Project Plan Report: IT System Development for Government Agency
VerifiedAdded on 2021/06/17
|12
|3630
|469
Project
AI Summary
This project plan report outlines the development and implementation of a new IT system for a government agency, focusing on leveraging mobile and Internet of Things (IoT) technologies to enhance incident handling capabilities. The project aims to replace an older system with a modern solution that incorporates AI, cloud computing, and advanced sensor technology to improve cyberattack detection and overall system reliability. The report details various aspects of the project, including the project scope, background, deliverables, human resource requirements, budget, acceptance criteria, expected benefits, and a benefits realization plan. The new system is designed to integrate with existing infrastructure, support mobile devices, incorporate social media data, and offer automated breach detection. Key components include a scope statement, critical success factors, deliverables, and a work breakdown structure. The project's success hinges on overcoming constraints related to time, resources, and personnel, with the ultimate goal of delivering a state-of-the-art sensor system that provides real-time communication, processing, and response capabilities, thus improving the agency's ability to manage and respond to cyber threats.

Project Plan Report 1
Project Plan Report
Name
Institution
Project Plan Report
Name
Institution
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Plan Report 2
Contents
Scope for Project....................................................................................................................................................... 2
Project Description.............................................................................................................................................. 3
Project Background............................................................................................................................................. 3
Project Deliverables............................................................................................................................................ 4
Human resource requirements.................................................................................................................... 4
Project Budget...................................................................................................................................................... 5
Project acceptance criteria................................................................................................................................ 5
Project Constraints.............................................................................................................................................. 6
Expected Benefits................................................................................................................................................... 6
Benefits Realisation Plan..................................................................................................................................... 7
Components of the project.................................................................................................................................. 7
Scope Statement................................................................................................................................................. 7
Critical Success Factors................................................................................................................................... 7
Deliverables......................................................................................................................................................... 8
Work Breakdown Structure.......................................................................................................................... 8
Project management process model............................................................................................................... 9
References............................................................................................................................................................... 10
Contents
Scope for Project....................................................................................................................................................... 2
Project Description.............................................................................................................................................. 3
Project Background............................................................................................................................................. 3
Project Deliverables............................................................................................................................................ 4
Human resource requirements.................................................................................................................... 4
Project Budget...................................................................................................................................................... 5
Project acceptance criteria................................................................................................................................ 5
Project Constraints.............................................................................................................................................. 6
Expected Benefits................................................................................................................................................... 6
Benefits Realisation Plan..................................................................................................................................... 7
Components of the project.................................................................................................................................. 7
Scope Statement................................................................................................................................................. 7
Critical Success Factors................................................................................................................................... 7
Deliverables......................................................................................................................................................... 8
Work Breakdown Structure.......................................................................................................................... 8
Project management process model............................................................................................................... 9
References............................................................................................................................................................... 10

Project Plan Report 3
Scope for Project
This project involves an IT team from a government agency led by Daisy and a consulting company, MQ
IT Solutions. It is aimed at replacing the old system which entails telephone or internet-based system
management of the government agency with a new system. The system developed in this project is
expected to focus on implementing the use of mobile and Internet of Things technology to enhance the
response capabilities of the organization in times of incidence handling. With the growing
implementation of Information Technology systems in organizations, we cannot overlook the other side
of the coin. There is an increased risk of exposure of organization’s details especially through
cyberattacks. In as much as we are using the internet to boost day to day business operations, people and
organizations must be protected.
In a big government agency such as Daisy’s, the absence of a proper system to deal with and respond to
cyber incidents, threats and attacks is a genuine problem (Coombs, 2015). But with the solution that
MQ IT Solutions is offering, there is no need to panic. The traditional system which utilizes telephone and
internet-based incident management is good but not just good enough for the emerging technologies.
However, the solution that MQ IT Solutions is offering is quite to the task. An incident management
system that focuses on making use of mobile and Internet of Things technology to enhance the response
capabilities of the organization in times of incidence handling.
The new incidence management system will come with a couple of advantages. For example, the mobile
system for managing incidences could obtain updates on information from the incident or attack alert
system of the nation, and then hand over the information to people to help (Gollenia, 2016). It could
also obtain information from the common online media platforms such as Facebook and twitter to get the
hot topics, predict an alert event and then use push messages to alert individual mobiles. We do not take
for granted recovery procedures from disasters. The new system will offer rehearsal of efficient attack
recovery procedures after disasters.
The current system works on guess works. The sensor sense normal human movement and touch and then
the alarm and alert system goes. The problem is the reliability. In most cases, it is a stranger wondering
around who is sensed and makes the alarm to go. The owner of the business premises as well as an alarm
response team then gets alerted and responds immediately only to realize that it was a stranger wondering
around. Now, if two to three false alarms go before a real alarm goes, there is a possibility that when the
real alarm goes the owner of business of the alarm response team may have grown weary and following
the false alarms and fail to respond accordingly. This may lead to theft and destruction of property which
Scope for Project
This project involves an IT team from a government agency led by Daisy and a consulting company, MQ
IT Solutions. It is aimed at replacing the old system which entails telephone or internet-based system
management of the government agency with a new system. The system developed in this project is
expected to focus on implementing the use of mobile and Internet of Things technology to enhance the
response capabilities of the organization in times of incidence handling. With the growing
implementation of Information Technology systems in organizations, we cannot overlook the other side
of the coin. There is an increased risk of exposure of organization’s details especially through
cyberattacks. In as much as we are using the internet to boost day to day business operations, people and
organizations must be protected.
