Project Management Project: AI in Cybersecurity Systems
VerifiedAdded on 2022/11/16
|12
|2684
|317
Project
AI Summary
This project management project explores the application of Artificial Intelligence (AI) in cybersecurity. It begins with an introduction to the topic, followed by a discussion of the research problem, which centers on the increasing threats and vulnerabilities in cybersecurity. The research objectives aim to determine the issues organizations face, the applications of AI in cybersecurity, and how AI can resolve these problems. The research questions delve into these issues and applications. A comprehensive literature review covers AI's role in intrusion detection, expert systems, neural nets, intelligent agents, and other AI techniques, alongside the challenges of implementation. The methodology section outlines the research philosophy (positivism), approach (deductive), data collection method (secondary), and research design (explanatory). Ethical considerations are addressed, emphasizing honesty and data privacy. A timeline details the project's stages. The paper concludes by analyzing how AI can be used to detect and block unwanted spam and fraudulent emails.

Running head: PROJECT MANAGEMENT
Application of AI in cybersecurity system
Name of the Student
Name of the University
Author’s Note
Application of AI in cybersecurity system
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PROJECT MANAGEMENT
Table of Contents
1. Introduction..................................................................................................................................2
2. Research problem........................................................................................................................2
3. Research objective.......................................................................................................................3
4. Research questions.......................................................................................................................3
5. Literature review..........................................................................................................................3
6. Methodology................................................................................................................................6
7. Ethical considerations..................................................................................................................8
8. Timeline.......................................................................................................................................8
References......................................................................................................................................10
PROJECT MANAGEMENT
Table of Contents
1. Introduction..................................................................................................................................2
2. Research problem........................................................................................................................2
3. Research objective.......................................................................................................................3
4. Research questions.......................................................................................................................3
5. Literature review..........................................................................................................................3
6. Methodology................................................................................................................................6
7. Ethical considerations..................................................................................................................8
8. Timeline.......................................................................................................................................8
References......................................................................................................................................10

2
PROJECT MANAGEMENT
1. Introduction
The paper reflects on the application of AI in context to cyber security. According to
Gill (2019), the incorporation of the AI within the security system is mainly helpful in decreasing
the threats that are associated with cyber-security that is mainly faced by the global business. It is
found that across the industries applications which uses both AI as well as machine learning are
being used as data collection, storage capabilities as well as increment in computing power. In
real time, it is quite difficult to handle the data with the help of the humans. It is stated by
Yampolskiy and Spellchecker (2016) that with the help of AI, huge amount of data can generally
be reduced down such that the enterprise can easily determine the threat. Different types of
barrier against the digital weapons have indicated proper and quick expansion of malware as well
as different types of digital weapons.
2. Research problem
Cybersecurity is one of the vital concerns all over the world in today’s era. It is found that
as per the report of the CBS Money Watch, 80% of the businesses in US have been hacked quite
successfully such that the hackers are aware of the different types of vulnerabilities that the
organizations generally face. The problems or challenges that occurs due to the issues of
cybersecurity which further includes different types of unprecedented attacks, cyber espionage,
data theft, ransomware evolution and more. For successfully handling the issues of cyber-
security related issues, both the corporate as well as the government sectors are trying hard to
master AI in order to protect data for creating much more opportunities. With the advancement
within AI, most of the companies are generally started using as one of the important weapons
against the cyber-attacks.
PROJECT MANAGEMENT
1. Introduction
The paper reflects on the application of AI in context to cyber security. According to
Gill (2019), the incorporation of the AI within the security system is mainly helpful in decreasing
the threats that are associated with cyber-security that is mainly faced by the global business. It is
found that across the industries applications which uses both AI as well as machine learning are
being used as data collection, storage capabilities as well as increment in computing power. In
real time, it is quite difficult to handle the data with the help of the humans. It is stated by
Yampolskiy and Spellchecker (2016) that with the help of AI, huge amount of data can generally
be reduced down such that the enterprise can easily determine the threat. Different types of
barrier against the digital weapons have indicated proper and quick expansion of malware as well
as different types of digital weapons.
