
Academic Year: 2019-20
Module: Setting up Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
Table of content
Abstract .............................................................................................................2
Introduction........................................................................................................3
Background Information....................................................................................3
Literature Review..............................................................................................4
Scope and limitations.........................................................................................5
Network Diagram...............................................................................................6
Experimental Analysis.......................................................................................7
Testing and Evaluation......................................................................................14
Conclusion..........................................................................................................16
References...........................................................................................................17
Table of content
Abstract .............................................................................................................2
Introduction........................................................................................................3
Background Information....................................................................................3
Literature Review..............................................................................................4
Scope and limitations.........................................................................................5
Network Diagram...............................................................................................6
Experimental Analysis.......................................................................................7
Testing and Evaluation......................................................................................14
Conclusion..........................................................................................................16
References...........................................................................................................17

2
Abstract
Information and computing infrastructure (ICT) include levels of unpredictability that are
exceptionally powerful in nature. This is expected in no little measure to the expansion of
innovations, for example, distributed computing and disseminated frameworks structures,
information mining and multidimensional examination, and enormous scope undertaking
frameworks, to give some examples. Successful processing and system frameworks
organization is indispensable to the strength and versatility of these perplexing programming,
equipment, and correspondence frameworks. Frameworks organization includes the structure,
examination, and nonstop improvement of the exhibition or activity of information and
computing frameworks. Furthermore, social and regulatory obligations have become about as
basic for the frameworks manager similar to the specialized requests that have been forced
for quite a long time. The zones of tasks explore (OR) and framework elements (SD)
displaying offer framework managers a rich exhibit of investigative and improvement
apparatuses that have been created from assorted controls, which include: mechanical,
logical, building, monetary and money related, to give some examples. This paper proposes
an exploration structure by which OR and SD displaying strategies may demonstrate helpful
to computing and system frameworks organization, which include: direct programming,
arrange examination, whole number programming, nonlinear advancement, Markov forms,
queueing displaying, reproduction, choice investigation, heuristic procedures, and framework
elements displaying.
Abstract
Information and computing infrastructure (ICT) include levels of unpredictability that are
exceptionally powerful in nature. This is expected in no little measure to the expansion of
innovations, for example, distributed computing and disseminated frameworks structures,
information mining and multidimensional examination, and enormous scope undertaking
frameworks, to give some examples. Successful processing and system frameworks
organization is indispensable to the strength and versatility of these perplexing programming,
equipment, and correspondence frameworks. Frameworks organization includes the structure,
examination, and nonstop improvement of the exhibition or activity of information and
computing frameworks. Furthermore, social and regulatory obligations have become about as
basic for the frameworks manager similar to the specialized requests that have been forced
for quite a long time. The zones of tasks explore (OR) and framework elements (SD)
displaying offer framework managers a rich exhibit of investigative and improvement
apparatuses that have been created from assorted controls, which include: mechanical,
logical, building, monetary and money related, to give some examples. This paper proposes
an exploration structure by which OR and SD displaying strategies may demonstrate helpful
to computing and system frameworks organization, which include: direct programming,
arrange examination, whole number programming, nonlinear advancement, Markov forms,
queueing displaying, reproduction, choice investigation, heuristic procedures, and framework
elements displaying.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
Introduction
The job of the frameworks overseer, or sysadmin, keeps on advancing drastically, due for the
most part to fast development territories, for example, dispersed distributed computing,
foundation as-an administration (IaaS), programming as-an administration (SaaS), and other
related help arranged data and processing advancements (ICT). The sysadmin connects
fundamentally in the structure, examination, and persistent improvement of the presentation
or activity of data and registering frameworks, which additionally incorporates client support.
In total, the sysadmin is required to guarantee the continuous dependability of complex and
strategic specialized and human-PC frameworks(Ankit, Sengupta, and Roy, 2017,
November). The disappointment of such complex foundations might be both troublesome and
exorbitant [1]. The soundness of the product, equipment, system, database, and human-PC
interface (HCI) "outfit" by sysadmins requires appropriate arranging and the board of
complex IT foundations. To suit such requests, ongoing exploration endeavors look at all the
more intently specific specialized and non-specialized (i.e., "delicate") requirements of
sysadmins, with the end goal that a more extensive and more extravagant cluster of models
and apparatuses may offer more noteworthy help of their workspace(Ceselli, Premoli, and
Secci, 2017).
Background information
The historical backdrop of frameworks organization starts nearly 60 years prior, with the
advancement in 1952 of the IBM 701, the main business PC [6]. Around then, framework
administrators, who were themselves utilized by clients' associations, were urged to arrange
with IBM the sharing of data, encounters, arrangements, and such(Verdú et al., 2017).
