Advanced Financial Accounting: Risk Management Report Analysis
VerifiedAdded on 2021/06/14
|21
|4741
|38
Report
AI Summary
This comprehensive report delves into the intricacies of risk management within the realm of advanced financial accounting. It begins by differentiating between proactive and reactive risk management strategies, emphasizing their respective objectives and applications. The report then outlines the risk management process, highlighting key steps such as risk identification, significance assessment, and control measure implementation. It explores various sources of risk within an organization, the function of a risk register, and the distinction between general and operational risks. The analysis further examines the effectiveness of risk control measures, particularly the limitations of LTIFR, and the preference for lower loss and risk costs with higher control costs. The report also defines and analyzes Total Cost of Risk (TCOR), and customer risk, providing parameters for risk comparison and evaluation. Finally, it presents a critical evaluation of the Risk Matrix, considering its practical application and limitations, and concludes with a discussion on event analysis and outcome analysis diagrams.

Advanced Financial Accounting
Student’s Name:
University Name:
Author’s Name:
Student’s Name:
University Name:
Author’s Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2Advanced Financial Accounting
Table of Contents
Part (A) (1).................................................................................................................................4
Difference between pro-active and reactive risk management...............................................4
2. Summarise in a logical manner (that is, the way in which the process would be carried out) the process of risk management. 4
3. What are the main types of sources of risk in an organisation?.........................................5
4. What is a risk register and what information does it contain?...........................................5
5. Why is there a need to distinguish between general risks and operational risks?..............6
6. How do you know if risk is under successful control?.......................................................6
7. Explain the difference between a risk management system and a systemic approach to risk management 7
8. Summarise the necessary content of a risk management system.......................................7
Part A (2)....................................................................................................................................7
Explain why LTIFR is not a useful measure of that aspect of risk that is associated with high Consequence values. 7
Can you explain why any competent management team would prefer to operate with lower loss and risk costs and with higher risk control
costs?......................................................................................................................................8
Table of Contents
Part (A) (1).................................................................................................................................4
Difference between pro-active and reactive risk management...............................................4
2. Summarise in a logical manner (that is, the way in which the process would be carried out) the process of risk management. 4
3. What are the main types of sources of risk in an organisation?.........................................5
4. What is a risk register and what information does it contain?...........................................5
5. Why is there a need to distinguish between general risks and operational risks?..............6
6. How do you know if risk is under successful control?.......................................................6
7. Explain the difference between a risk management system and a systemic approach to risk management 7
8. Summarise the necessary content of a risk management system.......................................7
Part A (2)....................................................................................................................................7
Explain why LTIFR is not a useful measure of that aspect of risk that is associated with high Consequence values. 7
Can you explain why any competent management team would prefer to operate with lower loss and risk costs and with higher risk control
costs?......................................................................................................................................8

3Advanced Financial Accounting
Consider an organisation with which you are familiar and identify and define the constituents of TCOR. 8
Part B (1)....................................................................................................................................8
1. Define it carefully, ensuring you have a proper understanding of the way Risk is defined.8
2. What parameters could be used to describe this Risk in a manner that enabled it to be compared in significance with other Risks of a
different nature? Identify them and briefly explain your choice...........................................9
Change in cost of the proposed changes.............................................................................9
Urgency or sensitivity.........................................................................................................9
Imposition of the risk..........................................................................................................9
Locus of control over the Risk..........................................................................................10
3. What parameters could be used to allow this particular Risk to be compared with other Risks of the same type? Identify them and briefly
explain your choice...............................................................................................................10
1. Describe a specific situation in which the above type of Risk might exist......................10
Read the relevant notes, the paper by Pickering and Cowley and the provided papers by Peace and by Viner et al to provide you with a basis
(along with your personal experience of using it) for writing a critical evaluation of the Risk Matrix idea - both the reality of using the matrix
and the very idea of the matrix as something that can be used for this purpose. (Approximately 500 words) 12
Consider an organisation with which you are familiar and identify and define the constituents of TCOR. 8
Part B (1)....................................................................................................................................8
