Advanced Network Security: Penetration Test and Boot-to-Root Challenge
VerifiedAdded on 2022/11/14
|21
|1324
|243
Report
AI Summary
This report details a penetration test and a boot-to-root challenge performed as part of an advanced network security course (ITNET302A). The penetration test involved vulnerability scanning using Nessus, exploitation with Metasploit, and a risk assessment of identified vulnerabilities, categorized as critical, high, medium, and low. The report outlines the testing methodology, including reconnaissance, scanning, exploitation, post-exploitation, and reporting phases. The boot-to-root challenge involved exploiting a target system to gain root access and retrieve flags. The report includes findings, risk assessment criteria, and a conclusion summarizing the identified vulnerabilities and mitigation strategies, along with references to relevant resources. The student used VPN-KALI, Sploit and Red boxes to perform the tasks.

Penetration testing and the boot to root
challenge-
challenge-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Penetration testing and the boot to root challenge-....................................................................1
Executive summary-...................................................................................................................3
Scope –.......................................................................................................................................4
Penetration testing......................................................................................................................5
Testing methodology-................................................................................................................5
Reconnaissance-.....................................................................................................................5
Scanning-................................................................................................................................5
Exploitation-...........................................................................................................................8
Post exploitation-...................................................................................................................9
Reporting-..............................................................................................................................9
Finding summary-....................................................................................................................10
Risk Assessment Criteria-....................................................................................................11
Risk matrix-..........................................................................................................................12
Conclusion-..............................................................................................................................17
BOOT 2 ROOT CHALLENGE-..............................................................................................18
Flag first-..................................................................................................................................18
Flag second-.............................................................................................................................18
Flag third-.................................................................................................................................19
Flag fourth-...............................................................................................................................19
Flag fifth-.................................................................................................................................20
Flag sixth-.................................................................................................................................20
References-...............................................................................................................................21
Penetration testing and the boot to root challenge-....................................................................1
Executive summary-...................................................................................................................3
Scope –.......................................................................................................................................4
Penetration testing......................................................................................................................5
Testing methodology-................................................................................................................5
Reconnaissance-.....................................................................................................................5
Scanning-................................................................................................................................5
Exploitation-...........................................................................................................................8
Post exploitation-...................................................................................................................9
Reporting-..............................................................................................................................9
Finding summary-....................................................................................................................10
Risk Assessment Criteria-....................................................................................................11
Risk matrix-..........................................................................................................................12
Conclusion-..............................................................................................................................17
BOOT 2 ROOT CHALLENGE-..............................................................................................18
Flag first-..................................................................................................................................18
Flag second-.............................................................................................................................18
Flag third-.................................................................................................................................19
Flag fourth-...............................................................................................................................19
Flag fifth-.................................................................................................................................20
Flag sixth-.................................................................................................................................20
References-...............................................................................................................................21

Executive summary-
The principle motivation behind this report is to exhibit vulnerabilities and their abuse
through infiltration test and relieve unapproved assault to ensure our IT organization
framework. This appraisal was worked by Bikalpa Sharma with the assistance of VPN
condition on framework.
To start with, I have arranged root kali with VPN and run TAFE-kali by means of secure
attachment shell for example SSH student@10.220.0.0/24. In this procedure, Nmap is
utilized as a security scanner which gives data of adaptation of OS, ports, application and
administrations from target address. We have filtered the system through NESSUS in which
we can get the data of vulnerabilities. These vulnerabilities are classifications into basic, high,
medium, low and information. Abuse is propelled to the various sorts of vulnerabilities
through Metasploit that endeavours the area of vulnerabilities with their range.
This penetration test causes me to decide the sorts of vulnerabilities with hazard effect of
basic, high, medium, okay effect. This report demonstrates 8 sorts of vulnerabilities for
example 4 from basic risk, 1 from high chance of the risk, 2 from medium risk and 1 from
generally safe.
The principle motivation behind this report is to exhibit vulnerabilities and their abuse
through infiltration test and relieve unapproved assault to ensure our IT organization
framework. This appraisal was worked by Bikalpa Sharma with the assistance of VPN
condition on framework.
To start with, I have arranged root kali with VPN and run TAFE-kali by means of secure
attachment shell for example SSH student@10.220.0.0/24. In this procedure, Nmap is
utilized as a security scanner which gives data of adaptation of OS, ports, application and
administrations from target address. We have filtered the system through NESSUS in which
we can get the data of vulnerabilities. These vulnerabilities are classifications into basic, high,
medium, low and information. Abuse is propelled to the various sorts of vulnerabilities
through Metasploit that endeavours the area of vulnerabilities with their range.