Consequent stages in the advancement of processing prompted a reshaping and further
Introduction
The job of the frameworks overseer, or sysadmin, keeps on advancing drastically, due for the
most part to fast development territories, for example, dispersed distributed computing,
foundation as-an administration (IaaS), programming as-an administration (SaaS), and other
related help arranged data and processing advancements (ICT). The sysadmin connects
fundamentally in the structure, examination, and persistent improvement of the presentation
or activity of data and registering frameworks, which additionally incorporates client support.
In total, the sysadmin is required to guarantee the continuous dependability of complex and
strategic specialized and human-PC frameworks(Ankit, Sengupta, and Roy, 2017,
November). The disappointment of such complex foundations might be both troublesome and
exorbitant [1]. The soundness of the product, equipment, system, database, and human-PC
interface (HCI) "outfit" by sysadmins requires appropriate arranging and the board of
complex IT foundations. To suit such requests, ongoing exploration endeavors look at all the
more intently specific specialized and non-specialized (i.e., "delicate") requirements of
sysadmins, with the end goal that a more extensive and more extravagant cluster of models
and apparatuses may offer more noteworthy help of their workspace(Ceselli, Premoli, and
Secci, 2017).
Background information
The historical backdrop of frameworks organization starts nearly 60 years prior, with the
advancement in 1952 of the IBM 701, the main business PC [6]. Around then, framework
administrators, who were themselves utilized by clients' associations, were urged to arrange
with IBM the sharing of data, encounters, arrangements, and such(Verdú et al., 2017).
Consequent stages in the advancement of processing prompted a reshaping and further
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
refinements to frameworks the executives, all of which have prompted the present figuring
condition that currently includes distributed computing, disseminated frameworks, and a
bunch of complex equipment, programming, and systems administration models. A
contemporary definition for frameworks organization is proposed in, which states: "System
and framework organization is a part of designing that worries the operational administration
of human-PC frameworks." The reference further expresses that "we are presently compelled
to think frameworks not only PCs," due for the most part to the degree of unpredictability
found with current processing and conduct frameworks(Ceselli, Premoli, and Secci, 2018).
Literature review
For all intents and purposes, the obligations of a framework and system manager length
operational (every day), strategic (arranging and procedure changes), administrations
provisioning, and the executives rehearses, all of which involve specialized and non-
specialized (or socio-specialized) prerequisites and requests(Yadav, Das, and Tripathi, 2017).
Such obligations extend from issues related with essentials, for example, workstations,
servers, systems, security, and helpdesk, to the executives rehearses, for example,
authoritative structures, clients' impression of foundation, specialized and non-specialized
administration, and recruiting and terminating of frameworks organization faculty(Chen et
al., 2016). A change in outlook gives off the impression of being in progress, which extends
the extent of study in the region of frameworks organization(Wang et al., 2017). This is
proved by the ongoing advancement of a conventional hypothesis of framework organization,
utilizing a numerical structure(Rezaee et al., 2017), the target of which is to make conceivable
dynamical soundness of the framework all in all. Reference (Yao et al., 2019) points out that
the multifaceted nature of the connection among people and PCs presents a fascinating test
toward the definition of any scientific hypothesis or framework organization. Curiously, this
intricacy of human-PC communication carries us to the second part of this change in
refinements to frameworks the executives, all of which have prompted the present figuring
condition that currently includes distributed computing, disseminated frameworks, and a
bunch of complex equipment, programming, and systems administration models. A
contemporary definition for frameworks organization is proposed in, which states: "System
and framework organization is a part of designing that worries the operational administration
of human-PC frameworks." The reference further expresses that "we are presently compelled
to think frameworks not only PCs," due for the most part to the degree of unpredictability
found with current processing and conduct frameworks(Ceselli, Premoli, and Secci, 2018).
Literature review
For all intents and purposes, the obligations of a framework and system manager length
operational (every day), strategic (arranging and procedure changes), administrations
provisioning, and the executives rehearses, all of which involve specialized and non-
specialized (or socio-specialized) prerequisites and requests(Yadav, Das, and Tripathi, 2017).
Such obligations extend from issues related with essentials, for example, workstations,
servers, systems, security, and helpdesk, to the executives rehearses, for example,
authoritative structures, clients' impression of foundation, specialized and non-specialized
administration, and recruiting and terminating of frameworks organization faculty(Chen et
al., 2016). A change in outlook gives off the impression of being in progress, which extends
the extent of study in the region of frameworks organization(Wang et al., 2017). This is
proved by the ongoing advancement of a conventional hypothesis of framework organization,
utilizing a numerical structure(Rezaee et al., 2017), the target of which is to make conceivable
dynamical soundness of the framework all in all. Reference (Yao et al., 2019) points out that
the multifaceted nature of the connection among people and PCs presents a fascinating test
toward the definition of any scientific hypothesis or framework organization. Curiously, this
intricacy of human-PC communication carries us to the second part of this change in

5
perspective(Govindan, Fattahi, and Keyvanshokooh, 2017). In particular, there as of late has
been an outstanding increment in the number of studies that investigate parts of frameworks
organization that are: (1) administrative authoritative; (2) administrations situated; (3) socio-
conduct; and (4) execution driven; all of which investigate all things considered the human-
PC connection (HCI) part of frameworks organization. It is explicitly this aggregate HCI
perspective around which we build up our proposed look into the system. The dynamic idea
of registering and system foundations requires the accessibility of "toolsets" that would
additionally emotionally supportive networks chairmen's operational and arranging needs.