1. Define it carefully, ensuring you have a proper understanding of the way Risk is defined.8
2. What parameters could be used to describe this Risk in a manner that enabled it to be compared in significance with other Risks of a
different nature? Identify them and briefly explain your choice...........................................9
Change in cost of the proposed changes.............................................................................9
Urgency or sensitivity.........................................................................................................9
Imposition of the risk..........................................................................................................9
Locus of control over the Risk..........................................................................................10
3. What parameters could be used to allow this particular Risk to be compared with other Risks of the same type? Identify them and briefly
explain your choice...............................................................................................................10
1. Describe a specific situation in which the above type of Risk might exist......................10
Read the relevant notes, the paper by Pickering and Cowley and the provided papers by Peace and by Viner et al to provide you with a basis
(along with your personal experience of using it) for writing a critical evaluation of the Risk Matrix idea - both the reality of using the matrix
and the very idea of the matrix as something that can be used for this purpose. (Approximately 500 words) 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4Advanced Financial Accounting
Part C........................................................................................................................................13
1. Define the appropriate Event and draw, with brief written explanation, a Mechanism analysis logic diagram 13
2. Determine and explain your choice of the ‘questions’ which you would use to provide structure to the Outcome process and draw an
Outcome Analysis diagram for the case based on those questions......................................14
Reference List..........................................................................................................................16
Part (A) (1)
Difference between pro-active and reactive risk management
Proactive risk management is primarily the mitigation of the risks associated with the threat events before they might occur and bring a negative
impact upon the organisation. On the contrary, reactive risk management encompasses the responses to risk events as they occur. The primary
objective of reactive risk mitigation is to prevent the risk event from causing a large negative impact upon the organisation (Allet and Hudon,
2015). In case of proactive risk management, the management generally tends to protect the critical assets of the projected mission of the
organisation. The threat intelligence team of the company should be aware of the threat agents and results of security testing conducted before
the launch of a mission. Lastly, the mission organisers should also keep track of the source codes used for the project, and protect those from
Part C........................................................................................................................................13
1. Define the appropriate Event and draw, with brief written explanation, a Mechanism analysis logic diagram 13
2. Determine and explain your choice of the ‘questions’ which you would use to provide structure to the Outcome process and draw an
Outcome Analysis diagram for the case based on those questions......................................14
Reference List..........................................................................................................................16
Part (A) (1)
Difference between pro-active and reactive risk management
Proactive risk management is primarily the mitigation of the risks associated with the threat events before they might occur and bring a negative
impact upon the organisation. On the contrary, reactive risk management encompasses the responses to risk events as they occur. The primary
objective of reactive risk mitigation is to prevent the risk event from causing a large negative impact upon the organisation (Allet and Hudon,
2015). In case of proactive risk management, the management generally tends to protect the critical assets of the projected mission of the
organisation. The threat intelligence team of the company should be aware of the threat agents and results of security testing conducted before
the launch of a mission. Lastly, the mission organisers should also keep track of the source codes used for the project, and protect those from
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5Advanced Financial Accounting
falling in the hands of the hackers. Again, the CISOs, in reactive risk management, basically focus on events encompassing unplanned risk
management (Bromiley et al 2015).
The CSIOs keep focus on the incident responses of the various stakeholders along with remediation of the application vulnerabilities, either prior
to the production release or patching applications which have been produced already.
2. Summarise in a logical manner (that is, the way in which the process would be carried out) the process of risk management.
The first step of Risk management is identification and description of the risks. The primary applications involved in this step are development
of policy for registering the risks in the mission and conduction of formal risk analysis (Campopiano and De Massis, 2015).
The second step is the realisation of the significance of the risks. Based on the priority level of the risk, the organisation can implement an
insurance plan. The insurance company, in this case, would act as a bank account which ensures that if in case the risk incident occurs, the
organisation has money to compensate for it. The organisation should be conscious that actual costs of the consequences are anticipated well by
the company and the policy covers all such risks (Cavusgil and Knight, 2015). An insurance policy would not directly cover risks like monetary
loss due to business interruption and lack of customer confidence. Hence the effective policy would be of value larger than the anticipated risk
value.
The third step is a recognition and acknowledgement of the risk control measures already in practice. This practice would help in easy
application of reactive risk management.
falling in the hands of the hackers. Again, the CISOs, in reactive risk management, basically focus on events encompassing unplanned risk
management (Bromiley et al 2015).