This penetration test causes me to decide the sorts of vulnerabilities with hazard effect of
basic, high, medium, okay effect. This report demonstrates 8 sorts of vulnerabilities for
example 4 from basic risk, 1 from high chance of the risk, 2 from medium risk and 1 from
generally safe.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Scope –
In this assignment, the principle motivation behind this evaluation is to play out an entrance
test and assess various kinds of potential vulnerabilities sorted under network hazard level. A
few dangers related with vulnerabilities can cause enormous loss of information or private
data, framework slammed, etc. To relieve conceivable dangers on framework, various kinds
of arrangement, for example, stock potential vulnerabilities and others should use to verify
organize framework.
We also have to follow the table given below:-
Hostname Comment
VPN-KALI Run the exploitation
Sploit Performing the penetration testing
Red Performing the boot to root process
In this assignment, the principle motivation behind this evaluation is to play out an entrance
test and assess various kinds of potential vulnerabilities sorted under network hazard level. A
few dangers related with vulnerabilities can cause enormous loss of information or private
data, framework slammed, etc. To relieve conceivable dangers on framework, various kinds
of arrangement, for example, stock potential vulnerabilities and others should use to verify
organize framework.
We also have to follow the table given below:-
Hostname Comment
VPN-KALI Run the exploitation
Sploit Performing the penetration testing
Red Performing the boot to root process
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Penetration testing
Penetration testing, is additionally called as pen testing or as ethical hacking, is the act of
testing a PC framework, system or web application to discover security vulnerabilities that an
aggressor could abuse. Entrance testing can be robotized with programming applications or
performed physically.
Testing methodology-
There are five phases of testing which are Reconnaissance, scanning, exploitation, post
exploitation and the analysis report.
Reconnaissance-
It is the first phase of testing methodology which define the:-
Characterizing the extension and objectives of a test, including the frameworks to be
tended to and the testing techniques to be utilized.
Social affair knowledge (e.g., system and area names, mail server) to all the more likely
see how an objective functions and its potential vulnerabilities.
Scanning-
This is the second phase of testing which will uses the tool Nessus for scanning the
vulnerability in two form:-
Static investigation – Inspecting an application's code to assess the manner in which it
carries on while running. These devices can examine the total of the code in a solitary
pass.
Dynamic examination – Inspecting an application's code in a running state. This is a
progressively useful method for checking, as it gives a constant view into an application's
exhibition.
Penetration testing, is additionally called as pen testing or as ethical hacking, is the act of
testing a PC framework, system or web application to discover security vulnerabilities that an
aggressor could abuse. Entrance testing can be robotized with programming applications or
performed physically.
Testing methodology-
There are five phases of testing which are Reconnaissance, scanning, exploitation, post
exploitation and the analysis report.
Reconnaissance-
It is the first phase of testing methodology which define the:-
Characterizing the extension and objectives of a test, including the frameworks to be
tended to and the testing techniques to be utilized.
Social affair knowledge (e.g., system and area names, mail server) to all the more likely
see how an objective functions and its potential vulnerabilities.
Scanning-
This is the second phase of testing which will uses the tool Nessus for scanning the
vulnerability in two form:-
Static investigation – Inspecting an application's code to assess the manner in which it
carries on while running. These devices can examine the total of the code in a solitary
pass.
