Analysis of AI and IoT Technologies: A Detailed Report
VerifiedAdded on 2020/02/24
|8
|1536
|90
Report
AI Summary
This report delves into various aspects of Artificial Intelligence (AI) and the Internet of Things (IoT). It begins by exploring user interfaces, discussing visual collaboration, and the evolution of UI/no-UI interactions, touching upon software and hardware sensing paired with AI. The report then examines bandwidth considerations for different technologies (twisted pair, coaxial, fiber) and their associated costs and security levels. Further, it analyzes the role of sensors, including smart sensors, RFID, and video tracking, highlighting their applications in various sectors. The report also addresses the security and privacy risks associated with data collection, specifically concerning mobile applications and corporate transparency. It presents calculations related to processing time and communication models, along with an analysis of Nielsen's Law and Moore's Law concerning bandwidth and computing capabilities. References from academic sources are included to support the findings.
report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................2
Answer 3:.........................................................................................................................................3
Answer 4:.........................................................................................................................................5
Answer 5:.........................................................................................................................................6
Answer 6:.........................................................................................................................................6
References........................................................................................................................................7
Answer 1:.........................................................................................................................................2
Answer 2:.........................................................................................................................................2
Answer 3:.........................................................................................................................................3
Answer 4:.........................................................................................................................................5
Answer 5:.........................................................................................................................................6
Answer 6:.........................................................................................................................................6
References........................................................................................................................................7
Answer 1:
The user interface is mainly set with the concept which relates to the details defined in the
technology industry. For this, there are user interface and the extensions where the complete
genre is set for the building of the business with the proper setup of the UI. There is a visual
collaboration which relates to the personal solutions like the mobile and the desktop applications.
There are different cases where the customers are working on handling the no user training with
the group systems that are under the pressure of launching a proper collaboration. The pushing
content with the management of the participants is mainly magnified with the enabling of natural
movements to adjust the individual working. (Li et al, 2017). The no user interface is also able to
work on the different perspectives which relates to the collaboration and how the technology
oriented working is adjusted for this. Without any UI, there is a possibility to work with the UI
and to work on the vibration cue that is set with the computing devices for the interaction
options. The software and the hardware sensing is paired mainly with the Artificial Intelligence
which continue to transform depending upon the computing devices. Some of the examples of
the same are icon driven interfaces with the long, short and the double tapping. He other example
is how the no UI is able to handle the initiation of the responses with the factoring.
Answer 2:
Bandwidth distance Interference
rate
cost Security
Twisted <100MHz low Medium Cheapest Medium
Coaxial <1Ghz More than Medium Moderate Medium
The user interface is mainly set with the concept which relates to the details defined in the
technology industry. For this, there are user interface and the extensions where the complete
genre is set for the building of the business with the proper setup of the UI. There is a visual
collaboration which relates to the personal solutions like the mobile and the desktop applications.
There are different cases where the customers are working on handling the no user training with
the group systems that are under the pressure of launching a proper collaboration. The pushing
content with the management of the participants is mainly magnified with the enabling of natural
movements to adjust the individual working. (Li et al, 2017). The no user interface is also able to
work on the different perspectives which relates to the collaboration and how the technology
oriented working is adjusted for this. Without any UI, there is a possibility to work with the UI
and to work on the vibration cue that is set with the computing devices for the interaction
options. The software and the hardware sensing is paired mainly with the Artificial Intelligence
which continue to transform depending upon the computing devices. Some of the examples of
the same are icon driven interfaces with the long, short and the double tapping. He other example
is how the no UI is able to handle the initiation of the responses with the factoring.