The CSIOs keep focus on the incident responses of the various stakeholders along with remediation of the application vulnerabilities, either prior
to the production release or patching applications which have been produced already.
2. Summarise in a logical manner (that is, the way in which the process would be carried out) the process of risk management.
The first step of Risk management is identification and description of the risks. The primary applications involved in this step are development
of policy for registering the risks in the mission and conduction of formal risk analysis (Campopiano and De Massis, 2015).
The second step is the realisation of the significance of the risks. Based on the priority level of the risk, the organisation can implement an
insurance plan. The insurance company, in this case, would act as a bank account which ensures that if in case the risk incident occurs, the
organisation has money to compensate for it. The organisation should be conscious that actual costs of the consequences are anticipated well by
the company and the policy covers all such risks (Cavusgil and Knight, 2015). An insurance policy would not directly cover risks like monetary
loss due to business interruption and lack of customer confidence. Hence the effective policy would be of value larger than the anticipated risk
value.
The third step is a recognition and acknowledgement of the risk control measures already in practice. This practice would help in easy
application of reactive risk management.

6Advanced Financial Accounting
The last step is the evaluation of the chances of improvement of risk mitigation policies. The evaluation is based on the two parameters, namely
the degree of the risks and cost of introducing changes (Falkner and Hiebl, 2015). The organisation needs to evaluate financial, legal as well as
moral risks in this way.
3. What are the main types of sources of risk in an organisation?
There are three primary sources that might act as sources of risk in an organisation. They are:
i) Energy, that might account for rise in risk involved with physical damage.
ii) Functional failures of the organisation to fulfil the objectives of any mission might give rise to financial risk.
iii) Liabilities of legal guidelines and from the external stakeholders in a company might also account for risk of heavy financial losses in
the company.
4. What is a risk register and what information does it contain?
The Risk Register is a master document, created during the early phase of any operation of the company. This register is generally shared among
all external and internal stakeholders so that they are well aware of the issues and also keep on tracking the responses to counter the issues
(Ivanov et al. 2016). The risk register contains details about the project risks, description of the severity of the risks and a detailed evaluation of
the ways in which the risks might be mitigated. Most often, these information are arranged on a spreadsheet so that they might be easily found in
the register when required.
The last step is the evaluation of the chances of improvement of risk mitigation policies. The evaluation is based on the two parameters, namely
the degree of the risks and cost of introducing changes (Falkner and Hiebl, 2015). The organisation needs to evaluate financial, legal as well as
moral risks in this way.
3. What are the main types of sources of risk in an organisation?
There are three primary sources that might act as sources of risk in an organisation. They are:
i) Energy, that might account for rise in risk involved with physical damage.
ii) Functional failures of the organisation to fulfil the objectives of any mission might give rise to financial risk.
iii) Liabilities of legal guidelines and from the external stakeholders in a company might also account for risk of heavy financial losses in
the company.
4. What is a risk register and what information does it contain?
The Risk Register is a master document, created during the early phase of any operation of the company. This register is generally shared among
all external and internal stakeholders so that they are well aware of the issues and also keep on tracking the responses to counter the issues
(Ivanov et al. 2016). The risk register contains details about the project risks, description of the severity of the risks and a detailed evaluation of
the ways in which the risks might be mitigated. Most often, these information are arranged on a spreadsheet so that they might be easily found in
the register when required.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7Advanced Financial Accounting
5. Why is there a need to distinguish between general risks and operational risks?
General risks cover all risks associated with the services and/or products of the company and the strategic decisions taken by the company. A
general risk is the decision taken by the company to enter a new business market with the launch of a new product. Again, if a comp any signs a
partnership deal with a new company, then again nit is a general business risk (Lodhia, 2015).
Operational risks address the risk of internal decisions and practices of the organisation. In spite of a good and innovative business idea, the
organisation might fail to achieve success, owing to poor internal operation.
Operational risks might be mitigated by implementation of control programs, such as identification of the negative events that competitors faced
while conducting the same business. Generally risks are hard to map. For evidence, a company has hardly any means of predicting the nature of
material costs in future or anticipating the customer trends of the future (Lozano, 2015).
6. How do you know if risk is under successful control?
Three needs have to be addressed in order to state that the risk is under control. The first, is a statement from the stakeholders addressing the
achievement of their targets. The second is assurance of the company policies that address the mission and third are the means of influencing the
system that the company is trying to control (Marcelino-Sádaba et al. 2014).