The fields of activities look into (OR) and framework elements (SD) offer analysts
extraordinary potential for the investigation of applying suitable strategies that emotionally
supportive network managers(Floersch et al., 2016).
Scope and limitations
Costly to Install: For one, systems can be expensive to set up. While in the drawn-out
systems, for the most part, set aside your cash, the underlying expenses of the
establishment can be high. Links, organize cards, and programming is costly, and the
establishment may require the administrations of a professional, contingent upon what
number of PCs are included and what sort of system it is(Hadi et al., 2018).
Regulatory Time Requirements: Proper upkeep of a system requires significant
investment and preparation. Numerous individuals will set up a system and discover
they have not planned for the necessary support. Contingent upon the size of the
system you may need to enlist authoritative help or take some casual preparing of
your own(Karim, et al., 2017).
perspective(Govindan, Fattahi, and Keyvanshokooh, 2017). In particular, there as of late has
been an outstanding increment in the number of studies that investigate parts of frameworks
organization that are: (1) administrative authoritative; (2) administrations situated; (3) socio-
conduct; and (4) execution driven; all of which investigate all things considered the human-
PC connection (HCI) part of frameworks organization. It is explicitly this aggregate HCI
perspective around which we build up our proposed look into the system. The dynamic idea
of registering and system foundations requires the accessibility of "toolsets" that would
additionally emotionally supportive networks chairmen's operational and arranging needs.
The fields of activities look into (OR) and framework elements (SD) offer analysts
extraordinary potential for the investigation of applying suitable strategies that emotionally
supportive network managers(Floersch et al., 2016).
Scope and limitations
Costly to Install: For one, systems can be expensive to set up. While in the drawn-out
systems, for the most part, set aside your cash, the underlying expenses of the
establishment can be high. Links, organize cards, and programming is costly, and the
establishment may require the administrations of a professional, contingent upon what
number of PCs are included and what sort of system it is(Hadi et al., 2018).
Regulatory Time Requirements: Proper upkeep of a system requires significant
investment and preparation. Numerous individuals will set up a system and discover
they have not planned for the necessary support. Contingent upon the size of the
system you may need to enlist authoritative help or take some casual preparing of
your own(Karim, et al., 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
Record Server Failures: When a ground server goes down, this can mean the whole
system stops. While document servers are not any more vulnerable to disappointment