Answer 2:
Bandwidth distance Interference
rate
cost Security
Twisted <100MHz low Medium Cheapest Medium
Coaxial <1Ghz More than Medium Moderate Medium
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
twisted
Fibre <10Ghz highest High Expensive High
Answer 3:
Sensors
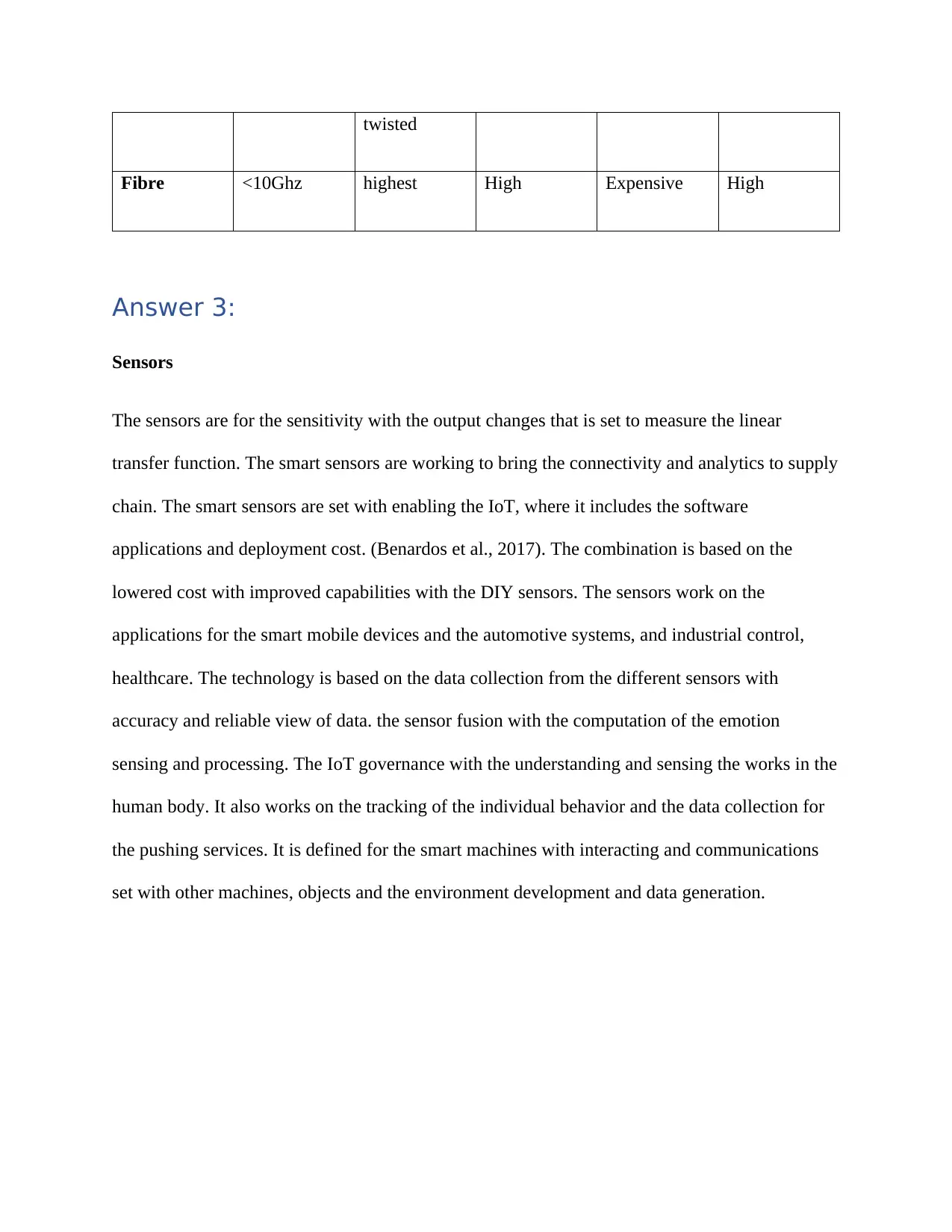
The sensors are for the sensitivity with the output changes that is set to measure the linear
transfer function. The smart sensors are working to bring the connectivity and analytics to supply
chain. The smart sensors are set with enabling the IoT, where it includes the software
applications and deployment cost. (Benardos et al., 2017). The combination is based on the
lowered cost with improved capabilities with the DIY sensors. The sensors work on the
applications for the smart mobile devices and the automotive systems, and industrial control,
healthcare. The technology is based on the data collection from the different sensors with
accuracy and reliable view of data. the sensor fusion with the computation of the emotion
sensing and processing. The IoT governance with the understanding and sensing the works in the
human body. It also works on the tracking of the individual behavior and the data collection for
the pushing services. It is defined for the smart machines with interacting and communications
set with other machines, objects and the environment development and data generation.