7. Explain the difference between a risk management system and a systemic approach to risk management
5. Why is there a need to distinguish between general risks and operational risks?
General risks cover all risks associated with the services and/or products of the company and the strategic decisions taken by the company. A
general risk is the decision taken by the company to enter a new business market with the launch of a new product. Again, if a comp any signs a
partnership deal with a new company, then again nit is a general business risk (Lodhia, 2015).
Operational risks address the risk of internal decisions and practices of the organisation. In spite of a good and innovative business idea, the
organisation might fail to achieve success, owing to poor internal operation.
Operational risks might be mitigated by implementation of control programs, such as identification of the negative events that competitors faced
while conducting the same business. Generally risks are hard to map. For evidence, a company has hardly any means of predicting the nature of
material costs in future or anticipating the customer trends of the future (Lozano, 2015).
6. How do you know if risk is under successful control?
Three needs have to be addressed in order to state that the risk is under control. The first, is a statement from the stakeholders addressing the
achievement of their targets. The second is assurance of the company policies that address the mission and third are the means of influencing the
system that the company is trying to control (Marcelino-Sádaba et al. 2014).
7. Explain the difference between a risk management system and a systemic approach to risk management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8Advanced Financial Accounting
The systemic approach generally applies to traditional projects that are plan driven. Such projects follow a planned approach of identification
and analysis of the risks followed by development of risk responses. Whereas a risk management system is a more flexible approach that has the
capability to address risks during the course of progression of the project. In a risk management system, it is not necessary to have a discreet risk
management policy for individual risks (Schaltegger and Burritt, 2018).
8. Summarise the necessary content of a risk management system.
Intended risk control measures designed in advance might fail during the operation process. It is necessary to carry out a formal risk analysis that
would identify, specific practical efforts to mitigate the risk. However the sustenance of these efforts is liable to the proficiency of the
management of the company and the continuity of its efforts (Soomro, Shah and Ahmed, 2016).
Part A (2)
Explain why LTIFR is not a useful measure of that aspect of risk that is associated with high Consequence values.
Many of the Risk mitigation policies and practices are cost incurring. However, installation of the facilities do not help to reduce the risk of
threat events in the entire arena of the organisation. Again, as the organisations are becoming more economic and commercially oriented they
are gradually leaning towards a high risk yet low operational cost policy. In the organisational context, this means less investment on
equipment, investment or training. Many organisations in order to gain short time productivity gains, have resorted to reducing their
maintenance costs (Van Der Vegt et al. 2015). Interestingly, many organisations are proud of their low lost time injury frequency rate.
The systemic approach generally applies to traditional projects that are plan driven. Such projects follow a planned approach of identification
and analysis of the risks followed by development of risk responses. Whereas a risk management system is a more flexible approach that has the
capability to address risks during the course of progression of the project. In a risk management system, it is not necessary to have a discreet risk
management policy for individual risks (Schaltegger and Burritt, 2018).
8. Summarise the necessary content of a risk management system.
Intended risk control measures designed in advance might fail during the operation process. It is necessary to carry out a formal risk analysis that
would identify, specific practical efforts to mitigate the risk. However the sustenance of these efforts is liable to the proficiency of the
management of the company and the continuity of its efforts (Soomro, Shah and Ahmed, 2016).
Part A (2)
Explain why LTIFR is not a useful measure of that aspect of risk that is associated with high Consequence values.
Many of the Risk mitigation policies and practices are cost incurring. However, installation of the facilities do not help to reduce the risk of
threat events in the entire arena of the organisation. Again, as the organisations are becoming more economic and commercially oriented they
are gradually leaning towards a high risk yet low operational cost policy. In the organisational context, this means less investment on
equipment, investment or training. Many organisations in order to gain short time productivity gains, have resorted to reducing their
maintenance costs (Van Der Vegt et al. 2015). Interestingly, many organisations are proud of their low lost time injury frequency rate.

9Advanced Financial Accounting
Again, at times the organisations also take them to be measure for safety and thus neglect risk mitigation. In 42% of the cases, it has been
found that low risk response rate has caused high threat events owing to excess dependency on LTIFR rate. Particularly when a heavy fire
breaks out, as it happened in the case of ESSO plant of Australia, low LTIFR does not matter. Lastly, it might be stated that LTIFR is only a
perception, it cannot be a standard in reality (Wang et al. 2016).