In a big government agency such as Daisy’s, the absence of a proper system to deal with and respond to
cyber incidents, threats and attacks is a genuine problem (Coombs, 2015). But with the solution that
MQ IT Solutions is offering, there is no need to panic. The traditional system which utilizes telephone and
internet-based incident management is good but not just good enough for the emerging technologies.
However, the solution that MQ IT Solutions is offering is quite to the task. An incident management
system that focuses on making use of mobile and Internet of Things technology to enhance the response
capabilities of the organization in times of incidence handling.
The new incidence management system will come with a couple of advantages. For example, the mobile
system for managing incidences could obtain updates on information from the incident or attack alert
system of the nation, and then hand over the information to people to help (Gollenia, 2016). It could
also obtain information from the common online media platforms such as Facebook and twitter to get the
hot topics, predict an alert event and then use push messages to alert individual mobiles. We do not take
for granted recovery procedures from disasters. The new system will offer rehearsal of efficient attack
recovery procedures after disasters.
The current system works on guess works. The sensor sense normal human movement and touch and then
the alarm and alert system goes. The problem is the reliability. In most cases, it is a stranger wondering
around who is sensed and makes the alarm to go. The owner of the business premises as well as an alarm
response team then gets alerted and responds immediately only to realize that it was a stranger wondering
around. Now, if two to three false alarms go before a real alarm goes, there is a possibility that when the
real alarm goes the owner of business of the alarm response team may have grown weary and following
the false alarms and fail to respond accordingly. This may lead to theft and destruction of property which
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project Plan Report 4
the sensors were installed to protect thus making the system ineffective. There is thus a great need for
improvement and this is exactly what MQ IT Solutions is bringing on board.
Project Description
MQ IT Solutions will develop, customize and implement a new system, which focuses on making use of
mobile and Internet of Things technology to enhance the response capabilities of the organization when it
comes to incidence handling. This customer organization is a government agency that deals with sensors
and is located within the central business district. There project team will comprise of a projects
implementation team from MQ IT Solutions and some individual from Daisy’s government agency who
will assist greatly in carrying out user acceptance testing (UAT’s). Previously, some members from both
teams during the first site visit examined and took some samples of the current sensors produced by the
system. There will be a second site visit to the government agency to assess and analyse the current
system so as to develop a system that will be easily integrated with current systems and also find wide
user acceptance.
Project Background
The government agency develops different types of sensors that are used for home security systems,
detecting cyberattacks as well as work place safety sensors. The two types of sensors work by either
detecting motion to provide burglar proof in both residential homes and business organizations or
detecting safety threat like smoke in a work place. For detecting cyberattacks, there is a big challenge to
cop up with current technology. There is a need to have automated that works in real-time. It should apply
machine learning techniques and real-time processing to analyse big data and look for threats at any point
of the organizations network (Gollenia, 2016). For burglary, there are two motion detector sensors
which are active motion sensors and passive motion sensors. The former work by sending out ultrasonic
waves. They send out ultrasonic waves that reflect back to the sensor. In the case of an intruder, the
ultrasonic waves will not reflect back to the sensor. This triggers the sensor to send a signal which can
sound an alarm. Passive motion sensors are mainly used in residential homes. They are given off by
humans and animals in the form of heat. Small fluctuations in temperatures are not detected by the sensor
to exclude natural causes like the sun.
Project Deliverables
MQ IT Solutions plans on delivering a system that is up to the current technology with the following
features;
the sensors were installed to protect thus making the system ineffective. There is thus a great need for
improvement and this is exactly what MQ IT Solutions is bringing on board.
Project Description
MQ IT Solutions will develop, customize and implement a new system, which focuses on making use of
mobile and Internet of Things technology to enhance the response capabilities of the organization when it
comes to incidence handling. This customer organization is a government agency that deals with sensors
and is located within the central business district. There project team will comprise of a projects
implementation team from MQ IT Solutions and some individual from Daisy’s government agency who
will assist greatly in carrying out user acceptance testing (UAT’s). Previously, some members from both
teams during the first site visit examined and took some samples of the current sensors produced by the
system. There will be a second site visit to the government agency to assess and analyse the current
system so as to develop a system that will be easily integrated with current systems and also find wide
user acceptance.
Project Background
The government agency develops different types of sensors that are used for home security systems,
detecting cyberattacks as well as work place safety sensors. The two types of sensors work by either
detecting motion to provide burglar proof in both residential homes and business organizations or
detecting safety threat like smoke in a work place. For detecting cyberattacks, there is a big challenge to
cop up with current technology. There is a need to have automated that works in real-time. It should apply
machine learning techniques and real-time processing to analyse big data and look for threats at any point
of the organizations network (Gollenia, 2016). For burglary, there are two motion detector sensors
which are active motion sensors and passive motion sensors. The former work by sending out ultrasonic
waves. They send out ultrasonic waves that reflect back to the sensor. In the case of an intruder, the
ultrasonic waves will not reflect back to the sensor. This triggers the sensor to send a signal which can
sound an alarm. Passive motion sensors are mainly used in residential homes. They are given off by
humans and animals in the form of heat. Small fluctuations in temperatures are not detected by the sensor
to exclude natural causes like the sun.
