Advanced System and Network Security Homework Solutions
VerifiedAdded on 2020/03/16
|18
|4395
|360
Homework Assignment
AI Summary
This document presents a comprehensive solution to an advanced system and network security assignment. The assignment explores the security architecture for distributed environments, analyzing potential threats such as denial-of-service attacks and data breaches. It specifies security services and mechanisms, including the use of firewalls, VPNs, and remote access servers, along with the placement of security components. The solution also delves into threat modeling, outlining the steps involved in identifying and mitigating risks. It analyzes the impact of security tool vendor failures in identifying attack signatures and provides solutions for string-based substitution ciphers, including ciphertext decryption, error analysis, and dictionary attack prevention. The document also covers the key size for general n-bit substitution block ciphers and explores triple encryption with CBC, discussing the impact of bit errors and analyzing the implications of various cryptographic techniques.

Running head: Advanced System and Network Security 1
Advanced System and Network Security
Name
Affiliate Institution
Advanced System and Network Security
Name
Affiliate Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Advanced System and Network Security 2
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................5
Question 3........................................................................................................................................8
Question 4......................................................................................................................................10
Question 5......................................................................................................................................13
Question 6......................................................................................................................................14
References......................................................................................................................................16
Table of Contents
Question 1........................................................................................................................................3
Question 2........................................................................................................................................5
Question 3........................................................................................................................................8
Question 4......................................................................................................................................10
Question 5......................................................................................................................................13
Question 6......................................................................................................................................14
References......................................................................................................................................16

Running head: Advanced System and Network Security 3
Question 1
Outline a security architecture for the distributed environment shown below, where users
wish to access enterprise services from various remote locations such as home, airport and
other branch offices.
a) Analyze the security threats that can arise in such an environment. State any assumptions
that you are making.
Solution
Physical threats
Using distributed environment such as cloud computing is not an assurance that denial of service
attacks cannot occur. When you work from a different location apart from the office, there are
other external factors that ca lead to denial of service, they include pets, children who can
destroy, hide or interfere with your work station at home. There doesn’t exist a solution to this
type of DOS unless if the organization issues devices like iPhone that supports feature such as
“find my iPhone”. (Stewart, Chapple & Gibson, 2012).
Cloud computing cannot totally prevent critical information from being transferred to devices
that are not appropriately secured. To stop this, some extra controls need to be put in place.
Use of emails by employees working remotely has enhanced loss of critical and confidential data
over time. In this particular generation, nobody really wants to utilize the secured browser
because of its unfriendly interface. Sometimes the system admin forgets that employees working
offline still have access to the data in their inboxes even after data center lock down in case of an
attack.
Sometimes the devices that the employees are using when working offline have the capability to
be wiped remotely. When this happens some of the crucial personal data that the employee had
stored there will be deleted permanently. (Wang, 2010).
b) Specify the types of security services that would be needed to counteract this security
threats and what type of security mechanisms could support these services.
Solution
Question 1
Outline a security architecture for the distributed environment shown below, where users
wish to access enterprise services from various remote locations such as home, airport and
other branch offices.
a) Analyze the security threats that can arise in such an environment. State any assumptions
that you are making.
Solution
Physical threats
Using distributed environment such as cloud computing is not an assurance that denial of service
attacks cannot occur. When you work from a different location apart from the office, there are
other external factors that ca lead to denial of service, they include pets, children who can
destroy, hide or interfere with your work station at home. There doesn’t exist a solution to this
type of DOS unless if the organization issues devices like iPhone that supports feature such as
“find my iPhone”. (Stewart, Chapple & Gibson, 2012).
Cloud computing cannot totally prevent critical information from being transferred to devices
that are not appropriately secured. To stop this, some extra controls need to be put in place.
Use of emails by employees working remotely has enhanced loss of critical and confidential data
over time. In this particular generation, nobody really wants to utilize the secured browser
because of its unfriendly interface. Sometimes the system admin forgets that employees working
offline still have access to the data in their inboxes even after data center lock down in case of an
attack.
Sometimes the devices that the employees are using when working offline have the capability to
be wiped remotely. When this happens some of the crucial personal data that the employee had
stored there will be deleted permanently. (Wang, 2010).
b) Specify the types of security services that would be needed to counteract this security
threats and what type of security mechanisms could support these services.
Solution
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Advanced System and Network Security 4
Securing Multiple Devices
Security of the devices the remote employee is using is very critical. These devices are very
vulnerable as they can easily get lost or stolen and sensitive data could land in to the wrong
person if not well handled. (Zia, Zomaya, Varadharajan & Mao, 2013).