than some other PC, the disappointment of a record server can mean much more
efficiency misfortune than the disappointment of a workstation or remain solitary PC,
since the whole system can lose access to required projects and documents(Ilyas, and
Mahgoub, 2018).
Broken Cables: While some system setups can limit the burden of a messed uplink,
with different arrangements, a wrecked link can mean a stop to the whole system,
when setting up your system, know about the effect of design on issues this
way(Korniyenko, and Galata, 2017).
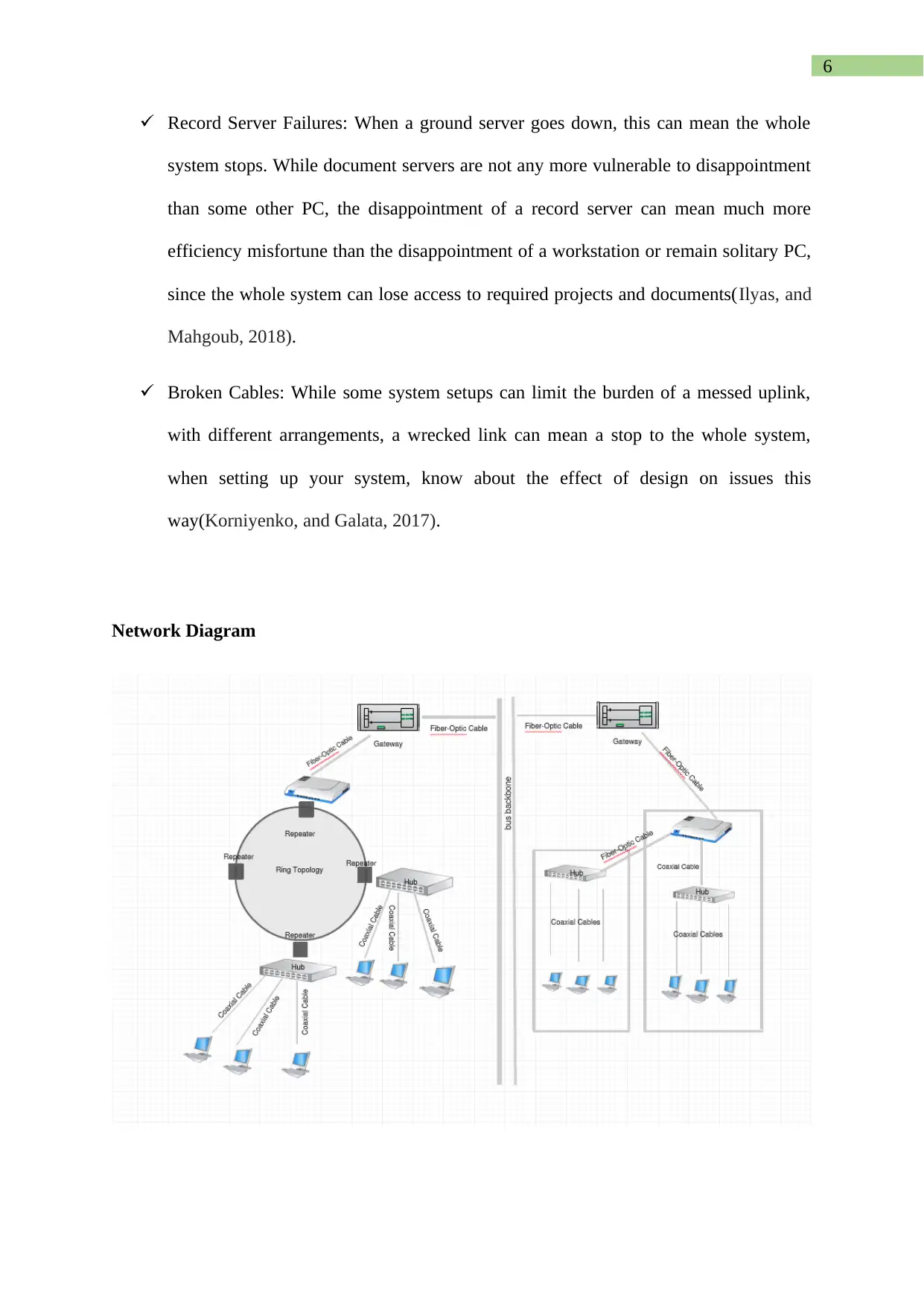
Network Diagram
Record Server Failures: When a ground server goes down, this can mean the whole
system stops. While document servers are not any more vulnerable to disappointment
than some other PC, the disappointment of a record server can mean much more
efficiency misfortune than the disappointment of a workstation or remain solitary PC,
since the whole system can lose access to required projects and documents(Ilyas, and
Mahgoub, 2018).
Broken Cables: While some system setups can limit the burden of a messed uplink,
with different arrangements, a wrecked link can mean a stop to the whole system,
when setting up your system, know about the effect of design on issues this
way(Korniyenko, and Galata, 2017).
Network Diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
Experimental work and analysis
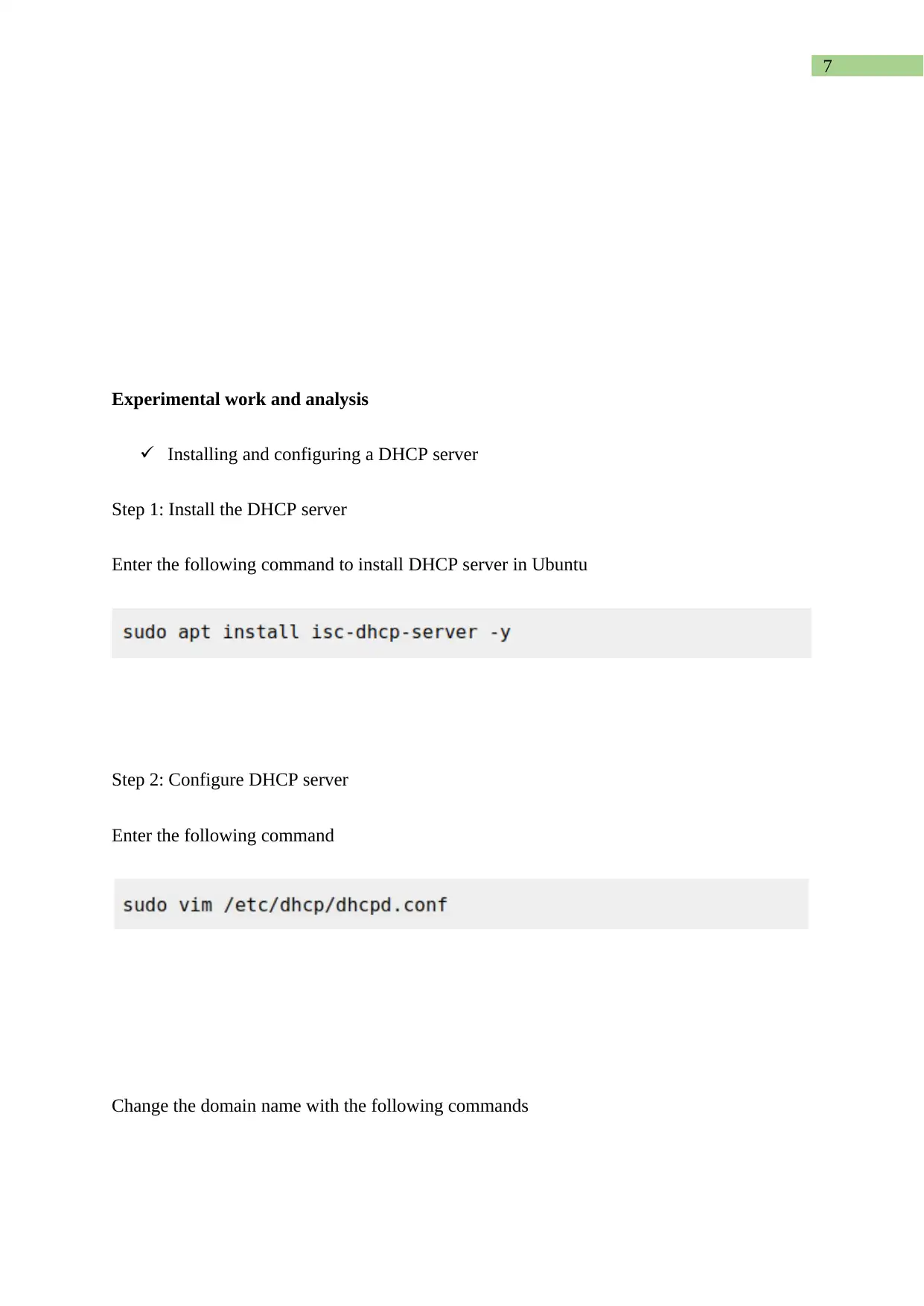
Installing and configuring a DHCP server