Dynamic examination – Inspecting an application's code in a running state. This is a
progressively useful method for checking, as it gives a constant view into an application's
exhibition.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
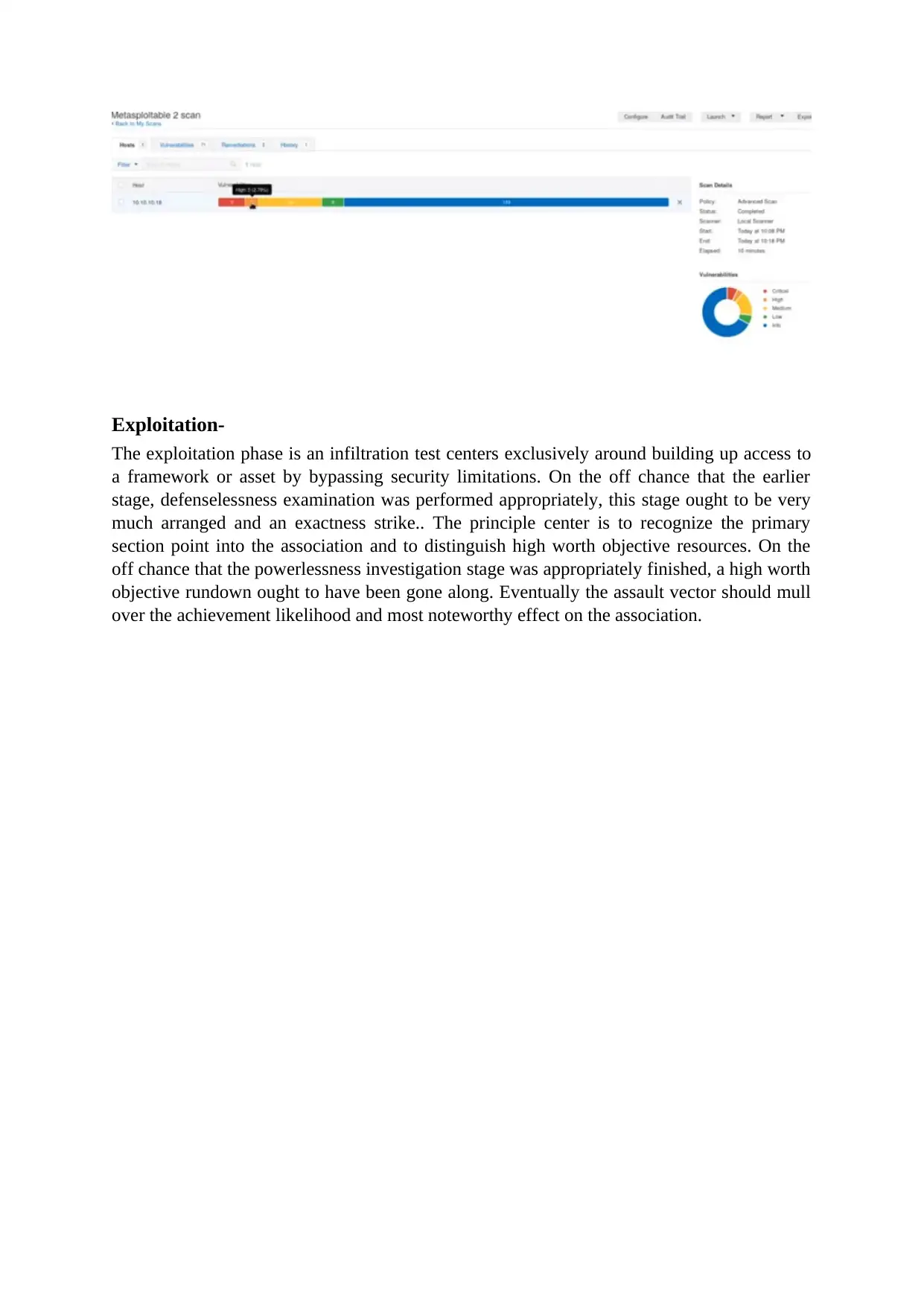
Exploitation-
The exploitation phase is an infiltration test centers exclusively around building up access to
a framework or asset by bypassing security limitations. On the off chance that the earlier
stage, defenselessness examination was performed appropriately, this stage ought to be very
much arranged and an exactness strike.. The principle center is to recognize the primary
section point into the association and to distinguish high worth objective resources. On the
off chance that the powerlessness investigation stage was appropriately finished, a high worth
objective rundown ought to have been gone along. Eventually the assault vector should mull
over the achievement likelihood and most noteworthy effect on the association.
The exploitation phase is an infiltration test centers exclusively around building up access to
a framework or asset by bypassing security limitations. On the off chance that the earlier
stage, defenselessness examination was performed appropriately, this stage ought to be very
much arranged and an exactness strike.. The principle center is to recognize the primary
section point into the association and to distinguish high worth objective resources. On the
off chance that the powerlessness investigation stage was appropriately finished, a high worth
objective rundown ought to have been gone along. Eventually the assault vector should mull
over the achievement likelihood and most noteworthy effect on the association.

Post exploitation-
This phase is being performed just after the exploitation of the target system. It is the most
important step of collecting the data by mitigating the exploits.
Reporting-
As the system is cracked we need to clear our presence from the system so that no one can
locate us or can track us. At the point when we attempt to gain admittance to framework
whether it is effective adventure or neglect to abuse, our exercises put away as log
information. A manager can without much of a stretch track programmer with the assistance
of put away information. That is the reason, it is most important to demolish our proof. In like
manner, I have made report on the base of my examination.