Project Deliverables
MQ IT Solutions plans on delivering a system that is up to the current technology with the following
features;
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Plan Report 5
Supports storage in the cloud,
Able to support most wired, wireless and mobile devices,
Able to support push messages functionality
Software that is open Source,
Incorporate information from social media such as Facebook and Twitter;
Must easily integrate with current systems.
Human resource requirements
For this project to be successful there is a need for human resources working together in a team and
efficiently. Some team members will come from MQ IT Solutions and mainly the experts in various areas
of the development of the system (Turner, 2016). They include;
Project director,
Software expert,
Marketing guru,
Accountant ,
Six administrative support staff who need not be present all the time and
Project management expert (Myself).
From the government agency side we need individuals we are quick to learn and understand the current
process so that they provide the information required by the consultant for easy integration. The team will
also be trained well enough about the new system in order to be able to support the new system when it is
finally delivered to the government agency and commissioned (Coombs, 2015). They may include but
are not limited to the following;
Communications person,
Administrative staff,
Technicians who work with the current system,
Representative from senior management preferable ICT manager and projects manager,
ICT representatives and
Project lead (Daisy).
Supports storage in the cloud,
Able to support most wired, wireless and mobile devices,
Able to support push messages functionality
Software that is open Source,
Incorporate information from social media such as Facebook and Twitter;
Must easily integrate with current systems.
Human resource requirements
For this project to be successful there is a need for human resources working together in a team and
efficiently. Some team members will come from MQ IT Solutions and mainly the experts in various areas
of the development of the system (Turner, 2016). They include;
Project director,
Software expert,
Marketing guru,
Accountant ,
Six administrative support staff who need not be present all the time and
Project management expert (Myself).
From the government agency side we need individuals we are quick to learn and understand the current
process so that they provide the information required by the consultant for easy integration. The team will
also be trained well enough about the new system in order to be able to support the new system when it is
finally delivered to the government agency and commissioned (Coombs, 2015). They may include but
are not limited to the following;
Communications person,
Administrative staff,
Technicians who work with the current system,
Representative from senior management preferable ICT manager and projects manager,
ICT representatives and
Project lead (Daisy).
Project Plan Report 6
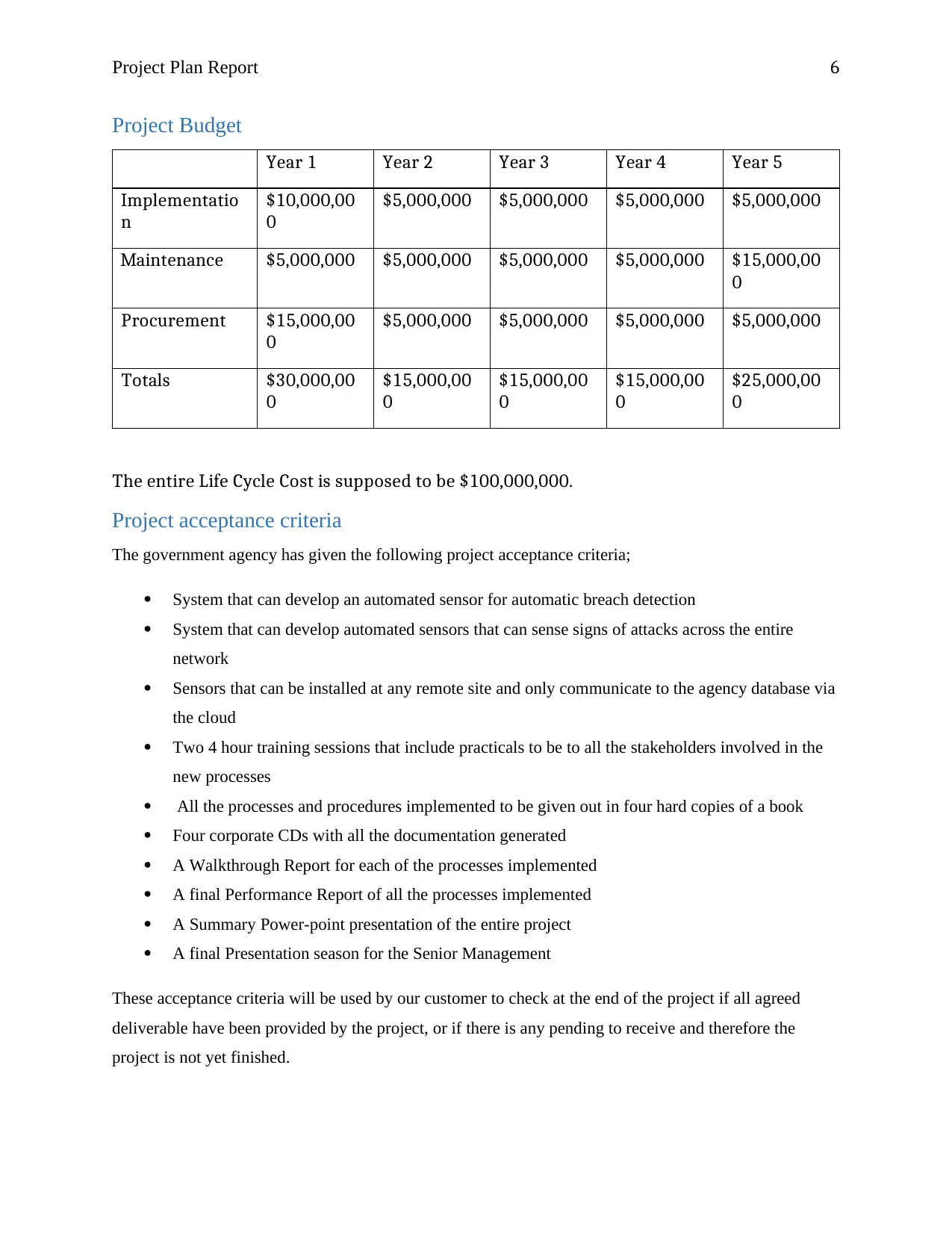
Project Budget
Year 1 Year 2 Year 3 Year 4 Year 5
Implementatio
n
$10,000,00
0
$5,000,000 $5,000,000 $5,000,000 $5,000,000
Maintenance $5,000,000 $5,000,000 $5,000,000 $5,000,000 $15,000,00
0
Procurement $15,000,00
0
$5,000,000 $5,000,000 $5,000,000 $5,000,000
Totals $30,000,00
0
$15,000,00
0
$15,000,00
0
$15,000,00
0
$25,000,00
0
The entire Life Cycle Cost is supposed to be $100,000,000.
Project acceptance criteria
The government agency has given the following project acceptance criteria;
System that can develop an automated sensor for automatic breach detection
System that can develop automated sensors that can sense signs of attacks across the entire
network
Sensors that can be installed at any remote site and only communicate to the agency database via
the cloud
Two 4 hour training sessions that include practicals to be to all the stakeholders involved in the
new processes
All the processes and procedures implemented to be given out in four hard copies of a book