Step 1: Install the DHCP server
Enter the following command to install DHCP server in Ubuntu
Step 2: Configure DHCP server
Enter the following command
Change the domain name with the following commands
Experimental work and analysis
Installing and configuring a DHCP server
Step 1: Install the DHCP server
Enter the following command to install DHCP server in Ubuntu
Step 2: Configure DHCP server
Enter the following command
Change the domain name with the following commands
8
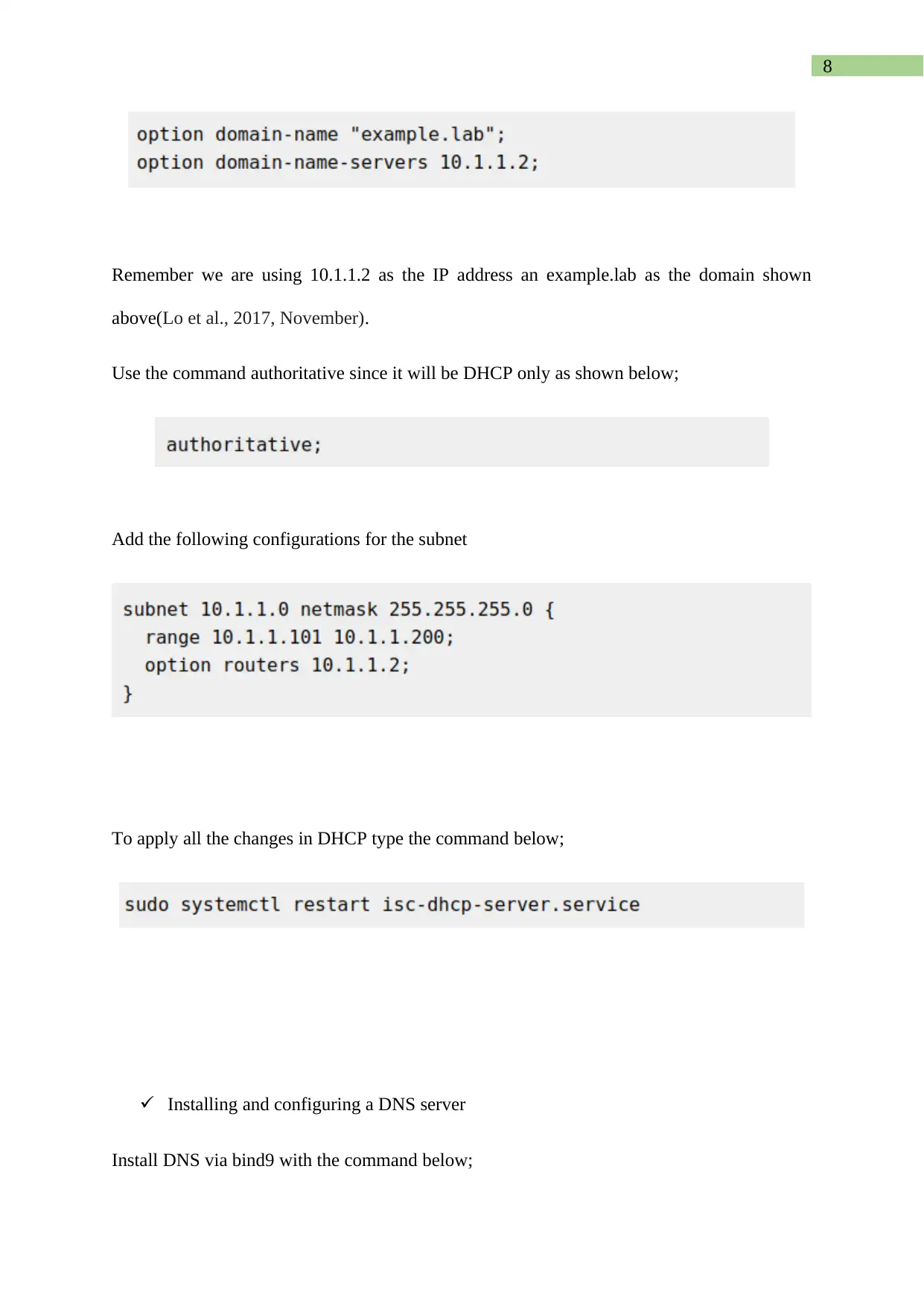
Remember we are using 10.1.1.2 as the IP address an example.lab as the domain shown
above(Lo et al., 2017, November).
Use the command authoritative since it will be DHCP only as shown below;
Add the following configurations for the subnet
To apply all the changes in DHCP type the command below;
Installing and configuring a DNS server
Install DNS via bind9 with the command below;
Remember we are using 10.1.1.2 as the IP address an example.lab as the domain shown
above(Lo et al., 2017, November).
Use the command authoritative since it will be DHCP only as shown below;
Add the following configurations for the subnet
To apply all the changes in DHCP type the command below;
Installing and configuring a DNS server
Install DNS via bind9 with the command below;
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
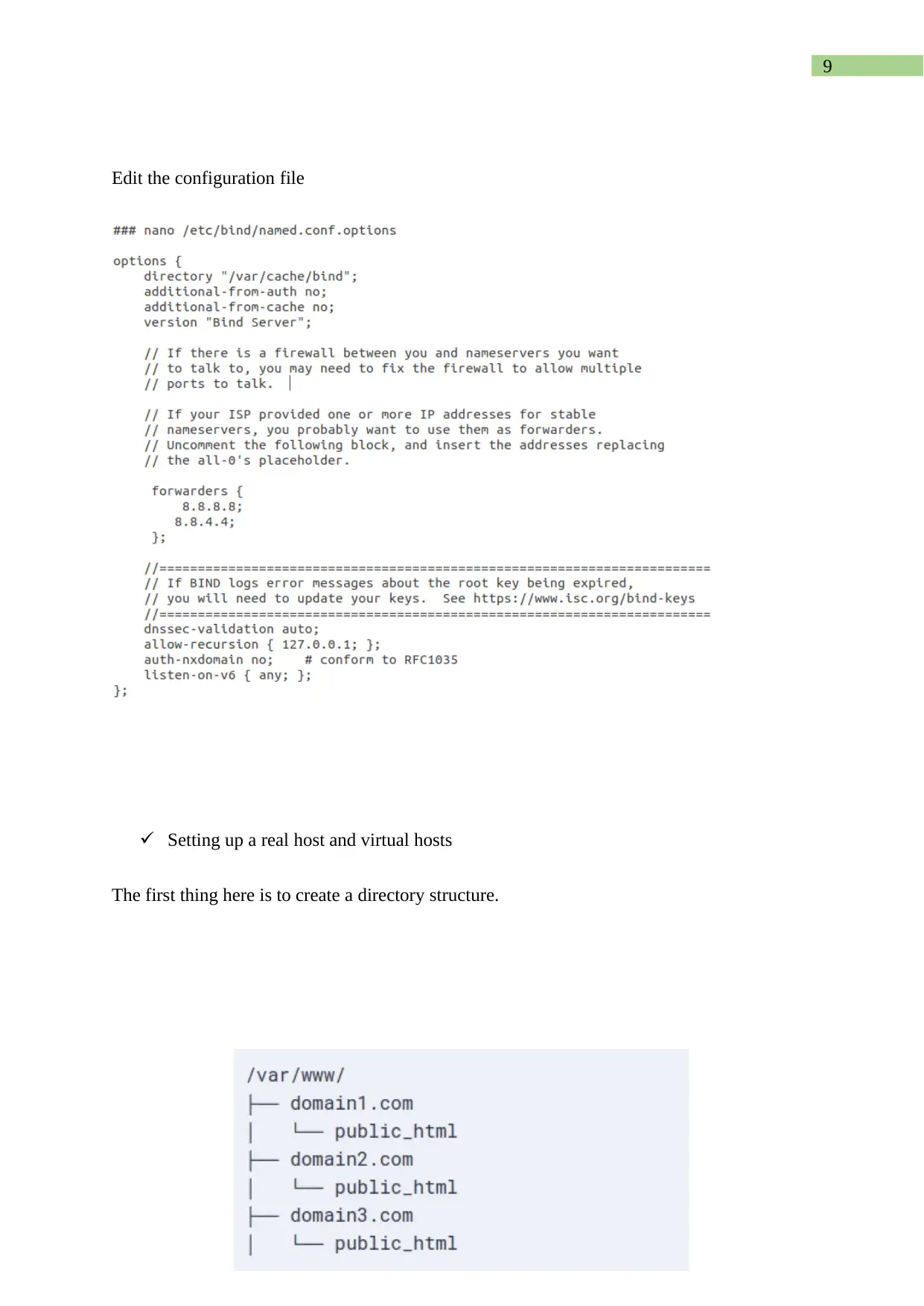
Edit the configuration file
Setting up a real host and virtual hosts
The first thing here is to create a directory structure.