The following are some of the ways to enable employees to work securely remotely.
It is important to always use enhanced security software in the end devices used by the remote
employees as malicious software that steals data always get in to the devices via emails and
when browsing.
It is recommended to use applications and interfaces provided by the cloud vendor. This ensure
that security of data is of high level since the vendor has implemented features to encrypt data
while being transmitted from the remote servers to the organization’s intranet. (Morana &
UcedaVelez, 2011).
Implementing virtual private network can help keep the connections and internet secured. VPN
provided by a third party vendor would have implemented all the security patches that are
require to continuously check the network for any malicious activity.
The company should always make sure that strict procedures on data access, usability and
modification have been clearly stated to the employees opting to work remotely. The
organization should clearly outline who have access to the data center and clearly defines the
protocols to be used during this access. (Shostack, 2014).
Detection of packet sniffers to identify if hackers have had root access to the computer system.
Packet sniffers are normally used by hackers to gather information transmitted by an
organization through the internet.
It is important to train employees on the characteristics of a denial of service attacks. If this is not
done, hackers are very cunning and can trick these employees into revealing their login
credentials.
If an employee account gets compromised it is important to immediately block that account from
further access, that is, suspend the account until further notice. This will stop data loss or
modification. (In Chang, In Ramachandran, In Walters & In Wills, 2017).
Securing Multiple Devices
Security of the devices the remote employee is using is very critical. These devices are very
vulnerable as they can easily get lost or stolen and sensitive data could land in to the wrong
person if not well handled. (Zia, Zomaya, Varadharajan & Mao, 2013).
The following are some of the ways to enable employees to work securely remotely.
It is important to always use enhanced security software in the end devices used by the remote
employees as malicious software that steals data always get in to the devices via emails and
when browsing.
It is recommended to use applications and interfaces provided by the cloud vendor. This ensure
that security of data is of high level since the vendor has implemented features to encrypt data
while being transmitted from the remote servers to the organization’s intranet. (Morana &
UcedaVelez, 2011).
Implementing virtual private network can help keep the connections and internet secured. VPN
provided by a third party vendor would have implemented all the security patches that are
require to continuously check the network for any malicious activity.
The company should always make sure that strict procedures on data access, usability and
modification have been clearly stated to the employees opting to work remotely. The
organization should clearly outline who have access to the data center and clearly defines the
protocols to be used during this access. (Shostack, 2014).
Detection of packet sniffers to identify if hackers have had root access to the computer system.
Packet sniffers are normally used by hackers to gather information transmitted by an
organization through the internet.
It is important to train employees on the characteristics of a denial of service attacks. If this is not
done, hackers are very cunning and can trick these employees into revealing their login
credentials.