Fibre <10Ghz highest High Expensive High
Answer 3:
Sensors
The sensors are for the sensitivity with the output changes that is set to measure the linear
transfer function. The smart sensors are working to bring the connectivity and analytics to supply
chain. The smart sensors are set with enabling the IoT, where it includes the software
applications and deployment cost. (Benardos et al., 2017). The combination is based on the
lowered cost with improved capabilities with the DIY sensors. The sensors work on the
applications for the smart mobile devices and the automotive systems, and industrial control,
healthcare. The technology is based on the data collection from the different sensors with
accuracy and reliable view of data. the sensor fusion with the computation of the emotion
sensing and processing. The IoT governance with the understanding and sensing the works in the
human body. It also works on the tracking of the individual behavior and the data collection for
the pushing services. It is defined for the smart machines with interacting and communications
set with other machines, objects and the environment development and data generation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
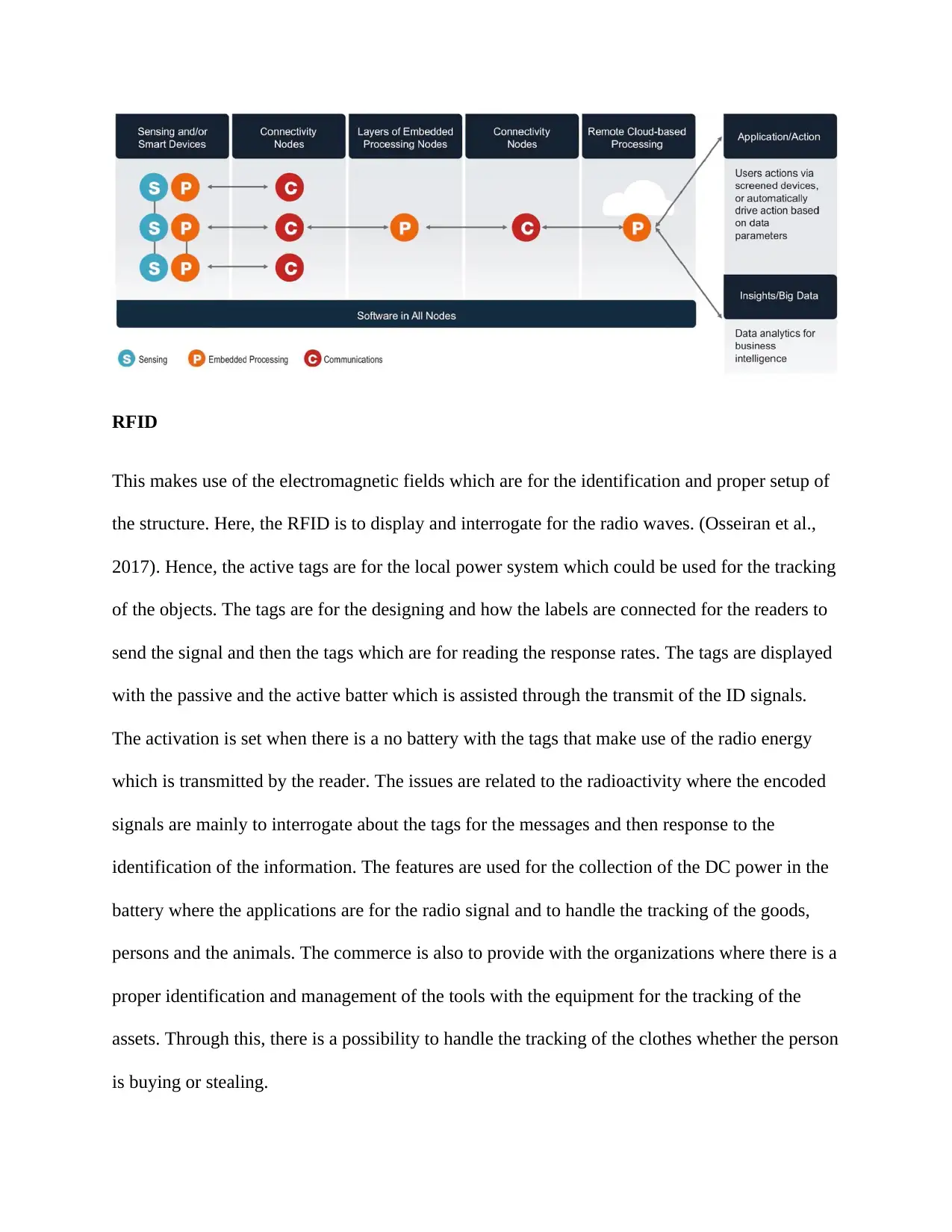
RFID
This makes use of the electromagnetic fields which are for the identification and proper setup of
the structure. Here, the RFID is to display and interrogate for the radio waves. (Osseiran et al.,
2017). Hence, the active tags are for the local power system which could be used for the tracking
of the objects. The tags are for the designing and how the labels are connected for the readers to
send the signal and then the tags which are for reading the response rates. The tags are displayed
with the passive and the active batter which is assisted through the transmit of the ID signals.