This phase is being performed just after the exploitation of the target system. It is the most
important step of collecting the data by mitigating the exploits.
Reporting-
As the system is cracked we need to clear our presence from the system so that no one can
locate us or can track us. At the point when we attempt to gain admittance to framework
whether it is effective adventure or neglect to abuse, our exercises put away as log
information. A manager can without much of a stretch track programmer with the assistance
of put away information. That is the reason, it is most important to demolish our proof. In like
manner, I have made report on the base of my examination.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
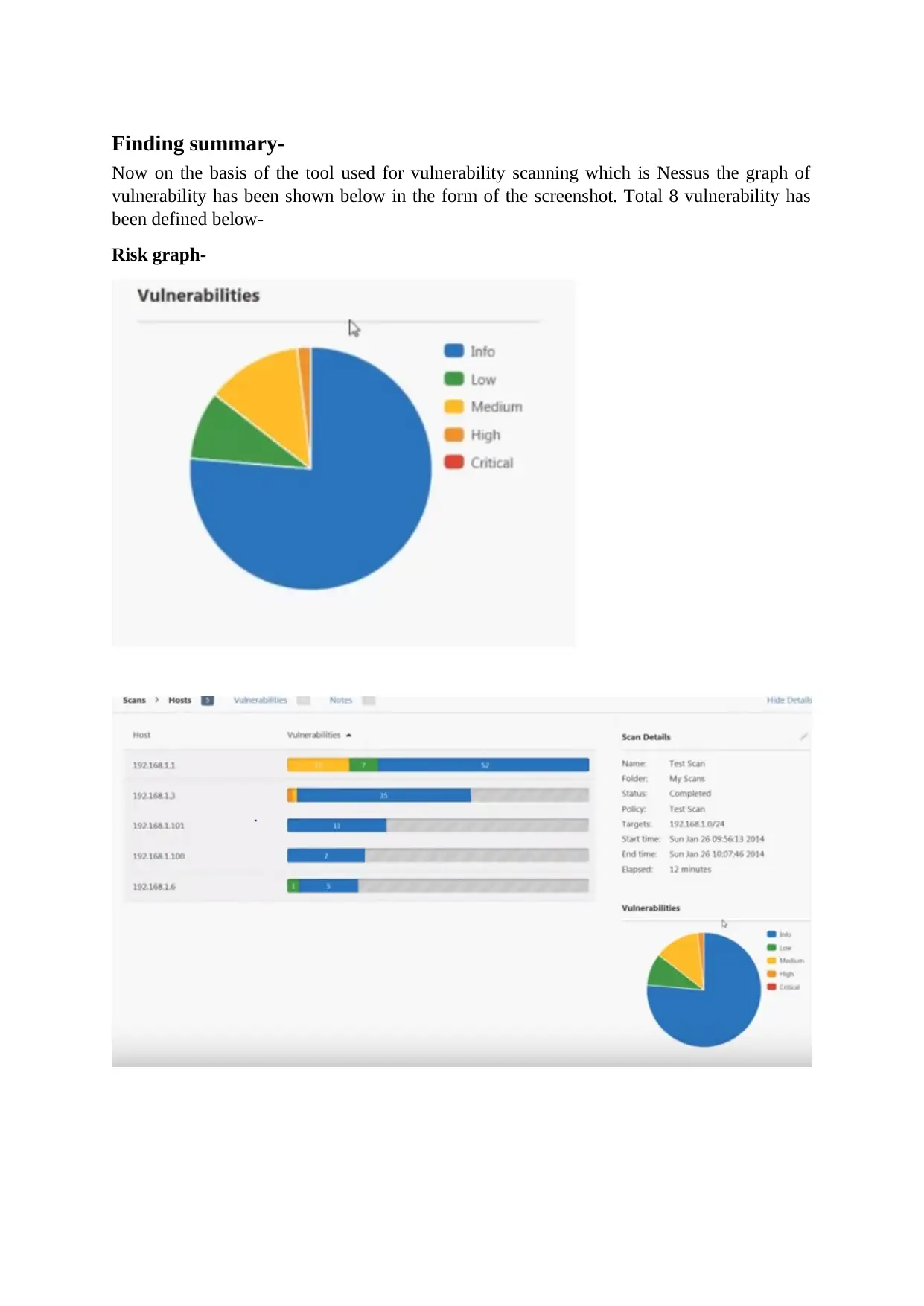
Finding summary-