If an employee account gets compromised it is important to immediately block that account from
further access, that is, suspend the account until further notice. This will stop data loss or
modification. (In Chang, In Ramachandran, In Walters & In Wills, 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
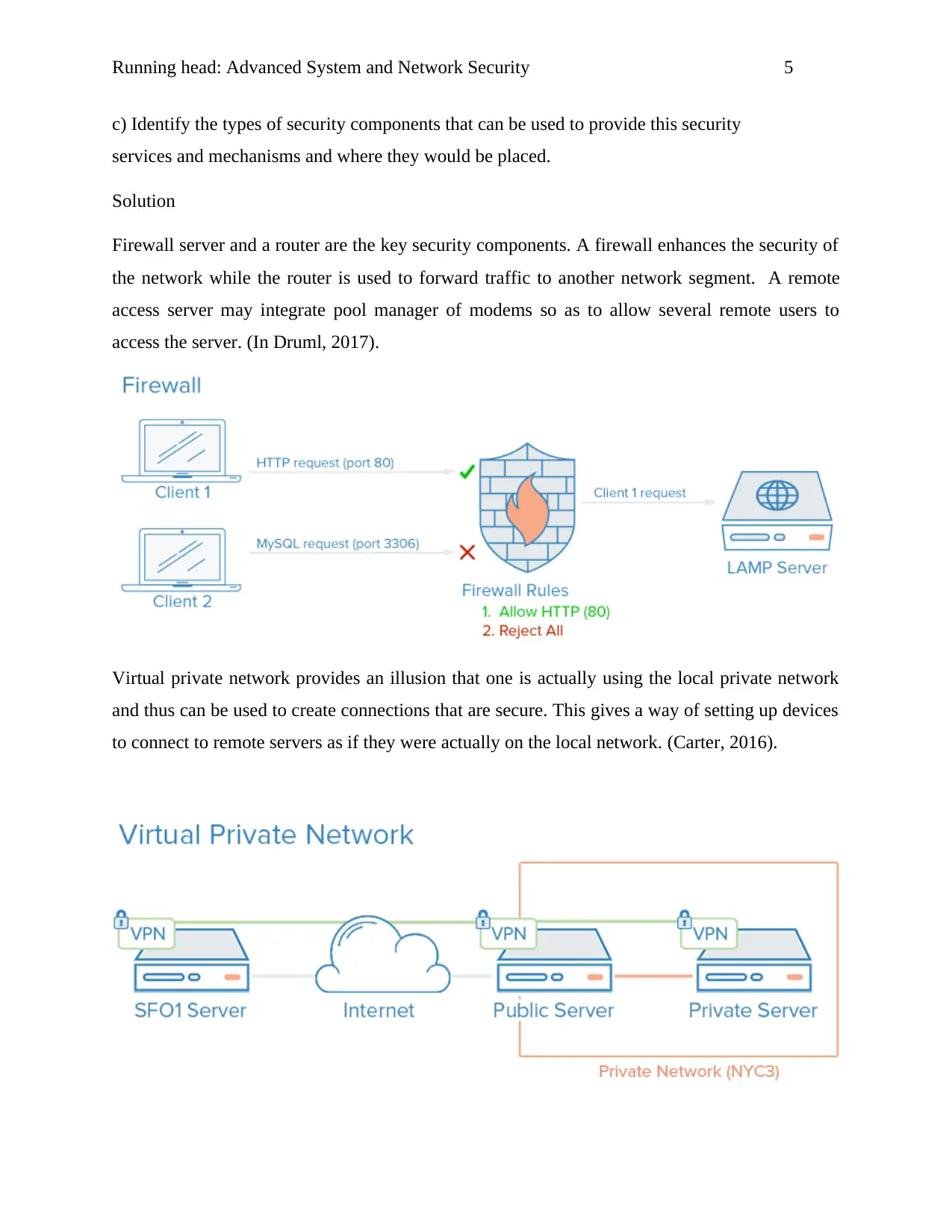
Running head: Advanced System and Network Security 5
c) Identify the types of security components that can be used to provide this security
services and mechanisms and where they would be placed.
Solution
Firewall server and a router are the key security components. A firewall enhances the security of
the network while the router is used to forward traffic to another network segment. A remote
access server may integrate pool manager of modems so as to allow several remote users to
access the server. (In Druml, 2017).
Virtual private network provides an illusion that one is actually using the local private network
and thus can be used to create connections that are secure. This gives a way of setting up devices
to connect to remote servers as if they were actually on the local network. (Carter, 2016).
c) Identify the types of security components that can be used to provide this security
services and mechanisms and where they would be placed.
Solution
Firewall server and a router are the key security components. A firewall enhances the security of
the network while the router is used to forward traffic to another network segment. A remote
access server may integrate pool manager of modems so as to allow several remote users to
access the server. (In Druml, 2017).
Virtual private network provides an illusion that one is actually using the local private network
and thus can be used to create connections that are secure. This gives a way of setting up devices
to connect to remote servers as if they were actually on the local network. (Carter, 2016).

Running head: Advanced System and Network Security 6
Question 2
a) What is threat modelling and describe the steps involved in a threat modelling process?
Solution
Threat modeling is the process of enhancing the security of a network by determining the goals,
weaknesses and identifying mitigation strategies to respond to impacts to the system. The
following are some of the steps followed when modelling a threat.
Step 1: Define
Determine security assets and goals.
Security goals plays a very important role in ensuring that system security principles such as
integrity, availability, confidentiality, authorization, accountability and authentication are met.
These goals aid engineers to concentrate on every objective and assess the entry locations
security tolerance against threats. (Martin, 2017).
Step 2: Design
Define Trust Boundaries and Attack Surface.
An attack surface is that point that an intruder can use to attack the system while trust boundaries
are the points at which trust changes. Declaration of trust boundaries and attack surfaces should
be done in order to enhance model objectives and scope. In this stage the analyst seeks to
determine the threats that might affect the security goals. This procedure entails asset analysis
and their threats, evaluation of entry and exit points, application layer and associated
communication media. (In Roychoudhury & In Liu, 2017).
Step 3: Measure
Threat Prioritization.
Threats should be defined and prioritized depending on the system impact. Prioritizing a threat is
usually based on damage cost. Both indirect and direct risks are considered in this situation. after
the threats have been prioritized, the next step is to implement appropriate controls to mitigate
them. Re-validation of controls should be made were appropriate.