The activation is set when there is a no battery with the tags that make use of the radio energy
which is transmitted by the reader. The issues are related to the radioactivity where the encoded
signals are mainly to interrogate about the tags for the messages and then response to the
identification of the information. The features are used for the collection of the DC power in the
battery where the applications are for the radio signal and to handle the tracking of the goods,
persons and the animals. The commerce is also to provide with the organizations where there is a
proper identification and management of the tools with the equipment for the tracking of the
assets. Through this, there is a possibility to handle the tracking of the clothes whether the person
is buying or stealing.
This makes use of the electromagnetic fields which are for the identification and proper setup of
the structure. Here, the RFID is to display and interrogate for the radio waves. (Osseiran et al.,
2017). Hence, the active tags are for the local power system which could be used for the tracking
of the objects. The tags are for the designing and how the labels are connected for the readers to
send the signal and then the tags which are for reading the response rates. The tags are displayed
with the passive and the active batter which is assisted through the transmit of the ID signals.
The activation is set when there is a no battery with the tags that make use of the radio energy
which is transmitted by the reader. The issues are related to the radioactivity where the encoded
signals are mainly to interrogate about the tags for the messages and then response to the
identification of the information. The features are used for the collection of the DC power in the
battery where the applications are for the radio signal and to handle the tracking of the goods,
persons and the animals. The commerce is also to provide with the organizations where there is a
proper identification and management of the tools with the equipment for the tracking of the
assets. Through this, there is a possibility to handle the tracking of the clothes whether the person
is buying or stealing.

Video Tracking
This is based on tracking and locating the objects. The time-consuming processes with the data
amounts are set where there are complexities with proper recognition of the objects. The tracking
and the challenging is associated with the target set for the employing of the motion model. The
example related to this is the tracking of the planar objects with the motion model that is for the
2D transformation of the image of the object. (Sharma et al., 2017). The issue is about the
orientation that is set with time. For the filtering and the data association, it includes the
incorporation of the information and the methods which are important to track all the complex
objects. The complexity is mainly due to the contour tracking and then working on the kernel
based tracking. Here, the methods are evaluated based on inertial measurement system with the
ability to pre-stabilize and reduce the required forms of the dynamic systems.
Answer 4:
This is considered to be dangerous mainly due to the fact that the data is unaware of what is
being collected. The mobile applications and the other products are connected to the Wi-Fi
where there are consumers who have the ability to run the virus and this leads to the loss of
information as well. There is other increased corporate transparency where the industry self-
regulation is set from the consumers with the collection of the data. The issues related to the lack
of the transport encryption, default credentials and the lack of the security of the code practices,
and the privacy concerns. They are considered the issue for handling the personal information.
Answer 5:
The time requested for the trigger is 1 s. the round trip is 12 ms and the processing time for the
request is 3ms where the application transportation is 2ms. The complete time is:
This is based on tracking and locating the objects. The time-consuming processes with the data
amounts are set where there are complexities with proper recognition of the objects. The tracking
and the challenging is associated with the target set for the employing of the motion model. The
example related to this is the tracking of the planar objects with the motion model that is for the
2D transformation of the image of the object. (Sharma et al., 2017). The issue is about the
orientation that is set with time. For the filtering and the data association, it includes the
incorporation of the information and the methods which are important to track all the complex
objects. The complexity is mainly due to the contour tracking and then working on the kernel
based tracking. Here, the methods are evaluated based on inertial measurement system with the
ability to pre-stabilize and reduce the required forms of the dynamic systems.