Can you explain why any competent management team would prefer to operate with lower loss and risk costs and with higher risk control costs?
High LTIFR value in an organisation, often prompts the management to plan risk management with least interest. They do not have a significant
blueprint of risk management. They operate with a high total cost of risk management. High safety management is their alternative idea. They
believe in reactive risk management. This prompts the management teams to operate with low risk and loss costs along with high risk control
costs (Wu, Chen and Olson, 2014).
Consider an organisation with which you are familiar and identify and define the constituents of TCOR.
TCOR is the summation of the cost incurred due to loss along with investment in risk control. However, cost incurred due to loss is
uncertain. This is because loss is a dependent factor. Some of the organisations have low cost due to loss along with high investment in risk
controlling. Again the reverse is true for some companies (Yawar and Seuring, 2017).
Part B (1)
Again, at times the organisations also take them to be measure for safety and thus neglect risk mitigation. In 42% of the cases, it has been
found that low risk response rate has caused high threat events owing to excess dependency on LTIFR rate. Particularly when a heavy fire
breaks out, as it happened in the case of ESSO plant of Australia, low LTIFR does not matter. Lastly, it might be stated that LTIFR is only a
perception, it cannot be a standard in reality (Wang et al. 2016).
Can you explain why any competent management team would prefer to operate with lower loss and risk costs and with higher risk control costs?
High LTIFR value in an organisation, often prompts the management to plan risk management with least interest. They do not have a significant
blueprint of risk management. They operate with a high total cost of risk management. High safety management is their alternative idea. They
believe in reactive risk management. This prompts the management teams to operate with low risk and loss costs along with high risk control
costs (Wu, Chen and Olson, 2014).
Consider an organisation with which you are familiar and identify and define the constituents of TCOR.
TCOR is the summation of the cost incurred due to loss along with investment in risk control. However, cost incurred due to loss is
uncertain. This is because loss is a dependent factor. Some of the organisations have low cost due to loss along with high investment in risk
controlling. Again the reverse is true for some companies (Yawar and Seuring, 2017).
Part B (1)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10Advanced Financial Accounting
Choose a type of Risk that is of interest to yourself. Ensure first that you understand what is meant by the phrase “Type of Risk”
1. Define it carefully, ensuring you have a proper understanding of the way Risk is defined.
Customer risk is a major risk that many potential companies are exposed to. The companies which do not collect upfront cash payments against
their goods and services always face a threat that the customer might not pay the money at all. The factors of non-payment might be negligence,
other financial losses, bankruptcy of the customer or mostly fraudulent cases. Again, delivering goods and services at first to the customer and
billing the customer later on exposes the company to credit risk throughout the period of the payment terms granted to the customer. The direct
impact of the Customer risk might fall on the cash flow and profitability of the company (Zou, Kiviniemi and Jones, 2017).
2. What parameters could be used to describe this Risk in a manner that enabled it to be compared in significance with other Risks of a different
nature? Identify them and briefly explain your choice.
Change in cost of the proposed changes
This is a parameter that is applicable on all risks including customer risk. A comparison of the suppliers risk with the Customer risk can be
made. In case if a supplier’s commodity price overshoots highly or a potential supplier signs a monopoly contract with another market peer,
the share cost of the change implementation in response to the risk would enhance. Again, if the customers brand loyalty changes, or the
target market becomes occupied with a new entrant, the same consequences might occur.
Urgency or sensitivity
Choose a type of Risk that is of interest to yourself. Ensure first that you understand what is meant by the phrase “Type of Risk”
1. Define it carefully, ensuring you have a proper understanding of the way Risk is defined.
Customer risk is a major risk that many potential companies are exposed to. The companies which do not collect upfront cash payments against
their goods and services always face a threat that the customer might not pay the money at all. The factors of non-payment might be negligence,
other financial losses, bankruptcy of the customer or mostly fraudulent cases. Again, delivering goods and services at first to the customer and
billing the customer later on exposes the company to credit risk throughout the period of the payment terms granted to the customer. The direct
impact of the Customer risk might fall on the cash flow and profitability of the company (Zou, Kiviniemi and Jones, 2017).