2. Research problem
Cybersecurity is one of the vital concerns all over the world in today’s era. It is found that
as per the report of the CBS Money Watch, 80% of the businesses in US have been hacked quite
successfully such that the hackers are aware of the different types of vulnerabilities that the
organizations generally face. The problems or challenges that occurs due to the issues of
cybersecurity which further includes different types of unprecedented attacks, cyber espionage,
data theft, ransomware evolution and more. For successfully handling the issues of cyber-
security related issues, both the corporate as well as the government sectors are trying hard to
master AI in order to protect data for creating much more opportunities. With the advancement
within AI, most of the companies are generally started using as one of the important weapons
against the cyber-attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PROJECT MANAGEMENT
3. Research objective
The research objectives are listed below:
To determine the issues that are faced by the organization due to cybersecurity
To determine the applications of AI in context to cybersecurity
To identify how AI is helpful in resolving the problem of cybersecurity
4. Research questions
The research questions are listed below:
What are the issues that are faced by the organization due to cybersecurity?
What are the applications of AI in cybersecurity system?
How AI is beneficial in resolving the problem of cybersecurity?
5. Literature review
According to Taddeo (2019), computer security as well as AI is generally considered as
the two different entities. It is found that in order to minimize the work of the human, the
researchers of AI are generally keen on creating appropriate programs while the different
security experts were attempting for fixing the problem of data leakage. Over the time, there are
two fields that are generally developed to be closer so that the attacks are generally focussed to
mimic the authentic execution at different human client level for successfully bringing down the
entire level of the system. It is opined by Anderson et al. (2017) that CAPTCHAs are generally
considered as one of the greatest combinations of AI as well as security. AI based strategies are
considered as an important way to intrusion location in order to make it very much conceivable
for reacting to various unidentified dangers. Moreover, it is found that AI based frameworks are
PROJECT MANAGEMENT
3. Research objective
The research objectives are listed below:
To determine the issues that are faced by the organization due to cybersecurity
To determine the applications of AI in context to cybersecurity
To identify how AI is helpful in resolving the problem of cybersecurity
4. Research questions
The research questions are listed below:
What are the issues that are faced by the organization due to cybersecurity?
What are the applications of AI in cybersecurity system?
How AI is beneficial in resolving the problem of cybersecurity?
5. Literature review
According to Taddeo (2019), computer security as well as AI is generally considered as
the two different entities. It is found that in order to minimize the work of the human, the
researchers of AI are generally keen on creating appropriate programs while the different
security experts were attempting for fixing the problem of data leakage. Over the time, there are
two fields that are generally developed to be closer so that the attacks are generally focussed to
mimic the authentic execution at different human client level for successfully bringing down the
entire level of the system. It is opined by Anderson et al. (2017) that CAPTCHAs are generally
considered as one of the greatest combinations of AI as well as security. AI based strategies are
considered as an important way to intrusion location in order to make it very much conceivable
for reacting to various unidentified dangers. Moreover, it is found that AI based frameworks are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PROJECT MANAGEMENT
generally planned in order to successfully learn as well as adjust in order to recognize the
changes within the settings.
It is opined by Patil (2016) that expert systems are generally considered as one of the
important AI tools. It is considered as one of the programs that is helpful in discovering various
types of answers to the different inquiries in different application area which are generally
discovered answers for the inquiries in some of the application area that are displayed by another
product. The expert system generally incorporates proper knowledge base where expert
information about a specific area is kept. The expert system-based shell is generally bolstered by
programs for making collaboration with the client. On the other hand, it is stated by Veiga (2018)
that neutral nets are one of the propelled branches of AI. Neutral nets can be able to master as
well as handle different types of interesting issues by successfully consolidating with different
other perceptron and they generally lean with the help entity. In addition to this, neutral nets are
helpful in empowering the recognition of different types of malware dangers which generally can
fill within the holes and generally can leave the entire organization that is mainly presented to
attacks.
According to Parkinson, Crampton and Hill (2018), intelligent agent is considered as one
of the entities that seems with the help of the sensors that generally follows proper domain that
generally utilizes information in order to properly accomplish the objectives. It is found that
intelligent mainly learn as well as utilize different types of information for accomplishing the
objectives. They generally adjust to learn time as well as new things with the help of proper
communication. It is mainly created against the distributed denial of service attacks. It is opined
by Anwar and Hassan (2017), search is one of the widespread strategies that is utilized for
appropriate critical thinking which can be connected in different situations when no strategies
PROJECT MANAGEMENT
generally planned in order to successfully learn as well as adjust in order to recognize the
changes within the settings.