Answer 4:
This is considered to be dangerous mainly due to the fact that the data is unaware of what is
being collected. The mobile applications and the other products are connected to the Wi-Fi
where there are consumers who have the ability to run the virus and this leads to the loss of
information as well. There is other increased corporate transparency where the industry self-
regulation is set from the consumers with the collection of the data. The issues related to the lack
of the transport encryption, default credentials and the lack of the security of the code practices,
and the privacy concerns. They are considered the issue for handling the personal information.
Answer 5:
The time requested for the trigger is 1 s. the round trip is 12 ms and the processing time for the
request is 3ms where the application transportation is 2ms. The complete time is:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1s+12ms+3ms+2m+2ms = 1.019 s
The publishing and setting a proper communication model is based on working over the request
time with the span of 1second which is removed. The processing request time is then handled
where the round trip gets half and the data transport could be done through one way. Hence, the
time is 6ms and 2ms=8ms.
Answer 6:
Neilsen law is based on the telecom companies which are becoming conservative. Here, the users
are working with the focus on handling the reluctance to spend the money on the bandwidth.
With this, the user base is also getting broader with the mainstream users who try to get the
information online. For this, there are certain low-end users than the high end which works
toward the average shifts which are even low. The technologies are based on the delivering of
the technologies which are related to the computing with the screen quality. The computation is
based on the tasks where there are higher speed and high cost options. It is seen that Moore’s law
is mainly for handling the computer’s capability which leads to the doubling of the capabilities in
the different times. (Oberlaender et al., 2017). Hence, the correspondence to the same is found to
be 60% of the annual growth where the bandwidth will tend to remain with gating factor.
The publishing and setting a proper communication model is based on working over the request
time with the span of 1second which is removed. The processing request time is then handled
where the round trip gets half and the data transport could be done through one way. Hence, the
time is 6ms and 2ms=8ms.
Answer 6:
Neilsen law is based on the telecom companies which are becoming conservative. Here, the users
are working with the focus on handling the reluctance to spend the money on the bandwidth.
With this, the user base is also getting broader with the mainstream users who try to get the
information online. For this, there are certain low-end users than the high end which works
toward the average shifts which are even low. The technologies are based on the delivering of
the technologies which are related to the computing with the screen quality. The computation is
based on the tasks where there are higher speed and high cost options. It is seen that Moore’s law
is mainly for handling the computer’s capability which leads to the doubling of the capabilities in
the different times. (Oberlaender et al., 2017). Hence, the correspondence to the same is found to
be 60% of the annual growth where the bandwidth will tend to remain with gating factor.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Benardos, P. G., & Vosniakos, G. C. (2017). Internet of things and industrial applications for precision
machining. In Solid State Phenomena (Vol. 261, pp. 440-447). Trans Tech Publications.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Oberlaender, A. M., Roeglinger, M., Rosemann, M., & Kees, A. (2017). Conceptualising business-to-thing
interactions–a sociomaterial perspective on the Internet of Things. European Journal of
Information Systems.
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE Communications
Standards Magazine, 1(2), 84-84.
Sharma, V., Sharma, V., & Mishra, N. (2017). Internet of Things. Exploring the Convergence of Big Data
and the Internet of Things, 73.
Benardos, P. G., & Vosniakos, G. C. (2017). Internet of things and industrial applications for precision
machining. In Solid State Phenomena (Vol. 261, pp. 440-447). Trans Tech Publications.
Li, S., & Da Xu, L. (2017). Securing the Internet of Things. Syngress.
Oberlaender, A. M., Roeglinger, M., Rosemann, M., & Kees, A. (2017). Conceptualising business-to-thing
interactions–a sociomaterial perspective on the Internet of Things. European Journal of
Information Systems.
Osseiran, A., Elloumi, O., Song, J., & Monserrat, J. F. (2017). Internet of Things. IEEE Communications
Standards Magazine, 1(2), 84-84.
Sharma, V., Sharma, V., & Mishra, N. (2017). Internet of Things. Exploring the Convergence of Big Data
and the Internet of Things, 73.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