2. What parameters could be used to describe this Risk in a manner that enabled it to be compared in significance with other Risks of a different
nature? Identify them and briefly explain your choice.
Change in cost of the proposed changes
This is a parameter that is applicable on all risks including customer risk. A comparison of the suppliers risk with the Customer risk can be
made. In case if a supplier’s commodity price overshoots highly or a potential supplier signs a monopoly contract with another market peer,
the share cost of the change implementation in response to the risk would enhance. Again, if the customers brand loyalty changes, or the
target market becomes occupied with a new entrant, the same consequences might occur.
Urgency or sensitivity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11Advanced Financial Accounting
In terms of urgency or sensitivity the Customer risk has equal value as in regard to other risks like share price or production process. The
required changes that are urgent or sensitive are applicable in all contexts.
Imposition of the risk
Loss of cash flow due to unavoidable external factors are risks pertaining to operational processes. This is external imposition of the risk.
Such as non-payment of customers or misplacement of customer payment an equal external imposition.
Locus of control over the Risk
The locus of control is internal for customer risk. However, if the payment of the customer do not reach the company owing to unavoidable
circumstances like accident or death of the customer then the locus would shift from internal to external.
3. What parameters could be used to allow this particular Risk to be compared with other Risks of the same type? Identify them and briefly
explain your choice.
The risk assessment parameters of customer risk are identification verification of the customer, risk pertaining to the validity of the citizenship of
the customer which is associated with the risk of taxation (Falkner and Hiebl, 2015). Again, other major parameters are sources of income of the
associated customer, occupation of the customer and the length and track record of the customer’s relationship with the organisation. The last
risk is the negative news that might spread against the customer.
In terms of urgency or sensitivity the Customer risk has equal value as in regard to other risks like share price or production process. The
required changes that are urgent or sensitive are applicable in all contexts.
Imposition of the risk
Loss of cash flow due to unavoidable external factors are risks pertaining to operational processes. This is external imposition of the risk.
Such as non-payment of customers or misplacement of customer payment an equal external imposition.
Locus of control over the Risk
The locus of control is internal for customer risk. However, if the payment of the customer do not reach the company owing to unavoidable