It is opined by Patil (2016) that expert systems are generally considered as one of the
important AI tools. It is considered as one of the programs that is helpful in discovering various
types of answers to the different inquiries in different application area which are generally
discovered answers for the inquiries in some of the application area that are displayed by another
product. The expert system generally incorporates proper knowledge base where expert
information about a specific area is kept. The expert system-based shell is generally bolstered by
programs for making collaboration with the client. On the other hand, it is stated by Veiga (2018)
that neutral nets are one of the propelled branches of AI. Neutral nets can be able to master as
well as handle different types of interesting issues by successfully consolidating with different
other perceptron and they generally lean with the help entity. In addition to this, neutral nets are
helpful in empowering the recognition of different types of malware dangers which generally can
fill within the holes and generally can leave the entire organization that is mainly presented to
attacks.
According to Parkinson, Crampton and Hill (2018), intelligent agent is considered as one
of the entities that seems with the help of the sensors that generally follows proper domain that
generally utilizes information in order to properly accomplish the objectives. It is found that
intelligent mainly learn as well as utilize different types of information for accomplishing the
objectives. They generally adjust to learn time as well as new things with the help of proper
communication. It is mainly created against the distributed denial of service attacks. It is opined
by Anwar and Hassan (2017), search is one of the widespread strategies that is utilized for
appropriate critical thinking which can be connected in different situations when no strategies

5
PROJECT MANAGEMENT
related associated with critical thinking are considered proper. In addition to this, it is stated by
Madhok, Gupta and Grover (2016) that learning is enhancing an IS with the help of expansion
and revamping of knowledge base by successfully enhancing the interference related machine.
This is considered as one of the standouts among the different fascinating issues for
counterfeiting consciousness which is generally under proper examination. Moreover, constraint
solving is one of the important methods that are generally created within AI in order to properly
discover the various types of issues which are mainly introduced by providing an arrangement.
According to Srivastava, Bisht and Narayan (2017), it is identified that AI can be utilized
in a number of ways for cyber-security. In the coming future, there are a lot of various types of
frameworks which can be utilized in order to resolve the issues that are related with
cybersecurity. The various types of modern advancements within the information related
comprehension generally helps in outlining as well as dealing with machine learning in order to
improve the capacity of the digital security. It is stated by Handa, Sharma and Shukla (2019) that
Gmail utilizes AI in order to detect as well as block different types of unwanted spam as well as
fraudulent emails. In addition to this, MasterCard based decision intelligence are used that are
totally based on AI and are helpful in detecting AI which utilizes different types of algorithm that
is generally based or dependent on customer behaviour. Moreover, botnet detection is also one of
the fields that mainly rely on AI and helps in recognizing patterns as well as timings within the
network-based requests.
In addition to the advantages, there a lot of issues which can also be faced while applying
AI for resolving the issue of cybersecurity. According to Lou et al. (2018), while making proper
arrangement for the future research, it is found that advancement as well as utilization of
different types of AI strategies in CD are utilized in order to recognize the objectives for haul
PROJECT MANAGEMENT
related associated with critical thinking are considered proper. In addition to this, it is stated by
Madhok, Gupta and Grover (2016) that learning is enhancing an IS with the help of expansion
and revamping of knowledge base by successfully enhancing the interference related machine.
This is considered as one of the standouts among the different fascinating issues for
counterfeiting consciousness which is generally under proper examination. Moreover, constraint
solving is one of the important methods that are generally created within AI in order to properly
discover the various types of issues which are mainly introduced by providing an arrangement.