Now on the basis of the tool used for vulnerability scanning which is Nessus the graph of
vulnerability has been shown below in the form of the screenshot. Total 8 vulnerability has
been defined below-
Risk graph-
Now on the basis of the tool used for vulnerability scanning which is Nessus the graph of
vulnerability has been shown below in the form of the screenshot. Total 8 vulnerability has
been defined below-
Risk graph-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
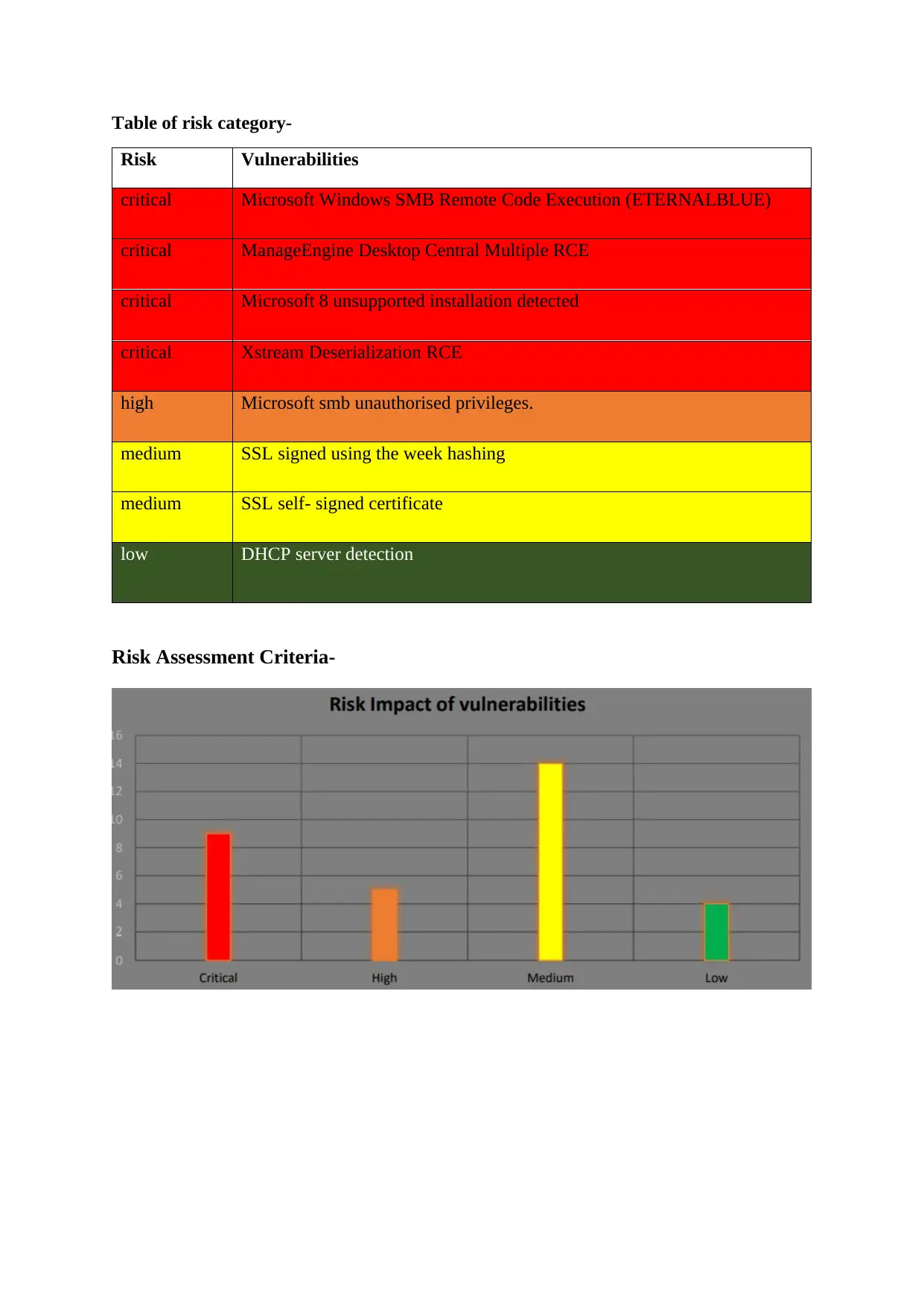
Table of risk category-
Risk Vulnerabilities
critical Microsoft Windows SMB Remote Code Execution (ETERNALBLUE)
critical ManageEngine Desktop Central Multiple RCE
critical Microsoft 8 unsupported installation detected
critical Xstream Deserialization RCE
high Microsoft smb unauthorised privileges.