Four corporate CDs with all the documentation generated
A Walkthrough Report for each of the processes implemented
A final Performance Report of all the processes implemented
A Summary Power-point presentation of the entire project
A final Presentation season for the Senior Management
These acceptance criteria will be used by our customer to check at the end of the project if all agreed
deliverable have been provided by the project, or if there is any pending to receive and therefore the
project is not yet finished.
Project Budget
Year 1 Year 2 Year 3 Year 4 Year 5
Implementatio
n
$10,000,00
0
$5,000,000 $5,000,000 $5,000,000 $5,000,000
Maintenance $5,000,000 $5,000,000 $5,000,000 $5,000,000 $15,000,00
0
Procurement $15,000,00
0
$5,000,000 $5,000,000 $5,000,000 $5,000,000
Totals $30,000,00
0
$15,000,00
0
$15,000,00
0
$15,000,00
0
$25,000,00
0
The entire Life Cycle Cost is supposed to be $100,000,000.
Project acceptance criteria
The government agency has given the following project acceptance criteria;
System that can develop an automated sensor for automatic breach detection
System that can develop automated sensors that can sense signs of attacks across the entire
network
Sensors that can be installed at any remote site and only communicate to the agency database via
the cloud
Two 4 hour training sessions that include practicals to be to all the stakeholders involved in the
new processes
All the processes and procedures implemented to be given out in four hard copies of a book
Four corporate CDs with all the documentation generated
A Walkthrough Report for each of the processes implemented
A final Performance Report of all the processes implemented
A Summary Power-point presentation of the entire project
A final Presentation season for the Senior Management
These acceptance criteria will be used by our customer to check at the end of the project if all agreed
deliverable have been provided by the project, or if there is any pending to receive and therefore the
project is not yet finished.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Plan Report 7
Project Constraints
Time frames: You cannot be so certain about time frames when it comes to IT projects but our
team will do the best to beat deadlines
Resources: The type, amount, and availability of resources to perform the project work are not
sufficient.
Personnel limitations: The personnel provided by both parties are not sufficient and hence the
need to work overtime to beat deadlines
Qualified employees to work with the new system
Expected Benefits
One major benefit from this project is a state of the art technology for developing sensors. We are looking
forward to sensors that need little human intervention as they can be accessed remotely through cloud
computing. These is a system that learns from past experience using the concept of machine learning from
its harvested data, big data. It thus incorporates artificial intelligence and is a more reliable system in
terms of accuracy when it comes to detecting cyberattacks and also other kinds of attacks. This system
will help develop sensors that have not been developed in the country before nor experienced by most of
the citizens.
Even better the new sensors from the system will open up new areas that are currently worrying due to
cyberattacks. As technology continues to permeate our lives, we move from operating technology to
integrating with it. This is especially true of autonomous systems that are by definition designed to blend
in with our society, becoming second nature. Take for example driverless cars and transport which have
taken all the limelight as far as autonomous systems are concerned. Though no cyberattacks have been
reported on these cars as yet, the fact still exists that they can be controlled remotely and thus the great
need for cyberattack detectors. This is an area where the new sensors that focus on making use of mobile
and Internet of Things technology can greatly help those involved, the nation and the globe at large.