According to Srivastava, Bisht and Narayan (2017), it is identified that AI can be utilized
in a number of ways for cyber-security. In the coming future, there are a lot of various types of
frameworks which can be utilized in order to resolve the issues that are related with
cybersecurity. The various types of modern advancements within the information related
comprehension generally helps in outlining as well as dealing with machine learning in order to
improve the capacity of the digital security. It is stated by Handa, Sharma and Shukla (2019) that
Gmail utilizes AI in order to detect as well as block different types of unwanted spam as well as
fraudulent emails. In addition to this, MasterCard based decision intelligence are used that are
totally based on AI and are helpful in detecting AI which utilizes different types of algorithm that
is generally based or dependent on customer behaviour. Moreover, botnet detection is also one of
the fields that mainly rely on AI and helps in recognizing patterns as well as timings within the
network-based requests.
In addition to the advantages, there a lot of issues which can also be faced while applying
AI for resolving the issue of cybersecurity. According to Lou et al. (2018), while making proper
arrangement for the future research, it is found that advancement as well as utilization of
different types of AI strategies in CD are utilized in order to recognize the objectives for haul
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
PROJECT MANAGEMENT
different points of view. There are a number of strategies that are generally helpful in pertinent in
CD. In addition to this, it is found that AI is not enough sophisticated to replace the human
analyst and therefore there are a number of false positives s well as missed detection. AI is
considered as considered as one of the best tool that helps in reducing the time as well as
resource but they are no considered as a tool that are helpful in replacing the analyst.
6. Methodology
6.1 Research philosophy
It is identified that for conducting the entire research properly on the application of AI on
cybersecurity, the research utilizes positivism philosophy. This philosophy is mainly used as it is
helpful in effectively understanding the entire reality which is mainly related with the research
work. In addition to this, the entire study undertakes proper scientific analysis on the different
types of data that is collected for creating appropriate framework.
6.2 Research approach
Deductive approach is utilized by the researcher in this specific research as it mainly
implies on establishing effective data as well as theories that are generally helpful in filling the
gap for completing the entire research study quite effectively (Bresler and Stake 2017). In this
particular case, it is found that inductive approach is generally not used within the research study
in order to reflect the applications of AI within as this particular approach general reflects on the
scientific based framework that is mainly took place. The entire research questions help in
learning the much more dominant concept within the entire enterprise modelling that is based on
the research domain.
6.3 Data collection method
PROJECT MANAGEMENT
different points of view. There are a number of strategies that are generally helpful in pertinent in
CD. In addition to this, it is found that AI is not enough sophisticated to replace the human
analyst and therefore there are a number of false positives s well as missed detection. AI is
considered as considered as one of the best tool that helps in reducing the time as well as
resource but they are no considered as a tool that are helpful in replacing the analyst.
6. Methodology
6.1 Research philosophy
It is identified that for conducting the entire research properly on the application of AI on
cybersecurity, the research utilizes positivism philosophy. This philosophy is mainly used as it is
helpful in effectively understanding the entire reality which is mainly related with the research
work. In addition to this, the entire study undertakes proper scientific analysis on the different
types of data that is collected for creating appropriate framework.
6.2 Research approach
Deductive approach is utilized by the researcher in this specific research as it mainly
implies on establishing effective data as well as theories that are generally helpful in filling the
gap for completing the entire research study quite effectively (Bresler and Stake 2017). In this
particular case, it is found that inductive approach is generally not used within the research study
in order to reflect the applications of AI within as this particular approach general reflects on the
scientific based framework that is mainly took place. The entire research questions help in
learning the much more dominant concept within the entire enterprise modelling that is based on
the research domain.
6.3 Data collection method
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
PROJECT MANAGEMENT
There are two different types of data collection method which are secondary as well as
primary data collection method. The collection of primary data is generally done with the help of
the survey as well as proper questionnaire method whereas the secondary data collection is done
by reviewing different types of papers as well as literatures. In this particular research, secondary
data collection method is mainly utilized in order to analyze the different applications of AI in
context to cyber-security (Fletcher 2017). It is found that different type of literatures as well as
research papers are generally reviewed in order to find out the proper applications of AI within
the cybersecurity system.
6.4 Research design
The most significant factor within a research method is that is that it is very much
structured as well as sequential that generally helps the researchers in carrying out the entire
research quite successfully. It is mainly considered as one of the important blueprints that help in
elaborating the specific plan on which the entire research is undertaken that is mainly based on
effective data analysis. In this particular research, it is found that explanatory design is mainly
used so that the researchers can be capable of understanding the entire research quite
successfully (McCusker and Gunaydin 2015). In addition to this, with the use of this specific
research, the researchers will be very much capable of understanding the gaps as well as
limitations. After getting information about the research, the researchers can be capable of
improving the research methods for properly achieving the goals of the research quite
successfully.