Question 2
a) What is threat modelling and describe the steps involved in a threat modelling process?
Solution
Threat modeling is the process of enhancing the security of a network by determining the goals,
weaknesses and identifying mitigation strategies to respond to impacts to the system. The
following are some of the steps followed when modelling a threat.
Step 1: Define
Determine security assets and goals.
Security goals plays a very important role in ensuring that system security principles such as
integrity, availability, confidentiality, authorization, accountability and authentication are met.
These goals aid engineers to concentrate on every objective and assess the entry locations
security tolerance against threats. (Martin, 2017).
Step 2: Design
Define Trust Boundaries and Attack Surface.
An attack surface is that point that an intruder can use to attack the system while trust boundaries
are the points at which trust changes. Declaration of trust boundaries and attack surfaces should
be done in order to enhance model objectives and scope. In this stage the analyst seeks to
determine the threats that might affect the security goals. This procedure entails asset analysis
and their threats, evaluation of entry and exit points, application layer and associated
communication media. (In Roychoudhury & In Liu, 2017).
Step 3: Measure
Threat Prioritization.
Threats should be defined and prioritized depending on the system impact. Prioritizing a threat is
usually based on damage cost. Both indirect and direct risks are considered in this situation. after
the threats have been prioritized, the next step is to implement appropriate controls to mitigate
them. Re-validation of controls should be made were appropriate.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
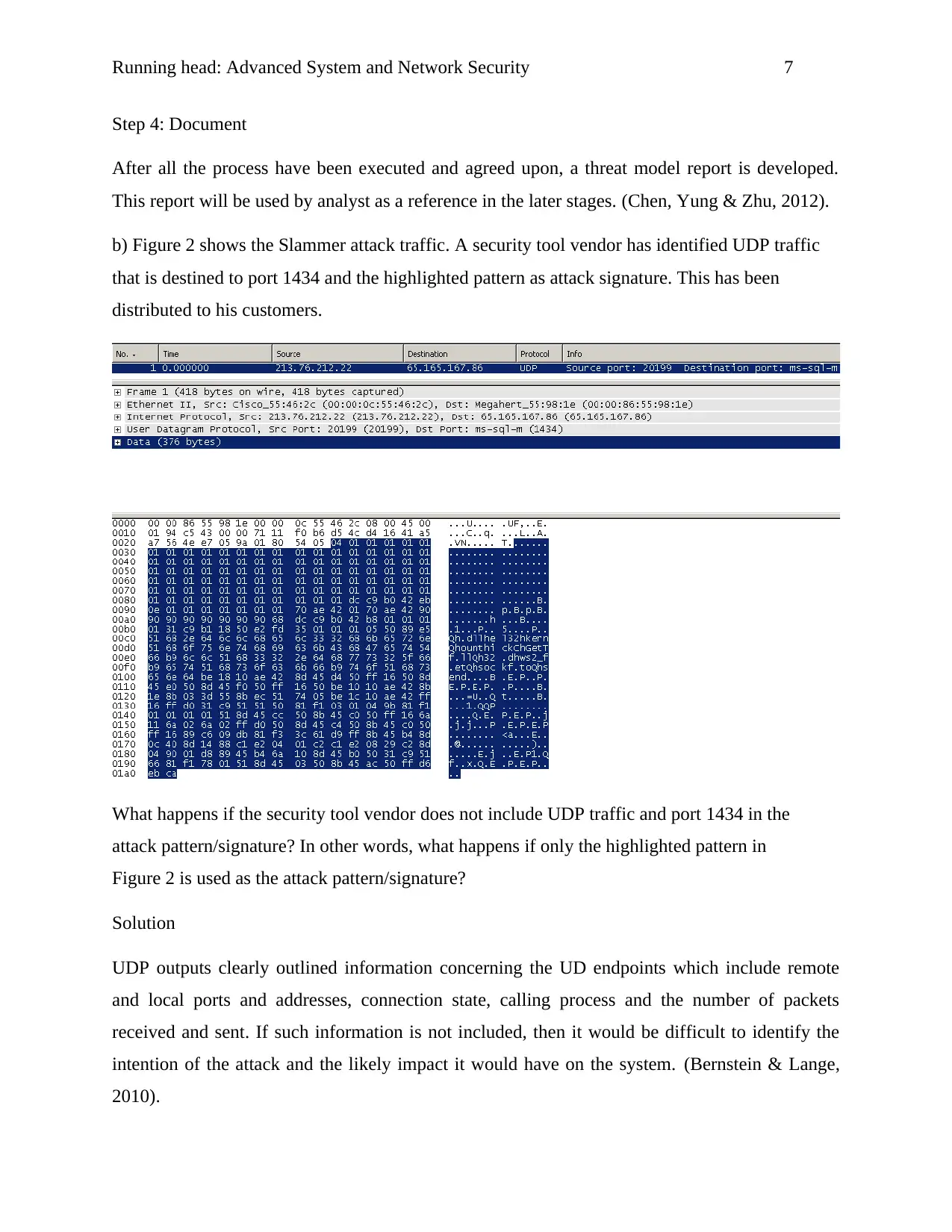
Running head: Advanced System and Network Security 7
Step 4: Document
After all the process have been executed and agreed upon, a threat model report is developed.