Though at first many may shy away due to the higher cost of sensors by the new system compared to the
older system, they will eventually see and even experience from the forerunners the effectiveness of
sensors from the new system. Even as demand increases and the sensors are produced in bulk, the cost
will go down hence attracting more and more customers day in day out.
Benefits Realisation Plan
As afore mentioned, the new system will offer a few benefits. To begin with, there is cloud computing
which will allow for real time communication, processing and response. Secondly, there is a milestone for
the country at large as far as cybersecurity is concerned. The country is now looking forward to the most
Project Constraints
Time frames: You cannot be so certain about time frames when it comes to IT projects but our
team will do the best to beat deadlines
Resources: The type, amount, and availability of resources to perform the project work are not
sufficient.
Personnel limitations: The personnel provided by both parties are not sufficient and hence the
need to work overtime to beat deadlines
Qualified employees to work with the new system
Expected Benefits
One major benefit from this project is a state of the art technology for developing sensors. We are looking
forward to sensors that need little human intervention as they can be accessed remotely through cloud
computing. These is a system that learns from past experience using the concept of machine learning from
its harvested data, big data. It thus incorporates artificial intelligence and is a more reliable system in
terms of accuracy when it comes to detecting cyberattacks and also other kinds of attacks. This system
will help develop sensors that have not been developed in the country before nor experienced by most of
the citizens.
Even better the new sensors from the system will open up new areas that are currently worrying due to
cyberattacks. As technology continues to permeate our lives, we move from operating technology to
integrating with it. This is especially true of autonomous systems that are by definition designed to blend
in with our society, becoming second nature. Take for example driverless cars and transport which have
taken all the limelight as far as autonomous systems are concerned. Though no cyberattacks have been
reported on these cars as yet, the fact still exists that they can be controlled remotely and thus the great
need for cyberattack detectors. This is an area where the new sensors that focus on making use of mobile
and Internet of Things technology can greatly help those involved, the nation and the globe at large.
Though at first many may shy away due to the higher cost of sensors by the new system compared to the
older system, they will eventually see and even experience from the forerunners the effectiveness of
sensors from the new system. Even as demand increases and the sensors are produced in bulk, the cost
will go down hence attracting more and more customers day in day out.
Benefits Realisation Plan
As afore mentioned, the new system will offer a few benefits. To begin with, there is cloud computing
which will allow for real time communication, processing and response. Secondly, there is a milestone for
the country at large as far as cybersecurity is concerned. The country is now looking forward to the most
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Plan Report 8
ever reliable sensors to counter cyberattacks. Sensors that are dynamic and that can learn from past data,
something enabled by the big data collected via cloud computing (Love et al., 2014). The country will
be the first in its small neighbourhood to produce these kind of cyberattack sensors and hence this is a
great opportunity to expand our customers behold national boundaries.
MQ IT Solutions is responsible for first the installation of cloud computing which will be useful as the
project advances and gets to the user acceptance testing stage. They will then hold the first training
session basically about the overview of what the new system is going to look like.
Components of the project
The new system will comprise of many components but a few key ones are mentioned
below;
1. Scope Statement
2. Critical Success Factors
3. Deliverables
4. Work Breakdown Structure
Scope Statement
The project is all about developing a new system for building sensor devices. The new system is supposed
to implement the use of mobile and Internet of Things technology to enhance the response capabilities of
the organization when it comes to incidence handling (Love et al., 2014). There is no existing
commercial off-the-shelf software suitable to be purchased for the organization. There are also
no prior similar projects to refer to. Due to this challenge, the project will start up with a survey
just to capture most of the expectations that the new system is supposed to address. The project
will also involve trainings and user acceptance testing all across its development.
Critical Success Factors
There are many success factors but the critical ones include the following;
Deadlines: Deliverables should always be submitted within the said time period. This is
going to apply both ways that is, us and also Daisy’s team.
Budget: This is critical for any project and so there is a need to stick within the said
budget to avoid elapsing the funds before the project is delivered (Rahi et al., 2012).
Quality standards: To build a project that satisfies the test of time, quality is key. As we
provide quality work it is also a means of marketing ourselves.
End user benefits: For this project we are going to make sure that the end user finds great
relief working with the new system. The efficiency must improve and human intervention
is going to be reduced.
ever reliable sensors to counter cyberattacks. Sensors that are dynamic and that can learn from past data,
something enabled by the big data collected via cloud computing (Love et al., 2014). The country will
be the first in its small neighbourhood to produce these kind of cyberattack sensors and hence this is a
great opportunity to expand our customers behold national boundaries.
MQ IT Solutions is responsible for first the installation of cloud computing which will be useful as the
project advances and gets to the user acceptance testing stage. They will then hold the first training
session basically about the overview of what the new system is going to look like.
Components of the project
The new system will comprise of many components but a few key ones are mentioned
below;
1. Scope Statement
2. Critical Success Factors
3. Deliverables
4. Work Breakdown Structure
Scope Statement
The project is all about developing a new system for building sensor devices. The new system is supposed
to implement the use of mobile and Internet of Things technology to enhance the response capabilities of
the organization when it comes to incidence handling (Love et al., 2014). There is no existing
commercial off-the-shelf software suitable to be purchased for the organization. There are also
no prior similar projects to refer to. Due to this challenge, the project will start up with a survey
just to capture most of the expectations that the new system is supposed to address. The project
will also involve trainings and user acceptance testing all across its development.