Edit the configuration file
Setting up a real host and virtual hosts
The first thing here is to create a directory structure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
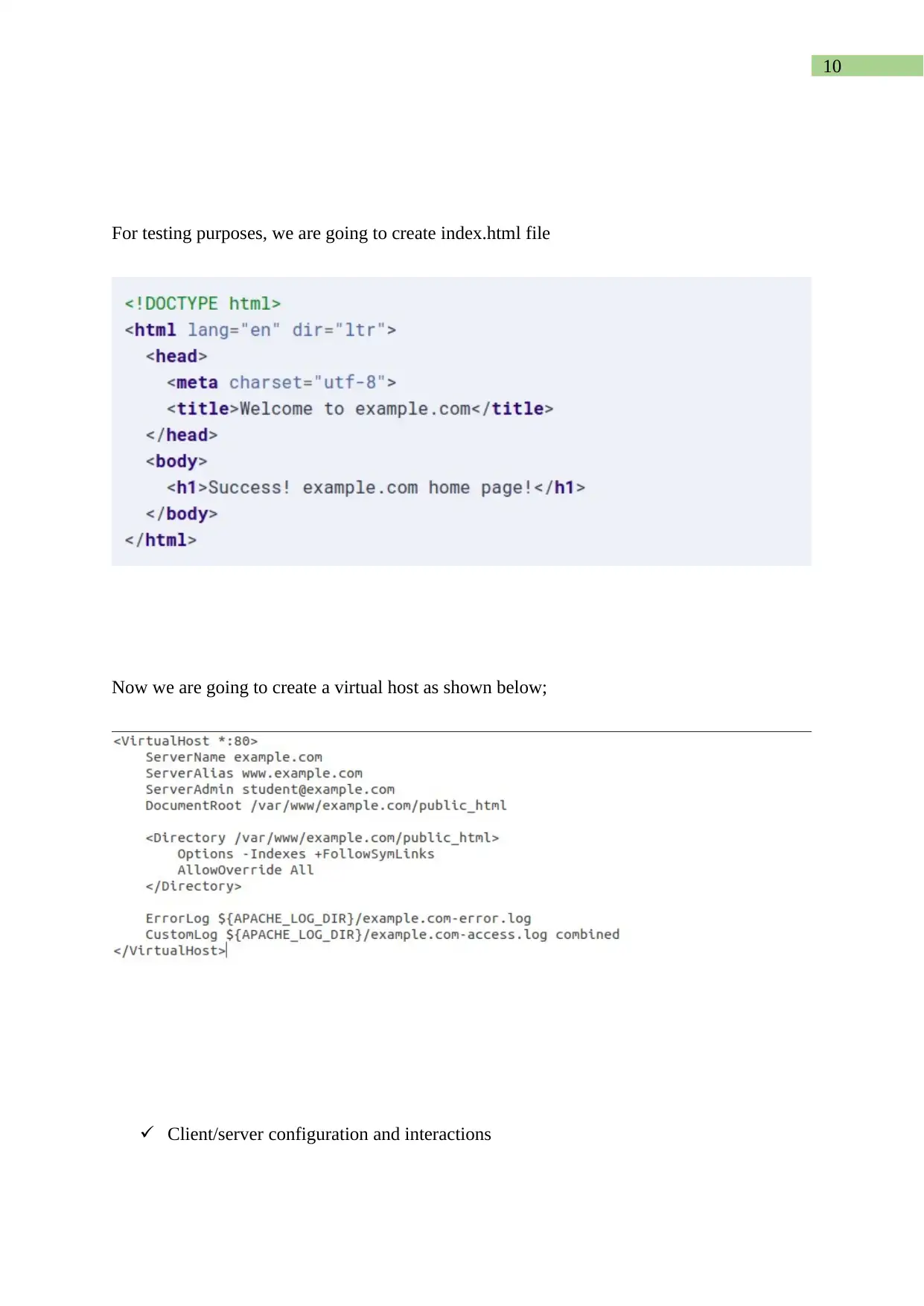
For testing purposes, we are going to create index.html file
Now we are going to create a virtual host as shown below;
Client/server configuration and interactions