This report will be used by analyst as a reference in the later stages. (Chen, Yung & Zhu, 2012).
b) Figure 2 shows the Slammer attack traffic. A security tool vendor has identified UDP traffic
that is destined to port 1434 and the highlighted pattern as attack signature. This has been
distributed to his customers.
What happens if the security tool vendor does not include UDP traffic and port 1434 in the
attack pattern/signature? In other words, what happens if only the highlighted pattern in
Figure 2 is used as the attack pattern/signature?
Solution
UDP outputs clearly outlined information concerning the UD endpoints which include remote
and local ports and addresses, connection state, calling process and the number of packets
received and sent. If such information is not included, then it would be difficult to identify the
intention of the attack and the likely impact it would have on the system. (Bernstein & Lange,
2010).
Step 4: Document
After all the process have been executed and agreed upon, a threat model report is developed.
This report will be used by analyst as a reference in the later stages. (Chen, Yung & Zhu, 2012).
b) Figure 2 shows the Slammer attack traffic. A security tool vendor has identified UDP traffic
that is destined to port 1434 and the highlighted pattern as attack signature. This has been
distributed to his customers.
What happens if the security tool vendor does not include UDP traffic and port 1434 in the
attack pattern/signature? In other words, what happens if only the highlighted pattern in
Figure 2 is used as the attack pattern/signature?
Solution
UDP outputs clearly outlined information concerning the UD endpoints which include remote
and local ports and addresses, connection state, calling process and the number of packets
received and sent. If such information is not included, then it would be difficult to identify the
intention of the attack and the likely impact it would have on the system. (Bernstein & Lange,
2010).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Advanced System and Network Security 8
Question 3
a) Consider the following simple string based substitution cipher. It takes a plaintext letter
as input from the English alphabet and produces a cipher text output by combining it with
a key string security. The encoding rule used is a=0, b=1, …., z=25 etc. The numerical
representation of this key string is (18, 4, 2, 20, 17, 8, 19, 24). The operation is a character-wise
addition modulo 26, i.e., (x + y) mod 26. Find the cipher text corresponding to the following
plaintext. (Treat both uppercase and lowercase characters to be the same)
“SecurityIsPeaceOfMind”
Solution
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
SecurityIsPeaceOfMind
Security - S=18, E=4, C=2, U=20, R=17, I=8, T=19, Y=24 the corresponding cipher equals
(18,4,2,20,17,8.19,24)
Is - I=8, s=18 the corresponding cipher equals (8,18)
Peace - P=15, e=4, a=0, c=2, e=4 the corresponding cipher equals (15,4,0,2,4)
Of - O=14, f=5 the corresponding cipher equals (14,5)
Mind - M=12, i=8, n=13, d=3 the corresponding cipher equals (12,8,13,3)
SecurityIsPeaceOfMind - the corresponding cipher equals (18,4,2,20,17,8.19,24, 8,18,
15,4,0,2,4,14,5, 12,8,13,3)
b) Assume the above cipher text is transferred over a network to a receiver. If an error
occurs during the transmission of this cipher text affecting one letter, how much of the
decrypted plaintext will be in error.
Solution
64/21=3 plus itself therefore resulting to 4
Question 3
a) Consider the following simple string based substitution cipher. It takes a plaintext letter
as input from the English alphabet and produces a cipher text output by combining it with
a key string security. The encoding rule used is a=0, b=1, …., z=25 etc. The numerical
representation of this key string is (18, 4, 2, 20, 17, 8, 19, 24). The operation is a character-wise
addition modulo 26, i.e., (x + y) mod 26. Find the cipher text corresponding to the following
plaintext. (Treat both uppercase and lowercase characters to be the same)
“SecurityIsPeaceOfMind”
Solution
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
SecurityIsPeaceOfMind
Security - S=18, E=4, C=2, U=20, R=17, I=8, T=19, Y=24 the corresponding cipher equals
(18,4,2,20,17,8.19,24)
Is - I=8, s=18 the corresponding cipher equals (8,18)
Peace - P=15, e=4, a=0, c=2, e=4 the corresponding cipher equals (15,4,0,2,4)
Of - O=14, f=5 the corresponding cipher equals (14,5)
Mind - M=12, i=8, n=13, d=3 the corresponding cipher equals (12,8,13,3)
SecurityIsPeaceOfMind - the corresponding cipher equals (18,4,2,20,17,8.19,24, 8,18,
15,4,0,2,4,14,5, 12,8,13,3)
b) Assume the above cipher text is transferred over a network to a receiver. If an error
occurs during the transmission of this cipher text affecting one letter, how much of the
decrypted plaintext will be in error.