Critical Success Factors
There are many success factors but the critical ones include the following;
Deadlines: Deliverables should always be submitted within the said time period. This is
going to apply both ways that is, us and also Daisy’s team.
Budget: This is critical for any project and so there is a need to stick within the said
budget to avoid elapsing the funds before the project is delivered (Rahi et al., 2012).
Quality standards: To build a project that satisfies the test of time, quality is key. As we
provide quality work it is also a means of marketing ourselves.
End user benefits: For this project we are going to make sure that the end user finds great
relief working with the new system. The efficiency must improve and human intervention
is going to be reduced.

Project Plan Report 9
Minimal change orders: There is no need to build a system and then have every single bit
of it criticized for improvement during user acceptance testing. Therefore as the projects
team we are going to take our time and deliver a system that is close to perfection.
Low rate of product rejections: If we produce quality work then of the sensors produced
by our system, only a few of them may have complaints.
Employee satisfaction: Our key purpose as we build the new system is to come up with a
system that satisfies employees and actually motivates and excites them (Rahi et al.,
2012). That is the reason we are engaging all the system users to state their preferences
with regard to the new system. We are also aware that it is impossible to please every
single user as some users are normally against change even if for no valid reason.
Nevertheless, it will be our sole duty to bring every single user on board especially by
ensuring the system is as simple as possible to work with.
Deliverables
As stated earlier on, this project will deliver a system that utilizes mobile and Internet of Things
to enhance the organizations capabilities in terms of incidence handling. The deliverables may be
broken down as follows;
Cloud-based storage to meet Daisy’s request for cloud-based implementation
Support push-functionalities: Because of the urgency of cyberattack information, push-
functionalities like push
Software that is Open Source;
Incorporate information from social media such as Facebook and Twitter;
Must easily integrate with current systems (Coombs, 2015).
Work Breakdown Structure
The work can be broken down as follows;
Review and survey of the current system and its functionalities
Preliminary training
Actual system development
User acceptance and testing
Implementation
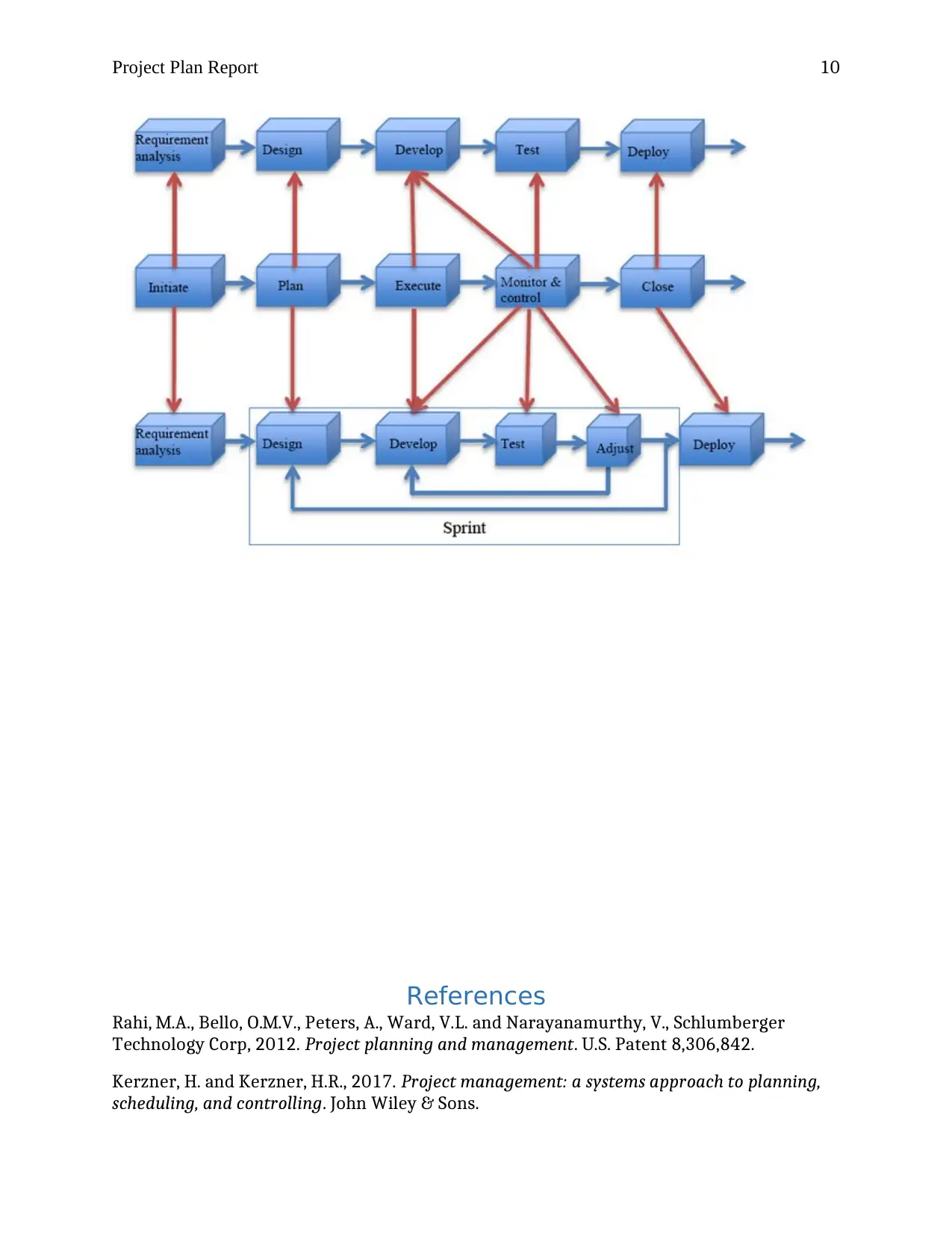
Project management process model
The following diagram illustrates the process model for building the new system for
making sensors.