PROJECT MANAGEMENT
There are two different types of data collection method which are secondary as well as
primary data collection method. The collection of primary data is generally done with the help of
the survey as well as proper questionnaire method whereas the secondary data collection is done
by reviewing different types of papers as well as literatures. In this particular research, secondary
data collection method is mainly utilized in order to analyze the different applications of AI in
context to cyber-security (Fletcher 2017). It is found that different type of literatures as well as
research papers are generally reviewed in order to find out the proper applications of AI within
the cybersecurity system.
6.4 Research design
The most significant factor within a research method is that is that it is very much
structured as well as sequential that generally helps the researchers in carrying out the entire
research quite successfully. It is mainly considered as one of the important blueprints that help in
elaborating the specific plan on which the entire research is undertaken that is mainly based on
effective data analysis. In this particular research, it is found that explanatory design is mainly
used so that the researchers can be capable of understanding the entire research quite
successfully (McCusker and Gunaydin 2015). In addition to this, with the use of this specific
research, the researchers will be very much capable of understanding the gaps as well as
limitations. After getting information about the research, the researchers can be capable of
improving the research methods for properly achieving the goals of the research quite
successfully.
8
PROJECT MANAGEMENT
7. Ethical considerations
The entire research is generally conducted as per the guidelines of the research. It is
found that the entire research is generally submitted within time and the data which are collected
are helpful in conducting the entire research that is very much accurate as well as based on the
knowledge of the researcher. The data which are collected for this paper are not disclosed and
the people who are associated with the research are not forced to share the data. Moreover, the
entire research is mainly completed with honesty so that accurate outcome or findings can be
achieved after undertaking the analysis.
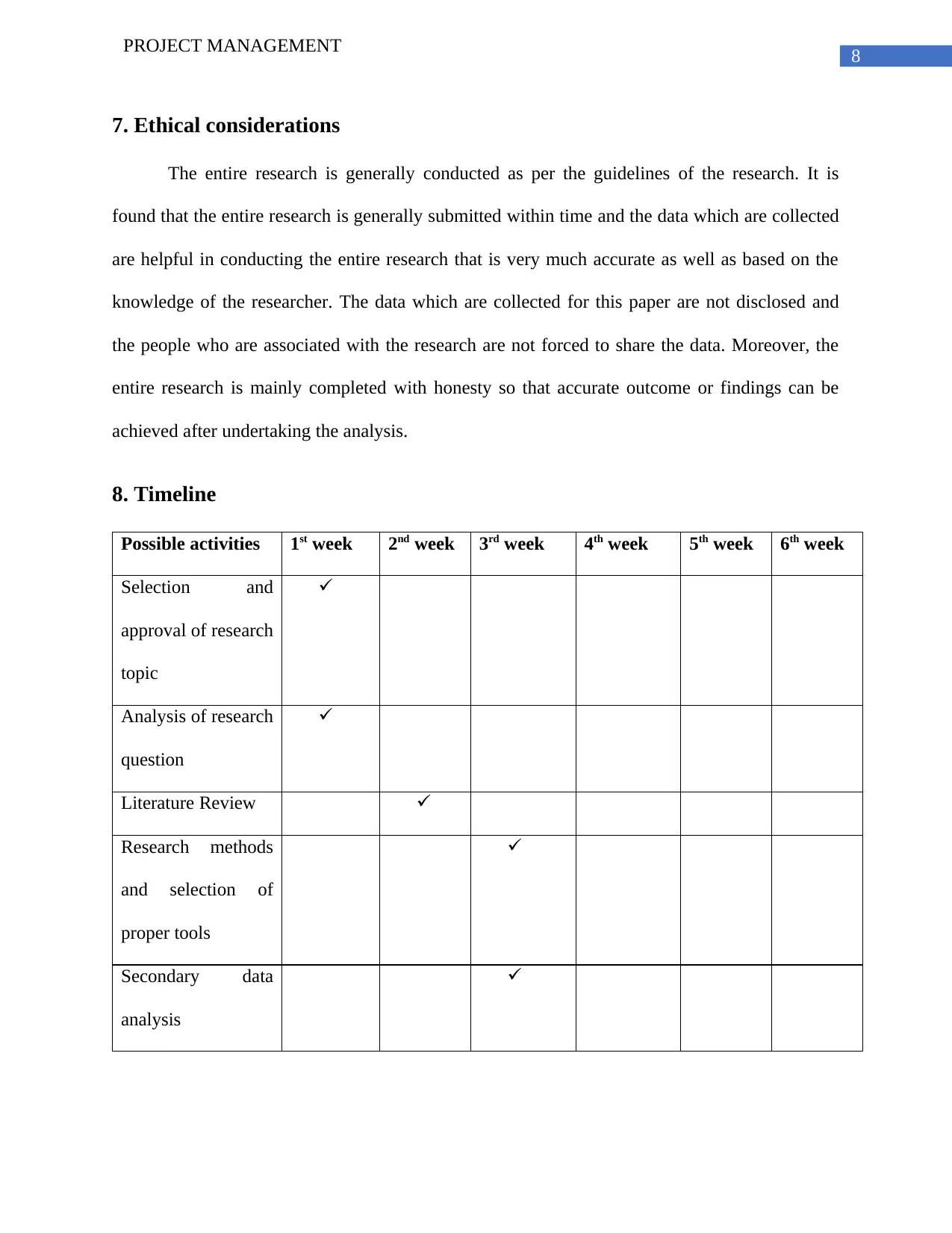
8. Timeline
Possible activities 1st week 2nd week 3rd week 4th week 5th week 6th week
Selection and
approval of research
topic
Analysis of research
question
Literature Review
Research methods
and selection of
proper tools
Secondary data
analysis
PROJECT MANAGEMENT
7. Ethical considerations
The entire research is generally conducted as per the guidelines of the research. It is
found that the entire research is generally submitted within time and the data which are collected
are helpful in conducting the entire research that is very much accurate as well as based on the
knowledge of the researcher. The data which are collected for this paper are not disclosed and
the people who are associated with the research are not forced to share the data. Moreover, the
entire research is mainly completed with honesty so that accurate outcome or findings can be
achieved after undertaking the analysis.
8. Timeline
Possible activities 1st week 2nd week 3rd week 4th week 5th week 6th week
Selection and
approval of research
topic
Analysis of research
question
Literature Review
Research methods
and selection of
proper tools
Secondary data
analysis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