circumstances like accident or death of the customer then the locus would shift from internal to external.
3. What parameters could be used to allow this particular Risk to be compared with other Risks of the same type? Identify them and briefly
explain your choice.
The risk assessment parameters of customer risk are identification verification of the customer, risk pertaining to the validity of the citizenship of
the customer which is associated with the risk of taxation (Falkner and Hiebl, 2015). Again, other major parameters are sources of income of the
associated customer, occupation of the customer and the length and track record of the customer’s relationship with the organisation. The last
risk is the negative news that might spread against the customer.
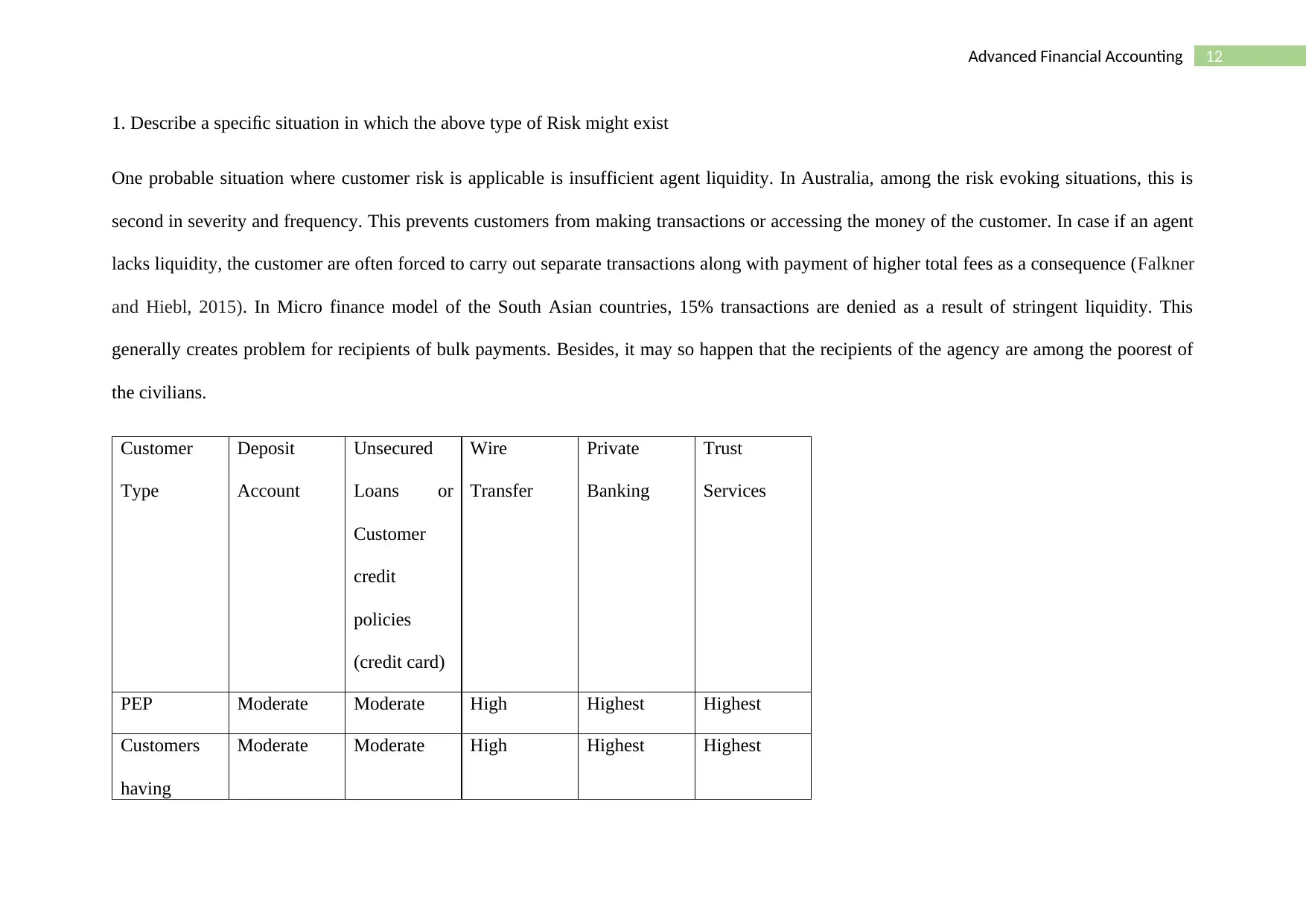
12Advanced Financial Accounting
1. Describe a specific situation in which the above type of Risk might exist
One probable situation where customer risk is applicable is insufficient agent liquidity. In Australia, among the risk evoking situations, this is
second in severity and frequency. This prevents customers from making transactions or accessing the money of the customer. In case if an agent
lacks liquidity, the customer are often forced to carry out separate transactions along with payment of higher total fees as a consequence (Falkner
and Hiebl, 2015). In Micro finance model of the South Asian countries, 15% transactions are denied as a result of stringent liquidity. This
generally creates problem for recipients of bulk payments. Besides, it may so happen that the recipients of the agency are among the poorest of
the civilians.
Customer
Type
Deposit
Account
Unsecured
Loans or
Customer
credit
policies
(credit card)
Wire
Transfer
Private
Banking
Trust
Services
PEP Moderate Moderate High Highest Highest
Customers
having
Moderate Moderate High Highest Highest
1. Describe a specific situation in which the above type of Risk might exist
One probable situation where customer risk is applicable is insufficient agent liquidity. In Australia, among the risk evoking situations, this is
second in severity and frequency. This prevents customers from making transactions or accessing the money of the customer. In case if an agent
lacks liquidity, the customer are often forced to carry out separate transactions along with payment of higher total fees as a consequence (Falkner
and Hiebl, 2015). In Micro finance model of the South Asian countries, 15% transactions are denied as a result of stringent liquidity. This
generally creates problem for recipients of bulk payments. Besides, it may so happen that the recipients of the agency are among the poorest of
the civilians.
Customer
Type
Deposit
Account
Unsecured
Loans or
Customer
credit
policies
(credit card)
Wire
Transfer
Private
Banking
Trust
Services
PEP Moderate Moderate High Highest Highest
Customers
having
Moderate Moderate High Highest Highest
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