Minimal change orders: There is no need to build a system and then have every single bit
of it criticized for improvement during user acceptance testing. Therefore as the projects
team we are going to take our time and deliver a system that is close to perfection.
Low rate of product rejections: If we produce quality work then of the sensors produced
by our system, only a few of them may have complaints.
Employee satisfaction: Our key purpose as we build the new system is to come up with a
system that satisfies employees and actually motivates and excites them (Rahi et al.,
2012). That is the reason we are engaging all the system users to state their preferences
with regard to the new system. We are also aware that it is impossible to please every
single user as some users are normally against change even if for no valid reason.
Nevertheless, it will be our sole duty to bring every single user on board especially by
ensuring the system is as simple as possible to work with.
Deliverables
As stated earlier on, this project will deliver a system that utilizes mobile and Internet of Things
to enhance the organizations capabilities in terms of incidence handling. The deliverables may be
broken down as follows;
Cloud-based storage to meet Daisy’s request for cloud-based implementation
Support push-functionalities: Because of the urgency of cyberattack information, push-
functionalities like push
Software that is Open Source;
Incorporate information from social media such as Facebook and Twitter;
Must easily integrate with current systems (Coombs, 2015).
Work Breakdown Structure
The work can be broken down as follows;
Review and survey of the current system and its functionalities
Preliminary training
Actual system development
User acceptance and testing
Implementation
Project management process model
The following diagram illustrates the process model for building the new system for
making sensors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Project Plan Report 10
References
Rahi, M.A., Bello, O.M.V., Peters, A., Ward, V.L. and Narayanamurthy, V., Schlumberger
Technology Corp, 2012. Project planning and management. U.S. Patent 8,306,842.
Kerzner, H. and Kerzner, H.R., 2017. Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
References
Rahi, M.A., Bello, O.M.V., Peters, A., Ward, V.L. and Narayanamurthy, V., Schlumberger
Technology Corp, 2012. Project planning and management. U.S. Patent 8,306,842.
Kerzner, H. and Kerzner, H.R., 2017. Project management: a systems approach to planning,
scheduling, and controlling. John Wiley & Sons.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Project Plan Report 11
Burke, R., 2013. Project management: planning and control techniques. New Jersey, USA.
Norman, T.A., Alcatel-Lucent SA, 2013. Methods and apparatus for associating and
displaying project planning and management information in conjunction with geographic
information. U.S. Patent 8,510,148.
Saunders, M.N. and Lewis, P., 2012. Doing research in business & management: An essential
guide to planning your project. Pearson.
Loucks, D.P. and Van Beek, E., 2017. Water resource systems planning and management: An
introduction to methods, models, and applications. Springer.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Harrison, F. and Lock, D., 2017. Advanced project management: a structured approach.
Routledge.
Fleming, Q.W. and Koppelman, J.M., 2016, December. Earned value project management.
Project Management Institute.
Turner, R., 2016. Gower handbook of project management. Routledge.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Lientz, B.P., 2011. Information technology project management. Palgrave Macmillan.
Buntin, M.B., Burke, M.F., Hoaglin, M.C. and Blumenthal, D., 2011. The benefits of health
information technology: a review of the recent literature shows predominantly positive
results. Health affairs, 30(3), pp.464-471.
Ru, X.W., Zhu, Y.H., Wu, H.Z. and Sun, L.W., 2013. Municipal Infrastructure Projects
Management and Decision-making Support System Based on GIS. In Advanced Materials
Research (Vol. 726, pp. 4596-4599). Trans Tech Publications.
Bryde, D., Broquetas, M. and Volm, J.M., 2013. The project benefits of building information
modelling (BIM). International journal of project management, 31(7), pp.971-980.
De Bakker, K., Boonstra, A. and Wortmann, H., 2010. Does risk management contribute to
IT project success? A meta-analysis of empirical evidence. International Journal of Project
Management, 28(5), pp.493-503.
Korobiichuk, I., Hryshchuk, R., Mamarev, V., Okhrimchuk, V. and Kachniarz, M., 2017,
September. Cyberattack Classificator Verification. In International Conference on
Diagnostics of Processes and Systems (pp. 402-411). Springer, Cham.
Parthasarathi, A., Ng, G.Y. and Honea, M., Cyence Inc, 2016. Cyber Risk Analysis and
Remediation Using Network Monitored Sensors and Methods of Use. U.S. Patent Application
15/082,890.