medium SSL signed using the week hashing
medium SSL self- signed certificate
low DHCP server detection
Risk Assessment Criteria-
Risk Vulnerabilities
critical Microsoft Windows SMB Remote Code Execution (ETERNALBLUE)
critical ManageEngine Desktop Central Multiple RCE
critical Microsoft 8 unsupported installation detected
critical Xstream Deserialization RCE
high Microsoft smb unauthorised privileges.
medium SSL signed using the week hashing
medium SSL self- signed certificate
low DHCP server detection
Risk Assessment Criteria-
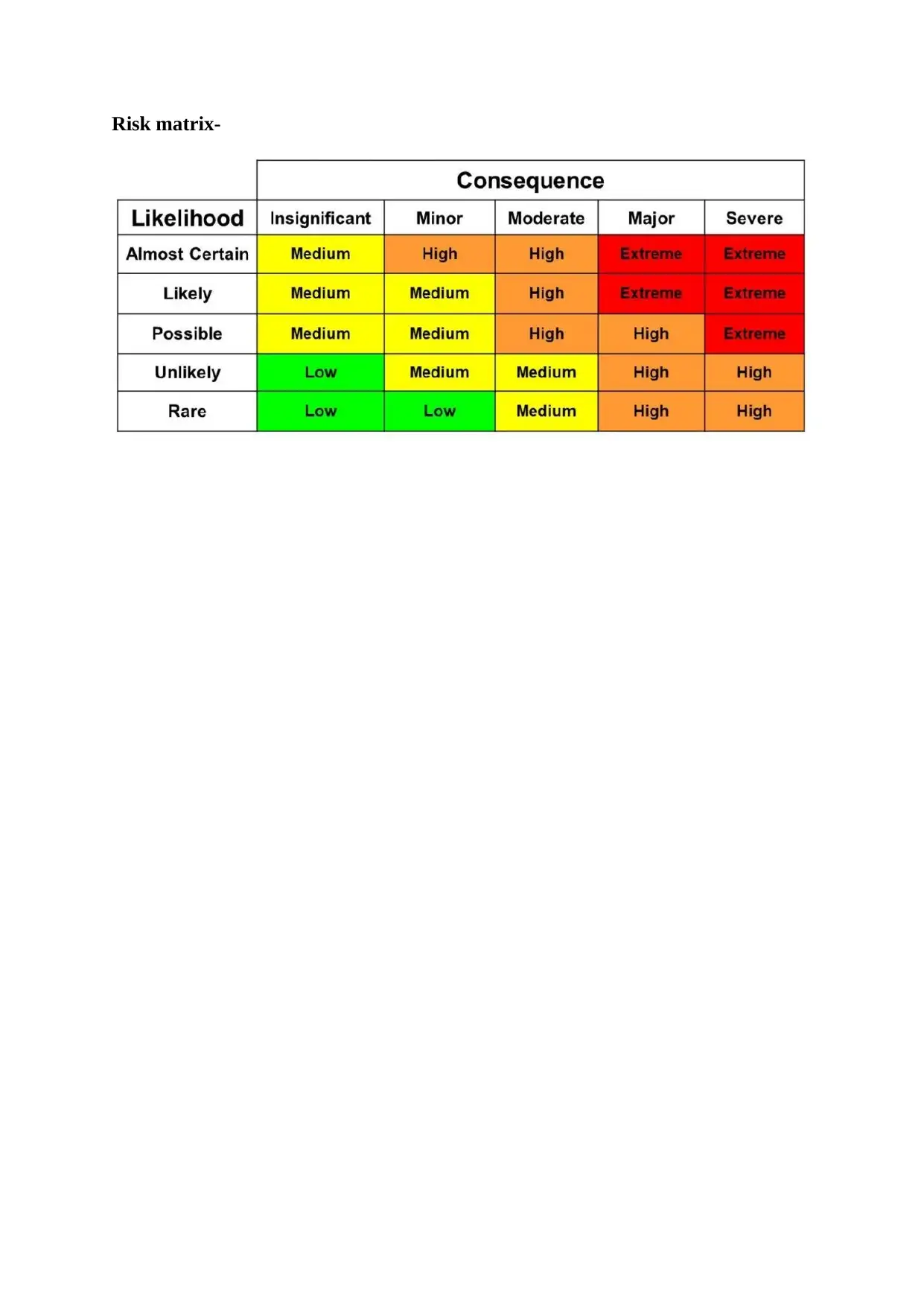
Risk matrix-
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