Solution
64/21=3 plus itself therefore resulting to 4

Running head: Advanced System and Network Security 9
c) What is a dictionary attack on a block cipher, and how can we ensure that such an attack
is infeasible?
Solution
Dictionary attack
Dictionary attacks makes use the ineffective traits of users who uses simple patterns and
characters when choosing their passwords. All the words in the dictionary are encrypted by the
dictionary attack and compares it with the encrypted password in the password or SAM file.
(Koç, 2009).
In order to protect yourself from such attacks; enhance your password needs by increasing
complexity and using special characters such as underscore, asterisk, numbers, caps and mall
letters in one password for example, ‘p@$sw0&rd_l0<ked’. The password should be uncommon
and hard to guess. (In Askoxylakis, In Ioannidis, In Katsikas & In Meadows, 2016).
It is recommended to set up password expiration for users. This will require them to update their
password after some specific period of time. It is very important to ensure that this feature is in
balance with the level of security of the system.
Also it is important to ensure that remote connection root login is disabled. Due to its
commonness it is prone to brute force attack.
Disable password authentication and use SSH keys to access remote server. It is a very secure
means of login into the remote server as compared to use of passwords.
The simplest way to identify and prevent dictionary attacks is to set a limited number of login
attempts. This is a tool that is used to temporarily suspend an account. This will help discourage
attackers from further trying to access the system. Also adding some wait time in between login
attempts is also a good strategy to prevent automated tools that can make thousands of guesses
automatically. (Tang, Muller & Sharif, 2010)
It is also good to allow only SSH connections for specific IP addresses or hosts. This makes sure
that devices connecting to the server are known and are validated to access the resources.
c) What is a dictionary attack on a block cipher, and how can we ensure that such an attack
is infeasible?
Solution
Dictionary attack
Dictionary attacks makes use the ineffective traits of users who uses simple patterns and
characters when choosing their passwords. All the words in the dictionary are encrypted by the
dictionary attack and compares it with the encrypted password in the password or SAM file.
(Koç, 2009).
In order to protect yourself from such attacks; enhance your password needs by increasing
complexity and using special characters such as underscore, asterisk, numbers, caps and mall
letters in one password for example, ‘p@$sw0&rd_l0<ked’. The password should be uncommon
and hard to guess. (In Askoxylakis, In Ioannidis, In Katsikas & In Meadows, 2016).
It is recommended to set up password expiration for users. This will require them to update their
password after some specific period of time. It is very important to ensure that this feature is in
balance with the level of security of the system.
Also it is important to ensure that remote connection root login is disabled. Due to its
commonness it is prone to brute force attack.
Disable password authentication and use SSH keys to access remote server. It is a very secure
means of login into the remote server as compared to use of passwords.
The simplest way to identify and prevent dictionary attacks is to set a limited number of login
attempts. This is a tool that is used to temporarily suspend an account. This will help discourage
attackers from further trying to access the system. Also adding some wait time in between login
attempts is also a good strategy to prevent automated tools that can make thousands of guesses
automatically. (Tang, Muller & Sharif, 2010)
It is also good to allow only SSH connections for specific IP addresses or hosts. This makes sure
that devices connecting to the server are known and are validated to access the resources.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Advanced System and Network Security 10
d) Consider a general n-bit substitution block cipher. What is the size of the key (number of
bits in the key) required for such a general block cipher? Explain how you arrive at the
answer.
Solution
Size of the key is 64
It enters a 64-bit plaintext P and a 56-bit key K
The key-schedule KS resulted from the 56-bit key K a series of 16 sub-keys, one
for every round that follows. Every sub-key has a length of 48-bits.
function DESK(P) // |K| = 56 and |P| = 64
(K1, . . . ,K16) ← KS(K) // |Ki| = 48 for 1 ≤ i ≤ 16
P ← IP(P)
Parse P as L0 k R0 // |L0| = |R0| = 32
for r = 1 to 16 do
Lr ← Rr−1 ; Rr ← f(Kr,Rr−1) ⊕ Lr−1
C ← IP−1(L16 k R16)
return C (Rhee, 2013).