Burke, R., 2013. Project management: planning and control techniques. New Jersey, USA.
Norman, T.A., Alcatel-Lucent SA, 2013. Methods and apparatus for associating and
displaying project planning and management information in conjunction with geographic
information. U.S. Patent 8,510,148.
Saunders, M.N. and Lewis, P., 2012. Doing research in business & management: An essential
guide to planning your project. Pearson.
Loucks, D.P. and Van Beek, E., 2017. Water resource systems planning and management: An
introduction to methods, models, and applications. Springer.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Harrison, F. and Lock, D., 2017. Advanced project management: a structured approach.
Routledge.
Fleming, Q.W. and Koppelman, J.M., 2016, December. Earned value project management.
Project Management Institute.
Turner, R., 2016. Gower handbook of project management. Routledge.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
Lientz, B.P., 2011. Information technology project management. Palgrave Macmillan.
Buntin, M.B., Burke, M.F., Hoaglin, M.C. and Blumenthal, D., 2011. The benefits of health
information technology: a review of the recent literature shows predominantly positive
results. Health affairs, 30(3), pp.464-471.
Ru, X.W., Zhu, Y.H., Wu, H.Z. and Sun, L.W., 2013. Municipal Infrastructure Projects
Management and Decision-making Support System Based on GIS. In Advanced Materials
Research (Vol. 726, pp. 4596-4599). Trans Tech Publications.
Bryde, D., Broquetas, M. and Volm, J.M., 2013. The project benefits of building information
modelling (BIM). International journal of project management, 31(7), pp.971-980.
De Bakker, K., Boonstra, A. and Wortmann, H., 2010. Does risk management contribute to
IT project success? A meta-analysis of empirical evidence. International Journal of Project
Management, 28(5), pp.493-503.
Korobiichuk, I., Hryshchuk, R., Mamarev, V., Okhrimchuk, V. and Kachniarz, M., 2017,
September. Cyberattack Classificator Verification. In International Conference on
Diagnostics of Processes and Systems (pp. 402-411). Springer, Cham.
Parthasarathi, A., Ng, G.Y. and Honea, M., Cyence Inc, 2016. Cyber Risk Analysis and
Remediation Using Network Monitored Sensors and Methods of Use. U.S. Patent Application
15/082,890.

Project Plan Report 12
Koppel, T., 2015. Lights out: a cyberattack, a nation unprepared, surviving the aftermath.
Broadway Books.
Dupont, D.H. and Eskerod, P., 2016. Enhancing project benefit realization through
integration of line managers as project benefit managers. International Journal of Project
Management, 34(4), pp.779-788.
Coombs, C.R., 2015. When planned IS/IT project benefits are not realized: a study of
inhibitors and facilitators to benefits realization. International Journal of Project
Management, 33(2), pp.363-379.
Love, P.E., Matthews, J., Simpson, I., Hill, A. and Olatunji, O.A., 2014. A benefits realization
management building information modeling framework for asset owners. Automation in
construction, 37, pp.1-10.
Irani, Z., 2010. Investment evaluation within project management: an information systems
perspective. Journal of the Operational Research Society, 61(6), pp.917-928.
Gollenia, L.A., 2016. Business transformation management methodology. Routledge.
Mossalam, A. and Arafa, M., 2016. The role of project manager in benefits realization
management as a project constraint/driver. HBRC Journal, 12(3), pp.305-315.
Too, E.G. and Weaver, P., 2014. The management of project management: A conceptual
framework for project governance. International Journal of Project Management, 32(8),
pp.1382-1394.
Khampachua, T. and Wisitpongphan, N., 2014, May. ICT benefit realization for dairy farm
management: Challenges and future direction. In Computer Science and Software
Engineering (JCSSE), 2014 11th International Joint Conference on (pp. 280-285). IEEE.
Koppel, T., 2015. Lights out: a cyberattack, a nation unprepared, surviving the aftermath.
Broadway Books.
Dupont, D.H. and Eskerod, P., 2016. Enhancing project benefit realization through
integration of line managers as project benefit managers. International Journal of Project
Management, 34(4), pp.779-788.
Coombs, C.R., 2015. When planned IS/IT project benefits are not realized: a study of
inhibitors and facilitators to benefits realization. International Journal of Project
Management, 33(2), pp.363-379.
Love, P.E., Matthews, J., Simpson, I., Hill, A. and Olatunji, O.A., 2014. A benefits realization
management building information modeling framework for asset owners. Automation in
construction, 37, pp.1-10.
Irani, Z., 2010. Investment evaluation within project management: an information systems
perspective. Journal of the Operational Research Society, 61(6), pp.917-928.
Gollenia, L.A., 2016. Business transformation management methodology. Routledge.
Mossalam, A. and Arafa, M., 2016. The role of project manager in benefits realization
management as a project constraint/driver. HBRC Journal, 12(3), pp.305-315.
Too, E.G. and Weaver, P., 2014. The management of project management: A conceptual
framework for project governance. International Journal of Project Management, 32(8),
pp.1382-1394.
Khampachua, T. and Wisitpongphan, N., 2014, May. ICT benefit realization for dairy farm
management: Challenges and future direction. In Computer Science and Software
Engineering (JCSSE), 2014 11th International Joint Conference on (pp. 280-285). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