For testing purposes, we are going to create index.html file
Now we are going to create a virtual host as shown below;
Client/server configuration and interactions
11
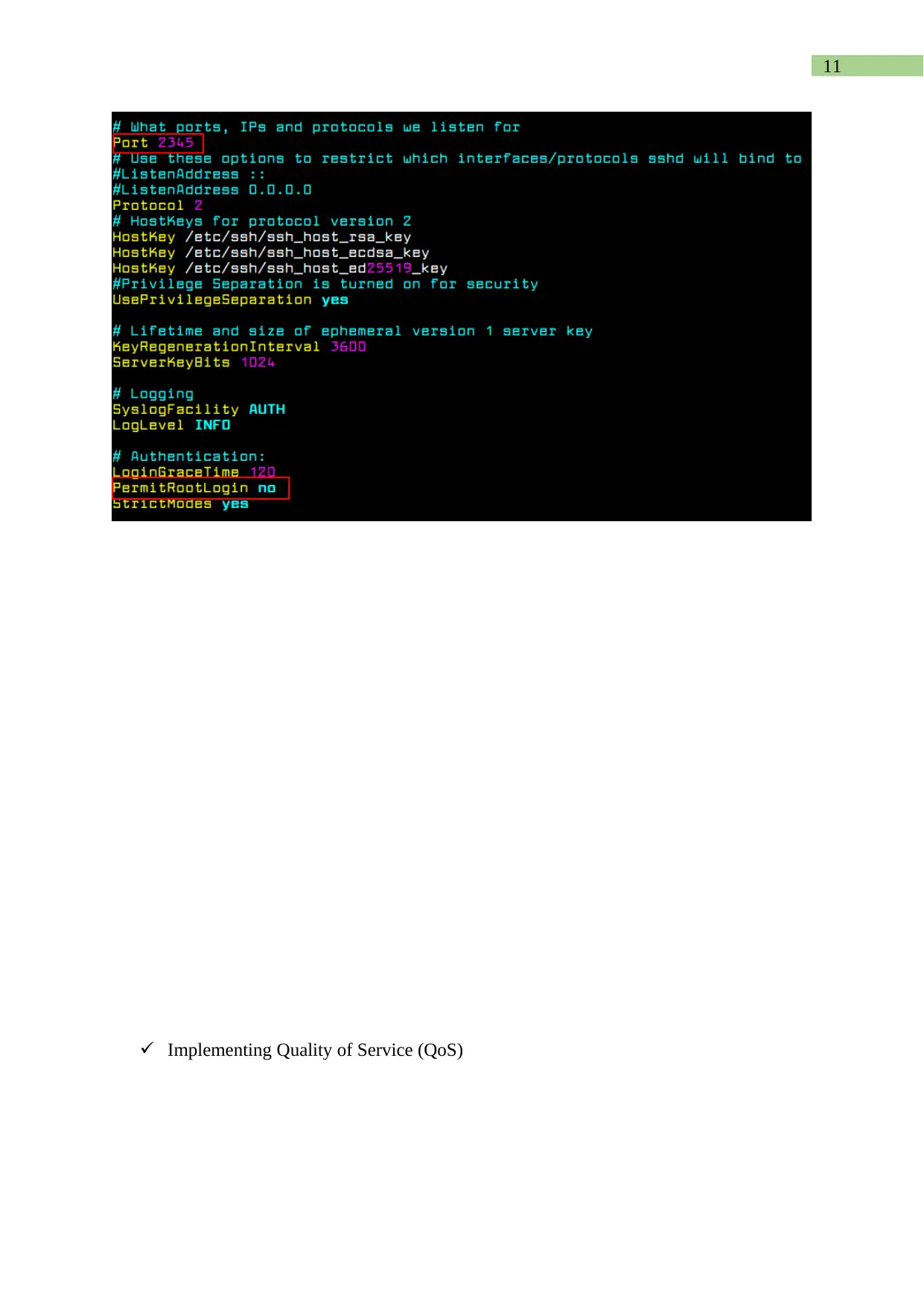
Implementing Quality of Service (QoS)
Implementing Quality of Service (QoS)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