Question 4
a) Consider triple encryption by using E-D-E with CBC on the inside. If a single bit “x” of the
cipher text block, say ”c2” is modified, then how does it affect the decrypted plaintext?
d) Consider a general n-bit substitution block cipher. What is the size of the key (number of
bits in the key) required for such a general block cipher? Explain how you arrive at the
answer.
Solution
Size of the key is 64
It enters a 64-bit plaintext P and a 56-bit key K
The key-schedule KS resulted from the 56-bit key K a series of 16 sub-keys, one
for every round that follows. Every sub-key has a length of 48-bits.
function DESK(P) // |K| = 56 and |P| = 64
(K1, . . . ,K16) ← KS(K) // |Ki| = 48 for 1 ≤ i ≤ 16
P ← IP(P)
Parse P as L0 k R0 // |L0| = |R0| = 32
for r = 1 to 16 do
Lr ← Rr−1 ; Rr ← f(Kr,Rr−1) ⊕ Lr−1
C ← IP−1(L16 k R16)
return C (Rhee, 2013).
Question 4
a) Consider triple encryption by using E-D-E with CBC on the inside. If a single bit “x” of the
cipher text block, say ”c2” is modified, then how does it affect the decrypted plaintext?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
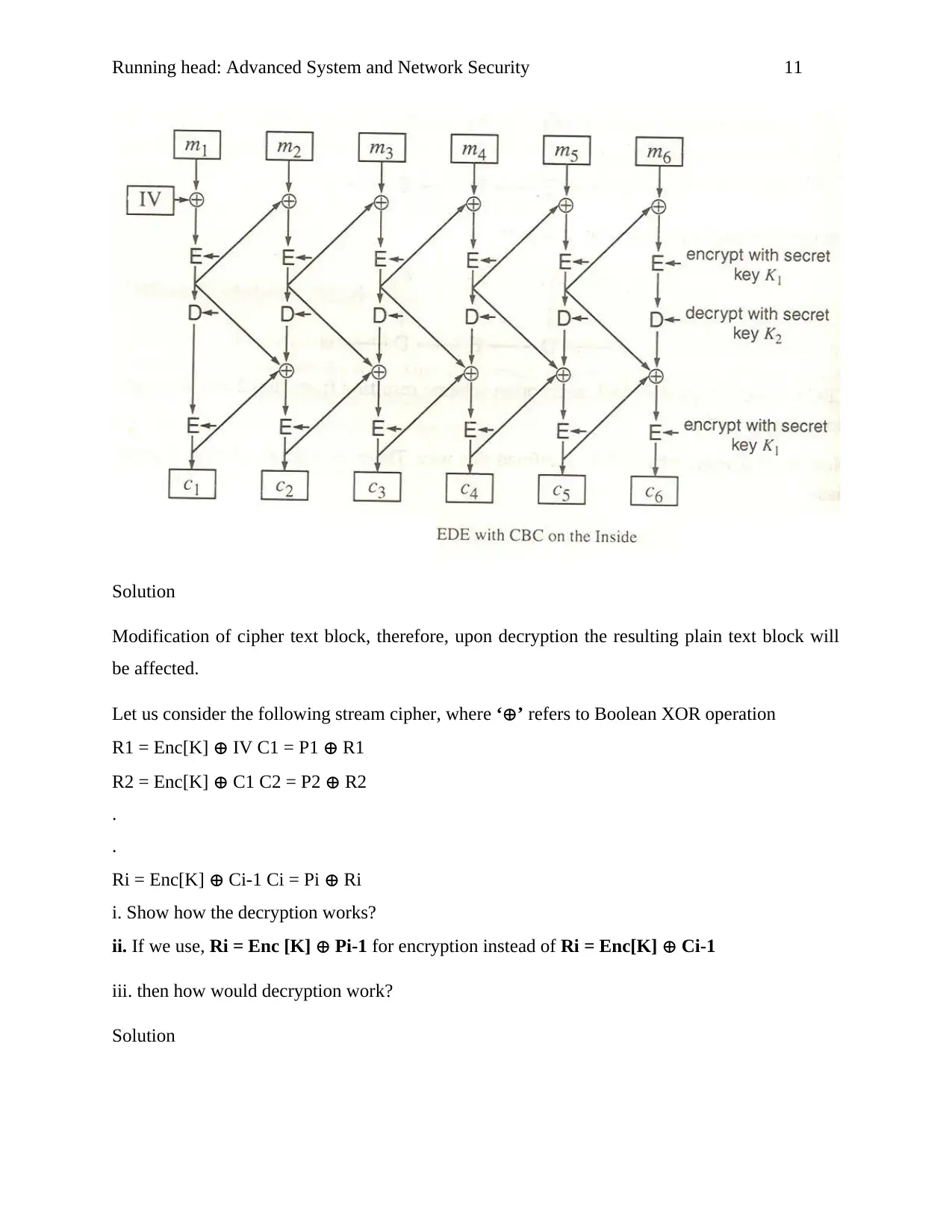
Running head: Advanced System and Network Security 11
Solution
Modification of cipher text block, therefore, upon decryption the resulting plain text block will
be affected.