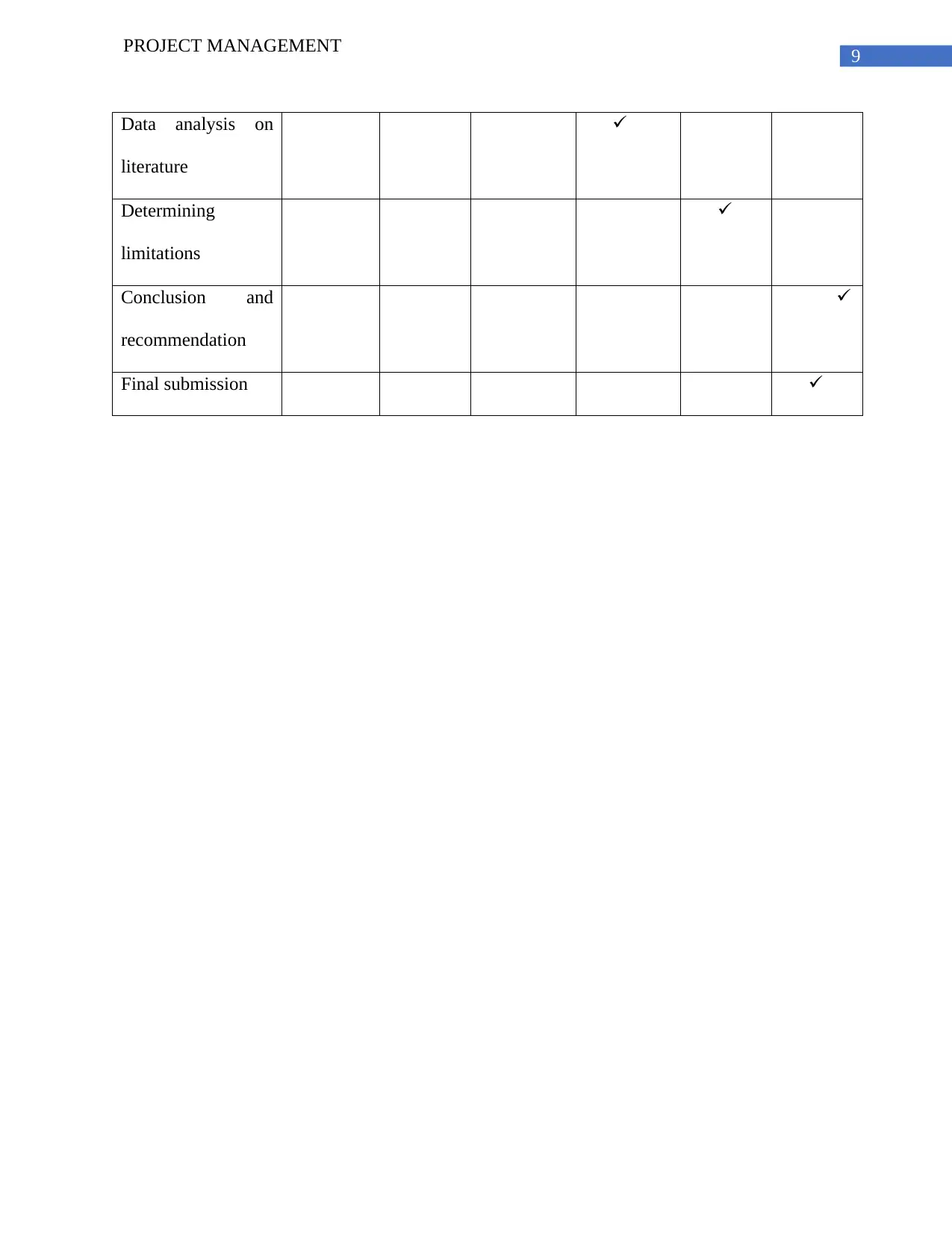
PROJECT MANAGEMENT
Data analysis on
literature
Determining
limitations
Conclusion and
recommendation
Final submission
PROJECT MANAGEMENT
Data analysis on
literature
Determining
limitations
Conclusion and
recommendation
Final submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
PROJECT MANAGEMENT
References
Anderson, M., Barták, R., Brownstein, J.S., Buckeridge, D.L., Eldardiry, H., Geib, C., Gini, M.,
Isaksen, A., Keren, S., Laddaga, R. and Lisy, V., 2017. Reports of the workshops of the thirty-
first AAAI conference on artificial intelligence. AI Magazine, 38(3), pp.72-82.
Anwar, A. and Hassan, S.I., 2017. Applying Artificial Intelligence Techniques to Prevent Cyber
Assaults. International Journal of Computational Intelligence Research, 13(5), pp.883-889.
Bresler, L. and Stake, R.E., 2017. Qualitative research methodology in music education.
In Critical Essays in Music Education (pp. 113-128). Routledge.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Gill, A.S., 2019. Artificial Intelligence and International Security: The Long View. Ethics &
International Affairs, 33(2), pp.169-179.
Handa, A., Sharma, A. and Shukla, S.K., 2019. Machine learning in cybersecurity: A
review. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 9(4), p.e1306.
Kumar, R., 2019. Research methodology: A step-by-step guide for beginners. Sage Publications
Limited.
Lou, X., Waedt, K., Gao, Y., Zid, I.B. and Watson, V., 2018, June. Combining Artificial
Intelligence planning advantages to assist preliminary formal analysis on Industrial Control
System cybersecurity vulnerabilities. In 2018 10th International Conference on Electronics,
Computers and Artificial Intelligence (ECAI) (pp. 1-8). IEEE.