Let us consider the following stream cipher, where ‘⊕’ refers to Boolean XOR operation
R1 = Enc[K] ⊕ IV C1 = P1 ⊕ R1
R2 = Enc[K] ⊕ C1 C2 = P2 ⊕ R2
.
.
Ri = Enc[K] ⊕ Ci-1 Ci = Pi ⊕ Ri
i. Show how the decryption works?
ii. If we use, Ri = Enc [K] ⊕ Pi-1 for encryption instead of Ri = Enc[K] ⊕ Ci-1
iii. then how would decryption work?
Solution
Solution
Modification of cipher text block, therefore, upon decryption the resulting plain text block will
be affected.
Let us consider the following stream cipher, where ‘⊕’ refers to Boolean XOR operation
R1 = Enc[K] ⊕ IV C1 = P1 ⊕ R1
R2 = Enc[K] ⊕ C1 C2 = P2 ⊕ R2
.
.
Ri = Enc[K] ⊕ Ci-1 Ci = Pi ⊕ Ri
i. Show how the decryption works?
ii. If we use, Ri = Enc [K] ⊕ Pi-1 for encryption instead of Ri = Enc[K] ⊕ Ci-1
iii. then how would decryption work?
Solution
Running head: Advanced System and Network Security 12
Plain text are converted to cipher texts by stream ciphers one bit at a time. XOR is an example of
implementation of stream cipher. In the implementation below, the generator keystream displays
a stream of bits k1, k2, k3……ki. This keystream is then XORed with plain text stream bits
p1 ,p2, p3…..pi to output cipher text stream bits. The formula ci=pi XOR ki describes this
operation. The cipher texts are XORed to recover the plaintext bits using identical keystreams.
The formula pi=ci XOR ki describes this operation. (Schneier, 2008).
encryption decryption IV Security
Ci = EK(Pi ⊕ Ci-1) Pi = DK(Ci) ⊕ Ci-1 unique + (+)
iv. Discuss the security of the above schemes.
Solution
The limitation of this scheme is that an attacker can easily identify the cipher-text and plaintext
for a group of messages. He or she can easily combine and match message blocks. This is
because block n belonging to plaintext ⊕’d with cipher-text block n+1 is D belonging to block
n+1 of plaintext. Once has identified D of the target block he or she can ⊕ with previous block
of the plaintext to display cipher-text correctly. (Anderson, 2008).
b) A system is designed to use the RSA public key scheme, where m is the modulus, (e, m) is
the public key and (d, p, q) is the corresponding private key. The system developer
Plain text are converted to cipher texts by stream ciphers one bit at a time. XOR is an example of
implementation of stream cipher. In the implementation below, the generator keystream displays
a stream of bits k1, k2, k3……ki. This keystream is then XORed with plain text stream bits
p1 ,p2, p3…..pi to output cipher text stream bits. The formula ci=pi XOR ki describes this
operation. The cipher texts are XORed to recover the plaintext bits using identical keystreams.
The formula pi=ci XOR ki describes this operation. (Schneier, 2008).
encryption decryption IV Security
Ci = EK(Pi ⊕ Ci-1) Pi = DK(Ci) ⊕ Ci-1 unique + (+)
iv. Discuss the security of the above schemes.
Solution
The limitation of this scheme is that an attacker can easily identify the cipher-text and plaintext
for a group of messages. He or she can easily combine and match message blocks. This is
because block n belonging to plaintext ⊕’d with cipher-text block n+1 is D belonging to block
n+1 of plaintext. Once has identified D of the target block he or she can ⊕ with previous block
of the plaintext to display cipher-text correctly. (Anderson, 2008).
b) A system is designed to use the RSA public key scheme, where m is the modulus, (e, m) is
the public key and (d, p, q) is the corresponding private key. The system developer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