PROJECT MANAGEMENT
References
Anderson, M., Barták, R., Brownstein, J.S., Buckeridge, D.L., Eldardiry, H., Geib, C., Gini, M.,
Isaksen, A., Keren, S., Laddaga, R. and Lisy, V., 2017. Reports of the workshops of the thirty-
first AAAI conference on artificial intelligence. AI Magazine, 38(3), pp.72-82.
Anwar, A. and Hassan, S.I., 2017. Applying Artificial Intelligence Techniques to Prevent Cyber
Assaults. International Journal of Computational Intelligence Research, 13(5), pp.883-889.
Bresler, L. and Stake, R.E., 2017. Qualitative research methodology in music education.
In Critical Essays in Music Education (pp. 113-128). Routledge.
Fletcher, A.J., 2017. Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Gill, A.S., 2019. Artificial Intelligence and International Security: The Long View. Ethics &
International Affairs, 33(2), pp.169-179.
Handa, A., Sharma, A. and Shukla, S.K., 2019. Machine learning in cybersecurity: A
review. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery, 9(4), p.e1306.
Kumar, R., 2019. Research methodology: A step-by-step guide for beginners. Sage Publications
Limited.
Lou, X., Waedt, K., Gao, Y., Zid, I.B. and Watson, V., 2018, June. Combining Artificial
Intelligence planning advantages to assist preliminary formal analysis on Industrial Control
System cybersecurity vulnerabilities. In 2018 10th International Conference on Electronics,
Computers and Artificial Intelligence (ECAI) (pp. 1-8). IEEE.

11
PROJECT MANAGEMENT
Madhok, E., Gupta, A. and Grover, N., 2016. Artificial Intelligence Impact on Cyber
Security. IITM Journal of Management and IT, 7(1), pp.100-107
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion, 30(7), pp.537-542.
Parkinson, S., Crampton, A. and Hill, R. eds., 2018. Guide to Vulnerability Analysis for
Computer Networks and Systems: An Artificial Intelligence Approach. Springer.
Patil, P., 2016. Artificial intelligence in cybersecurity. International Journal of Research in
Computer Applications and Robotics, 4(5), pp.1-5.
Srivastava, S., Bisht, A. and Narayan, N., 2017, January. Safety and security in smart cities using
artificial intelligence—A review. In 2017 7th International Conference on Cloud Computing,
Data Science & Engineering-Confluence (pp. 130-133). IEEE.
Taddeo, M., 2019. Three Ethical Challenges of Applications of Artificial Intelligence in
Cybersecurity. Minds and Machines, pp.1-5.
Veiga, A.P., 2018. Applications of artificial intelligence to network security. arXiv preprint
arXiv:1803.09992.
Yampolskiy, R.V. and Spellchecker, M.S., 2016. Artificial intelligence safety and cybersecurity:
A timeline of AI failures. arXiv preprint arXiv:1610.07997.
PROJECT MANAGEMENT
Madhok, E., Gupta, A. and Grover, N., 2016. Artificial Intelligence Impact on Cyber
Security. IITM Journal of Management and IT, 7(1), pp.100-107
McCusker, K. and Gunaydin, S., 2015. Research using qualitative, quantitative or mixed
methods and choice based on the research. Perfusion, 30(7), pp.537-542.
Parkinson, S., Crampton, A. and Hill, R. eds., 2018. Guide to Vulnerability Analysis for
Computer Networks and Systems: An Artificial Intelligence Approach. Springer.
Patil, P., 2016. Artificial intelligence in cybersecurity. International Journal of Research in
Computer Applications and Robotics, 4(5), pp.1-5.
Srivastava, S., Bisht, A. and Narayan, N., 2017, January. Safety and security in smart cities using
artificial intelligence—A review. In 2017 7th International Conference on Cloud Computing,
Data Science & Engineering-Confluence (pp. 130-133). IEEE.
Taddeo, M., 2019. Three Ethical Challenges of Applications of Artificial Intelligence in
Cybersecurity. Minds and Machines, pp.1-5.
Veiga, A.P., 2018. Applications of artificial intelligence to network security. arXiv preprint
arXiv:1803.09992.
Yampolskiy, R.V. and Spellchecker, M.S., 2016. Artificial intelligence safety and cybersecurity:
A timeline of AI failures. arXiv preprint arXiv:1610.07997.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





